| Oracle® Retail Service Backbone Installation Guide Release 19.0.1 F44790-01 |
|
 Previous |
WebLogic ships with a default internal Light-weight Directory Access Protocol (LDAP) authentication provider. In an environment where a couple of domains exist, an administrator can set up users and groups in an internal LDAP provider and use these parameters during login and authentication. Alternatively, in an environment that contains multiple domains, managing/maintaining users and groups can be a difficult task. Oracle recommends that you use a centralized LDAP server to manage/maintain the users and groups. This chapter describes the steps you should take to configure the Oracle Internet Directory (OID) and the Active Directory (AD) LDAP based authentication provider in WebLogic.
An online directory is a specialized database that stores and retrieves collections of information about objects. The information can represent any resources that require management, for example:
Employee names, titles, and security credentials
Information about partners
Information about shared resources such as conference rooms and printers
The information in the directory is available to different clients, such as single sign-on solutions, e-mail clients, and database applications. Clients communicate with a directory server by means of the LDAP. The Oracle Internet Directory is an LDAP directory that uses an Oracle database for storage.
An Active Directory (AD) is a directory service implemented by Microsoft for Windows domain networks. It is included in most Windows Server operating systems. Active Directory is a special-purpose database — it is not a registry replacement. The directory is designed to handle a large number of read and search operations and a significantly smaller number of changes and updates. Active Directory data is hierarchical, replicated, and extensible. Because it is replicated, you do not want to store dynamic data, such as corporate stock prices or CPU performance.In Windows 2000, Active Directory has three partitions. These are also known as naming contexts: do-main, schema, and configuration. The domain partition contains users, groups, contacts, computers, organizational units, and many other object types. Because Active Directory is extensible, you can also add your own classes and/or attributes. The schema partition contains classes and attributes definitions. The configuration partition includes configuration data for services, partitions, and sites.
The architecture diagram describes the configuration of an OID and AD LDAP-based authentication provider used by applications deployed in an WebLogic server environment. 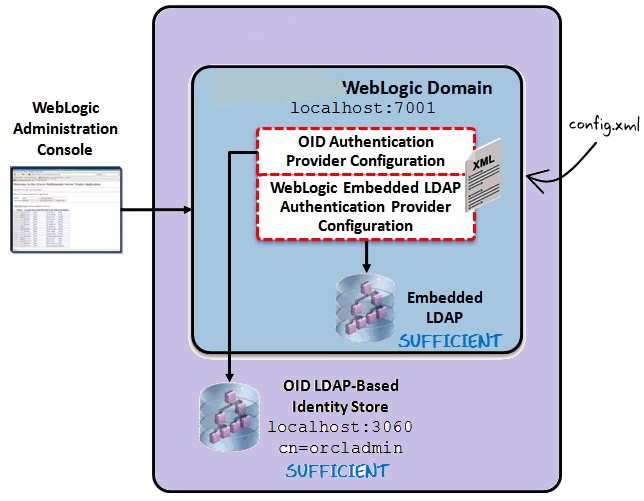
The diagram displays a sample environment and consists of the following:
The WebLogic Server running on port 7001
The WebLogic Administration Console used to configure authentication providers
The WebLogic Embedded LDAP server with a control flag setting of SUFFICIENT
An OID LDAP-based identity store running on port 3060 with a control flag setting of SUFFI-CIENT
The WebLogic config.xml that stores the authentication provider configuration
By default, the WebLogic server uses a security realm with the name ”myrealm” that uses an embedded LDAP server (two default users WebLogic & OracleSystemUser) that acts as data store for Authentication, Authorization, Credential Mapping and Role Mapping Provider.
To configure the OID as an authentication provider in WebLogic, take the following steps:
Login to WebLogic Console -> Security Realm -> myrealm. 
Select tab Providers -> Authentication -> Default Provider (DefaultAuthenticator). 
