| Oracle® Identity Manager Connector Guide for SAP User Management Engine Release 9.1.0 E17554-01 |
|
 Previous |
 Next |
| Oracle® Identity Manager Connector Guide for SAP User Management Engine Release 9.1.0 E17554-01 |
|
 Previous |
 Next |
Oracle Identity Manager automates access rights management, security, and provisioning of IT resources. Oracle Identity Manager connectors are used to integrate Oracle Identity Manager with external, identity-aware applications. This guide discusses the connector that enables you to use SAP User Management Engine as a managed (target) resource of Oracle Identity Manager.
|
Note: At some places in this guide, SAP User Management Engine has been referred to as the target system. |
In the account management (target resource) mode of the connector, data about users created or modified directly on the target system can be reconciled into Oracle Identity Manager. This data is used to provision (allocate) new resources or update resources already assigned to OIM Users. In addition, you can use Oracle Identity Manager to provision or update SAP User Management Engine resources assigned to OIM Users. These provisioning operations performed on Oracle Identity Manager translate into the creation of or updates to target system accounts.
This chapter contains the following sections:
Section 1.5, "Lookup Definitions Used During Connector Operations"
Section 1.8, "Roadmap for Deploying and Using the Connector"
Table 1-1 lists certified components for the connector.
Table 1-1 Certified Components
| Component | Requirement |
|---|---|
|
Oracle Identity Manager release 9.1.0.2 BP 04 or later See the following Oracle Technology Network Web page for information about certified components of Oracle Identity Manager:
|
|
|
JDK |
JDK 1.5 or later |
|
SAP User Management Engine running on SAP NetWeaver '04 SPS 14 or SAP NetWeaver 7.0 SPS 05 |
|
|
You must configure the Compliant User Provisioning module included in SAP GRC versions 5.2 SP4 or later and 5.3 SP5 or later. |
|
|
The connector uses OpenSPML Toolkit 2.0 (openspml2-toolkit.jar). See Section 2.1.1.4, "Copying OpenSPML Toolkit 2.0" for more information about addressing this requirement. |
The connector sets up Oracle Identity Manager as the front end for sending account creation or modification requests to applications that use the data source linked with SAP User Management Engine. These requests are processed and then forwarded by the Complaint User Provisioning module of SAP GRC.
Account data added or modified through provisioning operations performed directly on the data source can be reconciled into Oracle Identity Manager through SAP User Management Engine.
Figure 1-1 shows the connector integrating SAP User Management Engine with Oracle Identity Manager.
Figure 1-1 Connector Integrating SAP User Management Engine with Oracle Identity Manager
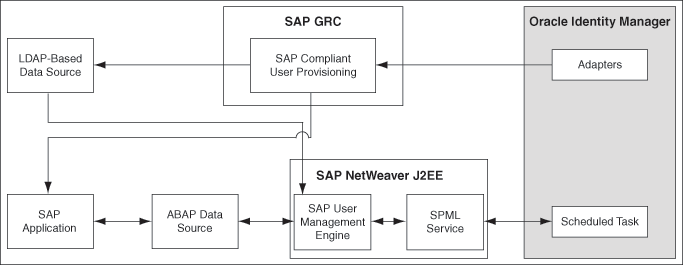
As shown in the figure, SAP User Management Engine is configured as the management tool for user data stored on a data source, which is either the ABAP module or an LDAP-based solution. User data changes made through the SAP User Management Engine UI are reflected on the SAP applications that use the data source or on the UI of the LDAP-based solution.
By deploying the connector, you configure SAP User Management Engine as a target resource of Oracle Identity Manager.
Provisioning requests sent from Oracle Identity Manager are routed through SAP GRC to the application or system that uses the data source linked with SAP User Management Engine. User data changes resulting from the provisioning requests can be viewed through the SAP User Management Engine UI. Reconciliation is performed directly from SAP User Management Engine.
During provisioning, adapters carry provisioning data submitted through the process form to the target system. The Compliant User Provisioning module of SAP GRC accepts provisioning data from the adapters, creates requests, and then forwards the requests to the application or system that forms the front end of the SAP User Management Engine data source.
In Compliant User Provisioning, workflows for processing these requests can be configured and users designated as approvers act upon these requests.
Reconciliation does not involve the Compliant User Provisioning module. Scheduled tasks on Oracle Identity Manager fetch data from the target system to Oracle Identity Manager.
The following is the detailed sequence of steps performed during a provisioning operation:
The provisioning operation is initiated through direct provisioning and access policy changes.
The connector sends requests and receives responses through the following Web services of SAP GRC:
SAPGRC_AC_IDM_SUBMITREQUEST: This Web service is used to submit requests.
