| Oracle® Fusion Middleware Upgrade Guide for Oracle Identity Management 11g Release 1 (11.1.1) E10129-02 |
|
 Previous |
 Next |
| Oracle® Fusion Middleware Upgrade Guide for Oracle Identity Management 11g Release 1 (11.1.1) E10129-02 |
|
 Previous |
 Next |
This chapter describes how to upgrade your existing 10g (10.1.4) Oracle Identity Federation to Oracle Identity Federation 11g.
This chapter contains the following sections:
Task 3: Install and Configure Oracle Identity Federation 11g
Task 4: Use the Upgrade Assistant to Upgrade Oracle Identity Federation
Task 5: Perform Any Required Oracle Identity Federation Post-Upgrade Tasks
Task 6: Verify that the Oracle Identity Federation Upgrade Was Successful
Before you install Oracle Identity Federation 11g, consider the topology you currently have in Oracle Application Server 10g (10.1.4), as well as any requirements for your Oracle Fusion Middleware 11g environment.
For more information, refer to Chapter 3, "Oracle Identity Federation Topologies".
Before you can upgrade to Oracle Identity Federation 11g, you must first install the Oracle Identity Federation schema into a supported database.
For more information, see "Upgrading and Preparing Your Databases" in the Oracle Fusion Middleware Upgrade Planning Guide.
For more information about installing the Oracle Identity Federation schema, refer to the following sections:
Verifying that the Database Meets the Minimum Requirements for the Oracle Identity Federation Schema
Running the Repository Creation Utility in Preparation for Upgrading Oracle Identity Federation
Before performing any installation you should read the system requirements and certification documentation to ensure that your environment meets the minimum installation requirements for the products you are installing.
For more information, refer to "System Requirements and Prerequisites" in the Oracle Fusion Middleware Installation Planning Guide.
To run the Repository Creation Utility to install the Oracle Identity Federation schema in the database, refer to the following resources:
Oracle Fusion Middleware Installation Guide for Oracle Identity Management
Oracle Fusion Middleware Repository Creation Utility User's Guide.
After you start the Repository Creation Utility, follow the instructions on the Repository Creation Utility screens to connect to the database and create the required schemas.
During the installation of the schema, note the following:
On the Select Componts screen, be sure to select the Oracle Identity Federation schema.
No other schemas are required unless you plan to use this database for installing other Oracle Fusion Middleware 11g components.
The following sections describes how to install and configure new Oracle Fusion Middleware 11g middle tier instances in preparation for an upgrade to Oracle Fusion Middleware 11g:
Task 3a: Install the Oracle WebLogic Server Software and Create the Middleware Home
Task 3b: Install and Configure Oracle Identity Federation 11g in Preparation for Upgrade
Task 3c: Create an Oracle HTTP Server Instance and Link It to Oracle Identity Federation 11g
To install Oracle WebLogic Server and create the middleware home, refer to "Installing Oracle WebLogic Server" in the Oracle Fusion Middleware Installation Guide for Oracle Identity Management.
For more information about the Middleware home, see "Understanding Oracle Fusion Middleware Concepts" in the Oracle Fusion Middleware Administrator's Guide.
Installing and configuring Oracle Identity Federation in preparation for an upgrade is similar to any other 11g installation. Later, you use the Oracle Fusion Middleware Upgrade Assistant to copy configuration information from the 10g environment to the new 11g environment.
To install and configure Oracle Identity Federation, in preparation for upgrade:
Locate the Oracle Identity Management CD–ROM.
Alternatively, you can download and unpack the installation kit from the Oracle Technology Network (OTN):
http://www.oracle.com/technology/
If you are installing from the CD–ROM, then navigate to the root directory of the CD–ROM.
Or, if you downloaded and unpacked the software from the Oracle Technology Network, then change directory to the Disk1 directory in the location where you unpacked the software.
Start Oracle Universal Installer:
On UNIX systems, enter the following command:
./runInstaller
On Windows systems, double-click the setup.exe file.
Follow the instructions in the installer to install Oracle Identity Federation.
