Chapter 3 Planning Your Network
This chapter describes the issues you must resolve in order to create your network in an organized, cost-effective manner. After you have resolved these issues, you can devise a plan for your network to follow as you set it up and administer it in the future.
If you are unfamiliar with TCP/IP fundamentals, refer to Chapter 2, TCP/IP Protocol Suite.
Designing the Network
The first phase in the life of a network--designing the network--involves making decisions about the type of network that best suits the needs of your organization. Some of the planning decisions you make will involve network hardware; for example:
-
Number of host machines your network can support
-
Type of network media to use: Ethernet, token ring, FDDI, and so on
-
Network topology; that is, the physical layout and connections of the network hardware
-
Types of hosts the network will support: standalone, diskless, and dataless
Based on these factors, you can determine the size of your local-area network.
Note -
Planning the network hardware is outside the scope of this manual. Refer to the manuals that came with your hardware for assistance.
Factors Involved in Network Planning
After you have completed your hardware plan, you are ready to begin network planning, from the software perspective.
As part of the planning process you must:
-
Obtain a network number and, if applicable, register your network domain with the InterNIC.
-
Devise an IP addressing scheme for your hosts, after you receive your IP network number.
-
Create a list containing the IP addresses and host names of all machines that make up your network, which you can use as you build network databases.
-
Determine which name service to use on your network: NIS, NIS+, DNS, or the network databases in the local /etc directory.
-
Establish administrative subdivisions, if appropriate for your network.
-
Determine if your network is large enough to require routers, and, if appropriate, create a network topology that supports them.
-
Set up subnets, if appropriate for your network.
The remainder of Chapter 3, Planning Your Network, explains how to plan your network with these factors in mind.
Setting Up an IP Addressing Scheme
The number of machines you expect to support will affect several decisions you will need to make at this stage of setting up a network for your site. Your organization may require a small network of several dozen standalone machines located on one floor of a single building. Alternatively, you may need to set up a network with more than 1000 hosts in several buildings. This arrangement may require you to further divide your network into subdivisions called subnets. The size of your prospective network will affect the
-
Network class you apply for
-
Network number you receive
-
IP addressing scheme you use for your network
Obtaining a network number and then establishing an IP addressing scheme is one of the most important tasks of the planning phase of network administration.
Parts of the IP Address
Each network running TCP/IP must have a unique network number, and every machine on it must have a unique IP address. It is important to understand how IP addresses are constructed before you register your network and obtain its network number.
The IP address is a 32-bit number that uniquely identifies a network interface on a machine. An IP address is typically written in decimal digits, formatted as four 8-bit fields separated by periods. Each 8-bit field represents a byte of the IP address. This form of representing the bytes of an IP address is often referred to as the dotted-decimal format.
The bytes of the IP address are further classified into two parts: the network part and the host part. Figure 3-1 shows the component parts of a typical IP address, 129.144.50.56.
Figure 3-1 Parts of an IP Address
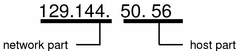
Network Part
This part specifies the unique number assigned to your network. It also identifies the class of network assigned. In Figure 3-1, the network part takes up two bytes of the IP address.
Host Part
This is the part of the IP address that you assign to each host. It uniquely identifies this machine on your network. Note that for each host on your network, the network part of the address will be the same, but the host part must be different.
Subnet Number (Optional)
Local networks with large numbers of hosts are sometimes divided into subnets. If you choose to divide your network into subnets, you need to assign a subnet number for the subnet. You can maximize the efficiency of the IP address space by using some of the bits from the host number part of the IP address as a network identifier. When used as a network identifier, the specified part of the address becomes the subnet number. You create a subnet number by using a netmask, which is a bit mask that selects the network and subnet parts of an IP address. (Refer to "Creating the Network Mask" for full details.)
Network Classes
The first step in planning for IP addressing on your network is to determine which network class is appropriate for your network. After you have done this, you can take the crucial second step: obtain the network number from the InterNIC addressing authority.
