9 Installing and Configuring Oracle Content Server
This chapter describes how to install and configure Oracle Content Server (OCS). It contains the following sections:
-
Section 9.4, "Configuring Oracle Content Server for Remote Oracle HTTP Server"
-
Section 9.7, "Configuring Oracle Content Server for WebCenter"
-
Section 9.8, "Adding Another Oracle HTTP Server and Configuring a Load Balancer"
-
Section 9.9, "Reconfiguring the Content Server to Support RAC"
9.1 Prerequisites
Ensure that you meet the following prerequisites:
9.2 Installing Oracle Content Server
Run the installer from WCHOST1, which is one of the two machines that will eventually form the OCS cluster. You will install OCS on the shared disk.
Run the OCS installer from the /install directory on the OCS media.
/install/UCM/ContentServer/linux/setup.sh
The installer is text-based. The following lines show an installer session. Your responses are in bold.
Please select your locale from the list. *4. English-US Select installation type from the list. *1. Install new server Please enter the full pathname to the installation directory. Content Server Core Folder [/oracle/ucm/server]: /shared/oracle/ucm/server // This is an example. Make sure that you specify an installation directory that is on a shared drive. Create Directory *1. Yes Java virtual machine *1. Sun Java 1.5.0_11 JDK Enter the location of the native file repository. This directory contains the native files checked in by contributors. Content Server Native Vault Folder [/shared/oracle/ucm/server/vault/]: < accept default > Create Directory *1. yes Enter the location of the web-viewable file repository. This directory contains files that can be accessed through the web server. Content Server Weblayout Folder [/shared/oracle/ucm/server/weblayout/]: < accept default > Create Directory *1. yes This server can be configured to manage its own authentication or to allow another master to act as an authentication proxy. Configure this server as a master or proxied server. *1. Configure as a master server. During installation, an admin server can be installed and configured to manage this server. If there is already an admin server on this system, you can have the installer configure it to administrate this server instead. Select admin server configuration. *1. Install an admin server to manage this server. Enter the location of an executable to start your web browser. This browser will be used to display the online help. Web Browser Path [/usr/local/bin/firefox]: < accept default > Content Server System locale *4. English-US Please select the region for your timezone from the list. *1. Use the timezone setting for your operating system Please enter the port number that will be used to connect to the Content Server. This port must be otherwise unused. Content Server Port [4444]: 9054 Please enter the port number that will be used to connect to the Admin Server. This port must be otherwise unused. Admin Server Port [4440]: 9050 // Do NOT take the default. Specify the list of all the IPs of WebCenter and // Oracle HTTP Server hosts in the cluster. For the EDG topology, this includes // WEBHOST1, WEBHOST2, WCHOST1, WCHOST2. // For example, 111.222.100.101|111.222.100.102|111.222.100.103|111.222.100.104 Enter a security filter for the server port. Hosts which are allowed to communicate directly with the server port may access any resources managed by the server. Insure that hosts which need access are included in the filter. See the installation guide for more details. Incoming connection address filter [127.0.0.1]: <list of IP addresses of all the Oracle HTTP Server and WebCenter servers in the cluster> // Either take the default or specify a new context root // Here we'll accept the default of 'idc'. Web Server Relative Root [/idc/]: /idc/ Enter the name of the local mail server. The server will contact this system to deliver email. Company Mail Server [mail]: < accept default or enter name of local mail server> Enter the e-mail address for the system administrator. Administrator E-Mail Address [sysadmin@mail]: < accept default or enter email of the system administrator > // Next question do NOT take the DEFAULT, specify host:port which your webserver is running Web Server HTTP Address [webhost1]: webhost1.us.oracle.com:7777 Enter the name for this instance. This name should be unique across your entire enterprise. It may not contain characters other than letters, numbers, and underscores. Server Instance Name [idc]: < accept default > Enter a short label for this instance. This label is used on web pages to identify this instance. It should be less than 12 characters long. Server Instance Label [idc]: < accept default > Enter a long description for this instance. Server Description [Content Server idc]: < accept default > // Choose Apache for Oracle HTTP Server Web Server *1. Apache Please select a database from the list below to use with the Content Server. Content Server Database *1. Oracle Manually configure JDBC settings for this database *2. no // Specify the hostname of one of the RAC DB machines. Oracle Server Hostname [localhost]: rachost1.us.oracle.com // Specify the database port Oracle Listener Port Number [1521]: 1521 // Specify the username (prefix_OCSERVER) of the schemas you installed using the RCU The user name is used to log into the database used by the content server. Oracle User [user]: WCEDG_OCSERVER // Specify the password (prefix_OCSERVER) of the schemas you installed using the RCU The password is used to log into the database used by the content server. Oracle Password []: < enter the schema password > //Specify the SID of one of the RAC instances. Oracle Instance Name [ORACLE]: orasid1 Configure the JVM to find the JDBC driver in a specific jar file *2. no // Accept the default. Do not choose to create database tables since they should // have been created with RCU already. The installer can attempt to create the database tables, or you can manually create them. If you choose to manually create the tables, you should create them now. Attempt to create database tables 2. No *1(Proceed) Select components to install. 1. ContentFolios: Collect related items in folios 2. LinkManager8: Hypertext link management support 3. OracleTextSearch: External Oracle 11g database as search indexer support 4. ThreadedDiscussions: Threaded discussion management Enter numbers separated by commas to toggle, 0 to unselect all, F to finish: F
The installer then installs Oracle Content Server. Ensure that Oracle Content Server starts up at the end of installation.
