| Oracle® Collaboration Suite Security Guide 10g Release 1 (10.1.1) Part Number B14489-02 |
|
|
View PDF |
| Oracle® Collaboration Suite Security Guide 10g Release 1 (10.1.1) Part Number B14489-02 |
|
|
View PDF |
In Oracle Collaboration Suite, components send requests to and receive responses from other components. These components can be Oracle Application Server components, such as OracleAS Single Sign-On, OracleAS Web Cache, or Oracle HTTP Server, or external clients such as browsers. To secure these communications, you can configure Oracle Collaboration Suite to use Secure Sockets Layer (SSL), which is an industry standard for securing communications.
This chapter contains the following sections:
SSL secures communication between two parties: a client and a server. If three or more parties are involved, for example, client browser, Web Cache, Oracle HTTP Server, and OC4J, then you may have to configure all components to use SSL.
Figure 5-1 shows typical communication paths between Oracle Collaboration Suite components and the protocols that they use. For example, browsers use HTTP to communicate with OracleAS Web Cache, and Oracle HTTP Server uses Apache Java Protocol (AJP) to communicate with OC4J. All these protocols can work with SSL.
When you enable SSL for Oracle Collaboration Suite, the HTTP communications depicted in Figure 5-1 will then use the HTTPS protocol for secure connections. URLs that require an SSL connection begin with https rather that http.
Figure 5-1 Communication Paths Between Components in Oracle Collaboration Suite
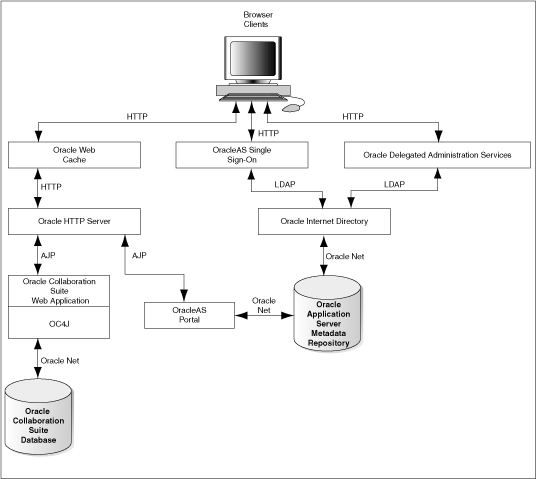
If you select the default options in the Oracle Collaboration Suite Infrastructure installation, none of the components are configured for SSL.
Oracle Collaboration Suite enables you to selectively configure SSL for the paths that you want to secure. There are many paths used by components, as illustrated in Figure 5-1. You might not want to secure all the paths for the following reasons:
SSL is resource-intensive. If you have heavy SSL traffic, then you should consider offloading SSL processing to an SSL accelerator.
If your computers are behind firewalls, then you might want to secure only those paths that are accessed by the public. For example, you might choose to secure only OracleAS Web Cache and Oracle HTTP Server if the public can access only these components. This chapter only provides instructions for this scenario.
To enable SSL communications in Oracle Collaboration Suite, follow these high-level steps:
Ensure that you have a working installation of Oracle Collaboration Suite. To verify that you have a valid Oracle Collaboration Suite installation, check the list of prerequisites for Oracle Collaboration Suite SSL. Refer to Validating Your Installation.
Obtain certificates for your Oracle Collaboration Suite components, and create a wallet on each computer in your Oracle Collaboration Suite installation that will accept SSL connections. Refer to Creating a Complete Wallet: Process Overview.
Configure the Infrastructure for SSL. Refer to SSL Configuration in Oracle Collaboration Suite Infrastructure.
Configure SSL for the Oracle Collaboration Suite Applications tier components. Refer to SSL Configuration in Oracle Collaboration Suite Applications.
Make configuration changes for Oracle Real-Time Collaboration to work with SSL. Refer to Enabling SSL in Oracle Real-Time Collaboration.
