|
Oracle® Application Server Upgrade and Compatibility Guide
10g Release 2 (10.1.2) for UNIX Part No. B14090-02 |
|
 Previous |
 Next |
|
Oracle® Application Server Upgrade and Compatibility Guide
10g Release 2 (10.1.2) for UNIX Part No. B14090-02 |
|
 Previous |
 Next |
This chapter contains the following sections:
Understanding the OracleAS Identity Management Database Requirements
Upgrading OracleAS Identity Management in a Colocated Infrastructure
Upgrading OracleAS Identity Management in a Non-Colocated 10g (9.0.4) Infrastructure
Upgrading Distributed OracleAS Identity Management Configurations
Performing an Oracle Internet Directory Multi-Master Replication Upgrade
Upgrading Oracle Internet Directory Version 9.2.0.x to 10g (10.1.2)
Decommissioning the Release 2 (9.0.2) or 10g (9.0.4) Oracle Home
OracleAS Identity Management is part of the Oracle Application Server Infrastructure. It consists of:
|
See Also: Oracle Application Server Concepts for an overview of the OracleAS InfrastructureOracle Application Server Installation Guide for information about installing OracleAS Identity Management |
Before you upgrade OracleAS Identity Management, you should be familiar with the various configurations that you may have implemented at your site.
The OracleAS Identity Management you want to upgrade will vary depending upon whether you are running Oracle Application Server Release 2 (9.0.2) or Oracle Application Server 10g (9.0.4). The following sections describe the configuration options available for each version of Oracle Application Server:
Oracle Application Server Release 2 (9.0.2) OracleAS Identity Management Configuration Options
Oracle Application Server 10g (9.0.4) OracleAS Identity Management Configuration Options
In Oracle Application Server Release 2 (9.0.2), the components of OracleAS Identity Management are always installed with a OracleAS Metadata Repository. As a result, each Oracle Application Server Release 2 (9.0.2) Infrastructure installations is a colocated Infrastructure.
|
See Also: Section 1.1.2, "Reviewing Your Current OracleAS Infrastructure Configuration" for definitions of colocated and non-colocated OracleAS Infrastructure installations |
However, even though all Release 2 (9.0.2) OracleAS Identity Management installations include an OracleAS Metadata Repository, the Release 2 (9.0.2) Identity Management configuration can still be non-distributed or distributed.
In a non-distributed Release 2 (9.0.2) OracleAS Identity Management installation, Oracle Application Server Single Sign-On and Oracle Internet Directory share a metadata repository, as shown in Figure 5-1.
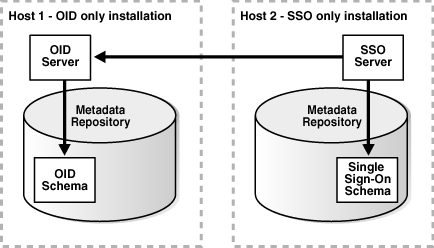
Alternatively, the Release 2 (9.0.2) Identity Management configuration can be distributed, in which Oracle Application Server Single Sign-On and Oracle Internet Directory each use a separate metadata repository. This is depicted in Figure 5-2.
Figure 5-2 Distributed Identity Management in Release 2 (9.0.2)
Oracle Application Server 10g (9.0.4) introduced three OracleAS Infrastructure installation types. These installation types are also available in Oracle Application Server 10g (10.1.2). These installation types allow you to install:
Identity Management and OracleAS Metadata Repository
Identity Management
OracleAS Metadata Repository
Selecting the Identity Management and OracleAS Metadata Repository installation type results in a colocated Infrastructure, where both the OracleAS Metadata Repository and OracleAS Identity Management are in the same Oracle home.
If you install only OracleAS Identity Management, you must provide connection details and logon credentials for a valid OracleAS Metadata Repository.
The option you choose when you install the OracleAS Infrastructure determines whether or not you are installing a colocated Infrastructure or a non-colocated Infrastructure.
|
See Also: Section 1.1.2, "Reviewing Your Current OracleAS Infrastructure Configuration" for more information about colocated Infrastructure and non-colocated Infrastructure installations |
As with Oracle Application Server Release 2 (9.0.2), your 10g (9.0.4) OracleAS Identity Management configuration can be distributed or non-distributed. The 10g (9.0.4) non-distributed configuration is the same as Release 2 (9.0.2) non-distributed OracleAS Identity Management configuration shown in Figure 5-1.
However, in 10g (9.0.4), the OracleAS Identity Management components do not require an OracleAS Metadata Repository in the same Oracle home. Consider the following examples of distributed OracleAS Identity Management installations:
Figure 5-3 shows how the OracleAS Single Sign-On component of OracleAS Identity Management can be installed in a separate 10g (9.0.4) Oracle home from the Oracle Internet Directory, but share the same OracleAS Metadata Repository.
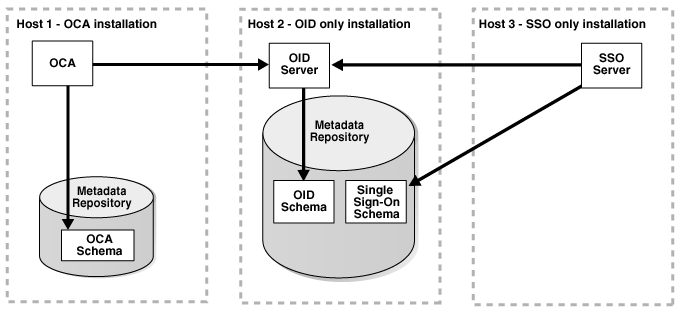
Figure 5-4 shows an extension of the previous example. It introduces a third host, which is used to host an Oracle Application Server Certificate Authority (OCA) installation. The OCA installation uses the same Oracle Internet Directory as OracleAS Single Sign-On, but it has its own OracleAS Metadata Repository to store the OCA schema.
Figure 5-3 Distributed Identity Management in 10g (9.0.4) - Example 1
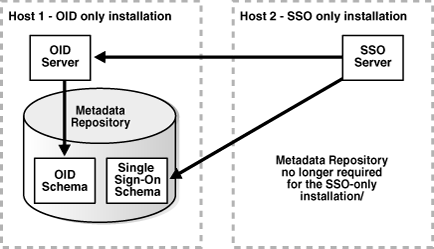
Figure 5-4 Distributed Identity Management in 10g (9.0.4) - Example 2
Oracle Application Server Certificate Authority (OCA) is an OracleAS Identity Management component that was introduced in 10g (9.0.4). It is unique among the OracleAS Identity Management components in that its schemas in the OracleAS Metadata Repository are not upgraded by the OracleAS Identity Management upgrade procedure performed by Oracle Universal Installer.
If you have installed OCA, the OracleAS Identity Management upgrade procedure will copy the OCA file-based configuration files, such as the password store, wallets, and other files from the OCA source Oracle home to the OCA destination Oracle home. This part of the upgrade is similar to other OracleAS Identity Management components.
However, unlike the other OracleAS Identity Management components, the OCA schemas are not upgraded during the OracleAS Identity Management upgrade. Instead, the OCA schemas in the OracleAS Metadata Repository must be upgraded using the Metadata Repository Upgrade Assistant (MRUA).
Regardless of the OracleAS Identity Management configuration, all OracleAS Identity Management installations require access to an OracleAS Metadata Repository. The OracleAS Metadata Repository is required because OracleAS Identity Management depends upon specific schemas that are created in the OracleAS Metadata Repository during the OracleAS Metadata Repository installation.
When you upgrade OracleAS Identity Management, the upgrade procedure upgrades the OracleAS Identity Management schemas in the OracleAS Metadata Repository. However, it can only do so if the database that hosts the OracleAS Metadata Repository is upgraded to a database version supported by Oracle Application Server 10g (10.1.2).
How you upgrade the database depends upon the whether or not the OracleAS Identity Management is part of a colocated or non-colocated Infrastructure.
|
See Also: Section 1.1.2, "Reviewing Your Current OracleAS Infrastructure Configuration" for a definition of colocated and non-colocated Infrastructures |
The following sections provide more details about the database requirements when upgrading OracleAS Identity Management:
Stopping the Database Listener When Prompted During the OracleAS Identity Management Upgrade
Summary of the OracleAS Identity Management Database Upgrade Requirements
If the OracleAS Identity Management you are upgrading is part of a colocated Infrastructure, Oracle Universal Installer automatically upgrades the OracleAS Metadata Repository database to a supported version when you upgrade OracleAS Identity Management.
After you upgrade OracleAS Identity Management in a colocated Infrastructure, refer to the following sections for information about post-upgrade tasks you should consider performing to help you manage and maintain the upgraded database:
Section 6.1.4, "Relocating the Database Datafiles, Control Files, and Log Files"
Section 6.1.5, "Configuring Oracle Enterprise Manager 10g Database Control"
|
Note: After you upgrade Release 2 (9.0.2) OracleAS Identity Management in a colocated Infrastructure, the upgraded database contains invalid objects and represents an unsupported configuration. As a result, you must run the Metadata Repository Upgrade Assistant (MRUA) immediately after the database upgrade.See Chapter 6, "Upgrading the OracleAS Metadata Repository" for more information about running MRUA. See Section 1.8, "Understanding Transitional, Stable, and Unsupported Configurations" for more information about transitional, stable, and unsupported configurations while upgrading to 10g (10.1.2). |
If the OracleAS Identity Management you are upgrading is part of a non-colocated Infrastructure, you must upgrade the OracleAS Metadata Repository first, before upgrading the OracleAS Identity Management installation.
The procedure you use to upgrade the database depends upon whether or not the database is a seed database or a OracleAS Metadata Repository Creation Assistant database.
Consider the following when upgrading a OracleAS Metadata Repository database in a non-colocated Infrastructure:
If the OracleAS Metadata Repository was installed in a seed database, as part of a 10g (9.0.4) OracleAS Metadata Repository installation, you can use Oracle Universal Installer to upgrade the database automatically.
On the other hand, if you used the OracleAS Metadata Repository Creation Assistant to create the OracleAS Metadata Repository, you must upgrade the database manually, using the standard Oracle database upgrade procedures.
Depending upon the OracleAS Identity Management configuration you are upgrading, you might be prompted to stop the database listener during the OracleAS Identity Management upgrade. If such a prompt appears, you can use the lsnrctl utility to stop the database listener as follows:
Set the ORACLE_HOME environment variable to the Oracle home of the listener you want to stop.
Verify the version of the listener you are about to stop by entering the following command:
$ORACLE_HOME/bin/lsnrctl version
The lsnrctl utility displays information about the current database listener. Review the information to verify that you are stopping the correct listener.
Stop the listener by entering the following command:
$ORACLE_HOME/bin/lsnrctl stop
In summary, before you upgrade OracleAS Identity Management, the database that hosts the OracleAS Identity Management schemas must be one of the following supported versions:
Oracle Database 10g (10.1.0.3.1)
This is the version of the database that Oracle Universal Installer creates and configures when you install a new 10g (10.1.2) OracleAS Metadata Repository using the Identity Management and OracleAS Metadata Repository installation type or the OracleAS Metadata Repository installation type.
Similarly, this is the version of the database that results when you use Oracle Universal Installer to upgrade a seed database in a colocated Infrastructure or non-colocated Infrastructure Oracle home.
You must upgrade your database to this version and apply patch 4015165 if you used the OracleAS Metadata Repository Creation Assistant to install the OracleAS Metadata Repository.
Before you begin upgrading your OracleAS Identity Management installation, perform a backup of the OracleAS Identity Management Oracle home, and perform a backup of the database that hosts the OracleAS Identity Management schemas.
If OracleAS Identity Management is installed as part of a colocated Infrastructure, you can use Oracle Universal Installer to do all of the following as part of the Oracle Application Server 10g (10.1.2) installation procedure:
Upgrade the OracleAS Metadata Repository database.
Upgrade the OracleAS Identity Management program, configuration, and data files.
Upgrade the OracleAS Identity Management schemas in the OracleAS Metadata Repository.
To upgrade OracleAS Identity Management in a colocated Infrastructure Oracle home:
If you are upgrading from Release 2 (9.0.2), make sure you have applied the latest Release 2 (9.0.2) patchsets.
The OracleAS Identity Management upgrade procedures have been tested using the latest patchsets available from OracleMetaLink. Therefore, before you upgrade Release 2 (9.0.2) OracleAS Identity Management, apply the latest Oracle Application Server 9.0.2 patchsets.
The OracleMetaLink Web site is at the following URL:
http://metalink.oracle.com/
At the time this document was published the most recent Oracle9iAS patchset release was the Oracle9iAS 9.0.2.3 patchset (3038037). To locate this patchset, search for patch number 3038037 on OracleMetaLink.
|
Note: After applying Oracle9iAS 9.0.2.3 patchset (3038037), verify that the patchset was applied successfully before proceeding with the 10g (10.1.2) upgrade. For example, verify that the Application Server Control, your deployed applications, and the components you use are functioning properly after you apply the patchset. |
Stop all the middle tiers that are using the services of the OracleAS Identity Management installation.