If Oracle Content Server does not start, check the logs for errors, and resolve them. The log files are located in the following places:
Table 9-1 Location of Log Files for Oracle Content Server
| Location | Description |
|---|---|
|
|
Basic installer log |
|
|
Output from starting Oracle Content Server |
|
|
HTML logs |
You can try to start the server manually by running:
<content_server_dir>/etc/idcserver_start <content_server_dir>/admin/etc/idcadmin_start
If you want to see some debug output, specify the -debug parameter:
<content_server_dir>/bin/IdcServer -debug
If you want to see more debug output, edit the <content_server_dir>/config/config.cfg file to include the following line:
TraceSectionsList=*
If you want to see even more debug output, add these lines to <content_server_dir>/config/config.cfg:
TraceSectionsList=* TraceIsVerbose=1
9.3 Running the WebCenter Configuration Script
Run the WebCenter configuration script, wc_contentserverconfig.sh, from the Oracle Content Server 10.1.3.4.1 media to prepare the server to work with Oracle WebCenter. This script installs the following:
-
Oracle Content Server 10.1.3.4.1 patch
-
Folders_g 10.1.3.4.1 component
-
WcConfigure component
The WcConfigure component performs the following tasks to configure Oracle Content Server for Oracle WebCenter:
-
Sets configuration values for UseAccounts and IsAutoNumber to true and AutoNumberPrefix to IDC_Name, if not set.
-
Updates, if necessary, the JDBC password and its encoding from ClearText to Intradoc.
-
Adds the document type DOCUMENT.
-
Configures folders so that dDocType and dSecurityGroup are inherited, and the system default information is set as follows: dDocType=DOCUMENT and dSecurityGroup=Public.
Perform these steps to run the wc_contentserverconfig WebCenter script:
-
Navigate to the
webcenter-confdirectory, which is in the root directory on the Oracle Content Server 10.1.3.4.1 media. -
Run the following command:
./wc_contentserverconfig.sh <content_server_dir> <path_to_source_directory>
Where
<content_server_dir>refers to the Oracle Content Server 10.1.3.3.3 installation directory and<path_to_source_directory>refers to thewebcenter-confdirectory on the Oracle Content Server 10.1.3.4.1 media. For example:wc_contentserverconfig.sh /shared/oracle/ucm/server /myproducts/ucmmedia/webcenter-conf
-
Restart Oracle Content Server Administration Server and Oracle Content Server.
To restart Administration Server, run
<content_server_dir>/admin/etc/idcadmin_restart.To restart Oracle Content Server, run
<content_server_dir>/etc/idcserver_restart.Where
<content_server_dir>refers to the Oracle Content Server installation directory.
