| Oracle® Identity Manager Connector Framework Guide Release 9.0.1 Part Number B31142-01 |
|
|
View PDF |
| Oracle® Identity Manager Connector Framework Guide Release 9.0.1 Part Number B31142-01 |
|
|
View PDF |
Oracle Identity Manager automates access rights management, security, and provisioning of IT resources. This chapter provides an overview of Oracle Identity Manager.
This chapter is divided into the following sections:
Oracle Identity Manager is based on the n-tier J2EE application architecture. Figure 1-1 illustrates the architecture of Oracle Identity Manager.
Figure 1-1 Architecture of Oracle Identity Manager
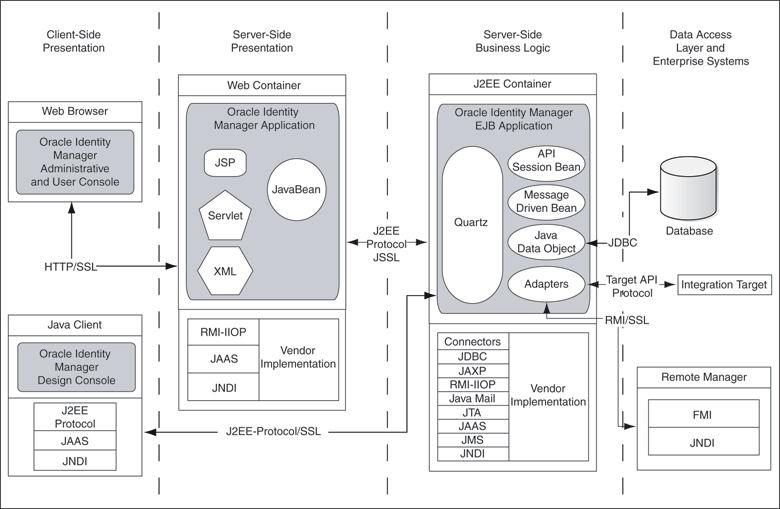
This section discusses the following tiers of the Oracle Identity Manager architecture:
The Presentation layer consists of two clients: the Oracle Identity Manager Administrative and User Console and the Oracle Identity Manager Design Console. The Administrative and User Console is a Web-based thin client that can be accessed from any Web browser. This console provides user self-service and delegated administration features that serve most of the provisioning requirements.
The Design Console provides the full range of the Oracle Identity Manager system configuration and development capabilities including Form Designer, Workflow Designer, and the Adapter Factory. You can access the Design Console by using a desktop Java client.
Because both the Administrative and User Console and the Design Console are highly dynamic, the Dynamic Presentation Logic layer guides the content displayed on these interfaces. In the case of the Administrative and User Console, there is a clear separation between the Presentation and Presentation Logic Layer. No such boundary exists in the Design Console.
The Business Logic layer is implemented as an EJB application. Oracle Identity Manager runs on leading J2EE-compliant application server platforms, leveraging the J2EE services provided by these application servers to deliver a high-performance, fault-tolerant enterprise application.
The following are components of the Business Logic layer:
The application server on which Oracle Identity Manager runs provides life-cycle management, security, deployment, and run-time services to the logical components that make up Oracle Identity Manager. These services include:
Scalable management of resources (clustering and failover)
Transaction management
Security management
Client access
Technology resources (such as database connection pooling and messaging)
The core functionality of the Oracle Identity Manager platform is implemented in Java using a highly modular, object-oriented methodology. This includes the various engines that comprise the Oracle Identity Manager platform: Workflow Engine, Request Engine, User Management Engine, Rule Engine, and Reconciliation Engine. It also includes the integration layer based on the Adapter Factory, which dynamically generates integration code based on the metadata definition of the adapters.
Access to the functionality of the platform is through a set of EJB Beans. These session beans can be divided into two types:
Nonpublished APIs: These are session beans that expose functionality used only by the Design Console.
Published Public APIs: These are session beans that expose the public functionality of Oracle Identity Manager.
The API layer provides access to high-level functionality in Oracle Identity Manager. It is the basis for the functionality implemented in the Oracle Identity Manager Administrative and User Console. It is also the interface that custom clients can use to access Oracle Identity Manager functionality.
J2EE contains several technologies for manipulating and interacting with transactional resources (such as databases) that are based on JDBC, JTA, and JTS. The Oracle Identity Manager architecture leverages the following J2EE services:
Database connection pooling
Integration with JNDI (lookup of DataSources in the JNDI namespace)
XA compliance
Batch updates
The system administrator can manage data sources in the same manner in which all standard J2EE applications in the enterprise are managed. Oracle Identity Manager can use these data sources to communicate with the database tier.
The Backend System Integration layer can be divided into the following:
The Database tier consists of the Oracle Identity Manager repository, which manages and stores Oracle Identity Manager metadata in an ANSI SQL 92-compliant relational database. All the data resides in the Oracle Identity Manager repository.