Currently there are three classes of TCP/IP networks. Each class uses the 32-bit IP address space differently, providing more or fewer bits for the network part of the address. These classes are class A, class B, and class C.
Class A Network Numbers
A class A network number uses the first eight bits of the IP address as its "network part." The remaining 24 bits comprise the host part of the IP address, as illustrated in Figure 3-2 below.
Figure 3-2 Byte Assignment in a Class A Address
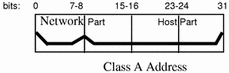
The values assigned to the first byte of class A network numbers fall within the range 0-127. Consider the IP address 75.4.10.4. The value 75 in the first byte indicates that the host is on a class A network. The remaining bytes, 4.10.4, establish the host address. The InterNIC assigns only the first byte of a class A number. Use of the remaining three bytes is left to the discretion of the owner of the network number. Only 127 class A networks can exist. Each one of these numbers can accommodate up to 16,777,214 hosts.
Class B Network Numbers
A class B network number uses 16 bits for the network number and 16 bits for host numbers. The first byte of a class B network number is in the range 128-191. In the number 129.144.50.56, the first two bytes, 129.144, are assigned by the InterNIC, and comprise the network address. The last two bytes, 50.56, make up the host address, and are assigned at the discretion of the owner of the network number. Figure 3-3 graphically illustrates a class B address.
Figure 3-3 Byte Assignment in a Class B Address
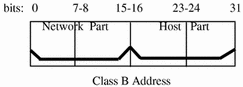
Class B is typically assigned to organizations with many hosts on their networks.
Class C Network Numbers
Class C network numbers use 24 bits for the network number and 8 bits for host numbers. Class C network numbers are appropriate for networks with few hosts--the maximum being 254. A class C network number occupies the first three bytes of an IP address. Only the fourth byte is assigned at the discretion of the network owners. Figure 3-4 graphically represents the bytes in a class C address.
Figure 3-4 Byte Assignment in a Class C Address
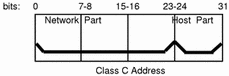
The first byte of a class C network number covers the range 192-223. The second and third each cover the range 1- 255. A typical class C address might be 192.5.2.5. The first three bytes, 192.5.2, form the network number. The final byte in this example, 5, is the host number.
Administering Network Numbers
If your organization has been assigned more than one network number, or uses subnets, appoint a centralized authority within your organization to assign network numbers. That authority should maintain control of a pool of assigned network numbers, assigning network, subnet, and host numbers as required. To prevent problems, make sure that duplicate or random network numbers do not exist in your organization.
Designing Your IP Addressing Scheme
After you have received your network number, you can then plan how you will assign the host parts of the IP address.
Table 3-1 shows the division of the IP address space into network and host address spaces. For each class, "range" specifies the range of decimal values for the first byte of the network number. "Network address" indicates the number of bytes of the IP address that are dedicated to the network part of the address, with each byte represented by xxx. "Host address" indicates the number of bytes dedicated to the host part of the address. For example, in a class A network address, the first byte is dedicated to the network, and the last three are dedicated to the host. The opposite is true for a class C network.
Table 3-1 Division of IP Address Space|
Class |
Range |
Network Address |
Host Address |
|---|---|---|---|
|
0-127 |
xxx |
xxx.xxx.xxx |
|
|
128-191 |
xxx.xxx |
xxx.xxx |
|
|
192-223 |
xxx.xxx.xxx |
xxx |
The numbers in the first byte of the IP address define whether the network is class A, B, or C and are always assigned by the InterNIC. The remaining three bytes have a range from 0-255. The numbers 0 and 255 are reserved; you can assign the numbers 1-254 to each byte depending on the network number assigned to you.
Table 3-2 shows which bytes of the IP address are assigned to you and the range of numbers within each byte that are available for you to assign to your hosts.