Make sure that the OracleAS Metadata Repository database and database listener are up and running.
Log in to the computer on which Release 2 (9.0.2) or 10g (9.0.4) instance is installed, as the same operating system user that performed the Release 2 (9.0.2) or 10g (9.0.4) installation.
Make sure the Oracle Internet Directory server is up and running.
To verify that Oracle Internet Directory is running, enter one of the following commands.
|
Note: You may have to temporarily set the ORACLE_HOME environment variable to the Oracle Internet Directory Oracle home before running theldapbind command.
After you verify that the Oracle Internet Directory is running, you must then make sure the ORACLE_HOME environment variable is not defined before you start the 10g (10.1.2) installer, as directed in Step 6. |
If you are running Oracle Internet Directory on a non-secure port:
SOURCE_ORACLE_HOME/bin/ldapbind -p Non-SSL_port
If you are running Oracle Internet Directory on a secure port:
SOURCE_ORACLE_HOME/bin/ldapbind -p SSL_port -U 1
These commands should return a "bind successful" message.
|
See Also: "Syntax for LDIF and Command-Line Tools" in the Oracle Internet Directory Administrator's Guide for more information about theldapbind utility
|
Set the required environment variables, as defined in the section "Environment Variables" in the "Requirements" chapter of the Oracle Application Server Installation Guide.
In particular, be sure to set following variables so they do not reference any Oracle home directories:
In addition, be sure the following environment variables are not set:
Mount the CD-ROM and start the installer.
|
See Also: Oracle Application Server Installation Guide for detailed instructions about starting Oracle Universal Installer on your platform |
Refer to Table 5-1 for information on the options you should select on each screen.
After the End of Installation screen appears, exit Oracle Universal Installer and then verify that Oracle Internet Directory and Oracle Application Server Single Sign-On are functioning and accessible in the new 10g (10.1.2) Oracle home.
|
See Also: Oracle Application Server Administrator's Guide, Chapter 1, "Accessing the Single Sign-On Server" |
If you are upgrading from Release 2 (9.0.2), immediately run the Metadata Repository Upgrade Assistant (MRUA) to upgrade the OracleAS Metadata Repository component schemas.
After you upgrade Release 2 (9.0.2) OracleAS Identity Management in a colocated Infrastructure, the upgraded database contains invalid objects and represents an unsupported configuration. As a result, you must run the Metadata Repository Upgrade Assistant (MRUA) immediately after the database upgrade.
|
See Also: Chapter 6, "Upgrading the OracleAS Metadata Repository" for more information about running MRUA.Section 1.8, "Understanding Transitional, Stable, and Unsupported Configurations" for more information about transitional, stable, and unsupported configurations while upgrading to 10g (10.1.2). |
If you are upgrading from 10g (9.0.4) and you have installed and configured Oracle Application Server Certificate Authority (OCA), run MRUA to upgrade the OCA schemas in the OracleAS Metadata Repository.
OCA is an OracleAS Identity Management component, but its schema is not upgraded by the OracleAS Identity Management upgrade process.
Table 5-1 Summary of the Oracle Universal Installer Screens During the OracleAS Identity Management Upgrade in a Colocated infrastructure
| Screen | Description and Recommended Options to Select |
|---|---|
| Welcome | Welcomes you to Oracle Universal Installer and the Oracle Application Server 10g (10.1.2) installation procedure. |
| Specify File Locations | Enter a name and path for the new Oracle home.
This new Oracle home will be the destination Oracle home for your Oracle Application Server 10g (10.1.2) upgrade. |
| Select a Product to Install | Select OracleAS Infrastructure 10g.
If multiple languages are used in the OracleAS Infrastructure you are upgrading, then click Product Languages. |
| Language Selection | The screen appears only if you clicked Product Languages on the Select a Product to Install screen.
If multiple languages are used in the OracleAS Infrastructure you are upgrading, select those languages. If you are not sure which languages were installed, but want languages other than English, click the double arrow button (>>) to select all languages. |
| Select Installation Type | Select Identity Management and OracleAS Metadata Repository.
Note: It is very important that you select the same installation type that is used in the Oracle home you are upgrading. |
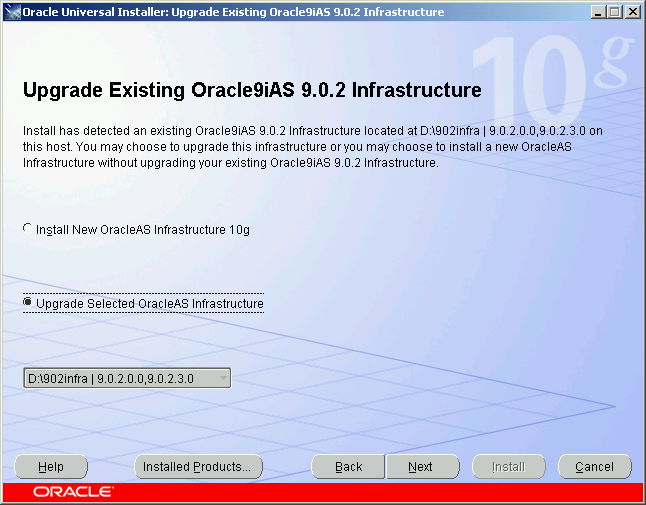
| Upgrade Existing Infrastructure | This screen (Figure 5-5) appears when Oracle Universal Installer detects an existing Oracle Application Server installation of the same type as the one you selected on the Select Installation Type screen.
Select the option to upgrade an existing OracleAS Infrastructure, and then select the Oracle home you want to upgrade from the drop-down list. (If there is only one Infrastructure of the selected time on the computer, then the drop-down list is inactive.) |
| Specify OID Login | Enter the Oracle Internet Directory superuser distinguished name (DN) in the Username field. The superuser DN cn=orcladmin is the default for this field; change this value if the Oracle Internet Directory superuser DN is not cn=orcladmin.
Enter the password for the superuser DN in the Password field. |
| Specify Infrastructure Database Connection Information | Enter SYS in the Username field and the SYS user's password in the Password field.
|
| Warning dialog box | This dialog box warns you that all the clients of the OracleAS Metadata Repository database must now be stopped. Oracle Universal Installer will automatically stop any clients within the source Oracle home.Foot 1
However, you must manually stop any database clients and OracleAS Metadata Repository clients that reside in another Oracle home. Clients of the OracleAS Metadata Repository include:
Within each middle tier that uses this OracleAS Metadata Repository, you must be sure to stop all components, including Oracle HTTP Server and OracleAS Web Cache. For more information, see the chapter "Starting and Stopping " in the Oracle Application Server Administrator's Guide. |
| Database Listener Warning Dialog Box | If a database listener is running on the host, a warning dialog box displays. Review the dialog box determine whether or not you need to stop the listener manually.
For more information, see Section 5.3.3, "Stopping the Database Listener When Prompted During the OracleAS Identity Management Upgrade". |
| Specify Instance Name and ias_admin Password | Enter a name for the new Oracle Application Server 10g (10.1.2) instance and a password for the ias_admin Administrator account.
You use the In general, the minimum length of the For more information, see the section "The ias_admin User and Restrictions on its Password" in the Oracle Application Server Installation Guide. |
| Summary | Use this screen to confirm the choices you've made. Click Install to begin upgrading to the new 10g (10.1.2) Oracle home.
A dialog box appears when the copying is complete. This dialog box prompts you to run a configuration script as the root user. Follow the instructions in the dialog box and click OK when the script is finished. |
| The Configuration Assistants | After the initial software is installed, a set of configuration assistants automatically set up the components in the new 10g (10.1.2) Oracle home. Use this screen to follow the progress of each assistant and to identify any problems during this phase of the installation.
Notes:
|
| End of Installation | When the installation and upgrade is complete, this screen provides important details about the 10g (10.1.2) Oracle home, such as the URL for the Application Server Control Console and the location of the setupinfo.txt file.
After you review the information on this screen, you can exit Oracle Universal Installer and proceed to the post-upgrade tasks. |
shutdownprocesses.log file, which is located in the cfgtoollogs directory in the destination Oracle home.Figure 5-5 Upgrade Existing OracleAS Infrastructure Screen
To upgrade OracleAS Identity Management in a non-colocated Infrastructure, you use Oracle Universal Installer just as you do when OracleAS Identity Management is in a colocated Infrastructure.
This section applies only to 10g (9.0.4) OracleAS Identity Management upgrades; Release 2 (9.0.2) did not support non-colocated Infrastructure installations.
Before you can upgrade OracleAS Identity Management in a non-colocated Infrastructure, you must verify that the OracleAS Metadata Repository that hosts the OracleAS Identity Management schemas is running in a supported version of the Oracle database.
If the OracleAS Metadata Repository is not hosted by a supported database version, you must upgrade the database. The method you use to upgrade the OracleAS Metadata Repository database varies, depending upon whether the database is a seed database or a OracleAS Metadata Repository Creation Assistant database.
After you determine whether or not the database is a seed database or an OracleAS Metadata Repository Creation Assistant database, you can upgrade the database by following the instructions for upgrading the OracleAS Metadata Repository database.
To upgrade OracleAS Identity Management in a non-colocated Infrastructure:
Verify that the version of the database that hosts the OracleAS Identity Management schemas is a supported version for 10g (10.1.2) OracleAS Identity Management.
The OracleAS Identity Management schemas are stored in an OracleAS Metadata Repository.
If necessary, upgrade the database by using the instructions in Section 6.1, "Upgrading the Database That Hosts the OracleAS Metadata Repository".
Make sure that the OracleAS Metadata Repository database and database listener are up and running.
Log in to the computer on which the 10g (9.0.4) instance is installed, as the same operating system user that performed the 10g (9.0.4) installation.
Make sure the Oracle Internet Directory server is up and running.
To verify that Oracle Internet Directory is running, enter one of the following commands.
|
Note: You may have to temporarily set the ORACLE_HOME environment variable to the Oracle Internet Directory Oracle home before running theldapbind command.
After you verify that the Oracle Internet Directory is running, you must then make sure the ORACLE_HOME environment variable is not defined before you start the 10g (10.1.2) installer, as directed in Step 6. |
If you are running Oracle Internet Directory on a non-secure port:
SOURCE_ORACLE_HOME/bin/ldapbind -p Non-SSL_port
If you are running Oracle Internet Directory on a secure port:
SOURCE_ORACLE_HOME/bin/ldapbind -p SSL_port -U 1
These commands should return a "bind successful" message.
|
See Also: "Syntax for LDIF and Command-Line Tools" in the Oracle Internet Directory Administrator's Guide for more information about theldapbind utility
|
Be sure to set the environment variables, as defined in the section "Environment Variables" in the "Requirements" chapter of the Oracle Application Server Installation Guide.
In particular, be sure to set following variables so they do not reference any Oracle home directories:
PATH
CLASSPATH
LD_LIBRARY_PATH
SHLIB_PATH
In addition, be sure the following environment variables are not set:
TNS_ADMIN
ORACLE_HOME
ORACLE_SID
Mount the Oracle Application Server 10g (10.1.2) CD–ROM and start the installer.
|
See Also: Oracle Application Server Installation Guide for detailed instructions about starting Oracle Universal Installer on your platform |
Refer to Table 5-2 for information on the options you should select on each screen.
After the End of Installation screen appears, exit Oracle Universal Installer and then verify that Oracle Internet Directory and Oracle Application Server Single Sign-On are functioning and accessible in the new 10g (10.1.2) Oracle home.
|
See Also: Oracle Application Server Administrator's Guide, Chapter 1, "Accessing the Single Sign-On Server" |
If you have installed and configured Oracle Application Server Certificate Authority, you must then run the Metadata Repository Upgrade Assistant to upgrade the OCA schema in the OracleAS Metadata Repository.
OCA is an OracleAS Identity Management component, but its schema is not upgraded by the OracleAS Identity Management upgrade process.
Table 5-2 Summary of the Oracle Universal Installer Screens During the OracleAS Identity Management Upgrade in a 10g (9.0.4) Non-Colocated infrastructure
| Screen | Description and Recommended Options to Select |
|---|---|
| Welcome | Welcomes you to Oracle Universal Installer and the Oracle Application Server 10g (10.1.2) installation procedure. |
| Specify File Locations | Enter a name and path for the new Oracle home.
This new Oracle home will be the destination Oracle home for your Oracle Application Server 10g (10.1.2) upgrade. |
| Select a Product to Install | Select OracleAS Infrastructure 10g.
If multiple languages are used in the OracleAS Infrastructure you are upgrading, then click Product Languages. |
| Language Selection | The screen appears only if you clicked Product Languages on the Select a Product to Install screen.
If multiple languages are used in the OracleAS Infrastructure you are upgrading, select those languages. If you are not sure which languages were installed, but want languages other than English, click the double arrow button (>>) to select all languages. |
| Select Installation Type | Select Identity Management.
