2 Manage Assets
Overview of actions included in managing assets in Oracle Enterprise Manager Ops Center.
Asset management is the process through which you discover your assets and organize them using groups and tags.
Topics
Introduction to Asset Management
Definition of asset management in Oracle Enterprise Manager Ops Center.
Asset management is the process through which Oracle Enterprise Manager Ops Center discovers your datacenter's assets and begins to manage and monitor them. Assets include server hardware, chassis, racks, network equipment, operating systems, virtualization software, and clustering software. Discovering assets is a prerequisite for almost every action in the software.
Roles for Asset Management
List of required roles for asset management tasks in Oracle Enterprise Manager Ops Center.
Table 2–1 lists the tasks and the role required to complete the task. Contact your administrator if you do not have the necessary role or privilege to complete a task. See Oracle Enterprise Manager Ops Center Administration for information about the different roles and the permissions they grant.
Table 2-1 Asset Management Tasks and Roles
| Task | Role |
|---|---|
|
View Assets |
Read |
|
Add Assets |
Asset Admin |
|
Find Assets |
Asset Admin |
|
Create Discovery Profile |
Asset Admin |
|
Update Management Credentials |
Security Admin |
|
Edit Asset Attributes |
Asset Admin |
|
Edit Access Points |
Security Admin |
|
Delete Assets |
Asset Admin |
|
Edit Tags |
Asset Management |
|
Create Group |
Asset Admin SuperCluster Systems Admin |
|
Edit Group |
Asset Admin SuperCluster Systems Admin |
|
Move Group |
Asset Admin SuperCluster Systems Admin |
|
Add or Remove Assets From a Group |
Asset Admin SuperCluster Systems Admin |
|
Delete Group |
Asset Admin SuperCluster Systems Admin |
Actions Available for Asset Management
List of available operations in Oracle Enterprise Manager Ops Center.
You can perform a variety of asset management actions, depending on the needs of your environment:
-
Add Assets by Declaring Servers for OS Provisioning
-
Add Assets by Declaring Servers for Service Processor Configuration
-
Add Assets Using a Discovery Profile
-
Find Assets
-
Create a Discovery Profile
-
Edit a Discovery Profile
-
Copy a Discovery Profile
-
Delete a Discovery Profile
-
Install Agent Controllers From the Command Line
-
Update Management Credentials
-
Edit Asset Attributes
-
Delete Assets
-
Use Access Points
Location of Asset Information in the User Interface
Lists the location of information about assets in Oracle Enterprise Manager Ops Center.
Asset Management actions and information are located in several sections of the user interface.
Table 2-2 Location of Asset Management Information in the BUI
| To Display: | Select: |
|---|---|
|
Asset Discovery and Management actions |
Expand Assets in the Navigation pane. |
|
Discovery Profiles |
Expand Plan Management in the Navigation pane, then select Discovery in the Profiles and Policies section. |
|
Number of assets’ access points |
Select Administration, then the Enterprise Controller. Click the Asset Counter tab in the center pane. |
About Discovering Assets
Overview of discovery of assets in Oracle Enterprise Manager Ops Center.
To manage an asset, you must first discover it. The discovery process locates the asset, logs into it, identifies its attributes and status, and populates the All Assets section of the Navigation pane. To discover an asset, you direct Oracle Enterprise Manager Ops Center to search for assets that comply with one of the following: a discovery profile, service tags, or specific server information.
After assets have been discovered, they are managed assets, giving Oracle Enterprise Manager Ops Center access to monitor them and make them available as targets for jobs that update and provision them.
Before You Begin to Discover Assets
Describes requirements for discovering various types of assets in Oracle Enterprise Manager Ops Center.
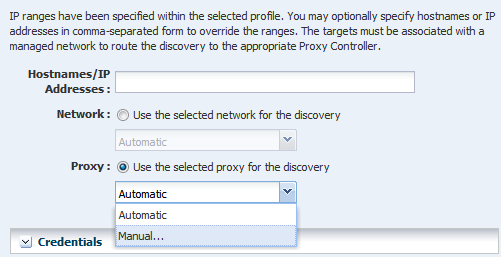
Oracle Enterprise Manager Ops Center requires at least one Proxy Controller that is accessible on a network before discovering and managing an asset on that network.
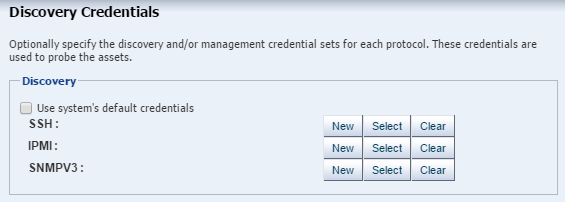
To discover and manage hardware assets, you must provide a set of credentials: a user account and password.
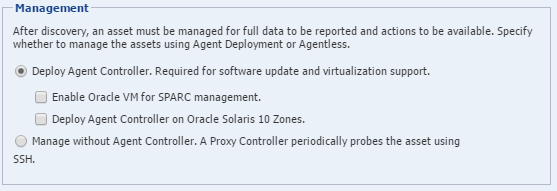
To discover and manage operating systems, you have the option of using an agent or using SSH transactions to manage the asset:
-
The default discovery installs an Agent Controller, software that can only respond to queries and commands from the Proxy Controller. The OS becomes an agent-managed asset and Oracle Enterprise Manager Ops Center can manage the asset completely. It takes several minutes for the Agent Controller to register in the Enterprise Controller and Oracle SE Java Runtime Environment is required. Non-Oracle versions work initially but might exhibit performance and memory issues.
-
You can choose to manage the asset through an SSH connection. For this agentless-managed asset, the Proxy Controller uses SSH credentials to probe and to perform actions on the OS. This mode is suitable for sites where installing the Agent Controller on an asset is not permitted or where full management capabilities, such as updating the OS, are not needed.
- You can change the mode after discovery, by either re-discovering the agent or using the Switch Management Access action. The current mode and the type of Agent Controller is displayed on the operating system's Dashboard. When you are changing the mode from agentless to agent-managed asset using the Switch Management Access action, you must provide the SNMPV3 credentials. See Switching Between Agent Controllers or Agent and Agentless for more details on selecting or adding the SNMPV3 credentials.
In addition to the Agent Controller, virtual assets use a Virtualization Controller to enable full monitoring and management capability.
-
Oracle VM Server for SPARC Virtualization Controller Agent: Manages the logical domains that run in the Control Domain. The agent monitors the configuration and reflects any changes on the configuration in its copy of the metadata.
-
Zones Virtualization Controller Agent: Manages the zones that run on the logical domains. The global zone is an asset and its non-global zones are assets.
If full management capabilities are not needed or not allowed, you have the option to manage these assets agentlessly. In the same way as the operating system’s Agent Controller, an agentless-managed virtual asset is monitored through an SSH connection between the logical domains and the Proxy Controller.
See “Functionality With and Without Agent Controllers” in the Oracle Enterprise Manager Operation Reference for a comparison of agent-managed assets and agentless-managed assets.
When using the SSH protocol to discover and manage assets, you have the option to enable the escalation of privileges on the target asset when the asset is discovered or managed. You must prepare the asset to allow escalation and then create credentials that use escalation. The privileges for the login account are escalated when SSH credentials are used with the sudo command or an Ops Center role is associated with the account.
You request this escalation when you create the credentials. To prepare the SSH credentials to use sudo, see “Preparing to Use sudo”. For instructions in creating credentials with escalated privileges, see “Creating Management Credentials.”
Some systems have unique discovery procedures. See “Special Discovery and Management Procedures.”
Actions for Proxy Controllers
Lists the actions available for managing a Proxy Controller in Oracle Enterprise Manager Ops Center.
Before you can discover an asset, create at least one Proxy Controller and associate it with at least one network. Proxy Controllers in maintenance mode and unreachable Proxy Controllers do not participate in discovery operations.
