| Oracle® Access Manager Integration Guide 10g (10.1.4.2) Part Number E10356-01 |
|
|
View PDF |
| Oracle® Access Manager Integration Guide 10g (10.1.4.2) Part Number E10356-01 |
|
|
View PDF |
This chapter provides an overview of integrating Oracle Access Manager with Plumtree Corporate Portal. Note that this product is now called BEA Aqualogic Interaction, however, the currently certified integration is with the Plumtree Corporate Portal product.
This chapter covers the following topics:
The integration between Oracle Access Manager and Plumtree Corporate Portal provides companies with a Web enterprise solution for building customized, secure business portals with integrated, identity-based Web access management.
In the integrated solution, Plumtree Corporate Portal acts as a gateway to an enterprise intranet or extranet, providing users centralized access to a broad variety of applications and content hosted by the enterprise.
Oracle Access Manager provides a robust identity management and access security system to accurately track and manage the identities of Plumtree Corporate Portal's employees, customers, and partners. Oracle Access Manager also provides a common enterprise security and user identity infrastructure that controls access to Plumtree Corporate Portal as well as to other enterprise applications and resources.
The integration supports single sign-on (SSO) between the applications within the portal framework and the enterprise Web applications that are secured by the Access System.
This integration offers these major benefits:
Single Sign-On: The Access System's single sign-on services offer authorized users a secure connection with minimal authentication challenges to the resources that they need. Users need to log in only once to gain access to all resources that they need at a given level of authentication. The access provided by Access System's single sign-on services improves user efficiency, productivity, and user satisfaction.
Delegated Administration: Oracle Access Manager offers delegated administration capabilities that complement those of Plumtree Corporate Portal. Oracle Access Manager's delegated administration distributes responsibilities for managing identity and security policy information. Users can update some of their information; managers, suppliers, and partners can set up, change, and delete user identity information.
User and Group Management: Oracle Access Manager manages an LDAP directory server that contains user identity information. Plumtree Corporate Portal synchronizes its own user database with the LDAP directory. This eliminates the need to create and manage separate identity profiles for each application.
Oracle Access Manager also provides strong group management capabilities, including support for static, dynamic, nested, and hybrid groups. The Identity System manages the group information that the Plumtree Corporate Portal application uses to personalize the portal. Group affiliation is immediately reflected in the portal without manual changes.
Centralized Security Management: Oracle Access Manager provides a common security management platform for all applications within an enterprise. This facilitates the maintenance of consistent security policies across an entire enterprise.
User Personalization: Oracle Access Manager enables you to personalize portal content based on any user attribute, such as job title.
This integration does not change the users' experience in Plumtree Corporate Portal. Users can continue to access the portal guest pages without logging into Plumtree Corporate Portal. When a user attempts to log in, the Access System intercepts the request and uses an authentication scheme to determine whether the user is authorized to access the portal. Those who are not authorized are denied access to Plumtree Corporate Portal.
Figure 12-1 illustrates how Oracle Access Manager components protect the Plumtree Corporate Portal.
The following summarizes the integration.
Task overview: Integrating with Plumtree
Enabling single sign-on for the Plumtree Corporate portal as described in "Enabling Single Sign-on in PlumTree 5.0.4" on page 12-4.
In the Plumtree installation, you set up single sign-on and LDAP authentication sources, edit configuration files to support single sign-on, and then synchronize data from the Oracle Access Manager LDAP directory with the data in the Plumtree database.
Setting up the Access System to protect the Plumtree Corporate portal as described in "Setting Up the Access System to Protect Plumtree 5.0.4" on page 12-8.
In the Access System, you create policies that specify the content that you want to protect. Policies are created in the Policy Manager.
(Optional.) Allow anonymous users to view the portal guest pages and creating a banner for the portal as described in "Integrating Other Features".
(Optional.) Personalize user pages, and embed Identity System identity management functions as described in "Integrating Other Features".
You can find support and certification information at the following URL:
http://www.oracle.com/technology/documentation/
You must register with OTN to view this information.
Also, you can see the supported versions and platforms for this integration on Metalink, as follows.
To view information on Metalink
In your browser, enter the following URL:
Log in to MetaLink.
Click the Certify tab.
Click View Certifications by Product.
Select the Application Server option and click Submit.
Choose Oracle Identity Management and click Submit.
Click Oracle Identity Management Certification Information 10g (10.1.4.0.1) (html) to display the Oracle Identity Management page.
Click the link for Section 6, Oracle Access Manager Certification to display the certification matrix.
