| Oracle® Collaboration Suite SSL Configuration Release 2 (9.0.4) Part Number B15611-01 |
|
|
View PDF |
| Oracle® Collaboration Suite SSL Configuration Release 2 (9.0.4) Part Number B15611-01 |
|
|
View PDF |
Oracle Collaboration Suite relies on the Infrastructure of Oracle9i Application Server to host and serve its applications. Enabling Secure Sockets Layer (SSL) for Oracle Collaboration Suite involves configuring the following components:
Oracle9i Application Server Web Cache
Oracle9i Application Server Single Sign-On
Oracle Delegated Administration Services
Oracle Collaboration Suite applications
Oracle HTTP Server (on the Middle Tier and the Infrastructure tier)
This document explains how to configure SSL for these components only, and provides instructions for both a single-box installation and a distributed installation of Oracle Collaboration Suite.
This document refers to the Infrastructure tier and the Middle Tier of Oracle Collaboration Suite. The following clarifies which components reside on each tier:
Infrastructure tier refers to the Oracle9iAS Single Sign-On, Oracle HTTP Server for Oracle9iAS Single Sign-On, and Oracle Delegated Administration Services.
Middle Tier refers to the Oracle Collaboration Suite applications, Oracle HTTP Server for Oracle Collaboration Suite applications, and Web Cache.
For a single-box installation, a Web Cache reverse proxy sits in front of the Middle Tier and accepts and redirects incoming HTTP/HTTPS requests. Web Cache in the Middle Tier is disabled.
For a distributed installation, Web Cache is running on the Middle Tier and accepts incoming HTTP/HTTPS requests to the Middle Tier. Requests to the Infrastructure tier bypass Web Cache in a distributed installation.
This chapter contains the following topics:
You enable components in Oracle9i Application Server to use SSL using the Enterprise Manager Web site. In some cases, you need to manually edit configuration files.
SSL secures communication between two parties: a client and a server. If three or more parties are involved, for example, client browser, Web Cache, Oracle HTTP Server, and OC4J, then you may have to configure all components to use SSL.
Figure 1-1 shows typical communication paths between Oracle9i Application Server components and the protocols that they use. For example, browsers use HTTP to communicate with Web Cache, and Oracle HTTP Server uses Apache Java Protocol (AJP) to communicate with OC4J. All these protocols can work with SSL.
When you enable SSL for Oracle Collaboration Suite, the HTTP communications depicted in Figure 1-1 will then use the HTTPS protocol for secure connections. URLs that require an SSL connection begin with https rather that http.
Figure 1-1 Communication Paths Between Components in Oracle9i Application Server
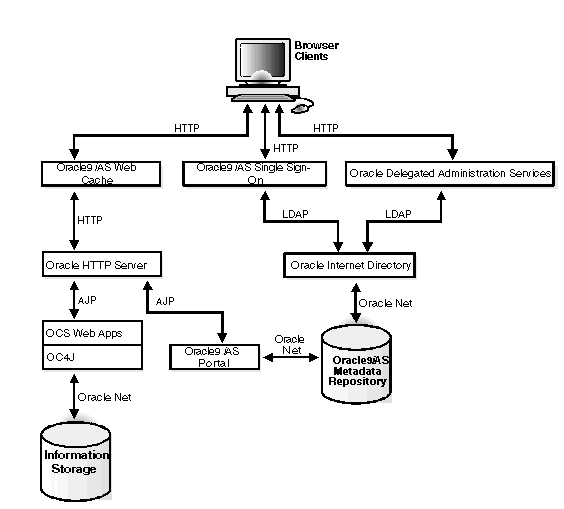
If you select the default options in the Oracle Collaboration Suite Infrastructure installation, none of the components are configured for SSL.
Oracle9i Application Server enables you to selectively configure SSL for the paths that you want to secure. There are many paths used by components, as illustrated in Figure 1-1. You might not want to secure all the paths for the following reasons:
SSL is resource-intensive. If you have heavy SSL traffic, then you should consider offloading SSL processing to an SSL accelerator.
If your computers are behind firewalls, then you might want to secure only those paths that are accessed by the public. For example, you might choose to secure only Web Cache and Oracle HTTP Server if the public can access only these components. This document only provides instructions for this scenario.
Configuring SSL involves changing the default HTTP and HTTPS ports for Web Cache and Oracle HTTP Server. Note that the Port and Listen directives in the httpd.conf configuration file of Oracle HTTP Server can be set to different values depending on your environment.
