1 Session Monitor Security Overview
This chapter provides an overview of Oracle Communications Session Monitor security.
Basic Security Considerations
The following principles are fundamental to using any application securely:
-
Keep software up to date. This includes the latest product release and any patches that apply to it.
-
Limit privileges as much as possible. Users should be given only the access necessary to perform their work. User privileges should be reviewed periodically to determine relevance to current work requirements.
-
Monitor system activity. Establish who should access which system components, and how often, and monitor those components.
-
Install software securely. For example, use firewalls, secure protocols using TLS (SSL), and secure passwords. See "Performing a Secure Session Monitor Installation".
-
Learn about and use the Session Monitor security features. See "Implementing Session Monitor Security".
-
Use secure development practices. For example, take advantage of existing database security functionality instead of creating your own application security. See "Security Considerations for Developers".
-
Keep up to date on security information. Oracle regularly issues security-related patch updates and security alerts. You must install all security patches as soon as possible. See the "Critical Patch Updates and Security Alerts" Web site:
http://www.oracle.com/technetwork/topics/security/alerts-086861.html
Understanding the Session Monitor Environment
When planning your Session Monitor implementation, consider the following:
-
Which resources need to be protected?
-
You must protect customer data.
-
You must protect internal data, such as proprietary source code.
-
You must protect system components from being disabled by external attacks or intentional system overloads.
-
-
Who are you protecting data from?
For example, you need to protect your subscribers' data from other subscribers, but someone in your organization might need to access that data to manage it. You can analyze your workflows to determine who needs access to the data; for example, it is possible that a system administrator can manage your system components without needing to access the system data.
-
What will happen if protections on strategic resources fail?
In some cases, a fault in your security scheme is nothing more than an inconvenience. In other cases, a fault might cause great damage to you or your customers. Understanding the security ramifications of each resource will help you protect it properly.
Overview of Session Monitor Security
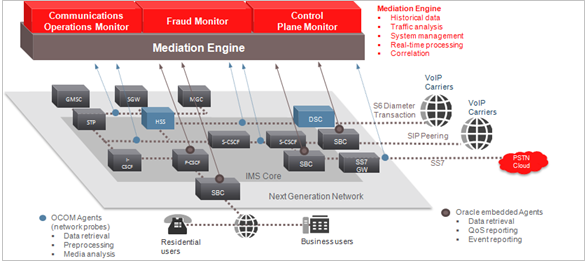
Figure 1-1 shows all the various components that comprise a Session Monitor system, including the components it connects to. Each installed or integrated component requires special steps and configurations to ensure system security.
Figure 1-1 Session Monitor System Components
Description of ''Figure 1-1 Session Monitor System Components''
Recommended Deployment Configurations
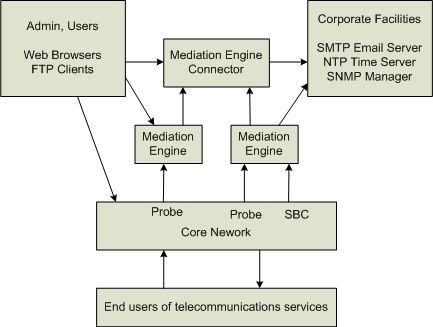
Figure 1-2 shows a typical Session Monitor system deployment.
Figure 1-2 Typical Session Monitor System
Description of ''Figure 1-2 Typical Session Monitor System''
Operating System Security
By default, shell access is disabled. To authorize Oracle Support access to your Session Monitor servers, you must provide direct shell access using Secure Shell (SSH). Shared desktop access is not direct shell access.
Oracle Support provides you the SSH credentials for authentication and authorization. You configure the credentials on the Remote Access page in Platform Setup Application (PSA). You can modify the credentials or disable shell access at anytime in PSA.
Oracle Support connects to your Session Monitor server using a VPN connection. Ensure that a VPN connection is created and tested, in the event that Oracle Support needs to use the VPN connection for an urgent case.
Network Security
Session Monitor uses the following protocols to communicate with various components on specific ports:
UDP:
-
Port 68: Used by the DHCP client.
-
Port 123: Used by the NTP client.
-
(Optional) Port 161: Used by the SNMP agent.
-
(Optional) Port 162 outbound: Used for SNMP traps.
-
(Optional) Port 5090: Used for Voice Quality from SIP phones on Mediation Engines.