The Remote Manager is an Oracle Identity Manager server component that runs on a target system computer. It provides the network and security layer required to integrate with applications that do not have network-aware APIs or do not provide security. It is built as a lightweight RMI server. The communication protocol is RMI tunneled over HTTP/S.
The J2EE RMI framework enables the creation of virtually transparent, distributed services and applications. RMI-based applications consist of Java objects making method calls to one another, regardless of their location. This enables one Java object to call methods on another Java object residing on another virtual computer in the same manner in which methods are called on a Java object residing on the same virtual computer.
This section discusses the following deployment configurations of Oracle Identity Manager:
You can use Oracle Identity Manager to create, maintain, and delete accounts on target systems. Oracle Identity Manager becomes the front-end entry point for managing all the accounts on these systems. After the accounts are provisioned, the users for whom accounts have been provisioned are able to access the target systems without any interaction with Oracle Identity Manager. This is the provisioning configuration of Oracle Identity Manager.
The purpose of provisioning is to automate the creation and maintenance of user accounts on target systems. Provisioning is also used to accommodate any requirement for workflow approvals and auditing that may be a component of that provisioning lifecycle.
Figure 1-2 illustrates the provisioning configuration.
Figure 1-2 Provisioning Configuration of Oracle Identity Manager
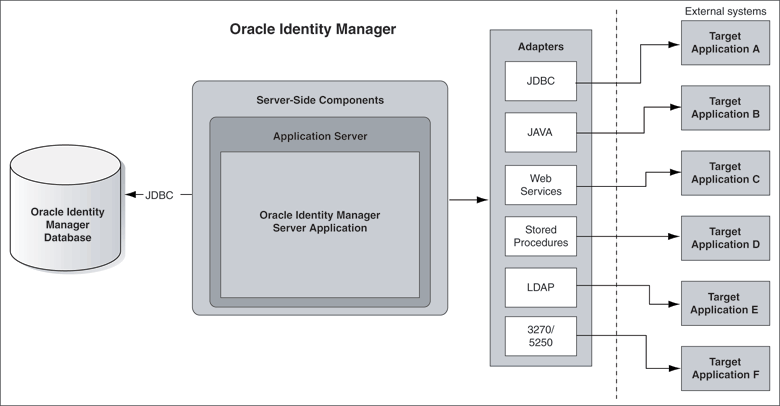
Provisioning events are initiated either through requests or by direct provisioning.
A request can be manually created by an administrator or, in certain cases, by target users themselves. Oracle Identity Manager automatically creates requests for some events. For example, a request is automatically created when Oracle Identity Manager enforces the requirements of an access policy. You can also use Oracle Identity Manager to create approval processes that can be run as part of the request-based provisioning cycle.
Direct provisioning is a special administrator-only function that lets you create an account for a particular user on a target application without having to wait for any workflow or approval processes.
Oracle Identity Manager provides a centralized control mechanism to manage user accounts and entitlements and to control user access to resources. However, you may choose not to use Oracle Identity Manager as the primary repository or front-end entry point of your user accounts. Instead, you may decide to use Oracle Identity Manager to periodically poll your system applications in order to maintain an accurate profile of all accounts that exist on those systems. This is the reconciliation configuration of Oracle Identity Manager.
Figure 1-3 illustrates the reconciliation configuration.
Figure 1-3 Reconciliation Configuration of Oracle Identity Manager
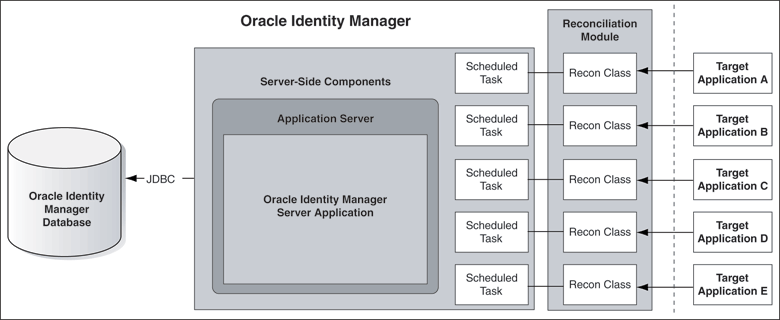
In this configuration, Oracle Identity Manager is used only as an archive for all account management actions that are performed on the target system. It is assumed that user accounts are created, deleted, and maintained by the local resource-specific administrators.
Reconciliation involves using the user discovery and account discovery features of Oracle Identity Manager.
User discovery is the process of recognizing the existence of a user account on a primary database. The primary database is the repository that is considered to contain the master list of user accounts. Within the context of user discovery and reconciliation, the primary database is also referred to as the trusted source or authoritative source. There may be more than one trusted source for each Oracle Identity Manager environment.
Account discovery is the process of recognizing changes to user-related information on resources. If the information that is changed affects the user's primary record, it is generally a change associated with a trusted source. If the information that is changed is related to a user's access to a resource, it is generally a change associated with a target resource.
