2 Performing a Secure BRM Installation
This chapter describes recommended installation steps for Oracle Communications Billing and Revenue Management (BRM).
For information about installing BRM, see BRM Installation Guide.
Pre-Installation Tasks
Perform the following pre-installation tasks:
-
The target operating system for BRM should have a default configuration, with the following differences:
-
Do not disable X Windows. It is required for local administration and is useful for troubleshooting.
-
Enable remote console access to run various operational processes such as billing and reporting. Do not use Telnet or rlogin, which do not encrypt passwords.
-
Do not disable SSH. Use SSH for remote console access to prevent password sniffing.
-
Disable file transfer protocol (FTP) or other remote file transfer services if there are no operations requiring them. For example, if there are no usage records, you do not need file transfer services enabled. If file transfer services are required, use secure FTP (SFTP) instead of FTP.
-
By default, the application uses the following ports. Ensure that iptables is configured to allow traffic to these ports and that any unused ports are closed:
22 both directions - used for SSH access.
80 both directions - if using HTTP.
443 both directions - if using HTTPS.
-
Further ports will need to be opened depending upon the ports specified for BRM during the installation process.
-
-
Configure Oracle Database advanced security encryption and integrity algorithms for a secure connection from the installer. See the Oracle Database documentation for advanced security configuration parameters. This is required for the BRM installer to make a secured (encrypted) database connection over the network. For more details, see Oracle Database Advanced Security Administrator's Guide at:
-
Install only the required components. This is true of both the BRM components and any third-party software that is required, such as the operating system and the database. This can be achieved by either carrying out a custom install and only selecting the required components or by removing any extraneous components as a post-installation step.
-
All third-party software should be installed following the security advice given by the vendor. In particular, default values for data such as user names, passwords, and port numbers should be avoided if possible by either selecting different values during the install or immediately changing the values as a post-installation step.
Installing BRM Securely
Follow the steps in BRM Installation Guide to install BRM. However, the port numbers, user name, password, and database SID should be changed from the default values.
The user name selected must be for an account that is used only for BRM and does not have unnecessary privileges for any other software. In particular, the account should not have root access privileges.
Post-Installation Tasks
Perform the following tasks after installing BRM:
Lock and Expire Default User Accounts
Oracle Database installs with many default (preset) database server user accounts. Upon the successful creation of a database server instance, the Database Configuration Assistant automatically locks and expires most of the default database user accounts.
Note:
If you use Oracle Universal Installer or the Database Configuration Assistant, you are prompted for new SYS and SYSTEM passwords, and the defaults change_on_install or manager are not accepted.After the database is installed, lock the SYS and SYSTEM accounts, and use AS SYSDBA for administrator access. Specify administrative passwords individually.
This account (AS SYSDBA) tracks the operating system user name, maintaining accountability. If you need access only for database startup and shutdown, use AS SYSOPER instead. SYSOPER has fewer administrative privileges than SYS, but enough to perform basic operations such as startup, shutdown, mount, backup, archive, and recover.
Change Default User Passwords
Security is most easily broken when a default database server user account still has a default password even after installation. The following steps fix this:
-
Change the default passwords of administrative users immediately after installing the database server.
-
Change the default password of the root customer service representative's (CSR's) account (user name root-0.0.0.1) immediately after installation.
-
In any Oracle environment (production or test), assign strong, secure passwords to the SYS and SYSTEM user accounts immediately upon successful installation of the database server. Under no circumstances should the passwords for SYS and SYSTEM retain their default values. Similarly, for production environments, do not use default passwords for any administrative accounts, including SYSMAN and DBSNMP.
-
In any Oracle development or test environment that is using real-world data for analysis, assign the same level of security as a production environment.
Use Strong Passwords for BRM User Schema
BRM requires one or more database users and database schema to store subscriber data. You must assign unique and complex passwords for each user and grant enough database privileges to perform the required BRM operations.
Enable SSL/TLS for SQL*NET
Configure Oracle Database to communicate over secure sockets layer (SSL) or transport layer security (TLS) channels to secure the data transmitted between the BRM server and the Oracle database.
