

The credential vault (AquaLogic Interaction 6.0 and above) provides a central repository that securely stores and manages all credentials. Portlets that need login information to access a back-end application can securely retrieve the appropriate user credentials from a central location. Credentials are sent in portlet headers, using RSA public key/private key encryption.
The IDK ICredentialProvider interface (com.plumtree.remote.portlet.ICredentialProvider) allows you to access user credentials stored in the central credential vault. Users enter their credentials only once in their account settings and have seamless access to every application they interact with throughout the portal session.
You can also use IDK methods to encrypt and decrypt authentication settings stored in the ALI database. For details, see Using IDK Encryption.
To use the credential vault, you must create a Lockbox in the portal that is associated with the authentication source. To create or configure a Lockbox, go to portal administration and click Choose Utility | Credential Vault Manager. For details on using the Credential Vault Manager and creating Lockboxes, see the portal online help.
To configure the credential vault for use with your portlet, three steps are required:
In the Remote Server editor, enter the public key for RSA encryption.

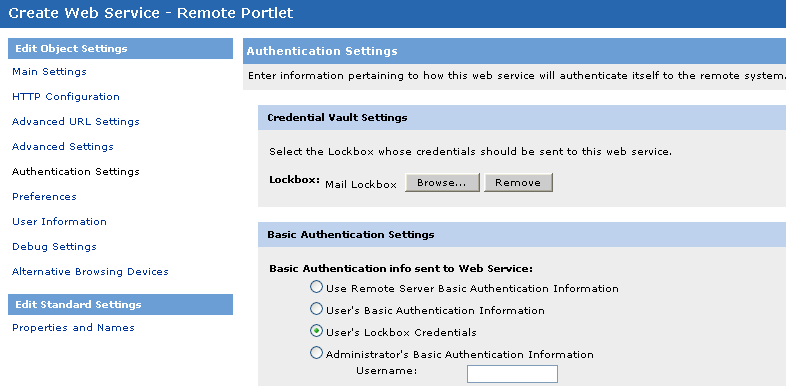
In the Web Service - Portlet editor on the Authentication Settings page, choose the appropriate Lockbox and set the Basic Authentication Settings to User's Lockbox Credentials. (You must have already created a Lockbox associated with the authentication source as explained above.)
Provide the private key for RSA encryption in one of two ways:
Note: If you do not enter a key, the credential vault will use Base64 encryption.
ICredentialProvider lets you retrieve the user name and password from portlet headers with a few lines of code. If the public key for RSA encryption is set in the web.xml/Web.config file, the setPrivateKey method is not required.
Note: The values in the configuration file override any value set through the setPrivateKey method.
You can also use ICredentialProvider to access settings encrypted in RC2, AES and Base64 that are stored in the ALI database. For details, see Using IDK Encryption.
Java:
|
// get an ICredentialProvider instance from IPortletContext // set the private key used to decrypt the password // get the username and password
|
C#:
|
// get an ICredentialProvider instance from IPortletContext // set the private key used to decrypt the password // get the username and password |
Next: Using IDK Encryption