Note: It is very important that you select the same installation type that is used in the Oracle home you are upgrading. |
| Upgrade Existing Infrastructure | This screen (Figure 5-5) appears when Oracle Universal Installer detects an existing Oracle Application Server installation of the same type as the one you selected on the Select Installation Type screen.
Select the option to upgrade an existing OracleAS Infrastructure, and then select the Oracle home you want to upgrade from the drop-down list. (If there is only one Infrastructure of the selected time on the computer, then the drop-down list is inactive.) |
| Specify OID Login | Enter the Oracle Internet Directory superuser distinguished name (DN) in the Username field. The superuser DN cn=orcladmin is the default for this field; change this value if the Oracle Internet Directory superuser DN is not cn=orcladmin.
Enter the password for the superuser DN in the Password field. |
| Specify Infrastructure Database Connection Information | Enter SYS in the Username field and the SYS user's password in the Password field.
|
| Warning dialog box | This dialog box warns you that all the clients of the OracleAS Identity Management installation must now be stopped. Oracle Universal Installer will automatically stop any clients within the source Oracle home automatically.Foot 1
However, you must manually stop any OracleAS Identity Management clients that reside in another Oracle home Clients of an OracleAS Identity Management instance include:
Within each middle tier that uses this OracleAS Identity Management instance, you must be sure to stop all components, including Oracle HTTP Server and OracleAS Web Cache. For more information, see the chapter "Starting and Stopping " in the Oracle Application Server Administrator's Guide. |
| Database Listener Warning Dialog Box | If a database listener is running on the host, a warning dialog box displays. Review the dialog box determine whether or not you need to stop the listener manually.
For more information, see Section 5.3.3, "Stopping the Database Listener When Prompted During the OracleAS Identity Management Upgrade". |
| Specify Instance Name and ias_admin Password | Enter a name for the new Oracle Application Server 10g (10.1.2) instance and a password for the ias_admin Administrator account.
You use the In general, the minimum length of the For more information, see the section "The ias_admin User and Restrictions on its Password" in the Oracle Application Server Installation Guide. |
| Summary | Use this screen to confirm the choices you've made. Click Install to begin upgrading to the new 10g (10.1.2) Oracle home. The install screen shows you the progress of the installation as it copies files to your local disk.
On UNIX systems, a dialog box appears when the copying is complete. This dialog box prompts you to run a configuration script as the root user. Follow the instructions in the dialog box and click OK when the script is finished. |
| The Configuration Assistants | After the initial software is installed, a set of configuration assistants automatically set up the components in the new 10g (10.1.2) Oracle home. Use this screen to follow the progress of each assistant and to identify any problems during this phase of the installation. |
| End of Installation | When the installation and upgrade is complete, this screen provides important details about the 10g (10.1.2) Oracle home, such as the URL for the Application Server Control Console and the location of the setupinfo.txt file.
After you review the information on this screen, you can exit Oracle Universal Installer and proceed to the post-upgrade tasks. |
shutdownprocesses.log file, which is located in the cfgtoollogs directory in the destination Oracle home.The following sections describe how to upgrade a distributed OracleAS Identity Management configuration:
Upgrading Release 2 (9.0.2) Distributed OracleAS Identity Management Configurations
Upgrading 10g (9.0.4) Distributed OracleAS Identity Management Configurations
Verifying Whether OracleAS Identity Management Components are Enabled or Disabled
Enabling Secure Sockets Layer (SSL) for Distributed OracleAS Identity Management Components
A distributed OracleAS Identity Management configuration consists of multiple Oracle homes. One of the Oracle homes contains the Oracle Internet Directory.
In a Release 2 (9.0.2) distributed OracleAS Identity Management installation, the other Oracle home contains OracleAS Single Sign-On and its own OracleAS Metadata Repository (Figure 5-2).
To upgrade a Release 2 (9.0.2) distributed OracleAS Identity Management configuration:
Review Section 5.7.3, "Verifying Whether OracleAS Identity Management Components are Enabled or Disabled" to determine exactly which OracleAS Identity Management components will be upgraded.
Use the procedure in Section 5.5, "Upgrading OracleAS Identity Management in a Colocated Infrastructure" to upgrade the Oracle home that includes the Oracle Internet Directory and its OracleAS Metadata Repository.
You must upgrade the Oracle Internet Directory first before upgrading the other distributed OracleAS Identity Management components.
|
Note: If you are running only Oracle Internet Directory from the Oracle home, check to be sure the other OracleAS Identity Management components are disabled so they will not be upgraded or started in the destination 10g (10.1.2) Oracle home.For more information, see Section 5.7.3, "Verifying Whether OracleAS Identity Management Components are Enabled or Disabled". |
Make sure you have applied the latest Release 2 (9.0.2) patchsets to the OracleAS Identity Management Oracle home you are about to upgrade.
The OracleAS Identity Management upgrade procedures have been tested using the latest patchsets available from OracleMetaLink. As a result, before you upgrade Release 2 (9.0.2) OracleAS Identity Management, apply the latest Oracle Application Server 9.0.2 patchsets.
The OracleMetaLink Web site is at the following URL:
http://metalink.oracle.com/
At the time this document was published the most recent Oracle9iAS patchset release was the Oracle9iAS 9.0.2.3 patchset (3038037). To locate this patchset, search for patch number 3038037 on OracleMetaLink.
|
Note: After applying Oracle9iAS 9.0.2.3 patchset (3038037), verify that the patchset was applied successfully before proceeding with the 10g (10.1.2) upgrade. For example, verify that the Application Server Control, your deployed applications, and the components you use are functioning properly after you apply the patchset. |
Make sure that the OracleAS Metadata Repository database being used by Oracle Application Server Single Sign-On and its database listener are up and running.
Log in to the computer on which the other distributed OracleAS Identity Management components are installed, as the same operating system user that performed the Release 2 (9.0.2) installation.
Make sure the Oracle Internet Directory Server has been upgraded to 10g (10.1.2) and that it is up and running.
To verify that Oracle Internet Directory is running, enter one of the following commands.
|
Note: You may have to temporarily set the ORACLE_HOME environment variable to the Oracle Internet Directory Oracle home before running theldapbind command.
After you verify that the Oracle Internet Directory is running, you must then make sure the ORACLE_HOME environment variable is not defined before you start the 10g (10.1.2) installer, as directed in Step 6. |
If you are running Oracle Internet Directory on a non-secure port:
SOURCE_ORACLE_HOME/bin/ldapbind -p Non-SSL_port
If you are running Oracle Internet Directory on a secure port:
SOURCE_ORACLE_HOME/bin/ldapbind -p SSL_port -U 1
These commands should return a "bind successful" message.
|
See Also: "Syntax for LDIF and Command-Line Tools" in the Oracle Internet Directory Administrator's Guide for more information about theldapbind utility
|
Be sure to set the environment variables, as defined in the section "Environment Variables" in the "Requirements" chapter of the Oracle Application Server Installation Guide.
In particular, be sure to set following variables so they do not reference any Oracle home directories:
In addition, be sure the following environment variables are not set:
Mount the Oracle Application Server 10g (10.1.2) CD–ROM and start the installer.
|
See Also: Oracle Application Server Installation Guide for detailed instructions about starting Oracle Universal Installer on your platform |
Refer to Table 5-3 for information on the options you should select on each screen.
After the End of Installation screen appears, exit Oracle Universal Installer and then verify that Oracle Internet Directory and Oracle Application Server Single Sign-On are functioning and accessible in the new 10g (10.1.2) Oracle home.
|
See Also: "Accessing the Single Sign-On Server" in the Oracle Application Server Single Sign-On Administrator's Guide |
Table 5-3 Summary of the Oracle Universal Installer Screens During a Release 2 (9.0.2) Distributed OracleAS Identity Management Upgrade
| Screen | Description and Recommended Options to Select |
|---|---|
| Welcome | Welcomes you to Oracle Universal Installer and the Oracle Application Server 10g (10.1.2) installation procedure. |
| Specify File Locations | Enter a name and path for the new Oracle home.
This new Oracle home will be the destination Oracle home for your Oracle Application Server 10g (10.1.2) upgrade. |
| Select a Product to Install | Select OracleAS Infrastructure 10g.
If multiple languages are used in the OracleAS Infrastructure you are upgrading, then click Product Languages. |
| Language Selection | The screen appears only if you clicked Product Languages on the Select a Product to Install screen.
If multiple languages are used in the OracleAS Infrastructure you are upgrading, select those languages. If you are not sure which languages were installed, but want languages other than English, click the double arrow button (>>) to select all languages. |
| Select Installation Type | Select Identity Management and OracleAS Metadata Repository.
Note: It is very important that you select the same installation type that is used in the Oracle home you are upgrading. In this case, the Release 2 (9.0.2) OracleAS Single Sign-On installation includes its own OracleAS Metadata Repository, so you must select the colocated OracleAS Identity Management and OracleAS Metadata Repository installation type. |
| Upgrade Existing Infrastructure | This screen (Figure 5-5) appears when Oracle Universal Installer detects an existing Oracle Application Server installation of the same type as the one you selected on the Select Installation Type screen.
Select the option to upgrade an existing OracleAS Infrastructure, and then select the Oracle home you want to upgrade from the drop-down list. (If there is only one Infrastructure of the selected time on the computer, then the drop-down list is inactive.) |
| Specify OID Login | Enter the Oracle Internet Directory superuser distinguished name (DN) in the Username field. The superuser DN cn=orcladmin is the default for this field; change this value if the Oracle Internet Directory superuser DN is not cn=orcladmin.
Enter the password for the superuser DN in the Password field. |
| Specify Infrastructure Database Connection Information | Enter SYS in the Username field and the SYS user's password in the Password field.
These are the login credentials for the database installed in the OracleAS Single Sign-On Oracle home. See Figure 5-2, "Distributed Identity Management in Release 2 (9.0.2)". |
| Specify OID Database Login | Enter SYS in the Username field and the SYS user's password for the Oracle Internet Directory database in the Password field.
These are login credentials for the database where Oracle Internet Directory has been installed. See Figure 5-2, "Distributed Identity Management in Release 2 (9.0.2)". |
| Warning dialog box | This dialog box warns you that all the clients of the OracleAS Identity Management installation must now be stopped. Oracle Universal Installer will automatically stop any clients within the source Oracle home automatically.Foot 1
However, you must manually stop any OracleAS Identity Management clients that reside in another Oracle home Clients of an OracleAS Identity Management instance include:
Within each middle tier that uses this OracleAS Identity Management instance, you must be sure to stop all components, including Oracle HTTP Server and OracleAS Web Cache. For more information, see the chapter "Starting and Stopping " in the Oracle Application Server Administrator's Guide. |
| Database Listener Warning Dialog Box | If a database listener is running on the host, a warning dialog box displays. Review the dialog box determine whether or not you need to stop the listener manually.
For more information, see Section 5.3.3, "Stopping the Database Listener When Prompted During the OracleAS Identity Management Upgrade". |
| Specify Instance Name and ias_admin Password | Enter a name for the new Oracle Application Server 10g (10.1.2) instance and a password for the ias_admin Administrator account.
You use the In general, the minimum length of the For more information, see the section "The ias_admin User and Restrictions on its Password" in the Oracle Application Server Installation Guide. |
| Summary | Use this screen to confirm the choices you've made. Click Install to begin upgrading to the new 10g (10.1.2) Oracle home.
On UNIX systems, a dialog box appears when the copying is complete. This dialog box prompts you to run a configuration script as the root user. Follow the instructions in the dialog box and click OK when the script is finished. |
| The Configuration Assistants | After the initial software is installed, a set of configuration assistants automatically set up the components in the new 10g (10.1.2) Oracle home. Use this screen to follow the progress of each assistant and to identify any problems during this phase of the installation.
Notes:
|
| End of Installation | When the installation and upgrade is complete, this screen provides important details about the 10g (10.1.2) Oracle home, such as the URL for the Application Server Control Console and the location of the setupinfo.txt file.
After you review the information on this screen, you can exit Oracle Universal Installer and proceed to the post-upgrade tasks. |
shutdownprocesses.log file, which is located in the cfgtoollogs directory in the destination Oracle home.A distributed OracleAS Identity Management configuration consists of multiple Oracle homes. One of the Oracle homes contains the Oracle Internet Directory.
In a 10g (9.0.4) distributed OracleAS Identity Management installation, the other Oracle homes contain additional OracleAS Identity Management components, such as OracleAS Single Sign-On, Delegated Administration Services, Oracle Directory Integration and Provisioning, and OracleAS Certificate Authority.
To upgrade a 10g (9.0.4) distributed OracleAS Identity Management configuration (as shown in Figure 5-3), do the following:
Review Section 5.7.3, "Verifying Whether OracleAS Identity Management Components are Enabled or Disabled" to determine exactly which OracleAS Identity Management components will be upgraded.
Upgrade the Oracle home that includes the Oracle Internet Directory used by the other OracleAS Identity Management components.