Note:
For more information about how to start, stop, or restart Oracle Content Server, see the Content Server Installation Guide for UNIX athttp://download.oracle.com/docs/cd/E10316_01/owc.htm.9.4 Configuring Oracle Content Server for Remote Oracle HTTP Server
Perform these steps to configure Oracle Content Server for remote Oracle HTTP Server (that is, Content Server and Oracle HTTP Server run on different hosts). You must perform steps on the Content Server machine and on the Oracle HTTP Server machine:
-
Section 9.4.1, "Steps to Perform on the Content Server Machine"
-
Section 9.4.2, "Steps to Perform on the Oracle HTTP Server Machine"
9.4.1 Steps to Perform on the Content Server Machine
Perform these steps on the Content Server machine (WCHOST1):
-
Shut down Oracle Content Server and the Content Server Administration Server:
To stop Oracle Content Server, run this command:
WCHOST1> <content_server_dir>/etc/idcserver_stopTo stop the Content Server Administration Server, run this command:
WCHOST1> <content_server_dir>/admin/etc/idcadmin_stop -
Edit the
<content_server_dir>/config/config.cfgfile to include the following lines:IntradocServerHostName=<Content_Server_HostName> IdcAdminServerHostName=<Content_Server_HostName> HttpServerAddress=<Web_Server_URL>
Also, add
SocketHostAddressSecurityFilterif it is not already there. This should be set to a pipe-delimited list of hosts allowed to access Oracle Content Server.Example:
IntradocServerHostName=wchost1.us.oracle.com IdcAdminServerHostName=wchost1.us.oracle.com HttpServerAddress=WEBHOST1.us.oracle.com:7777 SocketHostAddressSecurityFilter=127.0.0.1 | IP_of_WEBHOST1 | IP_of_WEBHOST2 | IP_of_WCHOST1 | IP_of_WCHOST2
-
Edit the
<content_server_dir>/admin/bin/intradoc.cfgfile to include theSocketHostAddressSecurityFilterentry if it is not already there. See the previous step for the values for this parameter. -
Restart the content server.
If you do not restart the content server, the
SecurityInfo.hdafile under<content_server_dir>/data/usersis not updated.
9.4.2 Steps to Perform on the Oracle HTTP Server Machine
Perform these steps on the Oracle HTTP Server machine (WEBHOST1):
-
Create a local directory on WEBHOST1 with the same path name as the shared directory on WCHOST1:
WEBHOST1> mkdir -p /shared/oracle/ucm/serverThe remaining steps will refer to this directory as
<cs_on_webhost_dir>.This is a local directory: the WEBHOST machine does not have access to the shared drive.
-
Copy the following directories (the content server stub) from the Oracle Content Server machine to the directory on WEBHOST1 created in the previous step:
-
<content_server_dir>/data -
<content_server_dir>/idcplg(if it exists) -
<content_server_dir>/weblayout(without thegroupssubdirectory)
-
-
On WEBHOST1, create the
<cs_on_webhost_dir>/shared/os/<OS_Name>/libdirectory.For example:
WEBHOST1> mkdir /shared/oracle/ucm/server/shared/os/linux/lib -
Copy the
IdcApache22Auth.soandRedirectUrls.sofiles on the Content Server machine (these files are located in the<content_server_dir>/shared/os/<OS_Name>/libdirectory) to the directory created in the previous step, on the WEBHOST1 machine. -
On WEBHOST1, create the
<cs_on_webhost_dir>/data/users/SystemFilters.hdafile, and add the following lines:@Properties LocalData EnableRedirectUrls=1 @end @ResultSet IdcAuthPlugins 2 iapExportedSymbolName iapFileNameRoot RedirectUrls RedirectUrls @end
-
Create virtual directories for Oracle HTTP Server.
Add the following lines to Oracle HTTP Server's
httpd.conffile:Note:
The lines below useidcbecause it was the context root specified during the installation. If you specified a different context root, then enter your context root instead ofidc.LoadModule IdcApacheAuth <cs_on_webhost_dir>/shared/os/linux/lib/IdcApache22Auth.so IdcUserDB idc "<cs_on_webhost_dir>/data/users/userdb.txt" Alias /idc "<cs_on_webhost_dir>/weblayout" <Location /idc> Order allow,deny Allow from all DirectoryIndex portal.htm IdcSecurity idc </Location> UseCanonicalName Off
-
Restart Oracle Content Server.
-
Restart Oracle HTTP Server.
9.5 Validating the Installation
Verify that you can access the Admin interface at http://webhost1:7777/idc. The login is sysadmin/idc.
If the Admin interface does not come up, diagnose and resolve any problems before proceeding.
9.6 Backing Up the Installation
Back up all the installation files on both the Web machine and the Content Server machine.
