18 Configuring Human Workflow Service Components and Engines
This chapter describes how to configure human task service components and the human workflow service engine.
This chapter includes the following topics:
-
Section 18.1, "Configuring Human Workflow Notification Properties"
-
Section 18.2, "Configuring Human Workflow Task Service Properties"
-
Section 18.3, "Configuring Oracle HTTP Server for Task Form Attachments"
-
Section 18.4, "Configuring the Pluggable Notification Service"
-
Section 18.8, "Seeding Users, Groups, and Application Roles using LDAP Tools"
18.1 Configuring Human Workflow Notification Properties
You can configure human workflow notification properties, such as setting the notification mode for messages and setting actionable addresses. These properties are used to notify users of changes to the state of a task. Workflow notifications can use three types of addresses:
-
From address: For sending notifications.
-
Actionable address: For receiving actionable responses.
-
Reply to address: For receiving reply notifications.
Note:
In the following procedures, you must configure your channel drivers before configuring your workflow notification properties. Ensure that you know all necessary driver addresses before beginning (for example, the incoming IMAP and outgoing SMTP e-mail servers).To configure human workflow notification properties:
-
Access this page through one of the following options:
From the SOA Infrastructure Menu... From the SOA Folder in the Navigator... - Select SOA Administration > Workflow Notification Properties.
- Right-click soa-infra.
-
Select SOA Administration > Workflow Notification Properties.
The Workflow Notification Properties page appears.
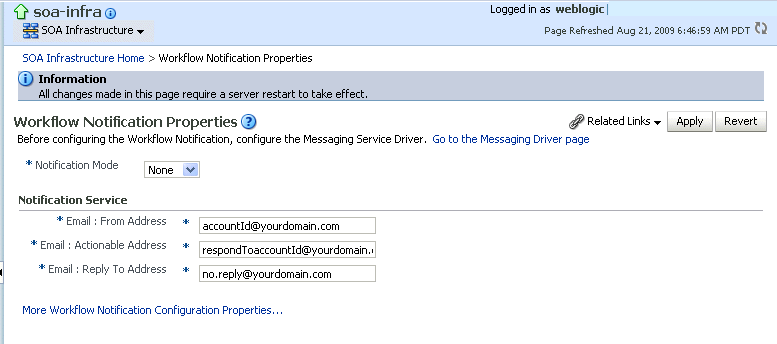
Description of the illustration soaadmin_hwf_notifprops.gif
You now configure Oracle User Messaging Service to send and receive notifications. During configuration, you provide the addresses that are used by human workflow.
-
Click Go to the Messaging Driver Page.
-
Click Configure Driver in the upper right section of the page. This takes you to a page to configure the messaging service driver, including properties such as incoming IMAP and outgoing SMTP e-mail servers, outgoing server user names and passwords, and so on. For handling incorrect e-mail responses, the e-mail driver should be configured to handle incoming mails. This action enables human workflow participants to receive and forward notifications. Messaging drivers support the various messaging transports. See section Section 24.4.1, "How to Configure a Driver" for instructions.
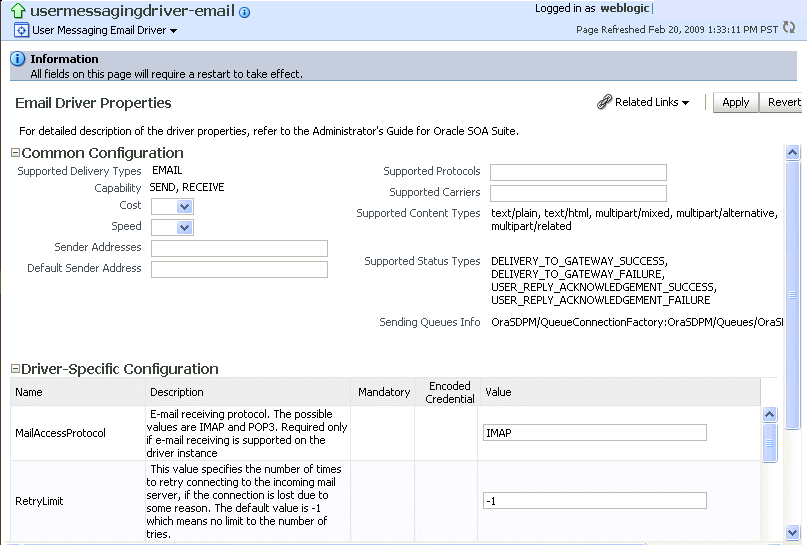
Description of the illustration hwf_ums.gif
Notes:
-
The host name and IP address of the e-mail server with which you configure must also be added to the
/etc/hostsfile of the server on which Oracle SOA Suite is running. For example, if the host name isxyz.oracle.comand the IP address isaa.bb.cc.dd, then add this information to the/etc/hostsfile. -
After you configure the inbound (IMAP) e-mail server, the outbound (SMTP) e-mail server, or both, you must restart the managed Oracle WebLogic Server on which the SOA Infrastructure is configured for these setting to take effect.
-
-
Return to the Workflow Notification Properties page.
-
Specify the mode of the notification service. The possible values are:
-
ALL: The e-mail, short message service (SMS), instant message (IM), and voice channels are configured and notification is sent through any channel that you use.
-
EMAIL: Only the e-mail channel is configured for sending notification messages.
-
NONE: No channel is configured for sending notification messages. This is the default setting.
-
-
Specify notification channel values:
-
Click Apply.
-
If you want to configure advanced notification properties in the System MBean Browser, click More Workflow Notification Configuration Properties. Properties that display include the following. Descriptions are provided for each property.
-
Make changes appropriate to your environment.
Note:
If your IM message contains content that appears to be actionable, note that acting upon the task from within the message does not cause any action to be taken. For example, acting upon the task in the following IM message does not cause any action to occur.Help desk request for wfaulk Task Help desk request for wfaulk requires your attention. NOTE: You can act on the task by copy-pasting one of following lines as your response. RESOLVED : [[NID]] : Pt12uRUu9H+Xem4NYS2o7dKDtqNLs42d4YIs8ySO8Gn0ZVYFsb1SQVenRukRE+ IcE7c4XDb+tPazvP v9T2iA0qylDg0bTaVxX13HhsrCYAg= : [[NID]] UNRESOLVED : [[NID]] : xT9l06rbaGRAey+BtgQyJIXk62mkFtCe7ocKxwNLIsPzyE5/7AnGwXlBodEgQxr6 jorvsw2F54k/C1 r5mvyAJpAp4I4IekOHi4qhQ3eSbBHdzET1IL4F3qV/KZ/BAUsq : [[NID]]
For more information about notifications and the User Messaging Service, see the following documentation:
18.2 Configuring Human Workflow Task Service Properties
You can assign the actionable e-mail account name, specify workflow session time out and custom classpath URL properties values, configure dynamic assignment and task escalation functions of the assignment service, and set additional human workflow properties.
