| Oracle® Identity Manager Connector Guide for Database User Management Release 9.1.0 E11193-04 |
|
 Previous |
 Next |
| Oracle® Identity Manager Connector Guide for Database User Management Release 9.1.0 E11193-04 |
|
 Previous |
 Next |
This chapter is divided into the following sections:
|
Note: These sections provide both conceptual and procedural information about configuring the connector. It is recommended that you read the conceptual information before you perform the procedures. |
Section 3.1, "Setting Up Lookup Definitions in Oracle Identity Manager"
Section 3.3, "Scheduled Task for Lookup Field Synchronization"
Section 3.6, "Guidelines on Performing Provisioning Operations"
You must provide Decode values for some of the entries of the following lookup definitions.
To set a Decode value for an entry in a lookup definition:
On the Design Console, expand Administration, and then double-click Lookup Definition.
Search for and open the lookup definition that you want to modify.
Enter the value in the Decode column for the Code Key that you want to set.
Click the Save icon.
Depending on whether you have configured your target system as a trusted source of target resource, see one of the following sections for information about the entries for which you must specify Decode values:
Section 3.1.1, "Setting Up the Configuration Lookup Definition for a Target Resource"
Section 3.1.2, "Setting Up the Configuration Lookup Definition for a Trusted Source"
Section 3.1.3, "Setting Up the ExclusionList Lookup Definition"
Depending on the target system that you are using, the following is the list of Configuration lookup definitions:
Provide Decode values for the following entries of the Configuration lookup definition:
Reconciliation Query Property File
Enter the full path and name of the file containing queries that must be run during reconciliation.
Reconciliation SQL Injection Keywords
Enter the list of SQL keywords that must not be used in the reconciliation query. Use the tilde (~) character as a separator if you want to specify more than one SQL keyword. During target resource reconciliation runs, the connector does not run a query (used for target resource reconciliation) that contains any of the keywords listed in the Decode column.
Reserved Words List
Enter the list of reserved words that are not supported in the OIM User process form fields during provisioning operations. Use the tilde (~) character as a separator if you want to specify more than one reserved word.
Target Date Format
Enter the format in which date values are stored on the target system.
Unsupported Special Characters
Enter the list of special characters that are not supported in the process form fields during provisioning operations.
Sample value: #*~^
Depending on the target system that you are using, the following is the list of Configuration lookup definitions:
For Microsoft SQL Server: Lookup.DBUM.MSSQL.TrustedRecon.Configuration
For Oracle Database: Lookup.DBUM.Oracle.TrustedRecon.Configuration
Provide Decode values for the following entries of the Configuration lookup definition:
Reconciliation Query Property File
Enter the full path and name of the file containing queries that must be run during reconciliation.
Reconciliation SQL Injection Keywords
Enter the list of SQL keywords that must not be used in the reconciliation query. Use the tilde (~) character as a separator if you want to specify more than one SQL keyword. During trusted source reconciliation runs, the connector does not run a query that contains any of the keywords listed in the Decode column.
Target Date Format
Enter the format in which date values are stored on the target system.
In the ExclusionList lookup definition, enter the user attributes of the target system accounts for which you do not want to perform target resource reconciliation and provisioning as follows:
On the Design Console, expand Administration and then double-click Lookup Definition.
Depending on the target system that you are using, search for and open one of the following lookup definitions:
Click Add.
If you want to specify the target system accounts on which you do not want to perform provisioning, then:
In the Code Key column, enter the name of the process form field.
In the Decode column, enter tilde-separated list of values for the process form field.
For example, if you are using IBM DB2 UDB as the target system and you do not want to provision users with user names DB2 admin, JDoe, and DFinn, then populate the lookup definition with the following values:
| Code Key | Decode |
|---|---|
| UD_DB_DB2_U_USERNAME | DB2 admin~JDoe~DFinn |
If you want to specify the target system accounts on which you do not want to perform target resource reconciliation, then:
In the Code Key column, enter the reconciliation field of the resource object.
In the Decode column, enter a tilde-separated list of values for the reconciliation field of resource object
For example, if you are using IBM DB2 UDB as your target system and you do not want to reconcile user account data of John, Mary, and Anna, then populate the lookup definition with the following values:
| Code Key | Decode |
|---|---|
| User Name | John~Mark~Anna |
Click the Save icon.
The following are guidelines that you must apply while configuring reconciliation:
|
Note: In Oracle Identity Manager release 11.1.1, a scheduled job is an instance of a scheduled task. In this guide, the term scheduled task used in the context of Oracle Identity Manager release 9.1.0.x is the same as the term scheduled job in the context of Oracle Identity Manager release 11.1.1.See Oracle Fusion Middleware System Administrator's Guide for Oracle Identity Manager for more information about scheduled tasks and scheduled jobs. |
Before a target resource reconciliation run is performed, lookup definitions must be synchronized with the lookup fields of the target system. In other words, the scheduled task for lookup field synchronization must be run before user reconciliation runs.
The scheduled task for user or login reconciliation must be run before the scheduled task for reconciliation of deleted user or login data.
After you configure batched reconciliation, if reconciliation fails during a batched reconciliation run, then rerun the scheduled task without changing the values of the task attributes.
The DBUM Lookup reconciliation scheduled task is used for lookup field synchronization. Table 3-1 describes the attributes of this scheduled task.
See Section 3.5, "Configuring Scheduled Tasks" for instructions on running the scheduled task.
Table 3-1 Attributes of the DBUM Lookup reconciliation Scheduled Task
| Attribute | Description |
|---|---|
|
Query Properties File Path |
Enter the full path and name of the file containing the queries for lookup field synchronization. In other words, enter the full path and name of the DBUMLookUpQuery.properties file. However, if you want to use a new properties file instead of the predefined DBUMLookUpQuery.properties file, then specify the full path and name of that file. Sample value: See Also:
|
|
IT Resource |
Enter the name of the IT resource that you configure by performing the procedure described in Section 2.3.5, "Configuring the IT Resource" Sample value: |
|
Lookup Definition Name |
Enter the name of the lookup definition in Oracle Identity Manager that you want to synchronize with the target system. Depending on the target system that you are using, the value can be one of the following:
Sample value: |
|
Exclusion List |
Enter the lookup value in the target system lookup fields that you do not want to synchronize with the corresponding lookup definitions in Oracle Identity Manager. If you want to specify more than one lookup value that must be excluded during lookup field synchronization, then enter a tilde-separated list of lookup values. If you do not want to exclude any lookup value, then leave the default value for this attribute unchanged. The following is an example of a list of role lookup values in Oracle Database that must be excluded during lookup reconciliation:
|
|
Task Name |
This attribute holds the name of the scheduled task. Value: Note: You must not change this value. |
|
Ref Data Provider Impl |
This attribute holds the name of the class that implements the logic for lookup field synchronization. Default value: Note: You must not change this value. |
As mentioned earlier in this guide, reconciliation involves duplicating in Oracle Identity Manager the creation of and modifications to user accounts on the target system. This section discusses the following topics related to configuring reconciliation:
Full reconciliation involves reconciling all existing user records from the target system into Oracle Identity Manager. After you deploy the connector, you must first perform full reconciliation. In addition, you can switch from incremental reconciliation to full reconciliation whenever you want to ensure that all target system records are reconciled in Oracle Identity Manager.
