|
Oracle® Application Server Certificate Authority Administrator's Guide
10g Release 2 (10.1.2) B14080-02 |
|
 Previous |
 Next |
|
Oracle® Application Server Certificate Authority Administrator's Guide
10g Release 2 (10.1.2) B14080-02 |
|
 Previous |
 Next |
The Oracle Application Server Certificate Authority administrative web interface covers the following three broad areas, each accessible from a tab on the home page:
Certificate issues, regarding issued certificates; requests for certificate issuance, revocation, or renewal: and certificate revocation lists (CRLs)
Configuration issues, regarding parameters for OracleAS Certificate Authority actions and for implementation of certificate security policies
Viewing logs of OracleAS Certificate Authority activity
This chapter describes the second and third of those areas: configuration management and viewing logs. It contains the following sections:
|
Note: For an overview of certificate configuration issues and the certificate policy statement, read "Certificate Requirements and Policies" in before proceeding. |
The home page of the graphical user interface (GUI) for Oracle Application Server Certificate Authority presents three additional tabs, as the following figure shows:
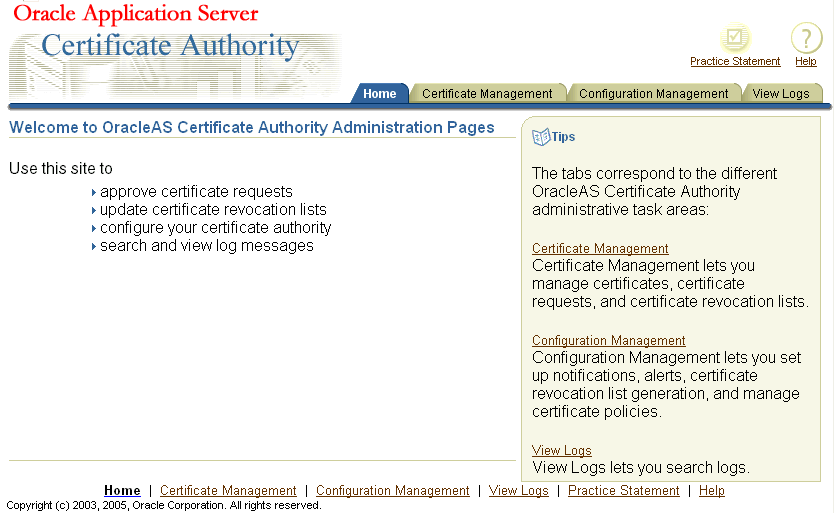
These three subtabs enable you to address specific tasks in managing certificates or configuring the Certificate Authority:
"Certificate Management Tab", described in Chapter 4, particularly in the section entitled "Managing Certificates"
"Configuration Management Tab", described in this chapter
"View Logs Tab", described in this chapter
The Configuration management tab is one of the four choices available when you first enter the OracleAS Certificate Authority web environment. Clicking the Configuration Management tab on the home page displays the first of the three subtabs, each representing a grouping of the OracleAS Certificate Authority configuration management facilities.
The content and use of those subtabs are explained in the following sections:
The "Policy Sub-tab of Oracle Application Server Certificate Authority" and "Policy Actions" are discussed in Chapter 6, "Managing Policies in Oracle Application Server Certificate Authority"
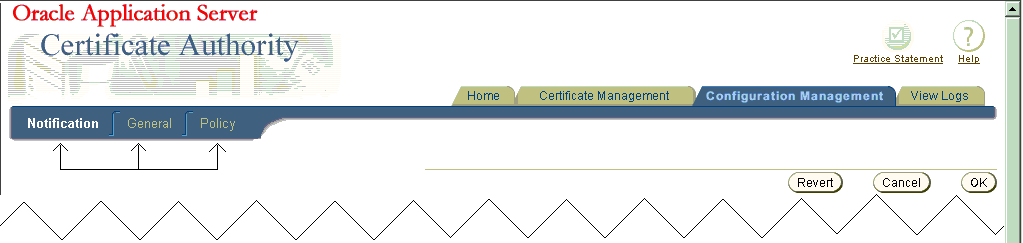
Table 5-1, Table 5-2, and Table 5-3 list the tasks encompassed by the Notification, General, and Policy sub-tabs of Configuration Management and provide links to discussions of those tasks.
