| Oracle® Access Manager Identity and Common Administration Guide 10g (10.1.4.3) Part Number E12489-01 |
|
|
View PDF |
| Oracle® Access Manager Identity and Common Administration Guide 10g (10.1.4.3) Part Number E12489-01 |
|
|
View PDF |
Before configuring and administering Oracle Access Manager, you might find it useful to preview the tasks that you perform as an administrator. It can also be useful to log in and view the user interface for the Identity System and Access System.
This chapter contains information you need before starting to configure and administer Oracle Access Manager, including these topics:
Note:
Although the product name has changed to Oracle Access Manager, in manuals and the product you might see the name NetPoint or Oblix. This is particularly true in file and path names.Oracle Access Manager should be installed and set up as described in the Oracle Access Manager Installation Guide. Read the Oracle Access Manager Introduction which provides an overview of Oracle Access Manager not found in other manuals.
This document focuses on Identity System administration in addition to common configuration and administration tasks.
You use the Identity System and objects in the directory service to manage identity information about individuals, groups, organizations, and other objects. The Master Administrator can delegate authority to other administrators, allowing the Identity System to scale millions of users.
In addition to managing identity information, the Identity System enables you to manage read, write, and modify privileges for a user based on a specific user attribute, membership in a group, or association with an organization. You can link privileges together into a workflow.
For example, you can set up a self-registration workflow so that when a user self-registers, the registration request is forwarded to appropriate people for approval, and upon approval, the user is immediately and automatically granted access to all resources appropriate for his or her identity attributes.
Finally, the Identity System enables you to accurately manage user identities, group memberships, and organizational objects. This information can then be leveraged by the Access System to manage access privileges for users based on user attributes, group membership, or association with an organizational entity.
The Identity System consists of these components:
The Identity Server
WebPass
Identity Server—A standalone server or several instances that manage identity information about users, groups, organizations, and other objects. The Identity Server provides the following applications:
User Manager—If you are an administrator or a user, the User Manager enables you to add, modify, and delete user identities provided that you are a participant in a workflow that performs this function. User Manager data can be leveraged by the Access System to provide users with access privileges based on their directory profiles. The User Manager also has reporting capability.
The User Manager typically enables end users to view other users and to modify their own identity information. The users that a person can view and the identity information that someone can modify depends on the privileges granted by a Master Administrator.
Group Manager—Enables administrators and users to create or delete groups, and enables users to subscribe or unsubscribe from groups. You must be a participant in a workflow that performs the desired function. The Group Manager also has reporting capability.
The Group Manager typically enables end users to view groups and to subscribe to membership in a group. The groups that a person can view and subscription rights are granted by a Master Administrator.
Organization Manager—If you are an administrator or a user, the Organization Manager enables you to create and delete organizations and other objects (such as floor plans and assets) that do not belong in the User Manager or Group Manager. You must be a participant in a workflow that performs the desired function. The Organization Manager also has reporting capability.
The Organization Manager enables end users to view organizational entities such as floor plans. The organizational entities that a person can view depend upon the rights granted by a Master Administrator.
Identity System Console—Enables administration and configuration of the Identity System. Using the System Console, you also create Administrators and assign the right to delegate administrative tasks.
The Identity Server stores user information on a directory server. The Identity Server keeps the directory current so that the Access Server gets the right information.
WebPass—WebPass is a Web server plug-in that passes information between the Web server and the Identity Server. WebPass can talk to multiple Identity Servers.
Details here include:
Installation and setup includes the following events:
At least one Identity Server and one WebPass were installed and the resulting Identity System was set up.
A transport security mode was chosen to protect communication between the Identity Server and WebPass.
The Identity Server was configured to communicate with an LDAP directory server or virtual directory.
You are prompted regarding automatic setup of your directory server schema. If you chose not to automatically update your schema, you are prompted to do so manually during configuration. Instructions on manual updates of your directory server schema are provided in this manual.
Each expected application was installed with the Identity Server.
When you log in to the Identity System, you see a series of tabs on the top navigation bar that match your applications. From these tabs you can configure the look and functionality of the User Manager, Group Manager, and Organization Manager applications.
Required attributes for the User and Group object classes were set up.
Other attributes might also have been configured.
At least one Master Administrator was selected.
This is the highest-level administrator. You must have at least one administrator defined to begin working with Oracle Access Manager. These are the people who configure the System. The Master administrator creates lower-level administrators called Master Identity Administrators.