Table 3-2 Range of Available Numbers|
Network Class |
Byte 1 Range |
Byte 2 Range |
Byte 3 Range |
Byte 4 Range |
|---|---|---|---|---|
|
0-127 |
1-254 |
1-254 |
1-254 |
|
|
128-191 |
Preassigned by Internet |
1-254 |
1-254 |
|
|
192-223 |
Preassigned by Internet |
Preassigned by Internet |
1-254 |
How IP Addresses Apply to Network Interfaces
In order to connect to the network, a computer must have at least one network interface, as explained in "Network Interfaces". Each network interface must have its own unique IP address. The IP address that you give to a host is assigned to its network interface, sometimes referred to as the primary network interface. If you add a second network interface to a machine, it must have its own unique IP number. Adding a second network interface changes the function of a machine from a host to a router, as explained in Chapter 5, Configuring Routers. If you add a second network interface to a host and disable routing, the host is then considered a multihomed host.
Each network interface has a device name, device driver, and associated device file in the /devices directory. The network interface might have a device name such as le0 or smc0, device names for two commonly used Ethernet interfaces.
Note -
This book assumes that your machines have Ethernet network interfaces. If you plan to use different network media, refer to the manuals that came with the network interface for configuration information.
Naming Entities on Your Network
After you have received your assigned network number and given IP addresses to your hosts, the next task is to assign names to the hosts and determine how you will handle name services on your network. You will use these names when you initially set up your network and, later, for expanding your network through routers or PPP.
The TCP/IP protocols locate a machine on a network by using its IP address. However, humans find it much easier to identify a machine if it has an understandable name. Therefore, the TCP/IP protocols (and the Solaris operating system) require both the IP address and the host name to uniquely identify a machine.
From a TCP/IP perspective, a network is a set of named entities. A host is an entity with a name. A router is an entity with a name. The network is an entity with a name. A group or department in which the network is installed can also be given a name, as can a division, a region, or a company. In theory, there is virtually no limit to the hierarchy of names that can be used to identify a network and its machines. The term for these named entities is domain.
Administering Host Names
Many sites let users pick host names for their machines. Servers also require at least one host name, which is associated with the IP address of its primary network interface.
As network administrator, you must ensure that each host name in your domain is unique. In other words, no two machines on your network could both have the name "fred," although the machine "fred" might have multiple IP addresses.
When planning your network, make a list of IP addresses and their associated host names for easy access during the setup process. The list can help you verify that all host names are unique.
Selecting a Name Service
The Solaris operating system gives you the option of using four types of name services: local files, NIS, NIS+, and DNS. Name services maintain critical information about the machines on a network, such as the host names, IP addresses, Ethernet addresses, and the like.
Network Databases
When you install the operating system, you supply the host name and IP address of your server, clients, or standalone machine as part of the procedure. The Solaris installation program enters this information into a network database called the hosts database. The hosts database is one of a set of network databases that contain information necessary for TCP/IP operation on your network. These databases are read by the name service you select for your network.
Setting up the network databases is a critical part of network configuration. Therefore, you need to decide which name service to use as part of the network planning process. Moreover, the decision to use name services also affects whether or not you organize your network into an administrative domain. Chapter 4, Configuring TCP/IP on the Network, has detailed information on the set of network databases.
Using NIS, NIS+, or DNS for Name Service
The NIS, NIS+, or DNS name services maintain network databases on several servers on the network. Solaris Naming Setup and Configuration Guide fully describes these name services and explains how to set them up. It also explains the "namespace" and "administrative domain" concepts in complete detail. If you are changing name services from NIS to NIS+, refer to NIS+ Transition Guide. You should refer to these manuals to help you decide whether to use these name services on your network.
Using Local Files for Name Service
If you do not implement NIS, NIS+, or DNS, the network will use local files to provide name service. The term "local files" refers to the series of files in the /etc directory that the network databases use. The procedures in this book assume you are using local files for your name service, unless otherwise indicated.
