9 Configuring Transport-Level Security (SSL)
For more information on SSL, see Understanding Transport-level and Application-level Security in Understanding Oracle Web Services Manager.
Topic:
9.1 About Configuring Keystores for SSL
You can use SSL with the OWSM Policy Manager by configuring keystores.
The policies listed in OWSM Policies that Require You to Configure SSL or List of Policies That Require You to Configure Two-Way SSL.
SSL provides secure connections by allowing two applications connecting over a network to authenticate the other's identity and by encrypting the data exchanged between the applications.
Authentication allows a client, and optionally a server, to verify the identity of the application on the other end of a network connection. Encryption makes data transmitted over the network intelligible only to the intended recipient. A client certificate (two-way SSL) can be used to authenticate the user.
This section describes the following topics:
9.1.1 Understanding KSS Keystore Configuration on WebLogic Server
The OPSS Keystore Service provides an alternate mechanism to manage keys and certificates for message security. This section briefly summarizes the steps that are required to configure the OPSS Keystore Service in WebLogic Server.
As described in "Managing Keys and Certificates with the Keystore Service" in Securing Applications with Oracle Platform Security Services, You use the OPSS Keystore Service to create and maintain keystores of type KSS.
See the following two sources for complete information:
-
"Servers: Configuration: Keystores" in Oracle WebLogic Server Administration Console Online Help.
-
Configuring Keystores in Administering Security for Oracle WebLogic Server 12c (12.2.1).
This section describes the following topics:
9.1.1.1 Configuring the OPSS Keystore Service for Demo Identity and Trust
The KSS demo identity and demo trust keystores are preconfigured when you create a domain, and no additional configuration of these keystores is required.
Perform the following steps to configure the OPSS Keystore Service for demo identity and trust:
9.1.1.2 Recreating the OPSS Keystore Service for Demo Identity and Trust
The KSS demo identity keystore is preconfigured when you create a domain, and no additional configuration of this keystore is required.
However, in case you have subsequently changed or removed the KSS demo identity keystore, use the instructions in this section to recreate the keystore.
You can perform the OPSS Keystore Service operations using either Fusion Middleware Control or the Keystore Service commands with WLST. This section demonstrates the Fusion Middleware Control steps, but "Managing Keys and Certificates with the Keystore Service" describes both options.
Perform the following steps to configure an OPSS Keystore Service for demo identity and trust:
-
Launch Fusion Middleware Control.
-
From the WebLogic Domain menu, select Security then Keystore.
-
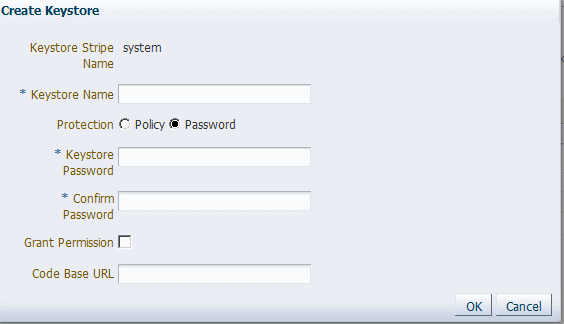
Create a keystore named
demoidentityin thesystemstripe. (See "Creating a Keystore with Fusion Middleware Control" for more information.)-
Select the
systemstripe and click Create Keystore.The Create Keystore page is shown in Figure 9-1.
-
Name this keystore
demoidentity. -
Set the protection type to Password.
-
Set the password to
DemoIdentityKeyStorePassPhrase, and confirm. -
Clear the Grant Permission check box.
-
Do not specify a code base URL.
-
-
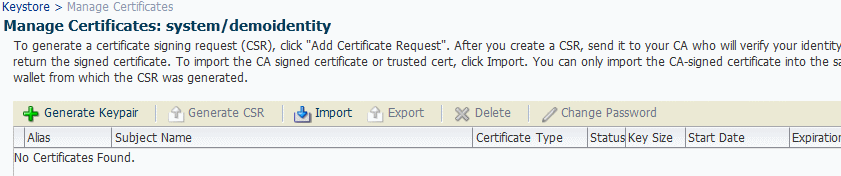
Select the
demoidentitykeystore you just created and click Manage.Enter the
DemoIdentityKeyStorePassPhrasepassword.The Manage Certificates screen shown in Figure 9-2 appears.
