| Oracle® Identity Federation Administrator's Guide 10g (10.1.4.0.1) B25355-02 |
|
 Previous |
 Next |
| Oracle® Identity Federation Administrator's Guide 10g (10.1.4.0.1) B25355-02 |
|
 Previous |
 Next |
This chapter describes tasks related to day-to-day administration of Oracle Identity Federation, and additional tasks that the administrator may need to perform on occasion. It contains these topics:
|
See Also: For details about initial server configuration, see Chapter 6, "Configuring Oracle Identity Federation" |
This section describes basic administration of Oracle Identity Federation. It contains these topics:
The Oracle Identity Federation administrator performs two roles, which can be characterized as:
Basic runtime administration of the server, including starting, stopping, and monitoring the server
Federated identity administration, which involves user administration (user creation, deletion, and federation), and maintaining information about trusted providers and the users affiliated with those providers
The remainder of this section provides information to help you plan your Oracle Identity Federation deployment.
Subsequent sections in this chapter focus on basic runtime tasks and identity administration.
When deploying Oracle Identity Federation in a network of trusted sources and destinations, you will need to exchange information with other site administrators, and configure identity providers and service providers accordingly.
|
See Also: "Architecture Options" in Chapter 2, "Planning Oracle Identity Federation Deployment" for details about managing server properties, federation protocols, and circle of trust provider information |
Exchange User Identities
In a federated environment, at the simplest level the service provider acts as a consumer of identity information, while the identity provider (where the user request originated) acts as the supplier of identity information. The identity provider may, in turn, adopt a consumer role as it communicates with an authentication and authorization mechanism (a AAA system) to obtain the necessary credentials. Service providers may also want to map users to identities at the destination, although this is not a requirement. Identity suppliers and consumers must be able to achieve a runtime exchange of data, which results in the source asserting some identity information about the principal which the destination can trust as a means of uniquely identifying the principal.
As an identity provider, you may wish to work with partner site administrators to provide the relevant lists of users from your domain. This is an optional information exchange.
Establish Cross-Domain Trust
Oracle Identity Federation can produce and consume provider metadata that conforms to the Liberty metadata specifications for ID-FF 1.1 and 1.2, as well as the SAML 2.0 metadata specification. Additionally, Oracle Identity Federation supports the ability to import provider metadata that uses the metadata extensions for SAML 2.0 query requesters.
You will need to establish cross-domain trust by setting up authentication and exchanging keys or certificates among the network of trusted sources and destinations.
For initial setup and testing, identity providers and service providers can both use default self-signed certificates. When going into production, however, consider the usage type when deciding whether self-signed certificates are sufficient: CA-issued certificates are most useful when there is no prior trust relation between entities, for example, when you use SSL to access a web site over the Internet. But given that the trust relationship between federation peers requires the exchange of metadata or the equivalent, which can and usually does include the peer certificates, self-signed certificates should be sufficient for production deployment so long as you can trust how you obtained the peer certificates. Note that CA-issued certificates might be used in the metadata exchange, for example signed e-mail or a download from a web server over SSL.
The process of setting up cross-domain trust can be simplified by the use of metadata. Oracle Identity Federation enables you to store provider-specific metadata which overrides global IdP and SP settings with data specific to communication with each peer provider.
|
Note: The SAML 1.x and WS-Federation protocols do not specify metadata formats, so peers using those protocols have to exchange the equivalent information, including certificates, on their own. |
PKI and SSL Encryption
Oracle Identity Federation provides secure communication using X.509 client certificate authentication.
Oracle Identity Federation provides encryption for data integrity using public key cryptography, a technique that uses a public and private key pair. Data is signed with a sending party's private key and the signature is verified by the recipient using the sender's public key.
Oracle Identity Federation uses documents known as certificates to enable peer providers to establish trust. A Certificate Authority (CA) issues a certificate to vouch for a user's identity, including the party's public key in the certificate for use by the receiving party.
You configure key pairs and certificates using a local keystore. The identity provider configures a public and private key pair and a certificate - providing validation of the public key from a Certificate Authority (CA) - when using the POST profile. The presentation of the public key by the IdP, and certificate importation by the SP, are critical aspects in managing the trust relationship between partners.
