10 Configuring Policies
This chapter discusses how to configure policies in Web services and Web service clients to achieve Quality of Service (QoS) requirements.
The predefined policies are described in Appendix B, "Predefined Policies". This Appendix is the definitive source of information for the format of the policies. Some information from the Appendix is repeated here for your convenience.
This chapter includes the following sections:
Determining Which Security Policies to Use
Use the following series of questions to help you identify the security policies that best meet your requirements:
-
What are the basic requirements of your security policy? Decide if you need to only authenticate users, or if you only need message protection, or if you need both.
-
Do you require authentication only? If yes, then go to step 2.
-
Do you require authorization only? If yes, then see "Authorization Policies and Configuration Steps"
-
Do you require authentication and authorization? If yes, then go to step 3.
-
Do you only require message protection? If yes, then see "Message Protection-Only Policies and Configuration Steps".
-
Do you require both authentication and message protection? If yes, then go to step 4.
-
-
If you only require authentication, then there are two basic questions you need to consider:
-
Where will the token be inserted? Will the token to be inserted in the transport layer or in a SOAP header?
-
Do you need to use a particular type of token? The supported credentials for authentication-only policies are username/password, SAML, and Kerberos tokens.
-
-
If you require authentication and authorization, then you need to consider the following:
-
Review the considerations provided for authentication in step 2.
-
Review "Authorization Policies and Configuration Steps" for more information about authorization policies.
-
-
If you require both authentication and message protection, then you need to consider the following:
-
Will message protection be handled in the transport layer? If yes, then there are four sets of policies to choose from: Username over SSL, SAML over SSL (Sender-Vouches), SAML over SSL (Token Bearer), and HTTP token over SSL.
In one set of policies (wss_http_token_over_ssl_client_policy and wss_http_token_over_ssl_service_policy) authentication is also handled in the transport layer. For the other three polices, authentication takes place in the SOAP header.
If you are using the WS-Security V1.0 or V1.1 standard, then both authentication and message protection occur in the SOAP header. There are five pairs of policies supporting the following tokens: username/password, SAML, and X.509 certificates.
For more information, see "Message Protection and Authentication Policies and Configuration Steps".
-
Protecting Messages
Message protection involves encrypting the message for message confidentiality and signing the message for message integrity. Oracle Fusion Middleware predefined policies and any policy you create using one of the message-protection assertion templates provide the options for message confidentiality, message integrity, or both.
The following steps summarizes what you must do in order to configure the clients and services for message protection:
-
Attach the appropriate message protection policy to each of the clients and services.
-
If you want message integrity, then the message must be signed.
-
If you want message confidentiality, then the message must be encrypted.
-
Add the required public and private keys to the keystores of the clients and services. This step requires you to configure the keystore, as described in "Setting up the Keystore for Message Protection".
Message Protection Basics
Message protection encompasses two concepts, message confidentiality and message integrity.
Message confidentiality involves keeping the data secret, as well as the identities of the sending and receiving parties. Confidentiality is achieved by encrypting the content of messages and obfuscating the identifies of the sending and receiving parties. The sender uses the recipient's public key to encrypt the message. Only the recipient's private key can successfully decrypt the message, ensuring that it cannot be read by third parties while in transit. The Web service's base64-encoded public certificate is published in the WSDL for use by the Web service client, as described in "Using Service Identity Certification Extension".
Message integrity is achieved by having an authority digitally sign the message. Digital signatures are used to authenticate the sender of the SOAP message and to ensure the integrity of the SOAP message (that is, to ensure that the SOAP message is not altered while in transit).
When a digital signature is applied to a SOAP message, a unique hash is produced from the message, and this hash is then encrypted with the sender's private key. When the message is received, the recipient decrypts the hash using the sender's public key.
Note:
Generally, the recipient does not need to have the sender's public key in its keystore to validate the certificate. It is sufficient to have the root certificate in the keystore to verify the certificate chain. However, if the sender's public key is not present in the message, as in the case of the Thumbprint and SerialIssuer mechanisms, the sender's public key must be in the recipient's keystore.This serves to authenticate the sender, because only the sender could have encrypted the hash with the private key. It also serves to ensure that the SOAP message has not been tampered with while in transit, because the recipient can compare the hash sent with the message with a hash produced on the recipient's end.
The message-protection assertion templates and predefined policies can be used to protect request and response messages by doing the following:
-
Signing messages
-
Encrypting messages
-
Signing and encrypting messages
-
Decrypting messages
-
Verifying signatures
-
Decrypting messages and verifying signatures
The Fusion Middleware Control user interface for the predefined message protection policies makes it easy to specify which message parts are signed, encrypted, or both, as shown in Figure 10-1. You can require that the entire body be signed, encrypted, or both, or identity specific header and body elements.
Figure 10-1 The Signing and Encryption Portion of Message Protection Policies
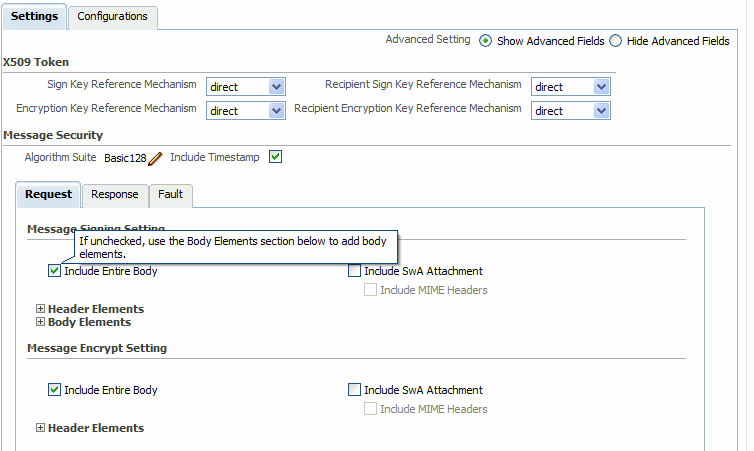
Description of "Figure 10-1 The Signing and Encryption Portion of Message Protection Policies"
Security SwA Attachments
Packaging as attachments in SOAP messages has become a norm in the Web services area for any data that cannot be placed inside SOAP Envelope. The primary SOAP message can reference additional entities as attachments or attachments with MIME headers.
Each SwA attachment is a MIME part and contains the MIME header. Include SwA Attachment signs the attachment but not the MIME header corresponding to that. Include MIME Headers signs the corresponding MIME headers as well as the attachments.
Which Policies Offer Message Protection?
The following policies offer message protection. The subsequent sections for each of these policies later in this chapter describe how each policy implements message protection.
-
oracle/wss10_message_protection_client_policy
-
oracle/wss10_message_protection_service_policy
-
oracle/wss10_username_id_propagation_with_msg_protection_client_policy
-
oracle/wss10_username_id_propagation_with_msg_protection_service_policy
-
oracle/wss10_username_token_with_message_protection_client_policy
-
oracle/wss10_username_token_with_message_protection_service_policy
-
oracle/wss10_username_token_with_message_protection_ski_basic256_client_policy
-
oracle/wss10_username_token_with_message_protection_ski_basic256_service_policy
-
oracle/wss10_x509_token_with_message_protection_client_policy
-
oracle/wss10_x509_token_with_message_protection_service_policy
-
oracle/wss10_saml_token_with_message_protection_client_policy
-
oracle/wss10_saml_token_with_message_protection_service_policy
-
oracle/wss10_saml_token_with_message_protection_ski_basic256_client_policy
-
oracle/wss10_saml_token_with_message_protection_ski_basic256_service_policy
-
oracle/wss11_message_protection_client_policy
-
oracle/wss11_message_protection_service_policy
-
oracle/wss11_kerberos_token_with_message_protection_client_policy
-
oracle/wss11_kerberos_token_with_message_protection_service_policy
-
oracle/wss11_saml_token_with_message_protection_client_policy
-
oracle/wss11_saml_token_with_message_protection_service_policy
-
oracle/wss11_username_token_with_message_protection_client_policy
-
oracle/wss11_username_token_with_message_protection_service_policy
-
oracle/wss11_x509_token_with_message_protection_client_policy
-
oracle/wss11_x509_token_with_message_protection_service_policy
Both the WS-Security 1.0 and WS-Security 1.1 standards are supported. Use the assertion template or predefined policy that supports the standard which both the Web service and client share in common. If you are starting anew, use the WS-Security 1.1 standard because it provides more options and requires less PKI deployment.
The assertion templates support partial signing and encryption as well as full signing and encryption of the message body. For those assertion templates or predefined policies that provide SOAP message protection, the default behavior is to protect the entire SOAP message body by signing and encrypting the entire SOAP body. You can configure the assertions and policies to protect selected elements, if you wish.
Authentication-Only Policies and Configuration Steps
Table B-1 in Appendix B, "Predefined Policies" summarizes the security policies that enforce authentication only, and indicates whether the token is inserted at the transport layer or SOAP header.
This section lists the authentication-only predefined policies, indicates the type of Web service to which they apply, and provides a link to the configuration steps you must perform to use them.
oracle/wss_http_token_client_policy
The oracle/wss_http_token_client_policy policy includes credentials in the HTTP header for outbound client requests. It is the analogous client policy to the oracle/wss_http_token_service_policy service endpoint policy.
This policy contains the following policy assertion: oracle/wss_http_token_client_template. See "oracle/wss_http_token_client_template" for more information about the assertion.
How to Set Up the Web Service Client
You can specify a value for csf-key on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy.
The value signifies a key that maps to a username/password. See "Configuring the Credential Store Provider" for information on how to add the key to the credential store.
If you do not set the Require Mutual Authentication control, SSL is not involved. If you do set the Require Mutual Authentication control, the client must supply credentials, and expect credentials back from the Web service. See "Configuring Two-Way SSL for a Web Service Client".
How to Set Up the Web Service Client at Design Time
See "Using Client Programmatic Configuration Overrides" for a description of the configuration settings you can override.
The client must pass the credentials in the HTTP header.
If you do not set the Require Mutual Authentication control, SSL is not involved. If you do set the Require Mutual Authentication control, the client must supply credentials, and expect credentials back from the Web service. See "Configuring Two-Way SSL for a Web Service Client".
oracle/wss_http_token_service_policy
The wss_http_token_service_policy uses the credentials in the HTTP header to authenticate users.
This policy contains the following policy assertion: oracle/wss_http_token_service_template. See "oracle/wss_http_token_service_template" for more information about the assertion.
How to Set Up WebLogic Server
The Web service must authenticate the supplied username and password credentials against the configured authentication source.
Use the WebLogic Server Administration Console to add an Authentication provider to the active security realm for the WebLogic domain in which the Web service is deployed, as described in "Configuring an Authentication Provider in WebLogic Server".
For mutual SSL authentication, you must configure WebLogic Server. See "Configuring SSL on WebLogic Server (Two-Way)".
oracle/wss_username_token_client_policy
Note:
This policy is not secure and is provided for demonstration purposes only. The password is sent in clear text.This policy includes credentials in the WS-Security UsernameToken header for all outbound SOAP request messages. A plain text mechanism is supported, in addition to a password not being required. It is the analogous client policy to the oracle/wss_username_token_service_policy service endpoint policy.
This policy contains the following policy assertion: oracle/wss_username_token_client_template. See "oracle/wss_username_token_client_template" for more information about the assertion.
How to Set Up the Web Service Client
You can specify a value for csf-key on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy.
The value signifies a key that maps to a username/password. See "Configuring the Credential Store Provider" for information on how to add the key to the credential store.
If you specify a password type of None on the Settings page, you do not need to include a password in the key.
How to Set Up the Web Service Client At Design Time
See "Using Client Programmatic Configuration Overrides" for a description of the configuration settings you can override.
The client must include a WS-Security UsernameToken element (<wsse:UsernameToken/>) in the SOAP request message. The client provides a username and password for authentication.
oracle/wss_username_token_service_policy
Note:
This policy is not secure and is provided for demonstration purposes only. The password is sent in clear text.This policy uses the credentials in the UsernameToken WS-Security SOAP header to authenticate users. The plain text mechanism is supported.
This policy contains the following policy assertion: oracle/wss_username_token_service_template. See "oracle/wss_username_token_service_template" for more information about the assertion.
How to Set Up WebLogic Server
Use the WebLogic Server Administration Console to add an Authentication provider to the active security realm for the WebLogic domain in which the Web service is deployed, as described in "Configuring an Authentication Provider in WebLogic Server".
oracle/wss10_saml_token_client_policy
Note:
This policy is not secure and is provided for demonstration purposes only. Although the SAML issuer name is present, the SAML token is not endorsed. Therefore, it is possible to spoof the message.This policy includes SAML tokens in outbound SOAP request messages.
This policy contains the following policy assertion: oracle/wss10_saml_token_client_template. See "oracle/wss10_saml_token_client_template" for more information about the assertion.
How to Set Up the Web Service Client
See "Configuring SAML".
You can specify a value for saml.issuer.name on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy. The saml.issuer.name property defaults to a value of www.oracle.com. See "Adding an Additional SAML Assertion Issuer Name" for additional considerations.
How to Set Up the Web Service Client at Design Time
See "How to Configure SAML Web Service Client at Design Time".
See "Using Client Programmatic Configuration Overrides" for a description of the configuration settings you can override.
Include a WS-Security Header Element (<saml:Assertion>) that inserts a SAML token in the outbound SOAP message. The confirmation type is always sender-vouches.
oracle/wss10_saml_token_service_policy
Note:
This policy is not secure and is provided for demonstration purposes only. Although the SAML issuer name is present, the SAML token is not endorsed. Therefore, it is possible to spoof the message.This policy authenticates users using credentials provided in SAML tokens in the WS-Security SOAP header.
This policy contains the following policy assertion: oracle/wss10_saml_token_service_template. See "oracle/wss10_saml_token_service_template" for more information about the assertion.
Configure the Login Module
Configure the saml.loginmodule login module. See "Configuring the SAML and Kerberos Login Modules" for more information.
How to Set Up Oracle Platform Security Services (OPPS)
See "Configuring SAML".
How to Set Up WebLogic Server
Use the WebLogic Server Administration Console to add an Authentication provider to the active security realm for the WebLogic domain in which the Web service is deployed, as described in "Configuring an Authentication Provider in WebLogic Server".
The SAML login module extracts the username from the verified token and passes it (via the NameCallback) to the provider.
oracle/wss11_kerberos_token_client_policy
This policy includes a Kerberos token in the WS-Security header in accordance with the WS-Security Kerberos Token Profile v1.1 standard.
Service principal names (SPN) are a key component in Kerberos authentication. SPNs are unique identifiers for services running on servers. Every service that uses Kerberos authentication needs to have an SPN set for it so that clients can identify the service on the network. If an SPN is not set for a service, clients have no way of locating that service and Kerberos authentication is not possible.
This policy contains the following policy assertion: oracle/wss11_kerberos_token_client_template. See "oracle/wss11_kerberos_token_with_message_protection_client_template" for more information about the assertion.
