Oracle Fusion applications contain preseeded job roles, duty roles, and object privileges. The same set of job roles generally apply across all Oracle Fusion applications, as well as any Oracle Business Intelligence products deployed in the same environment; for example: Oracle BI EE, BI Applications, Oracle Essbase, Oracle Data Integrator (ODI), Oracle Business Intelligence Publisher, and Real Time Decisions (RTD).
Users can define user names and passwords, grant predefined job roles to users, and define new privileges for customer-specific data. Users can also define new job roles and grant preseeded job roles to them and alter preseeded job roles by modifying duty role assignments. These tasks modify the role hierarchy, and are performed through Oracle® Platform Security Services.
Note: | This is primarily the extent to which security is modified for the Oracle Fusion BI security model. Normally no code or other implementation artifacts are modified. |
Many administrative aspects of Transactional Business Intelligence security are performed by application administrators. They consist of adjusting preseeded content, possibly adding new content, and provisioning user accounts and passwords. The following sections detail the tasks and dependencies for accomplishing this as part of the postinstallation setup of any deployed Oracle Fusion BI system.
Within the Oracle Fusion BI Security model, object security and data security are based on duty roles and indirectly on job roles. Because Transactional Business Intelligence view objects directly access the OLTP tables of the Oracle Fusion Applications, they must respect the data security constraints on these tables configured by the Application administrator. There are three key aspects of Oracle Fusion BI Security for Transactional Business Intelligence that affect the administration of Transactional Business Intelligence security. These are Oracle Fusion OLTP Function Security, Oracle Fusion OLTP Data Security, and Transactional Business Intelligence Function Security, respectively. OLTP Function Security has no direct applicability to Transactional Business Intelligence, while Transactional Business Intelligence data security is effectively the same as OLTP Data Security, and Transactional Business Intelligence Function Security is specific only to Transactional Business Intelligence.
 To ensure users are properly enabled for baseline BI reporting access, the following steps may need to be performed within a given Fusion Application:
To ensure users are properly enabled for baseline BI reporting access, the following steps may need to be performed within a given Fusion Application:
Search for an appropriate job role that should be used to authorize BI reporting access via OTBI (that is, an appropriate job for the user that directly or indirectly inherits from FBI_TRANSACTIONAL_BUSINESS_INTELLIGENCE_WORKER, as mentioned above).
In the Public Security Profile region, open the Person Security Profiles list of values and select View All Workers.
For more detailed information for a specific Fusion Application, refer to the help topics for that application.
For a comparison, a parallel abstract job role, OBIA_BUSINESS_INTELLIGENCE_APPLICATIONS_WORKER, is similarly defined for BI Applications. The following figure illustrates the inheritance relationships between the abstract job role and Transactional Business Intelligence content duty roles, with example job and duty names in parentheses.
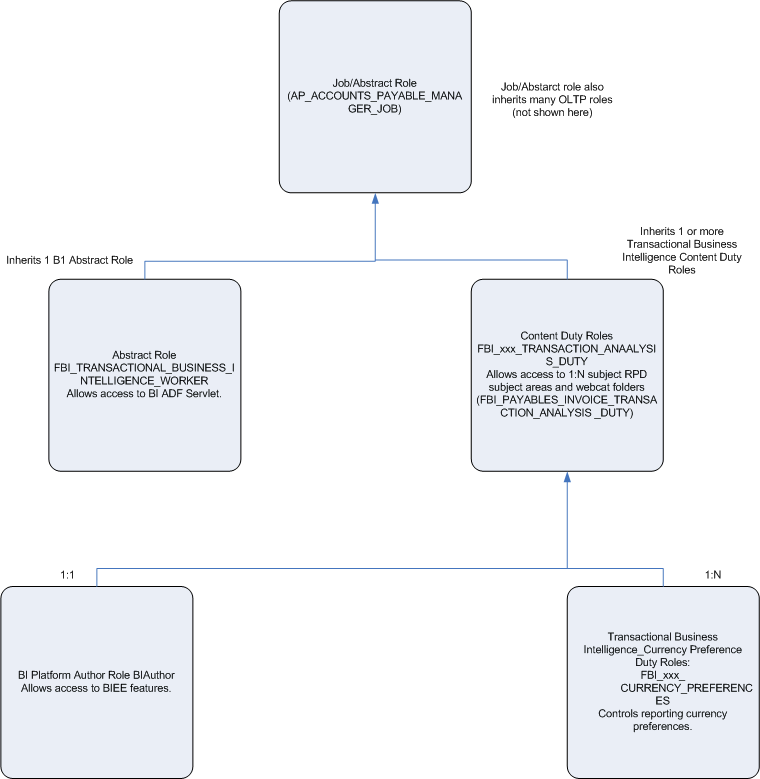
The following sections describe each role in varying detail, depending on its relevance to Transactional Business Intelligence security administration.