Dynamic assignment functions select a particular user or group from either a group, or from a list of users or groups. The selection is made according to criteria specific to the particular dynamic assignment function.
To configure human workflow task service properties:
-
Access this page through one of the following options:
From the SOA Infrastructure Menu... From the SOA Folder in the Navigator... - Select SOA Administration > Workflow Task Service Properties.
- Right-click soa-infra.
-
Select SOA Administration > Workflow Task Service Properties.
The upper part of the Workflow Task Service Properties page displays the field for the actionable e-mail account and the automatically defined dynamic assignment functions.
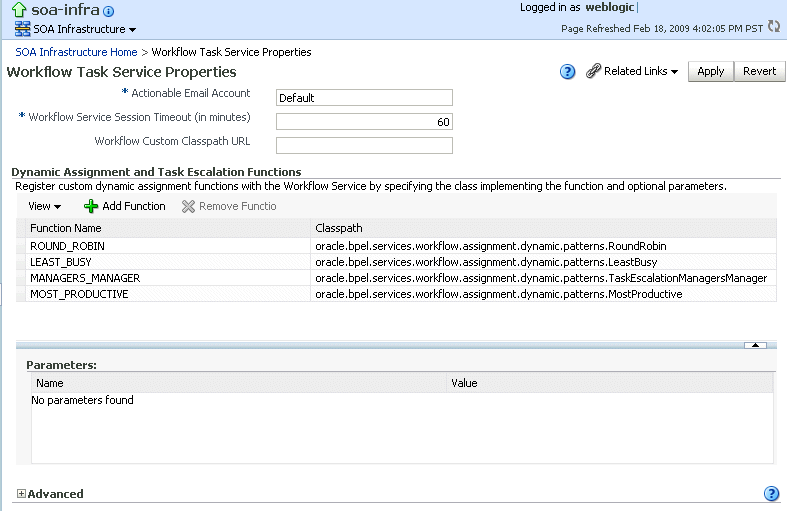
Description of the illustration soaadmin_hwf_taskservpropsu.gif
-
Enter the following details.
Function Description Actionable Email Account Enter the incoming, actionable e-mail account to use. The default account name is Default, which is the account configured in Section 18.1, "Configuring Human Workflow Notification Properties." If a different account name is specified in this field, then create and configure the account as described in Section 18.5, "Configuring Multiple Send Addresses."
Workflow Service Session Timeout (in minutes) Enter the length of time that a user logged into the Oracle BPM Worklist can remain inactive before their session expires, and they are required to log in again. This also applies to authenticated sessions created through one of the TaskQueryServiceauthentication methods.Workflow Custom Classpath URL Enter the URL classpath. This is the classpath used by workflow services to look up classes implementing custom dynamic assignment and task escalation functions, custom callbacks, and customized instances of the system resource bundle, WorkflowLabels.properties.This can be any valid URL (either a local file path or remote URL). The classpath can specify either a directory or a JAR file. If the URL specifies a directory, it must include a trailing '
/' character. -
Go to the Dynamic Assignment and Task Escalation Functions section.
The dynamic assignment functions are defined in the following table. You can also create your own functions and register them with the workflow service.
Function Type Description ROUND_ROBIN Dynamic assignment This function picks each user or group in turn. This function uses the initialization parameter MAX_MAP_SIZE. This parameter specifies the maximum number of sets of users or groups for which the function can maintainROUND_ROBINcounts. The dynamic assignment function holds a list of users and groups in memory for each group (or list of users and groups) on which it is asked to execute theROUND_ROBINfunction.LEAST_BUSY Dynamic assignment This function picks the user or group with the least number of tasks currently assigned to it. MANAGERS_MANAGER Task escalation This function picks the manager's manager. MOST_PRODUCTIVE Dynamic assignment This function picks the user or group that has completed the most tasks over a certain time period (by default, the last seven days).This function uses the initialization parameter DEAFULT_TIME_PERIOD. This parameter specifies the length of time (in days) over which to calculate the user's productivity. This value can be overridden when calling theMOST_PRODUCTIVEdynamic assignment function. Use an XPath function by specifying an alternative value as the third parameter in the XPath function call. -
Click a function to display its parameters and values in the Parameters section.
-
Click Add to add a function. You are prompted to specify the following:
-
Function name
-
Class path
-
Function parameter name
-
Function parameter value
Note that you cannot add multiple properties to a function on this page. To do that, use the System MBean Browser, which is available by selecting Administration > System MBean Browser from the SOA Infrastructure menu.
-
-
Click OK.
-
If you want to update the value of a parameter in a function, select the function in the Dynamic Assignment and Task Escalation Functions table.
The parameter value displays for editing.
-
Update the value.
-
Expand the Advanced section.
The Advanced section displays the following properties:
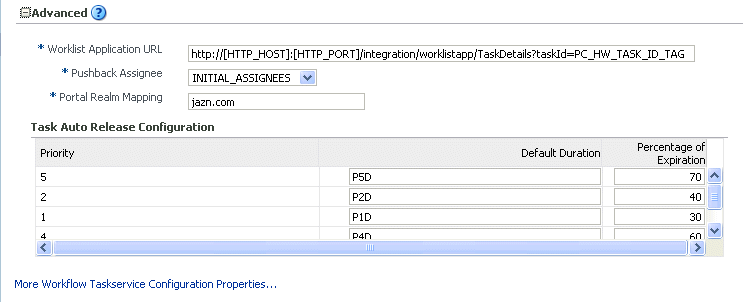
Description of the illustration soaadmin_hwf_taskservpropsl.gif
These properties are defined in the following table.