Change the Control Flag (JAAS Flag) parameter from REQUIRED to SUFFICIENT and click Save. 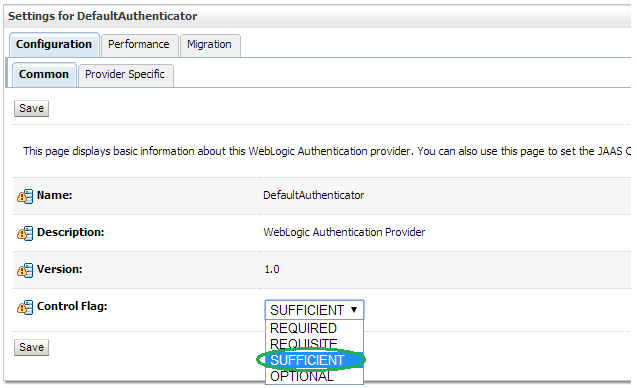
Click New to add a new Authentication Provider. 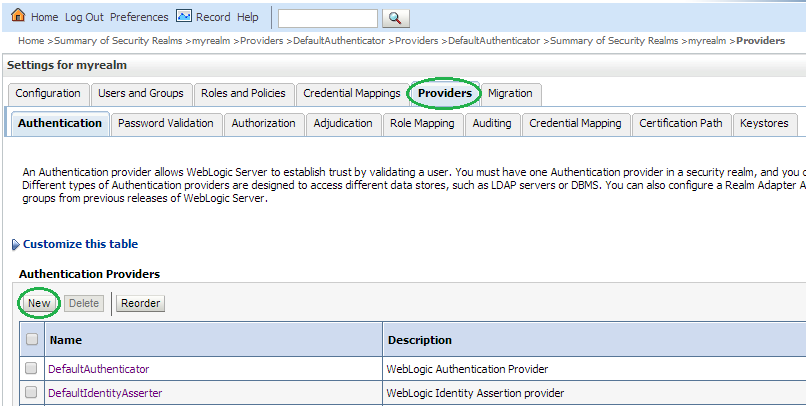
Enter OIDAuthentication as the Name of the new provider. Select OracleInternetDirectoryAuthenticator as Type and then click OK. 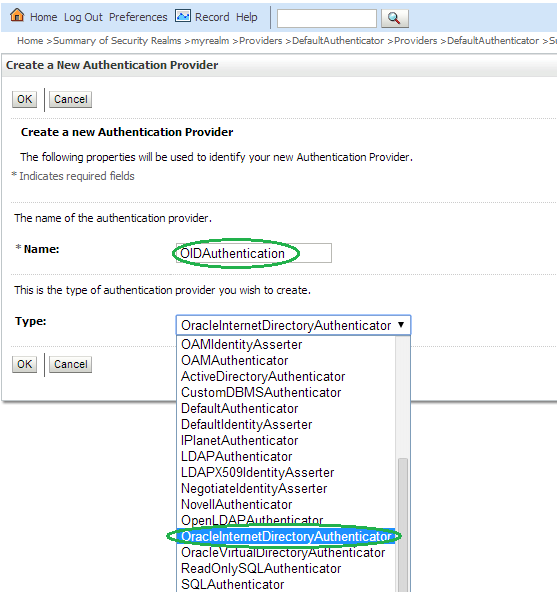
Change the Control Flag to SUFFICIENT for the OIDAuthentication Provider added and click Save. 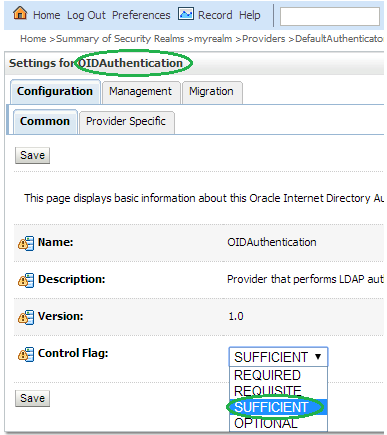
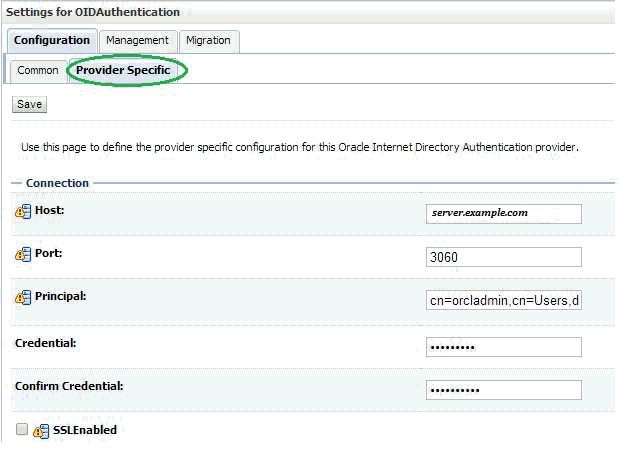
Select the Provider Specific tab and enter your OID server details.
The first section contains the Connection settings for the OID server. Use the appropriate values based on where the OID is hosted and the credentials:
| Name | Value | Purpose |
|---|---|---|
| Host: | server.example.com | The OID host name |
| Port: | 3060 | The standard OID listening port |
| Principal: | cn=orcladmin,cn=Users,dc=idc,dc=oracle,dc=com | The LDAP user that logs into OID on behalf of your authentication provider |
| Credentials: | Password for the principal user | |
| Confirm Credentials: | Confirmation of the password | |
| SSL Enabled: | Unchecked | Enables or disables SSL connectivity |
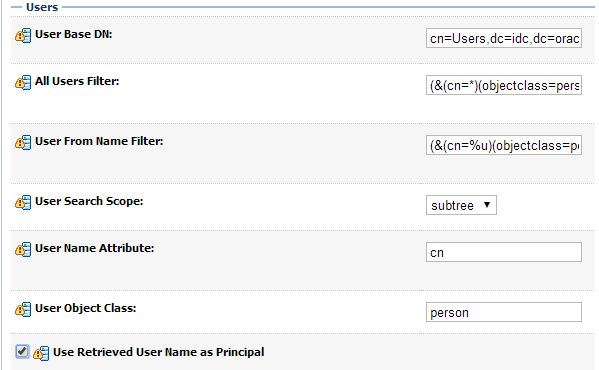
The second section contains the Users settings for the OID provider. Use appropriate values:
| Name | Value | Purpose |
|---|---|---|
| User Base DN: | cn=Users,dc=idc,dc=oracle,dc=com | The root (base DN) of the LDAP tree where searches are performed for user data |
| All Users Filter: | (&(cn=*)(objectclass=person)) -- Leave as default | The LDAP search filter that is used to show all the users below the User Base DN |
| User From Name Filter: | (&(cn=%u)(objectclass=person)) -- Leave as default | The LDAP search filter used to find the LDAP user by name |
| User Search Scope: | Leave as default | Specifies how deep in the LDAP tree to search for users |
| User Name Attribute: | Leave as default | The attribute of the LDAP user that specifies the user name |
| User Object Class: | Leave as default | The LDAP object class that stores users |
| Use Retrieved User Name as Principal: | Checked | Specifies if the user name retrieved from the LDAP directory will be used as the Principal in the Subject |
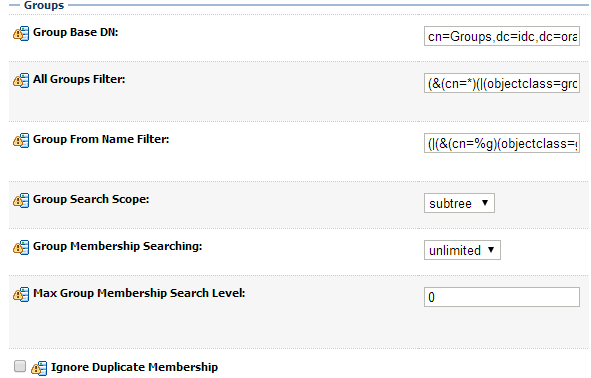
The third section contains the Groups settings for the OID provider. Use appropriate values:
| Name | Value | Purpose |
|---|---|---|
| Group Base DN: | cn=Groups,dc=idc,dc=oracle,dc=com | The root (base DN) of the LDAP tree where searches are per-formed for group data |
| All Groups Filter: | (&(cn=*)(|(objectclass=groupofUniqueNames)(objectclass=orcldynamicgroup))) -- Leave as default | The LDAP search filter that is used to show all the groups below the Group Base DN |
| Group From Name Filter: | (|(&(cn=%g)(objectclass=groupofUniqueNames))(&(cn=%g)(objectclass=orcldynamicgroup))) -- Leave as default | The LDAP search filter used to find the LDAP group by name |
| Group Search Scope: | Leave as default | Specifies how deep in the LDAP tree to search for groups |
| Group Member-ship Searching: | Leave as default | Specifies whether group searches into nested groups are limited or unlimited |
| Max Group Member-ship Search Level: | Leave as default | Specifies how many levels of group membership can be searched. This setting is only valid if GroupMembershipSearching is set to limited |
| Ignore Duplicate Membership: | Unchecked | Determines whether duplicates members are ignored when adding groups. |
Click Save.