For the HTTP Server machine, back up the configuration directory:
WEBHOST1> tar -cvpf ucmWHconfigback.tar /shared/oracle/ucm/server
For the Content Server machine, back up all install files and configuration:
WCHOST1> tar -cvpf ucmCSback.tar /shared/oracle/ucm/server
9.7 Configuring Oracle Content Server for WebCenter
To configure Oracle Content Server to work with WebCenter, perform the steps described in these sections:
9.7.1 Configuring Oracle Content Server
After installing Oracle Content Server, you must configure the server to use the same LDAP-based identity store that Oracle WebCenter has been configured to use. You can optionally configure Oracle Content Server for using WS-Security and enabling full-text search and index. Table 9-1 lists the various tasks and whether these tasks are mandatory or optional.
Table 9-2 Oracle WebCenter-Specific Post-Installation Configuration Tasks for Oracle Content Server
| Task | Mandatory/Optional |
|---|---|
|
Mandatory |
|
|
Optional |
|
|
Configuring Secure Socket Layer (SSL) in Oracle Content Server |
Optional |
9.7.1.1 Configuring the Identity Store
Both Oracle Content Server and Oracle WebCenter must be configured to use the same LDAP-based identity store. By default, Oracle Content Server is not set up with an LDAP-based identity store.
To configure Oracle Content Server to use the LDAP-based identity store:
-
Start the Oracle Content Server console and log on to the server with administrative permission.
-
From the Administration menu, select Providers.
-
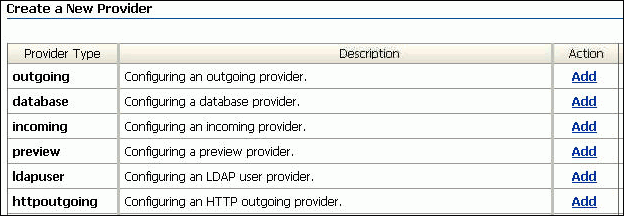
In the Create a New Provider section, click Add for the ldapuser provider type (Figure 9-1)
-
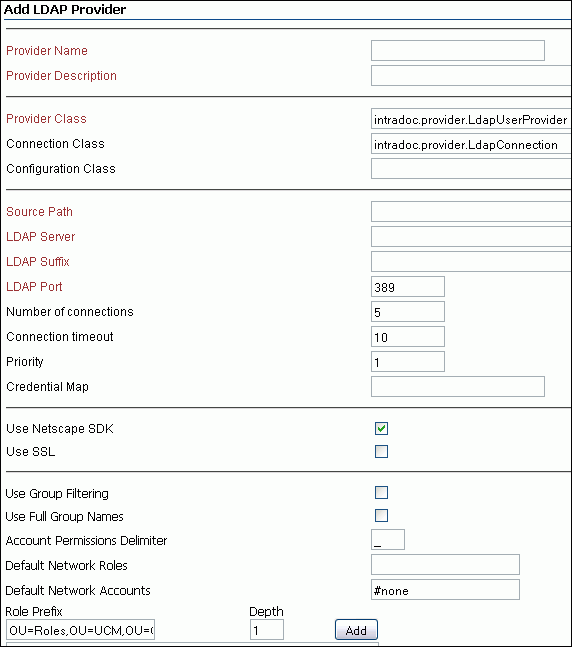
Specify details for the LDAP provider. You must specify the following information: provider name, provider description, provider class, source path, LDAP server, LDAP suffix, and LDAP port (Figure 9-2). The LDAP server details must be of the server that Oracle WebCenter is configured to use.
-
Provider Name field: The name of the provider, which becomes a subdirectory in the <install_dir>/data/providers/ directory.
Example: OIDProvider
-
Provider Description field: User-friendly description of the provider.
Example: MyOracleOIDProvider
-
Provider Class field: The Java class that implements the provider.
The default is intradoc.provider.LdapUserProvider.
-
Connection Class field: The Java class that implements the connection to the LDAP server.
The default is intradoc.provider.LdapConnection.
-
Configuration Class field: The name of a Java class that performs some extra configuration. This class is useful for database providers, where the connection classes are already providers. Optional.
-
Source Path field: A unique string that identifies the LDAP provider. The first time a user requests credentials through the provider, this string is stored with the user information so it can be used to match the user with the provider next time the user asks for credentials. We suggest using the name of the provider as the Source Path.
Example: OIDUCMAccounts
-
LDAP Server field: The host name of the LDAP server.