You can also implement SSL connections. For details on how to configure SSL connections and client certificates, see "Using SSL with Oracle Identity Federation".
|
Note: SSL functionality is external to Oracle Identity Federation. |
Besides exchanging identities and securing communications involving those identities, parties that plan to engage in a federated network must agree on a range of additional topics, such as:
federation protocols
services
profiles
You will need to work with others in your network to ensure that the various IdPs and SPs understand their business partners' setups in order for federation to work properly.
To log in to the Oracle Identity Federation administration console:
Start the login process by pointing to the login URL:
http://machine-name:port/fedadmin
A login window appears:
Log into Oracle Identity Federation using the username and password supplied during installation. The Server Configuration home page appears:
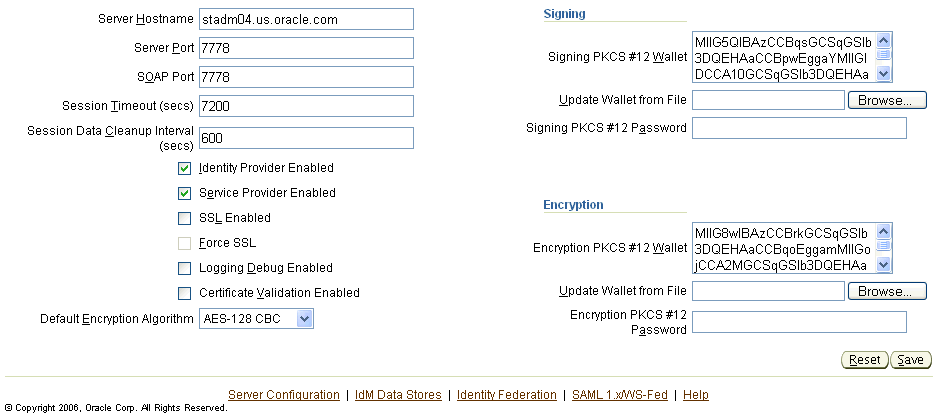
To log out, close your browser window.
You can start and stop the Oracle Identity Federation server through the Enterprise Manager console or by using the opmnctl command-line tool (Oracle Process Manager and Notification Server Control Utility) on the OC4J_FED container.
For example, the command to restart Oracle Identity Federation is:
opmnctl restartproc process-type=OC4J_FED
If Oracle Identity Federation is using an RDMBS data store, the server must be started or stopped in a specific sequence relative to the database:
The RDBMS must be started before Oracle Identity Federation is started.
The RDBMS must be stopped after Oracle Identity Federation is stopped.
If you do not follow this sequence, Oracle Identity Federation will not operate properly since the data store will not be available.
|
See Also:
|
You can change the federation server administration password through the Enterprise Manager console using these steps:
Click OC4J_FED.
Click Applications.
Click fed.
Click Security.
Click oif/oif_admin.
|
Note: You will need to restart theOC4J_FED instance for the password change to take effect. |
Oracle Identity Federation log files, including logs for SAML2.0/Liberty 1.x messages, are maintained in the $ORACLE_HOME/fed/log directory and provide useful information for managing and monitoring server instances. The log files include:
Table 5-1 Oracle Identity Federation Log Files
| Log File Name | Description |
|---|---|
|
|
Contains the runtime log records for the Oracle Identity Federation server. |
|
|
Contains error messages generated by the Oracle Identity Federation server. |
|
|
Contains the SAML2.0/Liberty 1.x messages exchanged between Oracle Identity Federation and peer providers. |
|
|
Contains a log of the installation session. |
|
|
Contains a log of the uninstall session. |
You should back up your configurations/systems with the tools that you normally employ to back up your systems on a daily basis.
Windows
Use this backup regimen:
Use the backup/restore system tools on window platforms.
Back up everything on all components in the Oracle Identity Federation configuration.
Linux/solaris:
Use this backup regimen:
Shut down all Oracle Application Server and Oracle Identity Federation components.
Run the tar command all on components, including Oracle Application Server, Oracle Identity Federation, and the RDBMS data files that Oracle Identity Federation is using.
For example:
tar cvzf oif10141_backup oif_folder
Clicking on the Identity Federation tab of the Oracle Identity Federation administration console brings you to a page where you can manage federations. Use this page to edit configuration details for Oracle Identity Federation trusted providers and users.
Clicking on Trusted Providers (default when the page loads) displays the list of all providers in the Oracle Identity Federation circle of trust.
Clicking on Users allows you to search for all users who have identity federations associated with this instance of Oracle Identity Federation.
|
See Also: For information about accessing the administration console, see "Administration Console Overview" |
This section contains these topics:
This page displays all providers in the Oracle Identity Federation server's circle of trust.