-
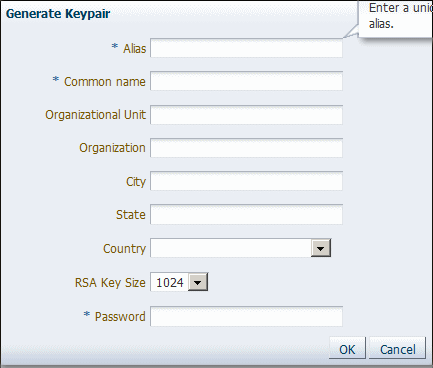
Click Generate Keypair to generate a private/public key pair.
The Generate Keypair screen is shown in Figure 9-3.
-
Specify
DemoIdentityas the alias for the key pair. -
Specify the Common Name as
DemoCertFor_<WLS Domain Name>, whereDemoCertFor_is a required constant and<WLS Domain Name>is the WebLogic Server domain name. For Example:DemoCertFor_base_domain.Note:
The WebLogic Server DefaultHostnameVerifier has been modified to accept this non-standard hostname format when you set the "Use KSS For Demo" flag in the security configuration for the Weblogic Server domain. Other hostname verifiers may not support this format.
-
Specify other site-specific information as appropriate.
-
You can accept the default RSA key size if appropriate for your environment. Oracle requires a key length of 1024 bits or larger.
-
Specify the password as
DemoIdentityPassPhrase. -
Click OK.
-
-
From the WebLogic Server Administration Console, navigate to the Domain -> Security -> Advanced page, and enable the "Use KSS For Demo" check box.
-
Configure the WebLogic Server instance to use Demo Identity and Demo Trust, as described in Configure keystores.
-
Configure SSL for the WebLogic Server instance, as described in Configuring One-Way SSL on WebLogic Server and Configuring Two-Way SSL on WebLogic Server.
Remember that the WebLogic Server DefaultHostnameVerifier has been modified to accept the non-standard
DemoCertFor_<WLS Domain Name>hostname format. Other hostname verifiers may not support this format. -
Restart WebLogic Server.
9.1.1.3 Configuring the OPSS Keystore Service for Custom Identity and Trust
You must configure the OPSS Keystore Service before you can use it for custom identity and trust with WebLogic Server.
You can perform the OPSS Keystore Service operations using either Fusion Middleware Control or the Keystore Service commands with WLST. This section demonstrates the Fusion Middleware Control steps, but "Managing Keys and Certificates with the Keystore Service" describes both options.
Perform the following steps to configure an OPSS Keystore Service for custom identity and trust:
-
Launch Fusion Middleware Control.
-
From the WebLogic Domain menu, select Security then Keystore.
-
Create a keystore in the
systemstripe. (See "Creating a Keystore with Fusion Middleware Control" for more information.)-
Select the
systemstripe and click Create Keystore.The Create Keystore page is shown in Figure 9-4.
-
Name this keystore.
-
Set the protection type to Password.
-
Set the password.
-
Clear the Grant Permission check box.
-
Do not specify a code base URL.
-
-
Select the keystore you just created and click Manage.
Enter the password.
The Manage Certificates screen shown in Figure 9-5 appears.
-
Click Generate Keypair to generate a private/public key pair.
The Generate Keypair screen is shown in Figure 9-6.
-
Specify the alias for the key pair.
-
Specify site-specific information as appropriate.
-
You can accept the default RSA key size if appropriate for your environment. Oracle requires a key length of 1024 bits or larger.
-
Specify the password.
-
Click OK.
-
-
You have the option to use this KSS Demo CA-signed key pair as-is, or to obtain a signed certificate from a reputable vendor such as Entrust, Verisign, and so forth.
To obtain the signed certificate from a reputable vendor, select the alias for the key pair and click Generate CSR. After you create a CSR, send it to your CA, which will authenticate the certificate request and create a digital certificate based on the request.
See "Importing a Certificate with Fusion Middleware Control" in Importing a Certificate with Fusion Middleware Control for instructions on how to import the CA-signed certificate.
-
If you do not use the preconfigured OPSS Keystore Service trust store
kss://system/trust, you must create your own.Note:
Oracle recommends you use the OPSS Keystore Service trust store because it simplifies trust configuration.
To create your own trust store, create another OPSS Keystore Service keystore, and import trusted certificates. See Importing a Certificate with Fusion Middleware Control in Securing Applications with Oracle Platform Security Services for instructions on how to import trusted certificates.