Note -
If you decide to use local files as the name service for your network, you can set up another name service at a later date.
Domain Names
Many networks organize their hosts and routers into a hierarchy of administrative domains. If you are going to use NIS, NIS+, or the DNS name services, you must select a domain name for your organization that is unique worldwide. To ensure that your domain name is unique, you should register it with the InterNIC. This is especially important if you plan to use DNS.
The domain name structure is hierarchical. A new domain typically is located below an existing, related domain. For example, the domain name for a subsidiary company could be located below the domain of the parent company. If it has no other relationship, an organization can place its domain name directly under one of the existing top-level domains.
Examples of top-level domains include:
-
.com - Commercial companies (international in scope)
-
.edu - Educational institutions (international in scope)
-
.gov - U.S. government agencies
-
.fr - France
The name that identifies your organization is one that you select, with the provision that it is unique.
Administrative Subdivisions
The question of administrative subdivisions deals with matters of size and control. The more hosts and servers you have in a network, the more complex your management task. You may wish to handle such situations by setting up additional administrative divisions in the form of more additional networks of a particular class or by dividing existing networks into subnets. The decision as to whether to set up administrative subdivisions for your network hinges on the following factors:
-
How large is the network?
A single network of several hundred hosts, all in the same physical location and requiring the same administrative services, can be handled by a single administrative division. On the other hand, a network of fewer machines, divided into a number of subnets and physically scattered over an extensive geographic area, would be likely to benefit from the establishment of several administrative subdivisions.
-
Do users on the network have similar needs?
For example, you may have a network that is confined to a single building and supports a relatively small number of machines. These machines are divided among a number of subnetworks, each supporting groups of users with different needs. Such a case could call for an administrative subdivision for each subnet.
Solaris Naming Administration Guide discusses administrative subdivisions in detail.
Registering Your Network
Before you assign IP addresses to the machines on your Solaris network, you must obtain a network number from the InterNIC. Moreover, if you plan to use administrative domains, you should register them with the InterNIC.
InterNIC and InterNIC Registration Services
The InterNIC was created in 1993 to act as a central body where users of the Internet could go for information, such as
-
What the Internet's policies are
-
How to access the Internet, including training services
-
What resources are available to Internet users, such as anonymous FTP servers, Usenet user groups, and so on.
The InterNIC also includes the InterNIC Registration Services, the organization with which you register your TCP/IP network. The InterNIC Registration Services provide templates for obtaining a network number and for registering your domain. Two points to remember about registration are:
Note -
Do not arbitrarily assign network numbers to your network, even if you do not plan to attach it to other existing TCP/IP networks.
Subnet numbers are not assigned by the InterNIC. Rather, they are composed partly of the assigned network number and numbers that you define, as explained in "What is Subnetting".
-
You--not InterNIC--determine the domain name for your network and then register it with the InterNIC.
How to Contact the InterNIC
You can reach the InterNIC Registration Services by:
-
Mail
Network Solutions Attn: InterNIC Registration Services 505 Huntmar Park Drive Herndon, Virginia 22070
-
Telephone
The phone number is 1-703-742-4777. Phone service is available from 7 a.m. to 7 p.m. Eastern Standard Time.
-
Send email regarding network registration to: Hostmaster@rs.internic.net
-
Anonymous FTP or Telnet inquiries, through the Gopher and WAIS interfaces. Connect to rs.internic.net. (Anonymous FTP and Telnet are outside the scope of this book; however, books on these subjects are available in computer bookstores.)
Adding Routers
Recall that in TCP/IP, two types of entities exist on a network: hosts and routers. All networks must have hosts, while not all networks require routers. Whether you use routers should depend on the physical topology of the network. This section introduces the concepts of network topology and routing, important when you decide to add another network to your existing network environment.
Network Topology
Network topology describes how networks fit together. Routers are the entities that connect networks to each other. From a TCP/IP perspective, a router is any machine that has two or more network interfaces. However, the machine cannot function as a router until properly configured, as described in Chapter 5, Configuring Routers.