To perform a full reconciliation run, specify values for the following attributes while performing the procedure described in Section 3.4.5, "Reconciliation Scheduled Tasks":
Last Execution Time: This attribute holds the time stamp at which the last reconciliation run started. You must set the value of this attribute to 0.
Custom Query: This attribute holds the query for filtering records returned during reconciliation. If you need to perform full reconciliation, then accept the default value of NODATA for this attribute.
Use Custom Query: Set the value of this attribute to No.
For Oracle Database, at the end of the full reconciliation run, the Last Execution Time attribute is automatically set to the time stamp at which the run started. For other target systems, the Last Execution Time attribute is automatically set to the time stamp at which the run started only if you have performed the procedure described in Section 2.3.1.7, "Configuring the Connector for Incremental Reconciliation". From the next run onward, only records created or modified after this time stamp value are considered for reconciliation.
This section describes the Last Execution Time attribute of the scheduled task.
The Last Execution Time attribute holds the time stamp at which the last reconciliation run started. This attribute is used in conjunction with the reconciliation query specified by the Query Name attribute. During a reconciliation run, only target system records added or modified after the time stamp value stored in the Last Execution Time attribute are fetched into Oracle Identity Manager for reconciliation.
Apply the following guidelines while deciding on a value for the Last Execution Time attribute:
If you want to fetch all target system records for reconciliation, then set the value of the attribute to 0.
If you want to specify a time stamp, then first run the query to convert the time stamp into the required format.
For example, on Oracle Database, you first run the following query:
SELECT (TO_DATE('DATE_TO_BE_CONVERTED','DD-MON-YYYY') - TO_DATE('01011970', 'DDMMYYYY')) *24*60*60*1000 as ts FROM DUAL
In this query, replace DATE_TO_BE_CONVERTED with the date that you want to use as the time stamp. For example, if you want to use 5-Dec-2008 as the time stamp, then run the following query:
SELECT (TO_DATE('5-Dec-2008','DD-MON-YYYY') - TO_DATE('01011970', 'DDMMYYYY')) *24*60*60*1000 as ts FROM DUAL
The query returns the following value:
1228435200000
Specify this value as the value of the Last Execution Time attribute.
The Last Execution Time attribute is updated during each reconciliation run. For example, the Last Execution Time attribute is set to the time stamp at which the run begins.
|
Note: You can configure the connector to perform batched reconciliation only if you are using IBM DB2 UDB or Oracle Database as the target system. |
During a reconciliation run, all changes in the target system records are reconciled into Oracle Identity Manager. Depending on the number of records to be reconciled, this process may require a large amount of time. In addition, if the connection breaks during reconciliation, then the process would take longer to complete.
You can configure batched reconciliation to avoid these problems.
To configure batched reconciliation, you must specify values for the following attributes while performing the procedure described in Section 3.4.5, "Reconciliation Scheduled Tasks":
Use Batched Reconciliation: Use this attribute to enable batched reconciliation. Set the value of this attribute to Yes.
Batch Reconciliation Query Name: Use this attribute to specify the name of the batched reconciliation query in the reconciliation query file that you want to run.
Batch Size: Use this attribute to specify the number of records that must be included in each batch. The default value is 100.
|
Note: This section describes an optional procedure. Perform this procedure only if you want to add filter parameters for reconciliation. |
By default, all target system records that are added or modified after the last reconciliation run are reconciled during the current reconciliation run. You can customize this process by specifying the subset of added or modified target system records that must be reconciled.
You can configure limited reconciliation by performing the procedures described in one of the following sections:
Section 3.4.4.1, "Specifying a Value for the Custom Query Attribute"
Section 3.4.4.2, "Adding a Filter Parameter in the Reconciliation Query"
If your target system database uses stored procedures to retrieve user records, and your database does not support filtering of records returned by the store procedure, then you can use the Custom Query scheduled task attribute to configure limited reconciliation. You set the value of the Custom Query attribute while performing the procedure described in Section 3.4.5.1, "Scheduled Tasks for Reconciling Data About Users and Logins".
You must use the following format to specify a value for the Custom Query attribute:
RESOURCE_OBJECT_FIELD_NAME=VALUE
For example, if you specify Last Name=Doe as the value of the Custom Query attribute, then only records for persons whose last name is Doe are considered for reconciliation.
You can add multiple query conditions by using a combination of resource object attributes and the following logical operators:
The AND operator represented by the ampersand (&)
The OR operator represented by the vertical bar (|)
The EQUAL operator represented by the equal sign (=)
For example, the following query condition is used to limit reconciliation to records of those persons whose first name is John and last name is Doe:
First Name=John & Last Name=Doe
The following query condition can be used to limit reconciliation to the records of those persons whose first name is either John or their User ID is 219786:
First Name=John | User ID=219786
You must apply the following guidelines while creating the query condition:
Use only the equal sign (=), ampersand (&), and vertical bar (|) in the query condition. Do not include any other special characters in the query condition. Any other character that is included is treated as part of the value that you specify.
Add a space before and after ampersand and vertical bars used in the query condition. For example:
First Name=John & Last Name=Doe
This is to ensure to help the system distinguish between ampersands and vertical bars used in the query and the same characters included as part of attribute values specified in the query condition.
You must not include unnecessary blank spaces between operators and values in the query condition.
A query condition with spaces separating values and operators would yield different results as compared to a query condition that does not contain spaces between values and operators. For example, the output of the following query conditions would be different:
First Name=John & Last Name=Doe
First Name= John & Last Name= Doe
In the second query condition, the reconciliation engine would look for first name and last name values that contain a space at the start.
If your target system database enables you to add a WHERE clause to the query that you use to retrieve user records, then you can configure limited reconciliation by adding a filter parameter in the reconciliation query and specifying a value for the parameter in the Query Filter lookup definition.
For example, you can add a parameter in the WHERE clause of the ORACLE_TARGET_USER_RECON query so that it returns records of users whose user name is the one that you specify in the lookup definition.
To add a filter parameter in a reconciliation query:
|
Note: Before you modify a query in the properties file, run the query by using any standard database client to ensure that the query produces the required results when it is run against the target system database. |
Modify the query as follows:
Open the properties file in a text editor.
Add the WHERE clause with the condition to the query that you want to modify.
|
Note: The parameter name must begin with the colon (:) as a prefix. In addition, there must be no space between the colon and parameter name and within the parameter name. |
For example, in the following snippet of the ORACLE_TARGET_USER_RECON query, the variable condition highlighted in bold has been added:
WHERE ((CREATED - TO_DATE('01011970','ddmmyyyy')) *24*60*60*1000) > :lastExecutionTime \
AND USERNAME = :username
Save and close the file.
Configure the Query Filter lookup definition as follows:
Log in to the Design Console.
Expand the Administration folder, and then double-click Lookup Definition.