Table 5-1 Notification Sub-tab Tasks and Discussions in Configuration Management
| Notification Sub-tab Tasks and Data | Links to Task Discussions |
|---|---|
|
Specify server name and email contacts for alerts and notifications. Specify desired types of alerts. Enable auto-generation of CRLs and specify its start time and the interval between generating CRLs, and the start time and interval for directory synchronizations |
|
Table 5-2 General Sub-tab Tasks and Discussions in Configuration Management
| General Sub-tab Tasks and Data | Links to Task Discussions |
|---|---|
|
Specify that certificate publishing uses SSL or non-SSL communication channel with Oracle Internet Directory. |
|
|
Specify that end-users can use SSL and OracleAS Single Sign-On authentication for certificate management. |
|
|
Specify default usage for client certificates |
|
|
Specify subject alternative name extension |
|
|
Specify logging, tracing, both, or neither. |
|
|
Specify default values for DN components shown in enrollment. |
|
|
See configuration parameters for the database and directory. |
Table 5-3 Policy Sub-tab Tasks and Discussions in Configuration Management
| Policy Sub-tab of Oracle Application Server Certificate Authority Tasks and Data (in Chapter 6) | Links to Task Discussions |
|---|---|
|
See the policies applicable to available operations, such as certificate requests, revocations, or renewals. |
|
|
Edit, enable, disable, delete, add, or reorder policies. |
|
Notification parameters control what events trigger notification emails to the administrator, how those emails are generated, and how often checking is done to reveal such events.
Changes you make to Notification configuration parameters will take effect only after OracleAS Certificate Authority is restarted.
Mail parameters enable email notifications to be sent to the email address you specify for the administrator and to OracleAS Certificate Authority users when appropriate. (Before selecting encrypted (S/MIME) email, you must first create an S/MIME certificate and wallet.) Notification emails use your specified server, sender, and template. You specify your choices in the following portion of the Notification subtab screen:
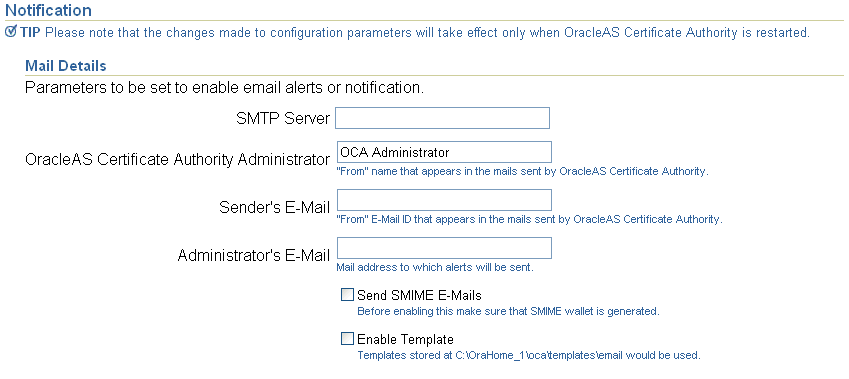
Note that the hint following Enable Template will, after installation, display the exact path to the template directory. For example, if $Oracle_Home is defined during installation as /private/sitename/username, then this hint will display as "Templates stored at /private/sitename/username/oca/templates/email."
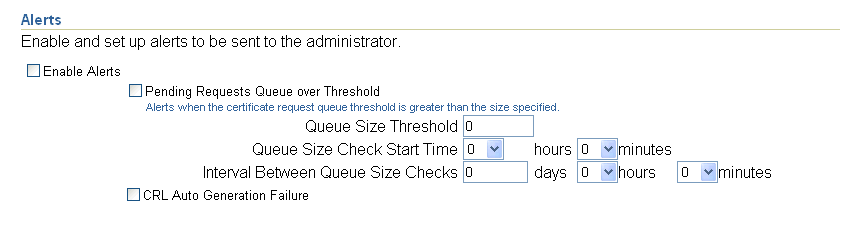
Alerts parameters enable you to specify whether you are to receive alerts in the following circumstances (if you have specified the email information):
When the number of pending certificate requests exceeds the queue threshold you specify here, to be checked on the schedule you specify here (start time and repeat interval). The start time refers to the server's time zone and is specified in a 24-hour format. For example, a start time of 14 hours 30 minutes starts the first check at 2:30 in the afternoon, server time. The interval (default one day) is added to that time to specify the time of the next check; it must be nonzero. Changes survive restarts.