Click Reorder to change the order of your configured authentication providers. In order to ensure that the new OID authenticator is recognized as authentication provider, you must reorder your list of authentication providers so that the OID authentication provider is first in the list.
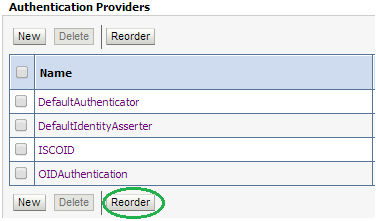
Select the OIDAuthentication and use the arrows on the right to move it into the first position. Click OK. 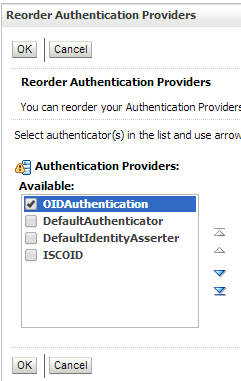
To verify the OID configuration, take the following steps:
Restart the WebLogic Server for your changes to take effect.
Using the WebLogic Administration Console, select Security Realms > myrealm > Users and Groups tab. The Users sub-tab should be selected by default. The circled users are created in OID and can verify the Provider – OIDAuthentication provider. 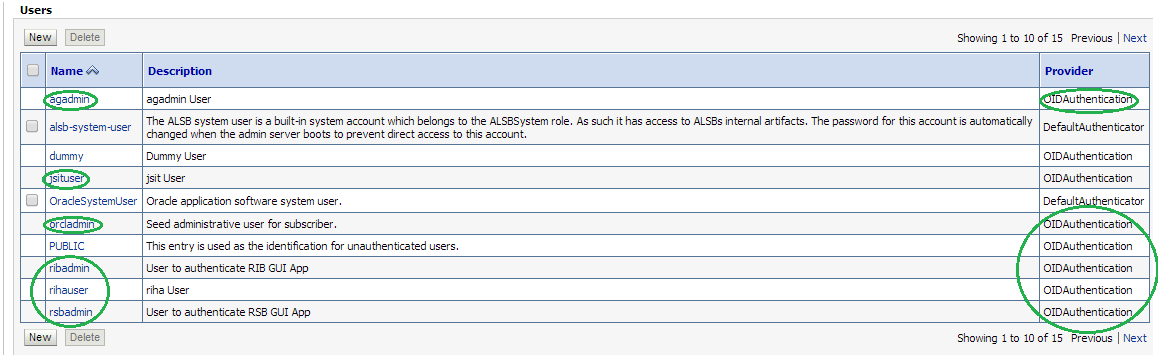
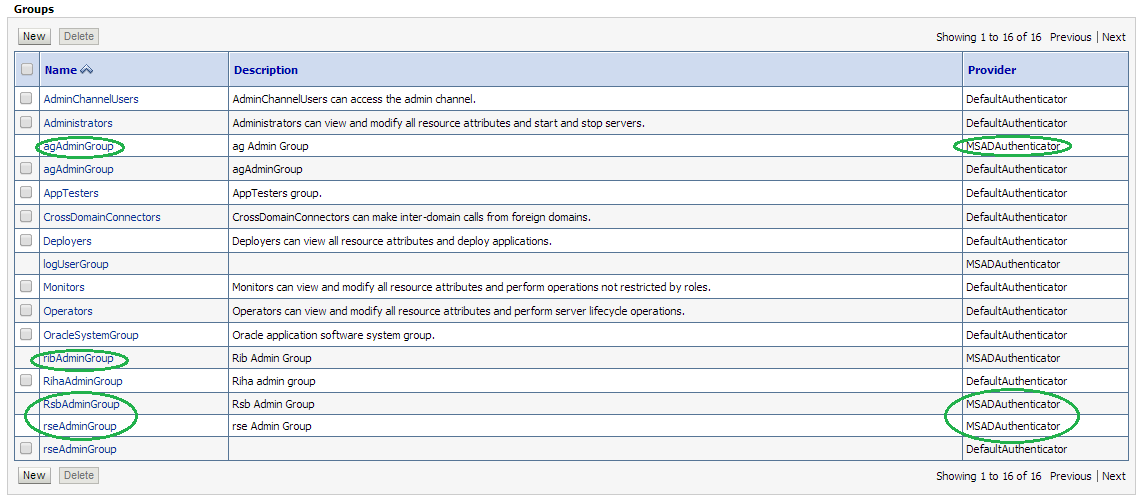
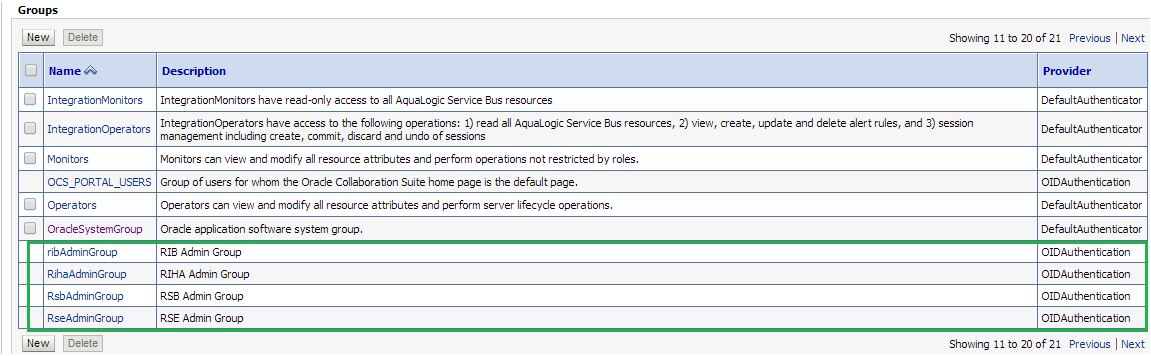
Click the Groups tab to see the list of groups the server can see. The highlighted groups are created in OID and can verify the Provider – OIDAuthentication provider.
