| Oracle® Fusion Middleware Administrator's Guide for Oracle Access Manager with Oracle Security Token Service 11g Release 1 (11.1.1) Part Number E15478-05 |
|
|
View PDF |
| Oracle® Fusion Middleware Administrator's Guide for Oracle Access Manager with Oracle Security Token Service 11g Release 1 (11.1.1) Part Number E15478-05 |
|
|
View PDF |
Internal communication among Oracle Access Manager 11g and its dependencies uses Internet Protocol Version 4 (IPv4). However, external communication is supported in IPv6 with Oracle HTTP Server with the mod_wl_ohs plug-in.
This appendix provides the following topics:
Regardless of the manner in which you plan to use Oracle Access Manager with IPv6 clients, the following tasks should be completed before you start activities herein:
An Oracle HTTP Server instance must be installed to act as a reverse proxy to the Web server (required for 10g and 11g Webgates).
Oracle Access Manager must be installed as described in Oracle Fusion Middleware Installation Guide for Oracle Identity Management
See Also:
"Using IPV6" in the chapter on changing network configurations in the Oracle Fusion Middleware Administrator's Guide for details about configuring OAM 10g Webgates for IPv6 clients.
Oracle HTTP Server Administrator's Guide
Among other features, IPv6 supports a larger address space (128 bits) than IPv4 (32 bits), providing an exponential increase in the number of computers that can be addressable on the Web. IPv6 is enabled with Oracle HTTP Server with the mod_wl_ohs plug-in.
The OAM Server and Webgate (10g and 11g) are IPv4 only. However, an IPv6 client can access Webgate on IPv4 through reverse proxy on an IPv4/IPv6 dual-stack host.
Note:
You can configure Oracle Access Manager 11g to work with clients that support IPv6 by setting up a reverse proxy server.The supported topologies for OAM 11g with IPV4/IPV6 are outlined in following lists.
Topology
Webgate 10g or Webgate 11g +protected applications on IPv4 protocol host
OHS reverse proxy on dual-stack host
Client on IPv6 protocol host
OAM Server Proxy
IPv6 client can access WebgateWebgate10g or Webgate 11g through OHS reverse proxy.
Note:
When the OAM Server is not running, login to the WebLogic Administration Console is successful,. However, when OAM Server is running, login to the WebLogic Administration Console is redirected to the OAM Server and authentication fails because the Identity Store fails to initialize. IPV6 for the Identity Store is not yet supported.For more information, see:
For a look at all supported topologies, including configuration for OAM 10g Webgates, see "Using IPV6" in the chapter on changing network configurations in the Oracle Fusion Middleware Administrator's Guide
Figure G-1 illustrates configuration with a single IPv6 to IPv4 Proxy (host configured myssohost and myapphost can use separate proxies).
With OAM 11g, the virtual host name must be specified as a host name, for example, myapphost.foo.com, not as an IP address. The redirect host name, for example, myssohost.foo.com must also be specified as a host name and not an IP address. The IPv6 address cannot be specified in a Webgate registration.
Note:
With OAM 11g, there is no concept of an authenticating Webgate or a resource Webgate. Instead, redirection always goes to OAM Server whether you have 11g Webgates or 10g Webgates.Figure G-1 IPv6 with OAM 11g and Challenge Redirect
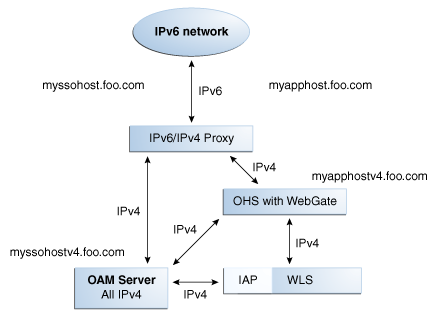
As illustrated in Figure G-1, the IPv6 network communicates with the IPv6/IPv4 proxy, which in turn communicates with the Oracle HTTP Server using IPv4. Webgate, Oracle Access Manager Server, and Oracle WebLogic Server with the Identity Asserter all communicate with each other using IPV4.
You should be able to access the application from a browser on the IPv6 network to the IPv6 server host (myapphost.foo.com) and have login with redirect to IPv6 myssohost.foo.com.
The following considerations apply to each intended use scenario:
IP validation does not work by default. To enable IP validation, you must add the IP address of the Proxy server as the Webgate's IPValidationException parameter value in the Oracle Access Manager Console.
See Also:
"Single Sign-On with OAM 11g"IP address-based authorization does not work because all requests come through one IP (proxy IP) that would not serve its purpose.
ipValidationException is required if IPValidation is On (parameter "ipValidation"=1). However, you cannot add this parameter using either the Oracle Access Manager Console or the remote registration tool. Instead, you must add the proxy's IP as single-valued user-defined parameter for the proxy in the oam-config.xml file.
OAM 10g provided a resource Webgate configuration (that redirects) and an Authenticating Webgate configuration. The OAM 11g credential collector replaces and performs the function of an OAM 10g authenticating Webgate.
Note:
With OAM 11g, the 10g Webgate always redirects to the OAM 11g credential collector which acts like the earlier "authenticating" Webgate.In this configuration you have multiple proxies: for example a separate proxy for the OAM Server and another proxy for the Webgate.