Refer to the Oracle Fusion Middleware Installation Guide for Oracle Identity Management or click Help for general information about the prerequisites and prompts required during an Oracle Identity Federation installation.
When the installation and configuration is complete, exit from the Oracle Identity Management installation and configuration tool.
The Oracle Fusion Middleware Upgrade Assistant automates the upgrade of many aspects of your Oracle Application Server 10g environment.
The Upgrade Assistant is installed automatically into the bin directory of your Oracle Fusion Middleware Oracle home.
You run the Upgrade Assistant once for each Oracle Application Server 10g Oracle home that you are upgrading. For example, if you are upgrading upgrading two different 10g Release 2 (10.1.2) Oracle homes that are a part of the same 10g Release 2 (10.1.2) farm, then you would run the Upgrade Assistant two times, once for each of the 10g Release 2 (10.1.2) Oracle homes.
Similarly, if you configure multiple Oracle instances in your new Oracle Fusion Middleware 11g environment, you must run the Upgrade Assistant once for each Oracle instance.
|
Note: If you have configured more than one data store, Authentication Engine, or SP Engine in your Oracle Identity Federation environment, the Upgrade Assistant will upgrade only the enabled resources to 11g. Any additional data stores, authentication engines, or SP engines that are are configured, but not enabled, will not be upgraded to the new Oracle Identity Federation 11g environment.After you upgrade, you can reconfigure the resources that were not upgraded. In addition, unlike Oracle Identity Federation 10g, you can enable more than one of these resources at a time in 11g. |
The following sections provide more information:
To start the Upgrade Assistant using the graphical user interface:
|
Note: You can also use the Upgrade Assistant command-line interface to upgrade your Oracle Application Server 10g Oracle homes. For more information, see "Using the Upgrade Assistant Command-Line Interface" in the Oracle Fusion Middleware Upgrade Planning Guide. |
Change directory the ORACLE_HOME/bin directory of the Oracle Fusion Middleware installation.
Enter the following command to start the Upgrade Assistant.
On UNIX system:
./ua
On Windows systems:
ua.bat
The Upgrade Assistant displays the Welcome screen as shown in Figure 6-1
Figure 6-1 Upgrade Assistant Welcome Screen
Click Next to display the Select Operation screen (Figure 6-2).
The options available in the Upgrade Assistant are specific to the Oracle home from which it started. When you start Upgrade Assistant from an Oracle Application Server Identity Management Oracle home, the options shown on the Select Operation screen are the valid options for an Oracle Application Server Identity Management Oracle home.
Figure 6-2 Upgrade Assistant Select Operation Screen for an Oracle Identity Federation Upgrade
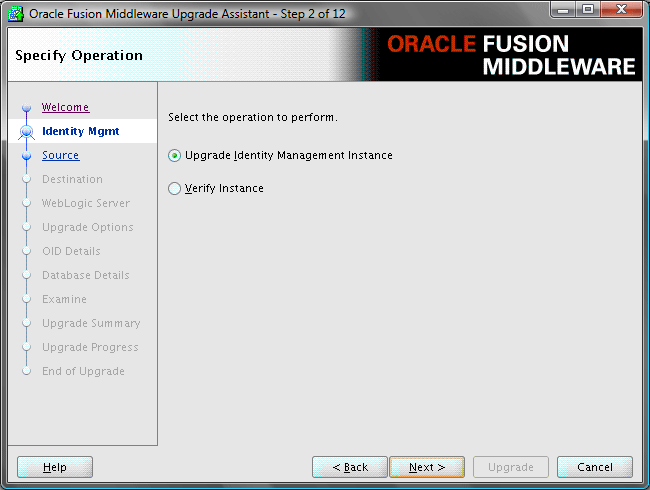
When you upgrade Oracle Identity Federation, the Upgrade Assistant upgrades the configuration files in the Oracle Identity Federation middle tier.
To upgrade Oracle Identity Federation when they reside in the same Oracle instance:
Start the Upgrade Assistant as described in Task 4a: Start the Upgrade Assistant for an Oracle Identity Federation Upgrade.