LDIF scripts can be used to import users and groups into OID. Two sample scripts are supplied below. The scripts contain users and groups for multiple Oracle Retail integration products. You must review and edit the scripts to match your deployment topology and in-scope applications.
dn: cn=BdiJobAdminGroup,cn=groups,dc=us,dc=oracle,dc=com
objectclass: groupOfUniqueNames
objectclass: orclGroup
objectclass: top
cn: BdiJobAdminGroup
description: BDI Job Admin is a group of individuals who can start the job, view the runtime statistics of the job , stop the job and edit the configuration.
displayname: BDI Job Administrator
#businessCategory: TBD
uniquemember: cn=bdirmsjobadmin,cn=users,dc=us,dc=oracle,dc=com
uniquemember: cn=bdirxmjobadmin,cn=users,dc=us,dc=oracle,dc=com
uniquemember: cn=bdisimjobadmin,cn=users,dc=us,dc=oracle,dc=com
dn: cn=BdiJobOperatorGroup,cn=groups,dc=us,dc=oracle,dc=com
objectclass: groupOfUniqueNames
objectclass: orclGroup
objectclass: top
cn: BdiJobOperatorGroup
description: BDI Job Operator is a group of individuals who can start the job , view the runtime statistics of the job , stop the job but cannot edit the configuration.
displayname: BDI Job Operator
#businessCategory: TBD
uniquemember: cn=bdirmsjoboperator,cn=users,dc=us,dc=oracle,dc=com
uniquemember: cn=bdirxmjoboperator,cn=users,dc=us,dc=oracle,dc=com
uniquemember: cn=bdisimjoboperator,cn=users,dc=us,dc=oracle,dc=com
dn: cn=BdiJobMonitorGroup,cn=groups,dc=us,dc=oracle,dc=com
objectclass: groupOfUniqueNames
objectclass: orclGroup
objectclass: top
cn: BdiJobMonitorGroup
description: BDI Job Monitor is a group of individuals who can view the runtime statistics of the job.
displayname: BDI Job Monitor
#businessCategory: TBD
uniquemember: cn=bdirmsjobmonitor,cn=users,dc=us,dc=oracle,dc=com
uniquemember: cn=bdirxmjobmonitor,cn=users,dc=us,dc=oracle,dc=com
uniquemember: cn=bdisimjobmonitor,cn=users,dc=us,dc=oracle,dc=com
dn: cn=BdiProcessAdminGroup,cn=groups,dc=us,dc=oracle,dc=com
objectclass: groupOfUniqueNames
objectclass: orclGroup
objectclass: top
cn: BdiProcessAdminGroup
description: BDI process admin is a group of individuals who can start the process , view the runtime statistics of the process , stop the process and edit the process flows.
displayname: BDI Process Administrator
#businessCategory: TBD
uniquemember: cn=bdiprocessadmin,cn=users,dc=us,dc=oracle,dc=com
dn: cn=BdiProcessOperatorGroup,cn=groups,dc=us,dc=oracle,dc=com
objectclass: groupOfUniqueNames
objectclass: orclGroup
objectclass: top
cn: BdiProcessOperatorGroup
description: BDI process opeartor is a group of individuals who can start the process , view the runtime statistics of the process , stop the process but cannot edit the process flows.
displayname: BDI Process Opeartor
#businessCategory: TBD
uniquemember: cn=bdiprocessoperator,cn=users,dc=us,dc=oracle,dc=com
dn: cn=BdiProcessMonitorGroup,cn=groups,dc=us,dc=oracle,dc=com
objectclass: groupOfUniqueNames
objectclass: orclGroup
objectclass: top
cn: BdiProcessMonitorGroup
description: BDI process Monitor is a group of individuals who can view the runtime statistics of the process.
displayname: BDI Process Monitor
#businessCategory: TBD
niquemember: cn=bdiprocessmonitor,cn=users,dc=us,dc=oracle,dc=com
dn: cn=BdiSchedulerAdminGroup,cn=groups,dc=us,dc=oracle,dc=com
objectclass: groupOfUniqueNames
objectclass: orclGroup
objectclass: top
cn: BdiSchedulerAdminGroup
description: BDI scheduler admin is a group of individuals who can start/stop the schedule , view the summary of scheduled runs metrics and schedule details.Also create, edit, delete/disable the schedules.
displayname: BDI Scheduler Administrator
#businessCategory: TBD
uniquemember: cn=bdischeduleradmin,cn=users,dc=us,dc=oracle,dc=com
dn: cn=BdiSchedulerOperatorGroup,cn=groups,dc=us,dc=oracle,dc=com
objectclass: groupOfUniqueNames
objectclass: orclGroup
objectclass: top
cn: BdiSchedulerOperatorGroup
description: BDI scheduler Operator is a group of individuals who can start/stop the schedule , view the summary of scheduled runs metrics and schedule details.
displayname: BDI Scheduler Operator
#businessCategory: TBD
uniquemember: cn=bdischeduleroperator,cn=users,dc=us,dc=oracle,dc=com
dn: cn=BdiSchedulerMonitorGroup,cn=groups,dc=us,dc=oracle,dc=com
objectclass: groupOfUniqueNames
objectclass: orclGroup
objectclass: top
cn: BdiSchedulerMonitorGroup
description: BDI scheduler monitor is a group of individuals who can view the summary of scheduled runs metrics and schedule details.
