4 Oracle Audit Vault Data Warehouse Schema
This chapter contains:
4.1 About the Oracle Audit Vault Data Warehouse Schema
The Oracle Audit Vault repository has an internal data warehouse schema that manages the audit data collected from the source databases. The data warehouse collects the data from the Oracle Audit Vault collection agents, organizes it, and then provides it in report format for the reports described in Chapter 3, "Using Oracle Audit Vault Reports."
If you plan to design custom reports using tools such as Oracle Business Intelligence Publisher and the Oracle Business Intelligence Suite, you must understand the structure of the Oracle Audit Vault data warehouse schema. This appendix describes the schema in detail. You must also understand the structure of the audit events provided by the source database products; Oracle Database, Microsoft SQL Server, Sybase Adaptive Server Enterprise, and IBM DB2. Appendix A through Appendix D describe the structure of these audit events.
4.2 Oracle Audit Vault Audit Data Warehouse Architecture
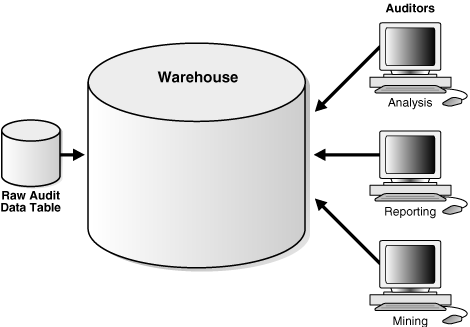
Figure 4-1 illustrates the Oracle Audit Vault audit data warehouse architecture. Audit Vault stores the audit records in the raw audit data table, which is typical of a traditional online transaction processing (OLTP) system that is optimized for insert performance for the records arriving from their audit sources.
Figure 4-1 Architecture of the Oracle Audit Vault Audit Data Warehouse
Description of "Figure 4-1 Architecture of the Oracle Audit Vault Audit Data Warehouse"
Audit records, stored in the raw audit data table go through an extraction and transformation process before the data loading process (ETL). The ETL operation takes place in the staging area. Oracle Audit Vault optimizes data in the data warehouse for data analysis, and includes the metadata and summaries that aid in these data analysis.
If you have been granted the AV_AUDITOR role, then you can directly access audit data in the audit data warehouse to analyze data, generate reports, and perform data mining. See Oracle Database Data Warehousing Guide for more information about Oracle data warehouses.
4.3 Design of the Audit Data Warehouse Schema
The audit data warehouse uses a logical design to model the logical relationships among the entities (tables) and their attributes (columns) as entity-relationship modeling. The audit record is the most important information, and it contains attributes or columns that describe it. Other information about the audit record is linked by foreign key to other tables that store this related information. This related information includes items such as its source information, its event information, its description of the objects in the source on which users performed actions, the client computer information from which these events originated, and the time when these events occurred. In data warehouse terminology, the audit record forms the fact table and its most important attributes form the dimension tables.
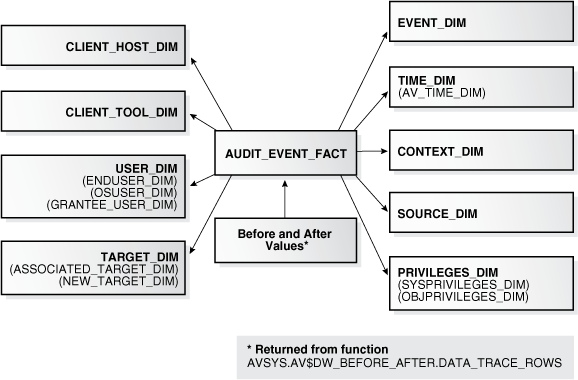
Figure 4-2 shows how Oracle Audit Vault uses a star schema to model the audit data warehouse. A star schema optimizes performance by keeping queries simple and providing fast response time. All the information about each level is stored in one row. For this star schema, the audit record is an entity (the fact table, AUDIT_EVENT_FACT) in the center of the star. The surrounding dimension tables describe the attributes of the AUDIT_EVENT_FACT fact table. If the audit records in the AUDIT_EVENT_FACT table have before and after values, then they can be accessed using the procedure described in "Accessing Data Trace Values".