How to Set Up the Web Service Client
The Web service client that is enforcing Kerberos client side policies needs to know the service principal name of the service it is trying to access. You can specify a value for service.principal.name on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy. The default value (place holder) is HOST/localhost@oracle.com.
How to Set Up the Web Service Client at Design Time
You must set the service principal name. The service principal name specifies the name of the service principal for which the client requests a ticket from the KDC.
If the Kerberos authentication is successful, then send the obtained Kerberos ticket and authenticator to the Web service enclosed in a BinarySecurityToken element in the SOAP Security header.
oracle/wss11_kerberos_token_service_policy
This policy is enforced in accordance with the WS-Security Kerberos Token Profile v1.1 standard.
Service principal names (SPN) are a key component in Kerberos authentication. SPNs are unique identifiers for services running on servers. Every service that uses Kerberos authentication needs to have an SPN set for it so that clients can identify the service on the network. If an SPN is not set for a service, clients have no way of locating that service and Kerberos authentication is not possible.
This policy contains the following policy assertion: oracle/wss11_kerberos_token_service_template. See "oracle/wss11_kerberos_token_with_message_protection_service_template" for more information about the assertion.
Configure the Login Module
Configure the krb5.loginmodule login module. See "Configuring the SAML and Kerberos Login Modules" for more information.
How to Configure WebLogic Server
Use the WebLogic Server Administration Console to add an Authentication provider to the active security realm for the WebLogic domain in which the Web service is deployed, as described in "Configuring an Authentication Provider in WebLogic Server".
Message Protection-Only Policies and Configuration Steps
See "Protecting Messages" for a description of how the predefined policies implement message protection.
Table B-2 summarizes the policies that enforce only message protection, and indicates whether the policy is enforced at the transport layer or SOAP header.
Message protection-only policies do not authenticate or authorize the requester.
There may be either one or two Security policies attached to a policy subject. A Security policy can contain an assertion that belongs to the authentication or message protection (as in this case) subtype categories, or a single assertion that belongs to both subtype categories. You can then use an assertion that belongs to the authorization subtype to authorize the requester.
oracle/wss10_message_protection_client_policy
This policy provides message protection (integrity and confidentiality) for outbound SOAP requests in accordance with the WS-Security 1.0 standard.
This policy contains the following policy assertion: oracle/wss10_message_protection_client_template. See "oracle/wss10_message_protection_client_policy" for more information about the assertion.
How to Set Up the Web Service Client
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the Web service keystore, as described in "Setting up the Keystore for Message Protection".
The Web service's base64-encoded public certificate is published in the WSDL for use by the Web service client, as described in "Using Service Identity Certification Extension".
As an alternative, you can specify a value for keystore.recipient.alias on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy. The keystore.recipient.alias specifies the alias used to look up the public key in the keystore when retrieving a key for encryption of outbound SOAP messages.
You can specify a value for keystore.sig.csf.key and keystore.enc.csf.key on the Configurations page, or override them on a per-client basis using the Security Configuration Details control when you attach the policy.
How to Set Up the Web Service Client at Design Time
This policy requires you to set up the Web service client keystore, as described in "Setting Up the Web Service Client Keystore at Design Time". The policy specifically requires that the client's and Web service's respective keystores already contain digital certificates containing each other's public key.
See "Using Client Programmatic Configuration Overrides" for a description of the configuration settings you can override.
Configure the policy assertion for message signing, message encryption, or both.
Example 10-1 shows the typical structure of a signature included in the Security header in conformance with the WS-Security 1.0 standards. In this example, the body element of the SOAP message is signed.
Example 10-1 WS-Security 1.0 Message Integrity of SOAP Message
<dsig:Signature xmlns:dsig="http://www.w3.org/2000/09/xmldsig#">
<dsig:SignedInfo>
<dsig:CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/>
<dsig:SignatureMethod Algorithm="http://www.w3.org/2000/09/xmldsig#rsa-sha1"/>
<dsig:Reference URI="#Timestamp-...">
<dsig:Transforms>
<dsig:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/>
</dsig:Transforms>
<dsig:DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha1"/>
<dsig:DigestValue>...</dsig:DigestValue>
</dsig:Reference>
<dsig:Reference URI="#Body-...">
<dsig:Transforms>
<dsig:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#"/>
</dsig:Transforms>
<dsig:DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha1"/>
<dsig:DigestValue>...</dsig:DigestValue>
</dsig:Reference>
<dsig:Reference URI="#KeyInfo-...">
<dsig:Transforms>
<dsig:Transform
Algorithm="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#STR-Transform">
<TransformationParameters xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<CanonicalizationMethod Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" xmlns="http://www.w3.org/2000/09/xmldsig#"/>
</TransformationParameters>
</dsig:Transform>
</dsig:Transforms>
<dsig:DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha1"/>
<dsig:DigestValue>...</dsig:DigestValue>
</dsig:Reference>
</dsig:SignedInfo>
<dsig:SignatureValue>....</dsig:SignatureValue>
<dsig:KeyInfo Id="KeyInfo-...">
<wsse:SecurityTokenReference xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<wsse:KeyIdentifier ValueType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-x509-token-profile-1.0#X509SubjectKeyIdentifier"
EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">
...</wsse:KeyIdentifier>
</wsse:SecurityTokenReference>
</dsig:KeyInfo>
</dsig:Signature>
Example 10-2 is an example of the typical structure of encryption elements included in the Security header in conformance with the WS-Security 1.0 standards. In this example, the body element is encrypted.
Example 10-2 WS-Security 1.0 Message Confidentiality of SOAP Message
<env:Body xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd" wsu:Id="Body-JA9fsCRnqbFJ0ocBAMKb7g22">
<xenc:EncryptedData xmlns:xenc="http://www.w3.org/2001/04/xmlenc#" Type="http://www.w3.org/2001/04/xmlenc#Content" Id="...">
<xenc:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes256-cbc"/>
<xenc:CipherData>
<xenc:CipherValue>...</xenc:CipherValue>
</xenc:CipherData>
</xenc:EncryptedData>
</env:Body>
oracle/wss10_message_protection_service_policy
This policy enforces message protection (integrity and confidentiality) for inbound SOAP requests in accordance with the WS-Security 1.0 standard.
The messages are protected using WS-Security's Basic 128 suite of asymmetric key technologies, specifically RSA key mechanism for message confidentiality, SHA-1 hashing algorithm for message integrity, and AES-128 bit encryption. This policy does not authenticate or authorize the requester.
This policy contains the following policy assertion: oracle/wss10_message_protection_service_template. See "oracle/wss10_message_protection_service_template" for more information about the assertion.
Properties You Can Configure
See Table C-17. You also have the option to override the keystore.sig.csf.key and keystore.enc.csf.key server-side configuration properties, as described in "Attaching Web Service Policies Permitting Overrides".
How to Set Up Oracle Platform Security Services (OPSS)
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the keystore, as described in "Setting up the Keystore for Message Protection".
Store the trusted certificate that corresponds to the client's private key (used to sign the message) in the keystore. You also need to store the service's private key in the keystore for decrypting the message, and the CA root certificate.
You must store the password for the decryption key in the credential store, as described in "Configuring the Credential Store Provider". Use keystore.enc.csf.key as the key name.
You also have the option to override the keystore.sig.csf.key and keystore.enc.csf.key server-side configuration properties, as described in "Attaching Web Service Policies Permitting Overrides".
oracle/wss11_message_protection_client_policy
This policy provides message integrity and confidentiality for outbound SOAP requests in accordance with the WS-Security 1.1 standard.
This policy contains the following policy assertion: oracle/wss11_message_protection_client_template. See "oracle/wss11_message_protection_client_template" for more information about the assertion.
How to Configure the Web Service Client
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the Web service keystore, as described in "Setting up the Keystore for Message Protection".
The Web service's base64-encoded public certificate is published in the WSDL for use by the Web service client, as described in "Using Service Identity Certification Extension".
As an alternative, you can specify a value for keystore.recipient.alias on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy. The keystore recipient alias specifies the alias used to look up the public key in the keystore when retrieving a key for encryption of outbound SOAP messages.
You can specify a value for keystore.enc.csf.key on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy.
How to Configure the Web Service Client at Design Time
This policy requires you to set up the Web service client keystore, as described in "Setting Up the Web Service Client Keystore at Design Time". The policy specifically requires that the client's and Web service's respective keystores already contain digital certificates containing each other's public key.
This policy uses symmetric key technology, which is an encryption method that uses the same shared key to encrypt and decrypt data. The symmetric key is used to sign the message.
See "Using Client Programmatic Configuration Overrides" for a description of the configuration settings you can override.
Configure the policy assertion for message signing, message encryption, or both.
Example 10-3 is an example of the typical structure of encryption elements included in the Security header in conformance with the WS-Security 1.1 standards. In this example, the body element is encrypted.
Example 10-3 WS-Security 1.1 Message Confidentiality of SOAP Message
<xenc:EncryptedKey xmlns:xenc="http://www.w3.org/2001/04/xmlenc#" Id="EK-...">
<xenc:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#rsa-oaep-mgf1p">
<dsig:DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha1" xmlns:dsig="http://www.w3.org/2000/09/xmldsig#" />
</xenc:EncryptionMethod>
<dsig:KeyInfo xmlns:dsig="http://www.w3.org/2000/09/xmldsig#">
<wsse:SecurityTokenReference xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<wsse:KeyIdentifier ValueType="http://docs.oasis-open.org/wss/oasis-wss-soap-message-security-1.1#ThumbprintSHA1"
EncodingType="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0#Base64Binary">...</wsse:KeyIdentifier>
</wsse:SecurityTokenReference>
</dsig:KeyInfo>
<xenc:CipherData>
<xenc:CipherValue>...</xenc:CipherValue>
</xenc:CipherData>
<xenc:ReferenceList>
<xenc:DataReference URI="#_..." />
</xenc:ReferenceList>
</xenc:EncryptedKey>
<env:Body xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd" wsu:Id="Body-...">
<xenc:EncryptedData xmlns:xenc="http://www.w3.org/2001/04/xmlenc#" Type="http://www.w3.org/2001/04/xmlenc#Content" Id="...">
<xenc:EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes256-cbc" />
<dsig:KeyInfo xmlns:dsig="http://www.w3.org/2000/09/xmldsig#">
<wsse:SecurityTokenReference xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd"
xmlns="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd">
<wsse:Reference URI="#EK-..." ValueType="http://docs.oasis-open.org/wss/oasis-wss-soap-message-security-1.1#EncryptedKey" />
</wsse:SecurityTokenReference>
</dsig:KeyInfo>
<xenc:CipherData>
<xenc:CipherValue>...</xenc:CipherValue>
</xenc:CipherData>
</xenc:EncryptedData>
</env:Body>
oracle/wss11_message_protection_service_policy
This policy enforces message integrity and confidentiality for inbound SOAP requests in accordance with the WS-Security 1.1 standard.
This policy contains the following policy assertion: oracle/wss11_message_protection_service_template. See "oracle/wss11_message_protection_service_template" for more information about the assertion.
Properties You Can Configure
See Table C-20. You also have the option to override the keystore.enc.csf.key server-side configuration property, as described in "Attaching Web Service Policies Permitting Overrides".
How to Set Up Oracle Platform Security Services (OPSS)
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the keystore, as described in "Setting up the Keystore for Message Protection".
Store the trusted certificate that corresponds to the client's private key (used to sign the message) in the keystore. You also need to store the service's private key in the keystore for decrypting the message, and the CA root certificate.
You must store the password for the decryption key in the credential store, as described in "Configuring the Credential Store Provider". Use keystore.enc.csf.key as the key name.
You also have the option to override the keystore.enc.csf.key server-side configuration property, as described in "Attaching Web Service Policies Permitting Overrides".
Message Protection and Authentication Policies and Configuration Steps
Table B-3 summarizes the policies that enforce both message protection and authentication, and indicates whether the policy is enforced at the transport layer or SOAP header. These polices are described in the sections that follow.
See "Protecting Messages" for a description of how the predefined policies implement message protection.
Configuring a Policy With an OR Group
The oracle/wss11_saml_or_username_token_with_message_protection_service_policy and oracle/wss_saml_or_username_token_over_ssl_service_policy policies contain assertions as an OR group--meaning that either type of assertion can be enforced by a client.
In addition, you can add an OR group to the policy of your choice, as described in "Adding an OR Group to a Policy".
The oracle/wss11_saml_or_username_token_with_message_protection_service_policy policy contains the following assertions:
-
oracle/wss11_saml_token_with_message_protection_service_template. See "oracle/wss11_saml_token_with_message_protection_service_policy" for information about configuring the policy.
-
oracle/wss11_username_token_with_message_protection_service_template. See "oracle/wss11_username_token_with_message_protection_service_policy" for information about configuring the policy.
The oracle/wss_saml_or_username_token_over_ssl_service_policy policy contains the following assertions:
-
oracle/wss_saml_token_over_ssl_service_template. See "oracle/wss_saml_token_over_ssl_service_policy" for information about configuring the policy.
-
oracle/wss_username_token_over_ssl_service_template. See "oracle/wss_username_token_over_ssl_service_policy" for information about configuring the policy.
oracle/wss_http_token_over_ssl_client_policy
This policy includes credentials in the HTTP header for outbound client requests.
This policy also verifies that the transport protocol is HTTPS. Requests over a non-HTTPS transport protocol are refused. This policy can be applied to any HTTP-based endpoint.
Note:
Currently only HTTP basic authentication is supported.This policy contains the following policy assertion: oracle/wss_http_token_over_ssl_client_template. See "oracle/wss_http_token_over_ssl_client_template" for more information about the assertion.
How to Set Up the Web Services Client
You can specify a value for csf-key on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy.
The value signifies a key that maps to a username/password. See "Configuring the Credential Store Provider" for information on how to add the key to the credential store.
If you do not set the Require Mutual Authentication control, one-way SSL is involved. See "Configuring SSL for a Web Service Client".
If you do set the Require Mutual Authentication control, the client must supply credentials, and expect credentials back from the Web service. See "Configuring Two-Way SSL for a Web Service Client".
How to Set Up the Web Service Client at Design Time
See "Using Client Programmatic Configuration Overrides" for a description of the configuration settings you can override.
The client must pass the credentials in the HTTP header.
If you do not set the Require Mutual Authentication control, one-way SSL is involved. See "Configuring SSL for a Web Service Client".
If you do set the Require Mutual Authentication control, the client must supply credentials, and expect credentials back from the Web service. See "Configuring Two-Way SSL for a Web Service Client".
oracle/wss_http_token_over_ssl_service_policy
This policy extracts the credentials in the HTTP header and authenticates users.
This policy verifies that the transport protocol is HTTPS. Requests over a non-HTTPS transport protocol are refused. This policy can be applied to any HTTP-based endpoint.
Note:
Currently only HTTP basic authentication is supported.This policy contains the following policy assertion: oracle/wss_http_token_over_ssl_service_template. See "oracle/wss_http_token_over_ssl_service_template" for more information about the assertion.
