| Oracle® Identity Manager Concepts Release 9.1.0.1 Part Number E14065-01 |
|
|
View PDF |
| Oracle® Identity Manager Concepts Release 9.1.0.1 Part Number E14065-01 |
|
|
View PDF |
This chapter discusses the following deployment configurations of Oracle Identity Manager:
You can use Oracle Identity Manager to create, maintain, and delete users on target systems. In this configuration, Oracle Identity Manager acts as the front-end entry point for managing all the user data on the target systems. After accounts are provisioned, the users for whom the accounts have been provisioned can access the target systems without any interaction with Oracle Identity Manager. This is the provisioning configuration of Oracle Identity Manager.
The purpose of provisioning is to automate the creation and maintenance of users on target systems. Provisioning is also used to accommodate any requirement for workflow approvals and auditing that can be a component of that provisioning life cycle. Figure 5-1 illustrates the working of the provisioning module.
Provisioning events can be started through any of the following ways:
Request-based provisioning
A request can be manually created by an administrator or, in certain cases, by users themselves. Approval workflows are started after a request is submitted and provisioning of the approved account profile is started after the approval is completed.
Policy-based provisioning
This type of provisioning refers to the automation of target resources being granted to users through access policies. Access policies are used to define the association between user groups (or roles) and target resources. By default, each member of these user groups gets a predefined account in the target resource. In addition, you can also use Oracle Identity Manager to create approval processes that can be run as part of the policy-based provisioning cycle.
This type of provisioning is a special administrator-only function. You can create an account for a particular user on a target system without having to wait for any approval processes.
Oracle Identity Manager provides a centralized control mechanism to manage users and entitlements and to control user access to resources. However, you can choose not to use Oracle Identity Manager as the primary repository or the front-end entry point of your user accounts. Instead, you can use Oracle Identity Manager to periodically poll your target systems for maintaining an up-to-date profile of all accounts that exist on those systems. This is the reconciliation configuration of Oracle Identity Manager.
Note:
For some target systems, the reconciliation of updates to user information takes place in real time and does not require periodic polling of the target system by Oracle Identity Manager.Figure 5-2 illustrates reconciliation.
As shown in this figure, Oracle Identity Manager is used only as a single updated store for all users, user groups, and organization data of the target system. Users are created, deleted, and maintained by local resource-specific administrators.
Reconciliation involves using the user discovery and account discovery features of Oracle Identity Manager.
The following sections provide more information about reconciliation:
Configuring reconciliation involves selecting a combination of options from the following reconciliation parameters:
To create a reconciliation configuration, you must select one option from each of these parameters. See "Sample Reconciliation Configurations" for examples of reconciliation configurations.
This section describes the reconciliation types, trusted source and target resource.
While configuring reconciliation, you can designate a target system as a trusted source. In a trusted source reconciliation run, newly created users on the target system are reconciled into Oracle Identity Manager. In other words, the target system acts as the trusted source for information about new users. Trusted source reconciliation also involves the reconciliation of changes to user records that already exist in both the target system and Oracle Identity Manager.
Figure 5-3 illustrates the steps involved in trusted source reconciliation.
In the operating environment of your organization, multiple target systems might act as trusted sources for the various attributes that constitute the user account. For example, employees' first names and last names might come from the HR system, and employees' e-mail addresses might come from Microsoft Active Directory. In such a scenario, you can configure each target system as a trusted source for a specific attribute or set of attributes of the user accounts. By doing this, you configure multiple trusted source reconciliation, which is a special implementation of trusted source reconciliation.
Note:
Figure 5-3 shows the target fields mapping to Oracle Identity Manager User attributes.In another form of multiple trusted source reconciliation, you designate multiple target systems as trusted sources for user accounts belonging to specific user types. This is illustrated by the following example.
In the operating environment of your organization, Siebel is used to track transactions with customers. User accounts created for customers are grouped under the Customer user type. Sun Java System Directory is used to store information about employees in the form of user accounts that are grouped under the Employee user type. When you configure multiple trusted source reconciliation, you designate Siebel as the trusted source for all accounts of the Customer user type and you designate Sun Java System Directory as the trusted source for all accounts of the Employee user type.
In summary, multiple trusted source reconciliation can be implemented in one of the following forms:
Each target system is designated as the trusted source for a specific attribute or a set of attributes of the user account.
Each target system is designated as the trusted source for a particular user type.