You must upgrade the Oracle Internet Directory first before upgrading the other distributed OracleAS Identity Management components.
To upgrade the Oracle Internet Directory Oracle home, use one of the following procedures, depending upon the type of installation used for the Oracle Internet Directory Oracle home:
If the Oracle Internet Directory Oracle home includes its OracleAS Metadata Repository, then use the procedure in Section 5.5, "Upgrading OracleAS Identity Management in a Colocated Infrastructure"
If the Oracle Internet Directory is in its own Oracle home, and the its OracleAS Metadata Repository resides in a different Oracle home, use the procedure in Section 5.6, "Upgrading OracleAS Identity Management in a Non-Colocated 10g (9.0.4) Infrastructure"
|
Note: If you are running only Oracle Internet Directory from the Oracle home, check to be sure the other OracleAS Identity Management components are disabled so they will not be upgraded or started in the destination 10g (10.1.2) Oracle home.For more information, see Section 5.7.3, "Verifying Whether OracleAS Identity Management Components are Enabled or Disabled". |
Make sure that the OracleAS Metadata Repository database and database listener used by the distributed components are up and running.
Log in to the computer on which the distributed OracleAS Identity Management components are installed, as the same operating system user that performed the 10g (9.0.4) installation.
|
Note: You must be logged in as a member of thedba operating system group.
|
Make sure the Oracle Internet Directory server is upgraded to 10g (10.1.2) and that it is up and running.
To verify that Oracle Internet Directory is running, enter one of the following commands.
|
Note: You may have to temporarily set the ORACLE_HOME environment variable to the Oracle Internet Directory Oracle home before running theldapbind command.
After you verify that the Oracle Internet Directory is running, you must then make sure the ORACLE_HOME environment variable is not defined before you start the 10g (10.1.2) installer, as directed in Step 6. |
If you are running Oracle Internet Directory on a non-secure port:
SOURCE_ORACLE_HOME/bin/ldapbind -p Non-SSL_port
If you are running Oracle Internet Directory on a secure port:
SOURCE_ORACLE_HOME/bin/ldapbind -p SSL_port -U 1
These commands should return a "bind successful" message.
Be sure to set the environment variables, as defined in the section "Environment Variables" in the "Requirements" chapter of the Oracle Application Server Installation Guide.
In particular, be sure to set following variables so they do not reference any Oracle home directories:
In addition, be sure the following environment variables are not set:
Mount the Oracle Application Server 10g (10.1.2) CD–ROM and start the installer.
|
See Also: Oracle Application Server Installation Guide for detailed instructions about starting Oracle Universal Installer on your platform |
Refer to Table 5-4 for information on the options you should select on each screen.
After the End of Installation screen appears, exit Oracle Universal Installer and then verify that Oracle Internet Directory and Oracle Application Server Single Sign-On are functioning and accessible.
|
See Also: "Accessing the Single Sign-On Server" in the Oracle Application Server Single Sign-On Administrator's Guide |
If you have installed and configured Oracle Application Server Certificate Authority, you must then run the Metadata Repository Upgrade Assistant to upgrade the OCA schema in the OracleAS Metadata Repository.
OCA is an OracleAS Identity Management component, but its schema is not upgraded by the OracleAS Identity Management upgrade process.
Table 5-4 Summary of the Oracle Universal Installer Screens During a 10g (9.0.4) Distributed OracleAS Identity Management Upgrade
| Screen | Description and Recommended Options to Select |
|---|---|
| Welcome | Welcomes you to Oracle Universal Installer and the Oracle Application Server 10g (10.1.2) installation procedure. |
| Specify File Locations | Enter a name and path for the new Oracle home.
This new Oracle home will be the destination Oracle home for your Oracle Application Server 10g (10.1.2) upgrade. |
| Select a Product to Install | Select OracleAS Infrastructure 10g.
If multiple languages are used in the OracleAS Infrastructure you are upgrading, then click Product Languages. |
| Language Selection | The screen appears only if you clicked Product Languages on the Select a Product to Install screen.
If multiple languages are used in the OracleAS Infrastructure you are upgrading, select those languages. If you are not sure which languages were installed, but want languages other than English, click the double arrow button (>>) to select all languages. |
| Select Installation Type | Select Identity Management or Identity Management and OracleAS Metadata Repository, depending upon the installation type you selected when you installed the distributed OracleAS Identity Management components.
Note: It is very important that you select the same installation type that is used in the Oracle home you are upgrading. In this case, you are upgrading a non-colocated OracleAS Identity Management installation, so you must select Identity Management. |
| Upgrade Existing Infrastructure | This screen (Figure 5-5) appears when Oracle Universal Installer detects an existing Oracle Application Server installation of the same type as the one you selected on the Select Installation Type screen.
Select the option to upgrade an existing OracleAS Infrastructure, and then select the Oracle home you want to upgrade from the drop-down list. (If there is only one Infrastructure of the selected time on the computer, then the drop-down list is inactive.) |
| Specify OID Login | Enter the Oracle Internet Directory superuser distinguished name (DN) in the Username field. The superuser DN cn=orcladmin is the default for this field; change this value if the Oracle Internet Directory superuser DN is not cn=orcladmin.
Enter the password for the superuser DN in the Password field. |
| Specify Infrastructure Database Connection Information | Enter SYS in the Username field and the SYS user's password in the Password field.
|
| Warning dialog box | This dialog box warns you that all the clients of the OracleAS Identity Management installation must now be stopped. Oracle Universal Installer will automatically stop any clients within the source Oracle home automatically.Foot 1
However, you must manually stop any OracleAS Identity Management clients that reside in another Oracle home Clients of an OracleAS Identity Management instance include:
Within each middle tier that uses this OracleAS Identity Management instance, you must be sure to stop all components, including Oracle HTTP Server and OracleAS Web Cache. For more information, see the chapter "Starting and Stopping " in the Oracle Application Server Administrator's Guide. |
| Database Listener Warning Dialog Box | If a database listener is running on the host, a warning dialog box displays. Review the dialog box determine whether or not you need to stop the listener manually.
For more information, see Section 5.3.3, "Stopping the Database Listener When Prompted During the OracleAS Identity Management Upgrade". |
| Specify Instance Name and ias_admin Password | Enter a name for the new Oracle Application Server 10g (10.1.2) instance and a password for the ias_admin Administrator account.
You use the In general, the minimum length of the For more information, see the section "The ias_admin User and Restrictions on its Password" in the Oracle Application Server Installation Guide. |
| Summary | Use this screen to confirm the choices you've made. Click Install to begin upgrading to the new 10g (10.1.2) Oracle home.
On UNIX systems, a dialog box appears when the copying is complete. This dialog box prompts you to run a configuration script as the root user. Follow the instructions in the dialog box and click OK when script is finished. |
| The Configuration Assistants | After the initial software is installed, a set of configuration assistants automatically set up the components in the new 10g (10.1.2) Oracle home. Use this screen to follow the progress of each assistant and to identify any problems during this phase of the installation.
Notes:
|
| End of Installation | When the installation and upgrade is complete, this screen provides important details about the 10g (10.1.2) Oracle home, such as the URL for the Application Server Control Console and the location of the setupinfo.txt file.
After you review the information on this screen, you can exit Oracle Universal Installer and proceed to the post-upgrade tasks. |
shutdownprocesses.log file, which is located in the cfgtoollogs directory in the destination Oracle home.When you upgrade a distributed OracleAS Identity Management configuration, the 10g (10.1.2) installer will upgrade any OracleAS Identity Management components that are enabled in the source Oracle home.
An OracleAS Identity Management component is considered enabled when it is marked as such in the following configuration file in the source Oracle home:
SOURCE_ORACLE_HOME/config/ias.properties
Before you upgrade your Oracle Internet Directory installation in a distributed OracleAS Identity Management configuration, you can check the contents of this file to verify which components are enabled. If necessary, modify the entries to reflect exactly which components you have enabled, and as a result, which components will be upgraded.
The entries in the ias.properties file vary, depending upon whether you are upgrading a Release 2 (9.0.2) Oracle home or a 10g (9.0.4) Oracle home. Refer to the following sections for more information:
Verifying Enabled OracleAS Identity Management Components in a Release 2 (9.0.2) Oracle Home
Verifying Enabled OracleAS Identity Management Components in a 10g (9.0.4) Oracle Home
If you are running only Oracle Internet Directory in a Release 2 (9.0.2) Oracle home, the ias.properties file should contain the following entries:
SSO.LaunchSuccess=False OID.LaunchSuccess=True
If there were other OracleAS Identity Management components configured in the Release 2 (9.0.2) source Oracle home after Release 2 (9.0.2) was installed, those other components, such as Oracle Delegated Administration Services (DAS), will not be upgraded to 10g (10.1.2) in the destination Oracle home. If you want to run those other components in the 10g (10.1.2) home, configure those components to the 10g (10.1.2) destination Oracle home.
If you are running only Oracle Internet Directory in a 10g (9.0.4) Oracle home, the ias.properties file should contain the following entries:
SSO.LaunchSuccess=False OID.LaunchSuccess=True DAS.LaunchSuccess=False DIP.LaunchSuccess=False OCA.LaunchSuccess=False
On the other hand, if you are running OracleAS Single Sign-On, Oracle Delegated Administration Services, and Oracle Directory Integration and Provisioning in one Oracle home, but using Oracle Internet Directory in another Oracle home, the entries would appear as follows:
SSO.LaunchSuccess=True OID.LaunchSuccess=False DAS.LaunchSuccess=True DIP.LaunchSuccess=True OCA.LaunchSuccess=False
If you are upgrading distributed OracleAS Identity Management components that were configured to use SSL, you must re-enable SSL for the OracleAS Single Sign-On and Oracle Delegated Administration Services after the upgrade.
There is no need to enable SSL for Oracle Internet Directory, since the upgrade procedure automatically re-enables SSL for Oracle Internet Directory in the destination Oracle home if you were using SSL with Oracle Internet Directory in the source Oracle home.
To enable SSL for OracleAS Single Sign-On, use the procedure described in the section "Enabling SSL" in the "Advanced Deployment Options" chapter of the Oracle Application Server Single Sign-On Administrator's Guide.
In particular, you must perform the following steps as described in that section of the Oracle Application Server Single Sign-On Administrator's Guide:
Enable SSL on the Single Sign-On middle tier.
Protect Single Sign-On URLs.
Restart the Oracle HTTP Server and the Single Sign-On Middle Tier.
Register mod_osso with the SSL virtual host as documented in the section "Configuring mod_osso with Virtual Hosts" in the Oracle Application Server Single Sign-On Administrator's Guide.
If you have also configured Oracle Delegated Administration Services in the upgraded Oracle home, you must reconfigure the Oracle Delegated Administration Services URL.
To reconfigure the Oracle Delegated Administration Services URL:
Start the Oracle Directory Manager in the Oracle Delegated Administration Services Oracle home:
ORACLE_HOME/bin/oidadmin
Use the Navigator Pane to expand the directory tree until you locate the following entry:
cn=OperationUrls,cn=DAS,cn=Products,cn=OracleContext
Select the entry in the tree.
Oracle Directory Manager displays the attributes of the entry in the right pane of the Directory Manager window.
Change the orcldasurlbase attribute so it references the HTTPS, SSL URL for the Oracle Delegated Administration Services:
https://hostname:http_ssl_port_number/
For example:
https://mgmt42.acme.com:4489/
|
See Also: "Using Oracle Directory Manager" in the Oracle Internet Directory Administrator's Guide |
This section describes how to upgrade Oracle Internet Directory in a replicated environment. You can upgrade one computer at a time, or all of the computers at one time. Instructions are provided for each method in the following sub-sections:
Preparing for an Oracle Internet Directory Multi-Master Replication Upgrade
Upgrading Oracle Internet Directory on Multiple Replicas Simultaneously
Oracle Corporation recommends that during upgrade, in order to prevent conflicts, the replication environment be a Single Master (that is, only one replica is read/write and all others are read only).
|
See Also: Oracle Internet Directory Administrator's Guide for information about managing and configuring Oracle Internet Directory replication configurations |
Before you begin upgrading Oracle Internet Directory 9.0.4.x.x in a replicated environment, you must perform the following steps for all replicas other than Master Definition Site (MDS) Replica or Primary supplier replica:
Locate the database registration entry of the database of replica to be upgraded.