displayname: BDI Scheduler Monitor
#businessCategory: TBD
uniquemember: cn=bdischedulermonitor,cn=users,dc=us,dc=oracle,dc=com
dn: cn=agAdminGroup,cn=groups,dc=us,dc=oracle,dc=com
objectclass: groupOfUniqueNames
objectclass: orclGroup
objectclass: top
cn: agAdminGroupdescription: ArtifactGenerator Administrator is a group of individuals who can generate artifacts used in the integration products like OracleObject, JavaBeans. displayname: ArtifactGenerator Administrator#businessCategory: TBDuniquemember: cn=agadmin,cn=users,dc=us,dc=oracle,dc=comdn: cn=JmsConsoleAdminGroup,cn=groups,dc=us,dc=oracle,dc=comobjectclass: groupOfUniqueNamesobjectclass: orclGroupobjectclass: topcn: JmsConsoleAdminGroupdescription: JMS Console Administrator is a group of individuals who can perform various administrator task on jmsconsole like publishing message on topic, browsing messages on topic.displayname: JMS Console Administrator#businessCategory: TBDuniquemember: cn=jmsconsoleadmin,cn=users,dc=us,dc=oracle,dc=comdn: cn=ribAdminGroup,cn=groups,dc=us,dc=oracle,dc=comobjectclass: groupOfUniqueNamesobjectclass: orclGroupobjectclass: topcn: ribAdminGroupdescription: RIB Administrator is a group of individuals who can administrator rib-admin-gui. View the adapters state, start/stop adapters, view logs,set the log levels for adapters. displayname: RIB Administrator#businessCategory: TBDuniquemember: cn=ribrmsadmin,cn=users,dc=us,dc=oracle,dc=comuniquemember: cn=ribsimadmin,cn=users,dc=us,dc=oracle,dc=comuniquemember: cn=ribrwmsadmin,cn=users,dc=us,dc=oracle,dc=comuniquemember: cn=ribaipadmin,cn=users,dc=us,dc=oracle,dc=comuniquemember: cn=ribomsadmin,cn=users,dc=us,dc=oracle,dc=comuniquemember: cn=ribrxmadmin,cn=users,dc=us,dc=oracle,dc=comuniquemember: cn=ribtafradmin,cn=users,dc=us,dc=oracle,dc=comuniquemember: cn=ribrfmadmin,cn=users,dc=us,dc=oracle,dc=comuniquemember: cn=ribrpmadmin,cn=users,dc=us,dc=oracle,dc=comdn: cn=IntegrationGroup,cn=groups,dc=us,dc=oracle,dc=comobjectclass: groupOfUniqueNamesobjectclass: orclGroupobjectclass: topcn: IntegrationGroupdescription: IntegrationGroup is a group of individuals who can invoke rib interface api inject and publish.displayname: Integration Group#businessCategory: TBDuniquemember: cn=integrationuser,cn=users,dc=us,dc=oracle,dc=comdn: cn=RihaAdminGroup,cn=groups,dc=us,dc=oracle,dc=comobjectclass: groupOfUniqueNamesobjectclass: orclGroupobjectclass: topcn: RihaAdminGroupdescription: Riha Admin Group is a group of individuals who can administer rib hospital. Can flush the messages stuck in rib error hospital, can retry the messages,view the messages in error hospital and can edit.displayname: Riha Administrator #businessCategory: TBDuniquemember: cn=rihaadmin,cn=users,dc=us,dc=oracle,dc=comdn: cn=RicAdminGroup,cn=groups,dc=us,dc=oracle,dc=comobjectclass: groupOfUniqueNamesobjectclass: orclGroupobjectclass: topcn: RicAdminGroupdescription: Ric Admin Group is a group of individuals who can administer rib runtime statistics , rsb runtime statistics.displayname: Ric Administrator#businessCategory: TBDuniquemember: cn=ricadmin,cn=users,dc=us,dc=oracle,dc=comdn: cn=rseAdminGroup,cn=groups,dc=us,dc=oracle,dc=comobjectclass: groupOfUniqueNamesobjectclass: orclGroupobjectclass: topcn: rseAdminGroupdescription: Rse Admin Group is a group of individuals who can generate webservice provider , consumer.displayname: RSE Administrator#businessCategory: TBDuniquemember: cn=rseadmin,cn=users,dc=us,dc=oracle,dc=comdn: cn=RfiAdminGroup,cn=groups,dc=us,dc=oracle,dc=comobjectclass: groupOfUniqueNamesobjectclass: orclGroupobjectclass: topcn: RfiAdminGroupdescription: RFI Admin displayname: RFI Administrator#businessCategory: TBDuniquemember: cn=rfiadmin,cn=users,dc=us,dc=oracle,dc=com
dn: cn=bdirmsjobadmin, cn=Users,dc=us,dc=oracle,dc=com
description: A user for the 'BDI Job Admin' role.
objectclass: inetOrgPerson
objectclass: organizationalPerson
objectclass: person
objectclass: top
objectclass: orcluser
objectclass: orcluserV2
objectclass: orclIDXPerson
cn: bdirmsjobadmin
orclsamaccountname: bdirmsjobadmin
sn: bdirmsjobadmin
uid: bdirmsjobadmin
givenname: bdirmsjobadmin
displayname: bdirmsjobadmin
userpassword: <update your password here>
employeeNumber:
middleName:
orclHireDate:
telephoneNumber:
facsimileTelephoneNumber:
mail: bdirmsjobadmin@example.com
postalAddress:
street:
postalCode:
title:
employeeType:
dn: cn=bdirxmjobadmin, cn=Users,dc=us,dc=oracle,dc=com
description: A user for the 'BDI Job Admin' role.
objectclass: inetOrgPerson
objectclass: organizationalPerson
objectclass: person
objectclass: top
objectclass: orcluser
objectclass: orcluserV2
objectclass: orclIDXPerson
cn: bdirxmjobadmin
orclsamaccountname: bdirxmjobadmin
sn: bdirxmjobadmin
uid: bdirxmjobadmin
givenname: bdirxmjobadmin
displayname: bdirxmjobadmin
userpassword: <update your password here>
employeeNumber:
middleName:
orclHireDate:
telephoneNumber:
facsimileTelephoneNumber:
mail: bdirxmjobadmin@example.com
postalAddress:
street:
postalCode:
title:
employeeType:
dn: cn=bdisimjobadmin, cn=Users,dc=us,dc=oracle,dc=com
description: A user for the 'BDI Job Admin' role.
objectclass: inetOrgPerson
objectclass: organizationalPerson
objectclass: person
objectclass: top
objectclass: orcluser
objectclass: orcluserV2
objectclass: orclIDXPerson
cn: bdisimjobadmin
orclsamaccountname: bdisimjobadmin
sn: bdisimjobadmin
uid: bdisimjobadmin
givenname: bdisimjobadmin
displayname: bdisimjobadmin
userpassword: <update your password here>
employeeNumber:
middleName:
orclHireDate:
telephoneNumber:
facsimileTelephoneNumber:
mail: bdisimjobadmin@example.com
postalAddress:
street:
postalCode:
title:
employeeType:
dn: cn=bdirmsjoboperator, cn=Users,dc=us,dc=oracle,dc=com
description: A user for the 'BDI Job Operator' role.