Properties Description Worklist Application URL In the e-mails that are sent for tasks, the link to the Oracle BPM Worklist is read from this property. This element identifies the URL. Configuring this is useful if the custom Oracle BPM Worklist is built. The tag
PC_HW_TASK_ID_TAGin this URL is replaced with the task ID when constructing the URL for the e-mail.Pushback Assignee A task can be pushed back to the previous approver or previous initial assignees. The original assignees do not need to be the approver, as they may have reassigned the task, escalated the task, and so on. The possible values for this element are INITIAL_ASSIGNEES and APPROVER. Portal Realm Mapping Used when authenticating a user from an HTTP servlet request through the task query service method createContext(for example, when Oracle BPM Worklist runs in a single sign-on (SSO) environment). The HTTP servlet request does not carry information about the identity service realm to which the remote user belongs; this parameter is used to configure which realm to use to authenticate the user in an HTTP servlet request remote user.Task Auto Release Configuration When a task is assigned to a group, application role, or multiple users, a user must first acquire the task before working on it. Once the task is acquired, other users cannot work on the task. If a user acquires a task, but does not act on it, the task is eventually automatically released, allowing other users to acquire the task. This prevents a user from acquiring tasks, then forgetting to work on them. This prevents others from working on them. Task auto release enables you to configure the time period that elapses after a user acquires a task and before the system automatically releases the task and makes it available again to other users. The auto release durations can be configured as a default duration and as a percentage of the expiration duration of a given task. The auto release durations can be configured differently for tasks of different priority. For example, assume the task automatic release duration for priority 2 tasks is set to 50%, with a default duration of 12 hours. If a priority 2 task is set to expire in two days, the task is automatically released after one day (which is 50% of the expiration duration). If no expiration date is set for the task, then the task is automatically released after 12 hours (which is the default automatic release duration).
-
Make changes appropriate to your environment.
-
Click Apply.
-
If you want to configure advanced task service properties in the System MBean Browser, click More Workflow Taskservice Configuration Properties. See Step 9 of Section 18.1, "Configuring Human Workflow Notification Properties" for a list of some advanced properties that are displayed.
-
Make changes appropriate to your environment.
For more information about the task service and assignment service, see Oracle Fusion Middleware Developer's Guide for Oracle SOA Suite.
18.3 Configuring Oracle HTTP Server for Task Form Attachments
When adding an attachment to the task form through Oracle HTTP Server (OHS), the location, /ADFAttachmenthelper, must be included in the OHS configuration. For example, add the following to the mod_wl_ohs.config file of OHS, under instance_home/config/OHS/ohs_instance:
<Location /ADFAttachmentHelper>
SetHandler weblogic-handler
PathTrim /weblogic
ErrorPage http:/WEBLOGIC_HOME:WEBLOGIC_PORT/
</Location>
18.4 Configuring the Pluggable Notification Service
Custom notification service implementations can be plugged in and used instead of the default notification service providers. You can plug in a custom notification service for all channels or selectively for specific channels. For example, the notification service provides the ability to plug in an existing SMS implementation instead of the default SMS notification service.
18.4.1 Pluggable Notification Service Implementation
To plug in a notification service, perform one of the following tasks:
-
Implement interface
oracle.bpel.services.notification.ICustomNotificationService -
Extend the abstract class
oracle.bpel.services.notification.AbstractCustomNotificationServiceImpl.
This interface has methods for the following channels:
-
E-mail
-
Voice
-
SMS
-
Instant messaging (IM)
The plugged-in notification service can override the default providers for one or more channels. When the custom notification service is overriding the default implementation for a subset of channels, the methods corresponding to the other channels (channels that are not overridden) are not called by the notification service. Those methods can just return null. Alternatively, the implementation can extend the following abstract class:
oracle.bpel.services.notification.AbstractCustomNotificationServiceImpl
which provides empty implementations for each of the channels. In that case, the implementation can just extend the methods for the interested channels.
The implementation and its dependent classes must be available in the classpath of Oracle WebLogic Server.
18.4.2 Pluggable Notification Service Registration
Once the implementation is available, you register it in the System MBean Browser.
To register the pluggable notification service:
-
Log in to Oracle Enterprise Manager Fusion Middleware Control Console.
-
In the navigator, expand the SOA folder.
-
Right-click soa-infra, and select Administration > System Mbean Browser.
The System MBean Browser displays on the right side of the page.
-
Expand Application Defined MBeans > oracle.as.soainfra.config > Server: server_name > HWFMailerConfig > human-workflow.
-
Click the CustomNSDriverPropertyNames property on the right side of the page.
-
Record the values displayed by CustomNSDriverPropertyNames for the All, Voice, Email, Fax, Pager, SMS, and IM properties.
-
Click Return.
-
Click the Operations tab.
-
Click setCustomNSDriverPropertyValue.
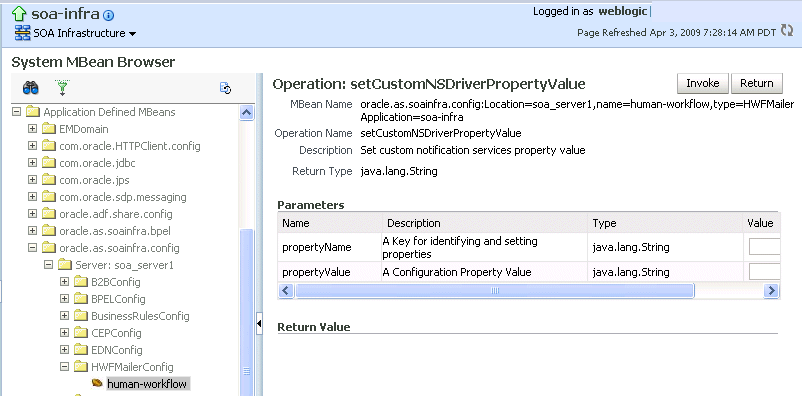
Description of the illustration hwf_plugnotif.gif
-
In the Value field for propertyName, enter one of the values you noted down for the All, Voice, Email, Fax, Pager, SMS, and IM properties on the CustomNSDriverPropertyNames page. Note the following details:
-
If you are overriding the default implementation for only the e-mail channel, use the Email value in the Value field for propertyName and the complete class name of your implementation in the Value field for propertyValue.
-
The override for other channels is configured the same way as the e-mail channel.
-
Using the value of the All property in the Value field for propertyName refers to an implementation for all specified channels.
-
-
In the Value field for propertyValue, provide the complete class name of your implementation.
-
Click Invoke.
-
Restart Oracle WebLogic Server.
18.5 Configuring Multiple Send Addresses
It may be necessary in some processes to distinguish e-mail notification based on the from address of the e-mail. For example, a human resources BPEL process sends e-mails with the from address set as HR@yourcompany.com, while a finance BPEL process sends e-mails with the from address set as finance@yourcompany.com.
To configure multiple send addresses:
-
Log in to Oracle Enterprise Manager Fusion Middleware Control Console.
-
In the navigator, expand the SOA folder.
-
Right-click soa-infra, and select Administration > System Mbean Browser.
The System MBean Browser displays on the right side of the page.