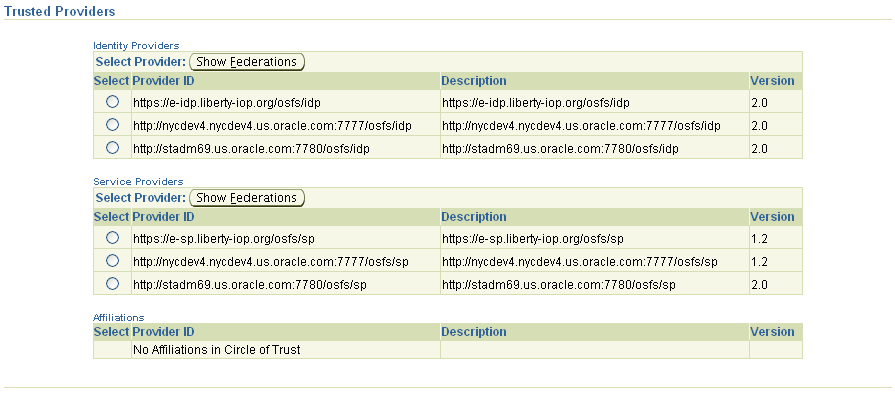
Use the information on the page as follows:
Select one of the available identity providers and click Show Federations to display the identity federations associated with this Oracle Identity Federation server for the selected provider.
Select one of the available service providers and click Show Federations to display the identity federations associated with this Oracle Identity Federation server for the selected provider.
Select an affiliation in the circle of trust.
The server will display federations between:
this Oracle Identity Federation server as an SP, and remote IdPs from the Identity Provider section of the table
this Oracle Identity Federation server as an IdP, and remote SPs from the Service Provider section of the table
this Oracle Identity Federation server as an IdP, and affiliations from the Affiliation section of the table
The display will not include federations between remote IdPs and affiliations when this Oracle Identity Federation server acts as an SP and is participating in the affiliations.
Provider ID
This is the ID of a service provider or identity provider in the Oracle Identity Federation circle of trust.
Description
This is a brief description of the provider.
Version
This is the protocol version:
1.1 (Liberty 1.1)
1.2 (Liberty 1.2)
2.0 (SAML 2.0)
This page allows you to search for and display users who have identity federations associated with a given trusted provider.
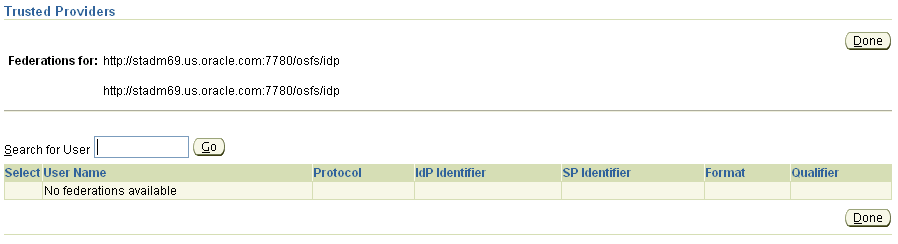
Enter a (partial or complete) name in the Search for user box, and click Go.
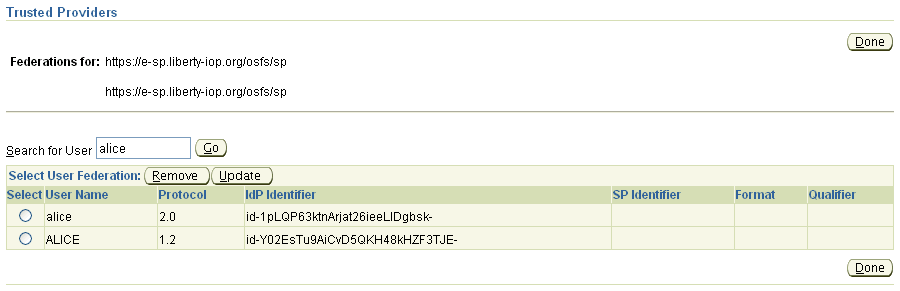
This example looks up user Alice:
|
Note: You can use substrings for user searches. In the example, entering eitheral or alice would return user alice; the search for al would return any additional users whose name contained that substring. |
User Name
This is the local name of a federation user.
Protocol
This is the federation protocol for this user.