If you have configured the target system as trusted source, then search for and open the appropriate lookup definition:
Lookup.DBUM.DB2.TrustedRecon.QueryFilter
Lookup.DBUM.MSSQL.TrustedRecon.QueryFilter
Lookup.DBUM.MySQL.TrustedRecon.QueryFilter
Lookup.DBUM.Oracle.TrustedRecon.QueryFilter
Lookup.DBUM.Sybase.TrustedRecon.QueryFilter
If you have configured the target system as target resource, then search for and open the appropriate lookup definition:
Lookup.DBUM.DB2.TargetRecon.QueryFilter
Lookup.DBUM.MSSQL.TargetRecon.QueryFilter
Lookup.DBUM.MySQL.TargetRecon.QueryFilter
Lookup.DBUM.Oracle.TargetRecon.QueryFilter
Lookup.DBUM.Sybase.TargetRecon.QueryFilter
To add a row, click Add.
In the Code Key column, enter the variable name that you specified in the properties file. Do not include the colon (:) character. For example, enter username in the Code Key column.
In the Decode column, enter the value that you want to assign to the parameter for subsequent reconciliation runs.
Sample value: jdoe
Click the Save icon.
When you next run the query that you have modified, the condition that you add is applied as an additional filter during reconciliation.
This connector supports both trusted source and target resource reconciliation. When you run the connector installer, the following scheduled tasks are automatically created in Oracle Identity Manager:
Section 3.4.5.1, "Scheduled Tasks for Reconciling Data About Users and Logins"
Section 3.4.5.2, "Scheduled Tasks for Reconciling Data About Deleted Users or Logins"
The following scheduled tasks are used to reconcile user or login data:
Scheduled tasks for target resource reconciliation
For IBM DB2 UDB: DBUM DB2 Target Resource User Reconciliation
For the Microsoft SQL Server login entity: DBUM MSSQL Target Resource Login Reconciliation
For the Microsoft SQL Server user entity: DBUM MSSQL Target Resource User Reconciliation
For MySQL: DBUM MySQL Target Resource User Reconciliation
For Oracle Database: DBUM Oracle Target Resource User Reconciliation
For the Sybase login entity: DBUM Sybase Target Resource Login Reconciliation
For the Sybase user entity: DBUM Sybase Target Resource User Reconciliation
Scheduled tasks for trusted source reconciliation
For IBM DB2 UDB: DBUM DB2 Trusted Source User Reconciliation
For Microsoft SQL Server: DBUM MSSQL Trusted Source User Reconciliation
For the MySQL: DBUM MySQL Trusted Source User Reconciliation
For Oracle Database: DBUM Oracle Trusted Source User Reconciliation
For the Sybase user entity: DBUM Sybase Trusted Source User Reconciliation
Table 3-2 describes the attributes of these scheduled tasks.
|
Note:
|
Table 3-2 Attributes of Scheduled Tasks for Fetching Data About Users or Logins During Target Resource Reconciliation
| Attribute | Description |
|---|---|
|
Batch Reconciliation Query Name |
Enter the name of the query that you want the connector to apply during batched reconciliation. Note: This attribute is valid only when the Use Batched Reconciliation attribute is set to Yes. This attribute is discussed later in this table. |
|
Batch Size |
Enter the number of records that must be included in each batch fetched from the target system.Default value: This attribute is discussed in Section 3.4.3, "Batched Reconciliation.". |
|
Custom Query |
Enter the query that you want the connector to apply during reconciliation. See Section 3.4.4, "Configuring Limited Reconciliation" for more information. Default value: Note: This attribute is valid only when the Use Custom Query attribute is set to Yes. If you enter a value for this attribute, then you must not enter a value for the Reconciliation Query Filter Lookup attribute. The Reconciliation Query Filter Lookup attribute is discussed later in this table. |
|
Is Login Recon |
Specifies whether or not reconciliation is to be carried out for the login entity of the target system. Enter |
|
Is Trusted Recon |
If you want reconciliation to be carried out in trusted mode, then enter |
|
IT Resource Name |
Enter the name of the IT resource that you configure by performing the procedure described in Section 2.3.5, "Configuring the IT Resource". Default value:
|
|
Last Execution Time |
This attribute holds the time stamp at which the last reconciliation run started. Default value: See Section 3.4.2, "Reconciliation Time Stamp" for information about setting a value for the Last Execution Time attribute. |
|
Query Name |
Enter the name of the query in the reconciliation query file that you want to run. Default value:
|
|
Reconciliation Attribute Mapping Lookup |
This attribute holds the name of the lookup definition that maps resource object attributes with column names or column name aliases used in the reconciliation query. For target resource reconciliation
For trusted source reconciliation
Note: You must not change this value. |
|
Reconciliation Query Filter Lookup |
This attribute holds the name of the lookup definition that contains information about reconciliation filter parameters. For target resource reconciliation
For trusted source reconciliation
Note: You must ensure that the filter parameters in this lookup definition can be applied along with the query specified by the Query Name attribute. An error is encountered if this condition is not met. |
|
Reconciliation Transformation Lookup |
This attribute holds the name of the lookup definition that is used to configure transformation of attribute values fetched from the target system during reconciliation. For target resource reconciliation
For trusted source reconciliation
Note: This attribute is valid only when the Use Transformation for Reconciliation attribute is set to Yes. That attribute is discussed later in this table. |
|
Reconciliation Validation Lookup |
This attribute holds the name of the lookup definition that is used to configure validation of attribute values that are fetched from the target system during reconciliation. For target resource reconciliation
For trusted source reconciliation
Note: This attribute is valid only when the Use Validation for Reconciliation attribute is set to Yes. That attribute is discussed later in this table. |
|
Recon Time Query Name |
Enter the name of the query in the reconciliation query file that is used to fetch the current time of the target system for incremental reconciliation. For IBM DB2 UDB, Microsoft SQL Server, MySQL, and Sybase, enter the name of the query that you create by performing Step 2 of Section 2.3.1.7, "Configuring the Connector for Incremental Reconciliation."
|
|
Resource Object Name |
This attribute holds the name of the resource object for the target system.
Note: Do not change the default value. However, if you create a copy of the resource object, then you can specify the name of the new resource object as the value of the Resource Object attribute. |
|
Status Reconciliation Primary Key Field |
Enter a value for this attribute only if you are writing your own implementation for determining the status of a target system record. While performing the procedure in Section 5.13, "Configuring Status Reconciliation,", you provide a value for the Status Reconciliation Class Name entry. If you are writing your own implementation, then enter the name of the primary key resource object attribute. Otherwise, enter |
|
Task Name |
This attribute holds the name of the scheduled task. For target resource reconciliation
For trusted source reconciliation
Note: For these scheduled tasks, you must not change the value of this attribute. However, if you create a copy of this scheduled task, then you must enter the unique name of that new scheduled task as the value of the Task Name attribute in that scheduled task. |
|
Use Batched Reconciliation |
Enter Default value: Note: If you set the value of this attribute to |
|
Use Custom Query |
Enter Default value: |
|
Use Resource Exclusion List |
Enter Default value: |
|
Use Transformation For Reconciliation |
Enter Default value: |
|
Use Validation For Reconciliation |
Enter Default value: |
Depending on whether you want to run target resource reconciliation or trusted source reconciliation, the following are the scheduled tasks that are used to reconcile data about deleted users or logins:
Scheduled tasks for target resource reconciliation
For IBM DB2 UDB: DBUM DB2 Target Delete Reconciliation
For the Microsoft SQL Server login entity: DBUM MSSQL Target Delete Login Reconciliation
For the Microsoft SQL Server user entity: DBUM MSSQL Target Delete User Reconciliation
For MySQL: DBUM MySQL Target Delete User Reconciliation
For Oracle Database: DBUM Oracle Target Delete Reconciliation
For the Sybase login entity: DBUM Sybase Target Delete Login Reconciliation
For the Sybase user entity: DBUM Sybase Target Delete User Reconciliation
Scheduled tasks for trusted source reconciliation
For IBM DB2 UDB: DBUM DB2 Trusted Delete Reconciliation
For Microsoft SQL Server: DBUM MSSQL Trusted Delete Reconciliation
For MySQL: DBUM MySQL Trusted Delete Reconciliation
For Oracle Database: DBUM Oracle Trusted Delete Reconciliation
For Sybase: DBUM Sybase Trusted Delete Reconciliation
Table 3-3 describes the attributes of these scheduled tasks.
