|
Oracle® Application Server Certificate Authority Administrator's Guide
10g Release 2 (10.1.2) B14080-02 |
|
 Previous |
 Next |
|
Oracle® Application Server Certificate Authority Administrator's Guide
10g Release 2 (10.1.2) B14080-02 |
|
 Previous |
 Next |
public key infrastructure (PKI) is designed to enable secure communications over public and private networks. In addition, PKI provides for secure email, digital signatures for non-repudiation, and data integrity, among other things. One of the challenges that PKI has faced over the past 25 years has been an inability to deploy the necessary infrastructure associated with PKI. In fact, the cost and complexity of that infrastructure has been the primary factor limiting widespread use of PKI.
The Oracle Identity Management infrastructure provides an ideal environment for PKI, combining high availability, scalability, directory services, single sign-on, delegated administration service, and directory integration services. These advantages make this infrastructure an ideal place for the Oracle Application Server Certificate Authority to reside. As a result, the OCA is part of the Oracle Identity Management infrastructure, whose centralization and scalability automatically reduce the complexity and cost of deploying PKI.
This chapter takes a closer look at PKI and covers the following topics:
A PKI integrates the following elements:
Encryption algorithms to secure data transmission and storage
Encryption keys to enable unique encryption for different users
Key distribution methods to permit widespread secure use of encryption while preserving secure decryption by only the appropriate recipient
Trusted entities to vouch for the relationship between a key and its legitimate owner
Together these components provide a high level of security for intranet, extranet, and e-commerce applications, as this chapter explains. The benefits include secure and reliable authentication of users, data integrity, non-repudiation of signed messages, and prevention of unauthorized access to transmitted or stored information.
This section examines key features of a PKI in the following topics:
Encryption refers to obscuring data to protect it from unauthorized access or alteration, using some method that nevertheless allows authorized recipients to recover the original data. Techniques for scrambling or substituting for that original data often use a text or number called a key, known only to the sender and recipient. When both use the same key, the encryption scheme is called "symmetric." One difficulty with relying on a symmetric system is how to get that key to both parties without allowing an eavesdropper to get it, too, destroying the desired secrecy. Another problem is that a separate key is needed for every two people, so that each communicator must maintain many keys, one for each recipient.
The heart of a PKI is the use of private/public key pairs, termed "asymmetric" because the public and private keys are different. Each person has only one key pair, regardless of how many others he communicates with.
Each key in a PKI consist of a binary number, typically from 512 to 2048 bits; 512 is considered weak encryption, 1024 is considered very strong encryption, and 2048 is considered military grade. An algorithm combines these key bits with data bits in a way that encrypts the data.
Each key pair owner keeps his private key secret while making his public key available. Others can use the public key to encrypt private messages that they wish to send to the key pair owner. The key pair owner, in turn, uses the private key to decrypt the messages or to sign critical messages he sends out. The efficacy of the system rests on the idea that the public key can be distributed easily and securely while the private key required for decryption is never shared at all.
A certification authority is a trusted third-party that vouches for the public key owner's identity. Oracle Application Server Certificate Authority, the subject of this book, is one such entity. Others include Verisign and Thawte. The certification authority validates the public key's link to a particular person by creating a digital certificate. This digital certificate contains the public key and information about the key holder and the signing certification authority. Using a PKI certificate to authenticate one's identity is analogous to identifying oneself with a driver's license or passport. Such certificates are almost impossible to forge or alter.
This section covers the following topics:
The CA signs the digital certificate with its private key. This signature enables anyone to use the CA's public key to verify that the signature is authentic and that the certificate is therefore valid. Once the certificate is validated, the owner's public key can be used with confidence to encrypt messages to the certificate's owner or to validate the owner's signature on messages.
There can be many levels of CAs. A hierarchy of trust is established when each CA receives its certificate from a more trusted source, that is, a higher-level CA. Each line of trusted links from the root CA through subordinate CA's down to lower level trust points is called a trusted path.
The top-level CA is called the root CA, and is the origin of the trust relationship. CAs below the root CA are called subordinate CAs. All end users sharing the same root CA can communicate with each other in trusted ways because they all trust the same ultimate source of authentication.