Figure 4-2 Structure of the Oracle Audit Data Warehouse
Description of "Figure 4-2 Structure of the Oracle Audit Data Warehouse"
The audit data warehouse involves a fact (the entity), which is an action, and dimensions (the attributes), which are details about the action. For example, a login attempt is a fact (an audit record). Who logged on, onto what system, at what time, using what authentication system, using what user name and password, and from what system are all dimensions (the attributes) about this fact. In the audit data warehouse, each fact represents an audit record and each dimension represents unique information about that audit record that further describes the audit record.
4.4 How the Fact Table and Dimension Tables Work
The fact table, AUDIT_EVENT_FACT, is linked to each dimension table by its foreign key. The fact table in the audit data warehouse contains the audit record ID, some attributes of the audit record for report generation, and the foreign keys to these dimensions. The main measure of the fact table is the result, whether a particular event was a success or failure.
A dimension is a structure, often composed of one or more hierarchies, that categorizes data to enable proper analysis of the data. Dimensions represent natural 1:n relationships between columns or column groups (the levels of a hierarchy) that cannot be represented with constraint conditions. Going up a level in the hierarchy is called rolling up the data, and going down a level in the hierarchy is called drilling down the data.
Level relationships specify top-to-bottom ordering of levels from most general (the root) to most specific information. They define the parent-child relationship between the levels in a hierarchy. A dimension hierarchy shows these level relationships. For example, the source dimension consists of two levels, source type and source, with the source being the child of its parent source type, as shown in Figure 4-3.
The primary key in the dimension tables is a unique identifier. Primary keys are represented with the characters PK. Foreign keys are represented by the characters FK.
The audit data warehouse includes the following dimensions:
-
Client Host. This dimension consists of various systems that are used by clients to perform the operation. The basic hierarchy is IP address, subnet, and domain. The
CLIENT_HOST_DIMdimension table, described in Section 4.6.2, stores this information. Oracle Audit Vault populates this table dynamically, as the audit records are entered into the raw audit data table. -
Client Tools. This dimension represents the information about the tools used to connect to the audit source database. The
CLIENT_TOOL_DIMdimension table, described in Section 4.6.3, stores this information. -
User. This dimension tracks the user information that is associated with the events occurring at the source database. There is no hierarchy associated with the user information. The
USER_DIMdimension table, described in Section 4.6.10, stores this information. -
Target. This dimension contains the information about the object on which the event is performed. The target is the object of the event. For example, if a user is granted a privilege, then the user becomes the target. If there is a query on the table, then the table is a target. The hierarchy is based on ownership of the target objects.
The
TARGET_DIMdimension table, described in Section 4.6.8, stores this information. Oracle Audit Vault updates theTARGET_DIMtable dynamically as audit records are entered into the raw audit data table. The target name is stored with the owner name appended to the target name (for example,SCOTT.EMPto represent theEMPtable in theSCOTTschema). -
Event. This dimension is built on the various events that can be performed in any of the source databases. Oracle Audit Vault uses a category of events to group events, and this forms the hierarchy used by this dimension. The
EVENT_DIMdimension table, described in Section 4.6.5, stores this information. -
Time. This dimension tracks actions over time. It is the most common use of the Oracle Audit Vault data warehouse. The hierarchy for time is based on calendar year.
The
TIME_DIMdimension table, described in Section 4.6.9, stores this information. The time dimension tracks event time as well as for the time when the record was received into the raw audit data table. The granularity of the time dimension is one day, and the actual time of the event and recording of the event are stored as measures in the fact table. Oracle Audit Vault uses this time measurement to filter events to granularity smaller than a day. -
Context. This dimension is used to represent the context information related to the audit event. This dimension has three levels:
sub_context,context, andparent_context. You can use these levels to group events based on the context during analysis. TheCONTEXT_DIMdimension table, described in Section 4.6.4, stores this information. -
Source. This dimension consists of the list of source databases that send audit data to the data warehouse. The
SOURCE_DIMdimension table, described in Section 4.6.7, stores this information. -
Privileges. This dimension represents the information about the privileges used during the event. There is no hierarchy for this dimension. The
PRIVILEGES_DIMdimension table, described in Section 4.6.6, stores this information.