SOURCE_ORACLE_HOME/bin/ldapsearch -h host -p port -D cn=orcladmin -w superuser_password -b "cn=oraclecontext" -s one "(objectclass=orcldbserver)" dn
This will return a list of Distinguished Names (DNs) corresponding to all the Databases registered in Oracle Internet Directory in the following form:
cn=database_name,cn=oraclecontext
Of these entries, locate the DN of the following entry, which will be used in Step 3 of this procedure:
cn=dbname_of_replica_to_be_upgraded,cn=oraclecontext
Identify the replica ID of the replica to be upgraded by issuing following command:
SOURCE_ORACLE_HOME/bin/ldapsearch -h hostname_of_replica_being_upgraded -p port -D cn=orcladmin -w superuser_password -b "" -s base "(objectclass=*)" orclreplicaid
Modify the seealso attribute of Replica Subentry of the replica to be upgraded as given below:
Create a file, for example mod.ldif, with following contents:
#File Name : mod.ldif dn: orclreplicaid=replicaid_from_step_2,cn=replication configuration changetype: modify replace: seeAlso #The DN used in seealso attribute is obtained in Step #1. seeAlso: cn=dbname_of_replica_being_upgraded,cn=oraclecontext
Modify replica subentry using ldapmodify command.
SOURCE_ORACLE_HOME/bin/ldapmodify -h hostname_of_replica_being_upgraded -p port -D superuser_DN -w superuser_password -v -f mod.ldif
Navigate to the following directory and locate ias.properties file:
SOURCE_ORACLE_HOME/config
Open the ias.properties file and modify properties as shown in Table 5-5.
Make sure the Oracle Internet Directory server is upgraded to 10g (10.1.2) and that it is up and running.
To verify that Oracle Internet Directory is running, enter one of the following commands.
|
Note: You may have to temporarily set the ORACLE_HOME environment variable to the Oracle Internet Directory Oracle home before running theldapbind command.
After you verify that the Oracle Internet Directory is running, you must then make sure the ORACLE_HOME environment variable is not defined before you start the 10g (10.1.2) installer, as directed in Step 6. |
If you are running Oracle Internet Directory on a non-secure port:
SOURCE_ORACLE_HOME/bin/ldapbind -p Non-SSL_port
If you are running Oracle Internet Directory on a secure port:
SOURCE_ORACLE_HOME/bin/ldapbind -p SSL_port -U 1
These commands should return a "bind successful" message.
Create an ldif file, for example add.ldif, with the contents shown in Example 5-1.
Start a second instance of LDAP server with "change log generation disabled" as shown below.
Note that this example assumes that the second instance is not in use and port 4444 is not used by any process.
oidctl connect=connect_string_of_db server=oidldapd instance=2 flags="-p 4444 -l false" start
Add the entries defined in the ldif file you created in Step 7 by using ldapadd tool as shown below.
To add these entries, you must use the port used for the LDAP server you started in Step 8. This example assumes that the LDAP server you started in step 7 is listening at port 4444.
ldapadd -p 4444 -h hostname -D cn=orcladmin -w password -f ldif_filename -c
For example:
ldapadd -p 4444 -h mgmt42.acme.com -D cn=orcladmin -w m03kslj -f add.ldif -c
Stop the second LDAP server as shown below.
This example assumes that the instance number used for the second instance was 2.
oidctl connect=<connect_string_of_db> server=oidldapd instance=2 stop
Table 5-5 Properties to Modify in ias.properties Before Replication Upgrade
Example 5-1 Contents of LDIF File Used to Prepare for Replication Upgrade
#File Name : add.ldif ################################ # Event Type Configuration ################################ dn: cn=ProvisioningEventTypeConfig,cn=odi,cn=oracle internet directory changetype: add cn: ProvisioningEventTypeConfig orclaci: access to entry by group="cn=Provisioning Admins, cn=changelog subscriber,cn=oracle internet directory" (browse,add,delete) orclaci: access to attr=(*) by group="cn=Provisioning Admins, cn=changelog subscriber,cn=oracle internet directory" (read,search,write,compare) objectclass: orclContainer dn: orclODIPProvEventObjectType=ENTRY,cn=ProvisioningEventTypeConfig,cn=odi, cn=oracle internet directory changetype: add orclODIPProvEventObjectType: ENTRY orclODIPProvEventLDAPChangeType: Add orclODIPProvEventLDAPChangeType: Modify orclODIPProvEventLDAPChangeType: Delete orclODIPProvEventCriteria: objectclass=* objectclass: orclODIPProvEventTypeConfig dn: orclODIPProvEventObjectType=USER,cn=ProvisioningEventTypeConfig,cn=odi, cn=oracle internet directory changetype: add orclODIPProvEventObjectType: USER orclODIPProvEventLDAPChangeType: Add orclODIPProvEventLDAPChangeType: Modify orclODIPProvEventLDAPChangeType: Delete orclODIPProvEventCriteria: objectclass=InetOrgPerson orclODIPProvEventCriteria: objectclass=orclUserV2 objectclass: orclODIPProvEventTypeConfig dn: orclODIPProvEventObjectType=IDENTITY,cn=ProvisioningEventTypeConfig,cn=odi, cn=oracle internet directory changetype: add orclODIPProvEventObjectType: IDENTITY orclODIPProvEventLDAPChangeType: Add orclODIPProvEventLDAPChangeType: Modify orclODIPProvEventLDAPChangeType: Delete orclODIPProvEventCriteria: objectclass=InetOrgPerson orclODIPProvEventCriteria: objectclass=orclUserV2 objectclass: orclODIPProvEventTypeConfig dn: orclODIPProvEventObjectType=GROUP,cn=ProvisioningEventTypeConfig,cn=odi, cn=oracle internet directory changetype: add orclODIPProvEventObjectType: GROUPorclODIPProvEventLDAPChangeType: Add orclODIPProvEventLDAPChangeType: Modify orclODIPProvEventLDAPChangeType: Delete orclODIPProvEventCriteria: objectclass=orclGroup orclODIPProvEventCriteria: objectclass=orclPrivilegeGroup orclODIPProvEventCriteria: objectclass=groupOfUniqueNames orclODIPProvEventCriteria: objectclass=groupofNames objectclass: orclODIPProvEventTypeConfig dn: orclODIPProvEventObjectType=SUBSCRIPTION,cn=ProvisioningEventTypeConfig, cn=odi,cn=oracle internet directory changetype: add orclODIPProvEventObjectType: SUBSCRIPTION orclODIPProvEventLDAPChangeType: Add orclODIPProvEventLDAPChangeType: Modify orclODIPProvEventLDAPChangeType: Delete orclODIPProvEventCriteria: objectclass=orclServiceSubscriptionDetail objectclass: orclODIPProvEventTypeConfig dn: orclODIPProvEventObjectType=SUBSCRIBER,cn=ProvisioningEventTypeConfig, cn=odi,cn=oracle internet directory changetype: add orclODIPProvEventObjectType: SUBSCRIBER orclODIPProvEventLDAPChangeType: Add orclODIPProvEventLDAPChangeType: Modify orclODIPProvEventLDAPChangeType: Delete orclODIPProvEventCriteria: objectclass=orclSubscriber objectclass: orclODIPProvEventTypeConfig ###################################################################### # DIPADMIN Account ###################################################################### dn: cn=dipadmin,cn=odi,cn=oracle internet directory changetype: add cn: dipadmin sn: dipadmin description: DIP Administrator Idenitity in OID objectclass: person ###################################################################### # DIPADMIN Group ###################################################################### dn: cn=dipadmingrp,cn=odi,cn=oracle internet directory changetype: add cn: dipadmin owner: cn=dipadmin,cn=odi,cn=oracle internet directory uniquemember: cn=orcladmin uniquemember: cn=dipadmin,cn=odi,cn=oracle internet directory description: DIP Administrator Group in OID objectclass: groupOfUniqueNames objectclass: orclprivilegegroup ###################################################################### # ODIPGROUP getting recreated here from 904 (Had been removed in 902*) ###################################################################### dn: cn=odipgroup,cn=odi,cn=oracle internet directory changetype: add cn: odipgroup objectclass: top objectclass: groupofUniquenames objectclass: orclprivilegegroup uniquemember: cn=orcladmin orclaci: access to entry by group="cn=dipadmingrp,cn=odi,cn=oracle internet directory" (browse) by * (none) orclaci: access to attr=(uniquemember) by group="cn=dipadmingrp,cn=odi, cn=oracle internet directory" (search,read,write,compare) by * (none) dn: cn=odisgroup,cn=odi,cn=oracle internet directory changetype: add cn: odisgroup objectclass: top objectclass: groupofUniquenames objectclass: orclprivilegegroup uniquemember: cn=orcladmin orclaci: access to entry by * (none) orclaci: access to attr=(*) by * (none)
Upgrading one computer at a time in a replicated environment ensures that Oracle Internet Directory available during the upgrade for additions, modifications, and searching.
The following sections describe how to upgrade one replica at a time:
Follow these steps to upgrade one replica at a time:
If you are upgrading from Release 2 (9.0.2), make sure you have applied the latest Release 2 (9.0.2) patchsets.
The OracleAS Identity Management upgrade procedures have been tested using the latest patchsets available from OracleMetaLink. As a result, before you upgrade Release 2 (9.0.2) OracleAS Identity Management, apply the latest Oracle Application Server 9.0.2 patchsets.
The OracleMetaLink Web site is at the following URL:
http://metalink.oracle.com/
At the time this document was published the most recent Oracle9iAS patchset release was the Oracle9iAS 9.0.2.3 patchset (3038037). To locate this patchset, search for patch number 3038037 on OracleMetaLink.
|
Note: After applying Oracle9iAS 9.0.2.3 patchset (3038037), verify that the patchset was applied successfully before proceeding with the 10g (10.1.2) upgrade. For example, verify that the Application Server Control, your deployed applications, and the components you use are functioning properly after you apply the patchset. |
Make sure you have completed the procedure in Section 5.8.1, "Preparing for an Oracle Internet Directory Multi-Master Replication Upgrade".
Identify the replica to be upgraded.
The replica can be an LDAP-based partial or fan-out replica, or it can be an Oracle Advanced Replication (ASR) based multimaster replica.
|
See Also: "Directory Replication Concepts" in the Oracle Internet Directory Administrator's Guide |
Stop the replication server on the replica to be upgraded.
Make sure that the LDAP server, the Oracle Internet Directory database, and the database listener are up and running.
If you are upgrading an ASR-based replica, then delete all ASR jobs on other replicas by issuing the following command:
SOURCE_ORACLE_HOME/ldap/admin/oidrdjob.sql
All ASR jobs on other master sites that transfer changes to this replica are deleted. This has the effect of taking the replica currently being upgraded out of the replication environment, so that no changes come to it, while other replicas continue to operate and replicate changes.
Upgrade the replica as described in Section 5.5, "Upgrading OracleAS Identity Management in a Colocated Infrastructure" or in Section 5.6, "Upgrading OracleAS Identity Management in a Non-Colocated 10g (9.0.4) Infrastructure".
Start the replication server database and listener in the upgraded replica Oracle home.
Test the connectivity to the other replicas.
The Net Services Upgrade assistant might have modified listener.ora and tnsnames.ora, breaking connectivity. If connectivity is broken, identify the entries that were modified in the files, and restore the entries from the corresponding files in the source Oracle home.
For example, copy the original entries from the following files in the source Oracle home:
SOURCE_ORACLE_HOME/network/admin/listener.ora SOURCE_ORACLE_HOME/network/admin/sqlnet.ora
Copy the values for the entries from these files to the corresponding files in the destination Oracle home:
DESTINATION_ORACLE_HOME/network/admin/listener.ora DESTINATION_ORACLE_HOME/network/admin/sqlnet.ora
If you are upgrading a Oracle Advanced Replication (ASR) based Replica, recreate jobs on each replica, after it is upgraded, by issuing the following command:
DESTINATION_ORACLE_HOME/bin/remtool –asrrectify
The jobs that were deleted in Step 5 are re-created. They will begin transferring the existing changes and new changes from other replicas to the upgraded replicas.
Perform the Oracle Internet Directory post-upgrade procedures.
After you upgrade a 10g (9.0.4) replica, reset the replication DN password of the upgraded replica by issuing following command:
DESTINATION_ORACLE_HOME/bin/remtool -presetpwd -v -bind host:port
Then, you can then start oidmon, LDAP server, and replication server. The replica is upgraded to Oracle Application Server 10g (10.1.2) and you can then proceed to upgrade the other replicas in the directory replication group.
After you upgrade a Release 2 (9.0.2) replica, you must perform the following steps before restarting and using the upgraded replica:
After upgrading the infrastructure to Oracle Application Server 10g Release, use a text editor to open the following configuration file in the destination Oracle home:
DESTINATION_ORACLE_HOME/opmn/conf/opmn.xml
Locate the entry that identifies the Oracle Internet Directory component entry in the opmn.xml file.
Add the ORACLE_SID environment variable within an environment element, as shown in Example 5-2.
Make sure that the value of the ORACLE_SID is set to the System Identifier (SID) of the Oracle Application Server 10g (10.1.2) database.
Save and exit the opmn.xml file.
Start the LDAP server and oidmon for the replica you are upgrading.
Use the following command to change the password of the replication distinguished name (DN) of upgraded replica:
DESTINATION_ORACLE_HOME/bin/remtool -presetpwd -v -bind host:port
Start the replication server.
Proceed with upgrading the remaining master site replicas as described in Section 5.8.2.1, "Upgrading the Oracle Internet Directory Replica".