You can access the application from a browser on the IPv4 network directly to an IPv4 server host name with a login redirect to an IPv6 host. For example:
Note:
You cannot use the IPv6 proxy name as the Preferred HTTP host in a Webgate registration.With OAM 11g, the ProxyRequests parameter must be "On" because Webgates (11g or 10g) always redirect to obrareq.cgi. This directive makes the proxy act as a forward proxy.
The Preferred http host should be set to the host:port of the Web server hosting the Webgate (or SERVER_NAME if the Web server hosting the Webgate is configured for virtual hosting).
If IPValidation is ON, IPValidationException must be added for the proxy.
If reverse proxy is configured to perform SSL termination, then the user-defined Webgate proxySSLHeaderVar parameter must be defined during remote registration. As described in Table 10-4, "Elements Common to Remote Registration Requests", this parameter is used when the Webgate is located behind a reverse proxy. The value of the proxySSLHeaderVar parameter defines the name of the header variable the proxy must set. The value of the header variable must be "ssl" or "nonssl". If the header variable is not set, the SSL state is decided by the SSL state of the current Web server. Syntax is as follows:
<name>proxySSLHeaderVar</name> <value>IS_SSL</value>
Modify the Load Balancing Router (reverse proxy Web server) settings to insert an HTTP header string that sets the IS_SSL value to ssl. For example, in the F5 load balancer, in Advanced Proxy Settings, you add the HTTP header string IS_SSL:ssl
In the following procedure, OHS_host and OHS_port are the host name and port of the actual Oracle HTTP Server that is configured for Webgate. Be sure to use values for your own environment. Your values will be different.
Prerequisites
Install and configure OHS Web server for reverse proxy. Ensure that you have a separate Web server instance for each proxy.
To configure IPv6 with a separate proxy for OAM 11g and Webgates
Enable mod_proxy to OAM 11g Server and Webgate: Configure Oracle HTTP Server 11g Release 1 (11.1.1) or any other server for multiple proxies, as follows:
Stop Oracle HTTP Server for the corresponding proxy instance with the following command:
opmnctl stopproc ias-component=<OHS instance name>
Edit the following file of the OHS instance for the corresponding proxy:
UNIX: ORACLE_INSTANCE/config/OHS/ohs_name1/httpd.conf Windows: ORACLE_INSTANCE\config\OHS\ohs_name1\httpd.conf
Proxy to OAM 11g Server: Append the following information for your environment to the httpd.conf file to enable mod_proxy. For example:
<IfModule mod_proxy.c> ProxyRequests On ProxyPreserveHost On ProxyPass / http://<oam_server_host:port>/ ProxyPassReverse / http://<oam_server_host:port>/ </IfModule>
Reverse Proxy to 11g Webgate: Append information for your environment to the httpd.conf file to enable mod_proxy, as follows:
<IfModule mod_proxy.c> ProxyRequests On ProxyPreserveHost On ProxyPass / http://<webgate_OHS_host:port>/ ProxyPassReverse / http://<webgate_OHS_host:port>/ </IfModule>
Restart Oracle HTTP Server with the following command:
opmnctl startproc ias-component=<OHS instance name>
In the Authentication Scheme, change the Challenge Redirect URL to http://<oam_server_proxy_host:port>/oam/server.
Set the Preferred HTTP host for each Webgate to the host:port of the Web server hosting the Webgate (or SERVER_NAME if the Web server hosting Webgate is configured for virtual hosting):
Note:
You can specify Preferred HTTP host using the appropriate field of the *Request.xml input during remote registration or using the Oracle Access Manager Console as shown here. See also, "About Remote Registration Request Files".Log in to Oracle Access Manager Console. For example:
http://hostname:port/oamconsole
Click System Configuration, Access Manager Settings, SSO Agents, OAM Agents.
Find the agent and click its name in the Search Results table to display the registration page.
Preferred HTTP Host: The name of the Oracle HTTP Server Web server that is configured for this Webgate. For instance, a Webgate deployed on myapphostv4.foo.com must use myapphostv4.foo.com as the Preferred HTTP host.
Click Apply.
Repeat for each Webgate and specify name of the Oracle HTTP Server Web server that is configured for this Webgate.
IPValidationException: If IPValidation is On (parameter "ipValidation"=1), add the proxy's IP as single-valued user-defined parameter for the proxy in the oam-config.xml file.
Stop all OAM Servers and the AdminServer.
Locate the oam-config.xml in the following path:
<WLS_DOMAIN_HOME>/config/fmwconfig/oamconfig.xml
Enter the following information:
<Setting Name="ipValidationExceptions"Type="xsd:string"> 10.1.1.1</Setting>
Save the file.
Restart the OAM Servers and AdminServer.
If reverse proxy is configured to perform SSL termination, the Webgate user-defined "proxySSLHeaderVar" parameter must be set (default is "IS_SSL"). Please modify the Load Balancing Router (reverse proxy Web server) settings to insert an HTTP header string that sets the IS_SSL value to ssl. For example, in the F5 load balancer, in Advanced Proxy Settings, you add the HTTP header string IS_SSL:ssl.