SAPGRC_AC_IDM_REQUESTSTATUS: This Web service is used to fetch request statuses.
SAPGRC_AC_IDM_AUDITTRAIL: This Web service is used to check if there are error messages in the SAP GRC Compliant User Provisioning logs.
The process form holds fields for both SAP User Management Engine and Compliant User Provisioning. However, for a Create User operation, only the Compliant User Provisioning fields (attributes) on the process form are used. Mappings for these fields are stored in the Lookup.SAP.CUP.ProvisionAttrMap and Lookup.SAP.CUP.ProvisionRoleAttrMap lookup definitions. If you specify values for any attribute that is not present in these lookup definitions, then the connector ignores those attributes during the Create User operation.
|
Note: SAP GRC Compliant User Provisioning does not process passwords. During Create User provisioning operations, any value entered in the Password field is directly propagated to SAP User Management Engine.See Section 3.7, "Guidelines on Performing Provisioning" for information about setting passwords when you configure Compliant User Provisioning. |
For a Modify User operation, a request is created only for attributes whose mappings are present in these lookup definitions. If you specify values for attributes that are not present in these lookup definitions, then the connector directly ignores those attributes.
When the request is created on SAP GRC Compliant User Provisioning, data sent back by Compliant User Provisioning is stored in the following read-only fields in Oracle Identity Manager:
Request ID: This field holds the request ID that is generated on SAP GRC Compliant User Provisioning. The request ID does not change during the lifetime of the request.
Request Status: This field holds the status of the request on SAP GRC Compliant User Provisioning. You configure and run the SAP CUP Status Update Recon scheduled task to fetch the latest status of the request from the target system. Section 3.5.3.3, "SAP CUP Status Update Recon" describes this scheduled task.
The request is passed through the workflow defined in SAP GRC Compliant User Provisioning. The outcome is one of the following:
If Compliant User Provisioning clears the request, then the outcome is the creation or modification of a user's account on the target system. The status of the request is set to Closed and a message is recorded in the Oracle Identity Manager logs.
If Compliant User Provisioning rejects the provisioning request, then the status of the request is set to Reject and a message is recorded in the Oracle Identity Manager logs.
If an error occurs during communication between Compliant User Provisioning and the target system, then the request remains in the Open state. A message stating that the operation has failed is recorded in the audit log associated with the request. An error message is displayed on the console.
SAP NetWeaver AS Java offers an SPML 1.0 compliant interface to manage users, groups, and roles in SAP User Management Engine over a network. The scheduled task provided by the connector acts as the SPML client to send SPML requests to the SPML service in this application server.
During reconciliation, a scheduled task establishes a connection with the SPML service. Reconciliation criteria are sent through SPML requests to this SPML service. The SPML service processes the requests and returns SPML responses containing user records that match the reconciliation criteria. The scheduled task brings these records to Oracle Identity Manager.
Each record fetched from the target system is compared with SAP User Management Engine resources that are already provisioned to OIM Users. If a match is found, then the update made to the record is copied to the SAP User Management Engine resource in Oracle Identity Manager. If no match is found, then the user ID of the record is compared with the user ID of each OIM User. If a match is found, then data in the target system record is used to provision an SAP User Management Engine resource to the OIM User.
The process form holds attributes for both SAP User Management Engine and Compliant User Provisioning. However, only the SAP User Management Engine fields (attributes) on the process form are used for reconciliation. Mappings for these fields are stored in the Lookup.SAP.UME.ReconAttrMap and Lookup.SAP.UME.ReconChildAttrMap lookup definitions.
The following are features of the connector:
Section 1.4.1, "Routing of Provisioning Requests Through SAP GRC Compliant User Provisioning"
Section 1.4.5, "Specifying Accounts to Be Excluded from Reconciliation and Provisioning Operations"
Section 1.4.6, "Transformation and Validation of Account Data"
Provisioning requests generated on Oracle Identity Manager are routed through SAP GRC Compliant User Provisioning. See Section 1.3.1, "Provisioning Process" for detailed information about this feature.
|
Note: The SPML UME API does not return records for which the Last Modified Date value is greater than a specified date. Therefore, the connector cannot support incremental reconciliation. This point is also mentioned in Section 5.2, "Connector Limitations Related to Features of the Target System." |
In full reconciliation, all records are fetched from the target system to Oracle Identity Manager. The list of valid characters allowed in SAP is stored in the Lookup.SAP.UME.FullReconFilter lookup definition. During reconciliation, an SPML request is sent to the target system to fetch user IDs that start with these characters. The second SPML request is sent to fetch the details of these users.