4.5 Fact Table Constraints and Indexes
Table 4-1 lists the constraints in the AUDIT_EVENT_FACT table. Each constraint references the primary key of a dimension. All constraints are in RELY DISABLE NOVALIDATE mode. The constraints are guaranteed to be validated by the extract, transform, load (ETL) process. RELY is specified to take advantage of query rewrites based on the constraint even though they are disabled.
Table 4-1 Fact Table Constraints and Indexes
| Constraint Name | Column Name | Reference Table |
|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Table 4-2 lists the local bitmap indexes in the AUDIT_EVENT_FACT table.
4.6 Relationships Between the Fact and Dimension Tables
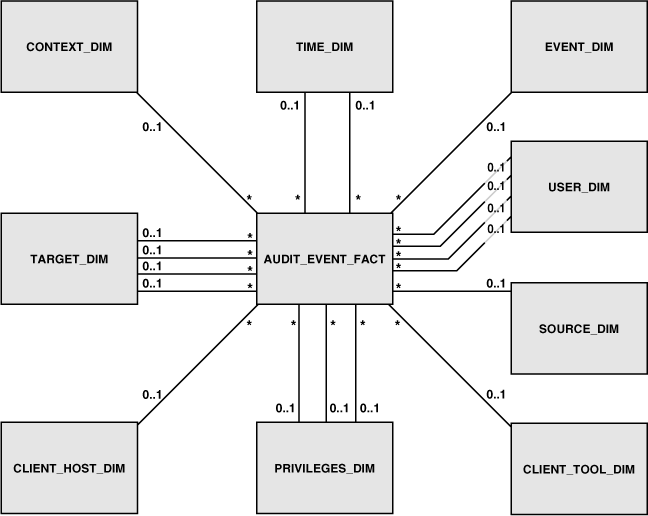
Figure 4-4 shows the relationships between the tables of the Oracle Audit Vault data warehouse.
Figure 4-4 Tables in the Oracle Audit Vault Data Warehouse
Description of "Figure 4-4 Tables in the Oracle Audit Vault Data Warehouse"
Table 4-3 through Table 4-12 contain information about the individual tables, including their columns, the data types for those columns, and whether the columns are allowed to be null. When the column is actually a reference to a dimension table, the referenced table is also listed. The asterisk and 0...1 show a one-to-many relationship that exists between the fact table and the dimension table.
4.6.1 AUDIT_EVENT_FACT Fact Table
Table 4-3 lists the contents of the AUDIT_EVENT_FACT table. This table stores audit data that the collectors have retrieved from the raw audit data store of the source databases.
Table 4-3 AUDIT_EVENT_FACT Fact Table
| Column | Data Type | References | Description |
|---|---|---|---|
|
|
|
None |
The SQL text of the command procedure that was executed that resulted in the audit event being triggered |
|
|
|
None |
The name of audit event |
|
|
|
None |
Object identifier affected by the triggered audit action |
|
|
|
None |
Name of the object affected by the action; also the object name corresponding to the |
|
|
|
None |
When an event includes grants, this field shows if the admin option was included |
|
|
|
|
Dimension key value to the |
|
|
|
None |
ID links to the |
|
|
|
None |
ID links to the |
|
|
|
None |
The time in which Oracle Audit Vault receives the audit trail record into the repository |
|
|
|
|
Dimension key value to the |
|
|
|
None |
Deprecated; will be removed in a future release |
|
|
|
|
Dimension key value to the |
|
|
|
None |
ID links to the |
|
|
|
|
Dimension key value to the |
|
|
|
None |
ID that links to the |
|
|
|
|
Dimension key to the |
|
|
|
None |
Date the audit trail record was created in the Oracle Database Vault audit trail |
|
|
|
None |
Database login user name of the user who created the Oracle Database Vault rule |
|
|
|
None |
If the event resulted in the update of a value, this item contains the value after the update. This may include changes in a target name or audit option. |
|
|
|
None |
Number of columns that have changed due to an insert or update |
|
|
|
None |
ID of the database specified by the |
|
|
|
None |
Name of the database specified in the |
|
|
|
None |
Domain name of the host system |
|
|
|
None |
Amount of elapsed time (in milliseconds) taken by the event |
|
|
|
|
Dimension key to the |
|
|
|
None |
Time at which the event ended. This column is not populated for starting event classes, such as |
|
|
|
None |
Error message number |
|
|
|
None |
Error message text |
|
|
|
|
Dimension key to the |
|
|
|
None |
ID of the If the action was successful, it shows a status of |
|
|
|
None |
Type of event subclass. This data column is not populated for all event classes. |
|
|
|
None |
Date and time of the creation of the audit trail entry (date and time of the user login for entries created by |
|
|
|
None |
The Oracle Database Vault factor identifiers for the current session at the point when the audit event was triggered |
|
|
|
None |
Fine-grained audit policy name; only applies to Oracle Database |