Example: idm.mycompany.com
-
LDAP Suffix field: The root suffix (naming context) to use for all LDAP operations (such as dc=webcenter, dc=au, dc=oracle,dc=com). All mapping of LDAP groups to content server roles and accounts begin at this root.
Example: dc=oracle,dc=com
Note:
Do not include spaces before or after commas. -
LDAP Port field: The port the LDAP server listens on.
The default is 389.
You may also specify the LDAP admin user and password.
Note:
Set the Default Network Account field to#none. Do not set any default role because all user security information is stored using the extended user attribute component of Oracle Content Server. You can set the Role Prefix and Account Prefix fields to any path that does not exist in the LDAP server. -
-
Click the Add button to add the LDAP provider.
-
Click the Test link on the main providers page to verify that the new LDAP connection works fine.
9.7.1.2 Enabling Full-Text Searching and Indexing
By default, the database used with Oracle Content Server is set up to provide metadata-only searching and indexing capabilities. You can additionally configure SQLServer, Oracle, and DB2 to support full-text searching and indexing. Configuring full-text search is optional, but advisable.
For information about enabling full-text searching and indexing, see the "Setting Up Database Search and Indexing" appendix in the Oracle Universal Content Management Content Server Installation Guide for Windows or UNIX available here:
9.7.1.3 Configuring Secure Socket Layer (SSL) in Oracle Content Server
If Oracle Content Server and the WebCenter application in which you have created a repository connection are not on the same machine or same trusted private network, then identity propagation is not secure. To ensure its security, you must configure SSL on Oracle Content Server.
To configure SSL on Oracle Content Server, you must perform the following tasks:
You can also see the "Secure Socket Layer (SSL) Communication" in Content Integration Suite (CIS) Installation Guide available at http://download.oracle.com/docs/cd/E10316_01/owc.htm. Perform these procedures, if you use self-signed certificates.
In a production environment, it is recommended that you use real certificates. For information on how to configure keystores when using real certificates, see "Using Service Providers" in Security Providers Component Administration Guide available at http://download.oracle.com/docs/cd/E10316_01/cs/cs_doc_10/documentation/extras/security_providers_guide.pdf.
Configuring a Keystore and Key on the Client Side
To configure a keystore on the WebCenter application (client) side:
-
In your development environment, go to
JDEV_HOME/jdk/binand open the command prompt. -
Generate the client keystore by running the following keytool command:
keytool -genkey -keyalg RSA -validity 5000 -alias Client private key alias -keystore client-keystore.jks -dname "cn=client" -keypass Private key password -storepass KeyStore password
-
To verify that the keys have been correctly created, run the following keytool command. This is an optional step:
keytool -list -keystore client-keystore.jks -storepass KeyStore password -
To use the key, sign it by running the following keytool command:
keytool -selfcert -validity 5000 -alias Client private key alias -keystore client-keystore.jks -keypass Private key password -storepass KeyStore password
-
Export the client public key by running the following keytool command:
keytool -export -alias Client private key alias -keystore client-keystore.jks -file client.pubkey -keypass Private key password -storepass KeyStore password
Configuring a Keystore and Key on the Server Side
To configure a keystore on the Oracle Content Server side:
-
In the same development environment, go to
JDEV_HOME/jdk/binand open the command prompt. -
Generate the server keystore by running the following keytool command:
keytool -genkey -keyalg RSA -validity 5000 -alias Server public key alias -keystore server-keystore.jks -dname "cn=server" -keypass Private server key password -storepass KeyStore password
-
To verify that the key has been correctly created, run the following keytool command:
keytool -list -keystore server-keystore.jks -keypass Server private key password -storepass KeyStore password
-
To use the key, sign it by running the following keytool command:
keytool -selfcert -validity 5000 -alias Server public key alias -keystore server-keystore.jks -keypass Private server key password -storepass KeyStore password
-
Export the server public key to the server keystore by running the following keytool command:
keytool -export -alias Server public key alias -keystore server-keystore.jks -file server.pubkey -keypass Server private key password -storepass KeyStore password
Verifying Signatures of Trusted Clients
To verify signatures of trusted clients, import the client public key into the server keystore:
-
In your development environment, go to
JDEV_HOME/jdk/binand open the command prompt. -
To verify the signature of trusted clients, import the client's public key in to the server keystore by running the following keytool command:
keytool -import -alias Client public key alias -file client.pubkey -keystore server-keystore.jks -keypass Private server key password -storepass KeyStore password
-
Import the server public key into the client keystore by running the following keytool command:
keytool -import -alias Server public key alias -file server.pubkey -keystore client-keystore.jks -keypass Private key password -storepass KeyStore password
When the tool prompts you if the key is self certified, you must enter Yes. Example 9-1 shows a sample output that is generated after this procedure is completed successfully.