Table 1-1 provides a review of Identity System installation and setup.
For more information, see theOracle Access Manager Installation Guide.
The Identity System consists of an administrative console and three end-user applications discussed earlier:
Identity System Console (includes User Manager Configuration, Group Manager Configuration, Org. Manager Configuration, Common Configuration, and System Configuration)
The User Manager application
The Group Manager application
The Organization Manager application
People use the Identity System end-user applications for tasks such as changing personal information, resetting passwords, adding other users, and looking up organizational information. This identity data originates in your LDAP directory. To configure the Identity System applications, you must know what attributes in the directory you want to display, and what attributes you want to be able to modify.
After configuring the Identity System to work with data in your directory, you configure the Identity System application profile pages. These profile pages display the directory data. For example, you can display a user's name, title, address, and phone number on a profile page in the User Manager application. You can also improve the efficiency of your organization by using Identity workflows. Identity workflows enable you to automate Identity System application-related activities, for example, creating a user and assigning email and other accounts to that user.
Finally, you use the Identity System to create Identity workflows. Identity workflows are definitions for a set of actions and the steps you perform to complete the actions. For instance, you can create workflow definitions for the way new employees are added to your various corporate information systems.
Table 1-1 provides an overview of configuring the Identity System:
Table 1-1 Overview of Identity System Configuration
| To perform this task | Description | Read |
|---|---|---|
|
Specify additional structural object classes for the Organization Manager and auxiliary object classes for all applications |
During setup, you configure one structural object class each for the User Manager, Group Manager, and Organization Manager. You can define additional structural objects classes for the Organization Manager. For instance, you might want the Organization Manager to display assets. You can also add auxiliary object classes to provide the Identity System applications with data. |
|
|
Configure attributes |
You can determine what attributes are available to the User, Group, and Organization Manager applications. You also can configure rules for how to display attribute values on an Identity System application profile page. For example, you might want employees to be able to select their department name from a list. |
|
|
Configure User, Group, and Organization application tabs |
In the User Manager, you configure what the user sees on the My Identity tab. In the Group Manager, you configure what the user sees on the My Groups tab. In the Organization Manager, you configure what the user sees on the Location tab and, optionally, additional tabs. |
|
|
Configure User, Group, and Organization profile pages |
Tabs contain one or more profile pages. A profile page contains a set of panels. A panel is a collection of attributes. For example, on a profile page for a user, you can define an Identity panel to display values for attributes such as Name, Photo, Title, and so on. |
|
|
Set the searchbase |
The searchbase determines the entry point in the directory tree for a search. |
|
|
Configure view and modify permissions for attributes |
You must determine who can find what, at what point in the searchbase, and with what filter. These decisions affect who can read or write to data and who receives email notification when an attribute has been modified. |
|
|
Define workflows |
A workflow is a series of steps for creating, deleting, and modifying attributes in the Identity System. For example, in the User Manager, you might want to define a workflow for creating a user that includes collecting information about the new user from several people in your organization. |
|
|
Configure password policies |
You can determine the length of passwords, frequency of password change, and so on. |
|
|
Delegate administration |
To scale your installation, you need multiple administrators, each overseeing a subset of users. |
You can extend your Identity System by adding servers, and expanding your network of Identity System administrators. You can configure audits and logs and perform other administrative functions. Table 1-2 provides an overview of managing the Identity System:
Table 1-2 What to Read for More Information on the Identity System
| To perform this task | Read |
|---|---|
|
Add more Identity Servers |
Oracle Access Manager Installation Guide. To ease this process, you can choose to add more Identity Servers through silent installation or cloning, as described in the Oracle Access Manager Installation Guide. |
|
Add more WebPasses |
Oracle Access Manager Installation Guide. To ease this process, you can choose to add more WebPasses through silent installation or cloning, as described in the installation manual. |
|
Add other Identity System components |
Oracle Access Manager Installation Guide describes how to install most components. Information on how to install the Access Manager SDK for custom AccessGates is located in the Oracle Access Manager Developer Guide. |
|
Configure container limits for Organization Manager |
Commonly used functions in the Oracle Access Manager user interface the following:
Login
Functional Areas on a Page
Online Help
Logout
Oracle Access Manager logs people in based on the roles they have been assigned. As described in "Specifying Identity System Administrators", you can specify the following roles for users:
End User: An end user can perform searches, view profile data, and modify profile data, depending on access permissions set for individual attributes.
