| Oracle® OpenSSO STS Administrator's Guide Release 11gR1. Version 11.1.1.3.0 Part Number E17844-01 |
|
|
View PDF |
| Oracle® OpenSSO STS Administrator's Guide Release 11gR1. Version 11.1.1.3.0 Part Number E17844-01 |
|
|
View PDF |
The Oracle OpenSSO Security Token Service (OpenSSO STS) Authentication Service retrieves credentials from an end-user, administrator, or client application and validates the credentials against a configured identity repository. Use the Access Control interface to manage the authentication modules and user data stores that OpenSSO STS uses to authenticate incoming security token requests.
This chapter contains the following sections:
The Configuration > Authentication subtab is where you configure global properties for a type of authentication service. The following figures illustrates the subtab in the OpenSSO STS console where you configure global authentication service properties. The figure also lists the types of authentication service supported in OpenSSO STS.
Figure 6-1 Configuration > Authentication Subtab for Configuring Global Authentication Service Properties
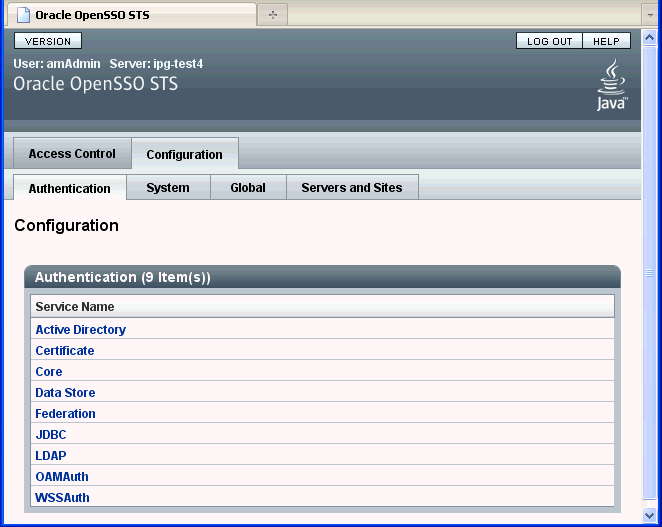
To Configure Active Directory Authentication Service Attributes
To Configure Certificate Authentication Service Realm Attributes
On the Configuration tab, click the Authentication subtab.
In the Authentication list, click Active Directory.
Provide values for the Active Directory Authentication Service Realm attributes. The following table provides a listing and descriptions of the attributes you can configure.
Table 6-1 Active Directory Authentication Service Realm Attributes
| Attribute | Description |
|---|---|
|
Primary Active Directory Server |
The Current Values list displays the host name and port number of the primary Active Directory server specified during OpenSSO STS installation. This is the first server contacted for Active Directory authentication. The format is hostname:port. The default port number is 389.
|
|
Secondary Active Directory Server |
The Current Values list displays the host name and port number of a secondary Active Directory server available to the OpenSSO STS platform. If the primary Active Directory server does not respond to a request for authentication, then this server is contacted. If the primary server is up, OpenSSO STS will switch back to the primary server.
|
|
DN to Start User Search |
The Current Values list displays the DN of the node where the search for a user starts.
|
|
DN for Root User Bind |
Specify the DN of the user that will be used to bind to the Directory Server specified in the Primary LDAP Server and Port fields as administrator. The authentication service must bind as this DN in order to search for a matching user DN based on the user login ID. The default is amldapuser. Any valid DN will be recognized. Make sure that password is correct before you logout. If it is incorrect, you will be locked out. If this should occur, you can login with the super user DN. By default, this the amAdmin account with which you would normally log in, although you will use the full DN. For example:
|
|
Password for Root User Bind |
Type the password for the administrator profile specified in the DN for Root User Bind field. There is no default value. Only the administrator's valid Active Directory password is recognized. |
|
Password for Root User Bind (confirm) |
Type the Root User Bind password again to confirm it. |
|
Attribute Used to Retrieve User Profile |
Specify the attribute used for the user entry naming convention. By default, OpenSSO STS assumes that user entries are identified by the uid attribute. If your Directory Server uses a different attribute such as givenname, specify the attribute name in this field. |
|
Attributes Used to Search for a User to be Authenticated |
The Current Values list displays the attributes to be used to form the search filter for a user that is to be authenticated, and that allows the user to authenticate with more than one attribute in the user's entry. For example, if this field is set to uid, employeenumber, and mail, then the user could authenticate with any of these names.
|
|
User Search Filter |
Displays the attributes to be used to find the user based on the value in the DN to Start User Search field. The filter works with the User Naming Attribute. There is no default value. Any valid user entry attribute will be recognized. |
|
Search Scope |
Choose the number of levels in the Directory Server that will be searched for a matching user profile. The search begins from the node specified in DN to Start User Search field. The default value is SUBTREE. Choose one of the following:
|
|
SSL Access to Active Directory Server |
When enabled, OpenSSO STS uses the SSL protocol to access the Directory Server specified in the Primary and Secondary Server and Port fields. By default, the box is not checked and the SSL protocol is not used to access the Directory Server. If the Active Directory server is running with SSL enabled (LDAPS), you must make sure that OpenSSO STS is configured with proper SSL trusted certificates. Otherwise OpenSSO STS cannot connect to Directory Server using the LDAPS protocol. |
|
Return User DN to Authenticate |
When enabled, the Active Directory authentication module instance returns the DN instead of the User ID, and no search is necessary. Normally, an authentication module instance returns only the User ID, and the authentication service searches for the user in the local OpenSSO STS instance. If the OpenSSO STS directory is the same as the directory configured for Active Directory, this option may be enabled. If an external Active Directory is used, this option is typically not enabled. |
|
Active Directory Server Check Interval |
Specify the number of minutes per interval in which a thread will "sleep" before verifying that the primary Active Directory server is running. This attribute is used for Active Directory Server failback. |
|
User Creation Attributes |
The Current Values list displays attributes used by the Active Directory authentication module instance when the Active Directory server is configured as an external Active Directory server. It contains a mapping of attributes between a local and an external Directory Server. The attribute uses the following form: attr1|externalattr1 attr2|externalattr2
|
|
Authentication Level |
Specify a value that indicates how much to trust an authentication mechanism. The default value is 0. The authentication level is set separately for each method of authentication. Once a user has authenticated, this value is stored in the If the authentication level stored in an SSOToken does not meet the minimum value required, the application can prompt the user to authenticate again through a service with a higher authentication level. 0 is a low value. For example, if the user accesses the URL protocol://openssoServer:openssoPort If no authentication level is specified, the SSO token stores the value specified in the Core Authentication attribute Default Authentication Level. |
On the Configuration tab, click the Authentication subtab.