Upgrade the database replication table by performing the following steps:
Stop the replication server on all replicas.
Quiesce the replication environment by issuing this command on the MDS replica:
DESTINATION_ORACLE_HOME/bin/remtool –suspendasr
Connect as REPADMIN (the database replication administrator) on the MDS replica and issue the following command:
execute DBMS_REPCAT.ALTER_MASTER_REPOBJECT (sname=> 'ODS', oname=> 'ASR_CHG_LOG', type=> 'TABLE', ddl_text=> 'alter table ods.asr_chg_log modify target_dn varchar2 (1024)')
Execute the following SQL command repeatedly until the "no rows selected" message appears:
SELECT * from dba_repcatlog WHERE request = 'ALTER_MASTER_REPOBJECT';
Generate replication support for the ASR_CHG_LOG table by issuing the command:
execute DBMS_REPCAT.GENERATE_REPLICATION_SUPPORT (sname=> 'ODS', oname=> 'ASR_CHG_LOG', type=> 'TABLE');
Execute the following SQL command repeatedly until the "no rows selected message appears:
SELECT * from dba_repcatlog WHERE request = 'ALTER_MASTER_REPOBJECT';
Resume the database replication by issuing the following command:
DESTINATION_ORACLE_HOME/bin/remtool -resumeasr
Start the replication server on all replicas.
Example 5-2 Adding the ORACLE_SID Environment Variable to the opmn.xml file when Upgrading a Release 2 (9.0.2) Oracle Internet Directory Replica
<?xml version = '1.0' encoding = 'UTF-8'?> <opmn xmlns="http://www.acme.com/ias-instance"> ... <ias-component id="OID" status="enabled"> <process-type id="OID" module-id="OID"> <environment> <variable id="ORACLE_SID" value="value_of_oracle_sid"/> </environment> <stop timeout="1800"/> <process-set id="OID" numprocs="1"> <dependencies> ... </ias-component> ... </opmn>
Upgrading multiple replicas simultaneously ensures that the entire network is upgraded without a transient stage. The procedure is simpler than upgrading one replica at a time, but involves directory service downtime.
The following sections describe how to upgrade multiple replicas at the same time:
Use the following procedure to upgrade all the replicas simultaneously:
In all replicas other than MDS replica or primary supplier replica, make sure you have completed the pre-upgrade steps provided in Section 5.8.1, "Preparing for an Oracle Internet Directory Multi-Master Replication Upgrade".
Stop the replication server on all replicas in the Directory Replication Group (DRG).
Upgrade all replicas as described in Section 5.5, "Upgrading OracleAS Identity Management in a Colocated Infrastructure" or in Section 5.6, "Upgrading OracleAS Identity Management in a Non-Colocated 10g (9.0.4) Infrastructure".
Start the database and the listener on all the upgraded replicas.
Test the connectivity to the other replicas.
The Net Services Upgrade assistant might have modified listener.ora and tnsnames.ora, breaking connectivity. If connectivity is broken, identify the entries that were modified in the files, and restore the entries from the corresponding files in the source Oracle home.
For example, copy the original entries from the following files in the source Oracle home:
SOURCE_ORACLE_HOME/network/admin/listener.ora SOURCE_ORACLE_HOME/network/admin/sqlnet.ora
Copy the values for the entries from these files to the corresponding files in the destination Oracle home:
DESTINATION_ORACLE_HOME/network/admin/listener.ora DESTINATION_ORACLE_HOME/network/admin/sqlnet.ora
Perform the Oracle Internet Directory post-upgrade procedures.
After you upgrade all the 10g (9.0.4) replicas, reset the replication DN password of the upgraded replica by issuing following command:
DESTINATION_ORACLE_HOME/bin/remtool -presetpwd -v -bind host:port
Then, you can then start the oidmon, LDAP server, and replication server for each replica. All replicas are then upgraded to Oracle Application Server 10g (10.1.2).
After you upgrade a Release 2 (9.0.2) replica, you must perform the procedure described in Section 5.8.2.3, "Completing the Upgrade of a Release 2 (9.0.2) Replica". After you complete that procedure, all the replicas will then be upgraded to Oracle Application Server 10g (10.1.2).
|
Important: This step should be performed only when all the nodes in the directory replication group are upgraded. Do not repeat this step after each replica upgrade. |
Oracle Internet Directory version 9.2.0.x, shipped with the Oracle9i Release 2 database, was a standalone release of Oracle Internet Directory. The Oracle Internet Directory database repository contained only Oracle Internet Directory schema.
The 10g (10.1.2) release supports upgrade of a v. 9.2.0.x Oracle Internet Directory deployed with the Oracle 9.2 database repository. Follow the steps below to perform this upgrade.
Stop all processes in the Oracle home.
Back up the database.
If the Oracle Internet Directory database was created with the Oracle9i Management and Integration installation type, you must install the Oracle9i Database 9.2.0.1.0 Software Only installation type into the same Oracle home, over the database created with the Management and Integration installation type. The Software Only installation type has the options required to use a 9.2 database as a metadata repository.
Use the Repository Creation Assistant to convert the 9.2 database to a metadata repository. See Chapter 10, "Installing the OracleAS Metadata Repository in an Existing Database" in the Oracle Application Server Installation Guide.
|
Note: On the Register with Oracle Internet Directory screen of the Repository Creation Assistant, select Register Later. |
The metadata repository now has the 10g (10.1.2) version of the schema for all OracleAS components except Oracle Internet Directory. The Oracle Internet Directory schema is still at version 9.2.
Create the Oracle Internet Directory tablespaces olts_svrmgstore and olts_battrstore in the 9.2.0.x Oracle Internet Directory database repository by executing the following SQL statements as SYS:
Create the imcfgregistry table in the 9.2.0.x Oracle Internet Directory database by running the following SQL statement as the ODS schema:
CREATE TABLE imcfgregistry (
Component VARCHAR2(255),
instMode VARCHAR2(255),
IASInstance VARCHAR2(255))
TABLESPACE OLTS_DEFAULT MONITORING;
Perform a 10g (10.1.2) Identity Management-only installation in a separate Oracle home, or on a different computer. (Select Oracle Internet Directory only), specifying the 9.2 database as the metadata repository database.
|
See Also: Oracle Application Server Installation Guide, Chapter 6, "Installing Oracle Internet Directory Only", for instructions. |
During the installation, the Oracle Internet Directory Configuration Assistant is invoked. It performs a version check on the Oracle Internet Directory schema; if the version is 9.2.0.x, then it upgrades Oracle Internet Directory to 10g Release 2 (10.1.2). The other configuration tools function as they would when a new installation is performed.
After the installation, the following conditions are in effect:
The Oracle Internet Directory server is running on the non-SSL and SSL ports, as determined by the 10g (10.1.2) installation process. The Oracle Internet Directory ports in use are identified in the following in the OIDport and OIDsslport properties of the following configuration file:
DESTINATION_ORACLE_HOME/config/ias.properties
The Oracle Internet Directory superuser and Oracle Internet Directory database schema (ODS) password are set to the same value as the ias_admin password specified during the Identity Management installation.
|
Note: Note: The 9.2.0.x metadata repository is in the original 9.2.0.x Oracle Internet Directory database Oracle Home. So you can connect from the 10g (10.1.2) Oracle Internet Directory Oracle Home only using the connect identifier:sqlplus ods/ods_password@oiddb
In this example, |
Set up appropriate access control policies required for the 10g (10.1.2) DAS and middle tier installation to operate with the upgraded Oracle Internet Directory by following the steps below:
Create an ldif (upgrade92.ldif) file with the entry shown below. Each value of the orclaci attribute (shown in bold below) must be a single line, without any line breaks, or an error will occur.
#--- BEGIN LDIF file contents--- dn: cn=Attribute Configuration, cn=DAS,cn=Products,cn=OracleContext changetype: modify add: orclaci orclaci: access to entry by group="cn=OracleDASConfiguration, cn=Groups,cn=OracleContext" (add,delete,browse) by * (noadd,nodelete) orclaci: access to attr=(*) by group="cn=OracleDASConfiguration, cn=Groups, cn=OracleContext" (read,write,search,compare) by * (nowrite,nocompare) dn: cn=Attribute Configuration, cn=DAS,cn=Products,cn=OracleContext,%rlmDN% changetype: modify add: orclaci orclaci: access to entry by group="cn=OracleDASConfiguration, cn=Groups,cn=OracleContext,%rlmDN%" (add,delete,browse) by * (noadd,nodelete) orclaci: access to attr=(*) by group="cn=OracleDASConfiguration, cn=Groups, cn=OracleContext,%rlmDN%" (read,write,search,compare) by * (nowrite,nocompare) #---END LDIF file contents------
Replace all occurrences of %rlmDN% in the upgrade92.ldif with the default realm DN. You can determine the default realm DN with the ldapsearch command shown below:
ldapsearch -h <oid host> -p <oid port> -D <OID superuser DN> -w <OID superuser password> -b "cn=common,cn=products,cn=oraclecontext" -s base "objectclass=*" orcldefaultsubscriber
Issue the ldapmodify command below:
<destination_Infra_OH>\bin\ldapmodify -p <oid port> -h <oid host> -D <OID superuser name> -w <OID superuser password> -v -f upgrade92.ldif
Perform the tasks in Section 5.10.3, "Completing the Oracle Internet Directory Upgrade".
This section details the post-upgrade procedures which will complete the Infrastructure upgrade to 10g (10.1.2). It is organized into these sections:
After you upgrade your OracleAS Identity Management, you can use the Oracle Enterprise Manager 10g Application Server Control Console to manage the upgraded 10g (10.1.2) OracleAS Identity Management instance.
However, the port used for the Application Server Control Console will be the port assigned by Oracle Universal Installer during the 10g (10.1.2) installation. You will not be able to use the port number that was previously used by Enterprise Manager in the source Oracle home.
|
See Also: Section 4.5.1, "About Port Values and the portlist.ini File After Upgrade" for information about how port numbers are changed during the upgrade process"Managing Ports" in the Oracle Application Server Administrator's Guide for information about changing the Application Server Control Console port after upgrade |
After you upgrade your Oracle Application Server instance, use the following passwords in the destination Oracle home:
To log in to the Application Server Control Console, use the ias_admin password you defined during the installation of the destination Oracle home.
To log in to the OracleAS Web Cache Manager, use the OracleAS Web Cache Administrator password you used in the OracleAS Web Cache source Oracle home.
To complete the Oracle Internet Directory Upgrade, you must perform the following tasks:
Running the oidpu904.sql Script to Recreate the orclnormdn Catalog
Configuring Oracle Internet Directory 10g (10.1.2) for Release 2 (9.0.2) Middle Tiers
Completing the Upgrade for the Oracle Directory Integration and Provisioning
Oracle Internet Directory Post-Upgrade Steps Required for OracleAS Portal
After you upgrade Oracle Internet Directory from Release 2 (9.0.2) to 10g Release 2 (10.1.2), you must run the oidpu904.sql script and recreate the orclnormdn catalog in the Oracle Internet Directory; otherwise, some Oracle Application Server components will not work correctly with the Oracle Internet Directory server.
Note that this procedure is not necessary if you have upgraded from Oracle Internet Directory 10g (9.0.4).
To perform this procedure:
Ensure that the ORACLE_HOME environment variable is set to destination Oracle home and the ORACLE_SID environment variable is set to the system identifier (SID) of the Infrastructure database.
Run following command:
sqlplus ods/ods_password@net_service_name_for_OID_database @DESTINATION_ORACLE_HOME/ldap/admin/oidpu904.sql
For example:
sqlplus ods/welcome1@iasdb @DESTINATION_ORACLE_HOME/ldap/admin/oidpu904.sql
Re-create the index for the orclnormdn attribute by executing the catalog.sh script, which drops and re-creates the catalog for the orclnormdn attribute.
Ensure that the Oracle Internet Directory server is operating in read-only mode. You can do this with the Oracle Directory Manager.
Issue these commands to re-create the index for the orclnormdn attribute:
DESTINATION_ORACLE_HOME/ldap/bin/catalog.sh -connect oid_database_net_service_name -delete -attr orclnormdn DESTINATION_ORACLE_HOME/ldap/bin/catalog.sh -connect oid_database_net_service_name -add -attr orclnormdn
Reset the Oracle Internet Directory server to operate in read-write mode. You can do this with the Oracle Directory Manager.
|
See Also: Oracle Internet Directory Administrator's Guide, for instructions on how to make the server operate in read-write mode. |
Starting with release 10.1.2, a certificate hash value can be used to bind to Oracle Internet Directory. The introduction of this hash value requires that user certificates issued before release 10.1.2 be updated in the directory. This is a post-upgrade step and it is required only if user certificates are provisioned in the directory. The upgradecert.pl tool is used for this purpose.
Complete instructions for running the Certificate Upgrade Tool are available in Appendix A, "Syntax for LDIF and Command-Line Tools," in the Oracle Internet Directory Administrator's Guide.