See Also:
The "Limited or Regular Reconciliation" section
The "Resource Objects Form" section in Oracle Identity Manager Design Console Guide for more information about multiple trusted source reconciliation
In the Oracle Identity Manager context, a target system that is not a trusted source is designated as a target resource. For an OIM User, you can create, modify, or delete target resource accounts through provisioning operations performed in Oracle Identity Manager.
See Also:
The glossary of Oracle Identity Manager Reference for the definitions of the terms OIM User and OIM AccountAlternatively, these operations can be performed on the target resource itself. A target resource reconciliation run is aimed at reconciling into Oracle Identity Manager the creation of or changes to user accounts on a target resource.
For example, a resource representing the Microsoft Active Directory target system is provisioned to an Oracle Identity Manager user, and an attribute of the resource is modified outside of Oracle Identity Manager. The modification in the provisioned instance can be reconciled into Oracle Identity Manager through target resource reconciliation.
Figure 5-4 illustrates the steps involved in target resource reconciliation.
Figure 5-4 Target Resource Reconciliation
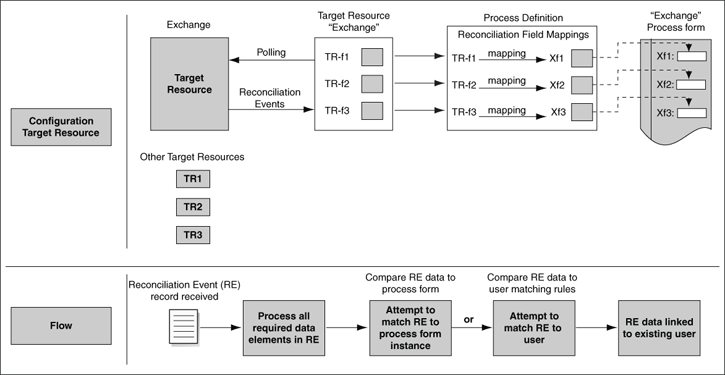
You can use Oracle Identity Manager to perform full reconciliation with a target system. The purpose of this mode of reconciliation is to reconcile all accounts on the target system into Oracle Identity Manager. Full reconciliation is performed by default during the first reconciliation run performed on a target system. At the end of this reconciliation run, the value of the timestamp IT resource parameter is set to the time at which the reconciliation run ended. For the next reconciliation run, only user account records that have been added, modified, or deleted after the first reconciliation run ended are fetched for reconciliation. In other words, from the second reconciliation run onward, incremental reconciliation becomes the default reconciliation mode.
You can manually switch from incremental reconciliation to full reconciliation by setting the value of the timestamp parameter to 0. At the end of the next reconciliation run, the timestamp IT resource parameter is set to the time at which the reconciliation run ends and incremental reconciliation is performed from then onward.
Note:
The implementation of the timestamp parameter is different for different target systems. For example, theLast Recon TimeStamp parameter is used in Sun Java System Directory.During a reconciliation run, all changes in the target system records are reconciled into Oracle Identity Manager by default. Depending on the number of records to be reconciled, this process might take a long time to complete. In addition, if the connection breaks during reconciliation, then the process takes longer to complete. You can configure batched reconciliation to avoid such problems.
In batched reconciliation, the total set of records to be reconciled is divided into batches containing the number of records that you specify as the batch size.
See Also:
The connector pack documentation for information about the actual implementation of this featureSuppose that Sun Java System Directory is configured as a target system in the operating environment of your organization. To configure batched reconciliation for this target system, you specify values for the following scheduled task attributes:
StartRecord: Use this attribute to specify the record number from which batched reconciliation must begin. You specify 120 as the value of this attribute.
BatchSize: Use this attribute to specify the number of records that must be included in each batch. You specify 50 as the value of this attribute.
NumberOfBatches: Use this attribute to specify the total number of batches that must be reconciled. You specify 6 as the value of this attribute.
At the start of the next reconciliation run, if there are 136 records to be reconciled, then these records will be divided into three batches of 50, 50, and 36 records and then each batch is reconciled into Oracle Identity Manager.
If you do not want to configure batched reconciliation, then do not specify a batch size. In this case, a nonbatched reconciliation will occur.
By default, all target system records that are added or modified after the previous reconciliation run are reconciled during the current reconciliation run. You can filter records for reconciliation by specifying the subset of newly added or modified records that must be reconciled. You implement this form of limited reconciliation by creating customized queries for reconciliation. The following example illustrates how limited reconciliation works:
For Sun Java System Directory, you implement limited reconciliation by specifying a customized query as the value of the CustomizedReconQuery IT resource parameter. The following are sample customized queries:
givenname=John&sn=Doe
With this customized query, records of users whose first name is John and last name is Doe are reconciled.
givenname=John&sn=Doe|departmentnumber=033
With this customized query, records of users who meet either of the following conditions are reconciled:
The user's first name is John and last name is Doe.