This section describes the following tasks for enabling single sign-on on the Plumtree portal:
Authentication is the process of users proving their identity to a server. After users present their credentials to the server, authentication plug-ins process those credentials. To enable the Access System to authenticate users and groups on Plumtree, you must create a single sign-on authentication source so that the Access System can authenticate users and groups in the Plumtree portal. To do this, you must first create a single sign-on password to use when you configure the single sign-on authentication source.
To create a single sign-on password
Launch the Plumtree Administrator Control Panel application and navigate to Start, select Settings, select Control Panel, then click Plumtree Administrator.
The Plumtree Administrator dialog box appears.
Click Single Sign-On.
Enter an SSO secret key.
Note:
This secret key can be any string of characters. Make note of the string.Click OK to close the Plumtree Administrator dialog box.
To create a single sign-on authentication source on Plumtree
Log in to Plumtree as the administrator. Click Administration. The Administration Menu appears.
Click Authentication Folder. In the Create Object drop down box select Authentication Source-SSO. The Authentication Source Wizard appears.
Enter the single sign-on password.
Click Validate Options to confirm that this password matches the secret key you entered in the Plumtree Administrator Control Panel.
On the Properties and Names page, enter a name and description for the new authentication source. Describe the source carefully, as this description appears in a list during Authentication Source setup.
Specify the properties for the Authentication Source.
To update the Plumtree database with the current user and group information, you must synchronize users and groups in the Plumtree database with information in the LDAP directory. To do this, you must first create an LDAP Authentication Source to import users and groups data from the LDAP directory into your Plumtree portal. To create an LDAP authentication source on Plumtree.
Log in to Plumtree as the administrator and click Administration.
The Administration Menu appears.
Click Authentication Folder. In the Create Object drop down box, select Authentication Source-SSO. The Authentication Source Wizard appears.
In the Authentication Source Category box, type the prefix used to distinguish the users and groups imported from this domain. For example, if you enter myDomain, each user name and each group name will be prefixed by the string myDomain. Thus, myUser becomes myDomain\myUser and myGroup becomes myDomain\myGroup.
You can set the category to any value you want, but after you create this authentication source, you cannot change this value.
Templates can populate configuration options with common default values. To use an existing template to populate the values in this editor, choose one from the Template list.
Add values under LDAP Settings to facilitate portal access to the LDAP server from which you are importing users. Consult online help for instructions.
To confirm the domain you entered, click Validate Options.
After the portal has attempted to find the domain, it displays a message stating whether it connected successfully or not.
If the validation fails, check for errors in your settings.
If the validation succeeds, go to the Synchronization page.
Select the single sign-on authentication source you created earlier from the list labelled Select an Authentication Partner. Select Full Synchronization.
On the Schedule page, select Create a Job/Add a Job for this Authentication Source. Consult online help for instruction on creating or adding a job.
Add appropriate properties on the Properties and Names page.
By default, the portal expects Oracle Access Manager to forward the user name header named uid. If you configure Oracle Access Manager to forward a user name header with a different name, you must configure your single sign-on implementation as BasicSSO service. For details about BasicSSO service, see the PlumTree Administration Guide.
Configure elements under the <Authentication> parent element in the PTConfig.xml, as detailed in Table 12-1.
Table 12-1 Parameters In Ptconfig.xml
| Parameter | Value |
|---|---|
|
SSOVendor |
For Oracle Access Manager the SSOVendor value is 3. |
|
DefaultAuthSourcePrefix |
Use the same value you specified for Authentication Source Category when you configured your authentication source. |
|
CookiePath |
" /" (Specify a different setting only if your single sign-on authentication server requires a different convention.) |
|
CookieDomain |
Specify the fully qualified domain name to which you want the cookie forwarded. For example, if you specify |
|
SSOCookieIsSecure |
0 or 1. 0 (the default) specifies that the connection to the remote server does not require SSL for the cookie to be forwarded. 1 specifies SSL is required. |
The following example enables integration with an Oracle Access Manager authentication server:
<SSOVendor value="3"/><DefaultAuthSourcePrefix value="HQ"/><CookiePath value="/"/><CookieDomain value=".company.com"/><SSOCookieIsSecure value="0"/>
Data synchronization ensures the updating of information on group memberships and users, which is crucial for portal access and personalization. You can synchronize data manually or automatically at specific time intervals. To synchronize manually, you schedule a job and run it once for immediate synchronization. For periodic synchronization, you schedule a job to run at specified time intervals.
After you run a job, you can view its status to see if it ran successfully. When a job has run successfully, you can view the replicated LDAP data in the Plumtree database.
Caution:
Initial full synchronization requires a long time if you have many entries.You must fully synchronize at least once to enable single sign-on between Plumtree and Oracle Access Manager.