The following are different forms of reconciliation:
You can use Oracle Identity Manager to perform a single, one-time reconciliation with a legacy target system. The purpose of this form of reconciliation is to import all accounts on that system into Oracle Identity Manager. After one-time reconciliation is performed, you can use Oracle Identity Manager to provision accounts for your users.
Figure 1-4 illustrates the steps involved in target resource reconciliation.
Figure 1-4 Target Resource Reconciliation
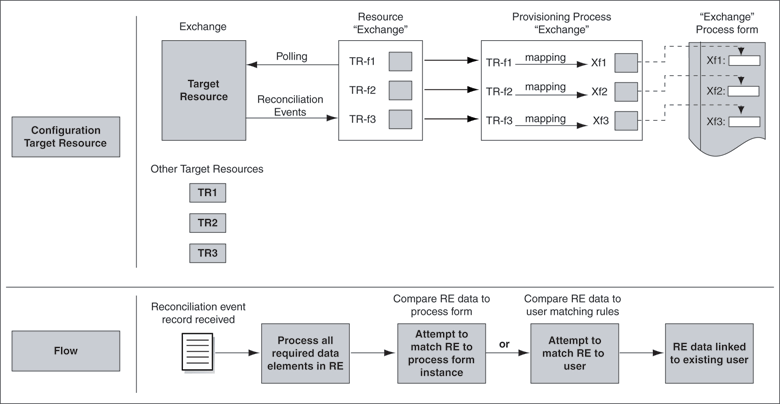
Figure 1-5 illustrates the steps involved in trusted source reconciliation.
Figure 1-6 illustrates the provisioning and reconciliation configuration in which you use Oracle Identity Manager to perform both provisioning and reconciliation activities. In this configuration, it is assumed that you allow accounts on target systems to be created and maintained by both local administrators and Oracle Identity Manager.
Figure 1-6 Provisioning and Reconciliation Configuration of Oracle Identity Manager
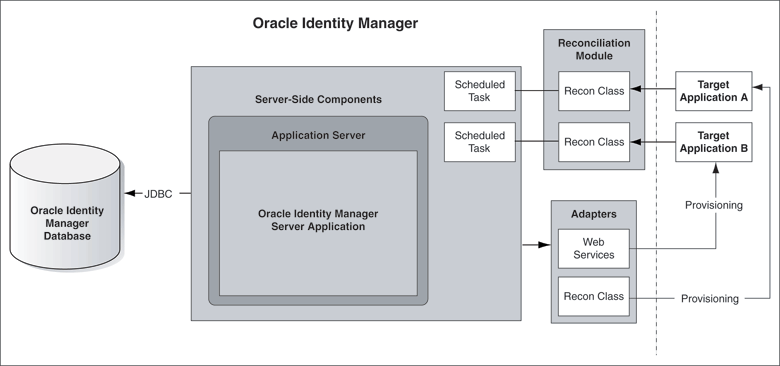
To achieve this configuration, you must perform all the steps associated with setting up both provisioning and reconciliation.
The following are the features of Oracle Identity Manager:
Scalable architecture
Oracle Identity Manager is based on open, standards-based technology. The J2EE application server model of Oracle Identity Manager offers scalability, failover, load-balancing, and built-in Web deployment features.
Comprehensive user management
Oracle Identity Manager can support unlimited user organizational hierarchies and user groups with inheritance, customizable user ID policy management, password policy management, and user access policies. It also offers the feature of delegated administration with comprehensive permission settings. You can use Oracle Identity Manager to maintain a resource allocation history and to manage application parameters and entitlements.
Web-based user self-service
Oracle Identity Manager contains a user self-service portal that is customizable and Web based. This portal can be used to manage user information, change and synchronize passwords, reset passwords, request access to applications, review and edit entitlements, and work on workflow tasks.
Flexible process engine
Using Oracle Identity Manager, you can create business and provisioning process models in applications like Microsoft Project and Microsoft Visio. Process models include support for approval workflows and escalations. You can track the progress of each provisioning event in the workflow.
Oracle Identity Manager provides support for complex branching, self-healing processes, and nested processes with data interchange and dependencies. The process flow can be customized without making code changes.
Comprehensive reporting for audit-trail accounting
Oracle Identity Manager provides status reports on all processes with full-state information, in real time. In addition, it even offers OLAP features.
Automated tool for connector management
Oracle Identity Manager provides an automated tool for connector generation. This tool, which is known as the Adapter Factory, supports a wide range of interfaces, applications, and devices. The adapters generated by the Adapter Factory run on the Oracle Identity Manager server, and they do not require any agents to be installed or updated on the target systems. The use of the Adapter Factory helps speed up the process of connector development and simplifies the task of updating existing connectors.
If the target system does not have a network-enabled interface, you can use the Oracle Identity Manager Remote Manager to provide an SSL-secured network communication channel and interface to local APIs that are not running on the Oracle Identity Manager server. By using the Remote Manager, you can run functions on target systems having APIs that are not network aware.
Built-in change management
Oracle Identity Manager enables you to package new processes, import and export existing processes, and move packages from one system to another.