-
Configure the WebLogic Server instance to use KSS for Custom Identity and Trust, as described in Configure keystores. You specify the fully-qualified path to the key store as the URI in the form
kss://system/keystore-name. The keystore type is KSS. -
Configure SSL for the WebLogic Server instance, as described in Configuring One-Way SSL on WebLogic Server and Configuring Two-Way SSL on WebLogic Server.
All the server SSL attributes are dynamic; when modified via the Console, they cause the corresponding SSL server or channel SSL server to restart and use the new settings for new connections. Old connections will continue to run with the old configuration. To ensure that all the SSL connections exist according to the specified configuration, you must reboot WebLogic Server.
9.1.2 Configuring a JKS Keystore on WebLogic Server
You can configure the JKS keystore in WebLogic Server.
This topic briefly summarizes the steps that are required to configure the JKS keystore in WebLogic Server.
You may find that using the KSS Keystore Service as described in Understanding KSS Keystore Configuration on WebLogic Server is the most convenient method of configuring a keystore. However, you also have the option of using a JKS keystore, including the WebLogic default identity keystore DemoIdentity.jks and the default trust keystore DemoTrust.jks.
For more information see :
- Servers: Configuration: Keystores in Oracle WebLogic Server Administration Console Online Help.
- Configuring Keystores in Administering Security for Oracle WebLogic Server 12c (12.2.1).
WebLogic Server is configured with a default identity keystore DemoIdentity.jks and a default trust keystore DemoTrust.jks. In addition, WebLogic Server trusts the certificate authorities in the cacerts file in the JDK. This default keystore configuration is appropriate for testing and development purposes. However, these keystores should not be used in a production environment.
To configure identity and trust for a server:
9.2 Configuring One-Way SSL on WebLogic Server
With one-way SSL, the server is required to present a certificate to the client but the client is not required to present a certificate to the server.
After you configure identity and trust keystores for a WebLogic Server instance as described in About Configuring Keystores for SSL, you configure its SSL attributes. These attributes describe the location of the identity key and certificate in the keystore specified on the Configuration: Keystores page. Use the Configuration: SSL page to specify this information.
This section summarizes the steps required to configure SSL on WebLogic Server. For complete information, see Configuring SSL.
To configure SSL:
9.3 Configuring Two-Way SSL on WebLogic Server
With two-way SSL, the server presents a certificate to the client and the client presents a certificate to the server. WebLogic Server can be configured to require clients to submit valid and trusted certificates before completing the SSL handshake.
After you configure identity and trust keystores for a WebLogic Server instance as described in About Configuring Keystores for SSL, you can configure its two-way SSL attributes if the policy or template you are using requires it, as described in List of Policies That Require You to Configure Two-Way SSL.
This section summarizes the steps required to configure SSL on WebLogic Server. For complete information, see Configuring SSL.
Perform the following steps to configure two-way SSL:
9.4 Configuring One-Way SSL for a Web Service Client
The core WebLogic Server security subsystem uses private key and X.509 certificate pairs, stored in the default keystores, for SSL.
You must ensure that the web service client trusts the X.509 certificate that WebLogic Server uses to digitally sign the request. Do one of the following:
-
Ensure that WebLogic Server obtains a digital certificate that the client automatically trusts, because it has been issued by a trusted certificate authority.
-
Create a certificate registry that lists all the individual certificates trusted by WebLogic Server, and then ensure that the client trusts these registered certificates.
-
If the client and WebLogic Server are on the same system, have them use the same trust store.
To configure one-way SSL for a web services client, you set the following properties in the client's JVM:
-
javax.net.ssl.trustStore -- The system property that specifies the trust store location. For JKS it is the name of the file that contains the trust store. For KSS it is the KSS URI.
You can either use the existing JKS or KSS trust store, or create a new one. For example, you can have
javax.net.ssl.trustStorepoint to the defaultkss://system/trusttrust store.To create a new JKS trust store you can use the keytool utility. To create a new KSS keystore you can use Fusion Middleware Control.
-
javax.net.ssl.trustStoreType -- The type of trust store object that you want the default TrustManager to use, either JKS or KSS.
-
javax.net.ssl.trustStorePassword -- JKS only. Specifies the trust store's password.
For Oracle Infrastructure web service clients, you can also set individual properties in their descriptor files. The properties set in individual descriptor files override properties set using the system properties:
-
For a SOA composite, set the properties in
composite.xml. -
For ADF web service data control (ADFDC), set the properties in
connections.xml. -
For ADF business components and WebCenter clients, set the properties in
oracle-webservices-client.xml.