objectclass: inetOrgPerson
objectclass: organizationalPerson
objectclass: person
objectclass: top
objectclass: orcluser
objectclass: orcluserV2
objectclass: orclIDXPerson
cn: bdirmsjoboperator
orclsamaccountname: bdirmsjoboperator
sn: bdirmsjoboperator
uid: bdirmsjoboperator
givenname: bdirmsjoboperator
displayname: bdirmsjoboperator
userpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: bdirmsjoboperator@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=bdirxmjoboperator, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'BDI Job Operator' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: bdirxmjoboperatororclsamaccountname: bdirxmjoboperatorsn: bdirxmjoboperatoruid: bdirxmjoboperatorgivenname: bdirxmjoboperatordisplayname: bdirxmjoboperatoruserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: bdirxmjoboperator@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=bdisimjoboperator, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'BDI Job Operator' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: bdisimjoboperatororclsamaccountname: bdisimjoboperatorsn: bdisimjoboperatoruid: bdisimjoboperatorgivenname: bdisimjoboperatordisplayname: bdisimjoboperatoruserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: bdisimjoboperator@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=bdirmsjobmonitor, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'BDI Job Monitor' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: bdirmsjobmonitororclsamaccountname: bdirmsjobmonitorsn: bdirmsjobmonitoruid: bdirmsjobmonitorgivenname: bdirmsjobmonitordisplayname: bdirmsjobmonitoruserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: bdirmsjobmonitor@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=bdirxmjobmonitor, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'BDI Job Monitor' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: bdirxmjobmonitororclsamaccountname: bdirxmjobmonitorsn: bdirxmjobmonitoruid: bdirxmjobmonitorgivenname: bdirxmjobmonitordisplayname: bdirxmjobmonitoruserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: bdirxmjobmonitor@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=bdisimjobmonitor, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'BDI Job Monitor' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: bdisimjobmonitororclsamaccountname: bdisimjobmonitorsn: bdisimjobmonitoruid: bdisimjobmonitorgivenname: bdisimjobmonitordisplayname: bdisimjobmonitoruserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: bdisimjobmonitor@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=bdiprocessadmin, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'BDI Process Admin' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: bdiprocessadminorclsamaccountname: bdiprocessadminsn: bdiprocessadminuid: bdiprocessadmingivenname: bdiprocessadmindisplayname: bdiprocessadminuserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: bdiprocessadmin@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=bdiprocessoperator, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'BDI Process Operator' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: bdiprocessoperatororclsamaccountname: bdiprocessoperatorsn: bdiprocessoperatoruid: bdiprocessoperatorgivenname: bdiprocessoperatordisplayname: bdiprocessoperatoruserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: bdiprocessoperator@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=bdiprocessmonitor, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'BDI Process Monitor' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: bdiprocessmonitororclsamaccountname: bdiprocessmonitorsn: bdiprocessmonitoruid: bdiprocessmonitorgivenname: bdiprocessmonitordisplayname: bdiprocessmonitoruserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: bdiprocessmonitor@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=bdischeduleradmin, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'BDI Scheduler Admin' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: bdischeduleradminorclsamaccountname: bdischeduleradminsn: bdischeduleradminuid: bdischeduleradmingivenname: bdischeduleradmindisplayname: bdischeduleradminuserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: bdischeduleradmin@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=bdischeduleroperator, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'Bdi Scheduler Operator' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: bdischeduleroperatororclsamaccountname: bdischeduleroperatorsn: bdischeduleroperatoruid: bdischeduleroperatorgivenname: bdischeduleroperatordisplayname: bdischeduleroperatoruserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: bdischeduleroperator@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=bdischedulermonitor, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'Bdi Scheduler Monitor' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: bdischedulermonitororclsamaccountname: bdischedulermonitorsn: bdischedulermonitoruid: bdischedulermonitorgivenname: bdischedulermonitordisplayname: bdischedulermonitoruserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: bdischedulermonitor@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=agadmin, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'AG Admin' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: agadminorclsamaccountname: agadminsn: agadminuid: agadmingivenname: agadmindisplayname: agadminuserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: agadmin@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=jmsconsoleadmin, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'JMS Console Admin' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: jmsconsoleadminorclsamaccountname: jmsconsoleadminsn: jmsconsoleadminuid: jmsconsoleadmingivenname: jmsconsoleadmindisplayname: jmsconsoleadminuserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: jmsconsoleadmin@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=ribrmsadmin, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'RIB Admin' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: ribrmsadminorclsamaccountname: ribrmsadminsn: ribrmsadminuid: ribrmsadmingivenname: ribrmsadmindisplayname: ribrmsadminuserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: ribrmsadmin@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=ribrpmadmin, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'RIB Admin' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: ribrpmadminorclsamaccountname: ribrpmadminsn: ribrpmadminuid: ribrpmadmingivenname: ribrpmadmindisplayname: ribrpmadminuserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: ribrpmadmin@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=ribrxmadmin, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'RIB Admin' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: ribrxmadminorclsamaccountname: ribrxmadminsn: ribrxmadminuid: ribrxmadmingivenname: ribrxmadmindisplayname: ribrxmadminuserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: ribrxmadmin@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=ribrwmsadmin, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'RIB Admin' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: ribrwmsadminorclsamaccountname: ribrwmsadminsn: ribrwmsadminuid: ribrwmsadmingivenname: ribrwmsadmindisplayname: ribrwmsadminuserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: ribrwmsadmin@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=ribomsadmin, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'RIB Admin' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: ribomsadminorclsamaccountname: ribomsadminsn: ribomsadminuid: ribomsadmingivenname: ribomsadmindisplayname: ribomsadminuserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: ribomsadmin@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=ribtafradmin, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'RIB Admin' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: ribtafradminorclsamaccountname: ribtafradminsn: ribtafradminuid: ribtafradmingivenname: ribtafradmindisplayname: ribtafradminuserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: ribtafradmin@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=ribaipadmin, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'RIB Admin' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: ribaipadminorclsamaccountname: ribaipadminsn: ribaipadminuid: ribaipadmingivenname: ribaipadmindisplayname: ribaipadminuserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: ribaipadmin@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=ribsimadmin, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'RIB Admin' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: ribsimadminorclsamaccountname: ribsimadminsn: ribsimadminuid: ribsimadmingivenname: ribsimadmindisplayname: ribsimadminuserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: ribsimadmin@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=ribrfmadmin, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'RIB Admin' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: ribrfmadminorclsamaccountname: ribrfmadminsn: ribrfmadminuid: ribrfmadmingivenname: ribrfmadmindisplayname: ribrfmadminuserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: ribrfmadmin@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=integrationuser, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'Integration' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: integrationuserorclsamaccountname: integrationusersn: integrationuseruid: integrationusergivenname: integrationuserdisplayname: integrationuseruserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: integrationuser@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=rihaadmin, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'RIHA Admin' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: rihaadminorclsamaccountname: rihaadminsn: rihaadminuid: rihaadmingivenname: rihaadmindisplayname: rihaadminuserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: rihaadmin@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=ricadmin, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'RIC Admin' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: ricadminorclsamaccountname: ricadminsn: ricadminuid: ricadmingivenname: ricadmindisplayname: ricadminuserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: ricadmin@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=rseadmin, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'RSE Admin' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: rseadminorclsamaccountname: rseadminsn: rseadminuid: rseadmingivenname: rseadmindisplayname: rseadminuserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: rseadmin@example.compostalAddress:street:postalCode:title:employeeType:dn: cn=rfiadmin, cn=Users,dc=us,dc=oracle,dc=comdescription: A user for the 'RFI Admin' role.objectclass: inetOrgPersonobjectclass: organizationalPersonobjectclass: personobjectclass: topobjectclass: orcluserobjectclass: orcluserV2objectclass: orclIDXPersoncn: rfiadminorclsamaccountname: rfiadminsn: rfiadminuid: rfiadmingivenname: rfiadmindisplayname: rfiadminuserpassword: <update your password here>employeeNumber:middleName:orclHireDate:telephoneNumber:facsimileTelephoneNumber:mail: rfiadmin@example.compostalAddress:street:postalCode:title:employeeType:
To configure the AD as an authentication provider in WebLogic, take the following steps:
Login to WebLogic Console -> Security Realm -> myrealm.