Example 9-1 Sample Output Generated by the Keytool
[user@server]$ keytool -import -alias client -file client.pubkey -keystore server-keystore.jks -keypass Server private key password -storepass Keystore password Owner: CN=client Issuer: CN=client Serial number: serial number, for example, 123a19cb Valid from: Date, Year, and Time until: Date, Year, and Time Certificate fingerprints: ... Trust this certificate? [no]: yes Certificate was added to keystore.
To secure identity propagation, you must configure SSL on Oracle Content Server.
-
Log into Oracle Content Server as an administrator.
-
From Administration, choose Providers. The Create a New Provider page displays.
-
Click Add for sslincoming. The Add Incoming Provider page displays.
-
In Provider Name, enter a name for the provider, for example,
sslincomingprovider.When the new provider is set up, a directory with the provider name is created as a subdirectory of the
CONTENT_SERVER_HOME/data/providersdirectory. -
In Provider Description, briefly describe the provider, for example,
SSL Incoming Provider for securing the Content Server. -
In Provider Class, enter the class of the sslincoming provider, for example,
idc.provider.ssl.SSLSocketIncomingProvider.Note:
You can add a new SSL keepalive incoming socket provider or a new SSL incoming socket provider. Using a keepalive socket improves the performance of a session and is recommended for most implementations. -
In Connection Class, enter the class of the connection, for example,
idc.provider.KeepaliveSocketIncomingConnection. -
In Server Thread Class, enter the class of the server thread, for example,
idc.server.KeepaliveIdcServerThread. -
In Server Port, specify an open server port, for example,
5555. -
Select the Require Client Authentication checkbox.
-
In Keystore password, enter the password to access the keystore.
-
In Alias, enter the alias of the keystore.
-
In Alias password, enter the password of the alias.
-
In Truststore password, enter the password of the trust store.
-
Click Add. The new incoming provider is now set up.
-
Go to the new provider directory that was created in step 4.
-
To specify truststore and keystore, create a file named
sslconfig.hda. -
Copy the server keystore to the server.
-
Configure the
sslconfig.hdafile. Example 9-2 shows how the.hdafile should look after you include the truststore and keystore information.
9.7.2 Configuring the Load Balancer
You must configure the load balancer to act as a socket load balancer. This will be used to make socket connections from the Oracle HTTP Server as well as WebCenter.
-
Configure load balancer addresses.
A virtual address should be configured on the load balancer. This address will only be used internally to access Oracle Content Server (OCS). This address should be configured to route to the OCS cluster.
Example:
Virtual host on load balancer: wcinternal.mycompany.com:9054
Maps to: WCHOST1:9054, WCHOST2:9054
Load-balancing method: round-robin
-
Reconfigure Oracle HTTP Server and Content Server.
Oracle HTTP Server and Content Server both must be reconfigured to support the new virtual address.
-
On the Content Server machine (WCHOST1), in the file
<content_server_dir>/config/config.cfg, replace the two occurrences of WCHOST1 (under@Properties LocalData and @ResultSet ProxiedServers) with the virtual host namewcinternal.mycompany.com.Ensure that the LBR IP address is added to "SocketHostAddressSecurityFilter".
-
Restart the Content Server server.
-
Copy the
SecurityInfo.hdafile to the same directory on the Oracle HTTP Server host. This should overwrite the copy of the file already there.
-
-
Restart Oracle HTTP Server. Verify that the address and login work as before.
9.7.3 Installing Content Server Cluster
Each Content Server node is installed using the cluster installer which can be found in <content_server_dir>/bin.
Before proceeding, shut down the Content Server and Administration Server from the previous installation. The installation process consists of the following steps:
9.7.3.1 Installing the First Content Server Node
From the first node (WCHOST1), run the following command (all on one line):
Installer -set-ClusterNodeIntradocDir=<ocs-stub> -set-ClusterNodeName=<node_name> -set-ClusterNodeAddress=<ip_of_node> -set-ClusterBinDirRule=<local|shared> ConfigureClusterNode ConfigureAdminClusterNode
For <node_name>, specify WCHOST1.