IdP Identifier
This is a value that the identity provider generates for the IdP name identifier.
SP Identifier
This is a value that the service provider generates for the SP name identifier.
Format
This is the NameID (Name Identifier) format. Example 1-2 illustrates the use of name identifiers for SAML 2.0.
Qualifier
This is the NameQualifier attribute of a name identifier. This qualifier is used to avoid name collisions - for example, two users from different domains with the same username. (The qualifier therefore serves the same purpose as XML namespaces and Java package names.)
Actions
|
Note: For all protocols, the Remove button works the same way. However, the Update action is protocol-dependent. |
Buttons on the page provide these actions:
Remove - Clicking on Remove initiates a federation termination protocol exchange between the Oracle Identity Federation instance and the trusted provider. When the exchange (FedTerm, RNI, MNI) completes, you are sent to an updated version of this page.
Update - Actions resulting from this button depend on the associated protocol.
Liberty 1.1 and Liberty 1.2
Clicking on Update initiates a Register Name Identifier protocol exchange between Oracle Identity Federation and the trusted provider. The Federation Server will generate a new value for the name identifier.
SAML 2.0
Clicking on Update initiates a Manage Name Identifier protocol exchange between Oracle Identity Federation and the trusted provider. If the Name Identifier Format is urn:oasis:names:tc:SAML:2.0:nameid-format:persistent, the Federation Server generates a new value for the name identifier. If the format is one of the other, non-opaque types, such as urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress, the Federation Server will take the new name identifier value from the corresponding attribute in the user repository.
The Users page is accessed by choosing Users from the Identity Federation tab on the Administration Console. Enter all or part of a user name in the Search for user box and click Go.
The page allows you to view basic data defined for the Oracle Identity Federation user.
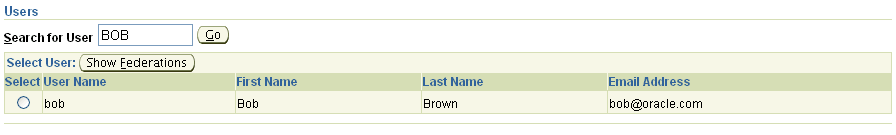
Enter a (partial or complete) name in the Search for User box, and click Go.
|
Note:
|
When viewing user information, click on the Show Federations button to view and update federations associated with that user.
User Name
This is username assigned to the user.
First Name
This is the user's first name.
Last Name
This is the user's last name.
Email Address
This is the user's e-mail address.
When viewing user information, click on the Show Federations button to view and update federations associated with that user.
For a given user, the server displays federations between:
this Oracle Identity Federation server as an SP, and remote IdPs
this Oracle Identity Federation server as an IdP, and remote SPs
this Oracle Identity Federation server as an IdP, and affiliations
affiliations in which this Oracle Identity Federation server (as an SP) is a member, and remote IdPs
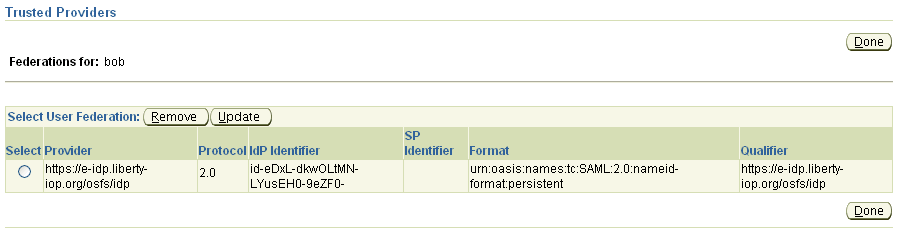
Provider
This is the provider name.
Protocol
This is the provider's federation protocol for this user.
IdP Identifier
This is a value that the identity provider generates for the IdP name identifier.
SP Identifier
This is a value that the service provider generates for the IdP name identifier.
Format
This is the SAML NameID (Name Identifier) format.
Qualifier
This is the provider URL, applicable for service providers.
Buttons on the page provide these actions:
Remove - Clicking on Remove initiates a federation termination protocol exchange between the Oracle Identity Federation instance and the trusted provider. When the exchange (FedTerm, RNI, MNI) completes, you are sent to an updated version of this page.
Update - Actions resulting from this button depend on the associated protocol.
Liberty 1.1 and Liberty 1.2
Clicking on Update initiates a Register Name Identifier protocol exchange between Oracle Identity Federation and the trusted provider. Oracle Identity Federation will generate a new value for the name identifier.