The user belongs to the department whose number is 033.
For any target system, if you do not specify a custom query, then a regular reconciliation takes place.
Multiple trusted source reconciliation by user type or any other user attribute is a special implementation of limited reconciliation. A customized query is used to specify the user type or attribute value, and only target system records that contain the specified value are fetched for reconciliation.
As mentioned earlier, you configure reconciliation by selecting specific options from the reconciliation parameters discussed in the preceding sections. The following sample reconciliation configurations are supported:
Trusted source, full, batched, and regular reconciliation for a single target system. For example, Oracle e-Business Employee Reconciliation for all Oracle Identity Manager users.
Trusted source, incremental, and regular reconciliation for a single target system. For example, Oracle e-Business Employee Reconciliation for all Oracle Identity Manager users.
Target resource, full, and regular reconciliation. For example, IBM RACF for all user accounts.
Target resource, incremental, and batched reconciliation. For example, Lotus Notes for all user accounts.
In a multiple trusted source environment, the combination of the following reconciliation runs provides the complete user identity population of a single Oracle Identity Manager deployment.
Multiple trusted source, full, nonbatched, and limited (userType=Employee) reconciliation. For example, Oracle e-Business Employee Reconciliation for only Employee OIM User type.
Multiple trusted source, full, batched, and regular reconciliation. For example, Microsoft Active Directory for only Contractor OIM User type.
This section describes the following components of the reconciliation module:
The published set of Oracle Identity Manager APIs includes a set related to reconciliation. Oracle Identity Manager uses these APIs to create reconciliation events. Because they are part of the generic API set, they can be used from any Java-based system. These APIs provide for the creation of both Regular and Delete Reconciliation events, and the mechanisms by which the appropriate data is provided for the events.
See Also:
Chapter 2, "What's New" of Oracle Identity Manager API Usage Guide for information about the APIs related to reconciliationWhen you define a target system as a resource object in Oracle Identity Manager, you create reconciliation fields to represent the actual fields of the target system. This eliminates setting up the reconciliation connection to translate data from target system field names to Oracle Identity Manager field names.
When defining a reconciliation field, you must provide information in addition to the name of the field. Define a field type that indicates the type of data that the field will receive. Values for field type are String, Number, Date, IT Resource, and Multi-Valued.
After you define the reconciliation fields, you must map them to the fields that are defined on a process form. These mappings serve the following purposes:
See Also:
"Process Definition Form" in Oracle Identity Manager Design Console GuideDefine how you use the data received from the target system to update the fields on the process form.
For example, if a reconciliation field for the Object1 resource object is attribute1, and it is mapped to the process form field field1, then the value received for attribute1 will be the value that is set on field1. For multivalued fields, the field will map to a particular child table on the process form. The interface will only show child table elements. For a trusted source, the process form fields are replaced with the fields from the entity form (user or organization form), including user-defined fields.
Some of the mappings can be defined as key mappings. These mappings constitute the Process Matching Rule used to identify the record that must be updated. Suppose that the mapping defined in the previous example is also identified as a key mapping. In this case, when the reconciliation engine performs rule evaluation, it searches for all provisioned instances of Object1 in which the value of field1 is the same as the value for attribute1 in the reconciliation data.
Note:
Key mappings hold true for target resource reconciliation only.See Also:
The "Reconciliation Field Mappings Tab" section in Oracle Identity Manager Design Console Guide for information about status reconciliationThe reconciliation matching rules are used by the reconciliation engine to determine the identity to which Oracle Identity Manager must assign a newly discovered account on the target system. The reconciliation engine can locate the user of the newly discovered account based on well-known patterns established for the target system. Consider the following example:
Suppose that all login IDs on the target system are created from the user's initial and last name. You could then set up a rule that accepts the login ID received from the target system and searches for any user whose first name starts with the first character of the login ID, and the last name is the same as the remainder of the login ID.
See Also:
"The Reconciliation Manager Form" in Oracle Identity Manager Design Console Guide for more information about reconciliation matching rulesUsing the reconciliation action rules, you can define the following actions that the reconciliation engine must automatically perform based on the scenarios that arise from reconciliation rule evaluations:
Assign an event to an administrator.