Delegated Access Administrator: A Delegated Administrator is a user who can perform all of the same tasks as an end user and can create user, group and organization objects, depending on the level of permissions he or she has been granted. A Delegated Administrator can also view requests.
Delegated Identity Administrator: A Delegated Identity Administrator is a user who has been delegated the right to view configuration tabs for the User Manager, Group Manager, and Organization Manager applications. This person can set attribute access controls, define workflows, and so on.
Identity Administrator: An Identity Administrator can view the User Manager, Group Manager, and Organization Manager applications, and use Identity System configuration functions in the Identity System Console.
For example, if you log in as an Identity Administrator, you can view every screen in every application. But if you log in as an end user, you might only see a subset of the User, Group, and Organization Manager applications, and you cannot access Identity System administrative functions.
By default, single sign-on is configured between the Identity and Access Systems. If you log in to one system, you should not be prompted to log in to the other system.
If you use the Access System to protect the Identity System applications, you can bypass the default login form and implement your own custom form. For details about protecting resources with policy domains, see the Oracle Access Manager Access Administration Guide.
The procedure for logging in to the Identity System depends on whether you customized the login screen, made it available as a portal insert, or protected it with the Access System.
This section covers the default login page that ships with the Identity System, and the impact of the default user type on login. See the Oracle Access Manager Customization Guide and the Oracle Access Manager Developer Guide for more information on customization.
You must configure an attribute with a semantic type of Login before users can log in to the Identity System. You can either automatically configure this attribute during installation, or manually configure it from the Identity System Console. See "Making Schema Data Available to the Identity System" for more information.
Note:
Only Master Identity Administrators and Delegated Identity Administrators have access to the Identity System Console. See "Specifying Identity System Administrators" for more information about configuring these administrators.To log in to the Identity System
In your browser, type the path to the Identity System and press Return.
For example:
https://hostname:port/identity/oblix
where hostname is the name of the computer on which the WebPass is installed and port is the Web server port for the WebPass. You can log in using the HTTP or HTTPS protocol.
The main product page appears. This page has links to one or more applications, including the User Manager, Group Manager, and Org Manager.
See the Oracle Access Manager Customization Guide for more information about changing this default.
Select the desired application.
A login page appears.
Enter your user name and password.
For Active Directory users, if the Domain field is present, select the domain in which this installation of the Identity System operates.
By default, when you log in to the Identity System, you see all of the functions available to an Identity System Administrator. For example, in the User Manager, you see functions such as "My Identity," "Reports," and the search function.
By default, a user is not required to log in to the Access System if he or she is already logged in to the Identity System, and vice versa. Session information is stored in a cookie called the ObTEMC cookie. You might choose to protect the Identity System applications in a policy domain, in which case a different authentication can be used. For details about protecting resources with policy domains, see theOracle Access Manager Access Administration Guide.
You must configure an attribute with a semantic type of Login before users can log in to the Access System. You can either automatically configure this attribute during installation, or manually configure it from the Identity System Console. See "Making Schema Data Available to the Identity System" for more information.
This section covers the default login screen that ships with the Access System.
Note :
Only Master Administrators and Master Access Administrators have access to the Access System Console. For details about configuring Master Access Administrators, see Oracle Access Manager Access Administration Guide.To log in to the Access System
In your browser, type the path to Access System and press Return.
Example: https://hostname:port/access/oblix
where hostname is the name of the computer on which the Policy Manager is installed and port is the Web server port for the Policy Manager. You can log in with the HTTP or HTTPs protocol.
The main product page appears. This page has links to one or more applications, including the Identity System, the Policy Manager, and the Access System Console.
Select the application you want.
Policy Manager—Only Delegated Access Administrators can see any policy domains. For details about delegating administration in the Policy Manager, see the Oracle Access Manager Access Administration Guide.
Access System Console—Only Master Administrators and Master Access Administrators can access its functions. For more information about configuring Master Access Administrators, see the Oracle Access Manager Access Administration Guide.
A login page appears.
The following identifies the main components of an Identity System page.
The following is a portion of an Identity System Console page. This page appears when you access the Identity System landing page, click the Identity System Console link on that page, then click the User Manager Configuration sub-tab.
