10 Managing Backup Encryption
Data is vital to an organization and it must be guarded against malicious intent while it is in an active state, on production servers, or in preserved state, on backup tapes. Data center security policies enable you to restrict physical access to active data. To ensure security of backup data stored on tapes, Oracle Secure Backup provides backup encryption.
Backup Encryption is an optional and easily configurable mechanism which ensures that all client data that Oracle Secure Backup writes to tape is encrypted. Backup encryption can be performed for both file-system data and Recovery Manager (RMAN) generated backups.
Note:
Encryption is not supported for volume duplication, volume migration, or media management. For more information on these topics, see Chapter 9, "Vaulting".This chapter contains these sections:
10.1 Enabling Backup Encryption
Backup encryption is designed to be easy to implement. In the simplest scenario, you change one global policy to ensure that all data from each client is encrypted. Backup encryption also offers a large degree of configuration flexibility.
To set encryption at the global level or for a specific client, set the encryption policy to one of the following values:
-
requiredAll data coming from this backup domain or client must be encrypted.
-
allowedAll data coming from this backup domain or client may be encrypted. The decision to encrypt is deferred to the next lower priority level. This is the default setting.
You can specify encryption settings at the following levels, from highest to lowest precedence:
-
Global
If backup encryption is set to
requiredat the global level, then all backup operations within the administrative domain will be encrypted. This global policy is defined using Oracle Secure Backup defaults and policies. -
Client
If the host encryption setting is
required, then all backup operations on the host will be encrypted regardless of whether or not encryption was configured at the backup level. If the host encrypted setting isallowed, then backups on the host will not be encrypted unless configured as part of the backup job itself or if the global encryption policy is set torequired. -
Job
If the host and global encryption policies are set to
allowed, then backup encryption will only be performed if it is configured at the backup level.
An encryption setting specified at a higher level always takes precedence over a setting made at a lower level. For example, if you enable backup encryption at the global level, and your file-system backup job disables encryption, then the backup is still encrypted because the setting at the higher level (global level) takes precedence.
Backup Encryption for File-System Backups
For file-system backups, you can select encryption for the entire administrative domain, a specific client, or a specific backup job. To define encryption for a particular file-system backup job, you specify the encryption policy in the backup schedule that is associated with your file-system backup job. You can also configure encryption for on-demand backups of file-system data.
Backup Encryption for Oracle Database Backups
For Oracle Database backups, encryption can be specified for the administrative domain, a specific client, or a specific backup job. You specify encryption for a specific Oracle Database backup job using database backup storage selectors or through the Recovery Manager (RMAN) media management parameter OB_ENCRYPTION. The encryption algorithm that Oracle Secure Backup uses depends on the algorithm configured for the Oracle Secure Backup host.
See Also:
"Adding a Database Backup Storage Selector" for information about defining backup storage selectorsFor a particular Oracle Database backup job, settings made using the OB_ENCRYPTION parameter override the settings made using the database storage selector associated with the backup job.
You can set the following values for the OB_ENCRYPTION parameter:
-
ONOracle Secure Backup encrypts the backup data unless it has already been encrypted by RMAN.
-
OFFOracle Secure Backup does not encrypt the backup data unless either the host or global policy is set to
required. SettingOB_ENCRYPTIONtoOFFis equivalent to specifying no value for it. -
FORCEDOFFOracle Secure Backup does not encrypt the database backup, overriding any host or domain encryption settings that are set to
required. TheFORCEDOFFsetting does not affect RMAN, which can still encrypt the backup data. -
SWENCRYPTIONOracle Secure Backup uses software encryption instead of hardware encryption. This option is provided in case you do not want hardware encryption used in some situations.
See Also:
Oracle Database Backup and Recovery User's Guide for more informationIf the RMAN data from the SBT is encrypted, then Oracle Secure Backup performs no further encryption. RMAN encryption satisfies a host or global required encryption setting within Oracle Secure Backup. For example, if a host is configured with encryption required and the backup was encrypted by RMAN, then Oracle Secure Backup does not re-encrypt the backup because the host encryption required configuration has been met. For RMAN encrypted backups, the encryption keys are managed by the database so the host encryption key settings configured within Oracle Secure Backup would not apply.
If a host is configured for encryption required, and if RMAN backup encryption is disabled, then Oracle Secure Backup encrypts the RMAN backups using Oracle Secure Backup encryption based on the host encryption configuration.