How to Set Up WebLogic Server
Configure SSL, as described in "Configuring SSL on WebLogic Server (One-Way)", or as in "Configuring SSL on WebLogic Server (Two-Way)" if Allow Mutual Authentication is checked.
Use the WebLogic Server Administration Console to add an Authentication provider to the active security realm for the WebLogic domain in which the Web service is deployed, as described in "Configuring an Authentication Provider in WebLogic Server".
oracle/wss_saml_token_bearer_over_ssl_client_policy
This policy includes SAML tokens in outbound SOAP request messages. The SAML token with confirmation method Bearer is created automatically.
This policy contains the following policy assertion: oracle/wss_saml_token_bearer_over_ssl_client_template. See "oracle/wss_saml_token_bearer_over_ssl_client_template" for more information about the assertion.
How to Set Up the Web Service Client
See "How to Configure SAML Web Service Client at Design Time".
If you do not set the Require Mutual Authentication control, one-way SSL is involved, as described in "Configuring SSL for a Web Service Client".
If you do set the Require Mutual Authentication control, the client must supply credentials, and expect credentials back from the Web service. See "Configuring Two-Way SSL for a Web Service Client".
How to Set Up the Web Service Client at Design Time
See "How to Configure SAML Web Service Client at Design Time".
See "Using Client Programmatic Configuration Overrides" for a description of the configuration settings you can override.
If you do not set the Require Mutual Authentication control, one-way SSL is involved, as described in "Configuring SSL for a Web Service Client".
If you do set the Require Mutual Authentication control, the client must supply credentials, and expect credentials back from the Web service. See "Configuring Two-Way SSL for a Web Service Client".
oracle/wss_saml_token_bearer_over_ssl_service_policy
This policy authenticates users using credentials provided in SAML tokens with confirmation method 'Bearer' in the WS-Security SOAP header.
This policy contains the following policy assertion: oracle/wss_saml_token_bearer_over_ssl_service_template. See "oracle/wss_saml_token_bearer_over_ssl_service_template" for more information about the assertion.
Configure the Login Module
Configure the saml.loginmodule login module. See "Configuring the SAML and Kerberos Login Modules" for more information.
How to Set Up Oracle Platform Security Services (OPSS)
See "Configuring SAML".
Use the WebLogic Server Administration Console to add an Authentication provider to the active security realm for the WebLogic domain in which the Web service is deployed, as described in "Configuring an Authentication Provider in WebLogic Server".
The SAML login module extracts the username from the verified token and passes it (via the NameCallback) to the Authentication provider.
To configure SSL, see "Configuring SSL on WebLogic Server (One-Way)", or "Configuring SSL on WebLogic Server (Two-Way)" if Require Mutual Authentication is checked.
oracle/wss_saml_token_over_ssl_client_policy
This policy enables the authentication of credentials provided via a SAML token within WS-Security SOAP header.
This policy contains the following policy assertion: oracle/wss_saml_token_over_ssl_client_template. See "oracle/wss_saml_token_over_ssl_client_template" for more information about the assertion.
How to Set Up the Web Service Client
See "How to Configure SAML Web Service Client at Design Time".
If you do not set the Require Mutual Authentication control, one-way SSL is involved, as described in "Configuring SSL for a Web Service Client".
If you do set the Require Mutual Authentication control, the client must supply credentials, and expect credentials back from the Web service. See "Configuring Two-Way SSL for a Web Service Client".
How to Set Up the Web Service Client at Design Time
See "How to Configure SAML Web Service Client at Design Time".
See "Using Client Programmatic Configuration Overrides" for a description of the configuration settings you can override.
If you do not set the Require Mutual Authentication control, one-way SSL is involved, as described in "Configuring SSL for a Web Service Client".
If you do set the Require Mutual Authentication control, the client must supply credentials, and expect credentials back from the Web service. See "Configuring Two-Way SSL for a Web Service Client".
oracle/wss_saml_token_over_ssl_service_policy
This policy enforces the authentication of credentials provided via a SAML token within WS-Security SOAP header.
This policy contains the following policy assertion: oracle/wss_saml_token_over_ssl_service_template. See "oracle/wss_saml_token_over_ssl_service_template" for more information about the assertion.
Configure the Login Module.
Configure the saml.loginmodule login module. See "Configuring the SAML and Kerberos Login Modules" for more information.
How to Set Up Oracle Platform Security Services (OPSS)
See "Configuring SAML".
How to Set Up WebLogic Server
Use the WebLogic Server Administration Console to add an Authentication provider to the active security realm for the WebLogic domain in which the Web service is deployed, as described in "Configuring an Authentication Provider in WebLogic Server".
The SAML login module extracts the username from the verified token and passes it (via the NameCallback) to the Authentication provider.
To configure SSL, see "Configuring SSL on WebLogic Server (One-Way)", or "Configuring SSL on WebLogic Server (Two-Way)" if Require Mutual Authentication is checked.
oracle/wss_username_token_over_ssl_client_policy
This policy includes credentials in the WS-Security UsernameToken header in outbound SOAP request messages. The plain text mechanism is supported. The policy also uses SSL for achieving transport layer security.
This policy contains the following policy assertion: oracle/wss_username_token_over_ssl_client_template. See "oracle/wss_username_token_over_ssl_client_template" for more information about the assertion.
How to Set Up the Web Service Client
If you do not set the Require Mutual Authentication control, one-way SSL is involved, as described in "Configuring SSL for a Web Service Client".
If you do set the Require Mutual Authentication control, the client must supply credentials, and expect credentials back from the Web service. See "Configuring Two-Way SSL for a Web Service Client".
You can specify a value for csf-key on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy.
The value signifies a key that maps to a username/password. See "Configuring the Credential Store Provider" for information on how to add the key to the credential store.
If you specify a password type of None on the Settings page, you do not need to include a password in the key.
How to Set Up the Web Service Client at Design Time
The client must include a WS-Security UsernameToken element (<wsse:UsernameToken/>) in the SOAP request message. The client provides a username and password for authentication.
See "Using Client Programmatic Configuration Overrides" for a description of the configuration settings you can override.
If you do not set the Require Mutual Authentication control, one-way SSL is involved. See "Configuring SSL for a Web Service Client".
If you do set the Require Mutual Authentication control, the client must supply credentials, and expect credentials back from the Web service. See "Configuring Two-Way SSL for a Web Service Client".
oracle/wss_username_token_over_ssl_service_policy
This policy uses the credentials in the UsernameToken WS-Security SOAP header to authenticate users. The plain text mechanism is supported.
This policy contains the following policy assertion: oracle/wss_username_token_over_ssl_service_template. See "oracle/wss_username_token_over_ssl_service_template" for more information about the assertion.
How to Set Up WebLogic Server
Use the WebLogic Server Administration Console to add an Authentication provider to the active security realm for the WebLogic domain in which the Web service is deployed, as described in "Configuring an Authentication Provider in WebLogic Server".
The username and password must exist and be valid.
To configure SSL, see "Configuring SSL on WebLogic Server (One-Way)", or "Configuring SSL on WebLogic Server (Two-Way)" if Require Mutual Authentication is checked.
oracle/wss10_saml_hok_token_with_message_protection_client_policy
This policy provides message-level protection and SAML holder of key based authentication for outbound SOAP messages in accordance with the WS-Security 1.0 standard.
This policy contains the following policy assertion: oracle/wss10_saml_hok_with_message_integrity_client_template. See "oracle/wss10_saml_hok_with_message_protection_service_template" for more information about the assertion.
How to Set Up the Web Service Client
See "How to Configure SAML Web Service Client at Design Time".
Override the saml.assertion.filename property to point to the file that has the holder-of-key assertion.
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the Web service keystore, as described in "Setting up the Keystore for Message Protection".
You can specify a value for saml.issuer.name on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy. The saml.issuer.name property defaults to a value of www.oracle.com. See "Adding an Additional SAML Assertion Issuer Name" for additional considerations.
The Web service's base64-encoded public certificate is published in the WSDL for use by the Web service client, as described in "Using Service Identity Certification Extension".
As an alternative, you can specify a value for keystore.recipient.alias on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy. The keystore recipient alias specifies the alias used to look up the public key in the keystore when retrieving a key for encryption of outbound SOAP messages.
You can specify a value for keystore.sig.csf.key and keystore.enc.csf.key on the Configurations page, or override them on a per-client basis using the Security Configuration Details control when you attach the policy.
How to Set Up the Web Service Client at Design Time
See "How to Configure SAML Web Service Client at Design Time".
This policy requires you to set up the Web service client keystore, as described in "Setting Up the Web Service Client Keystore at Design Time". The policy specifically requires that the client's and Web service's respective keystores already contain digital certificates containing each other's public key.
Override the saml.assertion.filename property to point to the file that has the holder-of-key assertion. See "Using Client Programmatic Configuration Overrides" for a description of the configuration settings you can override.
Configure the policy assertion for message signing, message encryption, or both.
Example 10-1 shows the typical structure of a signature included in the Security header in conformance with the WS-Security 1.0 standards. In this example, the body element of the SOAP message is signed.
Example 10-2 is an example of the typical structure of encryption elements included in the Security header in conformance with the WS-Security 1.0 standards. In this example, the body element is encrypted.
oracle/wss10_saml_hok_token_with_message_protection_service_policy
This policy enforces message-level protection and SAML holder of key based authentication for inbound SOAP requests in accordance with the WS-Security 1.0 standard.
This policy contains the following policy assertion: oracle/wss10_saml_hok_with_message_integrity_service_template. See "oracle/wss10_saml_hok_with_message_protection_service_template" for more information about the assertion.
Configure the Login Module
Configure the saml.loginmodule login module. See "Configuring the SAML and Kerberos Login Modules" for more information.
How to Set Up WebLogic Server
Use the WebLogic Server Administration Console to add an Authentication provider to the active security realm for the WebLogic domain in which the Web service is deployed, as described in "Configuring an Authentication Provider in WebLogic Server".
The SAML login module extracts the username from the verified token and passes it (via the NameCallback) to the Authentication provider.
How to Set Up Oracle Platform Security Services (OPSS)
See "Configuring SAML".
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the keystore, as described in "Setting up the Keystore for Message Protection".
Note:
A CertificateExpiredException is returned if an expired certificate is present in the keystore, regardless of whether this certificate is being referenced. To resolve this exception, remove the expired certificate from the keystore.Store the trusted certificate of the SAML authority in the keystore.
Store the trusted certificate that corresponds to the client's private key (used to sign the message) in the keystore. You also need to store the service's private key in the keystore for decrypting the message, and the CA root certificate.
You must store the password for the decryption key in the credential store, as described in "Configuring the Credential Store Provider". Use keystore.enc.csf.key as the key name.
You also have the option to override the keystore.sig.csf.key and keystore.enc.csf.key server-side configuration properties, as described in "Attaching Web Service Policies Permitting Overrides".
oracle/wss10_saml_token_with_message_integrity_client_policy
This policy provides message-level integrity and SAML-based authentication for outbound SOAP messages in accordance with the WS-Security 1.0 standard.
This policy contains the following policy assertion: oracle/wss10_saml_token_with_message_integrity_client_template. See "oracle/wss10_saml_token_with_message_protection_client_template" for more information about the assertion.
How to Set Up the Web Service Client
See "Configuring SAML".
This policy requires you to set up the Web service keystore, as described in "Setting up the Keystore for Message Protection".
You can specify a value for saml.issuer.name on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy. The saml.issuer.name property defaults to a value of www.oracle.com. See "Adding an Additional SAML Assertion Issuer Name" for additional considerations.
You can specify a value for user.roles.include on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy.
You can specify a value for keystore.sig.csf.key and keystore.enc.csf.key on the Configurations page, or override them on a per-client basis using the Security Configuration Details control when you attach the policy.
How to Set Up the Web Service Client at Design Time
See "How to Configure SAML Web Service Client at Design Time".
See "Using Client Programmatic Configuration Overrides" for a description of the configuration settings you can override.
This policy requires you to set up the Web service client keystore, as described in "Setting Up the Web Service Client Keystore at Design Time". The policy specifically requires that the client's and Web service's respective keystores already contain digital certificates containing each other's public key.
Include a WS-Security Header Element (<saml:Assertion>) that inserts a SAML token in the outbound SOAP message. The confirmation type is always sender-vouches.
Example 10-1 shows the typical structure of a signature included in the Security header in conformance with the WS-Security 1.0 standards. In this example, the body element of the SOAP message is signed.
Example 10-2 is an example of the typical structure of encryption elements included in the Security header in conformance with the WS-Security 1.0 standards. In this example, the body element is encrypted.
oracle/wss10_saml_token_with_message_integrity_service_policy
This policy enforces message-level integrity protection and SAML-based authentication for inbound SOAP requests in accordance with the WS-Security 1.0 standard.
This policy contains the following policy assertion: oracle/wss10_saml_token_with_message_integrity_service_template. See "oracle/wss10_saml_token_with_message_protection_service_template" for more information about the assertion.
Properties You Can Configure
See Table C-35.
You also have the option to override the keystore.sig.csf.key and keystore.enc.csf.key server-side configuration properties, as described in "Attaching Web Service Policies Permitting Overrides".
Configure the Login Module
Configure the saml.loginmodule login module. See "Configuring the SAML and Kerberos Login Modules" for more information.
How to Set Up Oracle Platform Security Services (OPSS)
See "Configuring SAML".
You also have the option to override the keystore.sig.csf.key and keystore.enc.csf.key server-side configuration properties, as described in "Attaching Web Service Policies Permitting Overrides".
How to Set Up WebLogic Server
Use the WebLogic Server Administration Console to add an Authentication provider to the active security realm for the WebLogic domain in which the Web service is deployed, as described in "Configuring an Authentication Provider in WebLogic Server".
The SAML login module extracts the username from the verified token and passes it (via the NameCallback) to the Authentication provider.
oracle/wss10_saml_token_with_message_protection_client_policy
This policy provides message-level protection and SAML-based authentication for outbound SOAP messages in accordance with the WS-Security 1.0 standard.
This policy contains the following policy assertion: oracle/wss10_saml_token_with_message_protection_client_template. See "oracle/wss10_saml_token_with_message_protection_client_template" for more information about the assertion.
How to Set Up the Web Service Client
See "Configuring SAML".
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the Web service keystore, as described in "Setting up the Keystore for Message Protection".
The Web service's base64-encoded public certificate is published in the WSDL for use by the Web service client, as described in "Using Service Identity Certification Extension".
As an alternative, you can specify a value for keystore.recipient.alias on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy. The keystore recipient alias specifies the alias used to look up the public key in the keystore when retrieving a key for encryption of outbound SOAP messages.
You can specify a value for keystore.sig.csf.key and keystore.enc.csf.key on the Configurations page, or override them on a per-client basis using the Security Configuration Details control when you attach the policy.
You can specify a value for saml.issuer.name on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy. The saml.issuer.name property defaults to a value of www.oracle.com. See "Adding an Additional SAML Assertion Issuer Name" for additional considerations.