Troubleshoot your Oracle Collaboration Suite SSL set up. Refer to Appendix B, "Troubleshooting SSL Configuration" for solutions to some common problems that you may encounter.
Before you begin configuring your Oracle Collaboration Suite installation for SSL, you must first ensure that you have a valid, working installation. It is important that you complete the original installation process without errors. Otherwise, you may not be able to complete the reregistration process necessary for SSL. This section provides some instructions for testing your current Oracle Collaboration Suite installation before beginning the SSL configurations.
Note:
If you are not sure about the ports that were assigned at installation time, then you will find the port assignments for your initial installation in:$ORACLE_HOME/install/portlist.ini
To validate your Oracle Collaboration Suite installation, run the following tests:
Verify that you can log in to OracleAS Single Sign-On Server Administration as the orcladmin user at the following URL:
http://infratierhostname:port/pls/orasso
Verify that you can log in to Oracle Internet Directory Delegated Administration Services as the orcladmin user at the following URL:
http://infratierhostname:port/oiddas
Ensure that you are able to add a new user and log out.
Verify that you can access all configured Oracle Collaboration Suite applications that require OracleAS Single Sign-On at the following URLs:
User URLs
Welcome Page: http://appstierhostname:port/welcome/index.jsp
Oracle Mail URL = http://appstierhostname:port/um
OracleAS Portal URL = http://appstierhostname:port/pls/portal
Oracle Search URL = http://appstierhostname:port/search
Oracle Calendar URL = http://appstierhostname:port/ocas-bin/ocas.fcgi?sub=web
Oracle Discussions URL= http://appstierhostname:port/discussions/app
Oracle Workspaces URL = http://appstierhostname:port/workspaces
Oracle Content Services URL = http://appstierhostname:port/content
Web Access = http://appstierhostname:port/ocsclient
Client Download Page = http://appstierhostname:port/welcome/download.jsp
Oracle Real-Time Collaboration URL = http://appstierhostname:port/imtapp/app/prelogin.uix
Administrator URLs
Enterprise Manager
Infrastructure tier = http://infratierhostname:1156
Applications tier = http://infratierhostname:1156
Oracle Mail = http://appstierhostname:port/um/
Oracle Voicemail & Fax = http://appstierhostname:port/um/
Oracle Calendar: http://appstierhostname:port/ocad-bin/ocad.cgi?object=nodeadm
Oracle Mobile Collaboration: http://appstierhostname:port/webtool/login.uix
Oracle Search: http://appstierhostname:port/search
Oracle Real-Time Collaboration: http://appstierhostname:port/imtapp/app/prelogin.uix
The Distributed Configuration Management utility, dcmctl, provides a command-line alternative to using Oracle Enterprise Manager. Ensure that you can run the dcmctl updateConfig command. Before running dcmctl, you must first shut down Oracle Enterprise Manager (emctl). Run the following commands:
$ORACLE_HOME/bin/emctl stop $ORACLE_HOME/dcm/bin/dcmctl updateConfig -v -d
Correct any problems with your installation before proceeding. After you have confirmed that there are no errors, shut down everything and perform a cold backup.
The requirements described in this section assume that your Oracle Collaboration Suite installation meets the following system requirements:
Oracle Collaboration Suite 10g Release 1 (10.1.1) is installed.
ORACLE_HOME is set to the location that was specified during installation.
PATH environment variable includes the $ORACLE_HOME/bin directory and $ORACLE_HOME/opmn/bin directory. You should update your PATH on both the Infrastructure and Applications tier.
You need a certificate for your site. When clients connect to your site requesting SSL communication, you usually have to send your certificate to them so that they can authenticate you.
Oracle Application Server supports X.509 V3 certificates, and certificates that conform to the PKIX standard (RFC 3280).