9.5 Configuring Two-Way SSL for a Web Service Client
To configure two-way SSL for a Web Service Client, you must ensure that WebLogic Server is able to validate the X.509 certificate that the client uses to digitally sign its request and that WebLogic Server in turn uses to encrypt its responses to the client.
Note:
See "Configuring SOA Composite Applications for Two-Way SSL Communication" in Administering Oracle SOA Suite and Oracle Business Process Management Suite for specific configuration steps when a SOA application is the web service client over two-way SSL.
Do one of the following to configure Two-Way SSL for a Web Service Client:
-
Ensure that the client application obtains a digital certificate that WebLogic Server automatically trusts, because it has been issued by a trusted certificate authority.
-
Create a certificate registry that lists all the individual certificates trusted by WebLogic Server, and then ensure that the client uses one of these registered certificates.
-
If the client and WebLogic Server are on the same system, have them use the same key store and trust store.
To configure SSL for a web service client, make sure that the following properties are set in the client's JVM:
-
javax.net.ssl.keyStore -- The system property that specifies the keystore location. For JKS it is the name of the file that contains the key store. For KSS it is the KSS URI.
You can either use the existing JKS or KSS key store, or create a new one. For example, you can have
javax.net.ssl.keyStorepoint to the defaultkss://system/castorekey store so that the web service client uses the X.509 certificates that WebLogic Server uses.To create a new JKS key store you can use the keytool utility. To create a new KSS keystore you can use Fusion Middleware Control.
-
javax.net.ssl.keyStoreType -- The type of KeyStore object that you want the default TrustManager to use, either JKS or KSS.
-
javax.net.ssl.trustStore -- The system property that specifies the trust store location. For JKS it is the name of the file that contains the trust store. For KSS it is the KSS URI.
You can either use the existing JKS or KSS trust store, or create a new one. For example, you can have
javax.net.ssl.trustStorepoint to the defaultkss://system/trusttrust store so that the web service client trusts the X.509 certificates that WebLogic Server trusts.To create a new JKS trust store you can use the keytool utility. To create a new KSS keystore you can use Fusion Middleware Control.
-
javax.net.ssl.trustStoreType -- The type of TrustStore object that you want the default TrustManager to use, either JKS or KSS.
-
javax.net.ssl.trustStorePassword -- JKS only. Specifies the trust store's password.
-
HTTPClient.ssl.identityAlias -- The alias of the certificate you want to use for identity. If the alias is null, the JSSE provider chooses one of the aliases in the keystore.
For Oracle Infrastructure web service clients, you can also set individual properties in their descriptor files. The properties set in individual descriptor files override properties set using the system properties:
-
For a SOA composite, set the properties in
composite.xml. -
For ADF web service data control (ADFDC), set the properties in
connections.xml. -
For ADF business components and WebCenter clients, set the properties in
oracle-webservices-client.xml.
9.6 Understanding SSL Configuration on Oracle HTTP Server
The HTTPS protocol uses an industry standard protocol called Secure Sockets Layer (SSL) to establish secure connections between clients and servers. You can use the HTTPS/SSL support offered by the Oracle HTTP Server as one of the communication protocols to communicate between the client and the web service. This section describes how to set up a web service client and a web service using OWSM policies to send requests over SSL.
Oracle HTTP Server is configured as a Web proxy that intermediates between the client and Oracle WebLogic Server. SSL is enabled at Oracle HTTP Server and SSL transport is turned on between the client and Oracle HTTP Server. Communication remains non-SSL between Oracle HTTP Server and WebLogic Server.
For more information, see:
-
"Configuring SSL in Oracle Fusion Middleware", in Administering Oracle Fusion Middleware.
-
"Configuring SSL" in Administering Security for Oracle WebLogic Server 12c (12.2.1).
-
"Set Up SSL" in the Oracle WebLogic Server Administration Console Online Help
-
"Configuring Secure Sockets Layer" in Administrator's Guide for Oracle HTTP Server.
This section describes how to configure the policies that require one-way SSL and two-way SSL. It includes the following topics:
9.6.1 Configuring One-Way SSL on Oracle HTTP Server
This section describes how to configure one-way SSL on Oracle HTTP Server.