In the Authentication list, click Certificate.
Provide values for the Certificate Authentication Realm attributes. The following table provides a listing and descriptions of the properties you can configure.
Table 6-2 Certificate Authentication Service Realm Attributes
| Attribute | Description |
|---|---|
|
Match Certificate in LDAP |
When enabled, the Certificate Authentication Module determines whether a user certificate presented at login is stored in the LDAP Server specified in the "LDAP Server Where Certificates are Stored" field below. If no match is found, then the user is denied access. If a match is found and no other validation is required, the user is granted access. By default, this option is disabled and the Certificate Authentication Module does not check for the user certificate. Note – A certificate stored in the Directory Server is not necessarily valid. It may be on the certificate revocation list. See Match Certificate to CRL. However, the web container may check the validity of the user certificate presented at login. |
|
Subject DN Attribute Used to Search LDAP for Certificates |
Specify the attribute of the certificate's SubjectDN value that will be used to search LDAP for certificates. This attribute must uniquely identify a user entry. The actual value will be used for the search. The default is cn. |
|
Match Certificate to CRL |
When enabled, the Certificate Authentication Module compares the user certificate against the Certificate Revocation List (CRL) in the LDAP Server. The CRL is located based on one of the attribute names in the issuer's SubjectDN. If the certificate is on the CRL, then the user is denied access. If the certificate is not on the CRL, then the user is allowed to proceed. By default this option is disabled. Certificates should be revoked when the owner of the certificate has changed status and no longer has the right to use the certificate or when the private key of a certificate owner has been compromised. |
|
Issuer DN Attribute Used to Search LDAP for CRLs |
Specify the attribute of the |
|
HTTP Parameters for CRL Update |
Specify the HTTP parameters for obtaining a CRL from a servlet for a CRL update. Contact the administrator of your CA for these parameters. |
|
OCSP Validation |
When enabled, Online Certificate Status Protocol (OCSP) validation is performed by contacting the appropriate OCSP responder. The OCSP responder is determined during runtime based on the following settings:
These settings can be configured on the Servers and Sites tab. Before enabling OCSP Validation, make sure that the time of day settings for the OpenSSO STS host and the OCSP responder host are synchronized as closely as possible. Also, the time of day setting for the OpenSSO STS host must be ahead of the time of day setting for the OCSP responder. For example, if the OCSP responder host is set at 12:00:00 PM, then the OpenSSO STS host could be set at 12:00:30 PM. |
|
LDAP Server Where Certificates are Stored |
The Current Values list displays the name and port number of the LDAP server where the certificates are stored. The default value is the host name and port specified when OpenSSO STS was installed.
|
|
LDAP Search Start DN |
The Current Values list displays the DN of the node where the search for the user's certificate should start.
Use the format servername|searchDN. There is no default value. You can enter any valid DN. Multiple entries must be prefixed by the local server name. Example: servername1|searchDN servername2|searchDN servername3|searchDN |
|
LDAP Server Principal User |
Specify the DN of the principal user for the LDAP server where the certificates are stored. There is no default value. You can use any valid DN. The principal user must be authorized to read, and search certificate information stored in the Directory Server. |
|
LDAP Server Principal Password |
Specify the LDAP password associated with the user specified in the LDAP Server Principal User field above. There is no default value. You can use any valid LDAP password for the specified principal user. This value is stored as readable text in the directory. |
|
LDAP Server Principal Password (confirm |
Type the password again to confirm it. |
|
Use SSL for LDAP Access |
Specifies whether to use SSL to access the LDAP server. The default is that the Certificate Authentication service does not use SSL for LDAP access. |
|
Certificate Field Used to Access User Profile |
From the following, choose the field in the certificate's Subject DN to be used to search for a matching user profile: email addressnoneothersubject CNsubject DNsubject UID
For example, if you choose email address, the Certificate Authentication service searches for the user profile that matches the attribute milder in the user certificate. The user logging in then uses the matched profile. The default field is subject CN. |
|
Other Certificate Field Used to Access User Profile |
This attribute is recognized only if 'other' is selected in the 'Certificate Field Used to Access User Profile' attribute above. Specify the attribute that will be selected from the received certificate's subjectDN value. The Certificate Authentication service will then search the user profile that matches the value of that attribute. |
|
SubjectAltNameExt Value Type to Access User Profile |
RFC822Name - Electronic email address UPN - User Principal Name none When 'none' is selected, the 'Certificate Field Used to Access User Profile' or 'Other Certificate Field Used to Access User Profile' attribute is used to access the User Profile. |
|
Trusted Remote Hosts |
The Current Values list displays hosts that can be trusted to send certificates to OpenSSO STS. OpenSSO STS must verify whether the certificate came from one of these hosts. This attribute is used for the Portal Server gateway, for a load balancer with SSL termination and for Distributed Authentication. By default, this attribute is set to 'none,' which disables certificate issuer host verification.