Select Upgrade Identity Management Instance on the Select Operation screen (Figure 6-2).
Refer to Table 6-1 for a description of the Upgrade Assistant screens that require input from you during an Oracle Identity Federation upgrade.
After the Specify Upgrade Options screen, the Upgrade Assistant performs the following tasks and provides the progress on each task:
Examines the components and schemas to be upgraded and verifies that they can be upgraded successfully.
Provides a summary of the components to be upgraded so you can verify that Upgrade Assistant is upgrading the components and schemas you expect.
Provides a progress screen so you can see the status of the upgrade as it proceeds.
Alerts you of any errors or problems that occur during the upgrade.
|
See Also: "Troubleshooting Your Upgrade" in the Oracle Fusion Middleware Upgrade Planning Guide for specific instructions for troubleshooting problems that occur while running the Upgrade Assistant |
Displays the End of Upgrade screen, which confirms that the upgrade was complete.
Exit the Upgrade Assistant.
Table 6-1 Upgrade Assistant Screens That Require Input During an Oracle Internet Directory and Oracle Directory Integration Platform Upgrade
| Upgrade Assistant Screen | Description |
|---|---|
|
Select the 10g (10.1.4) source Oracle home. If the Oracle home you want to upgrade does not appear in the drop-down lists, see "Source Oracle Home Not Listed by OracleAS Upgrade Assistant" in the Oracle Fusion Middleware Upgrade Planning Guide. |
|
|
Enter the complete path to the destination 11g Oracle home that you installed inside the middleware home. This is the Oracle home that contains the Oracle Identity Federation software. Alternatively, click Browse to select the directory. |
|
|
Enter the host, Administration Server port, and administration user credentials for the Oracle WebLogic Server domain you configured in Section 6.3.2, "Task 3b: Install and Configure Oracle Identity Federation 11g in Preparation for Upgrade". |
|
|
Warning Dialog Box |
The Upgrade Assistant displays this warning dialog box if the source Oracle home contains Oracle Application Server components that are not installed and configured in the destination Oracle instance. This warning appears, for example, if the source Oracle home contains an instance of Oracle HTTP Server, which is not available in the 11g Oracle home. If the information in the dialog box is accurate and you understand which components will be upgraded, click Yes to continue. Otherwise, click No and verify which components are installed and configured in each 11g Oracle instance. |
|
This screen offers these upgrade options:
Click Help to display more information about the upgrade options on this screen. |
The following sections describe the manual upgrade steps required when you upgrading to Oracle Identity Federation 11g:
Integrating Oracle Identity Federation 11g with Oracle Access Manager 10g
Using a Custom Authentication Engine or Custom SP Engine with Oracle Identity Federation 11g
Reconfiguring Oracle Single Sign-On Server After Upgrade to Work with Oracle Identity Federation 11g
Setting Oracle Identity Federation System Properties After Upgrade
If you were previously using Oracle Identity Federation 10g with Oracle Access Manager, you can use the following procedure to configure Oracle Identity Federation 11g so it can work successfully with your existing Oracle Access Manager 10g software.
Note that the steps described here are based on the instructions available in the section, "Deploying Oracle Identity Federation with Oracle Access Manager" in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Federation.
To use Oracle Identity Federation 11g with Oracle Access Manager 10g:
Upgrade to Oracle Identity Federation 11g using the instructions in the previous sections of this chapter.
Specifically, be sure you have installed and configured Oracle Identity Federation 11g and that you have used the Upgrade Assistant to upgrade the Oracle Identity Federation instance to 11g.
Optionally, use Oracle Access Manager 10g as the authentication engine for Oracle Identity Federation 11g.
For specific instructions, refer to "Integrate Oracle Access Manager as an Authentication Engine" in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Federation.
Optionally, integrate Oracle Access Manager 10g as an SP integration module.
For specific instructions, refer to "Integrate Oracle Access Manager as an SP Integration Module" in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Federation.
Optionally, configure Oracle Access Manager 10g so that protected resources are using the new Oracle Identity Federation 11g authentication schemes.
