| Oracle® Audit Vault Agent Installation Guide 10g Release 2 (10.2.2) Part Number E10087-02 |
|
|
View PDF |
| Oracle® Audit Vault Agent Installation Guide 10g Release 2 (10.2.2) Part Number E10087-02 |
|
|
View PDF |
Oracle Audit Vault is a powerful enterprisewide audit solution that efficiently consolidates, detects, monitors, alerts, and reports on audit data for security auditing and compliance. Oracle Audit Vault provides the ability to consolidate audit data and critical events into a centralized and secure audit warehouse.
This chapter is divided into the following sections:
Compliance regulations and legislations such as the U.S. Sarbanes-Oxley Act (SOX), U.S. Gramm-Leach-Bliley Act (GLBA), U.S. Healthcare Insurance Portability and Accountability Act (HIPAA), Payment Card Industry (PCI) Data Security Standard, Japan privacy laws, and European Union privacy directives require businesses to secure business and personal data related to customers, employees, and partners, and to demonstrate compliance with these regulations by auditing users, activities, and associated data.
Businesses use a wide variety of systems, databases, and applications that produce vast quantities of audit log data and must consolidate and monitor this data for a holistic view of enterprise data access. Auditors must analyze the audit log data in a timely fashion across disparate and heterogeneous systems. To facilitate the process, it is essential that audit data from multiple systems reside in a single audit data warehouse that is secure, scalable, reliable, and highly available.
Oracle Audit Vault solves these security and audit problems by:
Consolidating audit information from multiple systems across the enterprise
Detecting data changes associated with regular and privileged users
Protecting audit data from modification and tampering
Figure 1-1 shows an overview of the Oracle Audit Vault architecture. The architecture consists of a set of services and its collection system working within an enterprise. This set of services helps to facilitate storage management, policy enforcement, alerting, analysis, and reporting activities. The collection infrastructure enables the utilization of audit collectors that function as adaptors between an audit source and Oracle Audit Vault.
Figure 1-1 Oracle Audit Vault Architecture
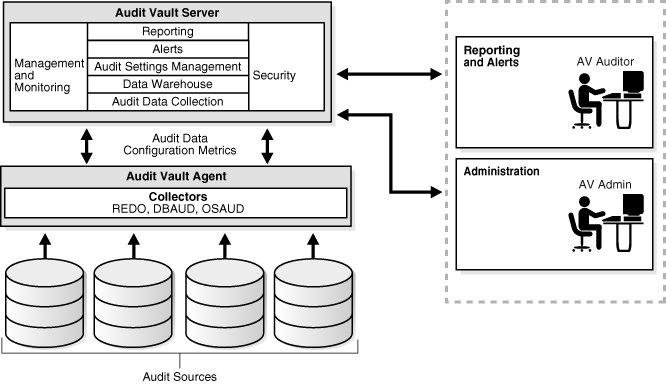
Oracle Audit Vault Components
Oracle Audit Vault consists of:
Audit Vault Server
Audit Vault Agents
Audit Vault Server
Audit Vault Server consists of:
Audit event repository
Audit Vault Console
The following services:
Audit data collection and storage
Creating and managing alerts
Managing and monitoring collectors
Configuration to assist in defining information about what sources are known to Audit Vault. It stores information (metadata) about the sources of audit data and policy information (database audit settings and alerts).
Creating and managing reports
Published data warehouse that can be used with reporting tools like Oracle BI Publisher to create customized reports
Audit policy management
Audit Vault Agents
Audit Vault Agents consists of:
Oracle Database client
Oracle Container for Java (OC4J)
Audit Vault management services
Audit data collectors for Oracle Database
Collecting audit data from Oracle Database operating system (OSAUD) audit logs, database (DBAUD) audit logs, and (REDO) redo logs
Oracle Audit Vault Interfaces and Administrator Access
Oracle Audit Vault provides a GUI interface and the Audit Vault Configuration Assistant (AVCA), Audit Vault Control (AVCTL), and Audit Vault Oracle Database (AVORCLDB) command-line utilities to manage the system. These components provide the ability to manage and monitor agents and collectors, and populate the data warehouse. See Oracle Audit Vault Administrator's Guide for information about these interfaces.
Auditors, compliance, and information technology (IT) security can use built-in reports based on user access and activity such as failed login attempts, use of system privileges, and changes to database structures. The drill-down capability offered through the Oracle Audit Vault Console provides full visibility into the details of the "what", the "where", the "when", and the "who" of the audit events. In addition, the Audit Vault Console can be used to monitor the alerts and the audit events across the enterprise.
Administrators are assigned different roles and gain access to Audit Vault to manage various components based on the role assigned. Table 1-1 describes the various Audit Vault administrator roles and the tasks permitted for each role.
Oracle Database Vault is used to protect the audit data warehouse from unauthorized access. See Oracle Database Vault Administrator's Guide for more information. Oracle Database Vault roles are essential for creating database user accounts and granting roles to Audit Vault administrators.