|
|
SSL Port Number |
Specify the port number for the secure socket layer (SSL). Currently, this attribute is only used by the Gateway servlet. Before you add or change an SSL Port Number, see the "Policy-Based Resource Management" section in the OpenSSO STS Administration Guide. |
|
HTTP Header Name for Client Certificate |
This attribute is used only when the Trusted Remote Hosts attribute is set to all' or has a specific host name defined. Specify the HTTP header name for the client certificate that is inserted by the load balancer or Secure Remote Access component. |
|
Authentication Level |
Specify a value that indicates how much to trust an authentication mechanism. The default value is 0. The authentication level is set separately for each method of authentication. Once a user has authenticated, this value is stored in the If the authentication level stored in an SSOToken does not meet the minimum value required, the application can prompt the user to authenticate again through a service with a higher authentication level. 0 is a low value. For example, if the user accesses the URL protocol://openssoServer:openssoPort If no authentication level is specified, the SSO token stores the value specified in the Core Authentication attribute Default Authentication Level. |
On the Configuration tab, click the Authentication subtab.
In the Authentication list, click Core.
On the Core page, provide values for the Core Authentication Service global attributes. The following table provides a listing and descriptions of the properties you can configure.
Table 6-3 Core Authentication Service Global Attributes
| Attribute | Description |
|---|---|
|
Pluggable Authentication Module Classes |
The Current Values list displays the Java classes of the available authentication modules.
|
|
Supported Authentication Modules for Clients |
The Current Values list displays authentication modules supported for a specific client. Formatted as:
|
|
LDAP Connection Pool Size |
The Current Values list displays the minimum and maximum connection pool size to be used on a specific LDAP server and port. Formatted as: host:port:min:maxThis attribute is for LDAP and Membership authentication services only.
|
|
Default LDAP Connection Pool Size |
Specify the default minimum and maximum connection pool to be used with all LDAP authentication module configurations. Use the format min:max. This value is superseded by a value defined for a specific host and port in the LDAP Connection Pool Size property. |
|
Remote Auto Security |
When enabled, OpenSSO STS validates the identity of the calling application, and all remote authentication requests require the calling application's |
|
Keep Post Process Objects for Logout Processing |
When enabled, the remote Auth Client must send the application |
|
Keep Authentication Module Objects for Logout Processing |
When enabled, the user session continues to hold the instances of authentication modules after authentication is complete. This may be required for special logout processing. |
In the Realm Attributes section, values for the Core Authentication Service Realm attributes. The following table provides a listing and descriptions of the attributes you can configure.
Table 6-4 Core Authentication Service Realm Attributes
| Property | Desription |
|---|---|
|
User Profile |
Choose a profile status for a successfully authenticated user.
|
|
Administrator Authentication Configuration |
Specify the authentication configuration that is invoked when the user accesses /openssosts/console directly.
|
|
User Profile Dynamic Creation Default Roles |
The Current Values list displays DNs of roles to be assigned to a new user whose profile is created when Dynamic or Dynamic with Alias is selected under the User Profile attribute. There are no default values. A role can be either an OpenSSO STS or LDAP role, but it cannot be a filtered role.
|
|
Persistent Cookie Mode |
Determines whether users can return to their authenticated session after restarting the browser. When enabled, a user session will not expire until its persistent cookie expires (as specified by the value of the Persistent Cookie Maximum Time attribute), or the user explicitly logs out. By default, the Authentication Service uses only memory cookies (expires when the browser is closed). The client must explicitly request a persistent cookie by appending the iPSPCCookie=yes parameter to the login URL. |
|
Persistent Cookie Maximum Time |
Specify the number of seconds after which a persistent cookie expires. The interval begins when the user session is successfully authentication. Persistent cookie mode must be enabled. The field will accept any integer value less than the maximum 214748647. |
|
Alias Search Attribute Name |
The Current Values list displays secondary LDAP attributes to use to search for a user profile when a search using the primary LDAP attribute has failed. This attribute is typically used when the user identification returned from an authentication module is not the same as that specified in the User Naming Attribute.
For example, a Certificate server might return abc1234, but the username is abc. There is no default value for this attribute. The field takes any valid LDAP attribute. |
|
Default Authentication Locale |
Specify the default language subtype to be used by the Authentication Service. The default value is en_US. To use a difference locale, a directory containing authentication templates for that locale must already exist. |
|
Organization Authentication Configuration |
Choose the default authentication chain used the users in the realm.
|
|
Login Failure Lockout Mode |
When enabled, the user is locked out or prevented from authenticating after repeated unsuccessful login attempt within a specified interval. Lockout criteria are defined in the Login Failure Lockout Count and Login Failure Lockout Interval attributes below. |
|
Login Failure Lockout Count |
Specify the number of times a user can attempt to authenticate within the interval defined in the Login Failure Lockout Interval property. When the user exceeds this number, the user is locked out or prevented from further authentication attempts. |
|
Login Failure Lockout Interval |
Specify in minutes the interval during which failed login attempts are counted. The lockout interval begins when a user first attempts to authenticate. The lockout count begins after two consecutive failed logins. The user is locked out if the number of attempts reaches the number specified in the Login Failure Lockout Count. If the user successfully authenticates within the Login Failure Lockout Interval, the lockout count is reset. |
|
Email Address to Send Lockout Notification |
Specify an email address or multiple email addresses to which notification will be sent if a user lockout occurs. For multiple addresses, separate each address with a space. For non-English locales, use the following format: email_address|locale|charset |
|
Warn User After N Failures |
Specify the number of authentication failures that can occur before OpenSSO STS displays a warning message to the user that the user will be locked out. |
|
Login Failure Lockout Duration |
Specify in minutes how long a user must wait after a lockout before attempting to authenticate again. If you enter a value greater than 0, then memory lockout is enabled and physical lockout is disabled. When memory lockout is enabled, the user account is locked in memory for the number of minutes you specified. The account is unlocked after that time has elapsed. |
|
Lockout Duration Multiplier |
Specify a value used to multiply the Login Failure Lockout Duration value for each successive lockout. The Lockout Duration is incrementally increased based on the number of times the user has been locked out. For example, if the Login Failure Lockout Duration is set to 3 minutes, and the Lockout Duration Multiplier is to 2, then the user will be locked out of the account for 6 minutes. After the 6 minutes has elapsed, if the user again provides the wrong credentials, the lockout duration is now 12 minutes. |
|
Lockout Attribute Name |
Specify the LDAP attribute to be used for physical lockout. The default value is inetuserstatus even when the field is empty. The Lockout Attribute Value field must also contain an appropriate value. |
|
Lockout Attribute Value |
Specify the action to taken on the attribute defined in the Lockout Attribute Name. The default value is inactive even if the field is empty. The Lockout Attribute Name field must also contain an appropriate value. |
|
Default Success login URL |
The Current Values list displays values that specify where users are directed after successful authentication.