Before you can use Release 2 (9.0.2) middle tiers against the upgraded 10g (10.1.2) Oracle Internet Directory, you must run configure Oracle Internet Directory using the imconfig script.
For information on using the imconfig script, see Section 4.2.1, "Before Installing the 10g (10.1.2) Middle Tier Against a Release 2 (9.0.2) Oracle Internet Directory".
The upgrade process for Oracle Internet Directory cannot modify the Access Control List (ACL) policies on the public groups container. The default ACL policies on this container may have been changed to suit the security needs of your deployment environment. Hence, after upgrading, you should combine the existing policies with the new 10g Release 2 (10.1.2) default policies and apply them on the public groups container.
The ACL policy required is described in the Oracle Internet Directory Administrator's Guide, in Chapter 17 in the section on "Default Privileges for Reading Common Group Attributes". The policy should allow members of the group cn=Common Group Attributes, cn=groups, Oracle_Context_DN browse, search, and read access on private and public groups, that is on groups where orclIsVisible is either not set or is set to TRUE or FALSE.
If you upgrade a 9.0.x node to 10g Release 2 (10.1.2) and then try to set up replication for this node, the replication server will fail to come up and the replication setup itself may fail. Therefore, before setting up replication, reset the replication wallet password on the upgraded 10g Release 2 (10.1.2) node by using the following command:
DESTINATION_ORACLE_HOME/bin/remtool -presetpwd -v -bind host:port
This step ensures that the upgrade node can be configured in replication, if required.
If you had an older version (9.0.2 or 9.0.4) of the Directory Integration Platform (DIP) operating in a different Oracle home, on a different computer, and using the Oracle Internet Directory you are currently upgrading, and you want to continue using the DIP, you must re-register the DIP server.
|
See Also: Oracle Identity Management Integration Guide for instructions on registering the DIP server. |
The following post-upgrade steps are required if you have configured OracleAS Portal against this Identity Management and Oracle Internet Directory was upgraded directly from Release 2 (9.0.2):
Apply Interoperability Patches for Oracle9iAS Portal Release 2 (9.0.2)
Reconfigure the OracleAS Portal Instances for the Oracle Internet Directory Server
Refresh the Oracle Delegated Administration Services (DAS) URL Cache
If Oracle Internet Directory was upgraded directly from Release 2 (9.0.2), and you are operating Oracle9iAS Portal Release 2 (9.0.2 or 9.0.2.3), an interoperability patch must be applied to the Oracle9iAS repository, as explained below. This step can be skipped if the Oracle9iAS Portal version is 9.0.2.6 or later:
If you are operating Portal version 9.0.2.0 or 9.0.2.2 (Oracle9iAS 9.0.2.0.1): You must apply Patch 3238095, which corrects problems with registering users and groups in Oracle9iAS Release 2 (9.0.2) Identity Management configuration, and resolves interoperability issues.
If you are operating Portal 9.0.2.3 (Oracle9iAS 9.0.2.3): You must apply Patch 3076511 to resolve interoperability issues.
To apply the patches:
Locate the patch specified for the Portal version you are operating.
Follow the instructions in the patch Readme file.
If Oracle Internet Directory was upgraded directly from Release 2 (9.0.2), and if there are any OracleAS Portal instances using the upgraded Oracle Internet Directory server, they should be reconfigured. Follow these steps to reconfigure OracleAS Portal from a middle tier whose version is 10g (10.1.2):
Change directory to the following location in the destination middle tier Oracle home:
DESTINATION_ORACLE_HOME/portal/conf
Run the following command:
ptlconfig -dad portal_DAD -oid
|
See Also: Oracle Application Server Portal Configuration Guide |
If the version of your middle-tier is lower than 10.1.2, you must use the Oracle Portal Configuration Assistant command line utility ptlasst to reconfigure OracleAS Portal instances to work with Oracle Internet Directory. Refer to the appropriate version of the Oracle Application Server Portal Configuration Guide for instructions on how to use ptlasst.
The URLs for the Delegated Administration Services are different in Oracle9iAS Release 2 (9.0.2) Oracle Internet Directory server and the Oracle Application Server 10g (10.1.2) Oracle Internet Directory server. When the Oracle Internet Directory server is upgraded, these URLs are updated to the correct values. However, OracleAS Portal maintains a cache of these URLs, which does not get upgraded, and is therefore inconsistent with the set of URLs in 10g (10.1.2).
If Oracle Internet Directory was upgraded directly from Release 2 (9.0.2), the DAS URL cache will have to be refreshed. The procedure for refreshing the cache is dependent on the OracleAS Portal version you have. To refresh the cache, follow the steps in one of the sections below:
To refresh the URL cache in Version 9.0.2.6 or later:
Log in to the Portal as a Portal administrator.
Click the Administer tab.
Click the Global Settings link in the Services portlet.
Click the SSO/OID tab.
Note the values that appear under the section Cache for OID Parameters.
Click the check box next to Refresh Cache for OID Parameters.
Click Apply.
Verify that the values displayed under Cache for OID Parameters have changed.
Click OK.
To refresh the URL cache in versions prior to 9.0.2.6:
Apply the one-off patch 3225970. This patch is available at:
Clear the Web Cache by performing these steps:
Log in to the Portal as a Portal Administrator.
Click the Administer tab.
Click the Global Settings link in the Services portlet.
Click the Cache tab.
Click the check box next to Clear the Entire Web Cache.
Click OK.
Clear the middle tier cache by performing a recursive delete of all the files and subdirectories inside the following directory:
DESTINATION_ORACLE_HOME/Apache/modplsql/cache
To complete the OracleAS Single Sign-On upgrade, depending on the configuration upgraded, you may need to perform the tasks described in the following sections:
Section 5.10.4.1, "Re-configuring the OracleAS Single Sign-On Middle Tier"
Section 5.10.4.3, "Installing Customized Pages in the Upgraded Server"
Section 5.10.4.6, "Upgrading the OracleAS Single Sign-On Server with a Customized Middle Tier"
Section 5.10.4.7, "Troubleshooting Wireless Voice Authentication"
Section 5.10.4.8, "Installing Languages in the OracleAS Single Sign-On Server"
Section 5.10.4.9, "Re-Registering OracleAS Portal with the Upgraded OracleAS Single Sign-On Server"
Section 5.10.4.10, "Re-Registering mod_osso with the Upgraded OracleAS Single Sign-On Server"
Section 5.10.4.12, "Inactivity Timeout Issues When Upgrading From Release 2 (9.0.2) to 10g (10.1.2)"
If the Release 2 (9.0.2) or 10g (9.0.4) middle tier for the Single Sign-On server had custom configurations (for example, Oracle HTTP Server configured for SSL, or the Oracle Application Server Single Sign-On server Database Access Descriptor had any custom configuration), then you must re-configure the upgraded 10g Release 2 (10.1.2) middle tier in a like manner.
|
See Also: Oracle Application Server Single Sign-On Administrator's Guide, Chapter 9, for instructions on configuring the middle tier. |
If the Release 2 (9.0.2) or 10g (9.0.4) middle tier was configured to authenticate with a user certificate or third party authentication mechanism, then you must re-configure the 10g Release 2 (10.1.2) OracleAS Single Sign-On server in a like manner.
|
See Also: Oracle Application Server Single Sign-On Administrator's Guide, Chapter 13, for instructions on configuring the middle tier. |
If you have customized the login, password and the sign-off pages in the Release 2 (9.0.2) or 10g (9.0.4) Single Sign-On server, then you must update those pages with 10g Release 2 (10.1.2) specifications. This is also applicable if you have enabled support for Application Service Providers and updated the deployment login page to enable the company field.
|
See Also: Oracle Application Server Single Sign-On Administrator's Guide, Chapter 12, for instructions on configuring the middle tier. |
|
Note: You do not need to perform this task if you upgraded from an OracleAS Single Sign-On version of 9.0.2.5 or later.You can verify the version of OracleAS Single Sign-On you are running by running the following SQL statement against the OracleAS Single Sign-On database: select version from orasso.wwc_version$; It should return a value like 9.0.2.5.x. |
To avoid ID conflicts while exporting and importing external application data among multiple OracleAS Single Sign-On server instances, external application IDs must be unique. In the Release 2 (9.0.2) release, external application IDs were sequential, and not unique across instances. If you are upgrading from Release 2 (9.0.2) directly to 10g Release 2 (10.1.2), then you must convert existing short external application IDs to the longer format in the OracleAS Single Sign-On schema. Follow the steps below to convert the IDs:
Set the ORACLE_HOME environment variable to the Oracle home of the OracleAS Single Sign-On instance.
Execute the following script from the OracleAS Single Sign-On Oracle home, by using the following commands:
sqlplus orasso/password spool extappid.log @?/sso/admin/plsql/sso/ssoupeid.sql spool off
|
See Also: "Obtaining the Single Sign-On Schema Password" in the Oracle Application Server Single Sign-On Administrator's Guide |
If you are not upgrading OracleAS Portal to 10g Release 2 (10.1.2), but you have upgraded OracleAS Single Sign-On from Release 2 (9.0.2) directly to 10g Release 2 (10.1.2), you must apply a patch to each OracleAS Portal instance that is not going to be upgraded to 10g Release 2 (10.1.2).
Refer to Table 5-6 for the appropriate patch number. Patches are available at:
http://metalink.oracle.com/
If you are using Oracle Internet Directory replication and want to also use OracleAS Single Sign-On replication, add the upgraded 10g Release 2 (10.1.2) tables in the replication group along with 9.0.4 Oracle Internet Directory. Follow the steps below to add OracleAS Single Sign-On tables for replication:
Stop the Oracle Internet Directory replication server on all replicas of the Directory Replication Group.
On the Master Directory replica, in $ORACLE_HOME/ldap/admin, issue the following command:
sqlplus repadmin/password@<mds connect id> @oidrssou.sql
Start the Oracle Internet Directory replication server on all replicas of the Directory Replication Group.
|
See Also: Oracle Internet Directory Administrator's Guide, Chapter 25, "Managing Directory Replication", for instructions. |
If the Release 2 (9.0.2) or 10g (9.0.4) OracleAS Single Sign-On server was using a middle tier other than the default mid-tier installation along with the OracleAS Single Sign-On server, then you must configure that middle tier to point to the upgraded OracleAS Single Sign-On server.
For example, if there was a reverse proxy configured in the Release 2 (9.0.2) or 10g (9.0.4) OracleAS Single Sign-On server middle tier, then you must configure it on the 10g Release 2 (10.1.2) OracleAS Single Sign-On server middle tier.
If you want to use wireless voice authentication with the 10g Release 2 (10.1.2) OracleAS Single Sign-On server, and it doesn't work, verify that the OracleAS Single Sign-On server entry is a member of the Verifier Services Group in Oracle Internet Directory (cn=verifierServices,cn=Groups,cn=OracleContext). This is a requirement for the wireless voice authentication feature. Follow the steps below to verify membership:
Issue the following command:
ldapsearch -h <host> -p <port> -D "cn=orcladmin" -w <password> -b "cn=verifierServices, cn=Groups, cn=OracleContext" "objectclass=*"
The OracleAS Single Sign-On server is a member of the Verifier Services Group if it is listed as a uniquemember in the entry, as shown in Example 5-3.
If you did not select any languages during the OracleAS Single Sign-On upgrade, or you want to install additional languages after the upgrade, you can install the necessary languages by following the steps below.
Copy the necessary language files from the Repository Creation Assistant CD-ROM to the OracleAS Single Sign-On server Oracle home:
copy repCA_CD/portal/admin/plsql/nlsres/ctl/lang\*.* DESTINATION_ORACLE_HOME/sso/nlsres/ctl/lang
In this example, lang is the language code. For example, the language code for Japanese is ja.
Load the languages into the server.
|
See Also: Oracle Application Server Single Sign-On Administrator's Guide, Chapter 2, "Configuring Globalization Support" section, for instructions on loading the languages. |
After performing a distributed Identity Management upgrade (depicted in Figure 5-2 and Figure 5-3) from Oracle9iAS Release 2 (9.0.2) to Oracle Application Server 10g Release 2 (10.1.2), the OracleAS Single Sign-On schemas are relocated in the Oracle Internet Directory database. OracleAS Portal keeps a database link reference to the OracleAS Single Sign-On server password store schema ORASSO_PS. This link reference must be updated.
To re-register OracleAS Portal with the upgraded OracleAS Single Sign-On server from a middle tier whose version is 10g (10.1.2):
Change directory to the following location in the destination middle tier Oracle home:
DESTINATION_ORACLE_HOME\portal\conf
Run the following command:
ptlconfig -dad portal_DAD -sso
|
See Also: Oracle Application Server Portal Configuration Guide, for more information about theptlconfig tool
|
If the version of your middle-tier is lower than 10.1.2, you must use the Oracle Portal Configuration Assistant command line utility ptlasst to reregister OracleAS Portal with Oracle Single Sign-On. Refer to the appropriate version of the Oracle Application Server Portal Configuration Guide for instructions on how to use ptlasst.