Table 1-1 Audit Vault Administrator Roles and Their Assigned Tasks
| Role | When Is Role Granted | Role Is Granted To Whom | Description |
|---|---|---|---|
|
|
During Server installation |
Audit Vault administrator |
Accesses Oracle Audit Vault services to administer, configure, and manage a running Oracle Audit Vault system. A user granted this role configures and manages audit sources, agents, collectors, the set up of the source with the agent, and the warehouse. A user is created and granted this role during the Audit Vault Server installation. |
|
|
During Server installation |
Audit Vault auditor |
Accesses Audit Vault reporting and analysis services to monitor components, detect security risks, create and evaluate alert scenarios, create detail and summary reports of events across systems, and manage the reports. A user granted this role manages central audit settings and alerts. This user also uses the data warehouse services to further analyze the audit data to assist in looking for trends, intrusions, anomalies, and other items of interest. A user is created and granted this role during the Audit Vault Server installation. |
|
|
Before agent installation |
Agent software component |
Manages agents and collectors by starting, stopping, and resetting them. A user is created and granted this role prior to an agent installation. The Agent software uses this role at run time to query Audit Vault for configuration information |
|
|
Before source registration |
Collector software component |
Manages the setting up of the sources for audit data collection. A user is created and granted this role prior to source and collector configuration. The collector software uses this role at run time to send audit data to Audit Vault |
|
|
Before archiving audit data |
Audit Vault archiver |
Archives and deletes audit data from Audit Vault and cleans up old unused metadata and alerts that have already been processed. A user granted this role can archive raw audit data. |
|
|
During Server installation |
Database Vault owner |
Manages Database Vault roles and configuration and grants Audit Vault roles. |
|
|
During Server installation |
Database Vault account manager |
Manages database user accounts. |
It is important to protect and ensure the integrity of the audit trail data against modification and tampering. Either external or internal intruders may try to "cover their tracks" by modifying audit trail records. Oracle Audit Vault delivers a "locked-down" audit warehouse that has been designed for the sole purpose of protecting and securing audit data. Access to the Oracle Audit Vault is only allowed for the predefined roles described in Table 1-1. All other roles, including the database administrator (DBA), are denied access to the audit data.
Figure 1-2 shows a detailed view of the various Audit Vault usage scenarios for which each of the Oracle Audit Vault administrator roles described in Table 1-1 plays an important role.
Figure 1-2 Usage Scenario Showing Important Roles of Audit Vault Administrators

This chapter provides an overview of the Oracle Audit Vault Agent installation process. This chapter includes the following sections:
You can choose different installation methods to install Oracle Audit Vault, as follows:
When you use the interactive method to install Oracle Audit Vault Agent, Oracle Universal Installer displays a series of screens that enable you to specify all of the required information to install the Oracle Audit Vault Agent software.
Audit Vault provides a response file template for Audit Vault Agent (avagent.rsp). The response template file can be found in the <AV installer location>/response directory on the Audit Vault Agent installation media.
When you start Oracle Universal Installer and specify a response file, you can automate all of the Oracle Audit Vault Agent installation. These automated installation methods are useful if you need to perform multiple installations on similarly configured systems or if the system where you want to install the software does not have X Window system software installed.
For Audit Vault Agent, Oracle Universal Installer can run in silent or non-interactive mode. In silent mode, specify both the -silent and -responseFile options followed by the absolute path of the response file on the command line when you invoke Oracle Universal Installer. For example:
For Linux and UNIX-based systems:
./runInstaller [-silent] -responseFile <Path of response file>
For Windows systems:
setup.exe [-silent] -responseFile <Path of response file>
where:
Path of response file: Identifies the full path of the response file.
-silent: Runs Oracle Universal Installer in silent mode and suppresses the Welcome window.
Oracle Universal Installer runs in silent mode if you use a response file that specifies all required information. None of the Oracle Universal Installer screens are displayed and all interaction (standard output and error messages) and install logs appear on the command line.
Prepare the response file by entering values for all parameters that are missing in the first part of the response file, then save the file. Do not edit any values in the second part of either response file.
See the following for information about performing an Audit Vault silent installation or more specific information:
Audit Vault Agent installation, see Section 3.3.
"Installing Oracle Products" in Oracle Universal Installer and OPatch User's Guide for more information about installing using response files
The Audit Vault Agent includes Oracle Containers for J2EE (OC4J) and Instant Client components, and is deployed within its own directory. The agent can be installed either on the same system as the Audit Vault Server, or on the same system that hosts the source of audit logs, or on a third, independent system. Where you deploy the agent will depend on the hardware resources available and on the requirements from the specific audit data collectors that need to run within the agent. As a best practice, the Oracle Audit Vault Agent should be installed on each host system to be audited. The DBAUD and REDO collectors do not place any restrictions on the deployment of the agent; they can be deployed anywhere depending on your requirements. However, the OSAUD collector needs local access to the disk that stores the audit trail files written by the source database. Therefore, it must be deployed on a host system that mounts these disks locally, not across the network.
The agent communicates with the Audit Vault Server to receive some configuration information and to send audit data for storage. This communication channel is OCI-based. Immediately following installation, password-based authentication is used to secure this channel. Administrators can further secure this channel after installation by using the HTTPS protocol to encrypt data. In this case, X.509 certificates, which must be provided by the administrator, are used for authentication.
The agent also communicates with the Audit Vault Console to exchange management information, such as starting and stopping collectors, and collecting performance metrics. This communication channel is HTTP-based. If X.509 certificates are provided, this channel can be further secured to use HTTPS encryption and mutual authentication with the Audit Vault Console.
This section contains information that you should consider before deciding how to install this product. It contains the following sections:
The platform-specific hardware and software requirements included in this installation guide were current at the time this guide was published. However, because new platforms and operating system versions might be certified after this guide is published, review the certification matrix on the OracleMetaLink Web site for the most up-to-date list of certified hardware platforms and operating system versions. The OracleMetaLink Web site is available at:
https://metalink.oracle.com
If you do not have a current Oracle Support Services contract, then you can access the same information at:
http://www.oracle.com/technology/support/metalink/content.html