|
|
Default Failure Login URL |
The Current Values list displays where users are directed after a failed authentication attempt.
|
|
Authentication Post Processing Class |
The Current Values list displays a Java class or multiple Java classes to be used for customizing post-authentication processes for either successful or unsuccessful logins.
|
|
Generate UserID Mode |
When enabled, if the user identifier entered by a user during the self-registration process is not valid or already existing, the Membership module will generate a list of alternate user identifiers. The user identifiers are generated by the class specified in the Pluggable User Name Generator Class property. |
|
Pluggable User Name Generator Class |
Specify the name of the class to be used for generating alternate user identifiers when Generate UserID Mode is enabled. The default value is |
|
Identity Types |
Click a box to mark the type or types of identities for which OpenSSO STS will search. |
|
Pluggable User Status Event Classes. |
The Current Values list displays the Java classes or Java classes used to provide a callback mechanism for user status changes during the authentication process.
|
|
Store Invalid Attempts in Data Store |
When enabled, information regarding failed authentication attempts is stored as the value of the sunAMAuthInvalidAttemptsData attribute in the user data store. To store data in this attribute, the OpenSSO STS schema must be loaded. Information stored includes the number of invalid attempts, time of last failed attempt, lockout time, and lockout duration. Storing this information in the identity repository allows the information to be shared among multiple instances of OpenSSO STS. |
|
Module Based Authentication |
When enabled, users authenticate using module-based authentication. When disabled, all attempts at authentication using the module=module-instance-name login parameter will fail. |
|
Use Attribute Mapping to Session Attribute |
The Current Values list displays user identity attributes that are mapped as session attributes in the user's SSOToken.
Use the form User-Profile-Attribute|Session-Attribute-Name. If Session-Attribute-Name is not specified, the value of User-Profile-Attribute is used. All session attributes contain the am.protected prefix to ensure that they cannot be edited by the Client SDK. |
|
Default Authentication Level |
Specify a value that indicates how much to trust an authentication mechanism. The default value is 0. The authentication level is set separately for each method of authentication. Once a user has authenticated, this value is stored in the If the authentication level stored in an SSOToken does not meet the minimum value required, the application can prompt the user to authenticate again through a service with a higher authentication level. 0 is a low value. For example, if the user accesses the URL protocol://openssoServer:openssoPort If no authentication level is specified, the SSO token stores the value specified in the Core Authentication attribute Default Authentication Level. |
Click Save.
On the Configuration tab, click the Authentication subtab.
In the Authentication list, click Data Store
On the Data Store Realm Attributes page, provide the Authentication Level value. The following table provides information about the Authentication Level attribute.
Table 6-5 Data Store Authentication Service Realm Attributes
| Attribute | Description |
|---|---|
|
Authentication Level |
Specify a value that indicates how much to trust an authentication mechanism. The default value is 0. The authentication level is set separately for each method of authentication. Once a user has authenticated, this value is stored in the If the authentication level stored in an SSOToken does not meet the minimum value required, the application can prompt the user to authenticate again through a service with a higher authentication level. 0 is a low value. For example, if the user accesses the URL protocol://openssoServer:openssoPort If no authentication level is specified, the SSO token stores the value specified in the Core Authentication attribute Default Authentication Level. |
Click Save.
On the Configuration tab, click the Authentication subtab.
In the Authentication list, click Federation.
On the Data Store Realm Attributes page, provide the Authentication Level value. The following table provides information about the Authentication Level attribute.
Table 6-6 Data Store Authentication Service Realm Attributes
| Attribute | Description |
|---|---|
|
Authentication Level |
Specify a value that indicates how much to trust an authentication mechanism. The default value is 0. The authentication level is set separately for each method of authentication. Once a user has authenticated, this value is stored in the If the authentication level stored in an SSOToken does not meet the minimum value required, the application can prompt the user to authenticate again through a service with a higher authentication level. 0 is a low value. For example, if the user accesses the URL protocol://openssoServer:openssoPort If no authentication level is specified, the SSO token stores the value specified in the Core Authentication attribute Default Authentication Level. |
Click Save.
On the Configuration tab, click the Authentication subtab.
In the Authentication list, click JDBC
On the JDBC Realm Attributes page, provide values for the JDBC Authentication Service Realm attributes. The following table provides a listing and descriptions of the properties you can configure.