-
Expand Application Defined MBeans > oracle.as.soainfra.config > Server: server_name > HWFMailerConfig > human-workflow.
-
Under the Attributes tab, record the value of the ASNSDrivers attribute. By default, only the Default value is available.
-
Click Return.
-
Click the Operations tab.
-
Click setASNSDriver.
-
For propertyName, enter a value (for this example,
EmailFromAddress). -
For propertyValue, enter a value (for this example,
HR@yourcompany.com). -
For driverName, enter a value (for this example,
HR). -
Click Invoke.
-
Add as many accounts as the number of from addresses needed:
-
For propertyName, enter a value (for this example,
EmailFromAddress). -
For propertyValue, enter a value (for this example,
finance@yourdomain.com). -
For driverName, enter a value (for this example,
Finance).
-
-
Click Invoke.
The ASNSDriver attribute now shows all the accounts created in the previous steps and the getCustomNSDriverPropertyValue operation now shows the addresses being used for each of the drivers.
-
Using Oracle WebLogic Server Administration Console, install multiple Oracle User Messaging Service e-mail drivers, one for each from address.
-
Configure the e-mail drivers to use the required from address for sending outgoing e-mails.
-
In Oracle JDeveloper during design time, use
HRas the account name to configure an e-mail activity for an HR BPEL process andFinanceas the account name to configure an e-mail activity for the finance BPEL process.
18.6 Configuring Notification Retries
Oracle SOA Suite provides support for reliable notifications. The outbound notification creates a notification message with a unique notification ID and stores the message and unique ID in the dehydration store. It then enqueues this unique ID in the JMS queue and commits the transaction. A message-driven bean (MDB) listening on this queue dequeues the message and sends a notification to the user. If there is any notification failure, the notification retries three times. If the retries all fail, it marks this notification as errored.
18.7 Configuring the Identity Service
By default, the identity service uses the embedded LDAP server in Oracle WebLogic Server as the default authentication provider. You can, however, configure Oracle WebLogic to use an alternative authentication provider, such as Oracle Internet Directory, Microsoft Active Directory, or Sun iPlanet, along with the default authenticator.
This section describes how to add an authentication provider and create users and groups in the authentication provider using either Oracle WebLogic Administration Console or Oracle Directory Services Manager.
This section describes the following topics:
18.7.1 Adding an Authentication Provider
You can add an authentication provider to a security realm using Oracle WebLogic Server Administration Console.
To add an authentication provider:
-
Log in to the Oracle WebLogic Server Administration Console.
-
Click Security Realms in the Domain Structure pane, and click the name of a realm in the list (myrealm, for example).
-
Click Providers > Authentication.
The Authentication Providers page appears.
Figure 18-1 Security Realm Authentication Providers
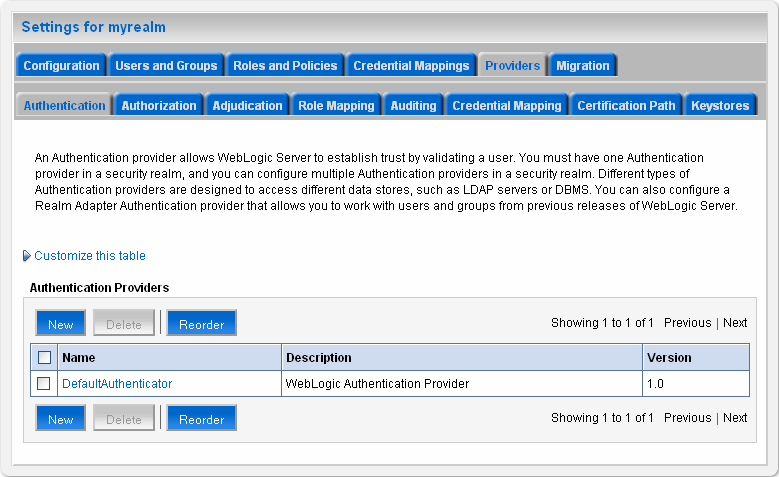
Description of "Figure 18-1 Security Realm Authentication Providers"
-
Click New to add a new authentication provider.
The Create a New Authentication Provider page appears.
Figure 18-2 Create a New Authentication Provider
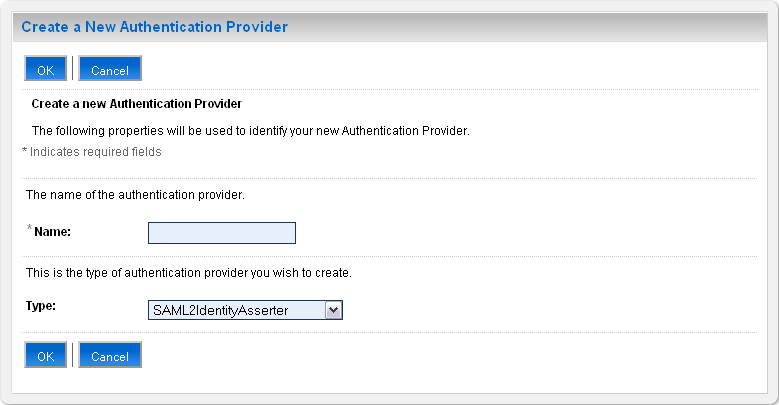
Description of "Figure 18-2 Create a New Authentication Provider"
-
Type a name for the provider in the Name field, choose the authenticator type using the Type drop-down list, and click OK.
For example, you can type
OIDAuthenticatoras the name and choose OracleInternetDirectoryAuthenticator as the type for a provider that authenticates users using the Oracle Internet Directory.Similarly, you can type a name and choose ActiveDirectoryAuthenticator, iPlanetAuthenticator, openLDAPAuthenticator, or NovellAuthenticator from the list to specify the corresponding authenticator.
Note:
When using Oracle Internet Directory as the authentication provider, you must set the orclsslinteropmode attribute to0(zero) using Oracle Directory Services Manager. See Section 18.7.3, "Configuring the Directory Service" for more information. -
On the Providers > Authentication page, click the authenticator that you just created.
The settings for the authentication provider appears.