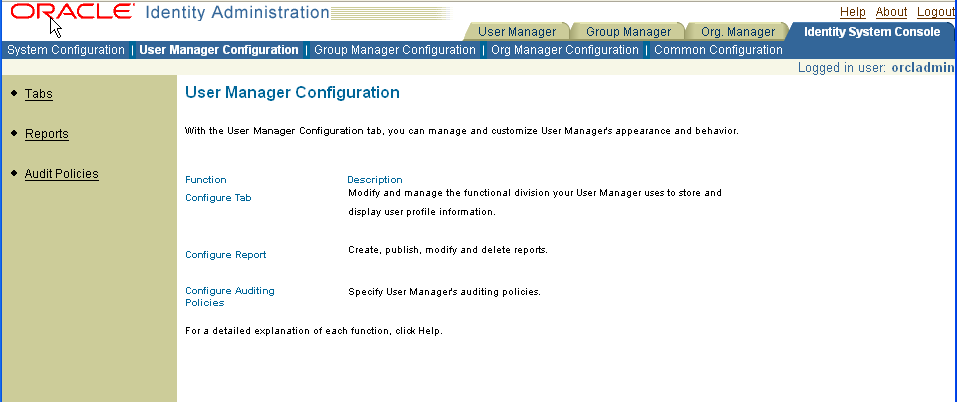
All pages have the following functional areas:
Application Tabs: A set of tabs that show the Identity System applications: the User Manager, Group Manager, Organization Manager (abbreviated to Org. in the user interface), and the Identity System Console.
Application Sub-Tabs: A set of tabs that show the main functions for the Identity System applications. For example, the Identity System Console contains modules for System Configuration, User Manager Configuration, Group Manager Configuration, and Common Configuration.
Help, About, and Logout links: These links appear at the top of the page.
Left Navigation Pane: The Identity System Console uses a left navigation pane. This pane contains a list of links to functions that are applicable to the tab or sub-tab that has been selected. The user applications use sub-tabs and panels instead of a left navigation pane.
Main Body: The main body displays a description of the currently selected function or the fields to be completed.
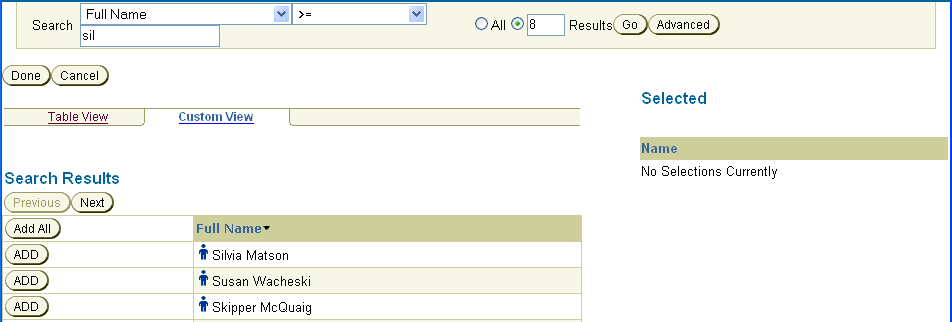
The user interface contains search fields to search for users or groups. These search fields appear on most Identity application pages. The number of fields available to you and the items that you can search on depend on how an administrator has configured the search function.
You query for users or groups by filling in the search criteria and clicking Go. Optionally, you can store the results of a query by clicking the Reports tab and selecting Generate Report. Oracle Access Manager uses a locale-based case insensitive sorting method when you click the column heading (Full Name, for example) in the search results table.
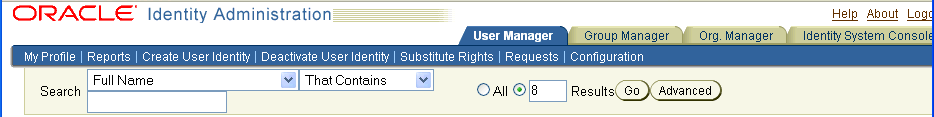
Enter your search criteria.
For the simplest kind of search, type a text string in the Search entry field.
By default, you need not enter a minimum number of characters. However, to help users narrow their search criteria you can control the minimum number of characters that users must enter in the search field by setting the searchStringMinimumLength parameter in oblixadminparams.xml. See the Oracle Access Manager Customization Guide for details.
Click Go.
Users or groups matching your search criteria appear on the screen.