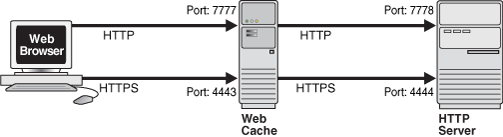
Default Port Layout for Oracle9i Application Server
In the basic port layout for a default Oracle9i Application Server installation, Web Cache runs on HTTP port 7777 (or HTTPS port 4443) and dispatches requests to Oracle HTTP Server HTTP port 7778 (or HTTPS port 4444). This means that the entry point for a browser to reach something on the HTTP Server is 7777 and not 7778. Browser requests are directed to the Web Cache port 7777. The HTTP Server ports are configured with the following directives in the httpd.conf file:
Listen: This directive defines the port on which the HTTP Server listens for incoming connections and receives them. This is the physical HTTP Server port.
Port: This directive defines the port through which the HTTP Server must be accessed. This value is used when the HTTP Server creates redirections to itself, and it is also passed to Web applications so that applications can create links and redirections to themselves by using it. This is the advertising port.
In links and redirections, a browser will never see the port of the HTTP Server. Instead, they are able to access only the port under which the HTTP Server is advertised.
In addition to connecting to port 7777 through HTTP, the browser can also connect to port 4443 through HTTPS. In the latter case, Web Cache dispatches the request to the HTTPS port 4444 of the HTTP Server.
|
Note: SSL is used both between the browser and Web Cache and between Web Cache and the HTTP Server. |
A VirtualHost declaration in the httpd.conf file is used to specify the ports for HTTPS connections. The default configuration is as follows:
<VirtualHost _default_:4444>
Port 4443
Listen 4444
SSLEngine on
</VirtualHost>
The second line, Port 4443, signifies that this port (4444) in the HTTP Server should be accessed through the front-end port of 4443. The HTTP Server generates redirections to itself by naming the Web Cache SSL port. Therefore, in redirections, a browser will not see the SSL port of the HTTP Server, but rather the SSL port under which the HTTP Server is advertised. This is illustrated in the following figure.
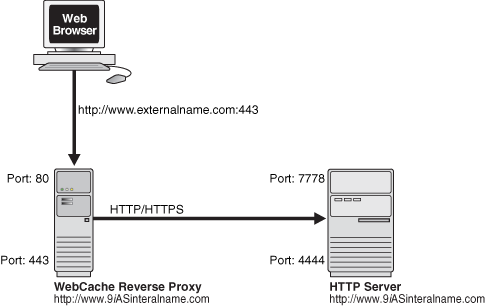
For a distributed installation, you must configure the Middle Tier and the Infrastructure tier to use the standard HTTP and HTTPS ports (80 and 443).
For a single-box installation of Oracle Collaboration Suite, a Web Cache reverse proxy can accept all incoming requests directed to the standard HTTP and HTTPS ports (80 and 443), and redirect them to the internal Oracle Collaboration Suite components running on the nonstandard ports. This is illustrated in the following figure.
To enable SSL communications in Oracle Collaboration Suite, follow these high-level steps:
Ensure that you have a working installation of Oracle Collaboration Suite. For instructions, refer to Oracle Collaboration Suite Installation and Configuration Guide, for your platform. To verify that you have a valid Oracle Collaboration Suite installation, check the list of prerequisites for Oracle Collaboration Suite SSL. See Chapter 2, "Before You Begin".
Obtain certificates for your Oracle Collaboration Suite components, and create a wallet on each computer in your Oracle Collaboration Suite installation that will accept SSL connections. See Chapter 3, "Creating Wallets".
Configure SSL to Oracle9i Application Server Web Cache. See Chapter 4, "Configuring Web Cache for SSL".
Configure SSL to Oracle9iAS Single Sign-On Administration. See Chapter 5, "Configuring SSL for Oracle9iAS Single Sign-On Administration".
Configure the Infrastructure for SSL. See Chapter 6, "Configuring SSL for the Infrastructure".
Configure Oracle HTTP Server and Oracle9iAS Single Sign-On for the Middle Tier Oracle Collaboration Suite components. See Chapter 7, "Configuring SSL for the Middle Tier Applications".
Make configuration changes for Oracle Web Conferencing to work with SSL. See Chapter 8, "Configuring Oracle Web Conferencing for SSL".
Make configuration changes for Oracle Calendar to work with SSL. See Chapter 9, "Configuring Oracle Calendar for SSL".
Troubleshoot your Oracle Collaboration Suite SSL set up. Refer to Appendix A, "Troubleshooting" for solutions to some common problems that you may encounter.