| Oracle® Access Manager Integration Guide 10g (10.1.4.2) Part Number E10356-01 |
|
|
View PDF |
| Oracle® Access Manager Integration Guide 10g (10.1.4.2) Part Number E10356-01 |
|
|
View PDF |
PeopleSoft is a Web-based eBusiness application suite that provides human resources, supply chain, CRM, analytics, portal, and other applications. This chapter describes the integration of Oracle Access Manager's single sign-on capabilities with PeopleSoft PeopleTools and applications.
This chapter covers the following topics:
Setting Up Oracle Access Manager Single Sign-On for PeopleSoft
Setting up PeopleSoft for Single Sign-On with Oracle Access Manager
This integration provides a secure Internet infrastructure for identity management for PeopleSoft's customer applications and processes. Oracle Access Manager provides identity and access management across PeopleSoft applications, enterprise resources, and other domains that are deployed on eBusiness networks. Oracle Access Manager provides the foundation for managing the identities of customers, partners, and employees across Internet applications. These user identities are protected by security policies for Web interaction.
This integration adds the following to PeopleSoft implementations:
Oracle Access Manager authentication, authorization, and auditing services for Siebel 7 applications.
Oracle Access Manager single sign-on (SSO) for PeopleSoft applications and other Oracle Access Manager-protected resources in a single domain or across domains.
Oracle Access Manager authentication schemes that provide single sign-on for PeopleSoft applications:
Basic: Users enter a user name and password in a window supplied by the Web server.
This method can be redirected to SSL.
Form: Similar to the basic challenge method, users enter information in a custom HTML form.
You choose the information that users must provide in the form.
X509 Certificates: X.509 digital certificates over SSL.
A user's browser must supply a certificate.
Integrated Windows Authentication (IWA): Users will not notice a difference between an Oracle Access Manager authentication and IWA when they log on to the desktop, open an Internet Explorer (IE) browser, request a Oracle Access Manager-protected Web resource, and complete single sign-on.
Custom: You can use other forms of authentication through the Oracle Access Manager Authentication Plug-in API.
Session timeout: Oracle Access Manager enables you to set the length of time that a user session is valid.
Ability to use the Identity System for identity management: The Identity System provides identity management features such as portal inserts, delegated administration, workflows, and self-registration to applications such as PeopleSoft.
You can determine how much access to provide to people upon self-registration. Identity System workflows enable a self-registration request to be routed to appropriate personnel before access is granted.
Oracle Access Manager also provides self-service, allowing users to update their own identity profiles.
This integration involves the following PeopleSoft components.
PeopleSoft Application Server: The application server is the core of PeopleSoft Pure Internet Architecture (PIA). An application server maintains the SQL connection to the database for browser requests and the PeopleTools development environment in Microsoft Windows. It runs business logic and issues SQL to the database server.
The application server consists of numerous PeopleSoft services and server processes. Just as different elements make up the physical environment in which an application server operates, for example, database servers and Web servers, a variety of elements operate on the application server, enabling it to respond effectively to multiple transaction requests and handle transaction processing, system scaling, browser requests, and so on.
PeopleSoft Database Server: The database server houses a database engine and the PeopleSoft application database. The database includes all the application's object definitions, system tables, application tables, and data. The database server must run one of the PeopleSoft-supported RDBMS and operating system combinations.
Multiple application servers can connect to the database server. The database server simultaneously handles the application server connections, development environment connections, and batch programs running against it.
PeopleSoft Internet Architecture: PeopleSoft Pure Internet Architecture enables Internet application deployment through a browser, and enables you to take advantage of PeopleSoft intranet solutions, Internet solutions, and integration technologies.
PeopleSoft Pure Internet Architecture runs seamlessly in portals created and managed by PeopleSoft portal technology.
PeopleTools portal technology is built on top of PeopleSoft Pure Internet Architecture and enables you to easily access and administer multiple content providers, including PeopleSoft databases such as PeopleSoft CRM and HRMS, as well as non-PeopleSoft content. It enables you to combine content from these multiple sources and deliver the result to users in a unified, simple-to-use interface.
PeopleSoft has a configurable authentication mechanism that allows it to authenticate a user against the following:
Native tables
LDAP
Custom plug-ins, including the ability to read HTTP Headers
Single sign-on with PeopleSoft involves the following:
Protecting PIA with a WebGate.
Populating a header variable with an attribute value that is stored in the LDAP directory used by Oracle Access Manager.