Oracle Enterprise Manager Ops Center Administration includes information to view and manage proxy controllers:
-
To associate, enable, and disable a network in a proxy controller see
Managing Proxy Controller Networks. -
To migrate an asset to a different proxy controller see
Migrating Assets Between Proxy Controllers. -
To view the status of a proxy controller see
Viewing Proxy Controllers. -
To check the status, start, stop, and set the maintenance mode of a proxy controller see
Viewing and Changing the EC, PC, and AC Status.
Preparing to Use sudo
Procedure to enable escalation of SSH credentials on discovered assets in Oracle Enterprise Manager Ops Center.
Example 2-1 Format of sudoers File for Ops Center
## sudoers file.
##
## This file MUST be edited with the 'visudo' command as root.
## Failure to use 'visudo' may result in syntax or file permission errors
## that prevent sudo from running.
##
## See the sudoers man page for the details on how to write a sudoers file.
##
##
## Host alias specification
##
## Groups of machines. These may include host names (optionally with wildcards),
## IP addresses, network numbers or netgroups.
# Host_Alias WEBSERVERS = www1, www2, www3
##
## User alias specification
##
## Groups of users. These may consist of user names, uids, Unix groups,
## or netgroups.
User_Alias OPSCENTER = <username>
##
## Cmnd alias specification
##
## Groups of commands. Often used to group related commands together.
Cmnd_Alias SOLARIS_DISCOVERY = /sbin/ifconfig -a, \
/usr/sbin/virtinfo -ap, \
/usr/sbin/dladm, \
/opt/SUNWldm/bin/ldm
Cmnd_Alias SOLARIS_PROVISIONING = /usr/bin/sc-console, \
/var/scn/install/uninstall, \
/usr/sbin/zlogin, \
/bin/cat */opt/SUNWxvm/xvm_zone_id, \
/var/tmp/OpsCenterAgent/install, \
/opt/SUNWxvmoc/bin/agentadm, \
/usr/lib/cacao/bin/cacaoadm, \
/usr/bin/unzip -q -o -d /var/tmp/ /var/tmp/OpsCenterAgent*
Cmnd_Alias LINUX_DISCOVERY = /sbin/ifconfig -a, \
/usr/sbin/virtinfo -ap
Cmnd_Alias LINUX_PROVISIONING = /usr/bin/sc-console, \
/var/scn/install/uninstall, \
/tmp/OpsCenterAgent/install, \
/opt/sun/xvmoc/bin/agentadm, \
/opt/sun/cacao2/bin/cacaoadm, \
/usr/bin/unzip -q -o -d /tmp/ /tmp/OpsCenterAgent*
##
## Defaults specification
##
## You may wish to keep some of the following environment variables
## when running commands via sudo.
##
## Locale settings
# Defaults env_keep += "LANG LANGUAGE LINGUAS LC_* _XKB_CHARSET"
##
## Run X applications through sudo; HOME is used to find the
## .Xauthority file. Note that other programs use HOME to find
## configuration files and this may lead to privilege escalation!
# Defaults env_keep += "HOME"
##
## X11 resource path settings
# Defaults env_keep += "XAPPLRESDIR XFILESEARCHPATH XUSERFILESEARCHPATH"
##
## Desktop path settings
# Defaults env_keep += "QTDIR KDEDIR"
##
## Allow sudo-run commands to inherit the callers' ConsoleKit session
# Defaults env_keep += "XDG_SESSION_COOKIE"
##
## Uncomment to enable special input methods. Care should be taken as
## this may allow users to subvert the command being run via sudo.
# Defaults env_keep += "XMODIFIERS GTK_IM_MODULE QT_IM_MODULE QT_IM_SWITCHER"
##
## Uncomment to enable logging of a command's output, except for
## sudoreplay and reboot. Use sudoreplay to play back logged sessions.
# Defaults log_output
# Defaults!/usr/bin/sudoreplay !log_output
# Defaults!/usr/local/bin/sudoreplay !log_output
# Defaults!/sbin/reboot !log_output
Defaults logfile=/var/log/sudo.log
##
## Runas alias specification
##
##
## User privilege specification
##
root ALL=(ALL) ALL
## The password of OPSCENTER must be mandatory.
OPSCENTER ALL=(root) SOLARIS_DISCOVERY,SOLARIS_PROVISIONING
## Uncomment to allow members of group wheel to execute any command
# %wheel ALL=(ALL) ALL
## Same thing without a password
# %wheel ALL=(ALL) NOPASSWD: ALL
## Uncomment to allow members of group sudo to execute any command
# %sudo ALL=(ALL) ALL
## Uncomment to allow any user to run sudo if they know the password
## of the user they are running the command as (root by default).
# Defaults targetpw # Ask for the password of the target user
# ALL ALL=(ALL) ALL # WARNING: only use this together with 'Defaults targetpw'
## Read drop-in files from /etc/sudoers.d
## (the '#' here does not indicate a comment)
#includedir /etc/sudoers.d
Note:
The ALL Configuration is not supported in etc/sudoers.About SNMPv3
SNMP is the Simple Network Management Protocol and is part of Transmission Control Protocol⁄Internet Protocol (TCP⁄IP) protocol.
The protocol has existed for many years and has three versions: Version 1, 2 with subversions, and 3. Starting with 12.3.2, Oracle Enterprise Manager Ops Center uses SNMPv3 to discover assets and for new or updated credentials. Existing assets continue to use SNMPv1. For releases prior to 12.3.2, only SNMPv1 is supported.
Note:
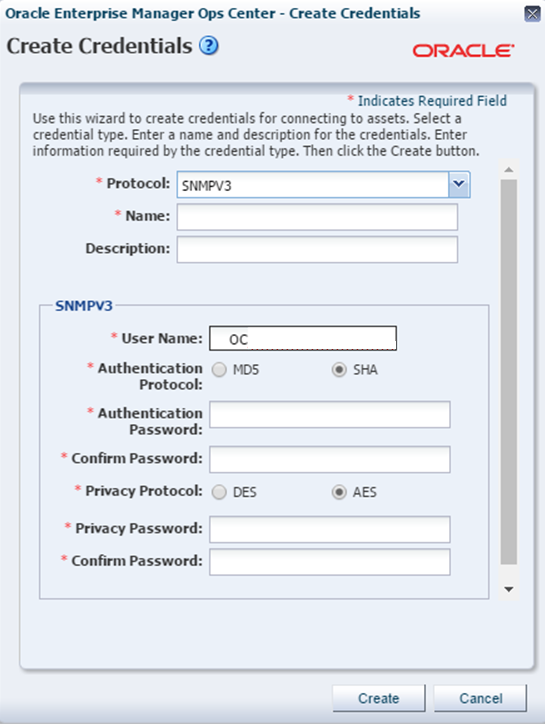
If your site updated from a previous release of Oracle Enterprise Manager Ops Center to Release 12.3.2, your site had the option to upgrade all assets that use SNMPv1 to SNMPv3.The difference between Version 3 and previous versions is Version 3 uses credentials instead of a public community string in its communication exchanges. The credentials includes username, a password for an authorization protocol, and a password for a privacy protocol.
The authorization protocol uses your password to create a one-way hash to verify that the transferred information is intact, acting as a digital signature. The available algorithms are MD5 and SHA. MD5 is a legacy algorithm that is not as strong as SHA (Standard Hash Algorithm), which is a 128-bit algorithm used as the US Federal Information Processing Standard.
The privacy protocol uses your password as the private key to encrypt the transferred information. The available protocols are DES and AES. DES (Data Encryption Standard) is not as strong as AES (Advanced Encryption Standard).
If you prefer to stop using SNMPv1 for existing assets and change to SNMPv3, you can migrate to SNMPv3 by using the Update Management Credentials action or use the Create Credentials profile and plan. Other actions, such Edit Credentials, also offer the ability to create SNMPv3 credentials.
Discovery Profiles
Overview of discovery profiles in Oracle Enterprise Manager Ops Center.
About Discovery Profiles
Describes the role of discovery profiles.
One of the ways of discovering assets is to select a discovery profile and then direct how the profile is used.