To automatically synchronize data
On the Plumtree portal host, navigate to Control Panel, then Services, and verify that the Plumtree Job Dispatcher service has started.
Log in to Plumtree as the administrator, then click Administration.
In the Administration Menu, navigate to the Administration folder, click Jobs, then select the job you earlier created / added for the LDAP Authentication Source. The main settings page appears.
Specify the time period when the synchronization job is to be run.
The Edit Job User page also provides options for checking the job log and history through the Job History tab. It also lets you check security-related options.
On the Plumtree portal host, navigate to Control Panel, then select Services, and verify that the Plumtree Job Dispatcher service has started.
Log in to Plumtree as the administrator, then click Administration.
In the Administration Menu, click the Administration folder, select Jobs, then select the job you earlier created / added for the LDAP Authentication Source. The main settings page appears.
Select Run Once - Now option in the settings. This job runs once, starting immediately.
After synchronization has been completed, you should be able to see all the users and groups from the LDAP data source replicated in the Plumtree database.
To view the updated Plumtree database
In the portal, click Administration.
In the Administration Menu, click your administration folder.
Expand the Users tab. The user names will be prefixed with the LDAP source name.
For example:
LDAPUsers\Accounting Managers
In a Group folder, you can also view the members of the groups.
When a user clicks the PlumTree Log Off button in an Access System-protected PlumTree session, users are logged out from PlumTree, but the ObSSOCookie generated for the users is not killed. Hence, the Oracle Access Manager session for that particular user remains active. Users need to customize the PlumTree logout functionality to facilitate logout from PlumTree as well as Oracle Access Manager.
Consult "Customizing the Portal UI: Using Plumtree Event Interfaces (PEIs)" section in "Enterprise Web Development Documentation" on the PlumTree Web site for information on modifying the PlumTree UI. Users need to implement the "OnBeforeLogout" interface as:
public virtual Redirect OnBeforeLogout(Object _oUserSession, ApplicationData _appData)
{
PTDebug.Trace(Component.Portal_UI_Infrastructure, TraceType.Error, "Before logout event");
String myCookie = _appData.GetCookie("ObSSOCookie");
if(myCookie != null)
{
Redirect myredirect = new Redirect();
myredirect.SetLinkToExternalURL("http://<AccessManager_Server_Name:port>/access/oblix/lang/en-us/logout.html");
return myredirect;
}
return null;
}
Typically, users click the Login button to log in to the Plumtree Corporate Portal. Once they are authenticated, they can view their personalized pages. To log out of the portal, users click the Logout button. In an alternate configuration, you might want all users to see a guest portal, then authenticate users only when they log in to the portal. (If you have enabled user access to the guest pages, then any user can go the main portal page and view those guest pages without ever logging into the portal).
When a user attempts to login, the Access System authentication policy challenges the user. Once the Access System authenticates the user, it checks to see if the user is authorized. If the user is authorized, an ObSSOCookie and a header variable are sent to enable single sign-on into Plumtree. The user is then logged in to Plumtree.
You can configure the Plumtree Corporate Portal so that when users log out, they are automatically logged out of both Plumtree and Oracle Access Manager. To set up the Access System's single sign-on service for Plumtree, after you have installed the Access System, you must create policies in the Policy Manager that specify the content you want to protect.
Setting up the Access System to protect Plumtree consists of the following tasks:
To integrate with Plumtree, you must install the following applications:
Identity Server
Access Server
WebPass
Policy Manager
WebGate
To enable the Access System to protect the portal, install a WebGate on the Plumtree Corporate Portal Web server.
Note:
You can install the Identity server, WebPass, and Access System on the same server. However, Oracle recommends that you do not install the Identity Server and WebPass on the server where Plumtree has been installed. For more information on installing and configuring Oracle Access Manager, see the Oracle Access Manager Installation Guide.To create the policy domain, follow the procedure in "Creating a Policy Domain".
For more information on policy domains, see the Oracle Access Manager Access System Administration Guide.
Install Oracle Access Manager, which includes the following components: Identity Server, WebPass, Access Server, and Policy Manager.
Launch the Access System, as follows:
http://Access_Server_install_dir:port/access/oblix.
Click the link for the Policy Manager application.
In the Policy Manager, create a policy domain.
In the Resources tab for this policy domain, select a backslash ("/") as the URL prefix and type the path to the SSO servlet in the adjacent text box.
For example: portal/SSOServlet or portal/sso/ssologin.aspx
Click the Authorization Rules tab for this policy domain and enter basic information for the new authorization rule.
Click the Actions sub-tab for the authorization rule and add the following action:
In the Type field, enter a descriptive name, for example, headerVar.