Table 6-7 JDBC Authentication Service Realm Attributes
| Attribute | Description |
|---|---|
|
Connection Type |
Choose the type of connection to be made to the SQL database.
|
|
Connection Pool JNDI Name |
If JNDI is selected in Connection Type, this field specifies the connection pool name. Because JDBC authentication uses the JNDI connection pool provided by the web container, the setup of JNDI connection pool may not be consistent among other web containers. See the OpenSSO STS Administration Guide for examples |
|
JDBC Driver |
If JDBC is selected in Connection Type, this field specifies the JDBC driver provided by Oracle Database. Example: oracle.jdbc.driver.OracleDriver. The class specified by JDBC Driver must be accessible to the web container instance on which OpenSSO has been deployed and configured. Include the JAR file that contains the JDBC driver class in the OpenSSO-deploy-base/WEB-INF/lib directory. |
|
JDBC URL |
Specify the database URL if JDBC is the selected Connection Type. Example: the URL for Oracle Database is jdbc:oracle:thin:@hostname:1521/databaseName. |
|
Connect This User to Database |
Specify the username from whom the database connection is made for the JDBC connection. |
|
Password for Connecting to Database |
Type the password for the User to Connect to Database. |
|
Password for Connecting to Database (confirm) |
Type the password again to confirm it. |
|
Password Column String |
Specify the password column name in the SQL database. |
|
Prepared Statement |
Specify the SQL statement that retrieves the password of the user that is logging in. For example: select Password from Employees where |
|
Class to Transform Password Syntax |
Specify the class name that transforms the password entered by the user for comparison to the password retrieved from the database. This class must implement the By default, the value of the attribute is |
|
Authentication Level |
Specify a value that indicates how much to trust an authentication mechanism. The default value is 0. The authentication level is set separately for each method of authentication. Once a user has authenticated, this value is stored in the If the authentication level stored in an SSOToken does not meet the minimum value required, the application can prompt the user to authenticate again through a service with a higher authentication level. 0 is a low value. For example, if the user accesses the URL protocol://openssoServer:openssoPort If no authentication level is specified, the SSO token stores the value specified in the Core Authentication attribute Default Authentication Level. |
Click Save.
On the Configuration tab, click the Authentication subtab.
In the Authentication list, click LDAP.
Provide values for the LDAP Realm Attributes. The following table provides a listing and descriptions of the properties you can configure.
Table 6-8 LDAP Authentication Service Realm Attributes
| Attributes | Description |
|---|---|
|
Primary LDAP Server |
The Current Values list displays the host name and port number of the primary LDAP server specified during OpenSSO STS installation. This is the first server contacted for authentication. If there is no port number, the default value is 389.
|
|
Secondary LDAP Server |
The Current Values list displays the host name and port number of a secondary LDAP server available to the OpenSSO STS platform. If the primary LDAP server does not respond to a request for authentication, this secondary server is contacted. When the primary server is up, OpenSSO STS will switch back to the primary server.
|
|
DN to Start User Search |
The Current Values lists displays the DN of the node where the search for a user would start. The default value is the root of the directory tree.
|
|
DN for Root User Bind |
Specify the DN of the user that will bind as administrator to the Directory Server specified in the Primary LDAP Server and Port field. The authentication service must bind as this DN in order to search for a matching user DN based on the user login ID. The default is amldapuser. You can enter any valid DN. |
|
Password for Root User Bind |
Type the password for the administrator profile specified in the DN for Root User Bind field. There is no default value. Only the administrator's valid LDAP password will be recognized. |
|
Password for Root User Bind (confirm |
Type the password again to confirm it. |
|
Attribute Used to Retrieve User Profile |
Specify the attribute used for the naming convention of user entries. By default, OpenSSO STS identifies user entries by the uid attribute. If your Directory Server uses a different attribute, such as givenname for example, type the attribute name in this field. |
|
Attributes Used to Search for a User to be Authenticated |
The Current Values list displays the attributes to be used to form the search filter for finding a user to be authenticated, and allows the user to authenticate with more than one attribute in the user's entry. For example, if this field is set to
|
|
User Search Filter |
Specify an attribute to use for finding the user under the 'DN to Start User Search' field. This attribute works with the User Naming Attribute. There is no default value. You can enter any valid user entry attribute. |
|
Search Scope |
Specify the number of levels in the Directory Server to search for finding a matching user profile. The search begins from the node specified in the 'DN to Start User Search' attribute. The default value is
|
|
SSL Access to LDAP Server |
When the OpenSSO STS directory is the same as the directory configured for LDAP, this option may be enabled. If enabled, this option allows the LDAP authentication module to return the DN instead of the User ID, and no search is necessary. Normally, an authentication module returns only the User ID, and the authentication service searches for the user in the local OpenSSO STS LDAP. If an external LDAP directory is used, this option is typically not enabled. |
|
Return User DN to Authenticate |
When the OpenSSO STS directory is the same as the directory configured for LDAP, this option may be enabled. If enabled, this option allows the LDAP authentication module to return the DN instead of the User ID, and no search is necessary. Normally, an authentication module returns only the User ID, and the authentication service searches for the user in the local OpenSSO STS LDAP. If an external LDAP directory is used, this option is typically not enabled |
|
LDAP Server Check Interval |
This attribute is used for LDAP Server failback. It defines the number of minutes in which a thread will "sleep" before verifying that the LDAP primary server is running. |
|
User Creation Attributes |
The Current Values list displays the attribute-pair used by the LDAP authentication module when the LDAP server is configured as an external LDAP server.
|
|
Minimum Password Length |
The minimum password length is a value which comes into play when the directory server instance which is being used by the authentication module instance has a password policy to allow the user to reset their password. If the directory server instance returns an LDAP code that the user should reset their password, the new password entered by the user should be equal to or greater than the value of Minimum Password Length. |
|
Authentication Level |
Specify a value that indicates how much to trust an authentication mechanism. The default value is 0. The authentication level is set separately for each method of authentication. Once a user has authenticated, this value is stored in the If the authentication level stored in an SSOToken does not meet the minimum value required, the application can prompt the user to authenticate again through a service with a higher authentication level. 0 is a low value. For example, if the user accesses the URL protocol://openssoServer:openssoPort If no authentication level is specified, the SSO token stores the value specified in the Core Authentication attribute Default Authentication Level. |
Click Save.