You get certificates from certificate authorities (CAs). CAs are trusted entities who sign the certificates that they issue with their private key. Clients can verify the issuer of a certificate (by using the public key of the CA). Examples of CAs include Verisign (http://www.verisign.com) and Thawte (http://www.thawte.com).
Oracle Application Server also has a certificate authority, called OracleAS Certificate Authority (OCA). You can use it to set up your own certificate authority. Refer to the Oracle Application Server Certificate Authority Administrator's Guide for details.
To get a certificate, you submit a certificate request to a CA. The certificate request contains your information including your public key. You can use tools to generate a certificate request. These tools can generate private and public key pairs for you. Examples of tools that can generate certificate requests include Oracle Wallet Manager and Sun's keytool (for OC4J only). For information on Oracle Wallet Manager, see Chapter 6, "Managing Wallets and Certificates".
Among other items, a certificate includes the following pieces of data:
Certificate owner's name
Certificate owner's public key
CA's name
Certificate expiration date
Certificate serial number
Certificates are valid until they expire or until they are revoked.
Note that if you use OracleAS Certificate Authority (OCA) to create certificates for your server, most browsers will not accept these certificates without input from the browser user. This is because most browsers are preconfigured to accept certificates from certain CAs, and OCA is not one of them. The browser will reject the certificate from the server unless the user chooses to accept certificates from the server or import the CA's certificate.
This problem exists for all CAs until the CA's certificate is imported into the browsers. For more information, refer to Oracle Application Server Certificate Authority Administrator's Guide.
For servers to communicate securely with clients, you must obtain an SSL server certificate for each computer and configure its network listener to use that certificate.
In the Oracle environment, use the Oracle Wallet Manager for secure creation and storage of certificates and the corresponding private keys. To obtain a certificate, use the Oracle Wallet Manager as described in the Oracle Advanced Security Administrator's Guide.
The general steps are as follows:
Create a new wallet, if one does not already exist. The same wallet can be used by all servers running on that computer.
Generate a certificate request, entering the host name along with the domain name as the Common Name. Requesting a certificate request generates the corresponding private key and stores it in the wallet.
Send the certificate request to a Certificate Authority, such as VeriSign, for signing.
Store the signed certificate in the wallet with the Auto Login option enabled. The certificate status should be set to Ready.
Remember to store the wallet with the Auto Login option enabled. The option is under the Wallet menu option in the Oracle Wallet Manager. This creates a cwallet.sso file in addition to the wallet.p12 that is the actual wallet. The files are stored in the $ORACLE_HOME/etc/ORACLE/WALLETS/userID directory.
During installation, the listener.ora file is updated with the required SSL and non-SSL listening end points for both the IMAP and POP servers. Administrators only need to set the wallet location in the listener.ora and the sqlnet.ora files, along with any optional SSL parameters, for the listener to receive SSL connections. These settings can be done manually or by using the Oracle Network Manager.
Manually Setting Wallet Location and Client Authentication
Add the following WALLET_LOCATION and SSL_CLIENT_AUTHENTICATION entries to the beginning of the $TNS_ADMIN/listener.ora and $TNS_ADMIN/sqlnet.ora files located on the Oracle Collaboration Suite Applications Tier:
WALLET_LOCATION = (SOURCE = (METHOD = FILE) (METHOD_DATA = (DIRECTORY = Directory_path_containing_the_cwallet.sso_file) ) SSL_CLIENT_AUTHENTICATION = FALSE
A typical directory parameter value looks like the following line:
/etc/ORACLE/WALLETS/userID
If the SSL_CLIENT_AUTHENTICATION parameter is not set, the default setting is TRUE and clients are required to present a certificate during the SSL handshake. If the intent is only to secure the communication, not to authenticate the client using the certificate, set this parameter to FALSE.
An Oracle wallet is a container that stores your credentials, such as certificates, certificate requests, and private keys. You can store Oracle wallets on the file system or in LDAP directories such as Oracle Internet Directory. Oracle wallets are password-protected.