|
|
|
|
Dimension key to the |
|
|
|
None |
Global user identifier value, which is dependent on the event class captured in the trace |
|
|
|
None |
Index ID associated with an audit event |
|
|
|
None |
The database instance number in an Oracle Real Applications Cluster |
|
|
|
None |
Indicates whether the event occurred on a system process or a user process:
|
|
|
|
None |
Deadlocks detected during the session |
|
|
|
None |
Logical reads for the session |
|
|
|
None |
Logical writes for the session |
|
|
|
None |
Logical reads for the session |
|
|
|
None |
Program that generated the audit trail record |
|
|
|
|
Dimension key to the |
|
|
|
None |
Object identifier affected by the triggered audit action |
|
|
|
|
Dimension key to the |
|
|
|
None |
Original content of an invalid record |
|
|
|
None |
Original content of an invalid record |
|
|
|
None |
Original content of an invalid record |
|
|
|
|
Dimension key to the |
|
|
|
None |
Type of the object that owns the lock; for lock events only |
|
|
|
None |
If the event resulted in the update of a value, this column contains the value prior to the update. This value can include changes in a target name or audit option. (Non-Oracle databases only) |
|
|
|
|
Dimension key to the |
|
|
|
None |
ID of the privilege used to execute a transaction |
|
|
|
None |
Unique process identifier that generated the audit action |
|
|
|
None |
The original login name if the event occurred while a set proxy was in effect |
|
|
|
None |
Session ID of the proxy user |
|
|
|
None |
Unique identifier of the audit record created when the audit trail is inserted into the Oracle Audit Vault repository |
|
|
|
None |
Row identifier; for example, for the Oracle Database table row that was accessed or modified |
|
|
|
None |
The unique identifier of the rule that was executing and caused the audit event to trigger in Oracle Database Vault |
|
|
|
None |
The unique name of the rule that was executing and triggered the audit event in Oracle Database Vault |
|
|
|
None |
The unique identifier of the rule set that was executing and triggered the audit event in Oracle Database Vault |
|
|
|
None |
The unique name of the rule set that was executing and triggered the audit event in Oracle Database Vault |
|
|
|
None |
Oracle system change number at the time of query submission when the audit action was recorded |
|
|
|
None |
Name of the instance of SQL Server, either server name or server name and instance name, being traced |
|
|
|
None |
ID to the |
|
|
|
None |
Amount of CPU time used by each session |
|
|
|
None |
The login name of the user who originated the session |
|
|
|
None |
Error severity |
|
|
|
None |
ID of the database in which the source of the object exists |
|
|
|
|
Dimension key to the |
|
|
|
None |
Audit event identifier from the source database |
|
|
|
None |
Bind variable data used by the SQL query statement, if any |
|
|
|
None |
SQL statement issued by the user that triggered the audit action |
|
|
|
None |
Numeric identifier for each SQL statement executed |
|
|
|
|
Dimension key to the |
|
|
|
|
Dimension key to the |
|
|
|
None |
SID of the login that is the target of some action |
|
|
|
None |
Type of object, such as table, function, or stored procedure |
|
|
|
None |
Unique thread identifier that generated the audit action |
|
|
|
|
Dimension key to the |
|
|
|
None |
ID to the |
|
|
|
None |
Not used |
|
|
|
None |
For Oracle Database Vault, the date on which the command rule or realm information was updated |
|
|
|
None |
For Oracle Database Vault, the user who updated the command rule or realm |
|
|
|
|
Dimension key to the |
|
|
|
None |
Global user identifier for the user, if the user has logged in as an enterprise user; also the global user identifier of Oracle Internet Directory user |
4.6.2 CLIENT_HOST_DIM Dimension Table
The CLIENT_HOST_DIM table contains information about various systems that are used by clients to perform an operation.