Writing PeopleCode to read the header variable and generate the PS_TOKEN.
A cookie is generated by PIA every time a user successfully logs in. It is used to enable single sign-on with other PeopleSoft applications.
Configuring PeopleSoft to invoke the PeopleCode as part of the authentication process, overriding the default authentication mechanism.
There are two ways to render PeopleSoft application pages for the user:
Using a PIA application server that has an HTTP Server and a J2EE container (required for the PIA servlets and Java code to run), for example, Oracle Application Server 10g.
Using a Java-enabled application server and setting up an HTTP server as a reverse proxy.
For example, you can use WebLogic as the PIA application server and iPlanet as the HTTP Server.
In both cases, the WebGate must be installed on the HTTP Server and it must be configured to protect the PeopleSoft URLs. See your PeopleTools version-specific documentation for the URL format.
The user accesses a PeopleSoft application using the Web browser. The WebGate intercepts the user's HTTP request and checks for an obSSOCookie. If the cookie does not exist or it has expired, the user is challenged for credentials. Oracle Access Manager verifies the credentials, and if the user is authenticated, the WebGate redirects the user to the requested resource and passes the required header variable to PeopleSoft. The header variable is read by PeopleSoft and used to generate the PS_TOKEN. Table 8-0 illustrates the integration environment and process flow:
Process Overview: Single Sign-On with PeopleSoft
A user attempts to access a PeopleSoft application.
A Webgate that is deployed on the PeopleSoft HTTP Server intercepts the request.
The Webgate checks the Access Server to determine if the resource (PeopleSoft URL) is protected.
The security policy consists of an authentication scheme, authorization rules, and allowed operations based on authentication and authorization success or failure.
If a valid session does not exist and the resource is protected, WebGate prompts the user for credentials.
If the credentials are validated, Oracle Access Manager executes the actions defined in the security policy for the PeopleSoft resource and sets a HTTP Header variable that maps to the PeopleSoft user ID.
If a valid session cookie exists and if the user is authorized to access the resource, WebGate redirects the user to the requested PeopleSoft resource.
PeopleSoft receives the request for the PeopleSoft resource and executes the PeopleCode defined in its authentication configuration.
The PeopleCode reads the HTTP header variable and sets that value as the logged-in PeopleSoft user.
It then generates the PS_TOKEN, which contains the same information.
PeopleSoft generates the application pages, subject to further authorization verification within PeopleSoft.
This chapter describes the integration of Oracle Access Manager 10g (10.1.4.0.1) with PeopleTools 8.47 and PeopleSoft Applications (HCM 8.9). However, any references to specific versions and platforms in this chapter are for demonstration purposes.
You can find support and certification information at the following URL:
http://www.oracle.com/technology/documentation/
You must register with OTN to view this information.
Also, you can see the supported versions and platforms for this integration on Metalink, as follows.
To view information on Metalink
In your browser, enter the following URL:
Log in to MetaLink.
Click the Certify tab.
Click View Certifications by Product.
Select the Application Server option and click Submit.
Choose Oracle Identity Management and click Submit.
Click Oracle Identity Management Certification Information 10g (10.1.4.0.1) (html) to display the Oracle Identity Management page.
Click the link for Section 6, Oracle Access Manager Certification to display the certification matrix.
Before you can integrate Oracle Access Manager with PeopleSoft, complete the following steps to prepare your environment.
Task overview: Preparing for the PeopleSoft integration
Install a supported directory server, according to vendor instructions.
Install and configure Oracle Access Manager using the directory server from the previous step as the LDAP repository.
Ensure that the PeopleSoft application pages are delivered using an HTTP Server.
Configure the Web browser to allow cookies, according to vendor instructions.
Follow the instructions in "Setting Up Oracle Access Manager Single Sign-On for PeopleSoft".
Follow the instructions in "Setting up PeopleSoft for Single Sign-On with Oracle Access Manager".
The following procedure describes setting up Oracle Access Manager single sign-on for PeopleSoft.
See also:
For more information on creating policy domains, policies, and associated authentication and authorization schemes, see the Oracle Access Manager Access System Administration Guide.To set up Oracle Access Manager for the PeopleSoft integration
Install and configure Oracle Access Manager on a supported platform, using a supported LDAP server.
See the Oracle Access Manager Installation Guide for details.
Install a WebGate on the PeopleSoft HTTP Server.