Whenever automatic generation of the CRL fails. Such failure could occur, for example, if the database or Oracle Internet Directory were temporarily unavailable. Other rare possibilities include unpredictable runtime or configuration errors related to memory, I/O, or connectivity issues.
You specify your choices in the following portion of the Notification subtab screen:
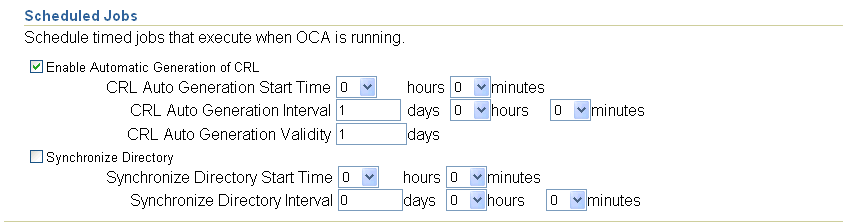
Scheduled Jobs parameters enable you to make the following choices about automatic jobs:
Whether a CRL is to be generated automatically, starting when, and how often thereafter. This feature, enabled by default when OracleAS Certificate Authority is installed, establishes a reliable, timely, and regular process supporting applications that depend on the CRL to detect revoked or expired certificates. The start time refers to the server's time zone and is specified in a 24-hour format. For example, a start time of 14 hours 30 minutes starts the first job at 2:30 in the afternoon, server time. The interval you specify is added to that start time to specify the time of the next CRL generation (default one day); it must be nonzero. Changes survive restarts.
Whether directories are to be synchronized, starting when, and how often thereafter. This feature ensures timely, regular updates to the certificate information in the Oracle Internet Directory. Even certificates issued (or revoked or expired) during any temporary directory downtime will be published (or removed) during synchronization. The start time refers to the server's time zone and is specified in a 24-hour format. For example, a start time of 14 hours 30 minutes starts the first job at 2:30 in the afternoon, server time. The interval you specify (default one day) is added to that start time to specify the time of the next synchronization; it must be nonzero. Changes survive restarts.
You specify your choices in the following portion of the Notification subtab screen:
You can specify and customize the body of e-mail alerts and notifications using templates, which are stored in the following directory:
$ORACLE_HOME/oca/templates/email
|
Note: Templates are turned off by default and must be explicitly enabled. |
You can use tokens to format the e-mail to provide specific information. These tokens are replaced before the e-mail is sent. Table 5-4 lists the notifications, filenames for e-mail format and the supported tokens.
Table 5-4 Tokens for Customizing E-mail
| Notifications | Template File Name | Supported Tokens |
|---|---|---|
|
CertificateRequestNotify |
|
#NAME#, #REQUESTID#, #SUBJECTDN#, #PHONE#, #EMAIL# |
|
RequestApprovalNotify |
|
#NAME#, #REQUESTID#, #SUBJECTDN#, #SERIALNUM#, #OCAURL#, #PHONE#, #EMAIL#, #VALIDITY# |
|
RequestRejectionNotify |
reqrej.txt |
#NAME#, #REQUESTID#, #SUBJECTDN#, #PHONE#, #EMAIL# |
|
PendingRequestsAlert |
|
#NAME#, #NUMBERREQUESTS# |
|
CRLAutoGenFailureAlert |
|
#NAME# |
|
Note: If you do not check the box for Use Template in Configuration Management in the Notification screen, then templates are not used. All alerts and notifications would be predefined text that cannot be changed. |
Table 5-5 describes the values that will replace each of the listed tokens before the alert or notification is sent:
Table 5-5 Supported Token Values
| Notifications and Template File Names | Supported Tokens and the Data to Replace Them |
|---|---|
|
CertificateRequestNotifyTemplate = reqacc.txt |
#NAME#: Replace with the contact data Name specified in the certificate request. #REQUESTID#: Replace with the request ID issued by OracleAS Certificate Authority to this request. #SUBJECTDN#: Replace with the DN in the certificate request. #PHONE#: Replace with the contact data phone number in the certificate request. #EMAIL#: Replace with the contact data email address in the certificate request. |
|
RequestApprovalNotify
Template = reqapp.txt |
#NAME#: Replace with the contact data Name specified in the certificate request. #REQUESTID#: Replace with the request ID issued by OracleAS Certificate Authority to this request. #SUBJECTDN#: Replace with the DN in the certificate request. #SERIALNUM#: Replace with the serial number of the certificate #OCAURL#: Replace with the URL of the user home page #PHONE#: Replace with the contact data phone number in the certificate request. #EMAIL#: Replace with the contact data email address in the certificate request. #VALIDITY#: Replace with the validity period for which the certificate request is approved by the administrator. |
|
RequestRejectionNotify
Template = reqrej.txt |