For more information on the OWSM policies that require one-way SSL configuration, see OWSM Policies that Require You to Configure SSL.
Perform the following steps to use one-way SSL:
-
Configure the Oracle HTTP Server as follows:
-
In the file ORACLE_INSTANCE
/config/OHS/<ohs_name>/ssl.conf, configure Oracle HTTP Server as a Web proxy and specify the list of URLs you want to access, as shown in the following example.# added properties for configuring OHS as webproxy <IfModule weblogic_module> WebLogicHost <host> WebLogicPort <port> SecureProxy Off WlProxySSL On Debug ALL WlLogFile /tmp/weblogic.log #the location attributes list the urls you want to access via OHS <Location /myWlsService> SetHandler weblogic-handler WebLogicHost <host> WeblogicPort <port> </Location> -
In the same file, set the following properties under virtual host configuration to ensure the client certificate information is sent to WebLogic Server:
SSLVerifyClient optional -
By default, SSL in enabled on Oracle HTTP Server. The default https port is 4443. For more information on configuring this port, see "Configuring SSL in Oracle Fusion Middleware" in Administering Oracle Fusion Middleware.
-
Restart Oracle HTTP Server.
For more information, see "Configuring SSL in Oracle Fusion Middleware" in Administering Oracle Fusion Middleware.
-
-
Create a wallet as described at "Managing Keystores, Wallets, and Certificates" in Administering Oracle Fusion Middleware and replace the default wallet. The default wallet is located in the ORACLE_INSTANCE
/config/OHS/<ohs_name>/keystores/defaultdirectory. The following example shows sample commands to create a wallet for one-way SSL../orapki wallet create -wallet <wallet_location> -pwd password -auto_login ./orapki wallet display -wallet <wallet_location> -pwd password ./orapki cert display -cert <wallet_location>/ohs.crt ./orapki wallet add -wallet <wallet_location> -keysize 512 -dn "CN=<host_name>,OU=st,O=owsm,L=N,ST=delhi,C=IN" -self_signed -validity 700 -serial_num 20 -cert <wallet_location>/ohs.crt -user_cert -pwd password ./orapki wallet display -wallet <wallet_location> -pwd password JAVA_HOME/bin/keytool -import -trustcacerts -file ohs.crt -alias sslcert -keystore client_keystore.jks -storepass password
-
In the Oracle WebLogic Administration Console, perform the following:
-
Navigate to the Servers page in the Environment tab.
-
Click Adminserver and in Configuration, select General.
-
In the Advanced section, check the following: WebLogic Plug-In Enabled, and Client Cert Proxy Enabled.
-
Save the changes.
-
Set the same parameters for the SOA server.
For more information, see "Server: Configuration: General" in the Oracle WebLogic Server Administration Console Online Help.
-
To modify the client to use one-way (server authentication mode), create a JSE client from the web service using JDeveloper. Modify the parameters and properties, as shown in the following example.
public static void main(String [] args)
{
class1Service = new Class1Service();
SecurityPolicyFeature[] securityFeatures =
new SecurityPolicyFeature[] { new SecurityPolicyFeature("oracle/wss_
saml_token_over_ssl_client_policy") };
Class1 class1 = class1Service.getClass1Port(securityFeatures);
((BindingProvider) class1).getRequestContext().put(BindingProvider.ENDPOINT_
ADDRESS_PROPERTY,
"https://<host>:4443/myWlsService/Class1Port");
((BindingProvider) class1).getRequestContext().put(BindingProvider.USERNAME_
PROPERTY, "weblogic");
System.setProperty("javax.net.ssl.trustStore","D:\\OWSM_
QA\\11g\\PS2\\OHS\\wallet\\client_keystore.jks");
System.setProperty("javax.net.ssl.trustStorePassword","password");
System.setProperty("javax.net.ssl.trustStoreType","JKS");
System.setProperty("weblogic.security.SSL.ignoreHostnameVerification" ,
"true");
System.setProperty("java.protocol.handler.pkgs",
"com.sun.net.ssl.internal.www.protocol");
System.setProperty("javax.net.debug","all");
System.out.println("Call to the SSL service...");
String response1 = class1.sayHello("test");
System.out.println("Response = " + response1);
}
9.6.2 Configuring Two-Way SSL on Oracle HTTP Server
This section describes how to configure two-way SSL on Oracle HTTP Server.
For more information on the OWSM policies that require two-way SSL configuration, see List of Policies That Require You to Configure Two-Way SSL.