On the Configuration tab, click the Authentication subtab.
In the Authentication list, click OAMAuth.
Provide values for the OAMAuth Authentication Service Realm attributes. The following table provides a listing and descriptions of the properties you can configure.
Table 6-9 OAMAuth Authentication Service Realm Attributes
| Attribute | Description |
|---|---|
|
Remote User Header Name |
Specify the name of the HTTP header used for an authenticated user. Example |
|
Allowed Users Values |
The Current Values list displays administrative users who are allowed to access the OpenSSO STS console.
|
|
Authentication Level |
Specify a value that indicates how much to trust an authentication mechanism. The default value is 0. The authentication level is set separately for each method of authentication. Once a user has authenticated, this value is stored in the If the authentication level stored in an SSOToken does not meet the minimum value required, the application can prompt the user to authenticate again through a service with a higher authentication level. 0 is a low value. For example, if the user accesses the URL protocol://openssoServer:openssoPort If no authentication level is specified, the SSO token stores the value specified in the Core Authentication attribute Default Authentication Level. |
Click Save.
On the Configuration tab, click the Authentication subtab.
In the Authentication list, click WSSAuth.
Provide values for the WSSAuth Authentication Service Realm attributes. The following table provides a listing and descriptions of the properties you can configure.
Table 6-10 WSSAuth Authentication Service Realm Attributes
| Attribute | Description |
|---|---|
|
User search attribute |
Specify the user attribute that is used to search for a user. Examples: uid or cn |
|
User realm |
Specify the realm that the user belongs to. For OpenSSO STS it is always root realm indicated by a forward slash (/ ). |
|
User password attribute |
Specify the password equivalent for the user. The default could be |
|
Authentication Level |
Specify a value that indicates how much to trust an authentication mechanism. The default value is 0. The authentication level is set separately for each method of authentication. Once a user has authenticated, this value is stored in the If the authentication level stored in an SSOToken does not meet the minimum value required, the application can prompt the user to authenticate again through a service with a higher authentication level. 0 is a low value. For example, if the user accesses the URL protocol://openssoServer:openssoPort If no authentication level is specified, the SSO token stores the value specified in the Core Authentication attribute Default Authentication Level. |
Click Save.
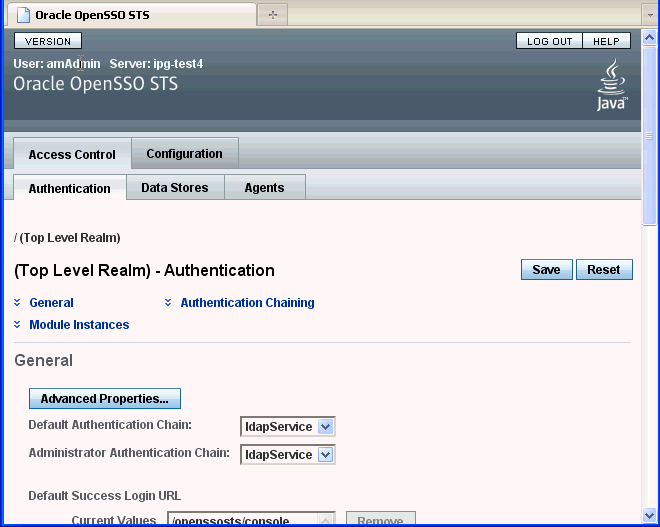
A realm is the administrative unit for OpenSSO STS. After OpenSSO STS is deployed and configured, a single top-level realm is created. The Top Level Realm contains all configuration data for the OpenSSO STS instance except for bootstrapping information configured during installation. The Top Level Realm cannot contain subrealms.
Use the OpenSSO STS Authentication tab to specify a supported authentication process, and to instantiate an authentication module used for the entire realm. You can also establish an authentication chain. When you configure multiple authentication module instances to form a chain, a user must pass authentication credentials to all of the module instances specified for the realm.
On the Access Control tab, click the Authentication subtab.
In the General section, provide values for the basic Realm properties. The following table provides a listing and descriptions of the properties you can configure.
Table 6-11 Basic Realm Properties
| Property | Description |
|---|---|
|
Administrator Authentication Chain |
Specify the authentication chain used by administrators when the process must be different from the authentication chain defined for end-users. |
|
Default Success Login URL |
The Currents Values list displays URLs that the user will be redirected to upon successful authentication to the realm.
|
|
Default Authentication Chain |
Specify the default authentication chain used by the realm's users. |
|
Administrator Authentication Chain |
Specify the authentication chain used by administrators when the process must be different from the authentication chain defined for end-users. |
Click Save.
To configure additional realm attributes, click Advanced Properties.
Provide values for the advanced Realm properties. The following table provides a listing and descriptions of the properties you can configure.
Table 6-12 Advanced Realm Properties
| Property | Description |
|---|---|
|
User Profile |
Choose a profile status for a successfully authenticated user.
|
|
Administrator Authentication Configuration |
Specify the authentication configuration that is invoked when the user accesses /openssosts/console directly.
|
|
User Profile Dynamic Creation Default Roles |
The Current Values list displays DNs of roles to be assigned to a new user whose profile is created when Dynamic or Dynamic with Alias is selected under the User Profile attribute. There are no default values. A role can be either an OpenSSO STS or LDAP role, but it cannot be a filtered role.
|
|
Persistent Cookie Mode |
Determines whether users can return to their authenticated session after restarting the browser. When enabled, a user session will not expire until its persistent cookie expires as specified by the value of the Persistent Cookie Maximum Time attribute, or the user explicitly logs out. By default, the Authentication Service uses only memory cookies so the session expires when the browser is closed. The client must explicitly request a persistent cookie by appending the iPSPCCookie=yes parameter to the login URL. |
|
Persistent Cookie Maximum Time |
Specify the number of seconds after which a persistent cookie expires. The interval begins when the user session is successfully authentication. Persistent cookie mode must be enabled. The field will accept any integer value less than the maximum 214748647. |
|
Alias Search Attribute Name |
The Current Values list displays secondary LDAP attributes to use to search for a user profile when a search using the primary LDAP attribute has failed. This attribute is typically used when the user identification returned from an authentication module is not the same as that specified in the User Naming Attribute.