To perform this task, use the instructions that help you verify the proper integration of Oracle Access Manager by allowing Oracle Identity Federation 11g to create policy objects and authentication schemes in Oracle Access Manager.
These instructions are located in the section, "Integrate Oracle Identity Federation with Oracle Access Manager" in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Federation.
When the integration with Oracle Access Manager is complete, delete any old access gates, authentication schemes, and policies for Oracle Identity Federation 10g from Oracle Access Manager 10g.
For more information, refer to the Oracle Access Manager documentation in the Oracle Identity Management 10g (10.1.4) documentation library, which is available on the Oracle Technology Network (OTN):
http://www.oracle.com/technology/documentation
If your Oracle Identity Federation 10g instance is integrated with a custom authentication engine, then use the information in the following sections to configure the custom authentication engine with Oracle Identity Federation 11g:
Changes to the Logout Service for Authentication or SP Engines
Creating the Authentication Engine in Oracle Identity Federation 11g
The HTTPServletRequestAttributes available to the authentication engines Oracle Identity Federation 11g are different from those in 10g. As a result, you must modify the authentication engine code so it can read the attribute values from their new parameter names.
Refer to the following sections for more information:
Changes to Parameters and Attributes Received by Oracle Identity Federation 11g
New Incoming Attributes Supported by Oracle Identity Federation 11g
Changes to Parameters and Attributes Sent to Oracle Identity Federation 11g
Additional Attributes to Include in a Request to Oracle Identity Federation 11g
Changes to Parameters and Attributes Received by Oracle Identity Federation 11g
Table 6-2 shows the new and changed parameters used for authentication engines in Oracle Identity Federation 11g.
Table 6-2 Parameters and Attributes received from Oracle Identity Federation
| Parameter or Attribute | Changes in Oracle Identity Federation 11g |
|---|---|
|
These query parameters are not available in 11g. In 11g, there is no need to consult these parameters to find where the user has to be forwarded after being identified by the authentication engine. In 11g, after successful authentication, the engine must forward the user to Oracle Identity Federation. To do this use the root context, |
|
|
This 10g query parameter has been changed to the following attribute in 11g: oracle.security.fed.authn.authnmech As a result, any occurences of request.getAttribute(“oracle.security.fed.authn.authnmech”) In 10g, the value of the the oracle:fed:authentication:password-protected In 11g, the |
|
|
This 10g query parameter has been changed to the following attribute in 11g: oracle.security.fed.authn.refid As a result, any occurrences of
request.getAttribute("oracle.security.fed.authn.refid")
|
New Incoming Attributes Supported by Oracle Identity Federation 11g
In addition to the changes described in Table 6-2, the following new incoming attributes are available in Oracle Identity Federation 11g; these attributes have no equivalents in Oracle Identity Federation 10g, but are available to the authentication engine in 11g:
oracle.security.fed.authn.providerid
oracle.security.fed.authn.providerdescription
oracle.security.fed.authn.engineid
oracle.security.fed.authn.userid
oracle.security.fed.authn.forceauthn
oracle.security.fed.authn.passive
oracle.security.fed.authn.attributes
oracle.security.fed.sessionid
For more information about these new attributes, see "Implementing the Service" the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Federation.
Changes to Parameters and Attributes Sent to Oracle Identity Federation 11g
The following attribute names must be changed after you upgrade to Oracle Identity Federation 11g:
Change oracle.security.sso.sasso.uid to oracle.security.fed.authn.userid
Change oracle.security.sso.sasso.refID to oracle.security.fed.authn.refid
Change oracle.security.sso.sasso.authnMech to oracle.security.fed.authn.authnmech
Change oracle.security.sso.sasso.authnInst to oracle.security.fed.authn.authntime
For example, suppose you have the following attribute in Oracle Identity Federation 11g:
request.setAttribute(“oracle.security.sso.sasso.uid”, userID)
For Oracle Identity Federation 11g, you must change this attribute as follows:
request.setAttribute(“oracle.security.fed.authn.userid”. userID);
For more information about the values that must be set by the authentication engine before doing an internal forward to Oracle Identity Federation 11g, see "Implementing the Service" the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Federation.