Perform the following sections to use two-way SSL:
-
Configure the Oracle HTTP Server as follows:
-
In the file ORACLE_INSTANCE
/config/OHS/<ohs_name>/ssl.conf, configure Oracle HTTP Server as a Web proxy and specify the list of URLs you want to access, as shown in the following example.# added properties for configuring OHS as webproxy <IfModule weblogic_module> WebLogicHost <host> WebLogicPort <port> SecureProxy Off WlProxySSL On Debug ALL WlLogFile /tmp/weblogic.log #the location attributes list the urls you want to access via OHS <Location /myWlsService> SetHandler weblogic-handler WebLogicHost <host> WeblogicPort <port> </Location> -
In the same file, set the following properties under virtual host configuration to ensure the client certificate information is sent to the WebLogic Server:
SSLVerifyClient optionalSSLOptions +StdEnvVars +ExportCertDataSSLOptions +ExportCertDatais a mod_ssl directive that ensures certificate-related information is sent to WebLogic Server.SSLOptions +StdEnvVars +ExportCertDataensures that SSL-related information is sent. -
By default, SSL in enabled on Oracle HTTP Server. The default https port is 4443. For more information on configuring this port, see "Configuring SSL in Oracle Fusion Middleware" in Administering Oracle Fusion Middleware.
-
Restart Oracle HTTP Server.
For more information, see "Configuring SSL in Oracle Fusion Middleware" in Administering Oracle Fusion Middleware.
-
-
Create a wallet as described at "Managing Keystores, Wallets, and Certificates" in Administering Oracle Fusion Middleware and replace the default wallet. The default wallet is located in the ORACLE_INSTANCE
/config/OHS/<ohs_name>/keystores/defaultdirectory. See the following example for sample commands to create a wallet for two-way SSL.JAVA_HOME/bin/keytool -genkey -alias twowayssl -keyalg RSA -keystore twowaykeystore.jks -storepass password -validity 700 ./orapki wallet add -wallet <wallet_location> -cert <wallet_location>/twowayssl.crt -trusted_cert -pwd password
-
In the Oracle WebLogic Administration Console, perform the following:
-
Navigate to the Servers page in the Environment tab.
-
Click Adminserver and in Configuration, select General.
-
In the Advanced section, check the following: WebLogic Plug-In Enabled, and Client Cert Proxy Enabled.
-
Save the changes.
-
Set the same parameters for the SOA server.
For more information, see "Server: Configuration: General" in the Oracle WebLogic Server Administration Console Online Help.
-
To modify the client to use two-way (mutual authentication mode) SSL, create a JSE client from the web service using JDeveloper. Modify the parameters and properties as described in the following example.
public static void main(String [] args)
{
class1Service = new Class1Service();
SecurityPolicyFeature[] securityFeatures =
new SecurityPolicyFeature[] { new SecurityPolicyFeature("oracle/wss_saml_token_over_ssl_client_policy") };
Class1 class1 = class1Service.getClass1Port(securityFeatures);
((BindingProvider) class1).getRequestContext().put(BindingProvider.ENDPOINT_
ADDRESS_PROPERTY,
"https://<host>:4443/myWlsService/Class1Port");
((BindingProvider) class1).getRequestContext().put(BindingProvider.USERNAME_
PROPERTY, "weblogic");
((BindingProvider) class1).getRequestContext().put(BindingProvider.PASSWORD_
PROPERTY, "password");
System.setProperty("javax.net.ssl.trustStore","D:\\OWSM_
QA\\11g\\PS2\\OHS\\wallet\\twowaykeystore.jks");
System.setProperty("javax.net.ssl.trustStorePassword","password");
System.setProperty("javax.net.ssl.trustStoreType","JKS");
System.setProperty("javax.net.ssl.keyStore","D:\\OWSM_QA\\11g\\PS2\\OHS\\wallet\\twowaykeystore.jks");
System.setProperty("javax.net.ssl.keyStorePassword","password");
System.setProperty("javax.net.ssl.keyStoreType","JKS");
System.setProperty("weblogic.security.SSL.ignoreHostnameVerification" ,
"true");
System.setProperty("java.protocol.handler.pkgs",
"com.sun.net.ssl.internal.www.protocol");
System.setProperty("javax.net.debug","all");
System.out.println("Call to the SSL service...");
String response1 = class1.sayHello("test");
System.out.println("Response = " + response1);
}