| Oracle® Identity Manager Connector Guide for IBM RACF Advanced Release 9.0.3 Part Number B32378-01 |
|
|
View PDF |
| Oracle® Identity Manager Connector Guide for IBM RACF Advanced Release 9.0.3 Part Number B32378-01 |
|
|
View PDF |
This appendix describes the IBM RACF Advanced Connector functionality in detail in the following sections:
The architecture for Oracle Identity Manager Advanced Connector begins with the Oracle Identity Manager LDAP Gateway. The LDAP Gateway is built on Java 1.4.2, allowing for portability across different platforms and operating systems and complete integration with the Oracle Identity Manager system.
The LDAP Gateway works transparently with Oracle Identity Manager to communicate with IBM RACF Advanced facilities in a z/OS environment. The LDAP Gateway is installed along with Oracle Identity Manager on the same server. In addition, the Reconciliation Agent enables the LDAP Gateway server to become a subscriber to security and identity events from IBM RACF Advanced.
Oracle Identity Manager maps mainframe authentication repositories by the LDAP DN. By changing the LDAP DN, different authentication repositories and different mainframe resources can be addressed.
The Provisioning Agent is a mainframe component, receiving native mainframe IBM RACF Advanced provisioning commands from the LDAP Gateway. These requests are processed against the IBM RACF Advanced authentication repository with the response parsed and returned to the LDAP Gateway.
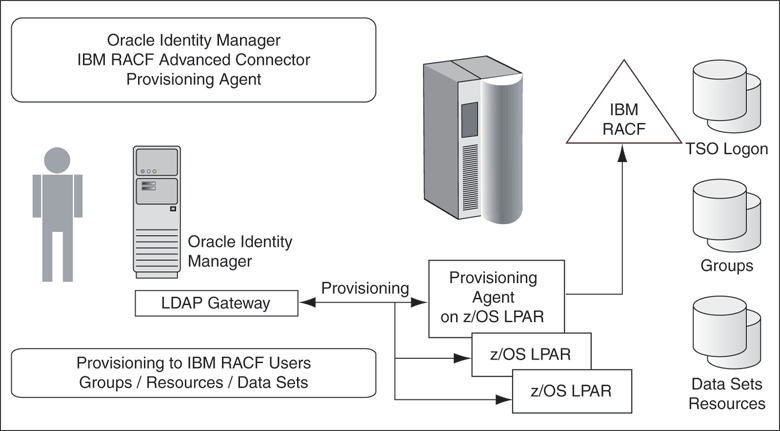
The Provisioning Agent includes LDAP bind and authorization requests. In addition to traditional provisioning functions, the Provisioning Agent can also build the necessary TSO logon functions, including the building CLIST files, and working to replicate existing mainframe user profile scenarios. Provisioning Agent can also extend authorization to data sets, groups, and resources through enterprise rules set in by Oracle Identity Manager.
Internal to mainframe architecture is significant communication of connector resources and internal mainframe memory subpools for enterprise loads at peak times, supporting over a million transactions per day. The entire Provisioning Agent is protected by AES 128 encryption and APF authorized resources.
The Provisioning Agent receives Identity and Authorization change events, and effects requested changes on the z/OS mainframe authentication repository, IBM RACF Advanced. The Provisioning Agent is a mainframe-installed component that receives native mainframe requests from the LDAP Gateway.
An important architectural feature of the Provisioning Agent is that provisioning updates are made from the LDAP Gateway to the IBM RACF Advanced authentication repository. As such, the Provisioning Agent needs to be installed on at least one z/OS LPAR. Provisioning commands sent from Oracle Identity Manager then change authentication and authorization across all LPARS serviced by the IBM RACF Advanced authentication repository. Within this framework, multiple IBM RACF Advanced systems which are not externally synchronized will require a second Provisioning Connector.
While most provisioning commands are designed around direct access to IBM RACF Advanced, some LDAP provisioning commands are executed in multiple mainframe commands. For example, to provision for TSO access, some systems require modification to a CLIST profile. The type of command depends on which mainframe process is to be accessed.
While not within the scope of standard Oracle Identity Management provisioning, the Provisioning Agent can extend control to TSO commands, CICS commands, batch jobs, and other mainframe resources.
When an event occurs on the mainframe, independent of any custom installed technology, the event is processed through an appropriate mainframe exit. Because the Reconciliation Agent uses exit technology, there are no hooks in the z/OS mainframe operating system.
Identity events that arise from a user at TSO login, changes by an administrator from the command prompt, or events resulting from batch jobs are detected and notification messages are securely sent in real time. The Reconciliation Agent captures changes to user attributes (any ALTUSER change), changes to a user account (REVOKE, RESUME), and certain changes to user authorization for groups and resources. If a user account is created or deleted on the mainframe, the Reconciliation Agent will notify Oracle Identity Manager and even create a corresponding account in Oracle Identity Manager.
