1 Understanding RADIUS Manager
This chapter provides a view of Oracle Communications Billing and Revenue Management (BRM) RADIUS Manager. Anyone who installs, configures, administers, or customizes RADIUS Manager should read this chapter.
Important:
RADIUS Manager is an optional component, not part of base BRM.Note:
Support for RADIUS Manager is added in BRM 7.5 Patch Set 9.Before using RADIUS Manager to set up a RADIUS configuration, you should be familiar with the RFC 2865: Remote Authentication Dial In User Service (RADIUS) and RFC 2866: RADIUS Accounting.
Important:
RADIUS Manager is not fully compliant with RFC 2865 and 2866. Only some of the RFC 2865 and 2866 features are supported. However, to meet specific business requirements, you can modify RADIUS Manager policy opcodes and write custom RADIUS modules to add functionality. See "Customizing RADIUS Manager Opcodes" and "Creating Custom Modules".About the RADIUS Protocol
The RADIUS protocol is an industry standard protocol for authentication, authorization, and accounting (AAA). Terminal servers or Network Access Server (NAS) use the RADIUS protocol to communicate AAA requests to, and return results from, a database of customer information.
RADIUS Manager uses the RADIUS protocol to provide AAA services in the BRM environment.
What You Can Do with RADIUS Manager
You use RADIUS Manager to perform the authentication, authorization and accounting services required when customers use your terminal server or Network Access Server (NAS) to connect to BRM.
RADIUS Manager performs these tasks:
-
Authentication: Verifying a customers identity by checking the user name and password
-
Authorization: Verifying a customers privileges for accessing the requested services
-
Accounting: Tracking when customers log in and log out, and the duration of the sessions.
Note:
When discussing RADIUS Manager, the term accounting refers to tracking customer usage.
How RADIUS Manager Works
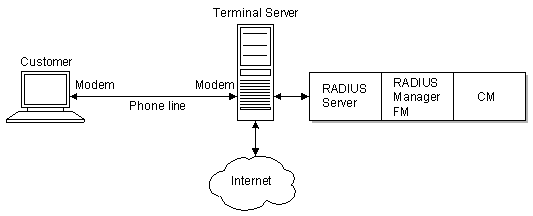
An organization connects a terminal server or Network Access Server (NAS), and the terminal server communicates with RADIUS Manager, as shown in Figure 1-1. Terminal servers authenticate incoming connections, authorize customers, then (if enabled) start accounting. To perform these operations, the NAS uses the RADIUS protocol to communicate with the pin_radiusd daemon. The pin_radiusd daemon accesses your BRM database. See "pin_radiusd_sig".
The RADIUS protocol can authorize access requests to:
-
BRM databases
-
Text-based user files
-
UNIX password files
-
iPass databases
-
Proxy databases
-
VPDN databases
RADIUS Manager Features and Functionality
You can perform these tasks with RADIUS Manager:
-
Custom RADIUS settings: You can customize your configuration of RADIUS Manager by setting the IP listen ports, debug options, data dictionary, vendor specific attributes (VSAs), number of threads, queue size, client list, secret, default return attributes, and configuration macros. For information on using these settings, see "Configuring RADIUS Manager".
-
Define the RADIUS workflow using general purpose modules: RADIUS Manager provides a variety of standard modules to handle most RADIUS requests. Use these modules to add or remove functionality without rebuilding your entire RADIUS server. For information about using modules, see "Understanding RADIUS Manager Modules".
-
Create custom modules: You can also add new functionality to RADIUS Manager by writing a custom module and editing the appropriate configuration files. For information on creating custom modules, see "Creating Custom Modules".
-
Authentication and authorization methods: You can use one or more authentication methods with your RADIUS configuration such as plain text or UNIX password authentication. For information, see "Using the Authentication and Authorization Modules".
-
Support proxy servers: RADIUS Manager supports the ability to forward (proxy) incoming RADIUS requests to other RADIUS servers. Forwarding requests to other servers can help you balance traffic flow, or allow you to use external servers for remote authentication and authorization. For information, see "Using the Proxy Module to Forward Incoming Requests to an External RADIUS Server".
-
Log RADIUS requests: Two methods for logging RADIUS requests are provided with RADIUS Manager. RADIUS requests can be logged to plain text log files or you can create custom CDRs. For information, see "Logging RADIUS Requests".
-
Support a Virtual Private RADIUS Network (VPDN): Use a Virtual Private RADIUS Network (VPDN) to support a secure RADIUS network connection between traveling users and corporate local area networks by using public IP networks. For information, see "Using a Virtual Private Dialup Network (VPDN)".