#NAME#: Replace with the contact data Name in the certificate request. #REQUESTID#: Replace with the request ID issued by OracleAS Certificate Authority to this request. #SUBJECTDN#: Replace with the DN in the certificate request #PHONE#: Replace with the contact data phone number in the certificate request. #EMAIL#: Replace with the contact data email address in the certificate request. |
|
PendingRequestsAlert
Template = pendreq.txt |
#NAME#: Replace with the value specified in the OracleAS Certificate Authority Administrator field under Configuration Management in the Notification screen. #NUMBERREQUESTS#: Replace with the number of pending requests in the OracleAS Certificate Authority repository |
|
CRLAutoGenFailureAlert
Template = crlfail.txt |
#NAME#: Replace with the value specified in the OCA Administrator field under Configuration Management in the Notification screen. |
|
Note: The language in which you edit these templates is used in the final results, so it is best to use the language of the server, because the message body is encoded in the language of the server locale. If you do not use templates, then all alerts and notifications will appear in the language of the server locale. |
This sub-tab enables you to set parameters controlling the following tasks:
Changes you make to General configuration parameters will take effect only after OracleAS Certificate Authority is restarted.
The choices in this section enable you to publish certificates to the directory. Since OracleAS Certificate Authority always connects to Oracle Internet Directory by using the SSL port, the second checkbox shown here is no longer needed ("Protect publication using SSL mode"). The direct Diffie Hellman SSL connection does not require authentication, and OracleAS Certificate Authority then authenticates itself to the directory server by sending its username/password over the now-secured SSL connection.

The choices in this section let you specify that SSL or OracleAS Single Sign-On users can be recognized automatically, meaning that their existing certificates (or OracleAS Single Sign-On authentication) are accepted as authenticating their identities. Enabled by default, such acceptance means OracleAS Certificate Authority will issue them a new certificate without administrator intervention.

The value you choose here appears as the selected usage when a client requests a certificate. This does not prevent the user from selecting a different usage from the drop-down list, which includes authentication, encryption, signing, and combinations of these, plus CA signing, and code signing.

For SSO users, the value chosen for this extension appears in the certificate to enable email encryption, signing, or use by other applications. Your choices are shown in Extension Content Choice.

Choose from None, Email, Principal Name (UID), or Email/Principal Name (UID). The choice made here appears in the certificate as the subject alternate name, enabling email encryption, signing, or use by other applications. (UID means user identifier or unique identifier.) Choosing "Email/Principal Name (UID)" causes both to be listed in the certificate.
If this box is checked, the Subject Alternate Name Extension is required for all SSO-authenticated certificates. If an email address or Principal Name cannot be found in Oracle Internet Directory for the user named in an SSO-authenticated certificate request, that request will be denied. An error message will state that an SSO-authenticated certificate could not be issued because an email account was not found in the Oracle Internet Directory, and that the requestor should contact the administrator.
The choices in this section let you specify whether to create a log file of all user activities, a tracing file of all details for every error, or both.
Logs are stored in the OracleAS Certificate Authority repository; you can view them from the View Logs tab. Trace is stored on the file system, in the file at $ORACLE_HOME/oca/logs/oca.trc.
The values you fill in here will be used to pre-fill some of the Distinguished Name elements on the manual enrollment request form used to submit certificate requests.
This facility is simply for the users' convenience, supplying common fields. The values you fill in here can be overridden as needed.
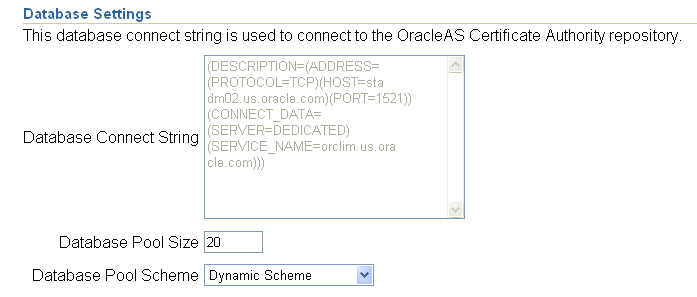
The settings shown here tell you the database connect string, the database pool size, and the database pool scheme. The connect string is the one being used to connect to the OracleAS Certificate Authority repository.