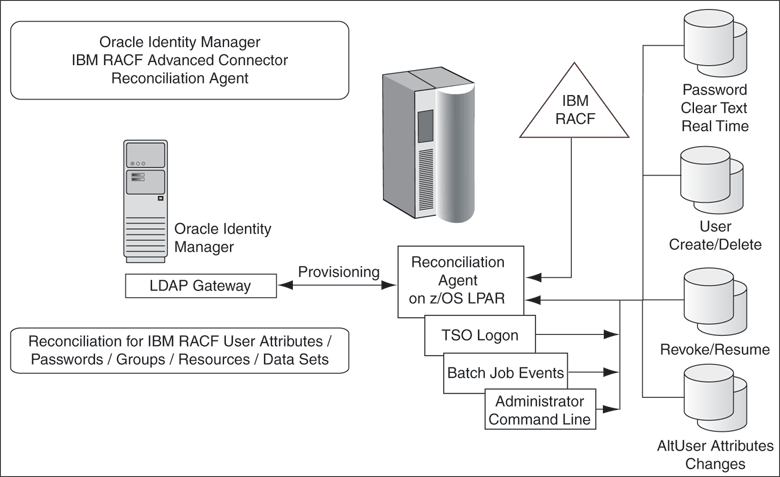
Passwords fall into a special category. If business rules permit, a password change will be passed to Oracle Identity Manager in clear text and real time. In a testing environment, it is almost immediate. Within other business rules, only a notification that the password has been changed will be passed.
Internal to mainframe architecture is significant communication of connector resources and internal mainframe memory subpools for enterprise loads at peak times. The Reconciliation Agent was specifically designed to handle peak loads from a mainframe batch job. By allocating one meg mainframe memory to the messaging subpools, 50,000 identity event messages can be held as fast as the batch job can produce them (about 8 minutes). These messages are then spooled to the LDAP Gateway, which supplies the messages to Oracle Identity Manager for subsequent processing (typically over the next hour). The entire Reconciliation Agent is protected by AES 128 encryption and APF authorized resources.
The Reconciliation Agent sends notification events to the Oracle Identity Manager LDAP Gateway from the z/OS mainframe. This architecture does not originate with IBM RACF Advanced, but captures the events just outside the operating system using exit technology, in real time.
A command execution is passed through an exit, just before full completion of the native mainframe command. A common use of this technology is to require user accounts or passwords to be formatted to a proper length or that they must contain at least one letter and one number. If the exit fails, the command fails and returns an error message. By capturing identity or authentication events at an exit, the Reconciliation Agent captures these events outside the operating system, just prior to completing the command and storing the results in the IBM RACF Advanced authentication repository.
As with the Provisioning Agent, there is an architectural dependence based on the LPAR. When a user account is created, is authorized to something, or works on the mainframe, they do this on an LPAR. Since all actions are within the LPAR and the Reconciliation Agent detected events from an LPAR exit, the Reconciliation Agent must be installed on each LPAR. This is a scheduled event, usually done with a maintenance schedule, because the an LPAR exit change is only recognized after an IPL.
The message transport layer is the process where the messages are exchanged between the LDAP Gateway and the IBM RACF Advanced Provisioning and Reconciliation Agent.
IBM MQ Series
Some IBM shops use the IBM MQ Series messaging system as their primary digital communication system. MQ Series is a secure and reliable message transport layer, utilizing internal encryption, conservation of resources, and guaranteed message delivery. The LDAP Gateway supports this message protocol.
TCP/IP
The LDAP Gateway also uses TCP/IP as a message transport layer to the Provisioning and Reconciliation Agent. This protocol is layered with an internal Advanced Encryption Standard (AES) encryption using 128-bit cryptographic keys. This encryption protocol is internal between the LDAP Gateway and Provisioning / Reconciliation Agent, not depending platform-specific programs or libraries.
The LDAP Gateway, Provisioning Agent, and Reconciliation Agent all coordinate bidirectional synchronization to a single IBM RACF Advanced authentication repository. Internally, the LDAP Gateway has 20 AES cryptographic keys which are randomly selected for a given message, 10 of which are dedicate for bidirectional messages between the Provisioning Agent and the other 10 are used for the Reconciliation Agent.
Messages between the LDAP Connector and the Provisioning Agent have a very short life span. The provisioning process that arises for Oracle Identity Manager expects a pass or fail LDAP message quickly. Typical logging and auditing protocols exist here and are usually all that are required.
Messages originating from the Reconciliation Agent require the same level of security and guaranteed delivery as MQ Series provides. Within this context, the Reconciliation Agent has been engineered for the following:
If the TCP/IP connection has not been established between the Reconciliation Agent and the LDAP Gateway, up to 50,000 messages are kept in a secure mainframe memory subpool prior to message processing.
During the message generation process, the Reconciliation Connector places both a time stamp and a sequential serial number to each message. An archive of the message is kept in an encrypted format in an APF authorized VSIM file, with both serial and time/date stamps.
Once transmitted, the messages are logged internally within the LDAP Connector, again in an encrypted format.
Overall, the entire TCP/IP message transport layer approaches the performance and security level of the IBM MQ Series. The Oracle Identity Manager TCP/IP message transport layer is included at no additional charge.