38.3 Administering Identity Federation As A Service Provider
When the integrated Identity Federation is configured as an SP, you must define any remote IdP partners as trusted by creating and managing profiles that contain details regarding each remote IdP.
To begin administration of the integrated Identity Federation server as an SP, click the Service Provider Administration link under Identity Federation from the Launch Pad in the Oracle Access Management Console. This section provides the following topics.
38.3.1 Creating Remote Identity Provider Partners
Use the New Identity Provider Page to define an identity provider (IdP) partner record for Access Manager. You can specify service details manually or load them from a metadata file.
Figure 38-1 shows the Create Identity Provider Partner page when service details are configured by loading an XML metadata file.
Figure 38-1 New Identity Provider Page, Service Details Loaded from Metadata
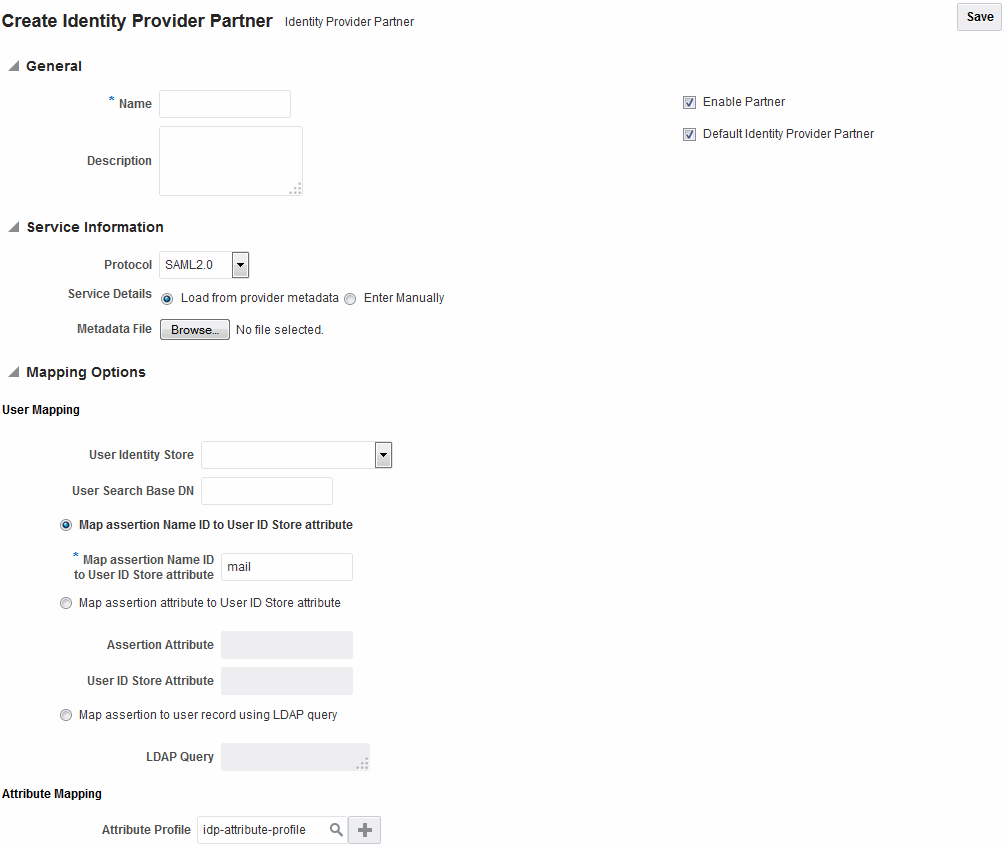
Description of "Figure 38-1 New Identity Provider Page, Service Details Loaded from Metadata"
Figure 38-2 shows the Create Identity Provider Partner page when service details are configured by entering values manually.