Figure 18-3 Settings for the Authentication Provider
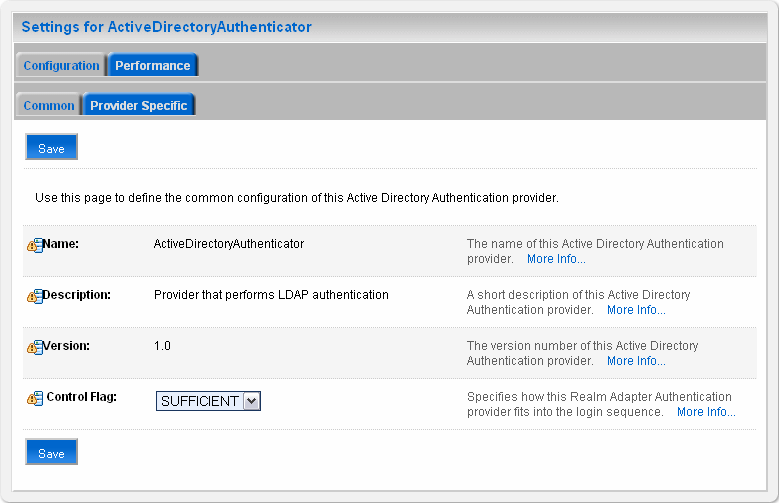
Description of "Figure 18-3 Settings for the Authentication Provider"
-
Choose SUFFICIENT from the Control Flag drop-down list, and click Save.
This specifies that if a user is authenticated successfully using this authenticator, WebLogic should accept the authentication and not continue to invoke any additional authenticators. If the authentication fails, Oracle WebLogic Server attempts to authenticate the user using the next authenticator in the list.
If you set the Control Flag to SUFFICIENT, ensure that all subsequent authenticators also have the Control Flag set to SUFFICIENT. Likewise, ensure that the Control Flag of the default authenticator is set to SUFFICIENT as well.
-
Click Provider Specific to enter the details for the authenticator server.
-
Enter the provider-specific information about the authentication provider, check the Use Retrieved User Name as Principal check box, and click Save.
Table 18-1 lists information you must specify. Use the default setting for the rest of the fields.
Table 18-1 Provider Specific Authentication Server Settings
Field Description Host
The host name or IP address on which the authenticator server is running.
Port
The port number on which the authenticator server is running.
Principal
The Distinguished Name (DN) of the authenticator server user that Oracle WebLogic Server should use when connecting to the server.
Credential
The credential (usually a password) used to connect to the authenticator server.
User Base DN
The base Distinguished Name (DN) of the tree in the LDAP directory that contains users.
Group Base DN
The base Distinguished Name (DN) of the tree in the LDAP directory that contains groups.
Use Retrieved User Name as Principal
Specifies whether to use the user name retrieved from the LDAP server as the principal in the subject.
User Name Attribute
The attribute of an LDAP user object class that specifies the name of the user (for example,
UID,CN,MAIL).If the user attribute being used is other than the default
usernameattribute in the LDAP server, add the following entries to the identity store instance in thejps-config.xmlfile:<property name="username.attr" value="desired_attr"/> <property name="user.login.attr" value="desired_attr"/>
where
desired_attrcan be one ofCN,UID, orMAIL. -
Click Security Realms > Providers > Authentication to return to the list of authentication providers.
-
Click Reorder.
The Reorder Authentication Providers page appears.
Figure 18-4 Reorder Authentication Providers
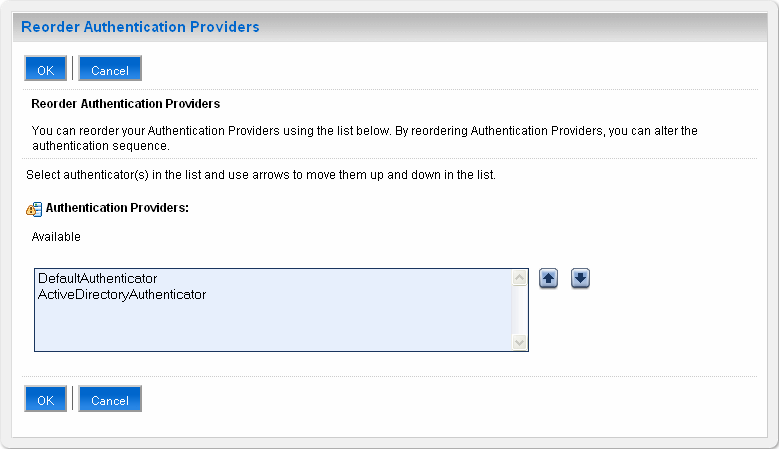
Description of "Figure 18-4 Reorder Authentication Providers"
-
Select the new authentication provider, click the Up arrow to move the provider to the top of the list, and click OK.
After reordering, the DefaultAuthenticator should appear at the bottom of the list. This action enables the system to handle logins as
weblogicthat are not typically in an LDAP directory, but still must be authenticated to start the server.Note that if multiple authentication providers are configured, authentication falls through the list of authenticators according to the control flags set. But the Java Portlet Specification (JPS) provides authorization against only the first entry in the list of providers.
18.7.2 Creating Users and Groups in the Authentication Provider
You can create users and groups in the authentication provider using either Oracle WebLogic Server Administration Console or Oracle Directory Services Manager.
18.7.2.1 Creating Users and Groups Using WebLogic Console
You can create users and groups for a specific provider, and define user and group membership, using the Oracle WebLogic Server Administration Console.
To create a user using WebLogic Console:
-
Log in to the Oracle WebLogic Console.
-
Click Security Realms in the Domain Structure pane, and click the name of a realm in the list (myrealm, for example).
-
Click Users and Groups > Users.
The Users page appears.