|
Note:
|
Table 3-3 Attributes of Scheduled Tasks for Fetching Data About Deleted Users or Logins During Target Resource Reconciliation
| Attribute | Description |
|---|---|
|
Delete Reconciliation Attribute Mapping Lookup |
This attribute holds the name of the lookup definition that holds mappings between the target system and the process form fields. Default value for target resource reconciliation:
Default value for trusted source reconciliation:
Note: You must not change this value. |
|
Is Login Recon |
Set the value of this attribute to |
|
IT Resource Name |
Enter the name of the IT resource that you configure by performing the procedure described in Section 2.3.5, "Configuring the IT Resource".
|
|
Query Name |
This attribute holds the name of the query for reconciliation of deleted records.
|
|
Resource Object Name |
This attribute holds the name of the resource object for the target system.
Note: Do not change the default value. However, if you create a copy of the resource object, then you can specify the name of the new resource object as the value of the Resource Object attribute. |
|
Task Name |
This attribute holds the name of the scheduled task. For target resource reconciliation
For trusted source reconciliation
Note: For this scheduled task, you must not change the value of this attribute. However, if you create a copy of this scheduled task, then you must enter the unique name of that new scheduled task as the value of the Task Name attribute in that scheduled task. |
This section describes the procedure to configure scheduled tasks. You can apply this procedure to configure the scheduled tasks for lookup field synchronization and reconciliation.
The following is a list of scheduled tasks that you must configure:
For lookup field synchronization
DBUM Lookup reconciliation
For target resource user or login data reconciliation
For IBM DB2 UDB: DBUM DB2 Target Resource User Reconciliation
For the Microsoft SQL Server login entity: DBUM MSSQL Target Resource Login Reconciliation
For the Microsoft SQL Server user entity: DBUM MSSQL Target Resource User Reconciliation
For MySQL: DBUM MySQL Target Resource User Reconciliation
For Oracle Database: DBUM Oracle Target Resource User Reconciliation
For the Sybase login entity: DBUM Sybase Target Resource Login Reconciliation
For the Sybase user entity: DBUM Sybase Target Resource User Reconciliation
For target resource reconciliation of deleted users or logins
For IBM DB2 UDB: DBUM DB2 Target Delete Reconciliation
For the Microsoft SQL Server login entity: DBUM MSSQL Target Delete Login Reconciliation
For the Microsoft SQL Server user entity: DBUM MSSQL Target Delete User Reconciliation
For MySQL: DBUM MySQL Target Delete User Reconciliation
For Oracle Database: DBUM Oracle Target Delete Reconciliation
For the Sybase login entity: DBUM Sybase Target Delete Login Reconciliation
For the Sybase user entity: DBUM Sybase Target Delete User Reconciliation
For trusted source reconciliation of deleted users or logins
For IBM DB2 UDB: DBUM DB2 Trusted Delete Reconciliation
For Microsoft SQL Server: DBUM MSSQL Trusted Delete Reconciliation
For MySQL: DBUM MySQL Trusted Delete Reconciliation
For Oracle Database: DBUM Oracle Trusted Delete Reconciliation
For the Sybase: DBUM Sybase Trusted Delete Reconciliation
To configure a scheduled task:
Log in to the Administrative and User Console.
Do one of the following:
If you are using Oracle Identity Manager release 9.1.0.x, expand Resource Management, and then click Manage Scheduled Task.
If you are using Oracle Identity Manager release 11.1.1, on the Welcome page, click Advanced in the upper-right corner of the page.
Search for and open the scheduled task as follows:
If you are using Oracle Identity Manager release 9.1.0.x, then:
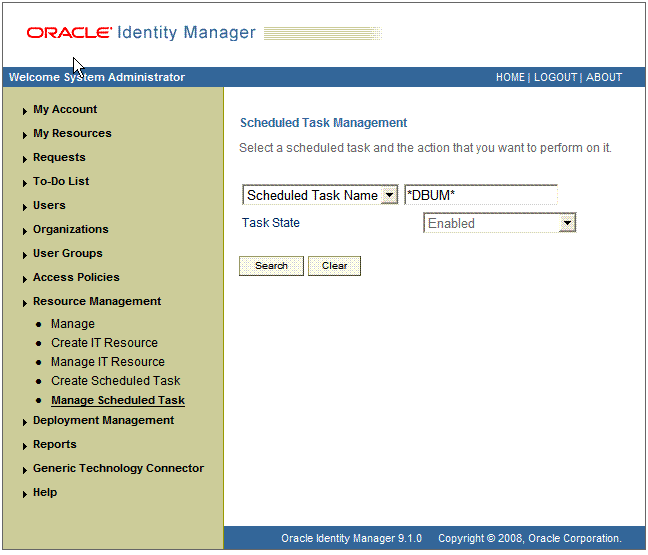
On the Scheduled Task Management page, enter the name of the scheduled task as the search criterion and then click Search.
The following screenshot shows the Scheduled Task Management page:
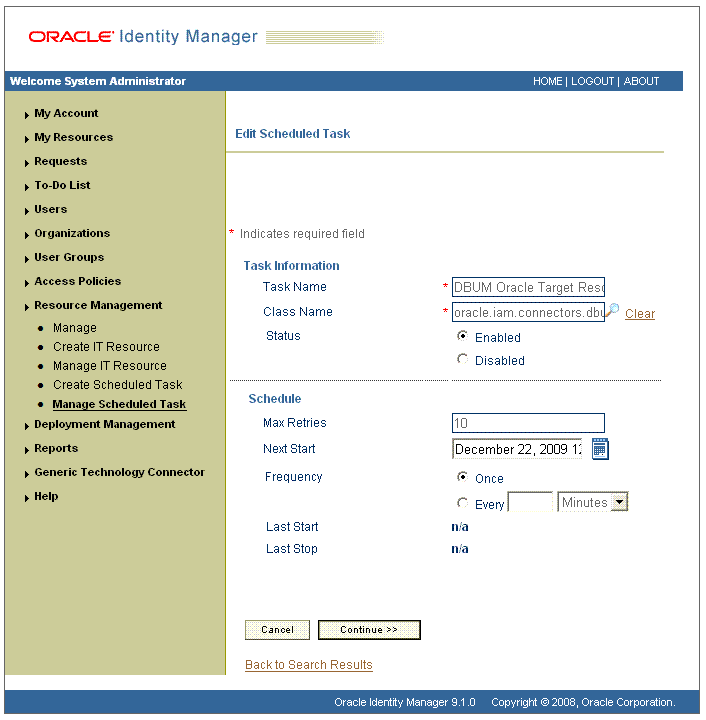
In the search results table, click the edit icon in the Edit column for the scheduled task.
