| Oracle® Audit Vault Auditor's Guide 10g Release 2 (10.2.2) Part Number B28853-02 |
|
|
View PDF |
| Oracle® Audit Vault Auditor's Guide 10g Release 2 (10.2.2) Part Number B28853-02 |
|
|
View PDF |
The analysis of audit data has become an important tool for detecting fraud and data misuse. Audit trails can contain extensive, detailed, and sensitive information about production systems. Auditing enables the detection of unauthorized actions, as well as the actions performed by authorized users. It reveals who did what, and what was affected. Even audit information that might seem harmless by itself can be used to infer other confidential information after some correlation.
The job of the auditor is to view predefined reports based on audit event categories, detect security risks, create and evaluate alert scenarios, and create and manage detailed and summary reports of events across systems. The auditor can create custom audit reports and use the Data Warehouse service to analyze audit data for trends, intrusions, anomalies, and so on.
Oracle Database provides a depth of auditing that readily enables businesses to implement enhanced protections, early detection of suspicious activities, and finely tuned security responses to address compliance and privacy requirements.
See Also:
Oracle Database Security Guide for detailed information about configuring database auditing.This chapter contains the following sections:
Database auditing is performed to protect and preserve privacy for the information stored in databases. Businesses leverage database auditing to address the following issues:
Insiders pose a major threat to information security. The CSI/FBI 2005 Computer Crime and Security Survey have documented that more than 70% of information system data losses and attacks have been perpetrated by insiders, that is, by those authorized at least some level of access to the system and its data. Authorized users include employees, partners, hosting companies, guests, and clients. Insider security breaches can be much more costly than attacks from outside the enterprise.
Every enterprise that collects personal information from its customers is responsible for protecting the privacy of that data. Securing sensitive customer information is a business necessity and, in many cases, it is mandated by law.
Identity theft has emerged as an organized criminal activity. Increased incidents of identity theft have caused growing concern among consumers regarding the privacy of their data. Recent headlines have trumpeted major thefts of customer data from banks, retailers, and information brokers. As a result, information protection and auditing have become top-level issues for many enterprises.
Businesses and governments have incurred substantial costs due to identity theft, including:
Business disruption
Time and money lost responding to the incidents
Direct financial losses (government fines, stock market losses, or customer lawsuits)
Imprisonment
Negative publicity and damage to reputation
Damage to national security
Loss of life
In response to severe corporate governance and structural failures over the last decade, governments and international bodies have dramatically increased their regulatory requirements. In addition, governments have enacted a wide range of legislation to safeguard investor, patient, consumer, and citizen data. Corporate governance and compliance regulations often require information systems auditing, log analysis and reporting, and log retention. Some of these regulations impose severe criminal penalties for noncompliance and malfeasance with protected data. International, U.S. federal and state laws, and regulations that require strong security and auditing include:
Sarbanes-Oxley Act (corporate financial compliance)
Basel Capital Accord (banking industry regulatory compliance)
SEC 17a-3 and 17a-4, NASD 3010, and NYSE (financial industry compliance)
FDA 21-CFR-11 (pharmaceutical industry regulatory compliance)
Homeland Security Presidential Directive (HSPD-12)
Gramm-Leach-Bliley Act (finance)
HIPAA (health care regulatory compliance)
Children's Online Privacy Protection Act (COPPA)
California SB 1386 (consumer)
Payment Card Industry (PCI) Data Security Standard
Family Educational Rights and Privacy Act (FERPA)
Canada's Personal Information Protection and Electronic Documents Act (PIPEDA) and the European Union Privacy Protection Directive 2002/58/EC (privacy compliance)
Auditing can help compliance and security auditors to perform the following tasks:
Determining the actions that occur within a system
Detecting attempts of unauthorized individuals to access the system
Detecting attempts by authorized users to misuse the system
Verifying regulatory compliance
You typically use auditing to:
Investigate suspicious activity
For example, if a user is deleting data from tables, then a security administrator might decide to audit all connections to the database and all successful and unsuccessful deletions of rows from all tables in the database.
Notify an auditor of unauthorized actions by users
For example, the unauthorized user could be manipulating or deleting data. The user might have more privileges than expected, and it might be time to reassess user authorizations.
Monitor and gather data about specific database activities
For example, the database administrator can gather statistics about which tables are being updated or how many concurrent users connect at peak times.
Detect problems with an authorization or access control implementation
For example, you can create audit policies that you expect will never generate an audit record because the data is protected in other ways. However, if these policies do generate audit records, then controls are not properly implemented.
Address auditing requirements for compliance
Regulations such as the Sarbanes-Oxley Act, Health Insurance Portability and Accountability Act (HIPAA), International Convergence of Capital Measurement and Capital Standards: a Revised Framework (Basel II), Japan privacy law, and the European Union Directive on Privacy and Electronic Communications have common auditing-related requirements.
Businesses use a wide variety of systems, databases, and applications that produce vast quantities of audit log data, and they must consolidate and monitor this data for a holistic view of enterprise data access. Auditors must analyze the audit log data in a timely fashion across disparate and heterogeneous systems. To facilitate the process, it is essential that audit data from multiple systems reside in a single audit data warehouse that is secure, scalable, reliable, and highly available.