If your PIA application server is WebSphere or WebLogic, install an HTTP server, for example, Apache, iPlanet, or Oracle HTTP Server, and then configure PIA so that PeopleSoft application pages are accessed and rendered through the HTTP server. You then need to protect the HTTP server with the appropriate WebGate designed for that HTTP server.
Create a host identifier for the PeopleSoft HTTP Server.
From the Access System landing page, select the Access System Console, click Access System Configuration, click Host Identifiers, and add information about the server.
Create a policy domain and policies to restrict access to PeopleSoft URLs.
From the Access System landing page, select the Policy Manager, then click create Policy Domain, and define a policy domain and policies.
The policy domain should protect all PeopleSoft URLs that users access. For example, if you use PeopleSoft Portal to consolidate access to various PeopleSoft applications, the policy must protect the portal and application URLs.
URL prefix formats are specific to your PeopleSoft implementation. For example, the version 8.47 URLs have the format /PORTAL/ps, HRMS/ps, and so on.
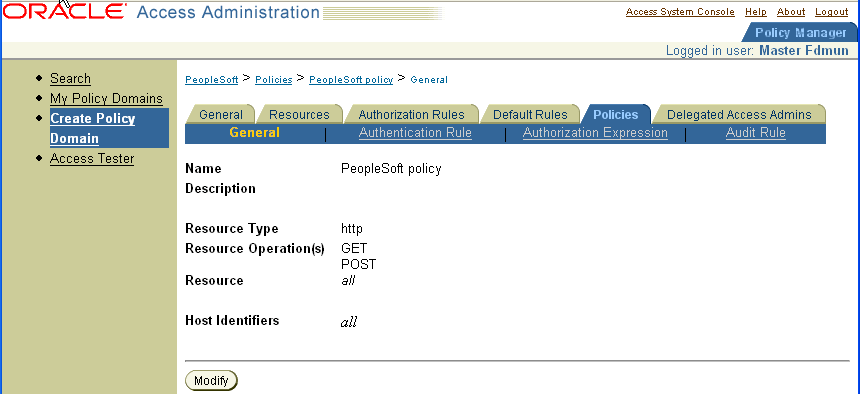
The following screen shot illustrates a PeopleSoft policy domain.
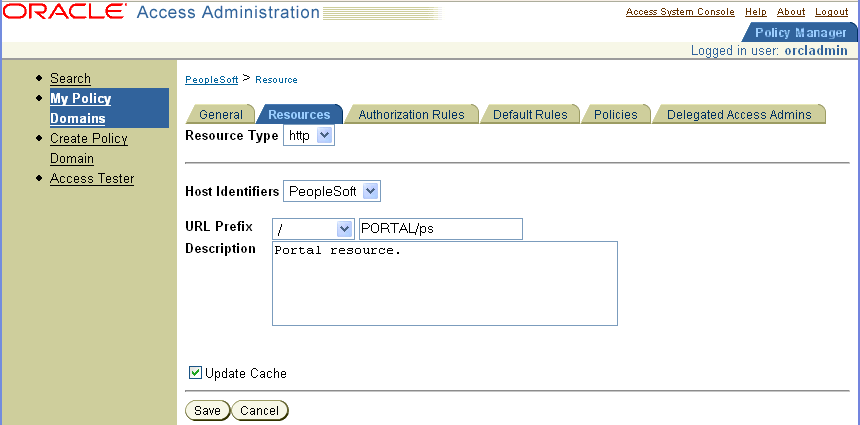
After saving the new policy domain, define an authorization rule that controls who has access to the PeopleSoft resources.
If you are already viewing the new policy domain, click Authorization rules. Otherwise, click My Policy Domains, click the link for the policy domain, and click Authorization rules.
The following is a screen shot of an Authorization Rules configuration page.
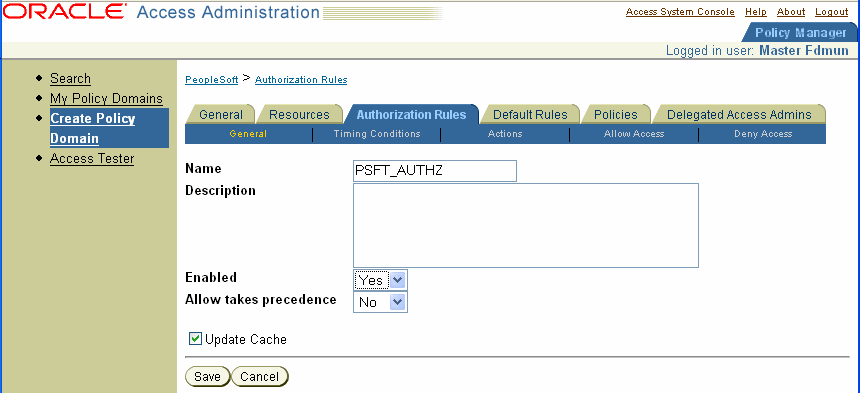
Define an authentication rule, for example, Oracle Access and Identity Basic Over LDAP, form authentication, and so on.