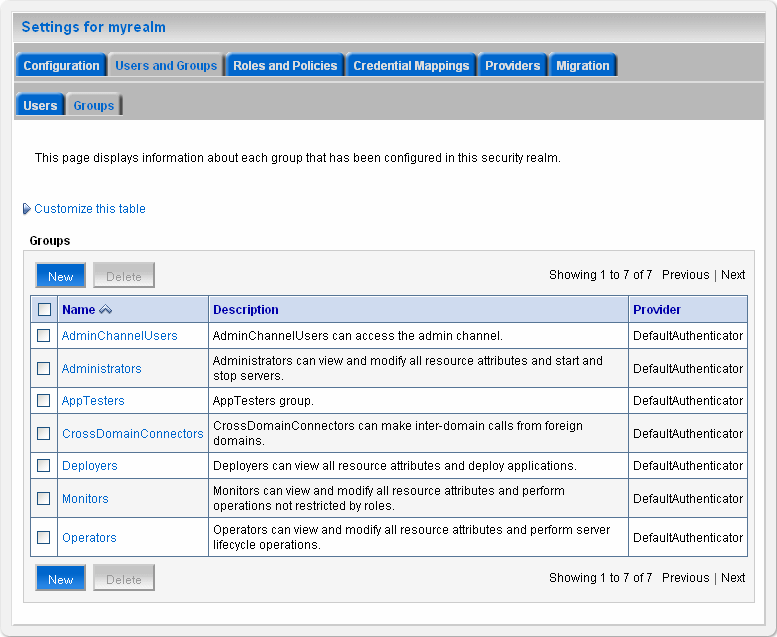
Figure 18-5 WebLogic Console Users and Groups
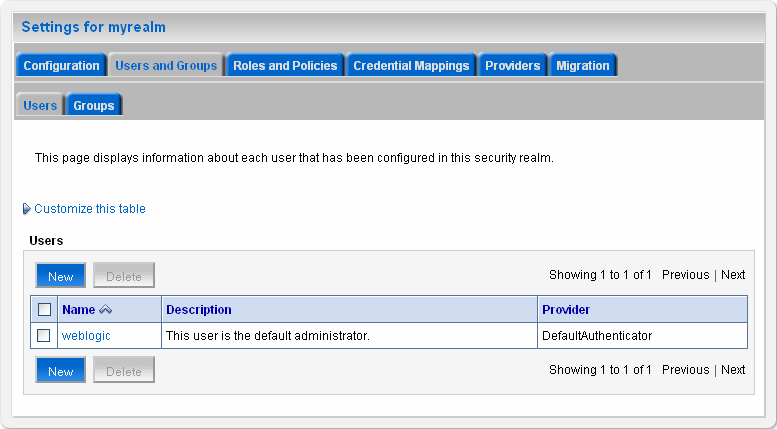
Description of "Figure 18-5 WebLogic Console Users and Groups"
-
Click New to add a new user. The Create a New User page appears.
-
Enter the required information about the user, and click OK.
Table 18-2 lists information you must specify.
Field Description Name
(Required) The name of the new user.
Description
A description of the new user.
Provider
The provider for the user.
Password
The password associated with the login name for the new user.
Confirm Password
Confirmation of the password.
The system creates the new user in the specified provider and shows the Users page. You can configure group membership for the user, as required.
-
To specify group membership for the user, click the newly-created user in the list. The settings for the new user page appear.
-
Click Groups to specify group membership for the user.
-
Select a group in the Available list and click the right arrow to move it to the Chosen list.
You can press Ctrl-Click to select multiple groups to move.
-
Click Save.
To create a group using WebLogic Console:
-
Click Users and Groups > Groups.
The Groups page appears.
-
Click New to add a new group. The Create a New Group page appears.
-
Enter the required information about the group, and click OK.
Table 18-3 lists information you must specify.
Field Description Name
(Required) The name of the new group.
Description
A description of the new group.
Provider
The provider for the group.
The system creates the new group in the specified provider and shows the Groups page. You can configure group membership for the group, as required.
-
To specify group membership for the group (specify parent groups), click the newly-created group in the list. The settings for the new group page appear.
-
Click Membership to add the group to other groups.
-
Select a parent group in the Available list and click the right arrow to move it to the Chosen list.
You can press Ctrl-Click to select multiple groups to move.
-
Click Save.
18.7.2.2 Creating Users and Groups Using Oracle Internet Directory
You can create users and groups using Oracle Internet Directory through the Oracle Directory Services Manager.
To connect to Oracle Internet Directory from the Oracle Directory Services Manager:
-
Launch the Oracle Directory Services Manager by navigating to the following URL using a Web browser:
http://host_name:port/odsm/faces/odsm.jspx
where
host_nameandportare the host name and the managed server port number on which Oracle Internet Directory is running. -
Click the Connect to a directory link and choose Create a New Connection in the drop-down menu. The New Connection dialog appears.
-
Select OID as the directory type, enter values in the required fields, and click Connect.
Table 18-4 lists information you can specify.
Field Description Name
The name of the connection.
Server
(Required) The host name or IP address of the system on which Oracle Internet Directory is running.
Port
(Required) The port number on the system on which Oracle Internet Directory is running.
SSL Enabled
Select to enable a Secure Sockets Layer (SSL) communication.
User Name
(Required) The user name used to log in to Oracle Internet Directory.
Password
(Required) The password associated with the user name.
Start Page
The start page after logging into Oracle Internet Directory.
The Oracle Directory Services Manager Home tab appears.
-
Click the Data Browser tab. You can use this tab to create and remove entries.
-
Click the Create a new entry button in the Data Tree pane. The Entry Properties page of the Create New Entry wizard appears.
-
Click the Add button to add the required object class for the domain. The Add Object Class dialog box appears.
-
Type the name of the object class. When the correct object class appears in the Name list, select it, and click OK.
-
Repeat Steps 2 and 3 to add all the required object classes for the domain. Generally, top, domain, and orclContainer are the object classes required for a domain.
-
Click Browse to choose the parent of the domain. The Select Distinguished Name (DN) Path dialog box appears.
Figure 18-7 Select Distinguished Name (DN) Path (Domain)
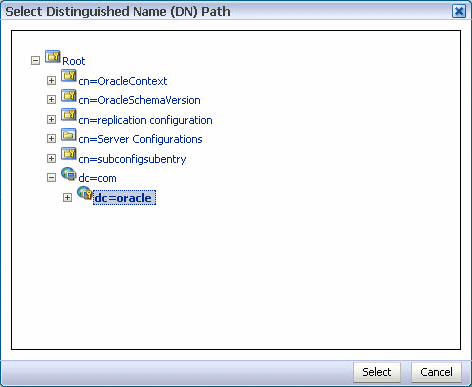
Description of "Figure 18-7 Select Distinguished Name (DN) Path (Domain)"
-
Select the parent of the domain and click Select. You can create a hierarchy of entries by selecting the appropriate parent domains.
-
Click Next in the Create New Entry dialog box. The Mandatory Properties page of the Create New Entry wizard appears.
-
Type and select values for the required fields, and click Next.
Table 18-5 lists information you can specify.
Table 18-5 Mandatory Properties (Domain)
Field Description dc
(Required) The domain component.
Relative Distinguished Name
(Required) The relative distinguished name of the user.
The Status page of the Create New Entry wizard appears.
-
Verify the status of the new domain, and click Finish to create the new domain.
-
Click the Create a new entry button in the Data Tree pane. The Entry Properties page of the Create New Entry wizard appears.
-
Click the Add button to add the required object class for the user. The Add Object Class dialog box appears.
-
Type the name of the object class. When the correct object class appears in the Name list, select it, and click OK.
-
Repeat Steps 2 and 3 to add all the required object classes for the user. Generally, top, person, inetorgperson, organizationalPerson, and orcluser are the object classes required for a user.