During full reconciliation, a single reconciliation event is generated for each target system account.
To limit or filter the records that are fetched into Oracle Identity Manager during a reconciliation run, you can specify the subset of added or modified target system records that must be reconciled.
See Section 3.5.2, "Limited Reconciliation" for more information.
Valid From and Valid Through are two user attributes on the target system. For a particular user in SAP, if the Valid Through date is less than the current date, then the account is in the Disabled state. Otherwise, the account is in the Enabled state. The same behavior is duplicated in Oracle Identity Manager through reconciliation. In addition, you can set the value of the Valid Through date to a current date or a date in the past through a provisioning operation.
|
Note: The Enabled or Disabled state of an account is not related to the Locked or Unlocked status of the account. |
You can specify a list of accounts that must be excluded from all reconciliation and provisioning operations. Accounts whose user IDs you specify in the exclusion list are not affected by reconciliation and provisioning operations.
See Section 2.3.5, "Setting Up the Lookup.SAP.UME.ExclusionList Lookup Definition" for more information.
You can configure validation of account data that is brought into or sent from Oracle Identity Manager during reconciliation and provisioning. In addition, you can configure transformation of account data that is brought into Oracle Identity Manager during reconciliation. The following sections provide more information:
Lookup definitions used during connector operations can be categorized as follows:
During a provisioning operation, you use a lookup field on the process form to specify a single value from a set of values. For example, you use the Role lookup field to select a role from the list of roles defined on the target system. When you deploy the connector, lookup definitions corresponding to the lookup fields on the target system are automatically created in Oracle Identity Manager. Lookup field synchronization involves copying additions or changes made to the target system lookup fields into the lookup definitions in Oracle Identity Manager.
|
Note: The target system allows you to use special characters in lookup fields. However, in Oracle Identity Manager, special characters are not supported in lookup definitions. |
The Lookup.SAP.UME.LookupMappings lookup definition is used to map each lookup definition with the data source from which values must be fetched for the lookup definition from the target system. The Code Key column of these lookup definitions contains names of the lookup definitions that are synchronized with the target system. The Decode column contains the data source name.
Table 1-2 lists the entries in these lookup definitions. The Decode column holds a list of parameters required to fetch values from each lookup field on the target system.
Table 1-2 Entries in the Lookup.SAP.UME.LookupMappings Lookup Definition
| Code Key | Decode |
|---|---|
|
Lookup.SAP.UME.Roles |
saprole |
|
Lookup.SAP.UME.Groups |
sapgroup |
The following is the format of entries in the lookup definitions listed in this table:
Code Key format: IT_RESOURCE_KEY~LOOKUP_FIELD_ID
In this format:
IT_RESOURCE_KEY is the numeric code assigned to the IT resource in Oracle Identity Manager.
LOOKUP_FIELD_ID is the target system code assigned to the lookup field entry.
Sample value: 1~SAP_EHS_SAF_UTIL
Decode format: IT_RESOURCE_NAME~LOOKUP_FIELD_ENTRY
In this format:
IT_RESOURCE_NAME is the name of the IT resource in Oracle Identity Manager.
LOOKUP_FIELD_ENTRY is the value or description of the lookup field entry on the target system.
Sample value: SAP UME IT Resource~Tools
The SAP UME Lookup Recon scheduled task is used to synchronize values of these lookup definitions with the target system. Section 3.2, "Scheduled Task for Lookup Field Synchronization" provides more information about this scheduled task.
While performing a provisioning operation on the Administrative and User Console, you select the IT resource for the target system on which you want to perform the operation. When you perform this action, the lookup definitions on the page are automatically populated with values corresponding to the IT resource (target system installation) that you select.
During lookup field synchronization, new entries are appended to the existing set of entries in the lookup definitions. Because the IT resource key is part of each entry created in each lookup definition, only lookup field entries that are specific to the IT resource you select during a provisioning operation are displayed.
Table 1-3 describes the other lookup definitions that are created in Oracle Identity Manager when you deploy the connector. These lookup definitions are either prepopulated with values or values must be manually entered in them after the connector is deployed.