-
Support iPass roaming: RADIUS Manager supports iPass roaming authentication. This allows users to connect to corporate networks by using the Internet instead of using more expensive telephone line connections.For information, see "Setting Up iPass Roaming".
-
Dynamic reconfiguration: Use Dynamic reconfiguration to reconfigure almost any aspect of the RADIUS server without stopping operation. Dynamic reconfiguration is a primary benefits of RADIUS Manager architecture. You can reconfigure your RADIUS server by modifying the configuration file, and then sending a reconfiguration event to the server. For information, see "Reconfiguring Your RADIUS Server without Stopping Operation".
How RADIUS Manager Performs Authentication and Authorization
RADIUS Manager uses the following opcodes for authenticating and authorizing customers:
-
PCM_OP_TERM_IP_DIALUP_AUTHENTICATE authenticates a user.
This opcode verifies a user's login and password. If a password is passed in to this opcode, it calls PCM_OP_ACT_FIND_VERIFY and PCM_OP_ACT_POL_SPEC_VERIFY to authenticate the password. If no password is passed in, this opcode assumes that CHAP authorization is used and it returns the unencrypted password for verification by the calling program.
-
PCM_OP_TERM_IP_DIALUP_AUTHORIZE assembles information from the NAS and a user's account, and authorizes the user. It calls the PCM_OP_TERM_POL_AUTHORIZE policy opcode. You can customize the PCM_OP_TERM_POL_AUTHORIZE to calculate maximum authorized charges for prepaid rating.
How RADIUS Manager Performs Accounting
RADIUS Manager uses the following opcodes for accounting:
-
PCM_OP_TERM_IP_DIALUP_ACCOUNTING_ON enables RADIUS Manager to tell BRM that it is ready for service. RADIUS Manager can be configured to mark the start of accounting by using the RADIUS protocol to handle Accounting-On requests. When BRM receives an Accounting-On request, it closes any open account associated with that RADIUS Manager opened before RADIUS Manager indicated it was active.
-
PCM_OP_TERM_IP_DIALUP_ACCOUNTING_OFF records the end of accounting. The Terminal Server can be configured to mark the end of accounting by the use of the RADIUS protocol to handle Accounting-Off requests. This feature allows the Terminal Server to communicate with BRM that it is going out of service. When BRM receives an Accounting-Off request it closes all accounts associated with that Terminal Server so that accounts are not left open if the Terminal Server is going out of service.
-
PCM_OP_TERM_IP_DIALUP_START_ACCOUNTING records the start of a previously authenticated IP dialup session.
This opcode calls PCM_OP_ACT_FIND to find the account. It then searches for current sessions and does one of the following actions:
-
If a session exists and is a duplicate, no new session is created.
-
If a session exists but is not a duplicate, the existing session is closed as an orphan session.
-
If no session exists, calls PCM_OP_ACT_START_SESSION to start a new session.
-
-
PCM_OP_TERM_IP_DIALUP_UPDATE_ACCOUNTING updates a previously started IP dialup session.
-
PCM_OP_TERM_IP_DIALUP_STOP_ACCOUNTING closes out a previously started IP dialup session.
This opcode calls PCM_OP_ACT_FIND to find the account. It then searches for current sessions and does one of the following actions:
-
If more than one session is found, returns an error.
-
If a session is open, or if a session was orphaned, closes the session.
-
If no session is found, creates and closes a session.
-
Customizing RADIUS Manager Opcodes
Use the following opcodes to customize RADIUS Manager:
-
Use the PCM_OP_TERM_POL_ACCOUNTING policy opcode to set the event type (such as /event/session/dialup/ascend) and extract extra fields from PIN_FLD_ARGS and PIN_FLD_INHERITED_INFO. You can then add these fields to an extended /event/session/dialup event.
The default implementation does nothing.
PCM_OP_TERM_IP_DIALUP_START_ACCOUNTING, PCM_OP_TERM_IP_DIALUP_STOP_ACCOUNTING, and PCM_OP_TERM_IP_DIALUP_UPDATE_ACCOUNTING call this opcode.
-
Use the PCM_OP_TERM_POL_AUTHORIZE policy opcode to merge attributes from the NAS and a user's account into a list to be returned to the NAS.
-
Use the PCM_OP_TERM_POL_REVERSE_IP policy opcode to find the user of a given IP address.
This opcode maps the IP address to the relevant account and service objects. It finds open event session for given IP address and returns user information based on that session.