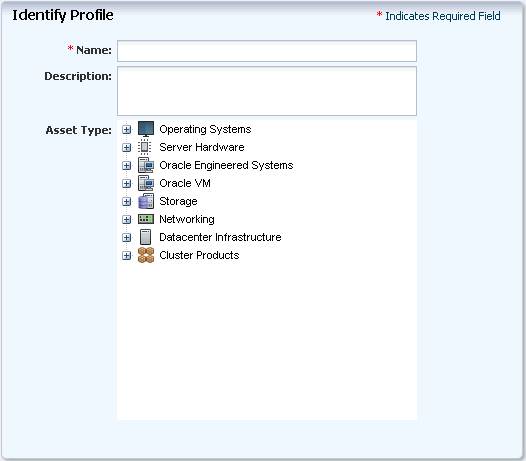
A discovery profile contains the attributes of assets. Oracle Enterprise Manager Ops Center uses the discovery profile to identify matching targets. You can make discovery profiles as specific or as generic as your site needs. Later, when you use the discovery profile, you can modify attributes in the profile.
All of the discovery profiles are available in the Plan Management section of the Assets pane, in the Profiles and Policies section. Expand Discovery to see the list of profiles.
Discovering Assets Using a Discovery Profile
Procedure for using a profile to discover assets in Oracle Enterprise Manager Ops Center.
The procedure uses a previously-created profile and directs Oracle Enterprise Manager Ops Center to apply it in a specified way.
Creating a Discovery Profile
You can create a profile and use it to discover assets that comply with the profile.
Editing a Discovery Profile
Procedure for changing a discovery profile in Oracle Enterprise Manager Ops Center.
To edit a discovery profile, perform the following steps:
- In the Navigation pane, click Plan Management.
- Under Profiles and Policies, click Discovery.
- Select the profile and click the Edit Profile icon.
- Edit any of the information in the discovery profile, then click Finish to save your changes.
Copying a Discovery Profile
Procedure for making a copy of an existing discovery profile in Oracle Enterprise Manager Ops Center
To copy a discovery profile, perform the following steps:
- In the Navigation pane, click Plan Management.
- Under Profiles and Policies, click Discovery.
- Select the profile and click the Copy Profile icon.
- Edit any of the information in the discovery profile, then click Finish to save the new discovery profile.
Deleting a Discovery Profile
Procedure for removing a discovery profile from Oracle Enterprise Manager Ops Center.
To delete a discovery profile, perform the following steps:
- In the Navigation pane, click Plan Management.
- Under Profiles and Policies, click Discovery.
- Select the profile and click the Delete Profile icon. The discovery profile is deleted.
Service Tags
Overview of service tags in Oracle Enterprise Manager Ops Center..
About Service Tags
Describes the use of service tags with the Find Assets Wizard in Oracle Enterprise Manager Ops Center.
Service tags are small XML files containing product information. Many Oracle systems come equipped with service tags. If you have hardware assets equipped with service tags, you can discover them using the Find Assets Wizard. This method lets you discover large numbers of assets quickly. The Find Assets Wizard searches known networks for service tags, then uses credentials that you specify to manage the discovered assets.
Starting with Oracle Enterprise Manager Ops Center 12c Release 2 (12.2.2.0.0), the Find Assets action is disabled by default.
Products without service tags cannot be discovered using this method. For example, ALOM systems do not have service tags.
Enabling Discovery by Service Tags
Procedure for using service tags to discover assets in Oracle Enterprise Manager Ops Center.
Starting with Oracle Enterprise Manager Ops Center 12c Release 2 (12.2.2.0.0), the Find Assets action is disabled because, in datacenters with many assets, discovery might expire before it can complete. If you prefer to discover assets using service tags, enable this feature:
Discovering Assets by Using Service Tags
Procedure for using service tags to discover assets in Oracle Enterprise Manager Ops Center.
To find assets, perform the following steps:
- In the Navigation pane, select All Assets.
- In the Actions pane, click Find Assets.
- Select Run Discovery Now.
- When the initial discovery is complete, select the assets in each category (hardware, operating systems, and engineered systems) that you want to manage and provide credentials for them, then click Finish.
Overview of Declaring Servers
Overview of discovering servers by declaring them in Oracle Enterprise Manager Ops Center.
A bare metal server is one that has no operating system or no service processor configuration or neither.
About Declaring Servers for OS Provisioning
Describes methods for bare metal provisioning of operating system.
Use the Declare Server option to prepare one or more bare metal systems for OS provisioning, even if the systems have no service processor.
To declare one server, use the Add Assets Wizards to specify information about the server. To declare multiple servers, create a discovery file as shown in Example 2-2.
Declaring One Server
Procedure for discovering a server in Oracle Enterprise Manager Ops Center.
- Select All Assets in the Navigation pane,
- Click Add Assets in the Actions pane.
- Select the Manually Declare a Server to be a Target of OS provisioning option in the wizard.
- Select the Declare a single server option.
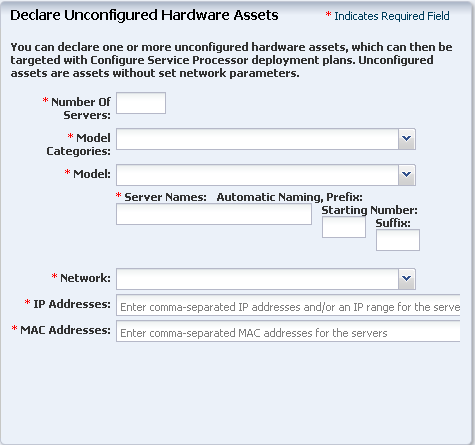
- Enter the server information, as show in “Information for Declaring a Server.”
Information for Declaring a Server
Lists the attributes required for discovering a server by declaring it.
-
Server Name: name of the server appearing on the UI.
-
IP Address: specify an IP address to route the discovery to the correct Proxy Controller. You do not need to use a server's actual IP address. You can use an IP address that is on the same subnet as that of the server to be discovered.
-
Model Categories: select the category in which the asset model appears.
-
Model: the model of the asset.
-
MAC Address and Port combination: used to connect to the server once it is available on the network. Click the Add or Edit icons to add or edit a MAC Address/Port combination, then select the combination.
Enter a logical port name for each network interface. One of these logical port names must be GB_0. Available logical port names are GB_0 through GB_11. You can also use mgmt as a management port. These logical port names will be mapped to network interfaces after the asset has been provisioned, according to the MAC addresses that you specify. If the server has only one network interface, use GB_0.
Enter the MAC addresses of the network interfaces in the server that you want to declare.
Declaring Multiple Servers
Procedure for discovering servers using a discovery file in Oracle Enterprise Manager Ops Center.
To declare multiple servers for OS Provisioning, perform the following steps:
Example 2-2 Example Discovery Profile
<?xml version='1.0' encoding='utf-8'?>
<servers>
<server name="T5440" model="Sun SPARC Enterprise T5440 Server"
guid="12345678"
proxyHostname="server"
ipAddress="10.0.0.0" >
<ethernetPort name="GB_0" mac="01:23:45:67:89:AB"/>
</server>
</servers>
About Declaring Servers for Service Processor Configuration
Describes the method for configuring a server’s service processor even if the server is not yet discovered.
Use the Declare Servers for Service Processor Configuration option to nominate one or more bare metal systems for service processor configuration.
The assets being declared do not need to be physically connected to the network at the time of the discovery, because the assets produced by an asset declaration are skeletal representations of the real assets. These assets can then be targeted with service processor configuration jobs. After the actual assets are connected to the network, provisioned and discovered, they are correlated with the declared version into complete assets.
Management Credentials
Overview of management credentials.
Oracle Enterprise Manager Ops Center stores the credentials that manage each asset. You can update, edit, and delete these credentials.
Upgrading Management Credentials From a Prior Version
Procedure for assigning new credentials to assets in Oracle Enterprise Manager Ops Center.