Create a new provisioned resource in Oracle Identity Manager and associate it with the corresponding owner identity.
Update the matched provisioned resource in Oracle Identity Manager.
Delete the matched provisioned resource in Oracle Identity Manager.
Create a new user in Oracle Identity Manager.
Update an existing user in Oracle Identity Manager.
Delete an existing user in Oracle Identity Manager.
See Also:
"The Resource Objects Form" in Oracle Identity Manager Design Console Guide for more information about reconciliation action rulesThe reconciliation engine uses all configurable components and includes the data processor and rule evaluator that use these components to convert input data into a list of action items. It also includes the components that determine whether or not the actions can be automated based on the rule context. When an action is performed, either automatically or manually, the engine performs the appropriate updates and provisioning actions.
The Reconciliation Event Manager is a form in the Design Console. You can use this form to examine a reconciliation event and perform the required actions. The Reconciliation Event Manager displays the data received, results of rule evaluation, actions that you can perform, and results of the actions.
The main section of the form displays the event information, including the resource object with which it is associated, the date the event occurred, its current status, and the entity to which it is linked. The following are action buttons in the form for the actions that you can perform:
Close Event: Closes an event without any resolution.
Re-apply Matching Rules: Takes the processed data and reapplies all matching rules by deleting the results from previous applications of the rule. This action must be performed when the rule is modified.
Create User: Enables the creation of an OIM User based on the data provided.
Create Organization: Enables the creation of an OIM Organization based on the data provided.
In target resource reconciliation, if an event is linked to an existing instance of a provisioned resource, then the process form for that resource instance is updated.
Note:
In trusted source reconciliation, the user or organization record is updated instead.If the account did not exist in Oracle Identity Manager before the reconciliation run, then the default provisioning process is initiated, adapters are suppressed, and all nonconditional tasks are completed automatically.
In both cases, a marker task is added to the provisioning process for the provisioned resource (or user/organization). The marker task can be either Reconciliation Insert Received or Reconciliation Update Received. These tasks might have adapters attached to them to begin provisioning. If no adapters are attached to the task, then a response code of "Event Processed" is assigned to that task. Additional provisioning process tasks could be generated based on this response code to start a provisioning flow due to the reconciliation event. This mechanism can be leveraged to initiate multitarget synchronization processes.
Reconciliation events can be divided into two types depending on their expected behavior within Oracle Identity Manager. If the incoming data relates to an account that must be either created (because Oracle Identity Manager was not aware of it before) or updated (because Oracle Identity Manager has a record of it), then the reconciliation event is a regular reconciliation event. In a regular reconciliation event, Oracle Identity Manager need not know about the existence of this account. The appropriate provisioning processes are set up and completed.
If the input data relates to an account that must be marked as having been deleted (revoked), then the reconciliation event is a delete reconciliation event. There are two types of delete reconciliation events:
The data for deleting an account is provided and the Oracle Identity Manager locates the matching account based on existing rules.
The matching account record in Oracle Identity Manager is provided as the data for deleting an account.
The latter happens when the delete detection mechanism of reconciliation is employed. In both cases, if the accounts are matched, the provisioning process is canceled and the resource instance is marked as revoked.
Figure 5-5 illustrates the provisioning and reconciliation configuration in which you use Oracle Identity Manager to perform both provisioning and reconciliation tasks. In this configuration, it is assumed that you allow accounts on target systems to be created and maintained by both local administrators and Oracle Identity Manager.
Figure 5-5 Provisioning and Reconciliation Configuration
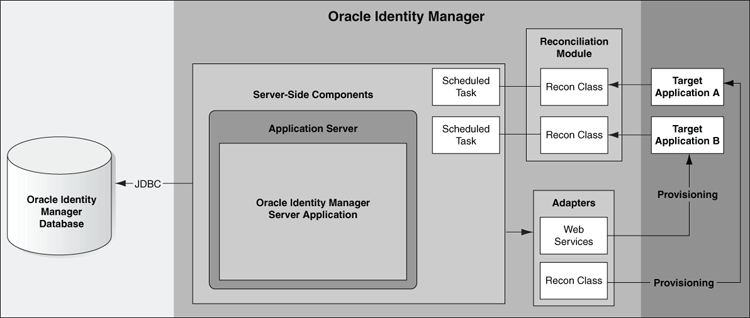
To achieve this configuration, you must perform all the steps associated with setting up both provisioning and reconciliation.