If you are already viewing the new policy domain, click Default Rules, then click Authentication Rule. Otherwise, click My Policy Domains, click the link for the policy domain, and click Default Rules, then click Authentication Rule.
The following is a screen shot of an Authentication Rule configuration page.
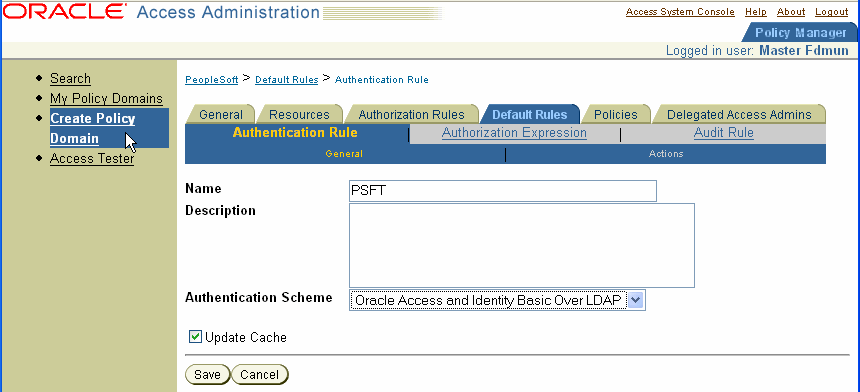
Define an authorization action that sets a custom HTTP header variable upon successful authorization.
If you are already viewing the new policy domain, click Authorization Rules, then click Actions. Otherwise, click My Policy Domains, click the link for the policy domain, click Authorization Rules, then click Actions.
The action should contain a redirection URL for authorization success.
The header variable should contain a value that maps to the PeopleSoft user ID.
The following is a screen shot of a saved authorization action.
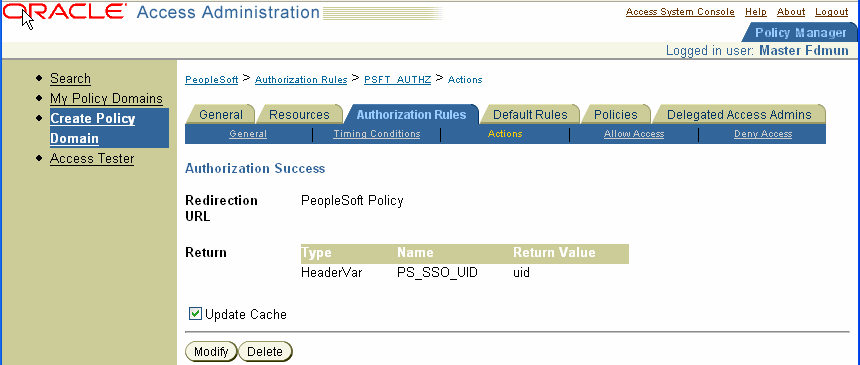
Define an access policy and add the PeopleSoft resources to it.
If you are already viewing the new policy domain, click Policies, then click Add. Otherwise, click My Policy Domains, click the link for the policy domain, click Policies, then click Add.
The following is a screen shot of a saved policy.
The following procedure describes setting up PeopleSoft for integration with Oracle Access Manager.
To set up PeopleSoft for integration with Oracle Access Manager
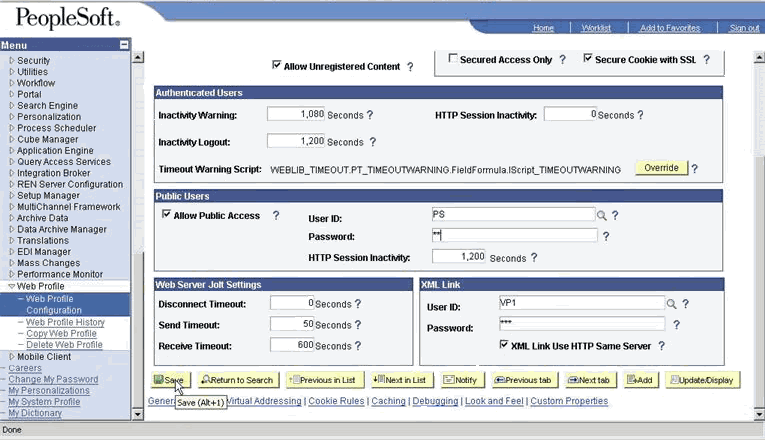
Configure PeopleSoft to allow public access.