Assets that were discovered and managed in prior versions of Oracle Enterprise Manager Ops Center might not have management credentials associated with them. You can associate new or existing sets of credentials with these assets.
If a discovered asset is blacklisted, the same can be removed by updating the management credentials.
To upgrade management credentials, perform the following steps:
Updating Management Credentials
Procedure for changing the credentials used to get access to an asset in Oracle Enterprise Manager Ops Center.
You can change the set of management credentials used by an asset or group of assets.
To update management credentials, perform the following steps:
Creating Management Credentials
Procedure for creating credentials for accessing assets in Oracle Enterprise Manager Ops Center.
Create a set of management credentials to discover and manage new assets or to manage existing assets.
To create management credentials, perform the following steps:
- On the Navigation pane, under Administration, select Credentials.
- In the Actions pane, click Create Credentials.
- Click on the drop-down list to see the list of available protocols. Accept the default SSH protocol or select a different protocol. Depending on the type of protocol you select, the remaining fields change to collect the required information for the credentials. For specific examples, see Creating SSH Credentials or Creating SNMPV3 Credentials.
- Specify a name and description, such as the purpose of the credentials.
- Select or specify the required information for the type of credential, such as the username and password.
- Click Create to create the management credentials.
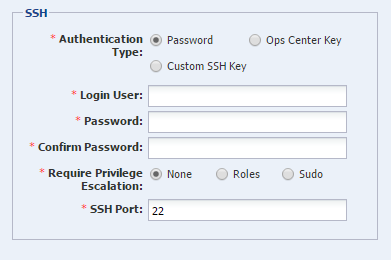
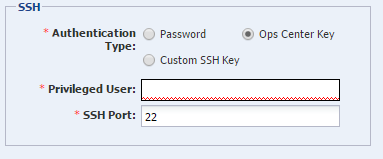
Creating SSH Credentials
Create a set of SSH credentials to discover and manage new assets or to manage existing assets.
The default protocol for managing assets is SSH. To create SSH credentials, perform the following steps:
Creating SNMPV3 Credentials
Procedure for creating credentials for accessing assets in Oracle Enterprise Manager Ops Center.
Create a set of management credentials to discover and manage new assets or to manage existing assets.
To create credentials that use the SNMPv3 protocol, perform the following steps:
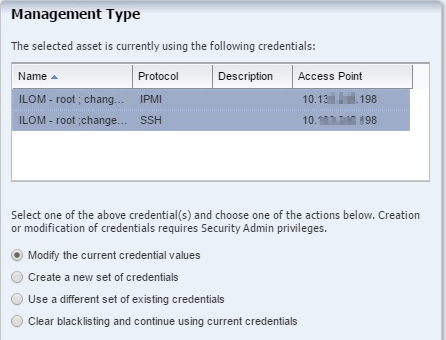
Editing Management Credentials
You can change an existing set of management credentials that you use to discover assets.
To edit management credentials, perform the following steps:
- On the Navigation pane, under Administration, then select Credentials.
- In the center pane, select a set of credentials.
- Click the Edit Credentials icon.
- You can change the description of the credentials and any characteristic of the existing credentials.
- Click Update to save the changes.
Copying Management Credentials
Procedure for making a copy of existing management credentials in Oracle Enterprise Manager Ops Center.
You can copy an existing set of management credentials to create a set.
To copy management credentials, perform the following steps:
- On the Navigation pane, under Administration, select Credentials.
- In the center pane, select a set of credentials and click the Copy Credentials icon.
- Edit the name, description, and the information required by the protocol, then click Copy to save the new set of credentials.
Deleting Management Credentials
Procedure for removing the credentials used to access an asset in Oracle Enterprise Manager Ops Center.
You can delete an existing set of management credentials if they are not in use by an asset. You can delete credentials that are used in discovery profiles but the discovery profiles must be edited to use new credentials. Agentless assets that are managed using the credentials must be given a new set.
To delete management credentials, perform the following steps:
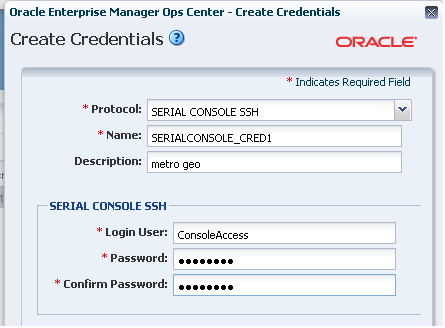
About Credentials for Access to the Serial Console or SSH Tunnel
Describes how Oracle Enterprise Manager Ops Center connects to a service processor and uses SSH.
To enable a connection to a service processor or virtual machine, define the user account that Oracle Enterprise Manager Ops Center uses to open an SSH tunnel on the Enterprise Controller or to create a serial connection.
Note:
If you do not specify this account, Oracle Enterprise Manager Ops Center creates an account each time it accesses a serial console and deletes the account when the connection is no longer needed. This activity might not conform to your site's security policy.
The following types of assets use SSH to connect to a serial console. Create an account for each type and define the same password for each account.
-
Proxy Controllers
-
Global zones that use agents and require access to the consoles of non-global zones
-
Control domains that use agents and require access to the consoles of logical domains
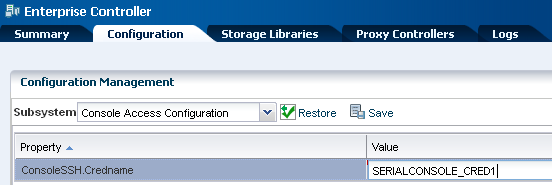
To create the account, define the ConsoleSSHCredname system property using the procedure in Defining the system property for console access and then define a user account for that property using either the procedure in Creating the account using Oracle Enterprise Manager Ops Center or the procedure in Creating the account using the useradd command.
Defining the System Property for Console Access
Procedure for configuring the serial console in Oracle Enterprise Manager Ops Center.
When the job is completed, define the account using the following procedure.
Creating the Account Using Oracle Enterprise Manager Ops Center
Procedure for creating a SSH account for the serial console in Oracle Enterprise Manager Ops Center.
You must have the Security Admin role to perform this procedure.
After you define the user account, the account is created automatically in /etc/passwd the first time a job for console access is run. However, if your site's security policy requires that the operating system account must be created outside of Oracle Enterprise Manager Ops Center's control or if you prefer to create the account manually, use the procedure described in Creating the account using the useradd command.
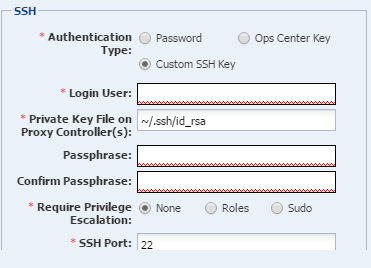
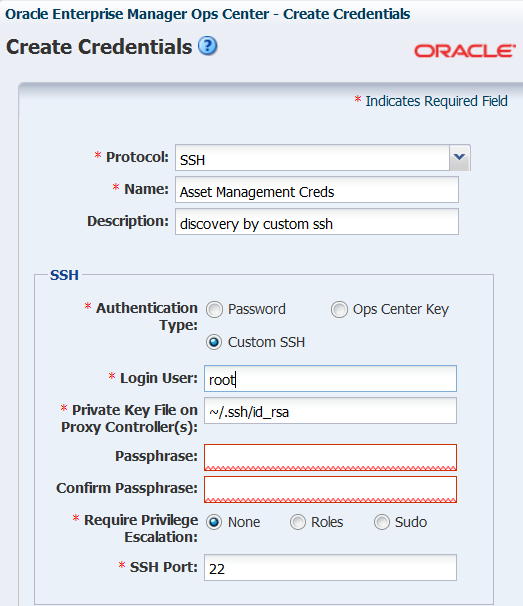
Using Custom SSH Keys for OS Discovery
Procedure for creating SSH credentials for discovering an operating system asset in Oracle Enterprise Manager Ops Center.
You can use SSH keys as an option when performing the OS discovery.
You must create SSH keys on each Proxy Controller that might access the target asset and also add the SSH public key to the ~/.ssh/authorized_keys location on the remote OS or use the hardware's web interface to upload the public keys.