By default, 8 results are displayed on a page. This applies to both Selector and Query Builder. If you perform a search or query that results in more than 20 hits, you receive truncated results. For instructions on changing this search cap, refer to the cookieBustLimit parameter documentation in the Oracle Access Manager Customization Guide. 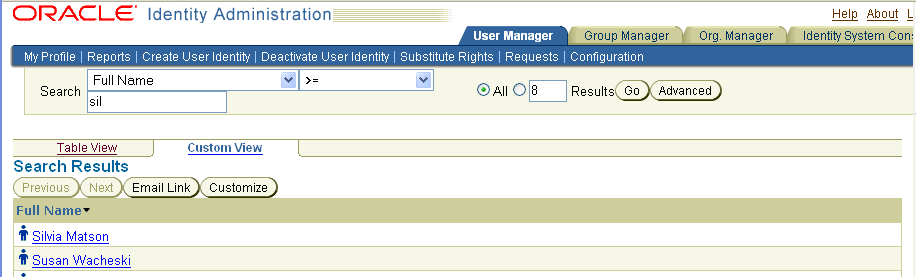
In the search results, click the links for the users or groups to select them.
Note:
If you receive a "Bad request" message when you click Done, your search string is too long for your browser. Browsers handle the search parameters as URLs, and they generate an error if the search exceeds their maximum URL length.In the search results, click the column heading to sort the list.
Note:
Oracle Access Manager uses a locale-based case insensitive sorting method.The selector provides search functionality and the ability to aggregate the results of a search. For example, to create a group, after clicking the Group Manager tab and the Create Group sub-tab, a page appears with selection buttons.
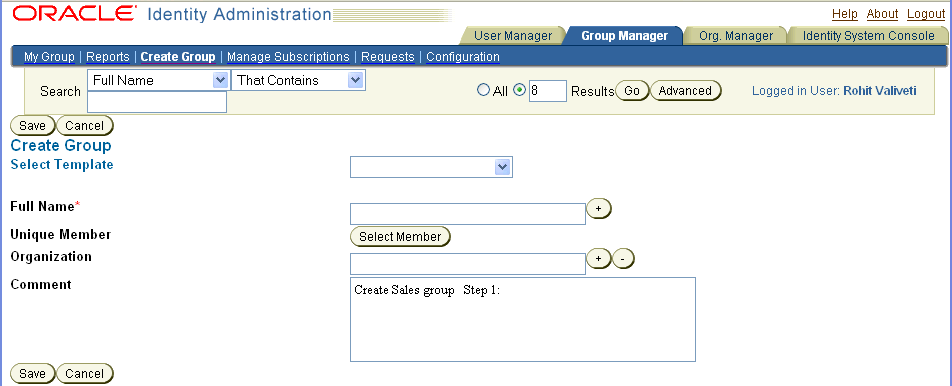
If you click a selection button (Select Member in this example), the Selector appears.
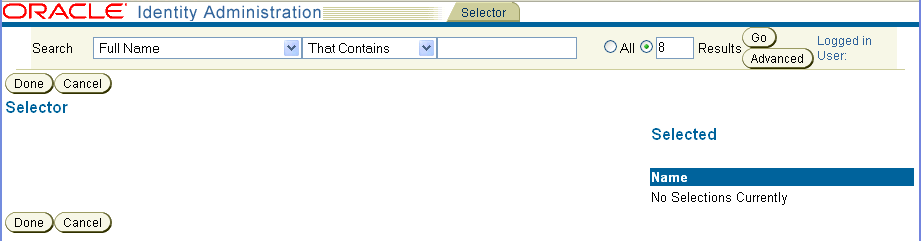
The Selector landing page is a blank search page with Done and Cancel buttons and an empty list of selected items. If you use the search functionality on this page, the Selector enables you to move retrieved items to the Selected list.
A Help link is located at the top right of Identity System screens, and in the side navigation bar of Access System screens. To access online Help, click this link.
You can perform the following tasks in an online Help window:
Scroll to view the entire Help topic.
Click Contents to display a list of topics.
Click Back or Forward to see other Help topics.
Click Exit to close the window.
A link to the About page is located at the top right of Identity and Access System pages. Click the About link to display the Oracle address, telephone numbers, and other contact information, and copyright information.
The View System Info button displays the server platform and version, and contact information for Oracle.
A Logout link is located at the top of the Identity and Access System pages. By default, if you log out of the Identity System, you are automatically logged out of the Access System and vice versa.
When you finish using Oracle Access Manager, to prevent unauthorized people from accessing your information you should log out and close your browser.
By default, sessions expire after three hours. To change the timeout, see "Configuring Session Timeout" for details.
Note:
On Firefox, you are prompted to manually close your browser window after logging out.