SAML 2.0
Clicking on Update initiates a Manage Name Identifier protocol exchange between Oracle Identity Federation and the trusted provider. If the Name Identifier Format is urn:oasis:names:tc:SAML:2.0:nameid-format:persistent, the Federation Server generates a new value for the name identifier. If the format is one of the other, non-opaque types, such as urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress, the Federation Server will take the new name identifier value from the corresponding attribute in the user repository.
At some point in time you may need to point your Oracle Identity Federation instance to a different Infrastructure - for example, when Oracle Identity Federation is currently deployed in a test environment and is now ready to enter the production environment. This section describes key aspects of reassociation and contains the following topics:
|
Note: Existing federation data is not migrated during reassociation. To ensure that all federation data is erased, you must delete federation data records as the first step in reassociation. |
|
See Also: For detailed instructions about pointing your Oracle Identity Federation instance to a different instance of Oracle Internet Directory or Oracle Application Server Single Sign-On, see "Reassociating the Server" |
The procedure for changing the federation data store used by an Oracle Identity Federation instance involves these steps:
Update the server's LDAP schema to be compatible with the Oracle Identity Federation LDAP data type.
LDIF Schema files for the supported directories are located in the $ORACLE_HOME/fed/setup/ldap folder of the Oracle Identity Federation installation.
Point your browser to the Oracle Identity Federation Administration Console.
Select IdM Data Stores - > Edit Federation Data Store.
Update the federation data store settings.
The procedure for changing the user data store that is used by an Oracle Identity Federation instance involves these steps:
Point your browser to the Oracle Identity Federation Administration Console.
Select IdM Data Stores - > Edit User Data Store.
Update the user data store settings.
An RDBMS can be used to store transient data as well as identity data.
To change the RDBMS data store used by an Oracle Identity Federation instance, you will need to run the configuration assistant described in "Command-Line Configuration Assistant to Change the Transient Data Store".
|
Note: You will need to invoke the configuration assistant with the-transient rdbms argument. |
You can delete federation data records or transient session data that were generated by an Oracle Identity Federation instance; it is also possible to remove the LDAP schema from the directory server used as the federation data store.
To delete federation data, delete transient data, or remove the LDAP schema, you will need to run the command-line configuration assistant described in "Command-Line Configuration Assistant for Uninstallation".
|
Note: This configuration assistant does not uninstall Oracle Identity Federation; it only cleans up the data stores. You will need to invoke this configuration assistant before you change the existing federation and user data stores to ensure that all data is erased. |
To move Oracle Identity Federation from a test to a production Oracle Access Manager, simply repeat the Oracle Access Manager setup steps:
Configure an AccessGate in the production instance of Oracle Access Manager, reconfigure the Oracle Access Manager user data store for Oracle Identity Federation and the associated AccessGate configuration, and restart.
If, for some reason, the Access Server SDK that was installed in Oracle Identity Federation for the test environment is not compatible with the production environment (for example, it is an older version), uninstall the SDK and install a compatible SDK.
This section provides instructions on how to delete Oracle Identity Federation-related policy objects from an Oracle Access Manager instance. This is needed if there was a previous installation of Oracle Identity Federation using Oracle Access Manager, which is being replaced by a new Oracle Identity Federation instance on a different host.
Take these steps:
If it is still running, stop the OC4J_FED instance for the previous Oracle Identity Federation server.
Log into the Access System Console as a Master Access Administrator.
Click on the Access Manager link to get the Policy Manager My Domains page.
Delete the policy domain named Fed Domain.
Change the authentication schemes for any policy domains that use the "Fed SSO" schemes. For each domain:
On the My Domains page, click on the domain name to get to the domain page.
Click on the Default Rules tab to get the default authentication rule for the domain.
If the authentication scheme for the rule is Fed SSO - SAML 1.x, Fed SSO - WS-Federation, or Fed SSO - SAML 2.0/Liberty 1.2:
Record the authentication scheme for this domain.
Click Modify.
Select another authentication scheme, preferably a basic scheme, from the drop-down list.
Click Save to return to the domain page.
Click on the Policies tab.
For each policy defined for the domain:
Click on the policy name to get the policy page.
Click on the Authentication Rule tab.
If the authentication scheme for the rule is Fed SSO - SAML 1.x, Fed SSO - WS-Federation, or Fed SSO - SAML 2.0/Liberty 1.2:
- Record the authentication scheme for this policy for this domain.