For a nonprivileged user, enter the Privileged User role credentials in the Privileged Role and Role Password fields respectively.
Switching Between Agent Controllers or Agent and Agentless
Procedure for switching management mode from agentless to agent-managed asset and from agent-managed to agentless asset in Oracle Enterprise Manager Ops Center.
To discover and manage operating systems, you have the option of using SNMPV3 credentials to manage the asset. For more information on switching the management modes, see Oracle Enterprise Manager Ops Center Operations Reference
To switch management mode:
Note:
When switching from agentless to agent-managed asset, providing SSH and SNMPV3 credentials is mandatory.
Overview of Installing Agent Controllers Using the Command Line Interface
Overview of installing an Agent Controller using the Command Line Interface in Oracle Enterprise Manager Ops Center.
Topics
Use these procedures to install an Agent Controller and to register the target system. See Using Agent Management for Operating Systems for more information about Agent Controllers and Virtualization Agent Controllers.
Requirements for Installing an Agent Controller on Oracle Solaris 11
List of requirements for installing an agent on an asset running Oracle Solaris 11 in Oracle Enterprise Manager Ops Center.
-
The Oracle Solaris 11 Package Repository must be configured and its initial synchronization completed.
-
The version of Oracle Solaris 11 installed on the target system must be available in the Oracle Solaris 11 Package Repository.
-
The Agent Controller packages must already be in the Oracle Solaris 11 Package Repository.
Before You Begin to Install an Agent Controller
Requirements for installing an Agent Controller on an asset in Oracle Enterprise Manager Ops Center.
To use the agentadm command, you need the following information:
-
To configure your Agent Controller software using an administrative user account on the Enterprise Controller you need:
-
User name: the user account provides authentication that supports Agent Controller registration. Use the user name of this account as the argument for the
-uoption of the agentadm command. -
Password: use this password to populate the
/var/tmp/OC/mypasswdfile. Then use this file name as the argument for the-poption of the agentadm command.
-
-
The auto-reg-token registration token from the
/var/opt/sun/xvm/persistence/scn-proxy/connection.propertiesfile on the appropriate Proxy Controller – If you decide not to use user credentials to configure your Agent Controller software, use this token to populate the/var/tmp/OC/mytokenfile. Then use this file name as the argument for theagentadm -toption. -
IP address or host name of the Proxy Controller with which you will associate the Agent Controller – Use this IP address or host name as the argument for the
agentadm -xoption. Typically, you would associate the Agent Controller with the Proxy Controller that is connected to the same subnet as the target system. -
The IP address of the network interface that the Agent Controller will use for registration – Use this IP address as the argument for the
agentadm -aoption.
Some example agentadm commands in this procedure use the alternative administrative user name droot. In these examples, the droot user exists on the Enterprise Controller.
When you install an Agent Controller on a global zone, the installation installs, or upgrades to, Oracle Java Runtime Environment (JRE) 1.6.0_91. If a later version of JRE is installed, the installation does not downgrade.
Installing and Configuring an Agent Controller Manually Using User Credentials
Procedure that uses credentials to install an Agent Controller in Oracle Enterprise Manager Ops Center.
This procedure creates a file that holds the password of the administrative user for your Oracle Enterprise Manager Ops Center installation.
Special Discovery and Management Procedures
Describes specific requirements for discovery of certain types of assets.
Most assets can be discovered and managed using standard procedures. However, some types of assets must be discovered or managed using special procedures:
Topics
-
Oracle Engineered Systems: Discovery requires a custom configuration file that is prepared by Oracle service. See Oracle Enterprise Manager Ops Center Operations for Oracle SuperCluster Reference for more information.
-
Oracle Solaris 11: Discovery requires that the Enterprise Controller and Proxy Controller are installed on Oracle Solaris 11 and the Oracle Solaris 11 Update Library is configured.
-
Windows Systems: You must enable Windows Management Instrumentation (WMI) on Microsoft Windows systems before discovering them.
-
M-Series Servers: You must ensure that user privileges and the status of each dynamic system domain are correct before discovering a Sun SPARC Enterprise M-Series server.
-
SPARC M5–32, M6–32, M7 Series Servers: These servers have ILOM server processors. You must get access the server using an account with Ops Center Admin and Ops Center Security Admin roles.
Note:
SPARC M5–32, M6–32, M7 series servers are supported, but some features have limitations. For more information see the
Target Serverssection of the Certified Systems Matrix document. -
Oracle ZFS Storage Appliance: You can discover both the storage appliance and its service processor using the appropriate discovery profile.
-
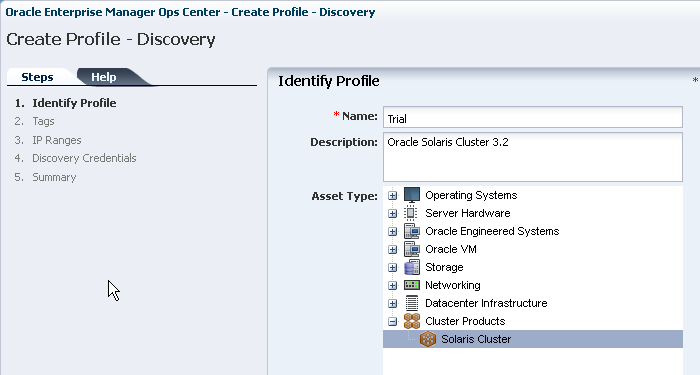
Oracle Solaris Cluster: You must discover and manage Oracle Solaris Clusters in a specific order so that Oracle Enterprise Manager Ops Center can manage the entire cluster.
Windows Systems
Describes requirements for discovery of Windows systems and WMI in Oracle Enterprise Manager Ops Center.
Microsoft Windows systems can be discovered and managed using normal discovery and management procedures. However, before the system can be discovered, the Windows Management Instrumentation (WMI) utility must be configured and have access through the Windows Firewall or Internet Connection Firewall.
Enabling WMI
Procedure for configuring Windows Management Interface (WMI) in Oracle Enterprise Manager Ops Center.
This procedure allows the Enterprise Controller or a Proxy Controller to connect to the target Windows system.
- Log in to the WMI on the target host.
- Click Administrative Tools, then click Computer Management.
- Expand Services and Applications.
- On WMI Control, right click Properties.
- Click the Security tab.
- Click the Security button.
- Select the Administrators group.
- Select the option to allow Remote Enable.
M-Series Servers
Overview of requirements for discovering an M-Series servers in Oracle Enterprise Manager Ops Center.
M-Series servers must be configured before they can be discovered and managed.
About Discovering a SPARC Enterprise M-Series Server
Describes discovery of the M3000, M4000, M5000, M8000, M9000, or Fujitsu M10 servers and their XSCF firmware.
To discover, manage, provision, and update a Sun SPARC Enterprise® M3000, M4000, M5000, M8000, M9000, or Fujitsu M10 server (SPARC Enterprise M-series servers), you monitor its XSCF service processor and its dynamic system domains.
The SPARC Enterprise M-series servers have a dedicated processor for system control that is independent of the system processor. A SPARC Enterprise M3000, M4000, and M5000 server has one service processor. The SPARC Enterprise M8000 and M9000 servers, each have two service processors; however, only one service processor is active at a time. The eXtended System Control Facility (XSCF) firmware runs on the dedicated service processor. The firmware manages hardware configuration, monitors cooling system (fan units), domain status, and error status, and can power on and power off peripheral devices.
The XSCF firmware can also create dynamic system domains. Each domain is a logical unit that can function as a system. An Oracle Solaris OS can operate in each domain.
Note:
Fujitsu M10 servers require XSCF Control Package (XCP) firmware version 2050 (XCP2050) to use the Automatic Service Requests (ASR) functions and to use service tags to enable server discovery with the Find Assets function.
Discovering a SPARC Enterprise M-Series Server
Procedure for discovering an M-Series Server in Oracle Enterprise Manager Ops Center.