You can specify a value for user.roles.include on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy.
How to Set Up the Web Service Client at Design Time
See "How to Configure SAML Web Service Client at Design Time".
This policy requires you to set up the Web service client keystore, as described in "Setting Up the Web Service Client Keystore at Design Time". The policy specifically requires that the client's and Web service's respective keystores already contain digital certificates containing each other's public key.
See "Using Client Programmatic Configuration Overrides" for a description of the configuration settings you can override.
Configure the policy assertion for message signing, message encryption, or both.
Example 10-1 shows the typical structure of a signature included in the Security header in conformance with the WS-Security 1.0 standards. In this example, the body element of the SOAP message is signed.
Example 10-2 is an example of the typical structure of encryption elements included in the Security header in conformance with the WS-Security 1.0 standards. In this example, the body element is encrypted.
oracle/wss10_saml_token_with_message_protection_service_policy
This policy enforces message-level protection and SAML-based authentication for inbound SOAP requests in accordance with the WS-Security 1.0 standard.
This policy contains the following policy assertion: oracle/wss10_saml_token_with_message_protection_service_template. See "oracle/wss10_saml_token_with_message_protection_service_template" for more information about the assertion.
Properties You Can Configure
See Table C-35.
You also have the option to override the keystore.sig.csf.key and keystore.enc.csf.key server-side configuration properties, as described in "Attaching Web Service Policies Permitting Overrides".
Configure the Login Module
Configure the saml.loginmodule login module. See "Configuring the SAML and Kerberos Login Modules" for more information.
How to Set Up WebLogic Server
Use the WebLogic Server Administration Console to add an Authentication provider to the active security realm for the WebLogic domain in which the Web service is deployed, as described in "Configuring an Authentication Provider in WebLogic Server".
The SAML login module extracts the username from the verified token and passes it (via the NameCallback) to the Authentication provider.
How to Set Up Oracle Platform Security Services (OPSS)
See "Configuring SAML".
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the keystore, as described in "Setting up the Keystore for Message Protection".
Store the trusted certificate that corresponds to the client's private key (used to sign the message) in the keystore. You also need to store the service's private key in the keystore for decrypting the message, and the CA root certificate.
You must store the password for the decryption key in the credential store, as described in "Configuring the Credential Store Provider". Use keystore.enc.csf.key as the key name.
You also have the option to override the keystore.sig.csf.key and keystore.enc.csf.key server-side configuration properties, as described in "Attaching Web Service Policies Permitting Overrides".
oracle/wss10_saml_token_with_message_protection_ski_basic256_client_policy
This policy provides message-level protection and SAML-based authentication for outbound SOAP messages in accordance with the WS-Security 1.0 standard.
This policy uses the Subject Key Identifier (ski) reference mechanism for the encryption key in the request, and for both the signature and encryption keys in the response.
This policy contains the following policy assertion: oracle/wss10_saml_token_with_message_protection_client_template. See "oracle/wss10_saml_token_with_message_protection_client_template" for more information about the assertion.
How to Set Up the Web Service Client
See "Configuring SAML".
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the Web service keystore, as described in "Setting up the Keystore for Message Protection".
The Web service's base64-encoded public certificate is published in the WSDL for use by the Web service client, as described in "Using Service Identity Certification Extension".
As an alternative, you can specify a value for keystore.recipient.alias on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy. The keystore recipient alias specifies the alias used to look up the public key in the keystore when retrieving a key for encryption of outbound SOAP messages.
You can specify a value for keystore.sig.csf.key and keystore.enc.csf.key on the Configurations page, or override them on a per-client basis using the Security Configuration Details control when you attach the policy.
You can specify a value for saml.issuer.name on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy. The saml.issuer.name property defaults to a value of www.oracle.com. See "Adding an Additional SAML Assertion Issuer Name" for additional considerations.
You can specify a value for user.roles.include on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy.
How to Set Up the Web Service Client at Design Time
See "How to Configure SAML Web Service Client at Design Time".
This policy requires you to set up the Web service client keystore, as described in "Setting Up the Web Service Client Keystore at Design Time". The policy specifically requires that the client's and Web service's respective keystores already contain digital certificates containing each other's public key.
See "Using Client Programmatic Configuration Overrides" for a description of the configuration settings you can override.
Configure the policy assertion for message signing, message encryption, or both.
Example 10-1 shows the typical structure of a signature included in the Security header in conformance with the WS-Security 1.0 standards. In this example, the body element of the SOAP message is signed.
Example 10-2 is an example of the typical structure of encryption elements included in the Security header in conformance with the WS-Security 1.0 standards. In this example, the body element is encrypted.
oracle/wss10_saml_token_with_message_protection_ski_basic256_service_policy
This policy enforces message-level protection and SAML-based authentication for inbound SOAP requests in accordance with the WS-Security 1.0 standard.
This policy uses the Subject Key Identifier (ski) reference mechanism for the encryption key in the request, and for both the signature and encryption keys in the response.
This policy contains the following policy assertion: oracle/wss10_saml_token_with_message_protection_service_template. See "oracle/wss10_saml_token_with_message_protection_service_template" for more information about the assertion.
Properties You Can Configure
See Table C-35.
You also have the option to override the keystore.sig.csf.key and keystore.enc.csf.key server-side configuration properties, as described in "Attaching Web Service Policies Permitting Overrides".
Configure the Login Module
Configure the saml.loginmodule login module. See "Configuring the SAML and Kerberos Login Modules" for more information.
How to Set Up WebLogic Server
Use the WebLogic Server Administration Console to add an Authentication provider to the active security realm for the WebLogic domain in which the Web service is deployed, as described in "Configuring an Authentication Provider in WebLogic Server".
The SAML login module extracts the username from the verified token and passes it (via the NameCallback) to the Authentication provider.
How to Set Up Oracle Platform Security Services (OPSS)
See "Configuring SAML".
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the keystore. When using the ski reference mechanism, use OpenSSL or another such utility to create the certificate.
Store the trusted certificate that corresponds to the client's private key (used to sign the message) in the keystore. You also need to store the service's private key in the keystore for decrypting the message, and the CA root certificate.
You must store the password for the decryption key in the credential store, as described in "Configuring the Credential Store Provider". Use keystore.enc.csf.key as the key name.
You also have the option to override the keystore.sig.csf.key and keystore.enc.csf.key server-side configuration properties, as described in "Attaching Web Service Policies Permitting Overrides".
oracle/wss10_username_id_propagation_with_msg_protection_client_policy
This policy provides message-level protection (that is, integrity and confidentiality) and identity propagation for outbound SOAP requests in accordance with the WS-Security 1.0 standard.
This policy contains the following policy assertion: oracle/wss10_username_id_propagation_with_msg_protection_client_template. See "oracle/wss10_username_token_with_message_protection_client_template" for more information about the assertion.
How to Set Up the Web Service Client
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the Web service keystore, as described in "Setting up the Keystore for Message Protection".
The Web service's base64-encoded public certificate is published in the WSDL for use by the Web service client, as described in "Using Service Identity Certification Extension".
As an alternative, you can specify a value for keystore.recipient.alias on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy. The keystore recipient alias specifies the alias used to look up the public key in the keystore when retrieving a key for encryption of outbound SOAP messages.
You can specify a value for keystore.sig.csf.key and keystore.enc.csf.key on the Configurations page, or override them on a per-client basis using the Security Configuration Details control when you attach the policy.
How to Set Up the Web Service Client at Design Time
The client must include a WS-Security UsernameToken element (<wsse:UsernameToken/>) in the SOAP request message. The client provides a username and password for authentication.
This policy requires you to set up the Web service client keystore, as described in "Setting Up the Web Service Client Keystore at Design Time". The policy specifically requires that the client's and Web service's respective keystores already contain digital certificates containing each other's public key.
Configure the policy assertion for message signing, message encryption, or both.
See "Using Client Programmatic Configuration Overrides" for a description of the configuration settings you can override.
Example 10-1 shows the typical structure of a signature included in the Security header in conformance with the WS-Security 1.0 standards. In this example, the body element of the SOAP message is signed.
Example 10-2 is an example of the typical structure of encryption elements included in the Security header in conformance with the WS-Security 1.0 standards. In this example, the body element is encrypted.
oracle/wss10_username_id_propagation_with_msg_protection_service_policy
This policy enforces message level protection (that is, integrity and confidentiality) and identity propagation for inbound SOAP requests using mechanisms described in WS-Security 1.0.
This policy contains the following policy assertion: oracle/wss10_username_id_propagation_with_msg_protection_service_template. See "oracle/wss10_username_token_with_message_protection_service_template" for more information about the assertion.
Properties You Can Configure
See Table C-39. You also have the option to override the keystore.sig.csf.key and keystore.enc.csf.key server-side configuration properties, as described in "Attaching Web Service Policies Permitting Overrides".
How to Set Up WebLogic Server
Use the WebLogic Server Administration Console to add an Authentication provider to the active security realm for the WebLogic domain in which the Web service is deployed, as described in "Configuring an Authentication Provider in WebLogic Server".
The SAML login module extracts the username from the verified token and passes it (via the NameCallback) to the Authentication provider.
How to Set Up Oracle Platform Security Services (OPSS
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the keystore, as described in "Setting up the Keystore for Message Protection".
Store the trusted certificate that corresponds to the client's private key (used to sign the message) in the keystore. You also need to store the service's private key in the keystore for decrypting the message, and the CA root certificate.
You must store the password for the decryption key in the credential store, as described in "Configuring the Credential Store Provider". Use keystore.enc.csf.key as the key name.
You also have the option to override the keystore.sig.csf.key and keystore.enc.csf.key server-side configuration properties, as described in "Attaching Web Service Policies Permitting Overrides".
oracle/wss10_username_token_with_message_protection_client_policy
This policy provides message-level protection (message integrity and confidentiality) and authentication for outbound SOAP requests in accordance with the WS-Security 1.0 standard.
This policy contains the following policy assertion: oracle/wss10_username_token_with_message_protection_client_template. See "oracle/wss10_username_token_with_message_protection_client_template" for more information about the assertion.
How to Set Up the Web Service Client
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the Web service keystore, as described in "Setting up the Keystore for Message Protection".
The Web service's base64-encoded public certificate is published in the WSDL for use by the Web service client, as described in "Using Service Identity Certification Extension".
As an alternative, you can specify a value for keystore.recipient.alias on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy. The keystore recipient alias specifies the alias used to look up the public key in the keystore when retrieving a key for encryption of outbound SOAP messages.
You can specify a value for keystore.sig.csf.key and keystore.enc.csf.key on the Configurations page, or override them on a per-client basis using the Security Configuration Details control when you attach the policy.
You can specify a value for csf-key on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy.
The value signifies a key that maps to a username/password. See "Configuring the Credential Store Provider" for information on how to add the key to the credential store.
How to Set Up the Web Service Client at Design Time
Configure the policy assertion for message signing, message encryption, or both.
See "Using Client Programmatic Configuration Overrides" for a description of the configuration settings you can override.
This policy requires you to set up the Web service client keystore, as described in "Setting Up the Web Service Client Keystore at Design Time". The policy specifically requires that the client's and Web service's respective keystores already contain digital certificates containing each other's public key.
Example 10-1 shows the typical structure of a signature included in the Security header in conformance with the WS-Security 1.0 standards. In this example, the body element of the SOAP message is signed.
Example 10-2 is an example of the typical structure of encryption elements included in the Security header in conformance with the WS-Security 1.0 standards. In this example, the body element is encrypted.
oracle/wss10_username_token_with_message_protection_service_policy
This policy enforces message-level protection (message integrity and confidentiality) and authentication for inbound SOAP requests in accordance with the WS-Security 1.0 standard.
This policy contains the following policy assertion: oracle/wss10_username_token_with_message_protection_service_template. See "oracle/wss10_username_token_with_message_protection_service_template" for more information about the assertion.
Properties You Can Configure
See Table C-38. You also have the option to override the keystore.sig.csf.key and keystore.enc.csf.key server-side configuration properties, as described in "Attaching Web Service Policies Permitting Overrides".
How to Set Up WebLogic Server
Use the WebLogic Server Administration Console to add an Authentication provider to the active security realm for the WebLogic domain in which the Web service is deployed, as described in "Configuring an Authentication Provider in WebLogic Server".
How to Set Up Oracle Platform Security Services (OPSS)
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the keystore, as described in "Setting up the Keystore for Message Protection".
Store the trusted certificate that corresponds to the client's private key (used to sign the message) in the keystore. You also need to store the service's private key in the keystore for decrypting the message, and the CA root certificate.
You must store the password for the decryption key in the credential store, as described in "Configuring the Credential Store Provider". Use keystore.enc.csf.key as the key name.
You also have the option to override the keystore.sig.csf.key and keystore.enc.csf.key server-side configuration properties, as described in "Attaching Web Service Policies Permitting Overrides".
oracle/wss10_username_token_with_message_protection_ski_basic256_client_policy
This policy provides message-level protection (message integrity and confidentiality) and authentication for outbound SOAP requests in accordance with the WS-Security 1.0 standard.
This policy uses the Subject Key Identifier (ski) reference mechanism for the encryption key in the request, and for both the signature and encryption keys in the response.
This policy contains the following policy assertion: oracle/wss10_username_token_with_message_protection_client_template. See "oracle/wss10_username_token_with_message_protection_client_template" for more information about the assertion.
How to Set Up the Web Service Client
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the Web service keystore, as described in "Setting up the Keystore for Message Protection".
The Web service's base64-encoded public certificate is published in the WSDL for use by the Web service client, as described in "Using Service Identity Certification Extension".
As an alternative, you can specify a value for keystore.recipient.alias on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy. The keystore recipient alias specifies the alias used to look up the public key in the keystore when retrieving a key for encryption of outbound SOAP messages.
You can specify a value for keystore.sig.csf.key and keystore.enc.csf.key on the Configurations page, or override them on a per-client basis using the Security Configuration Details control when you attach the policy.
You can specify a value for csf-key on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy.
The value signifies a key that maps to a username/password. See "Configuring the Credential Store Provider" for information on how to add the key to the credential store.
How to Set Up the Web Service Client at Design Time
Configure the policy assertion for message signing, message encryption, or both.
See "Using Client Programmatic Configuration Overrides" for a description of the configuration settings you can override.
This policy requires you to set up the Web service client keystore, as described in "Setting Up the Web Service Client Keystore at Design Time". The policy specifically requires that the client's and Web service's respective keystores already contain digital certificates containing each other's public key.
Example 10-1 shows the typical structure of a signature included in the Security header in conformance with the WS-Security 1.0 standards. In this example, the body element of the SOAP message is signed.
Example 10-2 is an example of the typical structure of encryption elements included in the Security header in conformance with the WS-Security 1.0 standards. In this example, the body element is encrypted.
oracle/wss10_username_token_with_message_protection_ski_basic256_service_policy
This policy enforces message-level protection (message integrity and confidentiality) and authentication for inbound SOAP requests in accordance with the WS-Security 1.0 standard.