Table 1-3 Preconfigured Lookup Definitions
| Lookup Definition | Description of Values | Method to Specify Values for the Lookup Definition |
|---|---|---|
|
Lookup.SAP.CUP.Configuration |
This lookup definition holds connector configuration entries that are used during reconciliation and provisioning by the Compliant User Provisioning feature. |
Section 2.3.7.4, "Setting Values in the Lookup.SAP.CUP.Configuration Lookup Definition" describes the entries for which you must set values. |
|
This lookup definition stores values that are used internally by the Compliant User Provisioning feature of the connector. The connector development team can use this lookup definition to make minor configuration changes in the connector. |
You must not modify the entries in this lookup definition. |
|
|
This lookup definition holds mappings between process form fields and single-valued attributes on SAP GRC Compliant User Provisioning. |
This lookup definition is preconfigured. Table 1-8 lists the default entries in this lookup definition. |
|
|
This lookup definition holds mappings between process form fields and multivalued attributes on SAP GRC Compliant User Provisioning. |
This lookup definition is preconfigured. Table 1-9 lists the default entries in this lookup definition. |
|
|
This lookup definition holds connector configuration entries that are used during reconciliation and provisioning. |
Some of the entries in this lookup definition are preconfigured. See Section 2.3.1, "Setting Values in the Lookup.SAP.UME.Configuration Lookup Definition" for information about the entries for which you can set values. |
|
|
This lookup definition stores values that are used internally by the connector. The connector development team can use this lookup definition to make minor configuration changes in the connector. |
You must not modify the entries in this lookup definition. |
|
|
This lookup definition holds user IDs of target system accounts for which you do not want to perform reconciliation and provisioning. |
You can enter user IDs in this lookup definition. See Section 2.3.5, "Setting Up the Lookup.SAP.UME.ExclusionList Lookup Definition" for more information. |
|
|
Lookup.SAP.UME.FullReconFilter |
This lookup definition contains the list of characters that can be used in the logon name of an SAP User Management Engine account. |
This lookup definition is preconfigured. You must not modify the entries in this lookup definition. |
|
These lookup definitions hold data required to synchronize other lookup definitions with the target system. |
This lookup definition is preconfigured. You must not modify the entries in this lookup definition. |
|
|
This lookup definition holds mappings between resource object fields and single-valued target system attributes. |
This lookup definition is preconfigured. Table 1-4 lists the default entries in this lookup definition. |
|
|
This lookup definition holds mappings between resource object fields and multivalued target system attributes. |
This lookup definition is preconfigured. Table 1-5 lists the default entries in this lookup definition. |
|
|
This lookup definition is used to configure transformation of attribute values that are fetched from the target system during user reconciliation. |
You manually create entries in this lookup definition. See Section 4.2, "Configuring Transformation of Data During User Reconciliation" for more information. |
|
|
This lookup definition is used to configure validation of attribute values that are fetched from the target system during reconciliation. |
You manually create entries in this lookup definition. See Section 4.1, "Configuring Validation of Data During Reconciliation and Provisioning" for more information. |
|
|
This lookup definition is used to hold the system IDs of application that use the data source with which SAP User Management Engine is linked. |
You manually create entries in this lookup definition. See Section 2.3.6, "Setting Up the Lookup.SAP.UME.System Lookup Definition" for more information. |
The SAP UME User Recon scheduled task is used to initiate a reconciliation run. This scheduled task is discussed in Section 3.5.3, "Reconciliation Scheduled Tasks".
|
See Also: The "Reconciliation" section in Oracle Identity Manager Connector Concepts for conceptual information about reconciliation |
This section discusses the following topics:
The Lookup.SAP.UME.ReconAttrMap lookup definition maps process form fields and target system attributes. The Code Key column stores the names of attributes in the SPML schema and the Decode column stores the labels of the process form fields.
Table 1-4 lists entries in this lookup definition.
Table 1-4 Entries in the Lookup.SAP.UME.ReconAttrMap Lookup Definition
| Target System Attribute | Process Form Label |
|---|---|
|
|
E Mail |
|
salutation |
Salutation |
|
title |
Title |
|
jobtitle |
Job Title |
|
mobile |
Mobile |
|
telephone |
Telephone Number |
|
fax |
Fax Number |
|
locale |
Locale |
|
timezone |
Time Zone |
|
department |
Department |
|
logonname |
User ID |
|
firstname |
First Name |
|
lastname |
Last Name |
|
validto |
Valid Through |
|
validfrom |
Valid From |
The Lookup.SAP.UME.ReconChildAttrMap lookup definition maps resource object fields and multivalued target system attributes. The Code Key column stores the names of attributes in the SPML schema, and the Decode column stores the names of reconciliation fields in the resource object.
Table 1-5 lists entries in this lookup definition.
|
See Also: Oracle Identity Manager Connector Concepts for generic information about reconciliation matching and action rules |
The following sections provide information about the reconciliation rules for this connector:
The following is the process-matching rule:
Rule name: SAP UME Recon Rule
Rule element: User Login Equals User ID
In this rule element:
User Login is the User ID field of the OIM User form.
User ID is the user ID of the SAP account.