Additional Attributes to Include in a Request to Oracle Identity Federation 11g
In addition to the existing 10g attributes, Oracle Identity Federation 11g expects the additional attributes shown in Table 6-3 in each request.
Table 6-3 Additional Attributes to Include in a Request to Oracle Identity Federation 11g
| Attribute | Description |
|---|---|
|
oracle.security.fed.authn.expirationtime |
Expiration time of the authenticated session as a Date Object |
|
oracle.security.fed.authn.engineid |
The identifier referencing the engine used to authenticate the user. The engine is created in the configuration of Oracle Identity Federation 11g. For more information, see Section 6.5.2.5, "Creating the Authentication Engine in Oracle Identity Federation 11g". |
|
oracle.security.fed.authn.attributes |
This optional map of attributes is stored in the user session. It will have String objects as the keys and Set of Objects as values. |
|
oracle.security.fed.sessionid |
This optional string contains the Oracle Identity Federation session identifier that Oracle Identity Federation will need to use to reference the user session. This allows the engine and the Oracle Identity Federation server to share the same identifier to reference the user session. Later, when the logout flow is being executed, Oracle Identity Federation will pass the sessionID that is being logged out to the engine, so that the engine can delete the data that was used for this user session. |
Similar to the its affect on authentication engines, the HTTPServletRequestAttributes available to the SP engines in Oracle Identity Federation 11g are different from those in 10g. As a result, you must modify the SP engine code so it can read the attribute values from their new parameter names.
Refer to the following sections for more information:
Initiating a Federation SSO Operation
In Oracle Identity Federation 10g, if the Service Provider Engine did not find a valid user, then it initiated single sign-on by redirecting to the Oracle Identity Federation server function as the service provider. The URL it redirects to is as follows:
http://SP_HOST_NAME:SP_PORT/fed/sp/initiatesso
The following values are set to Oracle Identity Federation as query parameters:
providerid – the provider ID of the IdP to use for single sign-on
returnurl – the URL to which Oracle Identity Federation should send the user after single sign-on
In OIF 11g these query parameters have changed:
The providerId should now be specified as the HTTPServletRequest attribute oracle.security.fed.sp.providerid
The returnurl query parameter no longer exists; instead, it can be specified in the HTTPServelet request attribute oracle.security.fed.sp.relaystate.
There are additional attributes in Oracle Identity Federation 11g that can be passed to the Oracle Identity Federation servers when initiating single sign-on. These additional attributes are as follows:
oracle.security.fed.sp.authnmech
oracle.security.fed.sp.federationid
oracle.security.fed.sp.engineid
oracle.security.fed.sp.localauthn
oracle.security.fed.sp.usedefault
oracle.security.fed.sp.forceauthn
oracle.security.fed.sp.allowfedcreation
oracle.security.fed.sp.passive
oracle.security.fed.sp.requestbinding
oracle.security.fed.sp.responsebinding
oracle.security.fed.sp.authnmechcomparison
oracle.security.fed.sp.nameidformat
For more information, see "Implementing the Service" the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Federation.
Processing the Request from the Federation Server
The following incoming parameter names for SP engines have changed in Oracle Identity Federation 11g:
The oracle.security.sso.sasso.uid attribute has changed to oracle.security.fed.sp.userid
oracle.security.sso.sasso.authnInst has changed to oracle.security.fed.sp.authntime
oracle.security.sso.sasso.expiryInst has changed to oracle.security.fed.sp.expirationtime
oracle.security.sso.sasso.targetURL is no longer available in Oracle Identity Federation 11g.
The SP Engine can store the targetURL (to which the user will be forwarded) in oracle.security.fed.sp.relaystate before forwarding to Oracle Identity Federation to initiate an single sign-on operation. Oracle Identity Federation will pass this parameter back to the SP after doing an single sign-on.