10.2 Backup Encryption Options
The encryption algorithm is inherited from the global default policy and can be overridden at the client level. Each client can use a different encryption algorithm. For example, a payroll computer can use a higher level of encryption than a test lab computer. The supported encryption algorithms are:
-
AES128
-
AES192
-
AES256
Note:
The backup encryption algorithm cannot be selected at the job level.A client rekeyfrequency policy defines when a different key is generated. For example, the policy might require that a different set of keys be generated every 30 days. Older keys are retained in a wallet-protected key store. This ensures that if a key or wallet and the associated backup tape are compromised, then only older data could be unencrypted. The default rekeyfrequency policy for a client is inherited from the global rekeyfrequency policy.
10.3 Backup Encryption Keys
Keys can be generated either automatically or with a passphrase. The suggested mode of operation and default value is automatic generation. Each newly created client gets an automatically generated key during the mkhost phase. This key is added to the wallet-protected key store that is specific for this client, and it remains valid for encryption until:
-
A key renewal event occurs
-
The backup administrator manually renews an automatically generated key
-
The backup administrator changes the key to a passphrase while providing a different passphrase
The passphrase is never stored anywhere. The hash of the passphrase and the key generated from the passphrase are stored in the encrypted store. Oracle Secure Backup does not enforce a minimum length for a passphrase.
Once the different key is created, it is added to the wallet-protected key store and marked as the active encryption key. Old encryption keys are left in the key store and used for automatic and seamless decryption of data. If clients are removed from the backup domain, then their key stores are still retained on the administrative server. This ensures that the backup administrator can always restore data no matter the age of the encrypted backup volume set.
Note:
There is one exception where a key is not automatically added to the key store. Keys for transient backups are effectively one-use keys and are not usually stored in the key store. You can override this behavior through a command line option. See "Transient Backups" to learn more about transient backups.When a key expires, a different key is automatically generated. For passphrase generated keys, however, there is some overhead for the backup administrator, who must type in a passphrase for each client that is using passphrase-generated keys. When a passphrase-generated key expires, Oracle Secure Backup generates a warning message stating that the backup administrator must update the passphrase for the stated client. This message is placed in the Oracle Secure Backup log files, the display output, and an email to the backup administrator.
10.4 Backup Encryption Security
Once backup encryption is enabled, all data is encrypted using the defined encryption algorithm. The data is encrypted before it leaves the client. The encryption keys are stored in a mechanism that is protected by the Oracle Secure Backup wallet.
The administrative server is considered a secure host. All keys and wallet-protected key stores for all clients are stored on this protected computer. When a backup or restore job is started, the encryption key is passed over a SSL connection to the client that is encrypting or decrypting data. The encryption keys are retained in memory only so long as needed to perform the encryption or decryption.
The encrypted key stores are extremely valuable, because they enable encryption and decryption of all tapes. If the key stores are lost, then all data would also be lost. It is a best practices task for the backup administrator to ensure that the encrypted key stores are backed up. This should be easy to accomplish, because the encrypted key stores reside within a file-system branch that should be backed up as a best practices task. The encrypted key store format is platform independent.
Backups of Oracle Secure Backup administrative data must not be encrypted with an automatically generated key. If they were, and if the administrative server were destroyed, then recovering the decryption key used to encrypt the encryption keys would be difficult. For this reason, making a transient backup of the administrative server tree is better.
10.5 Encrypting Data
Data is encrypted at the client level. Each client has its own set of keys. One key is the active key used for encrypting backups. Older keys are used to seamlessly restore older backups that were created with those keys.
Note:
Oracle Secure Backup does not encrypt backups of NAS devices. Oracle Secure Backup encryption is performed on the client host where Oracle Secure Backup software has been installed. Because backup software cannot be installed directly on NAS devices, NDMP is used for backup and restore operations.10.6 Transient Backups
In some cases you may need to back up a set of data from backup domain Site A and restore it at backup domain Site B. The backup set might contain backup files for several clients. Each of client backup file is encrypted to a client-specific encryption key, which was probably used in recent backups at Site A. For Site B to decrypt the data, you would have to collect all keys used in encrypting the data at Site A and then ship those keys to Site B.
This scenario would be a serious threat to security because these keys were used in other recent backups. Oracle Secure Backup enables cross-site backup encryption without this security threat by encrypting data at the volume set level for a given backup job. The key for volume set encryption is based on a passphrase. The data is encrypted against this passphrase-generated key for all clients that are part of this backup job. The backup administrator of Site A gives the passphrase and encryption algorithm used to Site B. The passphrase and encryption algorithm are provided when Site B does the restore operation, and the data can be decrypted.
