31 Configuring Oracle OPSS Keystore Service
This chapter describes how to configure the Oracle OPSS Keystore Service for use with WebLogic Server 12.1.3.
Chapter 30, "Configuring Keystores" describes how to configure identity and trust for WebLogic Server with the default JKS keystore type.
As described in "Managing Keys and Certificates with the Keystore Service" in Securing Applications with Oracle Platform Security Services, the OPSS Keystore Service provides an alternate mechanism to manage keys and certificates for message security. The OPSS Keystore Service makes using certificates and keys easier by providing central management and storage of keys and certificates for all servers in a domain. You use the OPSS Keystore Service to create and maintain keystores of type KSS.
This chapter includes the following sections:
-
Configuring the OPSS Keystore Service for Demo Identity and Trust: Main Steps
-
Configuring the OPSS Keystore Service for Custom Identity and Trust: Main Steps
This section assumes that you are familiar with a basic overview of the OPSS Keystore Service, as described in "Managing Keys and Certificates with the Keystore Service".
Prerequisites for Using the OPSS Keystore Service
You can use the OPSS Keystore Service with WebLogic Server only if you have installed the Oracle JRF template on the WebLogic Server system as described in Domain Template Reference and used this template to create the domain.
The OPSS Keystore Service is available only with the JRF template and is not available with the default WebLogic Server configuration.
Where is the OPSS Keystore Service Documented?
The OPSS Keystore Service is documented in "Managing Keys and Certificates with the Keystore Service" in Securing Applications with Oracle Platform Security Services. In particular, "Managing Keys and Certificates with the Keystore Service" describes how you create the KSS keystore, how to manage it, and what tools and commands are available.
This section briefly summarizes the steps you follow to configure the OPSS Keystore Service, but "Managing Keys and Certificates with the Keystore Service" in Securing Applications with Oracle Platform Security Services is the definitive source.
Configuring the OPSS Keystore Service for Demo Identity and Trust: Main Steps
You can perform the OPSS Keystore Service operations using either Fusion Middleware Control or the Keystore Service commands with WLST. This section demonstrates the Fusion Middleware Control steps, but "Managing Keys and Certificates with the Keystore Service" describes both options.
The KSS demo identity and demo trust keystores are preconfigured when you create a domain, and no additional configuration of these keystores is required.
Perform the following steps to configure an OPSS Keystore Service for demo identity and trust:
-
From the WebLogic Server Administration Console, navigate to the Domain -> Security -> Advanced page, and verify that the "Use KSS For Demo" check box is enabled.
-
Configure the WebLogic Server instance to use Demo Identity and Demo Trust, as described in Configure keystores.
-
Configure SSL for the WebLogic Server instance, as described in Set Up SSL.
Remember that the WebLogic Server DefaultHostnameVerifier has been modified to accept the non-standard
DemoCertFor_<WLS Domain Name>hostname format. Other hostname verifiers may not support this format. -
Restart WebLogic Server.
Configuring the OPSS Keystore Service for Custom Identity and Trust: Main Steps
You must configure the OPSS Keystore Service before you can use it for custom identity and trust with WebLogic Server.
You can perform the OPSS Keystore Service operations using either Fusion Middleware Control or the Keystore Service commands with WLST. This section demonstrates the Fusion Middleware Control steps, but "Managing Keys and Certificates with the Keystore Service" describes both options.
Perform the following steps to configure an OPSS Keystore Service for custom identity and trust:
-
Launch Fusion Middleware Control.
-
From the WebLogic Domain menu, select Security then Keystore.
-
Create a keystore in the
systemstripe. (See "Creating a Keystore with Fusion Middleware Control" for more information.)-
Select the
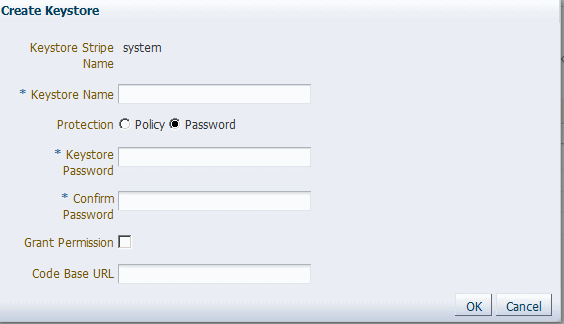
systemstripe and click Create Keystore.The Create Keystore page is shown in Figure 31-1.
-
Name this keystore.
-
Set the protection type to Password.
-
Set the password.
-
Uncheck the Grant Permission check box.
-
Do not specify a code base URL.
-
-
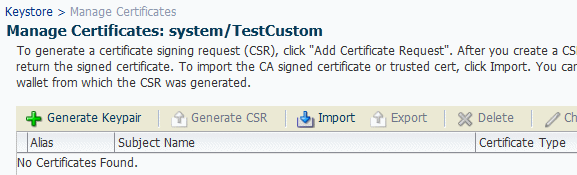
Select the keystore you just created and click Manage.
Enter the password.
The Manage Certificates screen shown in Figure 31-2 appears.
-
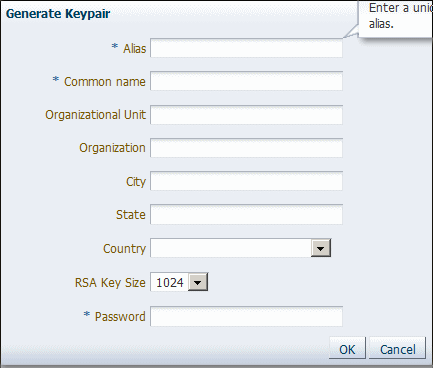
Click Generate Keypair to generate a private/public key pair.
The Generate Keypair screen is shown in Figure 31-3.
-
Specify the alias for the key pair.
-
Specify site-specific information as appropriate.
-
You can accept the default RSA key size if appropriate for your environment. Oracle requires a key length of 1024 bits or larger.
-
Specify the password.
-
Click OK.
-
-
You have the option to use this KSS Demo CA-signed key pair as-is, or to obtain a signed certificate from a reputable vendor such as Entrust, Verisign, and so forth.
To obtain the signed certificate from a reputable vendor, select the alias for the key pair and click Generate CSR. After you create a CSR, send it to your CA, which will authenticate the certificate request and create a digital certificate based on the request.
See "Importing a Certificate or Trusted Certificate with Fusion Middleware Control" in Securing Applications with Oracle Platform Security Services for instructions on how to import the CA-signed certificate.
-
If you do not use the preconfigured OPSS Keystore Service trust store
kss://system/trust, you must create your own.Note:
Oracle recommends you use the preconfigured OPSS Keystore Service trust store.To create your own trust store, create another OPSS Keystore Service keystore, and import trusted certificates. See "Importing a Certificate or Trusted Certificate with Fusion Middleware Control" in Securing Applications with Oracle Platform Security Services for instructions on how to import trusted certificates.
-
Configure the WebLogic Server instance to use KSS for Custom Identity and Trust, as described in Configure keystores. You specify the fully-qualified path to the keystore as the URI in the form
kss://system/keystore-name. The keystore type is KSS. -
Configure SSL for the WebLogic Server instance, as described in Set Up SSL.
All the server SSL attributes are dynamic; when modified via the Console, they cause the corresponding SSL server or channel SSL server to restart and use the new settings for new connections. Old connections will continue to run with the old configuration. To ensure that all the SSL connections exist according to the specified configuration, you must reboot WebLogic Server.