You manage Oracle wallets using Oracle Wallet Manager. Use Oracle Wallet Manager to perform tasks such as creating Oracle wallets, creating certificate requests, importing certificates into the wallet, and uploading wallets to an LDAP directory.
Oracle Wallet Manager supports PKCS #11 and PKCS #12 wallets:
Scenario 1: You generate a certificate request using Oracle Wallet Manager and decide to store the private key on the file system. When you get your certificate from the CA, you can import it into an Oracle wallet. This wallet uses the PKCS #12 format. Refer to Creating a Standard Wallet in Chapter 6, "Managing Wallets and Certificates" for details.
Scenario 2: You generate a certificate request using Oracle Wallet Manager and decide to store the private key on a hardware security module. When you get your certificate from the CA, you can import it into an Oracle wallet. This wallet uses the PKCS #11 format. Refer to Creating a Wallet to Store Hardware Security Module Credentials in Chapter 6, "Managing Wallets and Certificates" for details.
Scenario 3: You already have a certificate in a wallet that uses the PKCS #12 format, and you want to use it with Oracle Application Server. The wallet was created using a third-party tool. In this case, use the tool that was used to create the wallet and export the wallet to a file on the file system. You can then import the wallet. Refer to Importing Certificates Created with a Third-Party Tool in Chapter 6, "Managing Wallets and Certificates" for details.
Components that Use Oracle Wallets
Oracle Application Server components that act as SSL servers need Oracle wallets (the wallet already contains the certificate that you want the server to use). Examples of these components include Oracle HTTP Server, OracleAS Web Cache, OPMN, Oracle Internet Directory, and the Port Tunneling daemon (iaspt).
You configure the component with the location of the Oracle wallet. For example, to configure Oracle HTTP Server for SSL, you specify the location of the wallet using the SSLWallet directive. Refer to the component guide for specific instructions on how to specify the wallet location for the component.
Note:
The OC4J component uses a keystore instead of an Oracle wallet to store its certificate. You use a tool calledkeytool to import certificates into keystores. Refer to the Oracle Application Server Containers for J2EE Security Guide for details on keystores and keytool.If you need to authenticate your clients, you can configure the Oracle HTTP Server to require clients to send their certificates. Clients can also get their certificates from CAs.
If the clients are Oracle components, for example, OracleAS Web Cache can act as a client when communicating with Oracle HTTP Server, the client component can store its certificate in an Oracle wallet. OPMN also acts as a client when configured for SSL.
If the client is a browser, the client does not need an Oracle wallet. You can just import the certificate into the browser.
Other types of clients, such as SOAP or Web Services clients, have their own ways of configuring certificates and certificate stores.
When clients connect to your site using SSL, the extra processing required for SSL strains your servers, and your site as a whole (SSL as well as non-SSL connections) will experience slower performance and throughput. You should consider using SSL accelerator hardware to offload SSL computations and improve performance.
The various SSL accelerators are:
Protocol converters convert HTTPS traffic to HTTP. Protocol converters are standalone hardware computers. Oracle Application Server supports protocol converters from companies such as:
F5 (http://www.f5.com)
Cisco (http://www.cisco.com)
SonicWall (http://www.sonicwall.com)
Note:
SSL connections to protocol converters terminate at the protocol converter. When the converters forward the requests to Oracle Application Server, most of them do so in an unencrypted fashion.For the protocol converters that forward the requests to Oracle Application Server using SSL, this is still faster than not using a protocol converter because using a protocol converter eliminates most SSL key exchanges (which is the expensive operation).
Mathematics accelerators improve the speed of math operations used by SSL. Such devices are usually plugged into a server (often through TCP/IP) and have additional features such as key management and secure key stores.
Oracle Collaboration Suite supports mathematics accelerators that follow the PKCS #11 standard. For a list of certified accelerators, you can check the Oracle Metalink site, http://metalink.oracle.com.