Table 4-4 lists the contents of the CLIENT_HOST_DIM table.
Table 4-4 CLIENT_HOST_DIM Dimension Table
| Column | Data Type | Description |
|---|---|---|
|
|
|
Dimension key to the |
|
|
|
ID of the domain |
|
|
|
Domain name of the host system |
|
|
|
ID of the host computer |
|
|
|
Host IP address |
|
|
|
Name of the host |
|
|
|
Identifier for the user's terminal |
|
|
|
Name of the user's terminal |
4.6.3 CLIENT_TOOL_DIM Dimension Table
The CLIENT_TOOL_DIM table contains information about the tools used to connect to an audit source database.
Table 4-5 lists the contents of the CLIENT_TOOL_DIM table.
Table 4-5 CLIENT_TOOL_DIM Dimension Table
| Column | Data Type | Description |
|---|---|---|
|
|
|
Dimension key to the |
|
|
|
ID of the tools and programs used to connect to an audit source database |
|
|
|
The tools and programs used to connect to an audit source database |
4.6.4 CONTEXT_DIM Dimension Table
The CONTEXT_DIM table contains context information related to an audit event.
Table 4-6 lists the contents of the CONTEXT_DIM table.
Table 4-6 CONTEXT_DIM Dimension Table
| Column | Data Type | Description |
|---|---|---|
|
|
|
Session ID of the audit event |
|
|
|
An internal cross-reference to the |
|
|
|
Dimension key to the |
|
|
|
Sequence number or identifier of a transaction |
|
|
|
Sequence number or identifier of a transaction |
|
|
|
Transaction ID |
|
|
|
An internal cross-reference to the |
4.6.5 EVENT_DIM Dimension Table
The EVENT_DIM table contains information about various events that can be performed in the source databases.
Table 4-7 lists the contents of the EVENT_DIM table.
Table 4-7 EVENT_DIM Dimension Table
| Column | Data Type | Description |
|---|---|---|
|
|
|
Oracle Audit Vault audit event identifier |
|
|
|
Oracle Audit Vault category identifier |
|
|
|
Oracle Audit Vault category name |
|
|
|
Dimension key to the |
|
|
|
Description of the event |
|
|
|
Source audit event ID |
|
|
|
Source audit event name |
4.6.6 PRIVILEGES_DIM Dimension Table
The PRIVILEGES_DIM table contains information about the privileges used during an audit event.
Table 4-8 lists the contents of the PRIVILEGES_DIM table.
4.6.7 SOURCE_DIM Dimension Table
The SOURCE_DIM table contains information about the source databases that send audit data to the data warehouse.
Table 4-9 lists the contents of the SOURCE_DIM table.
Table 4-9 SOURCE_DIM Dimension Table
| Column | Data Type | Description |
|---|---|---|
|
|
|
Dimension key to the |
|
|
|
Description of the source that is defined when the source is added to Oracle Audit Vault |
|
|
|
Name of the host computer on which the audit source database resides |
|
|
|
IP of the host computer on which the audit source database resides |
|
|
|
ID of the audit source database assigned to Oracle Audit Vault |
|
|
|
Name of the source database that is defined when the source is added to Oracle Audit Vault |
|
|
|
Deprecated; will be removed in a future release |
|
|
|
Indicates if the source database is currently active in Oracle Audit Vault |
|
|
|
Version number of the source database |
|
|
|
Description of the type of source database in which audit trail records are being extracted |
|
|
|
ID of the type of source database in which audit trail records are being extracted |
|
|
|
Name of the type of source database in which audit trail records are being extracted |
4.6.8 TARGET_DIM Dimension Table
The TARGET_DIM table contains information about the schema object on which an audit event is performed.
Table 4-10 lists the contents of the TARGET_DIM table.