To discover a Sun SPARC Enterprise® M3000, M4000, M5000, M7000, M8000, M9000, or Fujitsu M10 server, run an Add Assets Using Discovery Profile job for the XSCF service processor. The discovery job discovers the XSCF service processor and its dynamic system domains.
Perform the following tasks to discover this type of asset:
- In the XSCF service processor, create a user account with
platadmprivilege if one does not exist. - Ensure that user privileges and the status of each dynamic system domain are correct.
- Check the status of each dynamic system domain, using the
showdomainstatus -acommand. Oracle Enterprise Manager Ops Center can only discover domains that do not have a “-" status. - Log in to the XSCF shell from an XSCF-LAN port or from the serial port.
- Discover the system using the Add Assets Using a Discovery Profile procedure.
A Discovery job is launched. Dynamic system domains and the XSCF service processor are discovered at the same time.
When the job is complete, the XSCF service processor and the dynamic system domains appear in the Managed Assets tab. Additionally, the service processor and the domains appear under the M-Series Servers group in the Assets tree.
See Related Resources for Asset Management for more information.
Discovering an Oracle SPARC M5, M6, or M7 Server
Procedure for discovering an M-Series Server in Oracle Enterprise Manager Ops Center.
Because these servers have ILOM service processors, use the Add Assets action with the ILOM service processor discovery profile to discover the ILOM service processor and its dynamic system domains. To discover an M7 server, you must use the current version of the product software.
- Create a Discovery Profile choosing an ILOM Service Processor for the Asset Type.
- Select existing or create new SSH and IPMI credentials.
- Run an Add and manage various types of assets via discovery probes job.
- Choose the Discovery Profile for the server and include the correct Hostnames or IP addresses.
- After the discovery job completes successfully find the server in the Navigation pane under the M-Series Server tree.
Note:
An M-Series system is significantly larger than a typical server so discovery and refreshes of data can exceed the default expiration of 30 minutes. If the discovery job fails, increase the number of seconds for operations on the ILOM service processor by editing the /var/opt/sun/xvm/hal.properties file for the following property:
ilom.sdm.maximum.command.execution.time=1800
See Oracle Enterprise Manager Ops Center Discovering and Managing Oracle SPARC M5, M6, and M7 Servers Guide for a complete example.
About the Oracle ZFS Storage Appliance
Description of the Oracle ZFS Storage Appliance and methods for discovering it.
The Oracle ZFS Storage Appliance family of products provides rich and efficient data services for file and block storage formats. Each appliance has the Analytics feature for observing the condition and behavior of the appliance in real time and the ZFS Hybrid Storage Pool feature, which uses Flash-memory devices, high-capacity disks, and DRAM memory within a data hierarchy to provide solid-state response time with spinning disk capacity.
Note:
Starting in Release 12.3.1.0, Oracle Enterprise Manager Ops Center supports an active-active configuration. Previous releases support an active-passive configuration. In both cases, if a head fails, the other head takes control of all resources and provides the services associated with those resources.
The Oracle ZFS storage appliances are available in a cluster configuration, in which two storage controllers, or heads, use storage and network resources to provide services. In an active-active cluster, both heads are active. In an active-passive cluster, one head is active.
When working with an active-active configuration, Oracle recommends a single storage pool on each active head. Although multiple pools on one head is supported, the result is poor performance, suboptimal allocation of resources, artificial partitioning of storage, and additional administrative complexity. Configuring multiple pools on the same host is only recommended when drastically different redundancy or performance characteristics are desired, for example, a mirrored pool and a RAID-Z pool. See the documentation for the Oracle ZFS storage appliance for more information.
Before you discover the storage appliance, configure the iSCSI targets on the storage appliance. In an active-passive cluster, one iSCSI target group is sufficient, although multiple target groups are supported. In an active-active configuration, you must configure at least two iSCSI target groups: one target group for the storage served from the first head and one target group for the storage served by the second head.
To discover a storage appliance In an active-passive cluster, discover the active head and its iSCSI and/or NFS storage, and then discover the passive head, which has no storage associated with it because it will take over the existing storage. The procedure is described in Discover an Oracle ZFS Storage Appliance and Configure Storage Libraries.
To discover a storage appliance in an active-active cluster, discover one head with its iSCSI and/or NFS storage, and then run a second job to discover the second head with its corresponding iSCSI and/or NFS storage. This will create dynamic storage libraries backed by each storage pool.
Because the storage appliance contains a service processor, it is possible to discover the appliance but not the service processor or to discover both. It is sufficient to discover only the storage appliance by using the Add Assets action with a discovery profile for storage appliances as described in Discover an Oracle ZFS Storage Appliance and Configure Storage Libraries. You also have the following alternatives.
-
Use Add Assets and a discovery profile to discover the storage appliance first and then use a service processor discovery profile to discover its service processor. When you discover the storage appliance, Oracle Enterprise Manager Ops Center displays the device in the Storage section of the Assets tree. When you discover the service processor, its information is mapped to the discovered appliance.
-
Use Find Assets. Each storage appliance is discovered as two assets: a service processor and a storage appliance. Select both the appliance and its service processor and enter the user credentials. Oracle Enterprise Manager Ops Center displays the asset in the Storage section.
Note:
Oracle Enterprise Manager Ops Center can use either the Storage Connect driver or the RESTful/SSH Ops Center driver to communicate with the storage appliance. Starting from Release 12.3.1.0, the RESTful/SSH Ops Center driver is the recommended option to communicate with the storage appliance. The procedure to specify a driver provided in the product software is described in Discover an Oracle ZFS Storage Appliance and Configure Storage Libraries. To change drivers after discovery, use the Switch Driver action.
About Oracle Solaris Cluster
Description of requirements for discovering Oracle Solaris Clusters.
Discovering and managing an Oracle Solaris Cluster has some specific requirements. The discovery and management must be performed in the correct order.
Note:
Do not configure a new zone cluster or add a new global node during the discovery and management process.
Discovering an Oracle Solaris Cluster
Procedure for discovering an M-Series Server in Oracle Enterprise Manager Ops Center.
Launching Oracle Solaris Cluster 4.2
Procedure for starting Oracle Solaris Cluster in Oracle Enterprise Manager Ops Center.
Starting in this version, you can launch the Oracle Solaris Cluster Manager:
- In the Navigation pane, select Solaris Cluster and then select a cluster.
- In the Actions pane, click Launch Web Console.
- Log into the Oracle Solaris Cluster Manager.
Preparing to Discover ALOM Assets
Procedure to enable discovery of ALOM service processors in Oracle Enterprise Manager Ops Center.
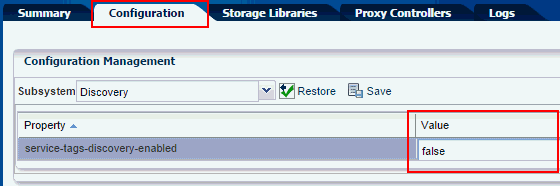
Starting in Release 12.3.1, the discovery of assets with the ALOM service processor is disabled by default. If your site has an asset with this type of service processor, enable discovery using this procedure:
- In the Navigation pane, select Administration.
- Select the Enterprise Controller.
- Click the Configuration tab.
- In the Subsystem drop-down list, click Discovery.
- Change the value of
ssh.alom.timeoutfrom 0 to the number of seconds to allow for discovery.
Managing Assets
Overview of actions for assets that have been discovered in Oracle Enterprise Manager Ops Center.
After discovery, the assets are now managed assets. Through their life cycle, you might need to make changes to their configuration or position. When an asset is moved, migrated, or deleted, the Asset tree might still display the original position of the asset for several minutes. To refresh the display of the Asset hierarchy manually, press the Ctrl key while clicking the Refresh button
Topics
Editing Asset Attributes
Procedure for changing the attributes of a specific asset in Oracle Enterprise Manager Ops Center.
All assets have a description that can be edited.
The description field can be used for descriptive information about a system.
To edit asset attributes, perform the following steps:
- On the Navigation pane, under Assets, select an asset.