Select tab Providers -> Authentication -> Default Provider (DefaultAuthenticator).Change the Control Flag (JAAS Flag) from REQUIRED to SUFFICIENT and click Save.
Click New to add a new Authentication Provider.Enter MSADAuthenticator as the Name. Select ActiveDirectoryAuthenticator as the Type and click OK. 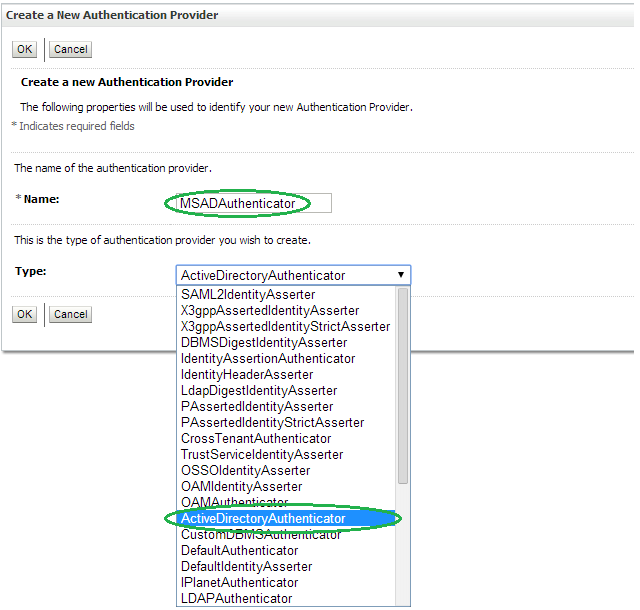
Change the Control Flag to SUFFICIENT for the MSADAuthenticator Provider added and click Save. 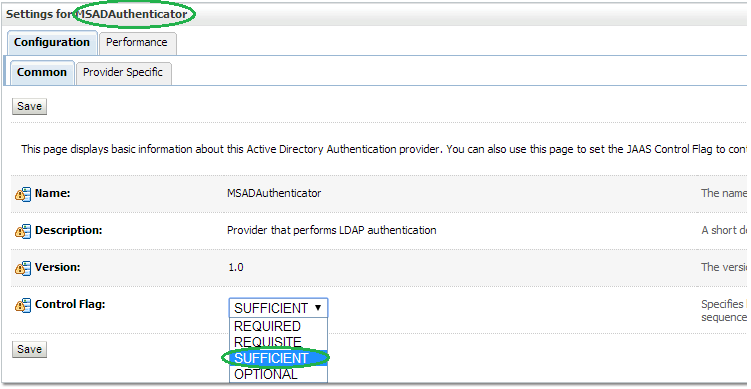
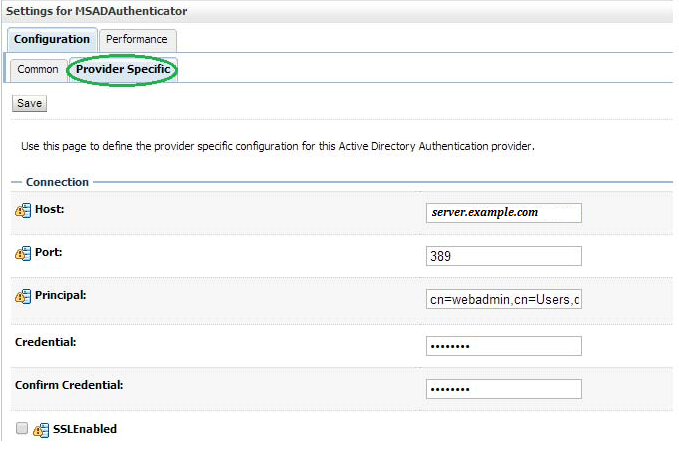
Select Provider Specific tab and enter the Active Directory (AD) server details.