Table 4-10 TARGET_DIM Dimension Table
| Column | Data Type | Description |
|---|---|---|
|
|
|
Dimension key to the |
|
|
|
ID of the owner of the target object |
|
|
|
Name of the owner of the target object |
|
|
|
ID of the target object that is being audited |
|
|
|
Name of the target object that is being audited |
4.6.9 TIME_DIM Dimension Table
The TIME_DIM table tracks actions over time. This table is the most commonly used by the data warehouse. It implements four levels in the dimension hierarchy (DAY, MONTH, QUARTER, YEAR). The CALENDAR prefix distinguishes between a fiscal quarter and a fiscal year.
Table 4-11 lists the contents of the TIME_DIM table.
Table 4-11 TIME_DIM Dimension Table
| Column | Data Type | Description |
|---|---|---|
|
|
|
Numeric representation for the |
|
|
|
Text description for level for the |
|
|
|
End date for the |
|
|
|
ID for the |
|
|
|
Same as |
|
|
|
Numeric representation for the month in this quarter (for example, |
|
|
|
Numeric representation for the month in the year (for example, 2 for February) |
|
|
|
Start date of the |
|
|
|
Duration of the |
|
|
|
Numeric representation for the |
|
|
|
Text description for the |
|
|
|
End date for the |
|
|
|
ID for the |
|
|
|
Same as |
|
|
|
Numeric representation of the calendar quarter (for example, 2 for the second quarter of the year) |
|
|
|
Start date of the |
|
|
|
Duration of the |
|
|
|
Numeric representation for the |
|
|
|
Text description for the |
|
|
|
End date for the |
|
|
|
ID of the |
|
|
|
Same as |
|
|
|
Start date of the |
|
|
|
Duration of the |
|
|
|
Numeric representation of the day (for example, |
|
|
|
Numeric representation for the |
|
|
|
Text description of for the |
|
|
|
End date for the |
|
|
|
ID for the |
|
|
|
Same as |
|
|
|
Numeric representation of the day of the calendar month (for example, |
|
|
|
Numeric representation of the day of the calendar quarter (for example, |
|
|
|
Numeric representation of the day of the calendar week (for example, |
|
|
|
Numeric representation of the day of the calendar year (for example, |
|
|
|
Start date of the |
|
|
|
Duration of the |
|
|
|
Unique key across all levels |
4.6.10 USER_DIM Dimension Table
The USER_DIM table tracks information about the user who is associated with the events that occur in the source database.
Table 4-12 lists the contents of the USER_DIM table.
4.7 Accessing Data Trace Values
You can include before and after values that have been collected from the Oracle redo logs in your data warehouse queries. To do so, use the AVSYS.AV$DW_BEFORE_AFTER PL/SQL package. Only users who have been granted the AV_AUDITOR role can invoke this package. This package contains one function, DATA_TRACE_ROWS, which is a pipelined table function that can create a virtual table listing before and after values from the redo log.
The syntax for the DATA_TRACE_ROWS function is as follows:
AV$DW_BEFORE_AFTER.DATA_TRACE_ROWS ( rec_id IN NUMBER, src_dim IN NUMBER, rec_time IN TIMESTAMP WITH LOCAL TIME ZONE) RETURN before_after_tab PIPELINED;
In this specification:
-
rec_idrefers to the record ID number from in theRECORD_IDcolumn in theAUDIT_EVENT_FACTtable. -
src_dimrefers to the source dimension table number from theSOURCE_DIMcolumn in theAUDIT_EVENT_FACTtable. -
rec_timerefers to the time that the record was created in the Audit Vault repository, based on the local time zone. It comes from theAV_TIMEcolumn in theAUDIT_EVENT_FACTtable.
Example 4-1 shows a query that uses the DATA_TRACE_ROWS function to include before and after values in a report similar to the Data Access Report you can access through the user interface."
Example 4-1 Using the DATA_TRACE_ROWS Function to Access Data Trace Values
select t.owner_name||'.'||t.target_name table_name, e.event_name, f.event_time, x.column_name, x.old_value, x.new_value from event_dim e, target_dim t, audit_event_fact f, table(av$dw_before_after.data_trace_rows(f.record_id, f.source_dim, f.av_time)) x where f.event_dim = e.dimension_key and f.target_dim = t.dimension_key and f.data_values_cnt > 0;
See Also:
Section 3.3.2.3 for information about the Data Access Report