Use Secure TLS Connections
You can configure BRM to communicate between the various components using encrypted TLS sockets by setting the enable_ssl entry in the CM's pin.conf configuration file. When this configuration is enabled, BRM uses TLS sockets for any communication between its components such as Oracle Data Manager (DM) (dm_oracle), Synchronization Queue Manager DM (dm_aq), Payload Generator EM (also called the EAI Java Server or eai_js), or Paymentech DM (dm_fusa).
For example, you can configure BRM client applications such as Customer Center, Payment Tool or any Client tier module such as Web Services Manager or JCA Resource Adapter to use encrypted TLS sockets to connect to BRM server.
BRM provides sample CA certificate and trusted client certificates. You must replace the sample CA certificate with your own CA certificate or use a CA certificate from a third party.
Figure 2-1 shows secure communications between BRM components using TLS.
Figure 2-1 Secure Communications Using TLS
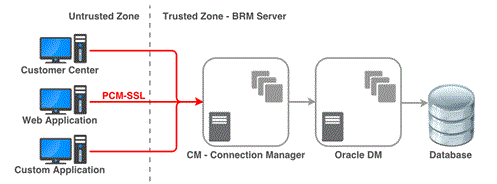
Description of ''Figure 2-1 Secure Communications Using TLS''
Note:
BRM pipeline batch rating engine and BRM real-time pipeline used for advanced discounting do not support SSL/TLS connections. Therefore, the communication between BRM CM and BRM real-time pipeline is not encrypted.See the discussion about enabling secure communication between BRM components in BRM System Administrator's Guide for more information.
Enforce Password Management
You must apply basic password management rules, such as password length, history, and complexity, to all user passwords.
With BRM 7.5 Patch Set 6, a policy implementation for enforcing the password complexity rules was introduced. However, by default, these password complexity rules are not enabled. You enable these rules by modifying the PCM_OP_CUST_POL_VALID_PASSWD policy opcode.
See the discussion about PCM_OP_CUST_POL_VALID_PASSWD in BRM Developer's Reference for more information.
Tighten File Permissions
You must ensure that all the installed files have their permission tightened to the maximum possible allowed that does not impact the operation of the software.
Configure Maximum Number of Invalid Login Attempts
You must set the MaxLoginAttempts parameter in the bus_params_act.xml configuration file to a value corresponding with internal security policies for the enterprise. It is set to a default value of 5.
The pin_bus_params utility is used to apply any changes to this configuration file.
See the discussion about configuring the maximum number of invalid login attempts in BRM System Administrator's Guide for more information.
If the maximum number of consecutive unsuccessful login attempts is reached, the user account is locked. Use the pin_unlock_service utility to unlock the account and reset the password of the locked account.
See the discussion about unlocking a locked CSR account in BRM System Administrator's Guide for more information.
Log Customer Service Representative Activities
CSRs need to be given special privileges to carry out their roles. It is important to monitor their activities to ensure that they are not abusing those privileges.
CSR activities are logged as part of BRM's session event logging functionality that can be enabled by changing the login_audit entry in the CM's pin.conf configuration file to 1. The pin_notify configuration file lists all those activities that will be logged.
The pin_load_notify utility is used to apply any changes to this configuration file.
See the discussion about logging CSR activities in BRM System Administrator's Guide for more information.
Configure Session Timeout
You can set a time interval in minutes after which the child process or thread terminates by using the cm_timeout entry in the CM's pin.conf file. If your BRM installation has multiple CMs, you must set the cm_timeout entry in the pin.conf file of each CM.
If a BRM connection reaches the maximum idle duration specified in the cm_timeout entry, the BRM server closes the connection.
Integrate Paymentech
If the BRM installation is integrated with Paymentech through the Paymentech DM (dm_fusa) component, Oracle recommends that the connection between BRM and Paymentech be protected using VPN. This encrypts the sensitive customer data being communicated between the two platforms and protects from any snooping attempts.
Mask Sensitive Customer Data
You can mask sensitive customer data such as financial payment information and passwords in system responses and logs. You can configure masking of sensitive data fields stored in string format in system responses to clients and logging to protect subscriber information.
See "About Securing Sensitive Customer Data with Masking" in BRM Managing Customers for more information on setting up data masking.