In the Name field, enter a descriptive name, for example, UID.
In the Return field, enter the name of an attribute that is used by the authentication source to map to the user name in the user directory.
For example, iPlanet LDAP uses the uid attribute by default. Other LDAP directories, including Active Directory, use cn by default.
Configure your WebGate following the procedure appropriate for your portal deployment in the Oracle Access Manager Installation Guide:
WebGate for Apache
WebGate for IIS
Use the version of the WebGate that matches the version of your Oracle Access Manager.
You can find support and certification information at the following URL:
http://www.oracle.com/technology/documentation/
You must register with OTN to view this information.
Also, you can see the supported versions and platforms for this integration on Metalink, as follows.
To view information on Metalink
In your browser, enter the following URL:
Log in to MetaLink.
Click the Certify tab.
Click View Certifications by Product.
Select the Application Server option and click Submit.
Choose Oracle Identity Management and click Submit.
Click Oracle Identity Management Certification Information 10g (10.1.4.0.1) (html) to display the Oracle Identity Management page.
Click the link for Section 6, Oracle Access Manager Certification to display the certification matrix.
To set up the WebGate for Apache
On the host computer for the Portal Server, install the version of Apache required by the WebGate.
Note:
The version of Apache provided by Plumtree and described in the Installation Guide for Plumtree Corporate Portal cannot be used with the WebGate. You must download the required Apache version from the Apache Web site.On the host computer for the Portal Server, install the WebGate for Apache. For details, see theOracle Access Manager Installation Guide.
On the Web application server to which the portal application is deployed, modify the Web application server setting to turn off URL rewrites. For details, refer to your Web application server documentation or Plumtree Knowledge Base article DA_239501, "Configuring Web Application Servers to not Rewrite URLs."
Install the version of the WebGate that matches your Oracle Access Manager.
To set up WebGate for IIS, run the WebGate for IIS installer on the host computer for the Portal Server.
Oracle Access Manager offers several other features that you can integrate with Plumtree such as allowing guest users to view portal pages, personalizing user pages, and embedding other identity management functions into your portal. You can also set up single sign-on to other portals, and manage passwords and self-registration.
The following tasks are discussed in this section:
You can allow anonymous users to access guest pages without logging into the portal. To do this, you must create a policy domain in the Access System that uses the Anonymous authentication scheme for the Oracle Access Manager Anonymous user. The Anonymous authentication scheme is a default that is supplied with the Access System.
This allows users to go to the main portal page and view guest pages without being challenged by the Access System.
You then lock the NetPointAnonymous account to allow anonymous users to view the guest pages without logging into the Plumtree portal. When a user goes to the main portal page but does not log in, the Access System logs in the user as NetPointAnonymous and creates an ObSSOCookie for this anonymous user. The ObSSOCookie is sent to the Plumtree portal but the portal treats the user as a guest because the account is locked. Thus, the user can view guest pages.
To create a policy domain for guest access
Launch the Policy Manager and click Create Policy Domain.
In the General tab, enter a name and description for the new policy domain.
In the Resources tab, select HTTP as the resource type.
To use a host identifier, create a host identifier in the Access System Console.
You must add a fully qualified host name as one of the host name variations; for example, plum1.oracle.com.
See the Oracle Access Manager Access System Administration Guide for more information.
Select the portal URL prefix from the list or create a new one. For example, /portal.
In the Default Rules tab, click Authentication Rule and from the Authentication Scheme list, select Anonymous Authentication.
This enables a user to view guest pages without logging in to Plumtree.
In the Policies tab, enter the following information:
Name: Enter a name for the policy.
Description: Enter a description of the policy.
Resource Type: Select HTTP.
Resource Operations: Select GET.
Host ID: Enter the ID of the portal host.
Resource: Select /portal.
URL pattern: Enter admin/loginoblix.asp.
Host identifiers: Enter the host identity.
Query String: Enter a query string.
Query String Variable: Enter User ID as the name and 2 as the value.
Note:
The Netscape Web server is case-sensitive. Do not change the case of the query string variable name.Click Save to save the policy.
In the Policies tab, click the name of your policy.
The policy details page appears.
Click Authentication Rule and create an authentication rule.
You can use any authentication scheme such as Basic over LDAP or any custom authentication scheme.