To do this, you modify the Web profile for the PeopleSoft environment that you are securing. In PeopleTools 8.47, the Web profile definition contains all the information that PIA needs to render the PeopleSoft pages.
To allow public (unprotected) access to PeopleSoft, PIA requires a PeopleSoft application user. PIA logs using this application user and renders the PeopleSoft pages. In the Web profile, provide a user ID and password of a PeopleSoft user. Ensure that this user has minimal applications privileges.
From the PeopleTools Application Designer, open the FUNCLIB_LDAP record.
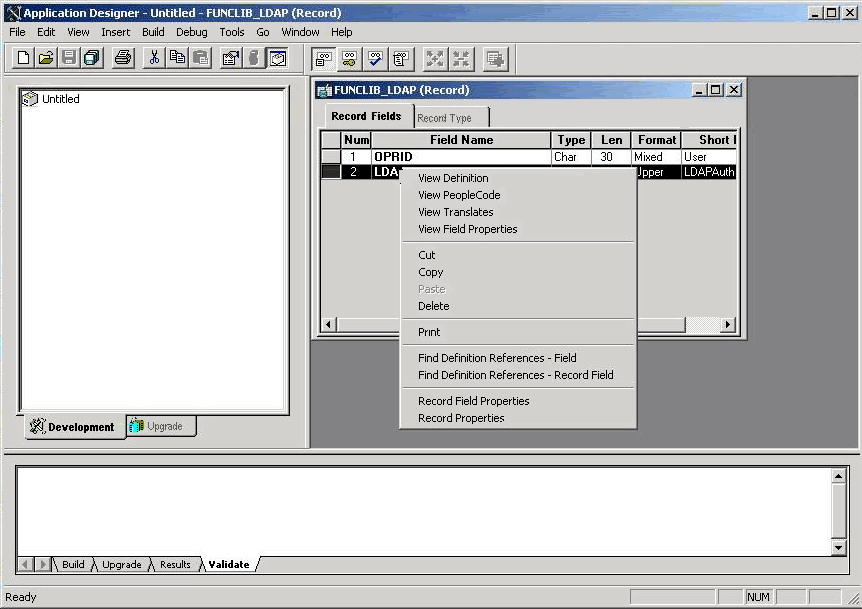
Modify the PeopleCode for the LDAPAUTH field event, as follows.
In the getWWWAuthConfig() function, replace the value that is assigned to the &defaultUserId with the user ID that you defined in the Web profile.
Function getWWWAuthConfig()
/* Begin - New code to support Oracle Access Manager */
/* authentication */
/* NOTE: replace v01475 with the default userid */
&defaultUserId = "v01475";
/* &defaultUserId = "";*/
/* End - New code to support Oblix authentication */
End-Function;
Add a new function that will read the HTTP header variable that is set by Oracle Access Manager, as indicated in the following code sample.