After performing a distributed Identity Management upgrade (depicted in Figure 5-2 and Figure 5-3) from Oracle9iAS Release 2 (9.0.2) to Oracle Application Server 10g Release 2 (10.1.2), you may need to re-register mod_osso in order for an Oracle9iAS Release 2 (9.0.2) middle tier to operate with the upgraded OracleAS Single Sign-On server.
You will need to do this if the Oracle HTTP Server host and port information for mod_osso was changed. Before re-registering mod_osso, you must first set the value of the ColocatedDBCommonName attribute in the following configuration file to the global database name of the new OracleAS Single Sign-On server database shared with Oracle Internet Directory (for example, iasdb.host.mydomain).
SOURCE_ORACLE_HOME/config/ias.properties
If you upgraded an Identity Management configuration that was in use by Oracle9iAS Discoverer Release 2 (9.0.2), and you want to continue operating Oracle9iAS Discoverer Release 2 (9.0.2) with the upgraded Identity Management, then you must change the value of the ColocatedDBCommonName attribute in the following configuration file:
SOURCE_ORACLE_HOME/config/ias.properties
The value must be changed to the global database name of the database used by the upgraded Oracle Internet Directory (for example, iasdb.oid_host_name.domain).
If you are upgrading OracleAS Single Sign-On server from Release 2 (9.0.2) to 10g (10.1.2) and you are using the inactivity timeout feature, then you must do the following:
Upgrade associated mid-tiers used by other applications, such as Portal, to 10g (10.1.2).
Re-register mod_osso to ensure that inactivity timeout cookie issued by 10g (10.1.2) OracleAS Single Sign-On server can be interpreted and used by associated mid-tiers to enforce inactivity timeout.
The following sections describe the tasks you must perform in order to complete the Oracle Application Server Wireless upgrade:
Section 5.10.5.1, "Upgrading Wireless User Accounts in Oracle Internet Directory"
Section 5.10.5.4, "Activating All OracleAS Wireless 10g Release 2 (10.1.2) Features"
Section 5.10.5.5, "Assigning Change Password Privilege to OracleAS Wireless"
Section 5.10.5.6, "Specifying URL Query Parameters for Wireless Services That Use the HTTP Adapter"
In Oracle Application Server Wireless Release 2 (9.0.2), user account numbers and PINs for wireless voice authentication were stored in the Wireless repository.
In Oracle Application Server Wireless 10g Release 2 (10.1.2), new attributes are added in the object definition of the orcluserV2 object class of Oracle Internet Directory to store the account number and PIN. As part of the Oracle Application Server Wireless upgrade from Release 2 (9.0.2) to 10g Release 2 (10.1.2), user account numbers and PINs must be transferred from the Wireless repository to Oracle Internet Directory.
This upgrade step can be performed only after the Oracle Application Server Infrastructure and all middle tiers are upgraded to 10g Release 2 (10.1.2). If they are not upgraded, the Oracle Application Server Wireless server will continue to authenticate voice devices locally (without Oracle Application Server Single Sign-On).
To upgrade the account numbers and PINs:
Issue the command:
DESTINATION_ORACLE_HOME/wireless/bin/migrate902VoiceAttrsToOID.sh DESTINATION_ORACLE_HOME ldapmodify_location userdn password dif_file_location log_file
In this example:
ldapmodify_location is the location of the ldapmodify utility, which is usually in the bin directory of the destination Oracle home.
user_dn is the DN of the Oracle Internet Directory administrator user
password is the password of the Oracle Internet Directory administrator user
ldif_file_location is the absolute path to the ldif (Lightweight Directory Interchange Format) file. This file contains user account numbers and PINs and is uploaded to Oracle Internet Directory by the ldapmodify utility. This temporary file may be removed after the user upgrade procedure has been completed successfully.
log_file is the absolute path to the log file
Example:
migrate902VoiceAttrsToOID.sh /dua0/oracle/as904/ /dua0/oracle/as904/bin/ldapmodify "cn=orcladmin" welcome1 /dua0/oracle/as904/users.ldif /dua0/oracle/as904/users.log
In 10g Release 2 (10.1.2), Oracle Internet Directory does not automatically set unique constraints on any user attributes. Wireless voice authentication will not function properly unless a unique constraint is set on the orclWirelessAccountNumber attribute of the orclUserV2 object class.
Set the unique constraint by performing the steps below after the middle tier and infrastructure upgrades are complete.
Execute the script addAccountNumberUniqueConstraint.bataddAccountNumberUniqueConstraint.sh, which is located in the following directory:
DESTINATION_ORACLE_HOME/wireless/bin
The script takes one argument, the full path to the Oracle home. For example:
addAccountNumberUniqueConstraint.sh DESTINATION_ORACLE_HOME
Restart the Oracle Internet Directory server.
When Oracle Application Server Wireless 10g Release 2 (10.1.2) is installed against an Oracle9iAS Release 2 (9.0.2) infrastructure, a number of triggers are automatically installed, that ensure that both Oracle9iAS Wireless Release 2 (9.0.2) and Oracle Application Server Wireless 10g Release 2 (10.1.2) middle tiers can function correctly. Once all Oracle9iAS Wireless Release 2 (9.0.2) middle tiers and the infrastructure tier have been upgraded to Oracle Application Server Wireless 10g Release 2 (10.1.2), you must execute the following script to disable any upgrade-related triggers.
disable902-904_trg.sh
This script is located in the following directory:
DESTINATION_ORACLE_HOME/wireless/bin
You must set the ORACLE_HOME environment variable before you execute the script.
When Oracle Application Server Wireless 10g Release 2 (10.1.2) is installed against an Oracle9iAS Release 2 (9.0.2) Infrastructure, a number of features are disabled by default, as they are not compatible with existing Oracle9iAS Wireless Release 2 (9.0.2) middle tiers that are installed against the same Infrastructure. After all Oracle9iAS Wireless Release 2 (9.0.2) middle tiers have been upgraded to Oracle Application Server Wireless10g (10.1.2), you can manually enable these features. Once you have enabled these features, the Oracle9iAS Wireless Release 2 (9.0.2) middle tiers will no longer function correctly.
Enable the Oracle Application Server Wireless 10g Release 2 (10.1.2) features by executing the following script from any of the Oracle Application Server Wireless 10g Release 2 (10.1.2) middle tiers, using the command below. This script is in the following directory of the destination Oracle home:
DESTINATION_ORACLE_HOME/wireless/bin
The command takes the following arguments:
upload.sh wireless_repository_location -l wireless_user_name/wireless_password
In this example:
wireless_repository_location is the relative path to the OracleAS Wireless XML-based repository
wireless_user_name is the name of the Oracle Application Server Wireless user
wireless_password is the password of the Oracle Internet Administrator
For example:
upload.sh ../repository/xml/activate-9040.xml -l orcladmin/welcome1
In Oracle Application Server 10g Release 2 (10.1.2), by default, the OracleAS Wireless application entity does not have the privileges to change the user password. Consequently, upon installation, users cannot change the password to the OracleAS Wireless server. However, you can enable functionality to change passwords by assigning the UserSecurityAdmins privilege to the OracleAS Wireless application entity.
To do this, execute the following script:
DESTINATION_ORACLE_HOME/wireless/bin/assignUserSecurityAdminsPrivilege.sh
The syntax is:
assignUserSecurityAminsPrivilege.sh oid_super_user_dn user_password
In this example:
oid_super user_dn is the Distinguished Name of the Oracle Internet Directory super user. This user should have privileges to grant UserSecurityAdmins privileges to application entities.
user_password is the password of the Oracle Internet Directory super user.
For example:
assignUserSecurityAdminsPrivilege.sh "cn=orcladmin" welcome1
|
See Also: "Resetting the Password" in Oracle Application Server Wireless Administrator's Guide |
When you use the HTTP adapter to build Wireless services, one of the service parameters that you must specify is the URL to a back-end application. In some cases, you may send some query parameters to the back-end application. There are two ways to do this from OracleAS Wireless, shown in Example 5-4 and Example 5-5. In Example 5-4, the parameter name is fn and the value is Joe.
The query parameter is sent only in the request for the first page of that service. If there is a link from the first page to some other pages, then the parameter is not added to the request for those pages.
Instead of modifying the URL, you add an extra service parameter with name fn and value Joe. The the parameter is sent to all pages, not just the first one. The parameter is also sent with all HTTP redirect requests. However, this method also sends extra URL parameters to the OracleAS Single Sign-On server, which causes the server to return an error.
The error occurs when the back-end application is protected by mod_osso. In that case, the request to that application is intercepted and redirected to the Oracle SSO server for user authentication. The OracleAS Single Sign-On server has restrictive rules concerning query parameters that can be sent to it. Consequently, for back-end applications protected by mod_osso, you must change the Wireless service and add the query parameter to the URL as shown in Example 5-4.
This section describes the steps you must perform after the Identity Management Upgrade to ensure that the upgrade was successful.
After the Identity Management upgrade is complete, log in to Oracle Application Server Single Sign-On as user ORCLADMIN. A successful login indicates that Oracle Application Server Single Sign-On and Oracle Internet Directory are functioning after the Identity Management upgrade.
In a browser, access the Oracle Enterprise Manager 10g Application Server Control Console in the destination Infrastructure Oracle home by entering its URL. Ensure that you provide the correct host name and port number. For example:
http://infrahost.mycompany.com:1812
Oracle Enterprise Manager 10g displays the Farm page, with the Oracle Application Server 10g Release 2 (10.1.2) Identity Management instance in the Standalone Instances section.
Click the link for the Identity Management instance.
The System Components page appears.
Verify that the status of the Oracle HTTP Server, Oracle Internet Directory, and Oracle Application Server Single Sign-On components is Up.
In the browser, access the ORASSO page by entering its URL. Ensure that you enter the correct host name and port number for the upgraded Oracle HTTP Server. For example:
http://infrahost.mycompany.com:7777/pls/orasso/ORASSO.home
The ORASSO page appears.
Click the Login link (in the upper right corner of the page).
A page appears with User Name and Password fields.
Enter ORCLADMIN in the User Name field, and the password you have selected for ORCLADMIN in the Password field.
Click Login.
The Oracle Application Server Single Sign-On Server Administration page appears, thus validating the basic operation of the upgraded Identity Management components (Oracle Application Server Single Sign-On and Oracle Internet Directory).
If you have upgraded Oracle Application Server Certificate Authority (OCA), you can verify that the upgrade completed successfully by accessing the OCA User page.
Open your Web browser and enter the following URL:
https://infrahost.mycompany.com:4400/oca/user
Check to be sure that you can log in as a regular user and view the user's existing certificates. This ensures that OCA is working with Oracle Internet Directory and OracleAS Single Sign-On.
After you upgrade your OracleAS Identity Management Oracle home, the source Oracle home can eventually be deinstalled. However, before you deinstall the source Oracle home, review the following sections carefully:
If you upgraded OracleAS Identity Management as part of a colocated Infrastructure, then you also upgraded the OracleAS Metadata Repository database to a supported database version.
After you upgrade the OracleAS Metadata Repository database using the OracleAS Upgrade Assistant, the datafiles, control files, and log files for the database remain in the source Oracle home. Before you deinstall or remove the Oracle home, you must first relocate the database files.
If there are application files or log files in the source Oracle home that are being referenced or used by the destination Oracle home, you should move them to another location before you decommission the source Oracle home, and, in the destination Oracle home, change any references to the files to the new location.
Be sure to remove the source instance from the farm before you deinstall the source Oracle home.
For example, after you upgrade an instance that was using an OracleAS Infrastructure, the source instance remains in the list of instances on the Application Server Control Console Farm page.
To remove the source instance from the farm and from the Farm page, use the following command in the source Oracle home:
SOURCE_ORACLE_HOME/dcm/bin/dcmctl leavefarm
|
See Also: Distributed Configuration Management Administrator's Guide for more information about thedcmctl leavefarm command
"Introduction to Administration Tools" in the Oracle Application Server Administrator's Guide for more information about the Farm page in the Application Server Control Console |
If you have 9.0.2 or 9.0.3 and 10g Release 2 (10.1.2) instances on the same computer, and you want to deinstall a 9.0.2 instance, review the information in Section 4.9.4, "Deinstalling a Release 2 (9.0.2) or Release 2 (9.0.3) Source Oracle Home".
When you are certain that the upgrade was successful, you have all of the necessary backups, and have no plans to revert to the source Oracle home, you may elect to remove the files from the source Oracle home. Use the Oracle Universal Installer to deinstall the instance.
Note, however, that deinstalling an Oracle9iAS Release 2 (9.0.2) or (9.0.3) instance when there is also an OracleAS 10g Release 2 (10.1.2) instance on the computer requires a patch. Before you deinstall such an instance, be aware of the issues associated with this deinstallation that may apply to your configuration.