This policy uses the Subject Key Identifier (ski) reference mechanism for the encryption key in the request, and for both the signature and encryption keys in the response.
This policy contains the following policy assertion: oracle/wss10_username_token_with_message_protection_service_template. See "oracle/wss10_username_token_with_message_protection_service_template" for more information about the assertion.
Properties You Can Configure
See Table C-38. You also have the option to override the keystore.sig.csf.key and keystore.enc.csf.key server-side configuration properties, as described in "Attaching Web Service Policies Permitting Overrides".
How to Set Up WebLogic Server
Use the WebLogic Server Administration Console to add an Authentication provider to the active security realm for the WebLogic domain in which the Web service is deployed, as described in "Configuring an Authentication Provider in WebLogic Server".
How to Set Up Oracle Platform Security Services (OPSS)
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the keystore. When using the ski reference mechanism, use OpenSSL or another such utility to create the certificate.
Store the trusted certificate that corresponds to the client's private key (used to sign the message) in the keystore. You also need to store the service's private key in the keystore for decrypting the message, and the CA root certificate.
You must store the password for the decryption key in the credential store, as described in "Configuring the Credential Store Provider". Use keystore.enc.csf.key as the key name.
You also have the option to override the keystore.sig.csf.key and keystore.enc.csf.key server-side configuration properties, as described in "Attaching Web Service Policies Permitting Overrides".
oracle/wss10_x509_token_with_message_protection_client_policy
This policy provides message-level protection and certificate credential population for outbound SOAP requests in accordance with the WS-Security 1.0 standard.
This policy contains the following policy assertion: oracle/wss10_x509_token_with_message_protection_client_template. See "oracle/wss10_x509_token_with_message_protection_client_template" for more information about the assertion.
How to Set Up the Web Service Client
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the Web service keystore, as described in "Setting up the Keystore for Message Protection".
The Web service's base64-encoded public certificate is published in the WSDL for use by the Web service client, as described in "Using Service Identity Certification Extension".
As an alternative, you can specify a value for keystore.recipient.alias on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy. The keystore recipient alias specifies the alias used to look up the public key in the keystore when retrieving a key for encryption of outbound SOAP messages.
You can specify a value for keystore.sig.csf.key and keystore.enc.csf.key on the Configurations page, or override them on a per-client basis using the Security Configuration Details control when you attach the policy.
How to Set Up the Web Service Client at Design Time
The Web service client needs to provide valid X.509 authentication credentials in the SOAP message through the WS-Security binary security token.
This policy requires you to set up the Web service client keystore, as described in "Setting Up the Web Service Client Keystore at Design Time". The policy specifically requires that the client's and Web service's respective keystores already contain digital certificates containing each other's public key.
See "Using Client Programmatic Configuration Overrides" for a description of the configuration settings you can override.
Configure the policy assertion for message signing, message encryption, or both.
Example 10-1 shows the typical structure of a signature included in the Security header in conformance with the WS-Security 1.0 standards. In this example, the body element of the SOAP message is signed.
Example 10-2 is an example of the typical structure of encryption elements included in the Security header in conformance with the WS-Security 1.0 standards. In this example, the body element is encrypted.
oracle/wss10_x509_token_with_message_protection_service_policy
This policy enforces message-level protection and certificate-based authentication for inbound SOAP requests in accordance with the WS-Security 1.0 standard.
This policy contains the following policy assertion: oracle/wss10_x509_token_with_message_protection_service_template. See "oracle/wss10_x509_token_with_message_protection_service_template" for more information about the assertion.
Attributes You Can Configure
See Table C-41. You also have the option to override the keystore.sig.csf.key and keystore.enc.csf.key server-side configuration properties, as described in "Attaching Web Service Policies Permitting Overrides".
How to Set Up Oracle Platform Security Services (OPSS)
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the keystore, as described in "Setting up the Keystore for Message Protection".
Store the trusted certificate that corresponds to the client's private key (used to sign the message) in the keystore. You also need to store the service's private key in the keystore for decrypting the message, and the CA root certificate.
You must store the password for the decryption key in the credential store, as described in "Configuring the Credential Store Provider". Use keystore.enc.csf.key as the key name.
You also have the option to override the keystore.sig.csf.key and keystore.enc.csf.key server-side configuration properties, as described in "Attaching Web Service Policies Permitting Overrides".
You need to configure an Authentication provider, as described in "Configuring an Authentication Provider in WebLogic Server", and make sure that you provide the X.509 callback information for this provider.
oracle/wss11_kerberos_token_with_message_protection_client_policy
This policy includes a Kerberos token in the WS-Security header, and uses Kerberos keys to guarantee message integrity and confidentiality, in accordance with the WS-Security Kerberos Token Profile v1.1 standard.
This policy contains the following policy assertion: oracle/wss11_kerberos_token_with_message_protection_client_template. See "oracle/wss11_kerberos_token_with_message_protection_client_template" for more information about the assertion.
How to Set up the Web Service Client
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the Web service keystore, as described in "Setting up the Keystore for Message Protection".
You can specify a value for keystore.sig.csf.key and keystore.enc.csf.key on the Configurations page, or override them on a per-client basis using the Security Configuration Details control when you attach the policy.
Also see "Using Kerberos Tokens".
How to Set Up the Web Service Client at Design Time
This policy requires you to set up the Web service client keystore, as described in "Setting Up the Web Service Client Keystore at Design Time".
Also see "Using Kerberos Tokens".
See "Using Client Programmatic Configuration Overrides" for a description of the configuration settings you can override.
Configure the policy assertion for message signing, message encryption, or both.
Example 10-3 is an example of the typical structure of encryption elements included in the Security header in conformance with the WS-Security 1.1 standards. In this example, the body element is encrypted.
oracle/wss11_kerberos_token_with_message_protection_service_policy
This policy is enforced in accordance with the WS-Security Kerberos Token Profile v1.1 standard.
This policy contains the following policy assertion: oracle/wss11_kerberos_token_with_message_protection_service_template. See "oracle/wss11_kerberos_token_with_message_protection_service_template" for more information about the assertion.
Properties You Can Configure
See Table C-44. You also have the option to override the keystore.enc.csf.key server-side configuration property, as described in "Attaching Web Service Policies Permitting Overrides".
Configure the Login Module
Configure the krb5.loginmodule login module. See "Configuring the SAML and Kerberos Login Modules".
How to Set Up Oracle Platform Security Services (OPSS)
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the keystore, as described in "Setting up the Keystore for Message Protection".
Store the trusted certificate that corresponds to the client's private key (used to sign the message) in the keystore. You also need to store the service's private key in the keystore for decrypting the message, and the CA root certificate.
You must store the password for the decryption key in the credential store, as described in "Configuring the Credential Store Provider". Use keystore.enc.csf.key as the key name.
You also have the option to override the keystore.enc.csf.key server-side configuration property, as described in "Attaching Web Service Policies Permitting Overrides".
Configure Kerberos, as described in "Using Kerberos Tokens".
Use the WebLogic Server Administration Console to add an Authentication provider to the active security realm for the WebLogic domain in which the Web service is deployed, as described in "Configuring an Authentication Provider in WebLogic Server".
oracle/wss11_saml_token_with_message_protection_client_policy
This policy enables message level protection and SAML token population for outbound SOAP requests using mechanisms described in WS-Security 1.1.
This policy contains the following policy assertion: oracle/wss11_saml_token_with_message_protection_client_template. See "oracle/wss11_saml_token_with_message_protection_client_template" for more information about the assertion.
How to Set Up the Web Service Client
See "How to Configure SAML Web Service Client at Design Time".
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the Web service keystore, as described in "Setting up the Keystore for Message Protection".
The Web service's base64-encoded public certificate is published in the WSDL for use by the Web service client, as described in "Using Service Identity Certification Extension".
As an alternative, you can specify a value for keystore.recipient.alias on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy. The keystore recipient alias specifies the alias used to look up the public key in the keystore when retrieving a key for encryption of outbound SOAP messages.
You can specify a value for keystore.sig.csf.key and keystore.enc.csf.key on the Configurations page, or override them on a per-client basis using the Security Configuration Details control when you attach the policy.
You can specify a value for saml.issuer.name on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy. The saml.issuer.name property defaults to a value of www.oracle.com. See "Adding an Additional SAML Assertion Issuer Name" for additional considerations.
You can specify a value for user.roles.include on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy.
How to Set Up the Web Service Client at Design Time
See "How to Configure SAML Web Service Client at Design Time".
This policy requires you to set up the Web service client keystore, as described in "Setting Up the Web Service Client Keystore at Design Time". The policy specifically requires that the client's and Web service's respective keystores already contain digital certificates containing each other's public key.
See "Using Client Programmatic Configuration Overrides" for a description of the configuration settings you can override.
Configure the policy assertion for message signing, message encryption, or both.
Example 10-3 is an example of the typical structure of encryption elements included in the Security header in conformance with the WS-Security 1.1 standards. In this example, the body element is encrypted.
oracle/wss11_saml_token_identity_switch_with_message_protection_client_policy
This policy enables identity switching. Identity switching means that the policy propagates a different identity than the one based on the authenticated Subject. Instead of using the username from the Subject, this policy allows you to set a new user name when sending the SAML Web service request.
This policy enables message level protection and SAML token population for outbound SOAP requests using mechanisms described in WS-Security 1.1.
This policy contains the following policy assertion: oracle/wss11_saml_token_with_message_protection_client_template. See "oracle/wss11_saml_token_with_message_protection_client_template" for more information about the assertion.
How to Set Up the Web Service Client
You attach the wss11_saml_token_identity_switch_with_message_protection_client_policy to a Web service client of any type.
See "Configuring SAML Web Service Clients for Identity Switching" for information about how to use this policy. In particular, you need to "Set the javax.xml.ws.security.auth.username Property", and "Set the WSIdentityPermission Permission".
See "How to Configure SAML Web Service Client at Design Time" for additional SAML considerations.
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the Web service keystore, as described in "Setting up the Keystore for Message Protection".
The Web service's base64-encoded public certificate is published in the WSDL for use by the Web service client, as described in "Using Service Identity Certification Extension".
As an alternative, you can specify a value for keystore.recipient.alias on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy. The keystore recipient alias specifies the alias used to look up the public key in the keystore when retrieving a key for encryption of outbound SOAP messages.
You can specify a value for keystore.sig.csf.key and keystore.enc.csf.key on the Configurations page, or override them on a per-client basis using the Security Configuration Details control when you attach the policy.
You can specify a value for saml.issuer.name on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy. The saml.issuer.name property defaults to a value of www.oracle.com. See "Adding an Additional SAML Assertion Issuer Name" for additional considerations.
subject.precedence is set to false to allow for the use of a client-specified username rather than the authenticated subject.
You can specify a value for saml.audience.uri on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy.
You can specify a value for user.roles.include on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy.
How to Set Up the Web Service Client at Design Time
See "How to Configure SAML Web Service Client at Design Time".
This policy requires you to set up the Web service client keystore, as described in "Setting Up the Web Service Client Keystore at Design Time". The policy specifically requires that the client's and Web service's respective keystores already contain digital certificates containing each other's public key.
See "Using Client Programmatic Configuration Overrides" for a description of the configuration settings you can override.
Configure the policy assertion for message signing, message encryption, or both.
Example 10-3 is an example of the typical structure of encryption elements included in the Security header in conformance with the WS-Security 1.1 standards. In this example, the body element is encrypted.
oracle/wss11_saml_token_with_message_protection_service_policy
This policy enforces message-level integrity protection and SAML-based authentication for inbound SOAP requests in accordance with the WS-Security 1.0 standard.
This policy contains the following policy assertion: oracle/wss11_saml_token_with_message_protection_service_template. See "oracle/wss11_saml_token_with_message_protection_service_template" for more information about the assertion.
Properties You Can Configure
See Table C-46.
You also have the option to override the keystore.enc.csf.key server-side configuration property, as described in "Attaching Web Service Policies Permitting Overrides".
Configure the Login Module
Configure the saml.loginmodule login module. See "Configuring the SAML and Kerberos Login Modules".
How to Set Up Oracle Platform Security Services (OPSS)
See "Configuring SAML".
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the keystore, as described in "Setting up the Keystore for Message Protection".
Store the trusted certificate that corresponds to the client's private key (used to sign the message) in the keystore. You also need to store the service's private key in the keystore for decrypting the message, and the CA root certificate.
You must store the password for the decryption key in the credential store, as described in "Configuring the Credential Store Provider". Use keystore.enc.csf.key as the key name.
You also have the option to override the keystore.enc.csf.key server-side configuration property, as described in "Attaching Web Service Policies Permitting Overrides".
Use the WebLogic Server Administration Console to add an Authentication provider to the active security realm for the WebLogic domain in which the Web service is deployed, as described in "Configuring an Authentication Provider in WebLogic Server".
The SAML login module extracts the username from the verified token and passes it (via the NameCallback) to the Authentication provider.
oracle/wss11_username_token_with_message_protection_client_policy
This policy provides message-level protection and authentication for outbound SOAP requests in accordance with the WS-Security 1.1 standard.
This policy contains the following policy assertion: oracle/wss11_username_token_with_message_protection_client_template. See "oracle/wss11_username_token_with_message_protection_client_template" for more information about the assertion.
How to Set Up the Web Service Client
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the Web service keystore, as described in "Setting up the Keystore for Message Protection".
The Web service's base64-encoded public certificate is published in the WSDL for use by the Web service client, as described in "Using Service Identity Certification Extension".
As an alternative, you can specify a value for keystore.recipient.alias on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy. The keystore recipient alias specifies the alias used to look up the public key in the keystore when retrieving a key for encryption of outbound SOAP messages.
You can specify a value for keystore.enc.csf.key on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy.
How to Set Up the Web Service Client at Design Time
This policy uses symmetric key technology, which is an encryption method that uses the same shared key to encrypt and decrypt data. The symmetric key is used to sign the message.
Configure the policy assertion for message signing, message encryption, or both.
See "Using Client Programmatic Configuration Overrides" for a description of the configuration settings you can override.
Example 10-3 is an example of the typical structure of encryption elements included in the Security header in conformance with the WS-Security 1.1 standards. In this example, the body element is encrypted.
oracle/wss11_username_token_with_message_protection_service_policy
This policy enforces message-level protection (that is, message integrity and message confidentiality) and authentication for inbound SOAP requests in accordance with the WS-Security 1.1 standard.
This policy contains the following policy assertion: oracle/wss11_username_token_with_message_protection_service_template. See "oracle/wss11_username_token_with_message_protection_service_template" for more information about the assertion.
Properties You Can Configure
See Table C-50. You also have the option to override the keystore.enc.csf.key server-side configuration property, as described in "Attaching Web Service Policies Permitting Overrides".
How to Set Up Oracle Platform Security Services (OPSS)
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the keystore, as described in "Setting up the Keystore for Message Protection".
Store the trusted certificate that corresponds to the client's private key (used to sign the message) in the keystore. You also need to store the service's private key in the keystore for decrypting the message, and the CA root certificate.