The following additional, new parameters are available in Oracle Identity Federation 11g for the SP Engine to use. These new parameters include:
oracle.security.fed.sp.authnresult
oracle.security.fed.sp.authnmech
oracle.security.fed.sp.attributesoracle.security.fed.sp.topstatus
oracle.security.fed.sp.lowstatus
oracle.security.fed.sp.statusmessage
oracle.security.fed.sp.providerid
oracle.security.fed.sp.engineid
oracle.security.fed.sp.sessionid
For more information, see "Implementing the Service" the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Federation.
When using the logout service for an authentiation or SP engine with Oracle Identity Federation 11g, consider the information in the following sections:
Changes When the Engine Initiates a Logout
In Oracle Identity Federation 11g, an authentication or SP engine can initiate a logout operation. For more information, see "Logout" in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Federation.
Changes When Oracle Identity Federation Forwards to the Engine for Logout
The following changes need to be made to the logout service of the authentication or SP engine if it is present:
The invokeOSFSLogout parameter and the doneUrl parameters are no longer sent to the engine. In Oracle Identity Federation 11g, the engine should always perform an internal forward to the /fed web context and /user/logoutretsso relative path.
The engineId of the invoked engine is available to the logout service through the http request attribute oracle.security.fed.authn.engineid
The oracle.security.fed.sessionid HTTP request attribute can optionally contain the session identifier of the session being logged out.
In Oracle Identity Federation 11g, the logout service should redirect the user to /fed/user/logoutretsso after logout rather than to the /fed/user/logoutsso URL.
Specify the engineId in the attribute referenced by oracle.security.fed.authn.engineid (if the engine is an Authentication Engine) or oracle.security.fed.sp.engineid (if the engine is an SP Engine).
You deploy the authentication or SP engine just the same as you deploy any Java EE aplication. For more information, refer to "Deploying Applications" in the Oracle Fusion Middleware Administrator's Guide.
To create an authentication engine for Oracle Identity Federation 11g:
In Oracle Enterprise Manager Fusion Middleware Control, navigate to the Oracle Identity Federation home page.
For more information, see "Getting Started Using Oracle Enterprise Manager Fusion Middleware Control" in the Oracle Fusion Middleware Administrator's Guide.
From the Oracle Identity Federation menu, select Administration, then Authentication Engines.
On the Custom Authentication Engines tab, click Add to create a new Authentication Engine, and then enter values for the following fields:
Name – a name for the engine
Enabled – selected
Web Context – the root context where the engine is deployed
Authentication Relative Path – the relative path to the engine
Logout Enabled – select this check box if the engine needs to perform logout when a logout operation is performed.
Logout Relative Path – the relative path of the engine logout service.
Click Save.
The Oracle Identity Federation server generates an Engine ID for the new engine. The Engine ID is the value of the oracle.security.fed.authn.engineid attribute that the custom engine needs to send to the Oracle Identity Federation server after authenticating the user.
To create an SP engine for Oracle Identity Federation 11g:
In Oracle Enterprise Manager Fusion Middleware Control, navigate to the Oracle Identity Federation home page.
For more information, see "Getting Started Using Oracle Enterprise Manager Fusion Middleware Control" in the Oracle Fusion Middleware Administrator's Guide.
From the Oracle Identity Federation menu, select Administration, then Service Provider Integration Modules.
On the Custom SP Engines tab, click Add to create a new Authentication Engine, and then enter values for the following fields:
Name – a name for the engine
Enabled – selected
Web Context – the root context where the engine is deployed
Authentication Relative Path – the relative path to the engine
Logout Enabled – select this check box if the engine needs to perform logout when a logout operation is performed.
Logout Relative Path – the relative path of the engine logout service.
Click Save.
The Oracle Identity Federation server generates an Engine ID for the new engine. The Engine ID is the value of the oracle.security.fed.sp.engineid attribute that the custom engine needs to send to the Oracle Identity Federation server after authenticating the user.
If you are using Oracle Single Sign-On with Oracle Identity Federation 10g, then after you upgrade to Oracle Identity Federation 11g, you must reconfigure Oracle Single Sign-On.