For <ocs-stub>, use a local directory, for example, /u01/app/oracle/product/ucm.
For Set-ClusterBinDirRule, specify local.
9.7.3.2 Installing the Second Content Server Node
From the second node (WCHOST2), run the command (all on one line):
Installer -set-ClusterNodeIntradocDir=<ocs-stub> -set-ClusterNodeName=<node_name> -set-ClusterNodeAddress=<ip_of_node> -set-ClusterBinDirRule=<local|shared> ConfigureClusterNode ConfigureAdminClusterNode
For <node_name>, specify WCHOST2.
For <ocs-stub>, use a local directory, for example, /u01/app/oracle/product/ucm.
For Set-ClusterBinDirRule, specify local.
9.7.3.3 Post-Installation Steps
After setting up the nodes, add the following lines to the <ocs-stub>/bin/intradoc.cfg and the <ocs-stub>/admin/bin/intradoc.cfg files on each of the nodes WCHOST1 and WCHOST2:
DisableSharedCacheChecking=true ClusterNodeName=<node_name> ClusterGroup=<cluster_name> SocketServerAddress=<server_IP_address> UserPublishCacheDir=<ocs-stub>/data/users SharedDir=<ocs-stub>/shared ArchiverDoLocks=true
<node_name> is the identifier for the node.
<cluster_name> is the identifier for the cluster.
All nodes should have a different node name, but should have the same cluster group name. For example, WCHOST1 would be configured as follows:
DisableSharedCacheChecking=true ClusterNodeName=WCHOST1 ClusterGroup=ucmcluster SocketServerAddress=<IP_of_WCHOST1> UserPublishCacheDir=<Stub_Location_on_WCHOST1>/data/users SharedDir=<Stub_Location_on_WCHOST1>/shared ArchiverDoLocks=true
And WCHOST2 would be configured as follows:
DisableSharedCacheChecking=true ClusterNodeName=WCHOST2 ClusterGroup=ucmcluster SocketServerAddress=<IP_of_WCHOST2> UserPublishCacheDir=<Stub_Location_on_WCHOST2>/data/users SharedDir=<Stub_Location_on_WCHOST2>/shared ArchiverDoLocks=true
9.7.3.4 Starting the Servers
Start Oracle Content Server and Administration Server on each node using the binaries in <ocs-stub>/bin.
Verify that the log and PID files are created in the <ocs-stub>/admin/etc and <ocs-stub>/etc directories.
Start Oracle HTTP Server on WEBHOST1.
9.8 Adding Another Oracle HTTP Server and Configuring a Load Balancer
This section contains the following sections:
9.8.1 Configuring the Second Oracle HTTP Server
To configure the second Oracle HTTP Server (that is, the Oracle HTTP Server on WEBHOST2), perform the steps in Section 9.4.2, "Steps to Perform on the Oracle HTTP Server Machine."
Validate that the Content Server is accessible at http://WEBHOST2:7777/idc.
9.8.2 Configuring the Load Balancer
The load balancer in the WebCenter enterprise topology should already be able to send requests from the load balancer address:
http://wcinternal.mycompany.com/idc
to both
http://webhost1:7777/idc
and
http://webhost2:777/idc
Validate the above before continuing.
9.9 Reconfiguring the Content Server to Support RAC
In the file <content_server_dir>/config/config.cfg, edit the JdbcConnectionString line to provide an RAC connection string. For example:
JdbcConnectionString=jdbc:oracle:thin:@(DESCRIPTION=
(ADDRESS_LIST=(ADDRESS=(PROTOCOL=TCP) (HOST=RACHOST1) (PORT=1521))
(ADDRESS=(PROTOCOL=TCP) (HOST=RACHOST2) (PORT=1521))
) (CONNECT_DATA=(SERVICE_NAME=wcedg)))
9.10 Backing Up the Installation
Back up all the installation files on both the Web machine and the Content Server machine.
For the HTTP Server machine, back up the configuration directory:
WEBHOST1> tar -cvpf ucmWHconfigback.tar /shared/oracle/ucm/server
For the Content Server machine, back up all install files and configuration:
WCHOST1> tar -cvpf ucmCSback.tar /shared/oracle/ucm/server
In addition, back up the cluster configuration files:
WCHOST1> tar -cvpf ucmCS1back.tar <ocs-stub> WCHOST2> tar -cvpf ucmCS2back.tar <ocs-stub>