You must store the password for the decryption key in the credential store, as described in "Configuring the Credential Store Provider". Use keystore.enc.csf.key as the key name.
You also have the option to override the keystore.enc.csf.key server-side configuration property, as described in "Attaching Web Service Policies Permitting Overrides".
Use the WebLogic Server Administration Console to add an Authentication provider to the active security realm for the WebLogic domain in which the Web service is deployed, as described in "Configuring an Authentication Provider in WebLogic Server".
oracle/wss11_x509_token_with_message_protection_client_policy
This policy provides message-level protection and certificate-based authentication for outbound SOAP requests in accordance with the WS-Security 1.1 standard.
This policy contains the following policy assertion: oracle/wss11_x509_token_with_message_protection_client_template. See "oracle/wss11_x509_token_with_message_protection_client_template" for more information about the assertion.
How to Set Up the Web Service Client
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the Web service keystore, as described in "Setting up the Keystore for Message Protection".
The Web service's base64-encoded public certificate is published in the WSDL for use by the Web service client, as described in "Using Service Identity Certification Extension".
As an alternative, you can specify a value for keystore.recipient.alias on the Configurations page, or override it on a per-client basis using the Security Configuration Details control when you attach the policy. The keystore recipient alias specifies the alias used to look up the public key in the keystore when retrieving a key for encryption of outbound SOAP messages.
You can specify a value for keystore.sig.csf.key and keystore.enc.csf.key on the Configurations page, or override them on a per-client basis using the Security Configuration Details control when you attach the policy.
How to Set Up the Web Service Client at Design Time
This policy requires you to set up the Web service client keystore, as described in "Setting Up the Web Service Client Keystore at Design Time". The policy specifically requires that the client's and Web service's respective keystores already contain digital certificates containing each other's public key.
The Web service client needs to provide valid X.509 authentication credentials in the SOAP message through the WS-Security binary security token.
See "Using Client Programmatic Configuration Overrides" for a description of the configuration settings you can override.
Configure the policy assertion for message signing, message encryption, or both.
Example 10-3 is an example of the typical structure of encryption elements included in the Security header in conformance with the WS-Security 1.1 standards. In this example, the body element is encrypted.
oracle/wss11_x509_token_with_message_protection_service_policy
This policy enforces message-level protection and certificate-based authentication for inbound SOAP requests in accordance with the WS-Security 1.1 standard.
This policy contains the following policy assertion: oracle/wss11_x509_token_with_message_protection_service_template. See "oracle/wss11_x509_token_with_message_protection_service_template" for more information about the assertion.
Properties You Can Configure
See Table C-53. You also have the option to override the keystore.enc.csf.key server-side configuration property, as described in "Attaching Web Service Policies Permitting Overrides".
How to Set Up Oracle Platform Security Services (OPSS)
Configure the policy assertion for message signing, message encryption, or both.
This policy requires you to set up the keystore, as described in "Setting up the Keystore for Message Protection".
Store the trusted certificate that corresponds to the client's private key (used to sign the message) in the keystore. You also need to store the service's private key in the keystore for decrypting the message, and the CA root certificate.
You must store the password for the decryption key in the credential store, as described in "Configuring the Credential Store Provider". Use keystore.enc.csf.key as the key name.
You also have the option to override the keystore.enc.csf.key server-side configuration property, as described in "Attaching Web Service Policies Permitting Overrides".
You need to configure the Authentication provider, as described in "Configuring an Authentication Provider in WebLogic Server", and make sure that you provide the X.509 callback information for this provider.
Authorization Policies and Configuration Steps
Frequently, authentication is the first step of determining whether a user should be given access to a Web service. After the user is authenticated, the second step is to verify that the user is authorized to access the Web service. This is accomplished using an authorization policy. You can create an authorization policy using the binding_authorization_template or the component_authorization_template assertion templates.
Policies created with these templates perform role- or permission-based access control (RBAC) and check that the authenticated user has been granted one of the roles or permissions allowed access to the Web service.
Predefined Policies summarizes the security policies that enforce authorization, and indicates whether the policy is enforced at the transport layer or SOAP header.
Note:
The authorization polices can follow any authentication policy where the subject is established.You cannot attach both a permitall and denyall policy to the same Web service.
Determining Which Resources to Protect
The authorization policies provide the following properties that you can use to specify which resources you want the policy to protect. Not all of the predefined policies feature all of the properties.
-
Constraint Pattern -- Reserved for future use.
-
Action Pattern -- The Web service operation for which permission-based checks are performed. This value can be a comma-separated list of values. This field accepts wildcards. * means all Web service operations.
The valid values for Action Pattern are determined by the Web service methods. For example, if the Web service method is validate(amountAvailable), enter the Action Pattern as validate.
-
Resource Pattern -- The name of the resource for which permission-based checks are performed. This field accepts wildcards, and the default is * for all resources in the Web services protected by the policy.
By convention you enter the Resource Pattern as (namespace of Web service + Web service name).
For example, if the namespace of the Web service is http://project11 and the Web service name is CreditValidation, you would enter the Resource Name as http://project11/CreditValidation.
If you specify a specific Resource Pattern, the policy is enforced only for those Web services that match the criteria. That is, entering a specific Resource Pattern limits the scope of the authorization policy. This condition also applies if you have bulk-attached this authorization policy to multiple subjects. The default of * protects all resources (namespace of Web service + Web service name) of the bulk-attached Web services.
-
Permission Check Class -- By default, it is oracle.wsm.security.WSFunctionPermission. The class must be in the classpath.
-
Authorization Setting -- Possible values are Permit All, Deny All, and Selected Roles. If you choose Selected Roles, you must then select from the enterprise (Global) roles defined in WebLogic Server, which may include the following:
-
AdminChannelUser
-
Anonymous
-
AppTester
-
CrossDomainConnector
-
Deployer
-
Monitor
-
Operator
-
OracleSystemRole
-
How Authorization Permissions Are Determined
Conceptually, determining whether an authenticated subject is authorized to access a particular resource protected by a Web service policy has two parts that work in tandem.
-
The Resource Pattern and Action Pattern parameters on the Policy Settings page for the policy determine what resources are being protected by the policy, as shown in Figure 10-2. (You can also override these properties, as described in "Configuring Server-Side Override Properties for Authorization Policies".)
You have the option to change the Permission Check Class configuration property for the policy, which identifies the permission class as per JAAS standards. The permission class must be available in the application or server classpath.
The custom permission class must extend the abstract Permission class and implement the Serializable interface. See the Javadoc at
http://java.sun.com/j2se/1.5.0/docs/api/java/security/Permission.html. The default is oracle.wsm.security.WSFunctionPermission.Figure 10-2 The Permission Settings for a Policy
Description of "Figure 10-2 The Permission Settings for a Policy"
-
The OPSS Application Policies page specifies whether the authenticated subject has invoke access to the Resource Name listed there, as shown in Figure 10-3.
Figure 10-3 Adding a Permission on the OPSS Create Application Grant Page
Description of "Figure 10-3 Adding a Permission on the OPSS Create Application Grant Page"
OPSS uses the Policy Settings page for the Web service to determine which resources require an authorization check. Then, access to the resource is allowed if the authenticated subject has been granted WSFunctionPermission (or other permission) for that resource via OPSS.
Note:
If you changed the Permission Check Class configuration property for the policy to a custom class, use the custom class here as well.Consider further the example shown in Figure 10-2 and Figure 10-3.
On the Policy Settings page, assume that you specify the following to protect the validate method of the http://project11/CreditValidation Web service:
Action pattern: validate Resource pattern: http://project11/CreditValidation Permission Check Class oracle.wsm.security.WSFunctionPermission
Then, on the OPSS Application Policies page, you would use http://project11/CreditValidation#validate for the Resource Name to specify that the authenticated subject has permission to invoke this resource:
Permission Class: oracle.wsm.security.WSFunctionPermission Resource Name: http://project11/CreditValidation#validate Permissions Action: invoke
You can grant the WSFunctionPermission permission to a user, a group, or an application role. If you grant WSFunctionPermission to a user or group it will apply to all applications that are deployed in the domain.
OPSS Resource Name Can Include Operation Name
In previous releases of Fusion Middleware Control, the Resource Name on the OPSS Application Policies page was determined by name-space-of-webservice/ServiceName. For example, if the name space of a Web service was http://project1/ and the service name was CreditValidation, the Resource Name would have been http://project1/CreditValidation. You could also use an asterisk (*) wildcard for providing permission to all the actions or all resources.
In this release, the resource target of the WSFunctionPermission is enhanced to include the actual Web service operation name. The syntax for the Resource Name is now name-space-of-webservice/servicename#[operation name]. (For a component it is compositename/componentname#[operation name].)]
You must now include at least the name-space-of-webservice/service name. That is, you can no longer use an asterisk (*) wildcard for providing permission to all the actions or all resources.
Instead, to specify all operations for a Web service, simply leave the operation name blank. For example, name-space-of-webservice/servicename#
Permission Action is always invoke.
oracle/binding_authorization_denyall_policy
This policy provides a simple role-based authorization policy based on the authenticated subject.
This policy denies all users with any role.
This policy should follow an authentication policy where the subject is established and can be attached to any SOAP-based endpoint.
You must have already configured a WebLogic Authentication provider, as described in "Configure Authentication Providers" in the Oracle WebLogic Server Administration Console Help.
This policy contains the following policy assertion: oracle/binding_authorization_template
See "oracle/binding_authorization_template" for more information about the assertion.
Settings You Can Change
See Table C-55.
To add roles:
-
Click Add.
-
To add roles, click the checkbox next to each role you want to add in the Roles Available column and click Move. To add all roles, click Move All.
To remove roles, click the checkbox next to each role you want to remove in the Roles Selected to Add column, and click Remove. To remove all roles, click Remove All.
To search for roles, enter a search string in the Role Name search box and click the go arrow. The Roles Available column is updated to include only those roles that match the search string.
-
Click OK.
To delete roles:
-
Select the role that you want to delete in the Selected Roles list.
-
Click Delete.
How to Set Up Oracle Platform Security Services (OPSS)
If you specify one or more of the WebLogic Server enterprise roles, the authenticated subject must already have that role. You use the WebLogic Server Administration Console to grant a role to a user or group, as described in the Oracle WebLogic Server Administration Console Help.
You must configure a WebLogic Authentication provider, as described in "Configure Authentication Providers" in the Oracle WebLogic Server Administration Console Help.
oracle/binding_authorization_permitall_policy
This policy provides a simple role-based authorization policy based on the authenticated subject.
This policy permits all users with any roles.
This policy should follow an authentication policy where the subject is established and can be attached to any SOAP-based endpoint.
You must have already configured a WebLogic Authentication provider, as described in "Configure Authentication Providers" in the Oracle WebLogic Server Administration Console Help.
This policy contains the following policy assertion: oracle/binding_authorization_template. See "oracle/binding_authorization_template" for more information about the assertion.
Settings You Can Change
See Table C-55.
To add roles:
-
Click Add.
-
To add roles, click the checkbox next to each role you want to add in the Roles Available column and click Move. To add all roles, click Move All.
To remove roles, click the checkbox next to each role you want to remove in the Roles Selected to Add column, and click Remove. To remove all roles, click Remove All.
To search for roles, enter a search string in the Role Name search box and click the go arrow. The Roles Available column is updated to include only those roles that match the search string.
-
Click OK.
To delete roles:
-
Select the role that you want to delete in the Selected Roles list.
-
Click Delete.
How to Set Up Oracle Platform Security Services (OPSS)
If you specify one or more of the WebLogic Server enterprise roles, the authenticated subject must already have that role. You use the WebLogic Server Administration Console to grant a role to a user or group, as described in the Oracle WebLogic Server Administration Console Help.
You must configure a WebLogic Authentication provider, as described in "Configure Authentication providers" in the Oracle WebLogic Server Administration Console Help.
oracle/binding_permission_authorization_policy
This policy provides a permission-based authorization policy based on the authenticated subject.
This policy ensures that the subject has permission to perform the operation. To do this, the Authorization Policy executor leverages OPSS to check if the authenticated subject has been granted oracle.wsm.security.WSFunctionPermission (or whatever permission class is specified in Permission Check Class) using the Resource Pattern and Action Pattern as parameters.
This policy should follow an authentication policy where the subject is established and can be attached to any SOAP-based endpoint.
This policy contains the following policy assertion: oracle/binding_permission_authorization_template. See "oracle/binding_permission_authorization_template" for more information about the assertion.
Attributes You Can Configure
You have the option to change the permission_class configuration property for the policy, which identifies the permission class as per JAAS standards. The permission class must be available in the application or server classpath.
The custom permission class must extend the abstract Permission class and implement the Serializable interface. See the Javadoc at http://java.sun.com/j2se/1.5.0/docs/api/java/security/Permission.html.
The default is oracle.wsm.security.WSFunctionPermission.
How to Set Up Oracle Platform Security Services (OPSS)
Use Fusion Middleware Control to grant the WSFunctionPermission (or other) permission to the user, group, or application that will attempt to authenticate to the Web service.
You have the option to change the permission_class configuration property for the policy, which identifies the permission class as per JAAS standards. The class must be available in the server classpath. The default is oracle.wsm.security.WSFunctionPermission.
You must configure a WebLogic Authentication provider, as described in "Configure Authentication Providers" in the Oracle WebLogic Server Administration Console Help.
oracle/component_authorization_denyall_policy
This policy provides a simple role-based authorization policy based on the authenticated subject.
This policy denies all users with any roles.
You must have already configured a WebLogic Authentication provider, as described in "Configure Authentication providers" in the Oracle WebLogic Server Administration Console Help.
This policy should follow an authentication policy where the subject is established and can be attached to any SCA-based endpoint.
This policy contains the following policy assertion: oracle/component_authorization_template. See "oracle/component_authorization_template" for more information about the assertion.
Settings You Can Change
See Table C-57.
To add roles:
-
Click Add.
-
To add roles, click the checkbox next to each role you want to add in the Roles Available column and click Move. To add all roles, click Move All.
To remove roles, click the checkbox next to each role you want to remove in the Roles Selected to Add column, and click Remove. To remove all roles, click Remove All.
To search for roles, enter a search string in the Role Name search box and click the go arrow. The Roles Available column is updated to include only those roles that match the search string.
-
Click OK.
To delete roles:
-
Select the role that you want to delete in the Selected Roles list.
-
Click Delete.
How to Set Up Oracle Platform Security Services (OPSS)
If you specify one or more of the WebLogic Server enterprise roles, the authenticated subject must already have that role. You use the WebLogic Server Administration Console to grant a role to a user or group, as described in the Oracle WebLogic Server Administration Console Help.
You must configure a WebLogic Authentication provider, as described in "Configure Authentication providers" in the Oracle WebLogic Server Administration Console Help.
oracle/component_authorization_permitall_policy
This policy provides a simple role-based authorization policy based on the authenticated subject.
This policy permits all users with any roles.