Function Oracle_Access_Manager_Authentication() /* Note: Following file will written to the default path.*/ /* Usually appserv/<instance name>/files */ &logfile = Getfile("oamaccess.log","A"); If &logfile.Isopen then &logfile.Writeline("INFO: Netpoint_Authentication_Profile started"); &logfile.Writeline(String(%Datetime)); &logfile.Writeline("authMethod: " &authMethod)); End-If; If %PSAuthResult = True And &authMethod <> "LDAP" And &authMethod <> "COREID" And &authMethod <> "SSO" Then If &logfile.Isopen then &logfile.Writeline("INFO: AuthResult and AuthMethod ok."); End-If; getWWWAuthConfig(); If &logfile.Isopen then &logfile.Writeline("INFO: After get wwwauthconfig."); &logfile.Writeline(&defaultUserId); End-If; If %SignonUserId = &defaultUserId Then If &logfile.Isopen then &logfile.Writeline("INFO: %SignonUserId = &defaultUserId "); End-If; &userID = %Request.GetHeader("PS_SSO_UID"); If &logfile.Isopen then &logfile.Writeline("INFO: After getting HTTPheader"); &logfile.Writeline(&userId); End-If; If &userID <> "" Then If &bConfigRead=False then getLDAPConfig(); If &logfile.Isopen then &logfile.Writeline("INFO: After getLDAPConfig()"); &logfile.Writeline(&userId); End-If; &GlobalUserID=&userID; If &logfile.Isopen then &logfile.Writeline("INFO: After DNTold"); &logfile.Writeline(&GlobalUserId); End-If; If &GlobalUserID <> "" Then SetAuthenticationResult(True,Upper(&GlobalUserID),"",False); &authMethod = "WWW"; If &logfile.Isopen then &logfile.Writeline("INFO: Userid is valid"); &logfile.Writeline(&GlobalUserID); End-If; End-If; End-If; Else If &logfile.Isopen then &logfile.Writeline("Warning: %SignonUserId not = &defaultUserId"); &logfile.Writeline(%SignonUserId); &logfile.Writeline(&defaultUserId); End-If; End-If; Else If &logfile.Isopen then /*Note: Next line sometimes wraps due to length – fix if necessary */ &logfile.Writeline("ERROR: %PSAuthResult = True And"); &logfile.Writeline("&authMethod <> ""LDAP"" And "); &logfile.Writeline("&authMethod <> ""SSO"""); &logfile.Writeline(%PSAuthResult); &logfile.Writeline(&defaultUSerId); &logfile.Writeline(%Request.GetHeader("PS_SSO_UID")); End-If; End-If; If &logfile.Isopen then &logfile.Writeline("INFO: Oracle_Access_Manager_Authentication_Profile exit"); &logfile.close(); End-If; End-If; End-Function;
Configure PeopleSoft to execute the function in the previous step when a user tries to access PeopleSoft pages.
To do this, modify the Signon PeopleCode function, enable the function in the previous step, and disable all other functions.
Restart the PeopleSoft Application Server and the PeopleSoft HTTP Server.
The following procedure describes how to configure single signoff for PeopleSoft.
To configure single signoff for PeopleSoft
On the Web server where PIA is installed, locate and open signin.html.
Copy signin.html to a file named signout.html.
Open signout.html in an editor and add the following information to it:
<HEAD> <meta HTTP-EQUIV='Refresh' CONTENT='1; URL=http://<Peoplesoft Web Server>/<Virtual PATH not protected by Access Manager>/logout.html'> </HEAD> </HTML>
Place the file logout.html that is provided with your Oracle Access Manager installation in a virtual path that is not protected by a WebGate.
The following is the default path:
Policy_Manager_install_dir/access/oblix/lang/en-us/logout.html
Where Policy_Manager_install_dir is the directory where the Policy Manager is installed.
The file contains Javascript that deletes the obTEMC cookie. See the appendix on configuring logout in the Oracle Access Manager Access System Administration Guide for details.
In your browser, in PIA, select PeopleTools, then select Web Profile, Web Profile Configuration, Look and Feel.
In the Signon/Logout Pages group box, change the value of the Logout Page field to signout.html.
An adminstrator may need to log in directly to PeopleSoft in the event that Oracle Access Manager is unavailable. This requires a workaround that opens a port for PeopleSoft.
The following example is specific to the Apache Oracle HTTP Server for PeopleSoft running on port 7777. In this example, the WebGate is configured to protect PeopleSoft only on port 7777, leaving other ports unprotected.
The following example assumes that you already have a complete integration of Oracle Access Manager and PeopleSoft.
To configure direct login to PeopleSoft on an Apache Oracle HTTP Server
Verify that listen port for the application that you want to protect with a WebGate exists in the httpd.conf.
For example if port 7778 is the port for a WebCache that points to the actual application on port 7777, the following may be configured:
Port 7777 Listen 7778
Comment out the default LocationMatch found in the Oblix or WebGate block in httpd.conf.
Add a new VirtualHost and LocationMatch directive at the end of httpd.conf.
The following is an example of modified httpd.conf file.
<!--[if !supportLists]-->1. <!--[endif]-->Comment out the following from the webgate section:
<LocationMatch "/*">
AuthType Oblix
require valid-user
</LocationMatch>
<!--[if !supportLists]-->2. <!--[endif]-->Add the following to the bottom of the file:
NameVirtualHost *:7777
<VirtualHost *:7777>
ServerName psw01.foo.com
<LocationMatch "/*">
AuthType Oblix
require valid-user
</LocationMatch>
</VirtualHost>