- In the Actions pane, click Edit Asset.
- Edit the name, description, and tags, then click Save.
About the Number of Assets
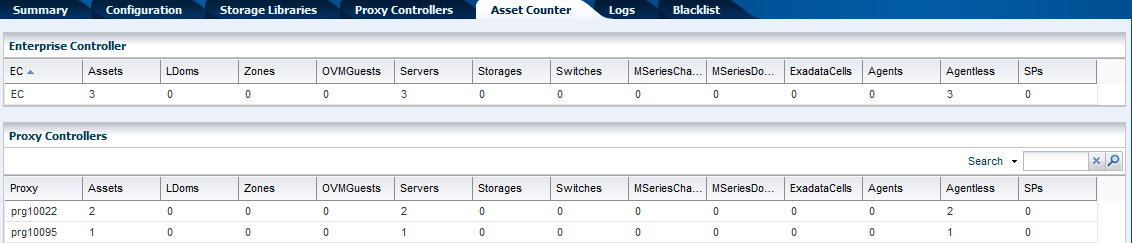
Description of how assets are counted in Oracle Enterprise Manager Ops Center.
The number of assets managed by the Enterprise Controller and by each of its Proxy Controllers is reported on the Asset Counter tab. The reported numbers are not a physical inventory of assets datacenter. These numbers represent the number of access points in the assets.
The Enterprise Controller can manage 3000 assets and each Proxy Controller can manage 500 assets. More assets can be managed but performance is affected. At 90% of capacity (2700 access points), a Warning alert is issued as an incident on the operating system of the Enterprise Controller. For a Proxy Controller, the warning incident is set at 450 access points. At 100% of capacity, a Critical alert is issued.
Viewing the Number of Assets
Procedure for displaying the number of each type of asset in Oracle Enterprise Manager Ops Center.
You can refresh the display by selecting Run Asset Counter Job in the Action pane.
Viewing and Removing Access Points
Procedure for displaying how an asset is included in Oracle Enterprise Manager Ops Center.
An asset's access points show how Oracle Enterprise Manager Ops Center connects to the asset.
The following are possible access points:
-
The discovery credentials used to discover the asset.
-
The discovery credentials used to discover a related asset. For example, an access point for a service processor is the discovery credentials of its operating system.
-
Agent Controller installed on the asset.
-
A virtual asset's virtualization host.
To view access points, select an asset and click the Configuration tab.
To delete an access point, perform the following steps:
- On the Navigation pane, under Assets, select an asset and click the Configuration tab.
- Select one or more access points, then click Delete Access Point.
Deleting Assets
Procedure for removing assets from Oracle Enterprise Manager Ops Center.
The Delete Asset option uninstalls Agent Controller software if it is present, removing the asset from Oracle Enterprise Manager Ops Center. All data for the asset is removed. You delete assets to stop managing them with Oracle Enterprise Manager Ops Center.
The operating systems that support the Enterprise Controller and Proxy Controllers cannot be deleted or removed.
Note:
Deleting a global zone also deletes its non-global zones. However, if a global zone is managed with an Agent Controller, its non-global zones continue to be managed agentlessly even if their Agent Controllers are removed.
Asset Groups
Overview of asset groups in Oracle Enterprise Manager Ops Center.
Assets are automatically placed into system groups based on asset type. You can also create your own groups and add assets to them, either by manually adding assets or by creating rules that add assets automatically based on asset characteristics.
About Types of Groups
Describes the default asset groups and custom asset groups in Oracle Enterprise Manager Ops Center.
Assets are members of two types of groups: System groups and User-defined groups. System groups are automatically generated for each category of asset. User-defined groups can contain any assets. You can configure rules to add any asset to the user-defined groups that meets the rule criteria.
Within system groups, a subgroup is created for each type of asset that Oracle Enterprise Manager Ops Center manages. You can use System Groups to locate and view assets of a specific type. You can also act on System Groups, such as changing monitoring thresholds and updating management credentials. You can view system groups by selecting them from the drop-down list at the top of the Assets section in the Navigation pane.
User-defined groups can contain any type of asset and can be organized by any criteria. You can configure rules for user-defined groups that automatically add assets with specific characteristics to the group.
You can take any action on a group that is applicable to the assets in the group. For example, you can update Automated Service Request (ASR) contacts for all assets in a group, or target a group containing operating systems with an OS update job.
System Groups
List of default asset groups in Oracle Enterprise Manager Ops Center.
Oracle Enterprise Manager Ops Center creates these system groups:
-
All Assets: contains all discovered and managed assets. This is the default view of the assets section.
-
Engineered Systems: contains all Oracle Engineered Systems.
-
Operating Systems: contains all operating systems with subgroups for each type of operating system such as Oracle Solaris OS, Oracle Linux, and SUSE Linux. The subgroups are further organized by version, such as Oracle Solaris 9 and Oracle Solaris 10 software.
-
Servers: contains all hardware that can receive OS provisioning.
-
Chassis: contains all hardware that can receive firmware updates but not OS provisioning.
-
Network Switches: contains all network switches.
-
Racks: contains all racks.
-
Server Pools: contains all server pools.
-
Storage: contains all storage systems.
-
Solaris Clusters: contains all Oracle Solaris Clusters.
User-Defined Groups
List of properties for a custom asset group in Oracle Enterprise Manager Ops Center.
You can specify the following characteristics for a user-defined group:
-
Group Name
-
Description
-
Group Location
-
Group Rules: group rules add any assets to the group that match the attributes and rules.
-
Subgroups: groups can be organized hierarchically.
About Asset Tags
Description of using labels to identify or sort assets.
A tag is a set of information attached to an asset. Each tag consists of a tag name, which is drawn from a list of values appropriate for each asset, and a tag value, which can be any text string. For example, an asset could have a tag with a tag name of oracle.cloud.resource.creation.time and a value of 12 June.
You can use tags to categorize assets and to simplify later searches. You can use tags to associate information with assets, and to create groups of assets based on their tags or tag values. To add assets to a group using tags, either discover them using a profile that includes the tag or, after discovery, create a new group or edit an existing group to require membership based on a rule that uses the tag.
Adding Tags
Procedure for adding tags to an asset in Oracle Enterprise Manager Ops Center.
You can create tags to assets during or after discovery. To add tags to one or more assets after discovery, perform the following steps:
Viewing Tags
Procedure displaying an asset’s tags in Oracle Enterprise Manager Ops Center.
Tags are displayed in the Dashboard tab for managed assets. Select an asset, then use the mouse to hover on the Tags icon in the center pane to display the tags.
About Group Data
Procedure for displaying information about a group of assets in Oracle Enterprise Manager Ops Center.
Each group can list all the assets in the group and can display data about their assets. Chassis and hardware groups display power usage information, and operating system groups display CPU, network, memory, and system load information.
You can select a group to see a dashboard page with information about the group, including:
-
A group summary that shows the group's name, description, tags, location, and number of members.
-
A membership graph showing the group's assets, any child groups, and any parent groups.
-
A status summary showing the problems of the assets within the group.
-
An asset summary showing basic data about the assets within the group.
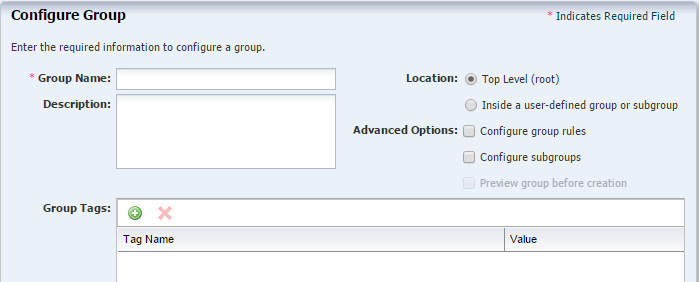
Creating a Group
Procedure for creating an asset group in Oracle Enterprise Manager Ops Center.