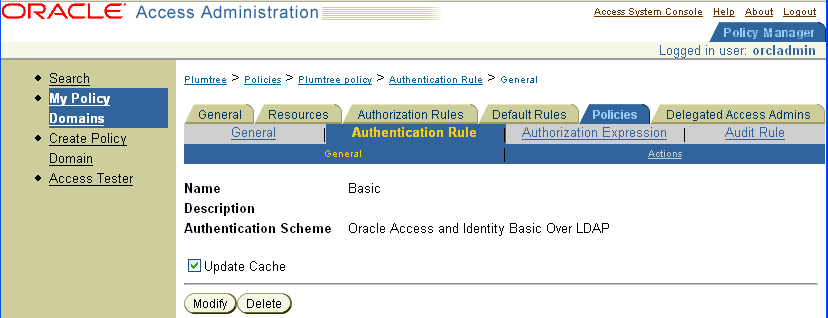
In the Authorization Rules tab, select Actions, and add a header variable that you specified in the file oblix.asp.
To facilitate single sign-on, you must specify this header variable to direct Plumtree to look for this header variable as described in "Editing Configuration Files to Support Single Sign-On".
In the Return Attribute field, enter the Login ID attribute and click Save.
Enable the policy domain.
On the Plumtree Portal, lockout the user as described in the section "To lock the NetPointAnonymous account".
To lock the NetPointAnonymous account
On Plumtree, log in as the administrator to the portal.
Click Users and click the folder that matches the authentication source category you created as your LDAP authentication source.
Click the user for the Anonymous authentication scheme.
It will have the prefix of the name you gave to the LDAP authentication source.
In the user page, select Lock this User so it cannot be used for login.
The NetPointAnonymous user becomes the equivalent of the Plumtree guest user.
Note:
If you want to log in to Plumtree with the Plumtree database credentials (such as administrator), you must first authenticate yourself to Oracle Access Manager and then click Login as a different User. The Plumtree Login screen appears and you can log in as a different Plumtree user.To log in to Oracle Access Manager as a different user, first click Logoff to log out of Plumtree and then click Login. The Login box appears, and you can log in as a different user.
The PlumTree 5.0.4 Knowledge Directory is a portal area that users browse to discover document records containing links to documents that have been uploaded by users or crawlers. Users can add Identity System links and Access System-protected resources links to the knowledge directory. Whenever a user tries to access links in the knowledge directory, the ObSSOCookie for that user, if it exists, is passed to the resource for user authentication, thus facilitating single sign-on.
The knowledge directory information is organized into subfolders in a manner similar to file storage volumes and shares. The default portal installation includes a Knowledge Directory root folder with one sub-folder named Unclassified Documents. Before you create additional subfolders, you must define your Knowledge Directory taxonomy, as described in the Deployment Guide for the Plumtree Enterprise Web.
This section discusses the following topics:
You specify how the Knowledge Directory displays documents and folders, including whether to generate the display of contents from a Search Server search or a database query, by setting Knowledge Directory preferences.
To set Knowledge Directory preferences
Click Administration.
In the Select Utility list, click Knowledge Directory Preferences.
Specify preferences according to the instructions provided through online help.
Click Finish.
To create a Knowledge Directory folder, complete the following procedure.
To create a Knowledge Directory folder
Navigate to Directory, then click Edit Directory.
Navigate to the folder into which you want to place a new subfolder.
Launch the Folder Editor.
Specify a name and description, then click OK.
Select the Edit Details icon, then complete the settings according to the instructions supplied in the online help.
To upload documents to the Knowledge Directory folder, complete the following procedure.
Browse to the folder where you want to upload the document.
From the Submit a Document list, choose Simple Submit or choose a data source.
Complete the submission forms as described in the online help.
Use filters to control what content goes into which folder. A filter sets conditions to sort documents into associated folders in the Knowledge Directory. Please see PlumTree documentation for more details.
The password policies that you set on the Access System are always enforced because Oracle Access Manager manages passwords and the Access System evaluates the policies when a user logs in to the portal.
Users who are not logged in to the Plumtree portal must have access to the Lost Password feature in Oracle Access Manager. This enables users who have lost their passwords to set a new one. See the Oracle Access Manager Identity and Common Administration Guide for details.
To enable password management, you must create appropriate policies in the Access System. You also need to use the knowledge directory to upload a document that contains a link to the Lost Password Management feature in Oracle Access Manager. See "Using the Knowledge Directory" for details.
Note:
Oracle recommends that you back up configuration files before you modify them.You need to enable, manage, and configure self registration. To enable self-registration, the appropriate self-registration workflow must be created in the User Manager. See the Oracle Access Manager Identity and Common Administration Guide for details. This workflow is used in the self-registration portal insert. To manage self-registration, you need to use knowledge directory to upload a document that invokes the Identity System self-registration feature. See "Using the Knowledge Directory" for details. The Plumtree database must then be synchronized to be updated with the newly created user.