TCP:
-
TCP port range 1024-65536: Used for connection from the Mediation Engines to the probes.
-
TCP port 443: Used for HTTPS connection from the Aggregation Engines to the Mediation Engines.
-
TCP port range 1024-65536: Used for connection from the Aggregation Engines to the Mediation Engines.
-
TCP port 4740: Used for IPFix over TLS.
-
(Optional) TCP port 4739: Used for IPFix from Oracle Communications Session Border Controller on Mediation Engines.
-
(Optional) TCP port 21: Used by the FTP and FTPS servers.
Probes:
Passively receives all telephony-related traffic.
Protocols that are marked optional are disabled by default. For information about how to enable these protocols, see Operations Monitor User's Guide.
Restrict access to Session Monitor machines by closing the unused ports. Session Monitor machines are typically connected to several networks; therefore, restrictions may vary for each machine.
Ensure that Session Monitor machines are not accessible from the Internet or have access to the Internet.
Connecting Oracle Communications Session Border Controllers to Mediation Engines
Connections from Oracle Communications Session Border Controllers to the Mediation Engine machines are encrypted. These encrypted (secure) connections use TLS on port 4740. The secure connections between the Mediation Engines and the session border controllers are established using SSL Certificates.
For a stand-alone system, you can register the certificates in Platform Setup Application on the Server Certificate page by downloading the Session Monitor certificate to the session border controller and uploading the session border controller certificate to the Session Monitor machine on the Trusted Certificate page.
If you manage certificates within a Public Key Infrastructure (PKI), you can download the Session Monitor certificates and have them signed by your Certificate Authority (CA). When you have the trusted CA certificate, upload the CA certificate to each Session Monitor machine.
Registering Certificates on the Session Border Controller
To register the certificates on the Oracle Communications Session Border Controller, go to the My Oracle Support Web site and follow the instructions in the Oracle Note at https://support.oracle.com/epmos/faces/DocContentDisplay?id=1679579.1 to do the following:
-
Configure the connection to Session Monitor
-
Create a certificate for the session border controller.
-
Register the certificate of Session Monitor, which can be downloaded from Platform Setup Application on the Server Certificate page. Alternatively, you can register the CA used to sign it.
-
Enable TLS
Registering Certificates in Platform Setup Application
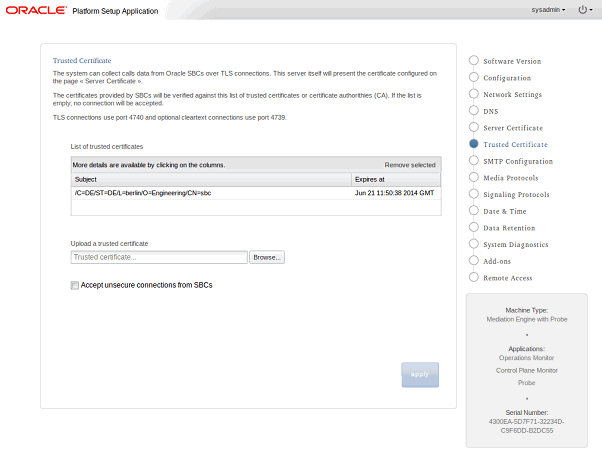
To register the certificates in Platform Setup Application, on the Trusted Certificate page in the Upload a trusted certificate section, upload the certificates of the session border controllers. The certificates will then appear under List of trusted certificates section (see Figure 1-3).
Alternatively, you can upload the CA that is used to sign session border controller's certificates. The certificate format is X.509 / PEM (X.509 extensions are not supported). Only the validity of the signatures are verified.
Unencrypted connections are not allowed by default, unless the system has been upgraded from an earlier release that did not support encrypted connections.
To use unencrypted connections (for example, in a testing environment), select Accept unsecure connections from SBCs; then disable the TLS option in the session border controller. The unencrypted connections use port 4739.
Using unencrypted connections are not recommended in production environments.
Email Security
Session Monitor uses email to send notifications and alerts. To send emails, Session Monitor needs access to an SMTP server. You configure the SMTP server details in Platform Setup Application on the SMTP Configuration page. Session Monitor supports TLS connections to the SMTP server.
If the SMTP server requires authentication, you will need to create an email account for Session Monitor. Ensure that the email account has only those privileges necessary for sending notification emails.