You can organize your assets into groups to aid in management and inventory. For a rule-based group, membership is determined by whether an asset conforms to the rule. For example, if you select Name as an Attribute, Contains as a condition, and Pod3 as a value, any asset with Pod3 in its name is added to the group.
-
In the Navigation pane, in the Assets section, select User Defined Groups from the drop-down list.
-
Click Create Group in the Actions pane.
-
In Group Name, specify the name to be displayed in the User-Defined Groups of the Navigation pane.
-
In Description:, describe the purpose of the group. This description is displayed in the group's dashboard.
-
In Group Location, specify whether the position of this group in the Asset tree. You can create a group at the top level (root), the default, or as a child of an existing user-defined group.
-
The Configure group rules option creates a rules-based group, that is, the membership of the group is determined by how an asset conforms to the rule. When you select this option, you will create one or more rules for the group. This selection also enables the Preview group before creation option.
- The
Configure subgroups option allows you to specify an existing user-defined group as a child of this group.
-
Keep the Preview Group Before Creation option if you are configuring group rules or subgroups to test your rules or selections.
-
You have the option to add tags to the new group. Click Next.
-
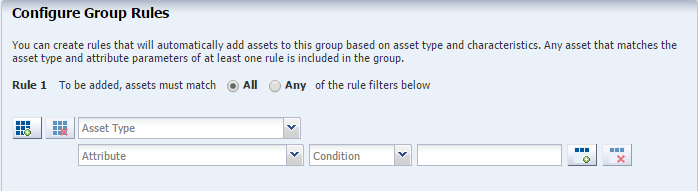
If you are creating a rules-based group, the next step defines one or more rules. The first rule, Rule 1, is required and specifies whether an asset must match all of the rules or at least one of the rules to be included in the group.
-
To specify the second rule, select the Asset Type from the drop-down list.
-
Depending on the type of asset, the attributes that can control membership change. Select an attribute from the drop-down list. See About Asset Attributes for a list of the asset attributes that can be used in group rules.
-
In the Condition dropdown list, select how the attribute is used in the rule. The options are:
-
Contains
-
Does not contain
-
Ends with
-
Equal
-
Matches
-
Not equal
-
Starts with
-
-
In the remaining field, enter the value that completes rule. For example, if the attribute is Name, the value is a string.
-
To add a third rule, click the Add icon and repeat the procedure. When you are finished adding rules, click Next.
-
If you are adding subgroups, drag and drop one or more groups from the available groups list to the selected groups list. When you are finished, click Next.
-
If you chose to preview the group, view the assets and subgroups that will be added to the group. If necessary, go back and change the group rules or the list of subgroups.
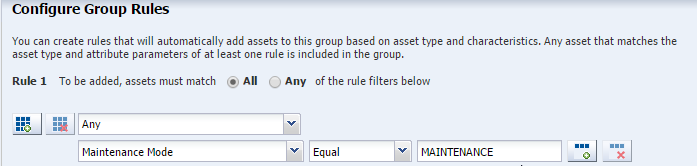
Creating a Group for Assets in Maintenance Mode
Procedure for creating a user-defined group containing assets in maintenance mode in Oracle Enterprise Manager Ops Center.
You can organize assets in Maintenance Mode into one rule-based group.
-
In the Navigation pane, in the Assets selection, select User Defined Groups from the drop-down list.
-
In the Actions pane, click Create Group.
-
For Group Name, enter a name for this custom group. This name is displayed in the User-Defined Groups of the Navigation pane
-
In the Description field, describe the purpose of the group, in this case, Maintenance. This description is displayed on the group’s Dashboard.
-
In the Location field, select Top Level (root).
-
In Advanced Options, select Configure group rules, then click Next.
-
Create the rule that constrains membership of the group to assets that are in Maintenance mode.
-
For Rule 1, click All .
-
For Asset Type, select Any.
-
For the Attribute, Maintenance Mode.
-
For the condition, select Equal.
-
For the value, enter MAINTENANCE . Uppercase is required.
-
-
Click Next to skip adding subgroups.
-
In the preview, verify that the assets are listed as you intend.
-
Click Finish to create the group.
Editing a Group
Procedure for editing the characteristics of an asset group in Oracle Enterprise Manager Ops Center.
You can change the attributes of an existing group, including its name, description, rules, subgroups, and parent group. If you change or remove the rules of an existing group, assets added by those rules are removed if they do not match the new rules. However, assets that were added manually can only be removed manually.
To edit a group, perform the following steps:
See Expression Query Language for a list of the asset attributes that can be used in group rules.
Adding Assets to a Group
Procedure for adding assets to a user-defined group in Oracle Enterprise Manager Ops Center.
You can place assets into user-defined groups to organize them. When an asset is added to a group, it continues to be displayed in the All Assets section. Assets can be added to any number of groups.
- In either the Managed Assets tab of the center pane or the Assets section of the Navigation pane, select the assets you want to add.
- Click Add Asset to Group.
- Select the destination group.
- Click Add Assets to Group.
Removing Assets from a Group
Procedure for removing an asset from a group in Oracle Enterprise Manager Ops Center.
When you remove an asset from a user-defined group, the asset remains in any other group of which it is a member.
If an asset was added to a group by the group's rules, it cannot be removed.
- On the Navigation pane, under Assets, select All User Defined Groups.
- Select the group that contains the assets.
- Select one or more assets.
- Click Remove Asset from Group
Moving Assets to a Group
Procedure for moving an asset from one group to another group in Oracle Enterprise Manager Ops Center.
When you move assets to a new user-defined group, the assets are removed from the current group and added to the new group.
If the current group has rules that match the asset you want to move, the asset remains in the original group and the new group.
To move assets to a new group, perform the following steps:
- On the Navigation pane, under Assets, select All User Defined Groups.
- Select the group that currently contains the assets.
- Select one or more assets and click Move Asset to Group.
- Select the destination group and click Move Assets to Group/Subgroup.
Moving a Group
Procedure for moving a group of assets in Oracle Enterprise Manager Ops Center.
You can move a user-defined group within the hierarchy of groups, making it a child of a different user-defined group or placing it at the top level.
- On the Navigation pane, under Assets, select All User Defined Groups.
- Select the group you want to move.
- Click Move Group.
- Select the new parent group.
- Click Move Group.
Deleting a Group
Procedure for removing an asset group from Oracle Enterprise Manager Ops Center.
Deleting a user-defined group removes the group and all of its subgroups from the user-defined group hierarchy without removing any of the assets.
To delete a group, select a group and click Delete Group in the Actions pane.
Related Resources for Asset Management
List of Oracle Enterprise Manager Ops Center documents with additional information.
-
To enable the Find Assets action, see Enabling Discovery by Service Tags.
-
See Management Credentials for information about credentials for discovering hardware assets.
-
See Oracle Enterprise Manager Operations Reference for a comparison of agent-managed assets and agentless-managed assets.
-
See Configure Monitoring Rules and Policiesfor information about how Oracle Enterprise Manager Ops Center generates alerts and incidents.
-
See Operations for Oracle SuperCluster Reference for more information about discovering the Oracle SuperCluster T4-4, T5-8, and M6-32 systems.
-
SPARC M5–32, M6–32, M7 series servers are supported, but some features have limitations. For more information see the
Target Serverssection of the Certified Systems Matrix document.See Oracle Enterprise Manager Ops Center Discovering and Managing Oracle SPARC M5, M6, and M7 Servers Guide for a complete example of discovery.
-
For end-to-end examples of discovering assets, see the workflows in the Deploy How To library at
http://docs.oracle.com/cd/E59957_01/nav/deploy.htm. In particular, see Discover an Oracle ZFS Storage Appliance and Configure Storage Libraries for an example of discovery. The workflows identify the how to documents for discovering and managing assets. -
For information about SPARC servers, see SPARC Systems at
http://www.oracle.com/technetwork/documentation/oracle-sparc-ent-servers-189996.html. -
See Systems Management and Diagnostics at
http://www.oracle.com/technetwork/documentation/sys-mgmt-networking-190072.htmlfor information about ILOM configurations.