The Edit Scheduled Task Details page is displayed. This is shown in the following screenshot:
If you are using Oracle Identity Manager release 11.1.1, then:
On the Welcome to Oracle Identity Manager Advanced Administration page, in the System Management region, click Search Scheduled Jobs.
On the left pane, in the Search field, enter the name of the scheduled job as the search criterion. Alternatively, you can click Advanced Search and specify the search criterion.
In the search results table on the left pane, click the scheduled job in the Job Name column.
Modify the details of the scheduled task. To do so:
If you are using Oracle Identity Manager release 9.1.0.x, on the Edit Scheduled Task Details page, you can modify the following parameters, and then click Continue:
Status: Specify whether you want to leave the task in the enabled state. In the enabled state, the task is ready for use.
Max Retries: Enter an integer value in this field. This number represents the number of times Oracle Identity Manager must attempt to complete the task before assigning the ERROR status to the task. The default value is 1.
Next Start: Use the date editor to specify the date when you want the task to run. After you select a date value in the date editor, you can modify the time value that is automatically displayed in the Next Start field.
Frequency: Specify the frequency at which you want the task to run.
If you are using Oracle Identity Manager release 11.1.1, on the Job Details tab, you can modify the following parameters:
Retries: Enter an integer value in this field. This number represents the number of times the scheduler tries to start the job before assigning the Stopped status to the job.
Schedule Type: Depending on the frequency at which you want the job to run, select the appropriate schedule type.
|
Note: See Oracle Fusion Middleware System Administrator's Guide for Oracle Identity Manager for detailed information about schedule types. |
In addition to modifying the job details, you can enable or disable a job.
Specify values for the attributes of the scheduled task. To do so:
|
Note:
|
If you are using Oracle Identity Manager release 9.1.0.x, on the Attributes page, select each attribute from the Attribute list, specify a value in the field provided, and then click Update.
The following screenshot shows the Attributes page. The attributes of the scheduled task that you select for modification are displayed on this page.
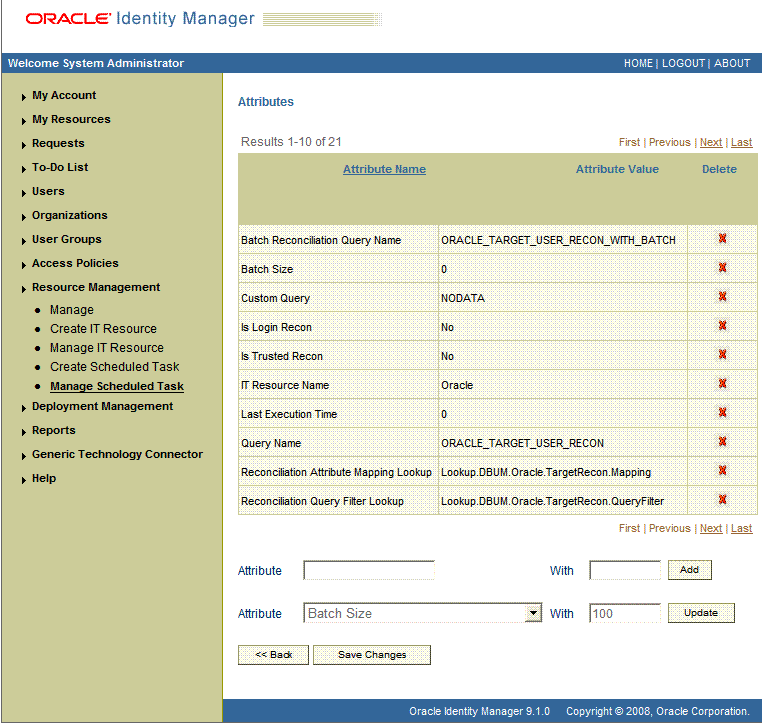
If you are using Oracle Identity Manager release 11.1.1, on the Job Details tab, in the Parameters region, specify values for the attributes of the scheduled task.
After specifying the attributes, do one of the following:
If you are using Oracle Identity Manager release 9.1.0.x, then click Save Changes to save the changes.
|
Note: The Stop Execution option is not available in the Administrative and User Console. If you want to stop a task, then click Stop Execution on the Task Scheduler form of the Design Console. |
If you are using Oracle Identity Manager release 11.1.1, then click Apply to save the changes.
|
Note: The Stop Execution option is available in the Administrative and User Console. You can use the Scheduler Status page to either start, stop, or reinitialize the scheduler. |
The following sections discuss guidelines that you must apply while performing provisioning operations:
Section 3.6.1, "Guidelines Common to Performing Provisioning Operations on Any Target System"
Section 3.6.2, "Guidelines on Performing Provisioning Operations in IBM DB2 UDB"
Section 3.6.3, "Guidelines on Performing Provisioning Operations in Microsoft SQL Server"
Section 3.6.4, "Guidelines on Performing Provisioning Operations in Oracle Database"
Section 3.6.5, "Guidelines on Performing Provisioning Operations in Sybase"
The following are guidelines that you must apply while performing provisioning operations on any target system:
Before you perform provisioning operations, lookup definitions must be synchronized with the lookup fields of the target system. In other words, the scheduled task for lookup field synchronization DBUM Lookup reconciliation must be run before provisioning operations.
Passwords for user accounts provisioned from Oracle Identity Manager must adhere to the password policy set in the target system.
The character length of target system fields must be taken into account when specifying values for the corresponding Oracle Identity Manager fields.
During an update password provisioning operation, ensure that you clear the existing text in the Password field, and then enter the new password. If you modify the password by appending new characters to the existing value, then the newly added characters will be displayed in clear text.
The following are guidelines that you must apply while performing provisioning operations on IBM DB2 UDB:
Authentication on IBM DB2 UDB is performed through the operating system. Therefore, the user that you want to provision must exist in the account database of the operating system.
For example, if you want to provision the domain, then the target (IBM DB2 UDB server) must exist on the domain server and the user that you want to provision must exist in the domain.
IBM DB2 UDB performs authentication externally and authorization internally. Authentication is performed through an accountID and password pair that is passed on to an external certifier. By default, the operating system performs the authentication. However, other programs can be used for this purpose. Authorization is done by mapping the accountID internally to various permissions at the database, index, package, schema, server, table, and/or table space level. When you perform provisioning operations on IBM DB2 UDB, keep in mind the following points:
Granting authorization does not automatically authenticate the accountID. You can, for example, authorize nonexistent accounts.
Revoking authorization does not remove publicly available authority from an accounted.