Oracle Audit Vault solves these security and audit problems by:
Consolidating audit information from multiple systems across the enterprise
Detecting data changes associated with regular and privileged users
Protecting audit data from modification and tampering
Figure 1-1 shows an overview of the Oracle Audit Vault architecture. The architecture consists of a set of services and its collection system working within an enterprise. This set of services helps to facilitate storage management, policy enforcement, alerting, analysis, reporting, and activities. The collection infrastructure enables the utilization of audit collectors that function as adaptors between an audit source and Oracle Audit Vault Server.
Figure 1-1 Oracle Audit Vault Architecture
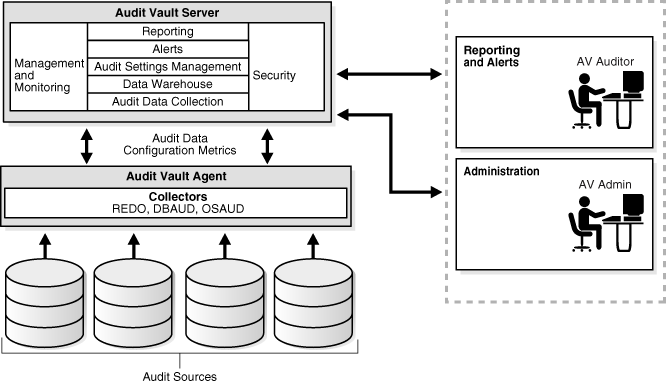
Oracle Audit Vault Components
Oracle Audit Vault consists of:
Audit Vault Server
Audit Vault Agents
Audit Vault Server
Audit Vault Server consists of:
Audit Data Store
Audit Vault Console
The following services:
Collector management and monitoring
Report management
Alert management
Audit settings management to establish your policy management
Published data warehouse that can be used with reporting tools like Oracle Business Intelligence Publisher to create customized reports
Audit data collection and storage management
Configuration services assist in defining information about what sources are known to Oracle Audit Vault. Oracle Audit Vault stores information (metadata) about the sources of audit data and policy information (database audit settings).
Audit Vault Agents
An Audit Vault Agent provides run-time support for audit data collection by Audit Vault collectors. It also contains the audit data collectors for Oracle Database sources. The following collectors are provided in Oracle Audit Vault 10g release 2 (10.2.2):
DBAUD
OSAUD
Note:
XML files are not supported in the OSAUD collector.OSAUD for Windows (EVTLOG)
REDO
Oracle Audit Vault Dashboard, also called Overview, is the home page for auditors to view alert summaries, drill down to reports, and view agent and collector status. It is shown in Figure 1-2.
When an audit record is generated, it is classified into a category. Audit event activity is monitored by the event category to which the audit record belongs. For example, a logon event belongs to the user session event category.
An alert is raised when data in a single audit record matches a predefined alert rule condition. For example, an alert rule condition might be defined for a logon event when three failed logon attempts by a user to gain access to a particular source of data are detected over a 5-minute period. When that rule condition is met, the audit event is evaluated and, because it matches the rule condition, an alert is raised. Alerts are grouped by the sources with which they are associated, by the event category to which the event belongs, and by the severity level of the alert (warning or critical).
From the Dashboard page, you can:
Select an event start time and end time in which to view Audit Vault event data.
View five types of graphical summaries (pie charts and bar graphs) of alert activity and event activity over the specified time period. Time periods are specified by either a month, week, or day time span or the period between a specified begin and end date. These graphical summaries include:
Alert Severity Summary (pie chart)
Click a section in this pie chart to drill down to a more detailed Alert Report Page to see what sources are showing a particular severity level.
Summary of Alert Activity (pie chart)
Click a section in this pie chart to drill down to an Alert Report Page to see the affected sources for all alert activity.
Top Five Audit Sources by Number of Alerts (bar graph)
Click a bar in this bar graph to drill down to see a more detailed Alert Report Page showing the alerts for a severity level for a particular source.
Alerts by Audit Event Category frequency (number of alerts) (bar graph)
Click an event category link in this bar graph to drill down to see a more detailed Alert Report Page showing all alerts for that event category.
Activity by Audit Event Category frequency (number of events) (bar graph)
Click an event category link in this bar graph to drill down to see events for that event category. You can generate activity reports for the following audit event categories:
Click a pie section or bar chart y-axis event category label to drill down to a more detailed report level.
As an Audit Vault auditor, you can use the Audit Vault Console Dashboard to view Audit Vault agents and collectors. To view collectors, click the Audit Status tab on the dashboard, then click Collectors on the upper left to reach the Collectors Page.
To view agents, click the Audit Status tab on the dashboard, then click the Agents tab on the upper left to reach the Agents Page.
From the Collectors page, you can view collectors listed by their name. Collector information includes the following column headings:
Collector – Name of the collector
Agent – The name of the agent to which this collector is associated
Audit Source – The name of the audit data source where the audit data is being collected
Status – Whether the collector is running or not. When the collector is up, a green up arrow indicator is displayed. When the collector is down, a red down arrow indicator is displayed. When there is a problem, an error is displayed.
From the Agents page, you can view agents listed by name. Agent information includes the following column headings:
Agent – The name of the agent
Host – The name of host system where the agent resides
Port – The port number for this agent
HTTPS – Whether the agent is communicating with Audit Vault using a secure communication channel (HTTPS) or not
Status – Whether or not the agent is running. When the agent is up, a green up arrow indicator is displayed. When the agent is down, a red down arrow indicator is displayed. When there is a problem, an error is displayed.