Figure 38-2 New Identity Provider Page, Service Details entered Manually
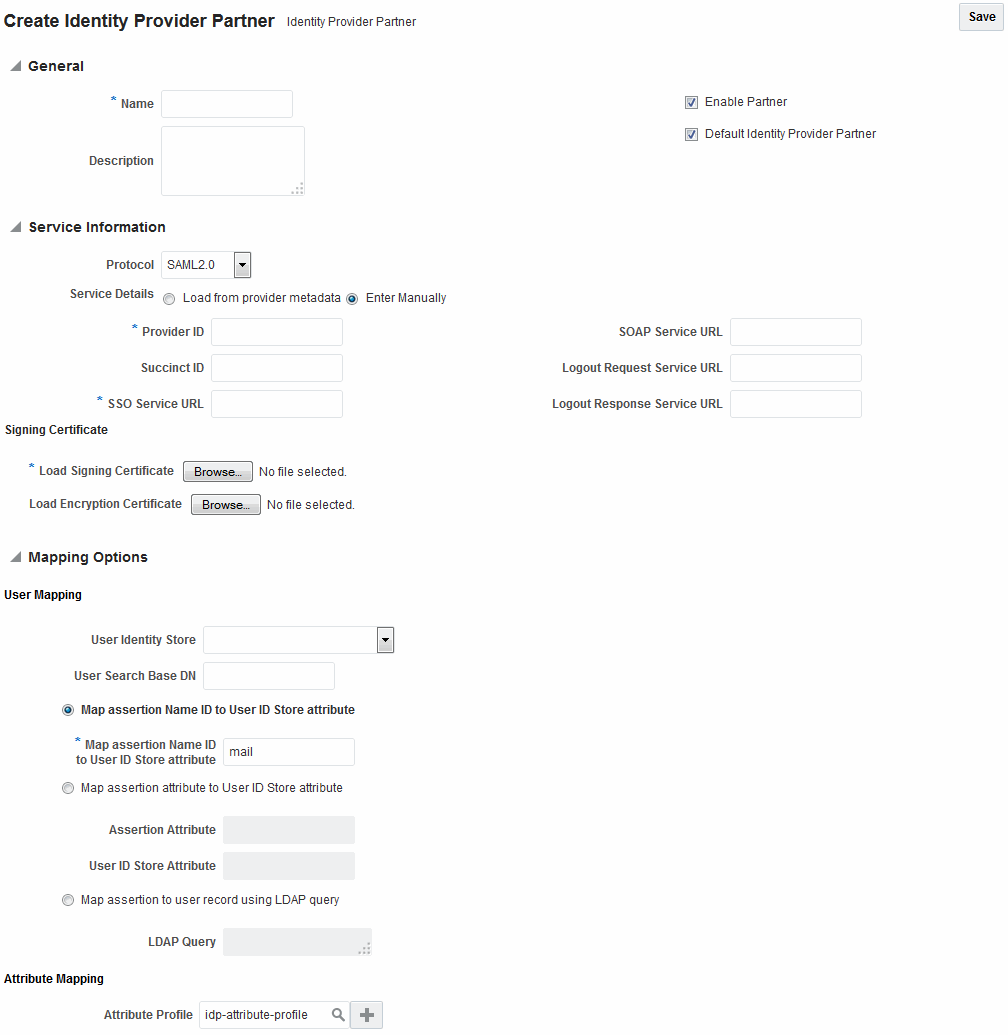
Description of "Figure 38-2 New Identity Provider Page, Service Details entered Manually"
Table 38-2 describes each element on the New Identity Provider page.
Table 38-2 Identity Provider Partner Settings
| Element | Description |
|---|---|
|
Name |
This is the provider name. |
|
Description |
This is a brief description of the provider. (Optional). |
|
Protocol |
This is the provider protocol (SAML 1.1, SAML 2.0 and so on). |
|
Service Details |
This drop-down enables you to choose whether to enter service details manually or load from metadata. |
|
Metadata File |
This field appears if loading metadata from a file. Click Browse to select a file to use. Applies to SAML 2.0 only. |
|
Issuer ID |
This is the issuer ID of the provider. Applies to SAML 2.0 and SAML 1.1 only. |
|
Succinct ID |
This is the succinct ID of the provider. This element is required if using the artifact profile. Applies to SAML 2.0 and SAML 1.1 only. |
|
SSO Service URL |
This is the URL address to which SSO requests are sent. |
|
SOAP Service URL |
This is the URL address to which a SOAP service request is sent. This element is required if using artifact profile. |
|
Logout Request Service URL |
This is the URL address to which a logout request is sent by the provider. This element is required if using the logout feature. Applies to SAML 2.0 only. |
|
Logout Response Service URL |
This is the URL address to which a logout response is sent. This element is required if using the logout feature. Applies to SAML 2.0 only. |
|
Signing Certificate |
This is the signing certificate used by the provider. You can specify it in |
|
User Identity Store |
This is the identity store in which the IdP's users will be located and mapped. Identity Federation supports multiple identity stores, defined on a per-partner basis. Optionally, if no user identity store is selected, the default Access Manager store is used. |
|
User Search Base DN |
This is the base search DN used when looking up user records. (Optional.) If omitted, the default user search base DN configured for the selected user identity store is used.) |
|
Mapping Option |
This setting indicates how an incoming assertion is mapped to a user in the identity store. Select one of the following:
|
|
Enable Basic HTTP Authentication |
Check this box to accept HTTP basic credentials. (Advanced element, available only in provider Edit mode.) |
|
Attribute Mapping Profile |
Indicates the attribute profile to which the partner is bound. |
|
Service Details |
Indicates which of the following options Identity Federation (the RP) uses to perform Federation SSO with the IdP. Applies to OpenID 2.0 only.
|
|
Discovery URL |
Defines the location where the IdP publishes its XRDS metadata. Applies to OpenID 2.0 only. |
|
Endpoint URL |
Defines the IdP SSO Service location. Applies to OpenID 2.0 only. |
|
Enable Global Logout |
Indicates whether or not Identity Federation should notify the remote partner when the user is signing off during the logout flow. Applies to SAML 2.0 only. |
|
HTTP POST SSO Response Binding |
Indicates whether the SAML Assertion should be sent back from the IdP using the HTTP POST Binding or the Artifact Binding. Applies to SAML 2.0 only. |
|
Authentication Request NameID Format |
Indicates the NameID format that Identity Federation will request from the IdP during the Federation SSO operation. If none is selected, a NameID format is not specified in the request. Applies to SAML 2.0 only. |
38.3.1.1 Defining a New SAML 2.0 Identity Provider for Federation
You can define a new SAML 2.0 identity provider (IdP) for federation.