The following are guidelines that you must apply while performing provisioning operations on Microsoft SQL Server:
Before you provision a Microsoft SQL Server account that uses Microsoft Windows authentication, you must ensure that the account you want to provision exists in the account database of the operation system.
If you are creating users accounts, then you must specify a value for the Database Name parameter of the IT resource. See Table 2-9 for more information about the Database Name parameter.
If you are provisioning a Microsoft SQL Server login account that uses Microsoft Windows authentication, then you must specify values for the following fields:
Default Database: Select the name of the default database that the user must connect to.
Default Language: Select the default language for the login.
Login Name: Enter the login name in the following format:
DOMAIN_NAME\LOGIN_NAME
In this format:
DOMAIN_NAME is the name of the domain to which the login account must belong.
LOGIN_NAME is the name of the login that you are creating in the target system.
The following is a sample value that you can enter in the Login Name field:
MyDomain\jdoe
If you are provisioning a Microsoft SQL Server login account that uses SQL Server authentication, then you must specify values for the following mandatory fields:
Login Name: Enter the name of the login account.
Password: Enter the password for the login account.
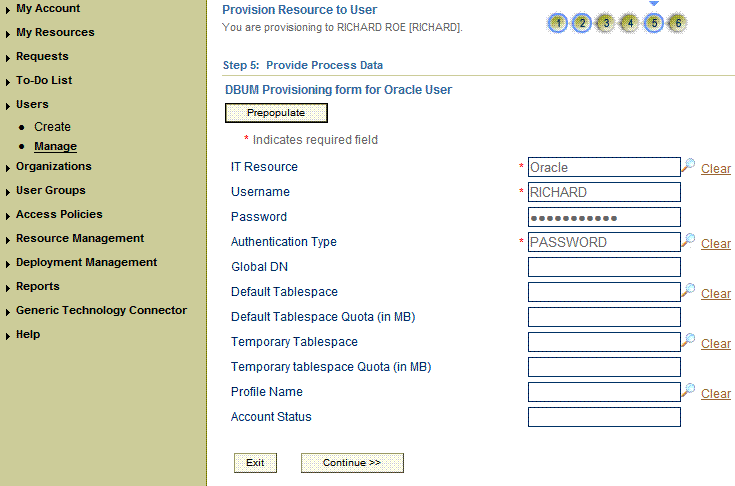
The following are guidelines that you must apply while performing provisioning operations on Oracle Database:
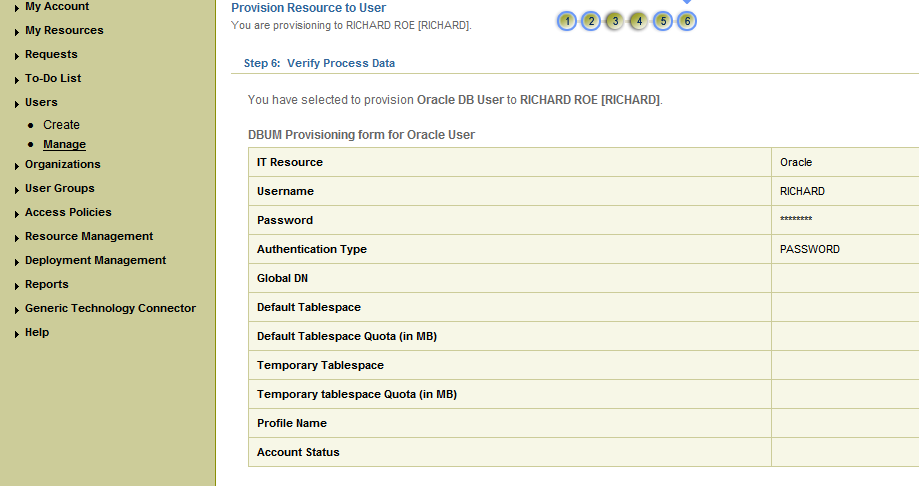
During a Create User provisioning operation, the following are some of the fields that are optional:
Default Tablespace
Temporary Tablespace
Profile Name
If you specify a value for any of these fields during a Create User provisioning operation, then you must not leave them empty during an Update User provisioning operation. Otherwise, the provisioning operation will fail. However, you can modify the existing values in these fields.
Before you provision an externally-authenticated user account, you must ensure that the account you want to provision must exist in the account database of the operation system.
For creating password-authenticated database users, you must specify values for the following fields:
IT Resource: Specify Oracle as the value of this lookup field.
Username: Enter the name of the database user.
Password: Enter the password for the database user.
Authentication Type: Specify PASSWORD as the value of this lookup field.
For creating globally-authenticated database users, you must specify a value for the following mandatory fields:
IT Resource: Specify Oracle as the value of this lookup field.
Username: Enter the name of the database user.
Authentication Type: Specify GLOBAL as the value of this lookup field.
Global DN: Enter the distinguished name (DN) for your organization.
Sample value: cn=ajones,cn=users,dc=oracle,dc=vm
After you submit the data required, the adapter runs the following query to create a globally-authenticated database user:
CREATE USER :ora_user_id IDENTIFIED GLOBALLY AS :ora_global_dn
For creating externally-authenticated database users, you must specify a value for the following mandatory fields:
IT Resource: Specify Oracle as the value of this lookup field.
Username: Enter the name of the database user in the following format:
OS_Authent_PrefixDomain_Name\User_Name
In this format:
OS_Authent_Prefix is a prefix that Oracle adds to every user's operating system account name.
Domain_Name is the name of the domain to which the user account being created must belong.
User_Name is the name of the user account existing in the operating system database.
Sample value: OPS$my_domain\jdoe
Authentication Type: Specify EXTERNAL as the value of this lookup field.
After you submit the data required, the adapter runs the following query to create a externally-authenticated database user:
CREATE USER :ora_user_id_external IDENTIFIED EXTERNALLY
If you specify values for the Default Tablespace Quota (in MB) or Temporary Tablespace Quota (in MB) fields, then enter values in the following format:
TABLESPACE_QUOTA M
In this format, TABLESPACE_QUOTA is the tablespace quota allocated to the user and M indicates that megabytes is the unit of measurement of quota. The following is a sample value: 300 M
If you want to allocate to a user unlimited quota on a tablespace, then specify the following as the value of the Default Tablespace Quota (in MB) or Temporary Tablespace Quota (in MB) fields:
UNLIMITED
If you are using Sybase for creating users accounts, then you must specify a value for the Database Name parameter of the IT resource. See Table 2-9 for more information about the Database Name parameter.
Provisioning a resource for an OIM User involves using Oracle Identity Manager to create a target system account for the user.
When you install the connector on Oracle Identity Manager release 11.1.1, the direct provisioning feature is automatically enabled. This means that the process form is enabled when you install the connector.
If you configure the connector for request-based provisioning, then the process form is suppressed and the object form is displayed. In other words, direct provisioning is disabled when you configure the connector for request-based provisioning. If you want to revert to direct provisioning, then see Section 3.8, "Switching Between Request-Based Provisioning and Direct Provisioning on Oracle Identity Manager Release 11.1.1."