This step is necessary because the values required for the SASSOAuthnUrl and SASSOLogoutUrl properfies have changed for Oracle Identity Federation 11g.
For more information, see "Configuring Single Sign-On" in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Federation.
Oracle Identity Federation 10g, as well as SHAREid/COREid Federation 2.x, provided service URLs for its SAML 1.x and WS-Federation protocol support, which were different from the SAML 2.0 and Liberty 1.x service URLs.
These URLs have been modified in the 11g Oracle Identity Federation server for consistency with the SAML 2.0 and Liberty 1.x service URLs. This means that customers upgrading to Oracle Identity Federation 11g, who use SAML 1.x or WS-Federation, will need to inform their partner providers of the new single sign-on service URLs.
To ease that transition, Oracle Identity Federation 11g provides a separate module that allows backwards compatibility with the SHAREid service URLs. This module is an installable J2EE application that is deployed alongside Oracle Identity Federation, which will handle requests for the ShareID/Oracle Identity Federation 10g service URLs and redirect or forward them to the corresponding Oracle Identity Federation 11g service URLs.
For information on how to set up this application, see "Setting up Backwards Compatibility for Oracle Identity Federation 10g and ShareID service URLs" in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Federation.
If you are using a shareId keystore for SSL support in Oracle Virtual Directory 10g, then the Upgrade Assistant automatically imports the keystore into Oracle Identity Federation 10g.
If the SSL identity and trust keystores you use in Oracle Virtual Directory 10g are stored in the following location, then there are no additional tasks to perform:
ORACLE_HOME/fed/shareid/oblix/config /keystore
However, if the keystores are stored in any other location, then you must perform the following tasks:
Copy the identify and trust keystores to a subdirectory inside the following directory:
WLS_HOME/user_projects/domains/domain_name/servers/server_name/stage/OIF
Configure Oracle WebLogic Server to point to the new keystore location, as follows:
Log in to the Oracle WebLogic Server Administration Console and select Environment, then Servers.
Select the server for which you want to set up SSL.
In the Keystores section, select Custom Identity and Custom Trust.
In the Identity section, fill in the properties as follows:
Custom Identity Keystore: location_of_keystore_containing_SSL_private key_and_certificate
Custom Identity Keystore type: jks
Custom Identity Keystore Passphrase: storepassword
In the Trust section, fill in properties as follows:
Custom Identity Keystore: location_of_keystore_containing_the_trusted certificate_entries
Custom Identity Keystore type: jks
Custom Identity Keystore Passphrase: storepassword
If you configured Oracle Identity Federation 10g by setting system properties, then you will have to manually configure those properties in the upgraded Oracle Identity Federation 11g instance. The Upgrade Assistant does not apply these settings to your 11g instance.
Table 6-4 lists the system properties that are not upgraded and explains how to set the equivalent properties in Oracle Identity Federation 11g. In many cases, the instructions refer to Oracle Enterprise Manager Fusion Middleware Control, the Oracle WebLogic Server Administration Console, or the WebLogic Scripting Tool (WLST), which are used to manage Oracle Fusion Middleware11g components.
For more information, see "Overview of Oracle Fusion Middleware Administration Tools" in the Oracle Fusion Middleware Administrator's Guide.