In all other cases, the encryption keys for backup encryption are automatically added to the appropriate wallet-protected key store. A transient key, however, is a one-time key used mainly for moving data to a remote location. Transient encryption keys, therefore, are not stored in the protected key stores by default. Oracle Secure Backup does provide an option to the backup administrator to store the transient encryption key in the key store.
See Also:
Oracle Secure Backup Reference for complete syntax and semantics of thebackup command in obtool10.7 One-Time Unencrypted Backups
Oracle Secure Backup enables the backup administrator to do a one-time unencrypted backup without changing global or client encryption settings.
Suppose the backup administrator is planning to move all home directories from one host to another and does not want to copy files directly between these two hosts. The backup administrator wants instead to back up a dataset worth of data to a tape, restore it to another host, and immediately destroy the tapes or the contents of the tapes after the transfer. The backup administrator does not want to use encryption because of the processing overhead that occurs.
In this special case, the backup administrator can use the backup --encryption forcedoff command. This command overrides global and client encryption settings and performs an unencrypted backup. Transcripts and all other reports for this job then state that encryption was forcibly disabled for this backup set. There is a similar mechanism available to RMAN backups using the OB_ENCRYPTION variable from within RMAN.
See Also:
Oracle Secure Backup Reference for complete syntax and semantics of thebackup command in obtool10.8 Day-to-Day Backup Encryption Example
By default the initial global and client backup encryption policy settings are allowed. Encryptions keys are generated automatically with a default AES192 encryption algorithm. If the backup administrator decides that the default configuration is sufficient for the enterprise, then no configuration is required. This section describes the configuration of a more complicated case.
In this more complicated enterprise, there are three classes of hosts that need differing types and amount of encryption:
-
Developers
These clients require encryption only for source code backup operations in a dataset called sourcecode.
-
Payroll
This client requires AES256 encryption with a different encryption key each week.
-
CEO
This client requires all data to be encrypted using a passphrase-generated key.
There are no options that must be changed for developer clients. The backup administrator instead updates the backup job for the sourcecode dataset that is used to back up the developer computers. If the backup schedule does not yet exist, then the backup administrator creates a backup schedule with a mkhost command:
mksched --dataset sourcecode --type backup --encryption yes SourceCode
If the backup schedule exists, then the backup administrator uses the chsched command with the same options specified.
The payroll host requires changes to the default client policies and settings for the encryption algorithm, key regeneration time, and client encryption flags. The backup administrator can make these changes with a chhost command:
chhost -algorithm aes256 -encryption required -rekeyfrequency 1week Payroll
This ensures that all data from the payroll client is always encrypted to the AES256 algorithm with a different key encryption key each week.
The default encryption is sufficient for the CEO client, but the backup administrator must change the encryption key type to passphrase-generated. This can be done with another chhost command:
chhost --keytype passphrase -passphrase "What's my password?" TheBoss
Once the initial configuration has been performed there is minimal additional overhead managing backup encryption.
The encryption state is displayed as part of the job transcript during a backup operation for both file-system and RMAN backups.
10.9 Hardware-Based Encryption
The disadvantage of encrypting backup data using RMAN or Oracle Secure Backup is the performance impact. Determining this impact can be difficult, and its importance depends on your circumstances. If you want encryption without performance impact, Oracle Secure Backup supports hardware-based encryption on the LTO4 tape drive.
The LTO4 interface to hardware encryption is implemented through the SCSI specification for hardware encryption. Other vendors offer similar hardware, and their products are certified for use with Oracle Secure Backup as they are tested and approved by Oracle. Information about every tape device supported by Oracle Secure Backup is available at the following URL:
http://www.oracle.com/technology/products/secure-backup/
Hardware-based encryption brings no changes to the existing Oracle Secure Backup encryption model. All that is required for hardware-based encryption, other than the LTO4 hardware, is that encryption be turned on at the policy, host, or backup job level within Oracle Secure Backup. All encryption decisions, policies, key management, and settings regarding hardware-based encryption are identical with those for software-based encryption.
You select hardware-based encryption either by selecting the LTO4 drive for a backup or by having nothing but LTO4 drives in your Oracle Secure Backup administrative domain. Oracle Secure Backup turns on the encryption feature within the LTO4 drive with SCSI commands and sends the encryption key to the LTO4 drive. Encryption is performed by the LTO4 drive in hardware instead of in software by Oracle Secure Backup. If an LTO4 drive is not found, or if there is not an LTO4 tape in the drive, then the existing Oracle Secure Backup software encryption model is used.