You must have already configured a WebLogic Authentication provider, as described in "Configure Authentication providers" in the Oracle WebLogic Server Administration Console Help.
It should follow an authentication policy where the subject is established and can be attached to any SCA-based endpoint.
This policy contains the following policy assertion: oracle/component_authorization_template. See "oracle/component_authorization_template" for more information about the assertion.
Settings You Can Change
See Table C-57.
To add roles:
-
Click Add.
-
To add roles, click the checkbox next to each role you want to add in the Roles Available column and click Move. To add all roles, click Move All.
To remove roles, click the checkbox next to each role you want to remove in the Roles Selected to Add column, and click Remove. To remove all roles, click Remove All.
To search for roles, enter a search string in the Role Name search box and click the go arrow. The Roles Available column is updated to include only those roles that match the search string.
-
Click OK.
To delete roles:
-
Select the role that you want to delete in the Selected Roles list.
-
Click Delete.
How to Set Up Oracle Platform Security Services (OPSS)
If you specify one or more of the WebLogic Server enterprise roles, the authenticated subject must already have that role. You use the WebLogic Server Administration Console to grant a role to a user or group, as described in the Oracle WebLogic Server Administration Console Help.
You must configure a WebLogic Authentication provider, as described in "Configure Authentication providers" in the Oracle WebLogic Server Administration Console Help.
oracle/component_permission_authorization_policy
This policy provides a permission-based authorization policy based on the authenticated subject.
This policy ensures that the subject has permission to perform the operation. To do this, the Authorization Policy executor leverages OPSS to check if the authenticated subject has been granted oracle.wsm.security.WSFunctionPermission (or whatever permission class is specified in Permission Check Class) using the Resource Pattern and Action Pattern as parameters. Resource Pattern and Action Pattern are used to identify if the authorization assertion is to be enforced for this particular request. Access is allowed if the authenticated subject has been granted WSFunctionPermission.
You can grant the WSFunctionPermission permission to a user, a group, or an application role. If you grant WSFunctionPermission to a user or group it will apply to all applications that are deployed in the domain.
This policy should follow an authentication policy where the subject is established and can be attached to any SCA-based endpoint.
This policy contains the following policy assertion: oracle/component_permission_authorization_template. See "oracle/component_permission_authorization_template" for more information about the assertion.
How to Set Up Oracle Platform Security Services (OPSS)
Use Fusion Middleware Control to grant the WSFunctionPermission permission to the user, group, or application that will attempt to authenticate to the Web service.
You must configure a WebLogic Authentication provider, as described in "Configure Authentication providers" in the Oracle WebLogic Server Administration Console Help.
WS-Addressing Policies and Configuration Steps
The Web Services Addressing (WS-Addressing) specification (http://www.w3.org/TR/ws-addr-core/) provides transport-neutral mechanisms to address Web services and messages. In particular, the specification defines a number of XML elements used to identify Web service endpoints and to secure end-to-end endpoint identification in messages.
This section describes the predefined WS-Addressing policies.
oracle/wsaddr_policy
This policy causes the platform to check inbound messages for the presence of WS-Addressing headers conforming to the W3C 2005 Final WS-Addressing Policy standard. In addition, it causes the platform to include a WS-Addressing header in outbound SOAP messages.
How to Set Up the Web Service Client at Design Time
Configure WS-Addressing for the Web service client as described in the Web Services Addressing 1.0 - SOAP Binding specification (http://www.w3.org/TR/ws-addr-soap/).
MTOM Attachment Policies and Configuration Steps
This section describes the predefined MTOM policies.
oracle/wsmtom_policy
SOAP Message Transmission Optimization Mechanism/XML-binary Optimized Packaging (MTOM/XOP) defines a method for optimizing the transmission of XML data of type xs:base64Binary or xs:hexBinary in SOAP messages.
The Message Transmission Optimization Mechanism (MTOM) policy rejects inbound messages that are not in MTOM format and verifies that outbound messages are in MTOM format.
MTOM refers to specifications http://www.w3.org/TR/2005/REC-soap12-mtom-20050125 and http://www.w3.org/Submission/2006/SUBM-soap11mtom10-20060405 for SOAP 1.2 and SOAP 1.1 bindings, respectively.
How to Set Up the Web Service Client at Design Time
To enable MTOM on the client of the Web service, pass the javax.xml.ws.soap.MTOMFeature as a parameter when creating the Web service proxy or dispatch, as illustrated in the following example.
package examples.webservices.mtom.client;
import javax.xml.ws.soap.MTOMFeature;
public class Main {
public static void main(String[] args) {
String FOO = "FOO";
MtomService service = new MtomService()
MtomPortType port = service.getMtomPortTypePort(new MTOMFeature());
String result = null;
result = port.echoBinaryAsString(FOO.getBytes());
System.out.println( "Got result: " + result );
}
}
Reliable Messaging Policies and Configuration Steps
WS-ReliableMessaging makes message exchanges reliable. It ensures that messages are delivered reliably between distributed applications regardless of software component, system, or network failures. Ordered delivery is assured and automatic retransmission of failed messages does not have to be coded by each client application.
Consider using reliable messaging if your Web service is experiencing the following problems:
-
network failures or dropped connections
-
messages are lost in transit
-
messages are arriving at their destination out of order
WS-ReliableMessaging considers the source and destination of a message to be independent of the client/server model. That is, the client and the server can each act simultaneously as both a message source and destination on the communications path.
This section describes the predefined Reliable Messaging policies.
WS-RM Policy Properties
Table 10-1 lists the properties that you can set for the WS-RM policies.
Table 10-1 WS-RM Policy Properties
| Property Name | Description | Default Value Used by Policy | Possible Values |
|---|---|---|---|
|
DeliveryAssurance |
Delivery assurance. The following defines the delivery assurance types:
|
InOrder |
InOrder AtLeastOnce AtLeastOnceInOrder ExactlyOnce ExactlyOnceInOrder AtMostOnce AtMostOnceInOrder |
|
StoreType |
Type of message store. |
InMemory |
InMemory FileSystem (not fully supported) JDBC |
|
StoreName |
Name of the message store. |
oracle |
String value |
|
jdbc-connection-name |
JNDI reference to a JDBC data source. This field is valid only if StoreType is set to JDBC. This value takes precedence over jdbc-connection-url. The username and password will be used if both are present. |
jdbc/MessagesStore |
Valid JDBC store |
|
InactivityTimeout |
Amount of time, in milliseconds, that can elapse between message exchanges associated with a particular WS-ReliableMessaging sequence. Once this value is reached, the sequence will be terminated and discarded automatically. |
600000 |
The amount of time in milliseconds. |
|
BaseRetransmissionInterval |
Interval, in milliseconds, that the source endpoint waits after transmitting a message and before it retransmits the message if it receives no acknowledgment for that message. |
3000 |
The amount of time in milliseconds. |
oracle/wsrm10_policy
This policy provides support for version 1.0 of the Web Services Reliable Messaging protocol. This policy can be attached to any SOAP-based client or endpoint.
How to Set Up the Web Service Client
The Web service client will automatically detect the WSDL policy assertions at runtime and use them to enable the advertised version of WS-RM on the client.
How to Set Up the Web Service Client at Design Time
For multi-message sequences, the client code must include explicit invocations of methods for delimiting sequence boundaries. Otherwise, every message is wrapped in its own sequence
Edit the client to enable a reliable messaging session for the messages sent to the service. The oracle.webservices.rm.client.RMSessionLifecycle interface provides the client with a mechanism for demarcating WS-RM sequence boundaries.
Example 10-4 illustrates sample WS-RM client code. In the code, a new TestService is created. The TestPort, through which the client will communicate with the service, is retrieved. The port object is cast to a RMSessionLifecycle object and a reliable messaging session is opened on it (openSession). After the messages are sent to the service, the session is closed (closeSession).
Example 10-4 Sample WS-Rm Client Code
public class ClientServlet extends HttpServlet {
public void doGet(HttpServletRequest request,
HttpServletResponse response) throws ServletException,
IOException {
int num1 = Integer.parseInt(request.getParameter("num1"));
int num2 = Integer.parseInt(request.getParameter("num2"));
String outputStr = null;
TestService service = new TestService();
Test port = service.getTestPort();
try {
((RMSessionLifecycle) port).openSession();
outputStr = port.hello(inputStr);
} catch (Exception e) {
e.printStackTrace();
outputStr = e.getMessage();
} finally {
((RMSessionLifecycle) port).closeSession();
response.getOutputStream().write(outputStr.getBytes());
}
}
}
oracle/wsrm11_policy
This policy provides support for version 1.1 of the Web Services Reliable Messaging protocol. This policy can be attached to any SOAP-based client or endpoint.
How to Set Up the Web Service Client
The Web service client will automatically detect the WSDL policy assertions at runtime and use them to enable the advertised version of WS-RM on the client.
How to Set Up the Web Service Client at Design Time
For multi-message sequences, the client code must include explicit invocations of methods for delimiting sequence boundaries. Otherwise, every message is wrapped in its own sequence
Edit the client to enable a reliable messaging session for the messages sent to the service. The oracle.webservices.rm.client.RMSessionLifecycle interface provides the client with a mechanism for demarcating WS-RM sequence boundaries.
Example 10-4 illustrates a servlet client. In the code, a new TestService is created. The TestPort, through which the client will communicate with the service, is retrieved. The port object is cast to a RMSessionLifecycle object and a reliable messaging session is opened on it (openSession). After the messages are sent to the service, the session is closed (closeSession).
Management Policies and Configuration Steps
This section describes the predefined Management policies.
oracle/log_policy
This policy causes the request, response, and fault messages to be sent to a message log.
This policy contains the following policy assertion: oracle/log_template. See "oracle/security_log_template" for more information about the assertion.
How to Set Up the Web Service or Client
Determine whether you want to log messages for the request and response, based on the following categories:
-
all
-
header
-
SOAP body
-
SOAP envelope
How to Set Up Oracle Platform Security Services (OPSS)
Messages are logged to the message log for the domain.
-
In the navigator pane, expand WebLogic Domain to show the domain for which you want to see the logged messages. Select the domain.
-
Using Fusion Middleware Control, click WebLogic Domain, then Logs and then View Log Messages.
Attaching Policy Files to Web Services and Clients
There are two ways to attach policies to Web service clients and Web services: at the client and service design time, and post deployment.
Post-deployment, you attach security and management policies to SOA composites, ADF, and WebCenter applications using the Oracle Enterprise Manager Fusion Middleware Control. This method provides the most power and flexibility because it moves Web service security to the control of the security administrator.
At design time, Oracle JDeveloper automates ADF and SOA client policy attachment. Or, you can attach Oracle WSM security and management policies to applications programmatically. You typically do this using your favorite IDE, such as Oracle JDeveloper.
Either way, the client-side policy must be the equivalent of the one associated with the Web service. If the two files are different, and there is a conflict in the assertions contained in the files, then the invoke of the Web service operation returns an error.
For example, if the oracle/wss_http_token_over_ssl_service_policy policy requires mutual authentication, the client policy must also be set for mutual authentication.
For the predefined policies, both client and Web service policies are included. If you create a new policy, generating the policy as described in "Creating Web Service Policies" increases the likelihood that the client policy will work with the service policy.
Using Client Programmatic Configuration Overrides
"Attaching Client Policies Permitting Overrides" describes the policy configuration override feature that allows you to specify certain Web service client configuration information when you attach a policy. However, you can also override this configuration information programmatically at design time. This section describes client programmatic overrides.
Table 10-2 shows the properties you can set via programmatic configuration overrides for a given policy. Example 10-5 shows an example of setting these properties from a program.