This following are types of provisioning operations:
|
See Also: Oracle Identity Manager Connector Concepts for information about the types of provisioning |
This section discusses the following topics:
To provision a resource by using the direct provisioning approach:
Log in to the Administrative and User Console.
If you want to first create an OIM User and then provision a database account to the user, then:
If you are using Oracle Identity Manager release 9.1.0.x, then:
From the Users menu, select Create.
On the Create User page, enter values for the OIM User fields and then click Create User.
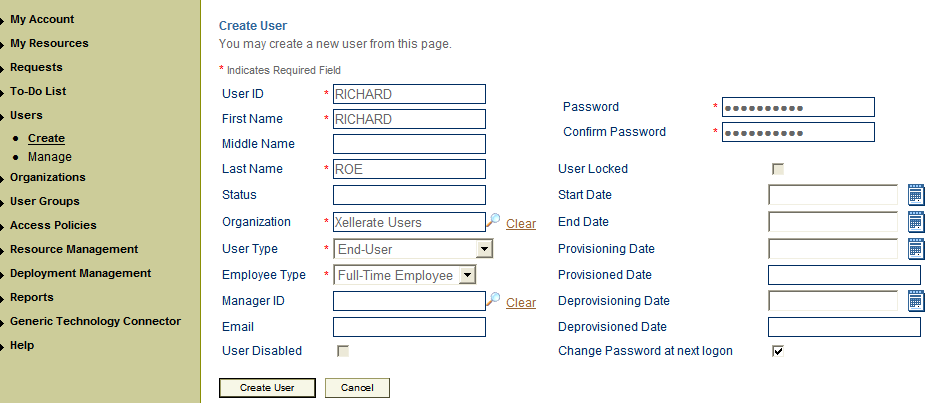
If you are using Oracle Identity Manager release 11.1.1, then:
On the Welcome to Identity Administration page, in the Users region, click Create User.
On the Create User page, enter values for the OIM User fields, and then click Save.
If you want to provision a database account to an existing OIM User, then:
If you are using Oracle Identity Manager release 9.1.0.x, then:
From the Users menu, select Manage.
Search for the OIM User, and select the link for the user from the list of users displayed in the search results.
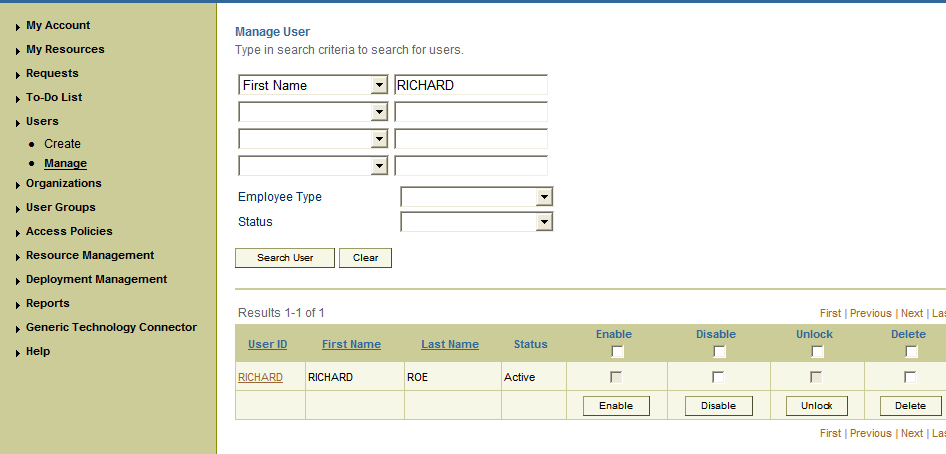
If you are using Oracle Identity Manager release 11.1.1, then:
On the Welcome to Identity Administration page, search for the user by selecting Users from the Search list on the left pane.
Alternatively, in the Users region, click Advanced Search - User, provide a search criterion, and then click Search.
From the list of users displayed in the search results, select the OIM User.
The user details page is displayed.
Depending on the Oracle Identity Manager release you are using, perform one of the following steps:
If you are using Oracle Identity Manager release 9.1.0.x, then:
On the User Detail page, select Resource Profile from the list at the top of the page.
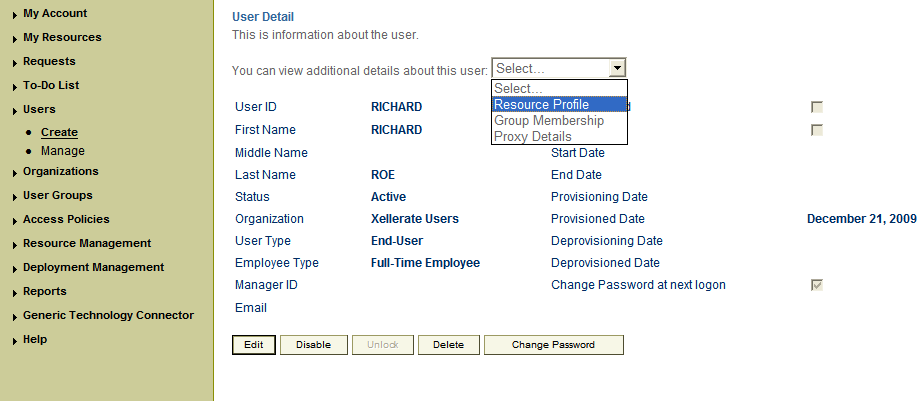
On the Resource Profile page, click Provision New Resource.
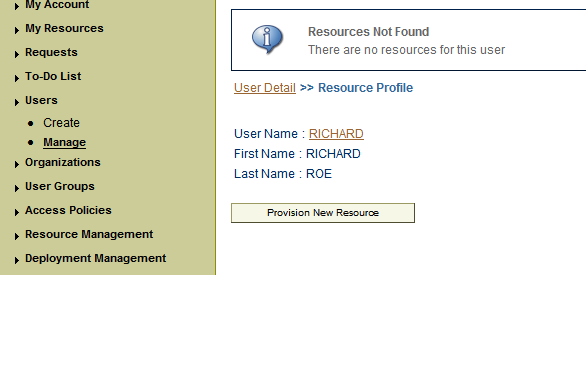
If you are using Oracle Identity Manager release 11.1.1, then:
On the user details page, click the Resources tab.
From the Action menu, select Add Resource. Alternatively, you can click the add resource icon with the plus (+) sign. The Provision Resource to User page is displayed in a new window.
On the Step 1: Select a Resource page, depending on the target system that you are using, select the appropriate resource from the list, and then click Continue.
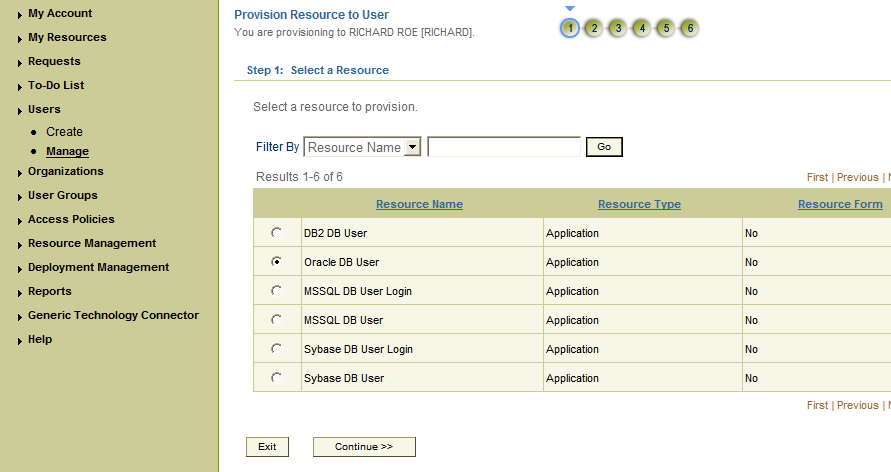
On the Step 2: Verify Resource Selection page, click Continue.