-
Click Browse to choose the parent of the user. The Select Distinguished Name (DN) Path dialog box appears.
Figure 18-8 Select Distinguished Name (DN) Path (User)
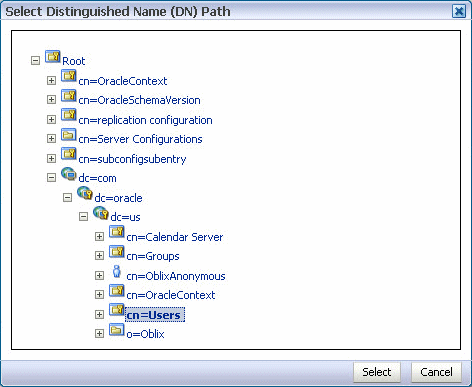
Description of "Figure 18-8 Select Distinguished Name (DN) Path (User)"
-
Select the parent of the user and click Select.
-
Click Next in the Create New Entry dialog box. The Mandatory Properties page of the Create New Entry wizard appears.
-
Type and select values for the required fields, and click Next.
Table 18-6 lists information you can specify.
Table 18-6 Mandatory Properties (User)
Field Description cn
(Required) The common name.
sn
(Required) The surname (last name).
Relative Distinguished Name
(Required) The relative distinguished name of the user.
The Status page of the Create New Entry wizard appears.
-
Verify the status of the new user, and click Finish to create the new user.
-
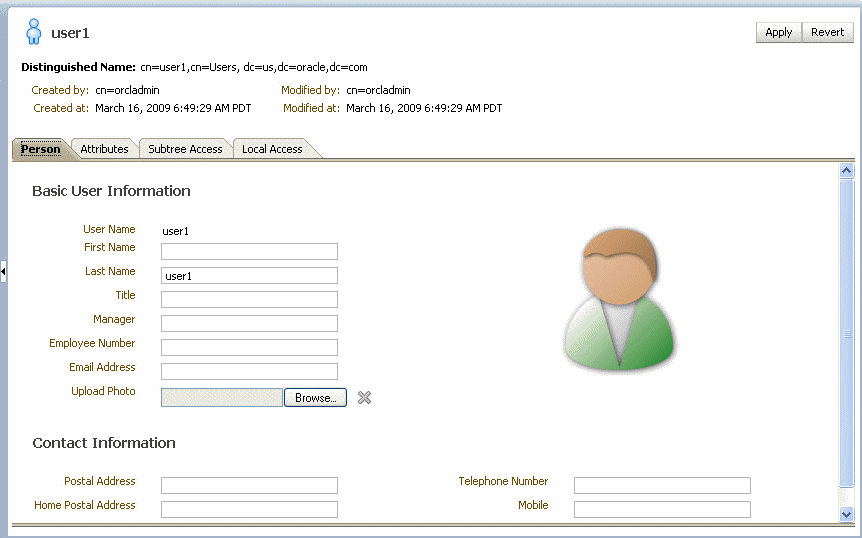
Click the entry for the newly-created user in the Data Tree pane. The Person tab for the user appears.
-
Enter details about the user, and click Apply.
-
Click the Create a new entry button in the Data Tree pane. The Entry Properties page of the Create New Entry wizard appears.
-
Click the Add button to add the required object class for the group. The Add Object Class dialog box appears.
-
Type the name of the object class. When the correct object class appears in the Name list, select it, and click OK.
-
Repeat Steps 2 and 3 to add all the required object classes for the group. Generally, top, groupOfUniqueNames, and orclGroup are the object classes required for a group.
-
Click Browse to choose the parent of the group. The Select Distinguished Name (DN) Path dialog box appears.
Figure 18-10 Select Distinguished Name (DN) Path (Group)
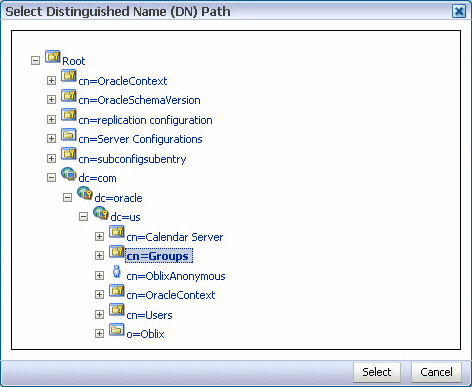
Description of "Figure 18-10 Select Distinguished Name (DN) Path (Group)"
-
Select the parent of the group and click Select.
-
Click Next in the Create New Entry dialog box. The Mandatory Properties page of the Create New Entry wizard appears.
-
Type and select values for the required fields, and click Next.
Table 18-7 lists information you can specify.
Table 18-7 Mandatory Properties
Field Description cn
(Required) The common name.
Relative Distinguished Name
(Required) The relative distinguished name of the group.
The Status page of the Create New Entry wizard appears.
-
Verify the status of the new group, and click Finish to create the new group.
-
Click the entry for the newly-created group in the Data Tree pane. The Group tab for the group appears.
Figure 18-11 Group Information: Group Tab
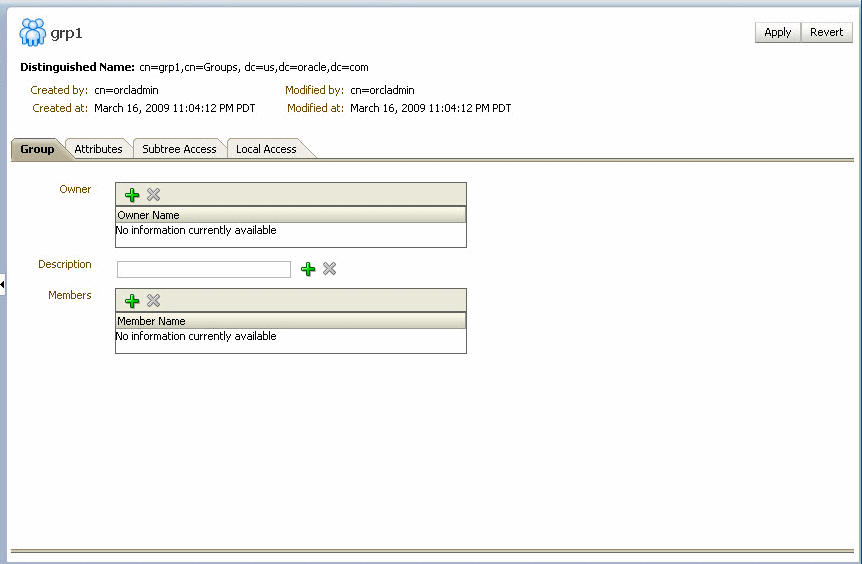
Description of "Figure 18-11 Group Information: Group Tab"
-
Specify details about the group, and click Apply.