You enter, in the Database Pool Size text box, the number of connections to the database (default: 20) that represents how many users you expect to access OracleAS Certificate Authority concurrently. Specify a number slightly larger than what you expect; for example, if you expect about 25 concurrent users, specify 27 or 28 as the Database Pool Size. When a user in that pool of connections exits OracleAS Certificate Authority, the connection becomes available to the next new user. For each user beyond that number, a new connection will be opened, to be closed as soon as that user has exited OracleAS Certificate Authority.
In Database Pool Scheme, you choose how you want to treat connection requests that come in after all the connections you specified in Database Pool Size are in use. The default, "dynamic," means that a new connection is opened immediately for the new user, and after that user exits OracleAS Certificate Authority, that connection is closed. If you choose "Fixed wait scheme", then after 20 users (or the number you specify) are connected to OracleAS Certificate Authority, every subsequent user attempting to connect simply waits until one of the original 20 users exits. If you choose "Fixed Return Null," then after the original pool size limit is reached, each new user attempting to connect simply gets an error message. No new user can connect until an existing OracleAS Certificate Authority user exits.
The database connect strings only change if OracleAS Certificate Authority's repository moves to a new location (or if a change is made directly to the connection string). Examples include changing the nodes or the port used for connection. In these cases, you can use the ocactl updateconnection command to update the repository connection settings, and then restart OracleAS Certificate Authority to use the new connection information.
|
See Also: |
The settings shown here simply tell you the host, agent, and port being used to connect with Oracle Internet Directory. If a change is made to the connection string, you can use the ocactl updateconnection command to update the repository connection settings, and then restart OracleAS Certificate Authority to use the new connection information.

The View Logs page enables you to view logs that record messages regarding transactions or errors occurring during use of OracleAS Certificate Authority. Such a screen would look like this:
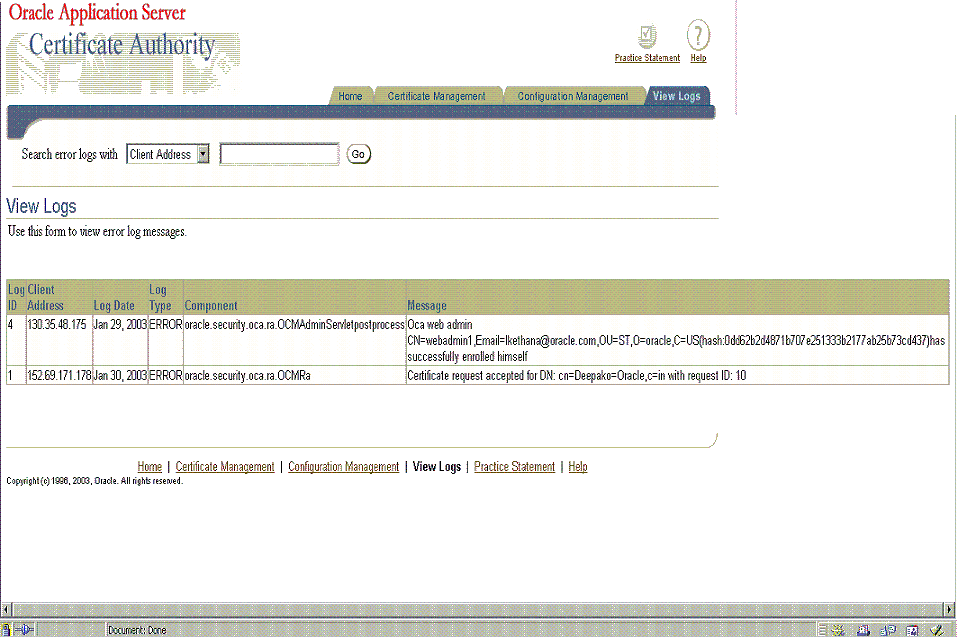
Each line of such a log contains six elements, beginning with a log id number, the IP address that initiated the client activity, and the date of the action. Each line also includes the log entry type, the component of OracleAS Certificate Authority generating the entry, and the component's message about the activity.
These logs can be searched, for example by client (IP) address or message content. The logs enable an administrator to learn where requests originated and what messages were issued for those requests. Searching enables review of specific message types, such as pertaining to rejections, and specific source IP addresses that may have initiated the actions that caused such messages.