Two or more networks can be connected together by routers to form larger internetworks. The routers must be configured to pass packets between two adjacent networks. They also should be able to pass packets to networks that lie beyond the adjacent networks.
Figure 3-5 shows the basic parts of a network topology. The first illustration shows a simple configuration of two networks connected by a single router. The second shows a configuration of three networks, interconnected by two routers. In the first case, network 1 and network 2 are joined into a larger internetwork by router R. In the second case, router R1 connects networks 1 and 2, and router R2 connects networks 2 and 3, thus forming a network made up of networks 1, 2, and 3.
Figure 3-5 Basic Network Topology
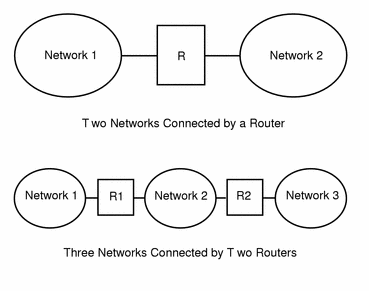
Routers join networks into internetworks and route packets between them based on the addresses of the destination network. As internetworks grow more complex, each router must make more and more decisions regarding where packets are to be sent.
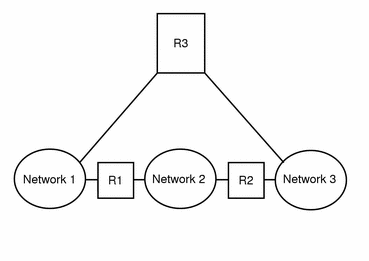
A step up in complexity is the case shown in Figure 3-6. Networks 1 and 3 are directly connected by a router R3. The reason for such redundancy is reliability. If network 2 goes down, router R3 still provides a route between networks 1 and 3. Any number of networks can be interconnected and communicate as long as they all adhere to the same network protocols.
Figure 3-6 Providing an Additional Path Between Networks
How Routers Transfer Packets
Routing decisions on a network are based on the network portion of the IP address of the recipient that is contained in the packet header. If this address includes the network number of the local network, the packet goes directly to the host with that IP address. If the network number is not the local network, the packet goes to the router on the local network.
Routers maintain routing information in routing tables. These tables contain the IP address of the hosts and routers on the networks to which the router is connected. The tables also contain pointers to these networks. When a router gets a packet, it consults its routing table to see if it lists the destination address in the header. If the table does not contain the destination address, the router forwards the packet to another router listed in its routing table. Refer to Chapter 5, Configuring Routers, for detailed information on routers.
Figure 3-7 shows a network topology with three networks connected by two routers.
Figure 3-7 Three Interconnected Networks
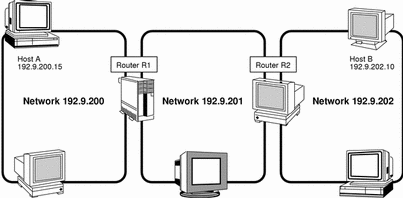
Router R1 connects networks 192.9.200 and 192.9.201. Router R2 connects networks 192.9.201 and 192.9.202. If host A on network 192.9.200 sends a message to host B on network 192.9.202, this is what happens.
-
Host A sends a packet out over network 192.9.200. The packet header contains the IP address of the recipient host B, 192.9.202.10.
-
None of the machines on network 192.9.200 has the IP address 192.9.202.10. Therefore, router R1 accepts the packet.
-
Router R1 examines its routing tables. No machine on network 192.9.201 has the address 192.9.202.10. However, the routing tables do list router R2.
-
R1 then selects R2 as the "next hop" router and sends the packet to R2.
-
Because R2 connects network 192.9.201 to 192.9.202, it has routing information for host B. Router R2 then forwards the packet to network 192.9.202, where it is accepted by host B.
- © 2010, Oracle Corporation and/or its affiliates