-
Select an entry in the Data Tree pane.
-
Click the Delete this entry button in the Data Tree pane.
18.7.3 Configuring the Directory Service
When using Oracle Internet Directory as the authentication provider, you must set the orclsslinteropmode attribute to 0 (zero) using Oracle Directory Services Manager.
To configure the directory service:
-
Launch Oracle Directory Services Manager and choose an Oracle Internet Directory connection using the drop-down list.
-
Click the Data Browser tab.
-
Expand the cn=subconfigsubentry > cn=osdldapd > cn=oid1 nodes.
Figure 18-12 Oracle Directory Services Manager Data Browser
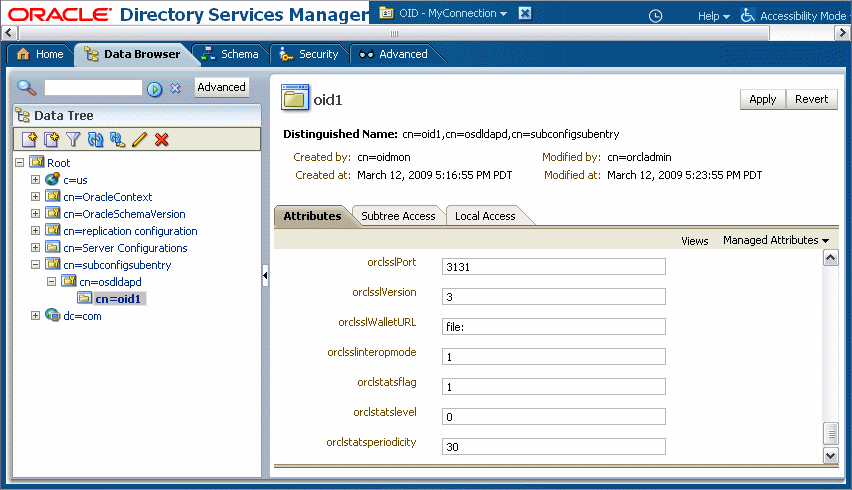
Description of "Figure 18-12 Oracle Directory Services Manager Data Browser"
-
In the Attributes tab, set the orclsslinteropmode attribute to
0. -
Click the Apply button.
18.8 Seeding Users, Groups, and Application Roles using LDAP Tools
This section provides an overview of the procedures required for seeding users, groups, and application roles with LDAP tools.
When you create a task, you assign humans to participate in and act upon the task. Participants can perform actions upon tasks during run time from Oracle BPM Worklist, such as approving a vacation request, rejecting a purchase order, providing feedback on a help desk request, or some other action. There are three types of participants:
-
Users
-
Groups
-
Application roles
For more information, see Oracle Fusion Middleware Developer's Guide for Oracle SOA Suite.
18.8.1 Changing the Default Password in the Embedded LDAP Server
The password credential is accessible from the Oracle WebLogic Server Administration Console by selecting Security > Embedded LDAP for your domain.
For instructions on changing the default password credential, see Chapter 9, "Managing the Embedded LDAP Server" of Oracle Fusion Middleware Securing Oracle WebLogic Server.
18.8.2 Seeding Users or Groups through the LDAP Browser
-
Start an LDAP browser (for example, openLdap browser, ldapbrowser, jXplorer, and so on). See the documentation for your browser for instructions.
-
Connect to the LDAP server by providing the host name, port number on which the server is running, and the administration user credentials with which to log in.
-
For Embedded LDAP:
-
The default managed server port number is
7001. -
The administration credential username is
cn=admin. -
The administration credential password is what you set in Section 18.8.1, "Changing the Default Password in the Embedded LDAP Server."
-
-
For OIDm:
-
The default port number is
3060. -
The administration username is
cn=orcladmin. -
The administration password is the password for the LDAP server.
-
-
-
Seed a user or group through the browser by performing the following steps:
-
Select a parent under which to add a user or group.
-
Select the Edit menu and choose an appropriate option to add a new entry.
-
Enter all required attribute values for the entry.
-
-
Seed users or groups through the LDIF file by performing the following steps:
-
Select the domain under which to seed the users or groups.
-
Select the LDIF menu and choose to import an LDIF file.
-
In the Import LDIF File dialog, browse for and select the LDIF file and click Import.
Similarly, the users or groups seeded on the LDAP server can be exported to an LDIF file by selecting the Export option from the LDIF menu.
-
-
Add attributes to the users or groups by performing the following steps:
-
Select an entry for which to add a new attribute.
-
Right-click and choose the option to add a new attribute.
-
In the Add Attribute dialog, provide the name and value of the attribute.
You can only add attributes that are defined in the LDAP server schema.
-
-
Delete attributes for users or groups by performing the following steps:
-
Select an entry for which to delete a new attribute.
-
Select an attribute from the list of attributes and delete it.
-
18.8.3 Seeding Application Roles using WLST Scripts
For instructions on using the WebLogic Scripting Tool (WLST) to seed application roles, see Chapter 4, "Infrastructure Security Custom WLST Commands" of Oracle Fusion Middleware WebLogic Scripting Tool Command Reference.
18.8.4 Seeding Application Roles in Oracle Enterprise Manager Fusion Middleware Control Console
-
In the navigator, select the appropriate Oracle WebLogic Server under WebLogic Domain > Farm_Domain_name.
-
In the right pane, select WebLogic Domain -> Security -> Application Roles.
-
Create an application role by performing the following steps:
-
Select the Create option in the Application Roles page.
The Create Application Role page appears.
-
In the Application list, select the application name (server_name/soa_infra) under which to create a role.
-
Enter the role name, display name, and description for the application role.
-
Add members by selecting Add Role in the Roles section and Add User in the Users section.
-
Click OK to create the application role.
-
-
Edit application roles by performing the following steps:
-
In the Application list of the Search section of the Application Roles page, select an appropriate application.
This action lists all the application roles created for that application.
-
To the right of the Role Name list, click the Search icon.
-
Select the application role to edit.
-
Click Edit.
-
Add or delete roles in the Roles section and Users section of the Edit Application Role page.
-
Click OK.
-
-
Delete application roles by performing the following steps:
-
In the Application list of the Search section of the Application Roles page, select an appropriate application.
This action lists all the application roles created for that application.
-
Select the application role to delete.
-
Click the Delete button to delete the application role.
-
Click Yes in the Confirmation dialog.
-