Table 10-2 Properties Set Via Programmatic Configuration Overrides
| Property List | Description | Applies to These Policies |
|---|---|---|
|
oracle.wsm.security.util.SecurityConstants.ClientConstants.WSS_CSF_KEY |
Gets the username and password corresponding to the csf-key specified in the credential store if the credential store is available to the client. Instead of using this property, you can also explicitly set the username and password as shown in Example 10-5 |
oracle/wss10_username_token_with_message_protection_client_policy oracle/wss10_username_token_with_message_protection_ski_basic256_client_policy oracle/wss11_username_token_with_message_protection_client_policy oracle/wss_username_token_client_policy oracle/wss_username_token_over_ssl_client_policy oracle/wss_username_token_with_digestpassword_client_policy oracle/wss10_username_id_propagation_with_msg_protection_client_policy oracle/wss_http_token_client_policy oracle/wss_http_token_over_ssl_client_policy |
|
oracle.wsm.security.util.SecurityConstants.ClientConstants.WSS_KEYSTORE_LOCATION |
This property sets the location of the keystore file. If provided, this value will override any statically configured value. Type: java.lang.String |
oracle/wss10_message_protection_client_policy oracle/wss10_saml_hok_token_with_message_protection_client_policy oracle/wss10_saml_token_with_message_integrity_client_policy oracle/wss10_saml_token_with_message_protection_client_policy oracle/wss10_saml_token_with_message_protection_ski_basic256_client_policy oracle/wss10_username_token_with_message_protection_client_policy oracle/wss10_username_token_with_message_protection_ski_basic256_client_policy oracle/wss10_x509_token_with_message_protection_client_policy oracle/wss11_kerberos_token_with_message_protection_client_policy oracle/wss11_message_protection_client_policy oracle/wss11_saml_token_with_message_protection_client_policy oracle/wss11_username_token_with_message_protection_client_policy oracle/wss11_x509_token_with_message_protection_client_policy |
|
oracle.wsm.security.util.SecurityConstants.ClientConstants.WSS_KEYSTORE_TYPE |
This property sets the type of keystore file. If provided, this value will override any statically configured value. Type: java.lang.String Default is JKS. |
oracle/wss10_message_protection_client_policy oracle/wss10_saml_hok_token_with_message_protection_client_policy oracle/wss10_saml_token_with_message_integrity_client_policy oracle/wss10_saml_token_with_message_protection_client_policy oracle/wss10_saml_token_with_message_protection_ski_basic256_client_policy oracle/wss10_username_token_with_message_protection_client_policy oracle/wss10_username_token_with_message_protection_ski_basic256_client_policy oracle/wss10_x509_token_with_message_protection_client_policy oracle/wss11_kerberos_token_with_message_protection_client_policy oracle/wss11_message_protection_client_policy oracle/wss11_saml_token_with_message_protection_client_policy oracle/wss11_username_token_with_message_protection_client_policy oracle/wss11_x509_token_with_message_protection_client_policy |
|
oracle.wsm.security.util.SecurityConstants.ClientConstants.WSS_KEYSTORE_PASSWORD |
This property sets the password of the keystore file. If provided, this value will override any statically configured value. Type: java.lang.String |
oracle/wss10_message_protection_client_policy oracle/wss10_saml_hok_token_with_message_protection_client_policy oracle/wss10_saml_token_with_message_integrity_client_policy oracle/wss10_saml_token_with_message_protection_client_policy oracle/wss10_saml_token_with_message_protection_ski_basic256_client_policy oracle/wss10_username_token_with_message_protection_client_policy oracle/wss10_username_token_with_message_protection_ski_basic256_client_policy oracle/wss10_x509_token_with_message_protection_client_policy oracle/wss11_kerberos_token_with_message_protection_client_policy oracle/wss11_message_protection_client_policy oracle/wss11_saml_token_with_message_protection_client_policy oracle/wss11_username_token_with_message_protection_client_policy oracle/wss11_x509_token_with_message_protection_client_policy |
|
oracle.wsm.security.util.SecurityConstants.ClientConstants.WSS_SIG_KEY_ALIAS |
This property sets the alias of the key within the keystore that will be used for digital signatures. If provided, this value will override any statically configured value. Type: java.lang.String For WSS11 policies, this property is used only in the case of mutual authentication. |
oracle/wss10_message_protection_client_policy oracle/wss10_saml_hok_token_with_message_protection_client_policy oracle/wss10_saml_token_with_message_integrity_client_policy oracle/wss10_saml_token_with_message_protection_client_policy oracle/wss10_saml_token_with_message_protection_ski_basic256_client_policy oracle/wss10_username_token_with_message_protection_client_policy oracle/wss10_username_token_with_message_protection_ski_basic256_client_policy oracle/wss10_x509_token_with_message_protection_client_policy oracle/wss11_kerberos_token_with_message_protection_client_policy oracle/wss11_message_protection_client_policy oracle/wss11_saml_token_with_message_protection_client_policy oracle/wss11_username_token_with_message_protection_client_policy oracle/wss11_x509_token_with_message_protection_client_policy |
|
oracle.wsm.security.util.SecurityConstants.ClientConstants.WSS_SIG_KEY_PASSWORD |
This property sets the password for the alias of the key within the keystore that will be used for digital signatures. If provided, this value will override any statically configured value. Type: java.lang.String For WSS11 policies, this property is used only in the case of mutual authentication. |
oracle/wss10_message_protection_client_policy oracle/wss10_saml_hok_token_with_message_protection_client_policy oracle/wss10_saml_token_with_message_integrity_client_policy oracle/wss10_saml_token_with_message_protection_client_policy oracle/wss10_saml_token_with_message_protection_ski_basic256_client_policy oracle/wss10_username_token_with_message_protection_client_policy oracle/wss10_username_token_with_message_protection_ski_basic256_client_policy oracle/wss10_x509_token_with_message_protection_client_policy oracle/wss11_kerberos_token_with_message_protection_client_policy oracle/wss11_message_protection_client_policy oracle/wss11_saml_token_with_message_protection_client_policy oracle/wss11_username_token_with_message_protection_client_policy oracle/wss11_x509_token_with_message_protection_client_policy |
|
oracle.wsm.security.util.SecurityConstants.ClientConstants.WSS_ENC_KEY_ALIAS |
This property sets the alias of the key within the keystore that will be used to decrypt the response from the service. If provided, this value will override any statically configured value. Type: java.lang.String Not used in WSS11 policies. |
oracle/wss10_message_protection_client_policy oracle/wss10_saml_hok_token_with_message_protection_client_policy oracle/wss10_saml_token_with_message_integrity_client_policy oracle/wss10_saml_token_with_message_protection_client_policy oracle/wss10_saml_token_with_message_protection_ski_basic256_client_policy oracle/wss10_username_token_with_message_protection_client_policy oracle/wss10_username_token_with_message_protection_ski_basic256_client_policy oracle/wss10_x509_token_with_message_protection_client_policy |
|
oracle.wsm.security.util.SecurityConstants.ClientConstants.WSS_ENC_KEY_PASSWORD |
This property sets the password for the key within the keystore that will be used for decryption. If provided, this value will override any statically configured value. Type: java.lang.String Not used in WSS11 policies. |
oracle/wss10_message_protection_client_policy oracle/wss10_saml_hok_token_with_message_protection_client_policy oracle/wss10_saml_token_with_message_integrity_client_policy oracle/wss10_saml_token_with_message_protection_client_policy oracle/wss10_saml_token_with_message_protection_ski_basic256_client_policy oracle/wss10_username_token_with_message_protection_client_policy oracle/wss10_username_token_with_message_protection_ski_basic256_client_policy oracle/wss10_x509_token_with_message_protection_client_policy |
|
oracle.wsm.security.util.SecurityConstants.ClientConstants.WSS_RECIPIENT_KEY_ALIAS |
This property sets the alias for the recipient's public key that is used to encrypt type outbound message. If provided this value will override any static configuration value. Type: java.lang.String |
oracle/wss10_message_protection_client_policy oracle/wss10_saml_hok_token_with_message_protection_client_policy oracle/wss10_saml_token_with_message_integrity_client_policy oracle/wss10_saml_token_with_message_protection_client_policy oracle/wss10_saml_token_with_message_protection_ski_basic256_client_policy oracle/wss10_username_token_with_message_protection_client_policy oracle/wss10_username_token_with_message_protection_ski_basic256_client_policy oracle/wss10_x509_token_with_message_protection_client_policy oracle/wss11_kerberos_token_with_message_protection_client_policy oracle/wss11_message_protection_client_policy oracle/wss11_saml_token_with_message_protection_client_policy oracle/wss11_username_token_with_message_protection_client_policy oracle/wss11_x509_token_with_message_protection_client_policy |
|
oracle.wsm.security.util.SecurityConstants.ClientConstants.WSM_SUBJECT_PRECEDENCE |
In case of SAML client policies, set this property to false if there is a need to use a client-specified username rather than subject. |
Applies to all of the SAML client policies listed in "Configuring SAML". |
|
oracle.wsm.security.util.SecurityConstants.ClientConstants.WSM_SAML_ISSUER_NAME |
This property sets the SAML issuer name when trying access a service that is protected using SAML mechanism. If provided this value will override any static configuration value. Type: java.lang.String |
Applies to all of the SAML client policies listed in "Configuring SAML". |
|
oracle.wsm.security.util.SecurityConstants.ClientConstants.WSM_INCLUDE_USER_ROLES |
This property sets the user roles in a SAML assertion. |
Applies to all of the SAML client policies listed in "Configuring SAML". |
|
oracle.wsm.security.util.SecurityConstants.ClientConstants.WSM_SAML_ASSERTION_FILE_NAME |
For SAML HOK policies, this file contains the assertion |
Applies to all of the SAML client policies listed in "Configuring SAML". |
|
oracle.wsm.security.util.SecurityConstants.ClientConstants.WSS_KERBEROS_SERVICE_PRINCIPAL |
This property sets the service principal name when trying access a service that is protected using the Kerberos mechanism. If provided this value will override any static configuration value. Type: java.lang.String |
oracle/wss11_kerberos_token_with_message_protection_client_policy |
|
BindingProvider.USERNAME_PROPERTY ( |
User name for authentication. |
Used by username policies, and SAML policies including identity switching policies. For username client policies, you have two options:
For SAML client policies including the identity switch policy, use |
|
BindingProvider.PASSWORD_PROPERTY ( |
Password for authentication. |
Used by username client policies. |
Configuration Override Example
Example 10-5 shows an example of a Web service client overriding the keystore and username/password.
If you need to clear an overridden configuration property, set it to an empty string.
Before you clear it, remember that other policies could be using the same property. The properties are client-specific and there could be multiple policies that are attached to the same client that use the same property.
Example 10-5 Overriding the Keystore and Username/Password
package example;
import oracle.wsm.security.utils.SecurityConstants;
public class MyClientJaxWs {
public static void main(String[] args) {
try {
URL serviceWsdl = new URL("http://localhost/myApp/myPort?WSDL");
QName serviceName = new QName("MyNamespace", "MyService");
Service service = Service.create(serviceWsdl, serviceName);
MyInterface proxy = service.getPort(MyInterface.class);
RequestContext context = ((BindingProvider)proxy).getRequestContext();
context.put(oracle.webservices.ClientConstants.CLIENT_CONFIG, new File( "c:/dat/client-pdd.xml" ) );
context.put(BindingProvider.USERNAME_PROPERTY, getCurrentUsername() );
context.put(BindingProvider.PASSWORD_PROPERTY, getCurrentPassword() );
context.put(SecurityConstants.ClientConstants.WSS_KEYSTORE_LOCATION, "c:/mykeystore.jks");
context.put(SecurityConstants.ClientConstants.WSS_KEYSTORE_PASSWORD, "keystorepassword" );
context.put(SecurityConstants.ClientConstants.WSS_KEYSTORE_TYPE, "JKS" );
context.put(SecurityConstants.ClientConstants.WSS_SIG_KEY_ALIAS, "your signature alias" );
context.put(SecurityConstants.ClientConstants.WSS_SIG_KEY_PASSWORD, "your signature password" );
context.put(SecurityConstants.ClientConstants.WSS_ENC_KEY_ALIAS, "your encryption alias" );
context.put(SecurityConstants.ClientConstants.WSS_ENC_KEY_PASSWORD, "your encryption password" );
System.out.println(proxy.myOperation("MyInput"));
} catch (Exception e) {
e.printStackTrace();
}
}
}
In Example 10-5, the contents of c:/dat/client-pdd.xml referenced might be as follows:
! -- The contents of c:/dat/client-pdd.xml file mentioned above -- >
<oracle-webservice-clients>
<webservice-client>
<port-info>
<policy-references>
<policy-reference uri="management/Log_Msg_Policy" category="management"/>
<policy-reference uri="oracle/wss10_username_token_with_message_protection_client_policy" category="security"/>
</policy-references>
</port-info>
</webservice-client>
</oracle-webservice-clients>
Configuring Local Optimization for a Policy
Oracle WSM supports a SOA local optimization feature for composite-to-composite invocations in which the reference of one composite specifies a Web service binding to a second composite running in the same container. Local optimization enables you to bypass the HTTP stack and SOAP/normalized message conversions during run time.
This SOA local optimization feature is described in "Policy Attachments and Local Optimization in Composite-to-Composite Invocations" in Oracle Fusion Middleware Administrator's Guide for Oracle SOA Suite and Oracle Business Process Management Suite and summarized here.
Controlling When Local Optimization is Used
There are two ways to control the local optimization feature, and they have different scope:
-
By adding the
oracle.webservices.local.optimizationproperty in the binding section of thecomposite.xmlfile. There are two possible values,trueandfalse:-
true-- Local optimization is used if the policy supports it as shown in Table 10-3 and the policy-level control is configured to use it as described in "Configuring the Policy-Level Optimization Control".If optimization is used, the policy is not applied.
-
false-- Local optimization is not used, regardless of the how the policy-level control is configured and the default policy setting for the local-optimization property shown in Table 10-3.This setting forces the policy to be applied.
The composite-level property is independent of the policy-level configuration. That is, if you want to turn off the optimization regardless of whether a policy is attached, set the composite-level property to
false.See "Policy Attachments and Local Optimization in Composite-to-Composite Invocations" for information on overriding the local-optimization setting for a policy by adding the
oracle.webservices.local.optimizationproperty in the binding section of thecomposite.xmlfile. -
-
By configuring the optimization control for a policy, as described in "Configuring the Policy-Level Optimization Control". The policy-level property controls the optimization wherever the policy is used, except as overridden by the composite-level property.
Configuring the Policy-Level Optimization Control
Note:
If there is a policy attached to the Web service, the policy may not be invoked if this optimization is used. Therefore, for each policy you need to decide whether you want to use the local optimization.The optimization control is available when you create or edit a policy, as shown in Figure 10-4.
Figure 10-4 Local Optimization Control When Creating a Policy
Description of "Figure 10-4 Local Optimization Control When Creating a Policy"
There are three possible settings for the Local Optimization control: On, Off, and Check Identity:
-
On -- Optimization is turned on and the policy is not applied.
-
Off -- Optimization is turned off and the policy is applied. The request goes through the usual WS/SOAP/HTTP process.
-
Check Identity -- Optimize only if a JAAS subject already exists in the current thread, indicating that authentication has already succeeded. Otherwise, go through the usual WS/SOAP/HTTP process.
Table 10-3 shows the predefined policies, and describes how each policy implements the local optimization feature.
Table 10-3 Default Optimization Setting of Predefined Policies
| Policy Name | Default Optimization Setting |
|---|---|
|
oracle/wsaddr_policy |
On |
|
oracle/binding_authorization_denyall_policy |
Always Off |
|
oracle/binding_authorization_permitall_policy |
Always Off |
|
oracle/binding_permission_authorization_policy |
Off |
|
oracle/component_authorization_denyall_policy |
Always Off. (Does not apply to bindings.) |
|
oracle/component_authorization_permitall_policy |
Always Off. (Does not apply to bindings.) |
|
oracle/component_permission_authorization_policy |
Off |
|
oracle/log_policy |
On |
|
oracle/wsmtom_policy |
On |
|
oracle/wss_http_token_client_policy |
Check Identity |
|
oracle/wss_http_token_service_policy |
Check Identity |
|
oracle/wss_http_token_over_ssl_client_policy |
Check Identity |
|
oracle/wss_http_token_over_ssl_service_policy |
Check Identity |
|
oracle/wss11_kerberos_token_client_policy |
Check Identity |
|
oracle/wss11_kerberos_token_service_policy |
Check Identity |
|
oracle/wss_username_token_client_policy |
Check Identity |
|
oracle/wss_username_token_service_policy |
Check Identity |
|
oracle/wss_username_token_over_ssl_client_policy |
Check Identity |
|
oracle/wss_username_token_over_ssl_service_policy |
Check Identity |
|
oracle/wss10_message_protection_client_policy |
On |
|
oracle/wss10_message_protection_service_policy |
On |
|
oracle/wss10_username_token_with_message_protection_client_policy |
Check Identity |
|
oracle/wss10_username_token_with_message_protection_service_policy |
Check Identity |
|
oracle/wss10_x509_token_with_message_protection_client_policy |
Check Identity |
|
oracle/wss10_x509_token_with_message_protection_service_policy |
Check Identity |
|
oracle/wss10_saml_token_with_message_protection_client_policy |
Check Identity |
|
oracle/wss10_saml_token_with_message_protection_service_policy |
Check Identity |
|
oracle/wss10_saml_token_client_policy |
Check Identity |
|
oracle/wss10_saml_token_service_policy |
Check Identity |
|
oracle/wss10_username_id_propagation_with_msg_protection_client_policy |
Check Identity |
|
oracle/wss10_username_id_propagation_with_msg_protection_service_policy |
Check Identity |
|
oracle/wss11_message_protection_client_policy |
On |
|
oracle/wss11_message_protection_service_policy |
On |
|
oracle/wss11_username_token_with_message_protection_client_policy |
Check Identity |
|
oracle/wss11_username_token_with_message_protection_service_policy |
Check Identity |
|
oracle/wss11_x509_token_with_message_protection_client_policy |
Check Identity |
|
oracle/wss11_x509_token_with_message_protection_service_policy |
Check Identity |
|
oracle/wsrm10_policy |
On |
|
oracle/wsrm11_policy |
On |