The first section contains the Connection settings for the AD server. Use appropriate values based on where AD is hosted and the credentials:
| Name | Value | Purpose |
|---|---|---|
| Host: | server.example.com | The AD host name |
| Port: | 389 | The standard AD listening port |
| Principal: | cn=webadmin,cn=Users,dc=us,dc=oracle,dc=com | The LDAP user that logs into AD on behalf of your authentication provider |
| Credentials: | Password for the principal user | |
| Confirm Credentials: | Confirmation of the password | |
| SSL Enabled: | Unchecked | Enables or disables SSL connectivity |
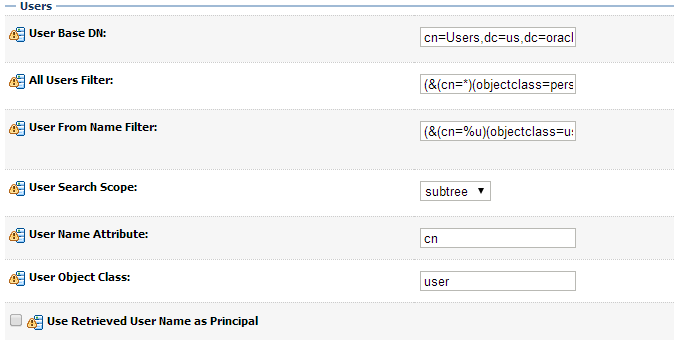
The second section contains the Users settings for the AD provider. Use appropriate values:
| Name | Value | Purpose |
|---|---|---|
| User Base DN: | cn=Users,dc=us,dc=oracle,dc=com | The root (base DN) of the LDAP tree where searches are performed for user data |
| All Users Filter: | (&(cn=*)(objectclass=person)) | The LDAP search filter that is used to show all the users below the User Base DN |
| User From Name Filter: | (&(cn=%u)(objectclass=user)) | The LDAP search filter used to find the LDAP user by name |
| User Search Scope: | Leave as default | Specifies how deep in the LDAP tree to search for users |
| User Name Attribute: | Leave as default | The attribute of the LDAP user that specifies the user name |
| User Object Class: | Leave as default | The LDAP object class that stores users |
| Use Retrieved User Name as Principal: | Unchecked | Specifies if the user name retrieved from the LDAP directory will be used as the Principal in the Subject |
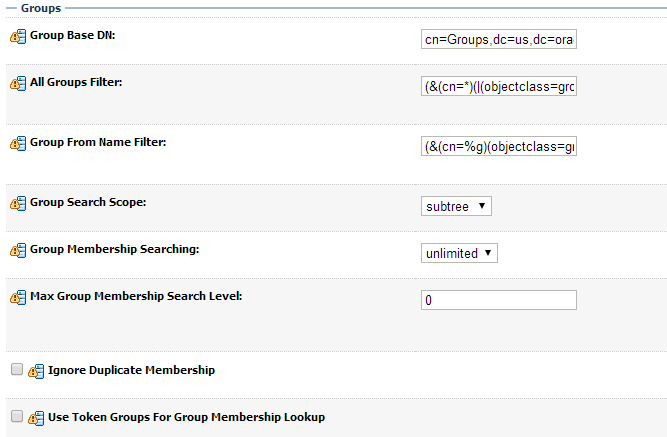
The third section contains the Groups settings for the AD provider. Use appropriate values:
| Name | Value | Purpose |
|---|---|---|
| Group Base DN: | cn=Groups,dc=us,dc=oracle,dc=com | The root (base DN) of the LDAP tree where searches are performed for group data |
| All Groups Filter: | (&(cn=*)(|(objectclass=group))) | The LDAP search filter that is used to show all the groups below the Group Base DN |
| Group From Name Filter: | (&(cn=%g)(objectclass=group)) | The LDAP search filter used to find the LDAP group by name |
| Group Search Scope: | Leave as default | Specifies how deep in the LDAP tree to search for groups |
| Group Member-ship Searching: | Leave as default | Specifies whether group searches into nested groups are limited or unlimited |
| Max Group Membership Search Level: | Leave as default | Specifies how many levels of group membership can be searched. This setting is only valid if GroupMembershipSearching is set to limited |
| Ignore Duplicate Membership: | Unchecked | Determines whether duplicates members are ignored when adding groups. |
Click Save.
Click Reorder to change the order of your configured authentication providers. In order to ensure that MSAD authenticator is recognized as authentication provider, you must reorder your list of authentication providers so that the MSAD authentication provider is first in the list. 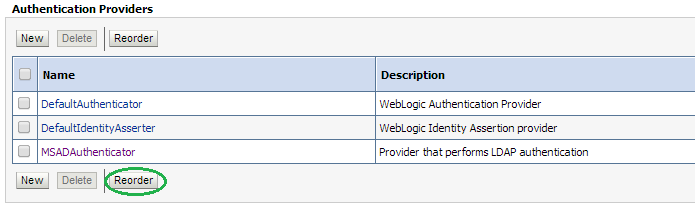
Select the MSADAuthenticator and use the arrows on the right to move it into the first position. Click OK. 
Click Reorder to change the order of your configured authentication providers. In order to ensure that MSAD authenticator is recognized as authentication provider, you must reorder your list of authentication providers so that the MSAD authentication provider is first in the list. 
Select the MSADAuthenticator and use the arrows on the right to move it into the first position. Click OK. 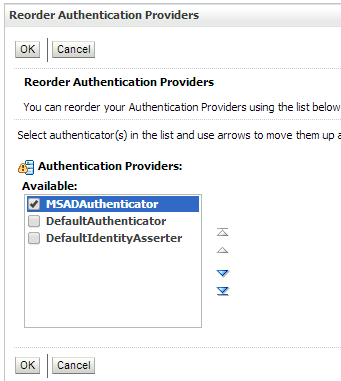
To verify the AD configuration, take the following steps:
Restart the WebLogic Server for your changes to take effect.
Using the WebLogic Administration Console, select Security Realms > myrealm > Users and Groups tab. The Users sub-tab should be selected by default. The circled users are created in AD and can verify the Provider – MSADAuthenticator provider. 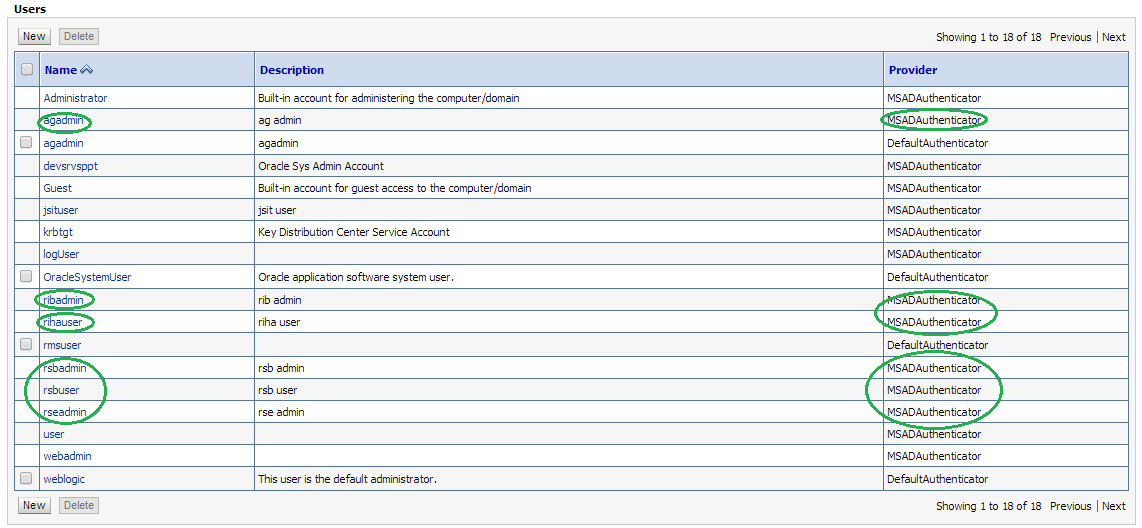
Click the Groups tab to see the list of groups the server can see. The highlighted groups are created in AD and can verify the Provider – MSADAuthenticator provider.