Trusting a certificate to legitimately represent prior verification of an identity linked with a public key means trusting the authority that issued the certificate: the CA. CAs in turn often rely on another entity, a registration authority (RA), to validate the information supplied on requests for certificates.
Digital certificates issued by OracleAS Certificate Authority comply with the X.509, Version 3, ISO standard and with RFC 2459, promulgated by the PKIX working group of The Internet Engineering Task Force, http://www.ietf.org/.
The X.509 v3 standard introduced extensions enabling separate certificates for SSL, encryption, and digital signatures. An X.509 v3 certificate contains the following user information:
DN of the certification authority that issued the certificate.
|
Note: For a DN, the DC and EMAIL components must use only printable (ASCII) characters. This restriction means that even in a locale that uses a multibyte character set, the DC and EMAIL components for Distinguished Names must still use ASCII characters. |
Certificate owner's public key
Certificate issuer's digital signature
Dates during which the certificate is valid
Figure 1-1 shows a newly issued certificate that contains all of these elements.
Figure 1-1 A Certificate Issued by OracleAS Certificate Authority
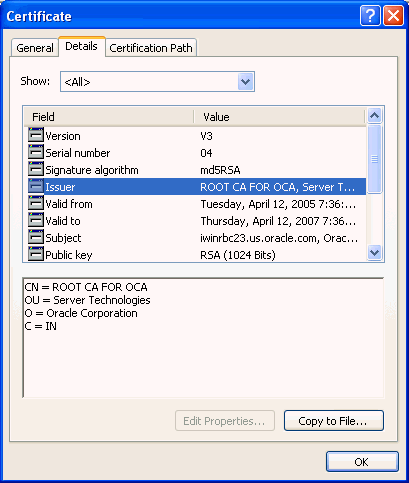
OCA issues and works with X.509 certificates, supporting multiple certificate types, and with X.509 CRLs (certificate revocation lists).
Containers are used to hold the various related credentials used for PKI operations like signing or verifying messages. The data structures in such a container securely store a user's private key, certificate, and a list of root certificates that the user trusts. The trusted certificates are used to verify a peer identity in an SSL connection or to verify a received signature. In browsers such as Netscape or Internet Explorer, the container for certificates can be called a certificate database or certificate cache. In the Oracle Identity Management Infrastructure, such a container is called an Oracle wallet.
A Registration Authority (RA) is an optional system to which a CA delegates certain management functions, such as verification and certification of end-entity identification. It acts as an interface between a CA and the user. The RA receives requests to issue new certificates, to renew expired certificates, and to revoke certificates. The RA evaluates identification supplied by the requestor to verify that the requestor is who it claims to be. For existing certificates, the RA verifies the association of the requestor with the supplied identification and public key and sends the approved request to the CA.
A PKI has the following benefits:
Secure and reliable authentication of users
Reliable authentication relies on two factors. The first factor is proof of possession of the private key part of the public/private pair, which is verified by an automatic procedure that uses the public key. The second factor is validation by a certification authority that a public key belongs to a specific identity. A PKI-based digital certificate validates that identity connection based on the key pair.
Using the private key of an established public/private key pair to sign digital transactions makes it difficult to alter the data in transit. This "digital signature" by the user X is a coded digest of the original message encrypted by X's private key. Recipients can readily use X's corresponding public key to verify that the message has not been altered and that it was in fact sent by X. Any change to the message or the digest would have caused a failure of the attempted verification using the public key, telling the recipient not to trust it.
A digital signature also makes it difficult for the message originator to disown the message.
Prevention of unauthorized access to transmitted or stored information
The time and effort that would be required to derive the private key from the public key makes it unlikely that the message would be decrypted by anyone other than the key pair owner.
This section introduces the OracleAS PKI. It covers the following topics:
Prior to the OracleAS PKI, acquiring a certificate to use for authentication was a process with many steps and delays. You had to acquire the appropriate form, fill it in precisely, and deliver it to the proper registration authority. Once that authority had validated your identity and returned the approved form to you, you then had to deliver it to the certificate authority, which would process this approved form and issue the actual certificate. Delivery often entailed cutting and pasting the approved request's contents into a different form. Once the certificate authority had received this new form, it could take days or weeks to receive the actual certificate.