To create a new identity provider:
- In the Oracle Access Management Console, click Federation at the top of the window.
- In the Federation console, select Create Identity Provider Partner from the Create (+) drop-down list in the Federation section.
- In the Service Details field, select Load from provider metadata. (SAML 2.0 is typically configured with metadata.)
- A new field named Metadata File appears. Click Browse.
- Select the metadata file of interest.
- The metadata is loaded from the file.
- Click Save to create the Identity Provider definition.
38.3.1.2 Defining a New SAML 1.1 Identity Provider for Federation
You can define a new SAML 1.1 identity provider (IdP) for federation.
To create a new identity provider:
38.3.1.3 Defining a New OpenID 2.0 Identity Providers for Federation
In 11g Release 2 (11.1.2.3) the Identity Federation supports OpenID, and acts as an OpenID RP/SP. OpenID Providers can be registered as IdP partners.
Authentication schemes created using these OpenID partners protect Access Manager resources using authentication services provided by the OpenID identity providers.
To define a new OpenID 2.0 identity provider (IdP) for federation:
-
In the Oracle Access Management Console, click Federation at the top of the window.
-
In the Federation console, select Create Identity Provider Partner from the Create (+) drop-down list in the Federation section.
-
Fill in the values appropriate for your environment either manually or by uploading a metadata file.
The information you provide depends on the protocol chosen for the provider and other factors.
-
Click Save to create the identity provider definition.
Google IdP Partners
To add Google as an OpenID 2.0 IdP.
-
In the Oracle Access Management Console, click Federation at the top of the window.
-
In the Federation console, select Create Identity Provider Partner from the Create (+) drop-down list in the Federation section.
-
From the Launch Pad, click Service Provider Administration under Identity Federation.
-
Select OpenID 2.0 from the Protocol drop down menu.
-
Select Google provider default settings from the Service Details drop down menu.
-
Click Save to create the identity provider definition.
The partner is configured so that the SP requests the assertion attributes from the Google IdP and maps them to the corresponding session attribute names:
SeeTable 38-3.
Table 38-3 Attributes for Google OpenID Partner
| Assertion Attribute Name | Session Attribute Name |
|---|---|
|
http://axschema.org/contact/country/home |
country |
|
http://axschema.org/contact/email |
|
|
http://axschema.org/namePerson/first |
firstname |
|
http://axschema.org/pref/language |
language |
|
http://axschema.org/namePerson/last |
lastname |
The Google partner uses mail as the user mapping attribute, so that an incoming http://axschema.org/contact/email attribute should match the mail attribute of the user in the user identity store.
Yahoo IdP Partners
To add Yahoo as an OpenID 2.0 IdP:
- In the Oracle Access Management Console, click Federation at the top of the window.
- In the Federation console, select Create Identity Provider Partner from the Create (+) drop-down list in the Federation section.
- Select OpenID 2.0 from the Protocol drop down menu.
- Select Yahoo provider default settings from the Service Details drop down menu.
- Click Save to create the identity provider definition.
The partner is configured so that the SP requests the assertion attributes from the Yahoo IdP and maps them to the corresponding session attribute names:
See Table 38-4.
Table 38-4 Attributes for Yahoo OpenID Partner
| Assertion Attribute Name | Session Attribute Name |
|---|---|
|
http://axschema.org/contact/country/home |
country |
|
http://axschema.org/contact/email |
|
|
http://axschema.org/namePerson/first |
firstname |
|
http://axschema.org/pref/language |
language |
|
http://axschema.org/namePerson/last |
lastname |
The yahoo partner uses mail as the user mapping attribute, so that an incoming http://axschema.org/contact/email attribute should match the mail attribute of the user in the user identity store.
38.3.1.4 Enabling OpenID Simple Registration
By default, Identity federation uses the Attribute Exchange extension to obtain user identity attributes from an OpenID IdP.
However, if you need to use the older Simple Registration (SREG) extension, you can enable it by running the following WLST commands:
putBooleanProperty("/spglobal/openid20axenabled", "false")
putBooleanProperty("/spglobal/openid20sregenabled", "true")
38.3.1.5 Disabling OpenID Simple Registration
You can disable Simple Registration to Attribute Exchange extension.
To switch from the Simple Registration (SREG) extension to the Attribute Exchange extension to obtain user identity attributes from an OpenID IdP:
putBooleanProperty("/spglobal/openid20axenabled", "true")
putBooleanProperty("/spglobal/openid20sregenabled", "false")