After you deploy the connector, you can view the reconciliation rule for reconciliation by performing the following steps:
|
Note: Perform the following procedure only after the connector is deployed. |
Log in to the Oracle Identity Manager Design Console.
Expand Development Tools.
Double-click Reconciliation Rules.
Search for and open the SAP UME Recon Rule rule. Figure 1-2 shows this reconciliation rule.
|
Note: No action is performed for rule conditions that are not predefined for this connector. You can define your own action rule for such rule conditions. See Oracle Identity Manager Design Console Guide for information about modifying or creating reconciliation action rules. |
The following sections provide information about the reconciliation rules for this connector:
Section 1.6.3.1, "Reconciliation Action Rules for Reconciliation"
Section 1.6.3.2, "Viewing Reconciliation Action Rules in the Design Console"
Table 1-6 lists the action rules for reconciliation.
After you deploy the connector, you can view the reconciliation action rules for reconciliation by performing the following steps:
Log in to the Oracle Identity Manager Design Console.
Expand Resource Management, and double-click Resource Objects.
If you want to view the reconciliation action rules for reconciliation, then search for and open the SAP UME Resource Object resource object.
Click the Object Reconciliation tab, and then click the Reconciliation Action Rules tab. The Reconciliation Action Rules tab displays the action rules defined for this connector. Figure 1-3 shows the reconciliation action rules for reconciliation.
Provisioning involves creating or modifying user data on the target system through Oracle Identity Manager.
|
See Also: The "Provisioning" section in Oracle Identity Manager Connector Concepts for conceptual information about provisioning |
This section discusses the following topics:
Table 1-7 lists the supported user provisioning functions and the adapters that perform these functions. The functions listed in the table correspond to either a single or multiple process tasks.
|
See Also: Oracle Identity Manager Connector Concepts for generic information about process tasks and adapters |
Table 1-7 User Provisioning Functions
| Function | Adapter |
|---|---|
|
Create a user account |
UME Create User |
|
Update a user account |
UME Modify User |
|
Delete a user account |
UME Delete User |
|
Lock or unlock a user account |
UME Lock UnLock User |
|
UME Enable User |
|
|
UME Disable User |
|
|
UME Modify Password |
|
|
Add (provision) a multivalued attribute (for example, role or group) |
UME Add Multivalue Data |
|
Remove (revoke) a multivalued attribute (for example, role or group) |
UME Remove Multivalue Data |
|
Update a multivalued attribute (for example, role or group) |
UME Update Multivalue Data |
In the Compliant User Provisioning feature, the Lookup.SAP.CUP.ProvAttrMap lookup definition maps process form fields with single-valued attributes in SAP GRC Compliant User Provisioning. Table 1-8 lists entries in this lookup definition.
Table 1-8 Entries in the Lookup.SAP.CUP.ProvAttrMap Lookup Definition
| Process Form Field | Target System Attribute |
|---|---|
|
CUP Requestor ID |
requestorId;TEXT;STANDARD;NONE;MANDATORY |
|
CUP Requestor First Name |
requestorFirstName;TEXT;STANDARD;NONE;MANDATORY |
|
CUP Requestor Last Name |
requestorLastName;TEXT;STANDARD;NONE;MANDATORY |
|
CUP Requestor Email |
requestorEmailAddress;TEXT;STANDARD;NONE;MANDATORY |
|
E Mail |
emailAddress;TEXT;STANDARD;E_MAIL;MANDATORY |
|
First Name |
firstName;TEXT;STANDARD;FIRSTNAME;MANDATORY |
|
Last Name |
lastName;TEXT;STANDARD;LASTNAME;MANDATORY |
|
User ID |
userId;TEXT;STANDARD;NONE;MANDATORY |
|
Valid From |
validFrom;DATE;STANDARD;GLTGV;NONE |
|
Valid Through |
validTo;DATE;STANDARD;GLTGB;MANDATORY |
In the Compliant User Provisioning feature, the Lookup.SAP.CUP.ProvisionRoleAttrMap lookup definition maps process form fields with multivalued attributes (roles and profiles) in SAP GRC Compliant User Provisioning. Table 1-9 lists entries in this lookup definition.
The following is the organization of information in the rest of this guide:
Chapter 2, "Deploying the Connector" describes procedures that you must perform on Oracle Identity Manager and the target system during each stage of connector deployment.
Chapter 3, "Using the Connector" describes guidelines on using the connector and the procedure to configure reconciliation runs and perform provisioning operations.
Chapter 4, "Extending the Functionality of the Connector" describes the procedures to perform if you want to extend the functionality of the connector.
Chapter 5, "Known Issues and Limitations" lists known issues and limitations associated with this release of the connector.