The OracleAS PKI removes and replaces most of those earlier steps and delays with their inherent costs and difficulties. It tightly integrates the authentication function, the user repository, and applications. It relieves users of the burden of requesting a certificate from a third party and personally submitting it to applications and to a central directory.
Oracle Application Server Certificate Authority, the centerpiece of the OracleAS PKI, provides an easy, one-stop solution, with an easy-to-use Web interface and a Registration Authority (RA) integrated into the CA. The user submits a request online, provides authentication information, and acquires a certificate automatically. This certificate is then automatically linked to the user's entry in Oracle Internet Directory, enabling Single Sign-on to authenticate a user by checking against the corresponding directory entry. Indeed, this Identity Management Infrastructure and OCA are used by many other Oracle components, including the database and Oracle Collaboration Suite.
Once the user is issued a certificate, it can take the place of single sign-on credentials. It thus enables immediate access to all single sign-on applications configured for PKI as well as to those whose authentication requirements are less stringent than PKI. As noted earlier, the user's key pair also enables digital signatures, with their attendant integrity and non-repudiation assurances.
The OracleAS PKI complies with industry-standard specifications, using the following components:
Several international standards define the form and content of a certificate and a container for certificates. As described in "Contents and Uses of a Digital Certificate", the X.509 version 3 standard provides these specifications for certificates. The PKCS#12 (Personal Information Exchange Syntax) standard provides specifications for containers.
Users with standard existing PKI credentials can export them in PKCS#12 format and import (install) them into browsers, such as Netscape Communicator or Microsoft Internet Explorer, or into Oracle Wallet Manager. The PKCS#12 standard thus increases interoperability and reduces the cost of PKI deployment for organizations.
Oracle Wallet Manager facilitates acquiring, using, and storing such certificates. It provides a graphical user interface that standardizes the normal operations done with or to such certificates and their containers, which in OracleAS are termed Oracle wallets.
|
See Also: Oracle Advanced Security Administrator's Guide |
In fact, a server administrator can use OWM to create a PKCS#10 certificate request. After OWM generates the completed request, the administrator can save it to the file system or copy it for pasting into OCA's Server/SubCA form for requesting an OracleAS Certificate Authority certificate. See the last link in the See Also references given earlier.
These wallets conform to the PKCS#12 standard, and are the containers used by OCA. Their interoperability with third-party applications such as Netscape Communicator and Microsoft Internet Explorer provides valuable portability across operating systems.
Secure Sockets Layer (SSL) is the most widely used protocol for securing the Internet. It uses public key cryptography to enable authentication, encryption, and data integrity. Using these tools, SSL also enables secure session key management by encrypting a unique one-time session password for use by both server and client. After this password is securely sent and received, it is used to encrypt all subsequent communications between server and client, making it infeasible for others to decipher those messages. All server components like Oracle HTTP Server, WebCache, Oracle Internet Directory, and the Oracle database use SSL to enable secure communication.
Oracle Internet Directory is an LDAP, Version 3, directory. LDAP stands for Lightweight Directory Access Protocol. This directory enables PKI-based single sign-on by providing the central repository for such authentication credentials, including publishing the certificates issued by OCA. Oracle Internet Directory enforces attribute-level access control, restricting read, write, or update privileges on specific attributes to specific users. It supports the use of SSL to protect and authenticate directory queries and responses.
A new addition to the OracleAS product suite, OracleAS Certificate Authority can be used to administer and manage the entire certificate life-cycle. This life-cycle includes recording and processing requests for new certificates, verifying user credentials, and issuing, renewing, or revoking these certificates. In the past, these processes required separate record-keeping and cut-and-paste operations that were tedious and sometimes error-prone.With OCA, a few clicks generates, submits, and stores a certificate. As a result, credential verification and authentication is simple and fast.
OCA is an optional infrastructure component in Oracle Application Server.