- Click Modify.
- Select another authentication scheme, preferably a basic scheme, from the drop down list.
- Click Save to go back to the policy page.
- Click Policies.
Click on the Access System Console link.
Click the Access System Configuration tab.
Click on the Authentication Management link.
Delete all authentication schemes that begin with "Fed". This includes the Fed SSO - SAML 1.x, Fed SSO - WS-Federation, and Fed SSO - SAML 2.0/Liberty 1.2 schemes, and any scheme created for a configured SAML 1.x assertion mapping, such as Fed SASSO Mapping or Fed Minimal Mapping.
Configure the Oracle Access Management user data store, and restart the new Oracle Identity Federation server. Oracle Identity Federation will automatically recreate the Access policy objects.
Restore the Fed SSO authentication schemes for the policy domains and policies recorded in step 5. For each recorded policy domain:
On the My Domains page, click on the domain name to get the domain page.
If the domain originally used a Fed SSO scheme for its default authentication rule, click the Default Rules tab.
click Modify.
Select the original Fed SSO scheme from the drop-down list.
click Save.
Click the Policies tab.
For each policy in the domain that originally used a "Fed SSO" scheme:
Click the policy name to get the policy page.
Click the Authentication Rule tab.
Click Modify.
Select the original Fed SSO scheme from the drop-down list.
Click Save.
Click Policies.
This section explains how to uninstall an Oracle Identity Federation instance. It contains these topics:
Un-installing Oracle Identity Federation requires these high-level actions:
Run the Oracle Identity Federation uninstall tool.
Run the Oracle Application Server instance deconfig tool.
Run Oracle Universal Installer for product deinstallation.
Clean up any remaining files.
Table 5-2 shows what items need to be removed and the relevant tool for each item.
Table 5-2 Oracle Identity Federation Items to De-install
| De-installed Item | Tool Used |
|---|---|
|
Files from the |
Oracle Universal Installer If the installer cannot remove all the files, you can remove any remaining files using |
|
Entries for the deleted instance in the |
Oracle Universal Installer |
|
Instance name from the Farm page |
Oracle Universal Installer |
|
Entries for the deleted instance in the |
Remove these entries manually. |
|
Entries for the deleted instance in Oracle Internet Directory |
|
|
Federation records |
|
Subsequent sections describe uninstallation steps and explain how to use these tools to complete uninstallation.
Oracle Universal Installer provides the ability to de-install products. It does not permit custom uninstallation of individual components.
Follow these uninstallation steps:
Log in as the operating system user who installed the instance that is to be un-installed.
Stop all processes associated with this instance.
See the Oracle Application Server Administrator's Guide for details on how to stop the processes.
Run the Oracle Identity Federation uninstall tool:
java -jar ORACLE_HOME/fed/lib/uninstall.jar <parameters>
For an explanation of parameters and other details about the uninstall tool, see "Command-Line Configuration Assistant for Uninstallation".
If an OracleAS Single Sign-On back-end is associated with the Oracle Identity Federation instance, run the Oracle Application Server deconfig tool:
cd $ORACLE_HOME/bin
$ORACLE_HOME/perl/bin/perl deconfig.pl <parameters>
|
See Also: For details of thedeconfig tool parameters, see "Oracle Application Server Instance Deconfig Tool" |
Start Oracle Universal Installer:
$ORACLE_HOME/oui/bin/runInstaller
If you are unable to start Oracle Universal Installer in this way, or when you select Start - > Programs - > Oracle - OracleHomeName - > Oracle Installation Products - > Universal Installer, run these commands at the system prompt to start the installer:
% cd ORACLE_HOME\oui\bin
% setup.exe -J-Dsun.java2d.noddraw=true -Dsun.awt.nopixfmt=true
Take these steps in Oracle Universal Installer:
On the Welcome screen, click Deinstall Products.
On the Inventory screen, select the instance you want to uninstall, and click Remove.
On the Confirmation screen, verify the components selected for uninstallation. Click Yes to continue.
Monitor progress on the Uninstallation Progress screen.
Exit the installer when the uninstallation is complete.
Delete any remaining files in the ORACLE_HOME directory of the deleted instance using an appropriate operating system command. For example:
rm -rf $ORACLE_HOME
Remove the line for the un-installed middle tier from the /var/opt/oracle/oratab file.