If an LTO4 drive contains an LTO4 tape but needs an additional LTO4 tape to complete a backup, then Oracle Secure Backup looks for an additional LTO4 tape. If it finds one, it mounts the LTO4 tape and continues with the backup. If Oracle Secure Backup cannot mount an additional LTO4 tape, then the job state shows as Running and input is required by the backup operator.
Note:
It is not possible to back up using hardware-based encryption and then restore using software-based encryption. Nor is it possible to back up using software-based encryption and then restore using hardware-base encryption.10.9.1 Hardware-Encrypted Transient Backups
You can disable hardware-based encryption on transient backups with the --disablehardwareencryption option of the backup command. This option forces Oracle Secure Backup to use software-based encryption for the backup.
See Also:
-
Oracle Secure Backup Reference for complete syntax and semantics for the
backupcommand
10.9.2 Hardware Encryption Reports and Logging
Hardware-based encryption generates no additional reports or logs, but it does affect the following existing reports and logs:
-
In any transcript, log, or report where Oracle Secure Backup shows encryption settings
on/off/forcedoff/rman, hardware-based encryption addshardwareandtransient_hardwaresettings for data that was encrypted by the LTO4 tape drive. -
Job transcripts show encryption type and algorithm.
-
Output of the
lssection--longcommand includes encryption type. -
Output of the
lsvol--longcommand shows if a volume can be encrypted in a Tape Attributes field. Possible values areunknown,hwencryptable, andnothwencryptable. Theunknownvalue persists until a tape is mounted and Oracle Secure Backup can determine if it supports hardware encryption. -
The
lsdev--long--geometrycommand reports on the availability of hardware encryption.
10.9.3 Hardware Encryption Algorithm
Oracle Secure Backup supports encryption algorithms AES128, AES192, and AES256 for software-based encryption. But the only encryption algorithm supported for the LTO4 hardware is AES256. So even if a global or client encryption policy specifies an algorithm other than AES256, all hardware-based backups are encrypted with the AES256 algorithm.
When a hardware-encrypted backup job completes, the job transcript and all other reports display the AES256 encryption algorithm. The archive section database and the tape header also show that the AES256 algorithm was used for the encryption.
This behavior matters only when you do a hardware-encrypted transient backup and do not store the key. In this situation, you must supply the AES256 algorithm when doing a restore. If the backup --store option was used on a hardware-encrypted transient backup, then the algorithm is not needed.
See Also:
-
Oracle Secure Backup Reference for complete syntax and semantics for the
backupcommand
10.9.4 Hardware Encryption Policies
Hardware-based encryption in Oracle Secure Backup is controlled by two backup encryption policies:
-
enablehardwareencryptionIf this policy is set to its default value
yes, then hardware-based encryption is considered. If the policy value is changed tono, then Oracle Secure Backup does software-based encryption instead of hardware based encryption. -
requireencryptablemediaIf this policy is set to its default value
no, then Oracle Secure Backup first attempts to mount a tape capable of hardware encryption. If that is not possible, then Oracle Secure Backup falls back to software encryption. If the policy value is changed toyes, then Oracle Secure Backup puts the job into a pending state until a hardware-encryptable tape is made available.This policy is ignored if the tape drive is incapable of hardware encryption or cannot identify encryption-capable tapes.
To change the values of these policies:
-
From the Oracle Secure Backup Home page, click Configure.
The Configure page appears.
-
In the Advanced section, click Defaults and Policies.
The Configure: Defaults and Policies page appears.
-
In the Policy column, click backupencryption.
The Configure: Defaults and Policies > backupencryption page appears.
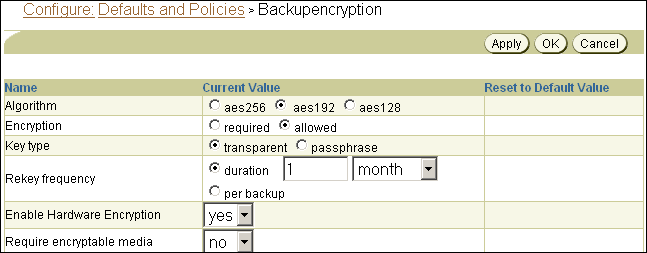
Description of the illustration osb_web47.gif
-
To disable hardware-based encryption, select no in the Enable Hardware Encryption list.
-
To put backup jobs in a pending state if an encryptable tape is not loaded in the LTO4 tape drive, select yes in the Require encryptable media list.
-
Click OK.
The Configure: Defaults and Policies page displays a success message.