Note that these properties are documented in Section 9.3, "Managing Oracle Identity Federation Performance," in the Oracle Identity Federation Administrator's Guide for 10g (10.1.4.0.1). This document can be found in the Oracle Application Server 10g (10.1.4.0.1) documentation library on the Oracle Technology Network (OTN):
http://www.oracle.com/technology/documentation/
Table 6-4 Setting Oracle Identity Federation 10g System Properties in Oracle Identity Federation 11g
| Oracle Identity Federation 10g System Property | How to Set the Property in Oracle Identity Federation 11g |
|---|---|
|
-Dhttp.fed.host=VALUE |
In Fusion Middleware Control, you can set this property as follows:
|
|
-Dhttp.fed.max.conn=VALUE |
In Fusion Middleware Control, you can set this property as follows:
|
|
-Dfed.ldap.ha=[true | false] |
In Oracle Identity Federation 10g, you used this system property to set one flag for all datastores. In 11g you can set this flag seperately for the LDAP user datastore, LDAP federation datastore, and LDAP authentication engine. Enter the WLST script environment for the Oracle Identity Federation instance, and set the To enable this property for the LDAP authentication engine:
setConfigProperty('authnengines', 'ldaphaenabled',
'true', 'boolean')
To enable this for the LDAP user datastore:
setConfigProperty('datastore', 'userldaphaenabled',
'true', 'boolean')
For enabling this for LDAP federation datastore:
setConfigProperty('datastore', 'fedldaphaenabled',
'true', 'boolean')
|
|
-Dfed.jdbc.min.conn=VALUE -Dfed.jdbc.max.conn=VALUE -Dfed.jdbc.max.usage=VALUE |
Use the Oracle WebLogic Server Administration Console to set the appropriate values on the JDBC data source that you are using for your Oracle Identity Federation 11g datastores or authentication engines. |
The following additional post-upgrade tasks should be performed after upgrading to Oracle Identity Federation 11g, in addition to those described in the Oracle Fusion Middleware Upgrade Guide for Oracle Identity Management:
If you are have configured Oracle Identity Federation 10g to use the SAML 1.x/WS-FED protocol, then after you upgrade to Oracle Identity Federation 11g, you must set a default single sign-on identity provider.
For more information, see "Configuring Service Providers" in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Federation.
Export the Identity Provider self-signed certificate to the service provider
The procedure you use to perform this task varies, depending on whether your service provider is a 10g or 11g service provider:
If you are using a 10g service provider, then refer to "Exporting the IdP's self-signed certificate to the SP" in the Oracle Identity Federation Administrator's Guide in the Oracle Application Server 10g (10.1.4.0.1) documentation library on the Oracle Technology Network (OTN):
http://www.oracle.com/technology/documentation/
If you are using an 11g service provider, then refer to "Set Up Single Sign-On for SAML 1.x and WS-Federation" in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Federation.
If you are using an 11g Identity Provider and a 10g service provider, and you are using the SAML 1.x/WS-FED protocol, then you configure the 10g service provider.
Specifically, for the 10g service provider, you must change the "Signing Certificate Subject DN" and "Signing Certificate Issuer DN" to 11g IdP format, which is of the form "CN=<host> Signing Certificate".
For more information, see "Configure This Domain as a Source/Identity Provider" in the Oracle Identity Federation Administrator's Guide in the Oracle Application Server 10g (10.1.4.0.1) documentation library on the Oracle Technology Network (OTN).
Enable "Send Signed Assertion" in Oracle Identity Federation 10g, or disable "Require Signed Assertions" in Oracle Identity Federation 11g.
This task is necessary because in 10g, signed assertions are disabled by default, and in 11g, signed assertions are enabled by default.
Depending whether you perform this task in 10g or 11g, refer to one the following:
"Configuring Service Providers" in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Federation.
Section 6.5.5, "Add Assertion Profile" in the Oracle Identity Federation Administrator's Guide in the Oracle Application Server 10g (10.1.4.0.1) documentation library on the Oracle Technology Network (OTN).
To verify that your Oracle Internet Directory and Oracle Directory Integration Platform upgrade was successful:
Run the Upgrade Assistant again and select Verify Instance on the Specify Operation page.
Follow the instructions on the screen for information on how to verify that specific Oracle Fusion Middleware components are up and running.
Use the following URL to verify that Oracle Identity Federation 11g is up and running:
http://<host>:<port>/fed/sp/metadata
For example:
http://host42.exmaple.com:7001/fed/sp/metadata
Alternatively, you can use Fusion Middleware Control to verify that Oracle Identity Federation and any other Oracle Identity Management components are up and running in the Oracle Fusion Middleware environment.
For more information, see "Getting Started Using Oracle Enterprise Manager Fusion Middleware Control" in the Oracle Fusion Middleware Administrator's Guide.