Towards the end of the file, you should see lines that specify the ORACLE_HOME directory. Remove the line for the ORACLE_HOME that you un-installed. For example, if your ORACLE_HOME is /private1/oif, the line would look like the following:
*:/private1/oif:N
You may see unable to delete file and unable to find make file errors in the oraInstalltimestamp.err file after you uninstall Oracle Identity Federation server instances. For example:
Ignoring Exception during de-install oracle.sysman.oii.oiil.OiilDeinstallException: An error occurred during runtime. oracle.sysman.oii.oiil.OiilDeinstallException: An error occurred during runtime. ... Ignoring Exception during de-install oracle.sysman.oii.oiil.OiilDeinstallException: Unable to delete file /home/j2ee/sysman/emd/targets.xml oracle.sysman.oii.oiil.OiilDeinstallException: Unable to delete file /home/j2ee/sysman/emd/targets.xml at instantiateFileEx.deinstallAction(instantiateFileEx.java:935) ... Ignoring Exception during de-installoracle.sysman.oii.oiil.OiilDeinstallException: Unable to find make file: /home/j2ee/network/lib/ins_net_client.mk oracle.sysman.oii.oiil.OiilDeinstallException: Unable to find make file: /home/j2ee/network/lib/ins_net_client.mk at ssmakeux.deinstallAction(ssmakeux.java:246) ...
These are harmless error messages and may safely be ignored.
The Oracle Application Server deconfig tool removes entries in the OracleAS Metadata Repository and Oracle Internet Directory for the Oracle Application Server instance that you are un-installing. If an OracleAS Single Sign-On back-end is associated with the Oracle Identity Federation instance, run the deconfig tool before de-installing from the Oracle Universal Installer.
To run the deconfig tool, run the Perl interpreter on the ORACLE_HOME/bin/deconfig.pl script. Use the Perl interpreter provided with Oracle Identity Federation:
cd $ORACLE_HOME/bin
$ORACLE_HOME/perl/bin/perl deconfig.pl <parameters>
If you run it without any parameters, the tool prompts you for the necessary information.
The syntax for the deconfig tool is:
$ORACLE_HOME/perl/bin/perl deconfig.pl [-u oid_user] [-w password] [-r realm] [-dbp sys_db_password]
You can also run the deconfig tool with the -h or -help parameter to display help:
$ORACLE_HOME/perl/bin/perl deconfig.pl -h
or
$ORACLE_HOME/perl/bin/perl deconfig.pl -help
The parameters are:
-u specifies the Oracle Internet Directory user.
You can specify the value using either the user's simple name or the user's distinguished name (DN). For example, the user's simple name can be jdoe@mycompany.com, which corresponds to the DN cn=jdoe,l=us,dc=mycompany,dc=com.
The Oracle Internet Directory user needs to have privileges for un-installing the components that are configured in the Oracle Application Server instance that you are uninstalling. These privileges are the same as for installing and configuring the component.
If you want to run the tool as the Oracle Internet Directory superuser, be sure to use cn=orcladmin, and not just orcladmin. Note that these are two different users. Both users are created when you install Oracle Internet Directory; cn=orcladmin is the Oracle Internet Directory superuser. For more information about this topic, see the Oracle Internet Directory Administrator's Guide.
-w specifies the password for the Oracle Internet Directory user.
-r specifies the realm in which to authenticate the user. This value is required only if your Oracle Internet Directory has more than one realm.
-dbp is deprecated and is not needed, so do not specify this parameter.
Take these steps to uninstall an OracleAS Cold Failover Cluster installation:
Stop the clusterware agents or packages that monitor and fail over the environment. See your clusterware documentation for details.
Perform the steps described in "Uninstallation Steps".
If you do not follow this order and take the resources offline first, the installer will hang during the uninstallation because the clusterware agents will try to fail over the resources.
If you forgot to shut down Oracle Identity Federation server processes before starting the installation, you will need to kill the processes manually because the files for these processes have been deleted. To check for processes that are still running, run an operating system command such as the Unix ps command:
% ps -ef
Note the process_id obtained from the command, then kill the process using a command such as the Unix kill command:
kill -9 process_id
If you need to shut down the dcmctl shell process, try exiting the shell by typing exit.
Oracle Universal Installer does not allow you to reinstall an Oracle Identity Federation server instance in a directory that already contains an Oracle Identity Federation server instance. To reinstall Oracle Identity Federation server in the same directory, you must uninstall and then install it.