For example, a Certificate server might return abc1234, but the username is abc. There is no default value for this attribute. The field takes any valid LDAP attribute. |
|
Default Authentication Locale |
Specify the default language subtype to be used by the Authentication Service. The default value is To use a difference locale, a directory containing authentication templates for that locale must already exist. |
|
Organization Authentication Configuration |
Choose the authentication configuration that is invoked when the user accesses /openssosts/UI/Login.
|
|
Login Failure Lockout Mode |
When enabled, the user is locked out or prevented from authenticating after repeated unsuccessful login attempts within a specified interval. Lockout criteria are defined in the Login Failure Lockout Count and Login Failure Lockout Interval properties below. |
|
Login Failure Lockout Count |
Specify the number of times a user can attempt to authenticate within the interval defined in the Login Failure Lockout Interval property. When the user exceeds this number, the user is locked out or prevented from further authentication attempts. |
|
Login Failure Lockout Interval |
Specify in minutes the interval during which failed login attempts are counted. The lockout interval begins when a user first attempts to authenticate. The lockout count begins after two consecutive failed logins. The user is locked out if the number of attempts reaches the number specified in the Login Failure Lockout Count. If the user successfully authenticates within the Login Failure Lockout Interval, the lockout count is reset. |
|
Email Address to Send Lockout Notification |
Specify an email address or multiple email addresses to which notification will be sent if a user lockout occurs. For multiple addresses, separate each address with a space. For non-English locales, use the following format: email_address|locale|charset |
|
Warn User After N Failures |
Specify the number of authentication failures that can occur before OpenSSO STS displays a warning message to the user that the user will be locked out. |
|
Login Failure Lockout Duration |
Specify in minutes how long a user must wait after a lockout before attempting to authenticate again. If you enter a value greater than 0, then memory lockout is enabled and physical lockout is disabled. When memory lockout is enabled, the user account is locked in memory for the number of minutes you specified. The account is unlocked after that time has elapsed. |
|
Lockout Duration Multiplier |
Specify a value used to multiply the Login Failure Lockout Duration value for each successive lockout. The Lockout Duration is increased incrementally based on the number of times the user has been locked out. For example, if the Login Failure Lockout Duration is set to 3 minutes, and the Lockout Duration Multiplier is to 2, then the user will be locked out of the account for 6 minutes. After the 6 minutes has elapsed, if the user again provides the wrong credentials, the lockout duration is now 12 minutes. |
|
Lockout Attribute Name |
Specify the LDAP attribute to be used for physical lockout. The default value is inetuserstatus even when the field is empty. The Lockout Attribute Value field must also contain an appropriate value. |
|
Lockout Attribute Value |
Specify the action to be taken on the attribute defined in the Lockout Attribute Name. The default value is inactive even if the field is empty. The Lockout Attribute Name field must also contain an appropriate value. |
|
Default Success login URL |
The Current Values list displays URLs where users are directed after successful authentication.
|
|
Default Failure Login URL |
The Current Values list displays URLs where users are directed after a failed authentication attempt.
|
|
Authentication Post Processing Class |
The Current Values list displays a Java class or multiple Java classes to be used for customizing post-authentication processes for either successful or unsuccessful logins.
|
|
Generate UserID Mode |
When enabled, if the user identifier entered by a user during the self-registration process is not valid or already exists, the Membership module generates a list of alternate user identifiers. The user identifiers are generated by the class specified in the Pluggable User Name Generator Class property. |
|
Pluggable User Name Generator Class |
Specify the name of the class to be used for generating alternate user identifiers when Generate UserID Mode is enabled. The default value is |
|
Identity Types |
Click a box to mark the type of identity or types of identities for which OpenSSO STS will search. |
|
Pluggable User Status Event Classes. |
The Current Values list displays the Java class or Java classes used to provide a callback mechanism for user status changes during the authentication process.
|
|
Store Invalid Attempts in Data Store |
When enabled, information regarding failed authentication attempts is stored as the value of the sunAMAuthInvalidAttemptsData attribute in the user data store. To store data in this attribute, the OpenSSO STS schema must be loaded. Information stored includes the number of invalid attempts, time of last failed attempt, lockout time, and lockout duration. Storing this information in the identity repository allows the information to be shared among multiple instances of OpenSSO STS. |
|
Module Based Authentication |
When enabled, users authenticate using module-based authentication. When disabled, all attempts at authentication using the |
|
Use Attribute Mapping to Session Attribute |
The Current Values list displays user identity attributes that are mapped as session properties in the user's SSOToken.
Use the form User-Profile-Attribute|Session-Attribute-Name. If Session-Attribute-Name is not specified, the value of User-Profile-Attribute is used. All session attributes contain the am.protected prefix to ensure that they cannot be edited by the Client SDK. |
|
Default Authentication Level |
Specify a value that indicates how much to trust an authentication mechanism. The default value is 0. The authentication level is set separately for each method of authentication. Once a user has authenticated, this value is stored in the If the authentication level stored in an SSOToken does not meet the minimum value required, the application can prompt the user to authenticate again through a service with a higher authentication level. 0 is a low value. For example, if the user accesses the URL protocol://openssoServer:openssoPort If no authentication level is specified, the SSO token stores the value specified in the Core Authentication attribute Default Authentication Level. |
Click Save.