On the Step 5: Provide Process Data page, enter the details of the account that you want to create on the target system and then click Continue.
If you want to provide child data, then on the Step 5: Provide Process Data page for child data, search for and select the child data for the user on the target system and then click Continue. Repeat the same step if you have more than one child data and you want to provision them.
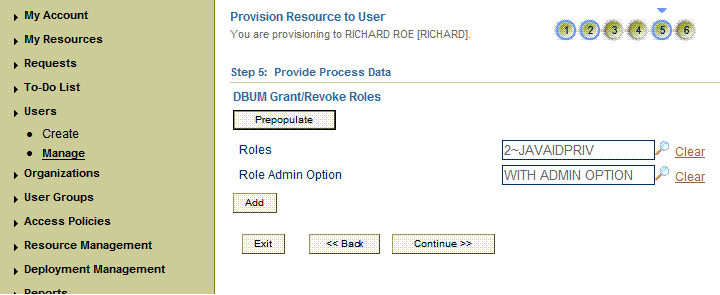
On the Step 6: Verify Process Data page, verify the data that you have provided and then click Continue.
The "Provisioning has been initiated" message is displayed. Perform one of the following steps:
If you are using Oracle Identity Manager release 9.1.0.x, click Back to User Resource Profile. The Resource Profile page shows that the resource has been provisioned to the user.
If you are using Oracle Identity Manager release 11.1.1, then:
Close the window displaying the "Provisioning has been initiated" message.
On the Resources tab, click Refresh to view the newly provisioned resource.
|
See Also: Section 1.7, "Connector Objects Used During Provisioning" for more information about the provisioning functions supported by this connector and the process form fields used for provisioning |
|
Note: The information provided in this section is applicable only if you are using Oracle Identity Manager release 11.1.1. |
A request-based provisioning operation involves both end users and approvers. Typically, these approvers are in the management chain of the requesters. The following sections discuss the steps to be performed by end users and approvers during a request-based provisioning operation:
|
Note: The procedures described in these sections are built on an example in which the end user raises or creates a request for provisioning a target system account. This request is then approved by the approver |
Section 3.7.2.1, "End User's Role in Request-Based Provisioning"
Section 3.7.2.2, "Approver's Role in Request-Based Provisioning"
The following steps are performed by the end user in a request-based provisioning operation:
|
See Also: Oracle Fusion Middleware User's Guide for Oracle Identity Manager for detailed information about these steps |
Log in to the Administrative and User Console.
On the Welcome page, click Advanced in the upper-right corner of the page.
On the Welcome to Identity Administration page, click the Administration tab, and then click the Requests tab.
From the Actions menu on the left pane, select Create Request.
The Select Request Template page is displayed.
From the Request Template list, select Provision Resource and click Next.
On the Select Users page, specify a search criterion in the fields to search for the user that you want to provision the resource, and then click Search. A list of users that match the search criterion you specify is displayed in the Available Users list.
From the Available Users list, select the user to whom you want to provision the account.
If you want to create a provisioning request for more than one user, then from the Available Users list, select users to whom you want to provision the account.
Click Move or Move All to include your selection in the Selected Users list, and then click Next.
On the Select Resources page, click the arrow button next to the Resource Name field to display the list of all available resources.
From the Available Resources list, select AD User, move it to the Selected Resources list, and then click Next.
On the Resource Details page, enter details of the account that must be created on the target system, and then click Next.
On the Justification page, you can specify values for the following fields, and then click Finish.
Effective Date
Justification
A message confirming that your request has been sent successfully is displayed along with the Request ID.
If you click the request ID, then the Request Details page is displayed.
To view details of the approval, on the Request Details page, click the Request History tab.
The following are steps performed by the approver in a request-based provisioning operation:
Log in to the Administrative and User Console.
On the Welcome page, click Self-Service in the upper-right corner of the page.
On the Welcome to Identity Manager Self Service page, click the Tasks tab.
On the Approvals tab, in the first section, you can specify a search criterion for request task that is assigned to you.
From the search results table, select the row containing the request you want to approve, and then click Approve Task.
A message confirming that the task was approved is displayed.
|
Note: It is assumed that you have performed the procedure described in Section 2.3.1.8, "Configuring Oracle Identity Manager for Request-Based Provisioning." |
On Oracle Identity Manager release 11.1.1, if you want to switch from request-based provisioning to direct provisioning, then:
Log in to the Design Console.
Disable the Auto Save Form feature as follows:
Expand Process Management, and then double-click Process Definition.
Search for and open the process definition for the target system that you are using:
See Section 4.5, "Configuring the Connector for Multiple Installations of the Target System" for a listing of the process definition for each target system.
Deselect the Auto Save Form check box.
Click the Save icon.
If the Self Request Allowed feature is enabled, then:
Expand Resource Management, and then double-click Resource Objects.
If you have configured the target system as a trusted source, then search for and open the DBUM Trusted Source resource object.
If you have configured the target system as a target resource, then search for and open one of the following resource objects:
For IBM DB2 UDB: DB2 DB User
For Microsoft SQL Server login entity: MSSQL User Login
For Microsoft SQL Server user entity: MSSQL User
For MySQL: MySQL DB User
For Oracle Database: Oracle DB User
For Sybase login entity: Sybase DB User Login
For Sybase user entity: Sybase DB User
Deselect the Self Request Allowed check box.
Click the Save icon.
On Oracle Identity Manager release 11.1.1, if you want to switch from direct provisioning back to request-based provisioning, then:
Log in to the Design Console.
Enable the Auto Save Form feature as follows:
Expand Process Management, and then double-click Process Definition.
Search for and open the process definition for the target system that you are using:
See Section 4.5, "Configuring the Connector for Multiple Installations of the Target System" for a listing of the process definition for each target system.
Select the Auto Save Form check box.
Click the Save icon.
If you want to enable end users to raise requests for themselves, then:
Expand Resource Management, and then double-click Resource Objects.
If you have configured the target system as a trusted source, then search for and open the DBUM Trusted Source resource object.
If you have configured the target system as a target resource, then search for and open one of the following resource objects:
For IBM DB2 UDB: DB2 DB User
For Microsoft SQL Server login entity: MSSQL User Login
For Microsoft SQL Server user entity: MSSQL User
For MySQL: MySQL DB User
For Oracle Database: Oracle DB User
For Sybase login entity: Sybase DB User Login
For Sybase user entity: Sybase DB User
Select the Self Request Allowed check box.
Click the Save icon.