OpenSSO STS is installed with a set of default authentication module instance types. An authentication module instance is a plug-in that collects user information such as a user ID and password, checks the information against entries in a database, and allows or denies access to the user. You can create new authentication module instances. You can also create multiple authentication instances of the same type, which you can configure separately.
The following figure illustrates the Access > Authentication subtab the OpenSSO STS console where you create and configure new authentication module instances.
Figure 6-2 Access Control > Authentication Subtab for Configuring Individual Authentication Modules
The following authentication module types (Module Instances) are supported in OpenSSO STS.
An Active Directory authentication module works similarly to the LDAP authentication module type, but uses the Microsoft Active Directory instead of an LDAP directory. Using this module type makes it possible to have both LDAP and Active Directory coexist under the same realm. See Section 6.3.1, "To Add a New Active Directory Module Instance" and Section 6.3.2, "To Configure an Active Directory Authentication Module Instance."
A Certificate authentication module enables a user to log in through a personal digital certificate (PDC). The module instance can require the use of the Online Certificate Status Protocol (OCSP) to determine the state of a certificate. Use of the OCSP is optional. The user is granted or denied access to a resource based on whether or not the certificate is valid. See Section 6.3.3, "To Add a New Certificate Authentication Module Instance" and Section 6.3.4, "To Configure a Certificate Authentication Module Instance."
A Data Store authentication modules enables OpenSSO STS to authenticate users against the Identity Repository. Using the Data Store module removes the requirement to write an authentication plug- in module, load, and then configure the authentication module if you need to authenticate against the same data store repository. Additionally, you do not need to write a custom authentication module where flat-file authentication is needed for the corresponding repository in that realm. See Section 6.3.5, "To Add a New Data Store Authentication Module Instance" and Section 6.3.6, "To Configure a Data Store Authentication Module Instance."
The Federation authentication module authenticates and validates Federation protocols. For example, when an Identity Provider sends a SAML2 artifact profile or post profile to a Service Provider, the Federation authentication module retrieves the SAML2 assertion and validates the assertion against the Identity Provider server. See Section 6.3.7, "To Add and Configure a New Federation Authentication Module Instance."
A Java Database Connectivity (JDBC) authentication module enables OpenSSO STS to authenticate users through any Structured Query Language (SQL) databases that provide JDBC-enabled drivers. The connection to the SQL database can be either directly through a JDBC driver or through a JNDI connection pool. The JDBC attributes are realm attributes. See Section 6.3.8, "To Add a New JDBC Authentication Module Instance" and Section 6.3.9, "To Configure a JDBC Authentication Module Instance."
An LDAP authentication module enables OpenSSO STS to authenticate users using LDAP bind, a Directory Server operation which associates a user ID password with a particular LDAP entry. OpenSSO validates the UserName with a cleartext password contained in a web service request to a web service provider. You can define multiple LDAP authentication configurations for a realm. See Section 6.3.10, "To Add an New LDAP Authentication Module Instance" and Section 6.3.11, "To Configure an LDAP Authentication Module Instance."x
The Oracle authentication module enables OpenSSO STS to authenticate and single sign-on an administrator, who previously authenticated to Oracle Access Manager, to OpenSSO STS. The administrator does not have to provide credentials OpenSSO STS.
See Section 6.3.12, "To Add a New Oracle Authentication Module Instance" and Section 6.3.13, "To Configure an Oracle Authentication Module Instance".
The Web Service Security authentication module enables OpenSSO STS to validate the UserName with a digest password received as an authentication token and contained in a service request from the web service client to a web service provider.
See Section 6.3.16, "To Delete an Authentication Module Instance" and Section 6.3.15, "To Configure a WSSAuth Authentication Module Instance."
In the Access Control tab, click the Authentication subtab.
In the Module Instances section, click New.
In the Name field, type a name for this Active Directory module instance.
The name cannot contain spaces.
For Type, choose Active Directory.
Click OK.
Configure the Active Directory Authentication Module Instance. See Section 6.3.2, "To Configure an Active Directory Authentication Module Instance."
In the Access Control tab, click the Authentication subtab.
In the Module Instances section, click name of the Active Directory Authentication module instance you want to configure.
Provide values for the Active Directory Authentication Module Instance Realm attributes. The following table provides a listing and descriptions of the properties you can configure.
Table 6-13 Active Directory Authentication Module Instance Realm Attributes
| Attribute | Description |
|---|---|
|
Primary Active Directory Server |
The Current Values list displays the host name and port number of the primary Active Directory server specified during OpenSSO STS installation. This is the first server contacted for Active Directory authentication. The format is hostname:port. The default port number is 389.
|
|
Secondary Active Directory Server |
The Current Values list displays the host name and port number of a secondary Active Directory server available to the OpenSSO STS platform. If the primary Active Directory server does not respond to a request for authentication, then this server is contacted. If the primary server is up, OpenSSO STS will switch back to the primary server.
|
|
DN to Start User Search |
The Current Values list displays the DN of the node where the search for a user starts.
|
|
DN for Root User Bind |
Specify the DN of the user that will be used to bind to the Directory Server specified in the Primary LDAP Server and Port fields as administrator. The authentication service must bind as this DN in order to search for a matching user DN based on the user login ID. The default is amldapuser. Any valid DN will be recognized. Make sure that password is correct before you logout. If it is incorrect, you will be locked out. If this should occur, you can login with the super user DN. By default, this the amAdmin account with which you would normally log in, although you will use the full DN. For example:
|
|
Password for Root User Bind |
Type the password for the administrator profile specified in the DN for Root User Bind field. There is no default value. Only the administrator's valid Active Directory password is recognized. |
|
Password for Root User Bind (confirm) |
Type the Root User Bind password again to confirm it. |
|
Attribute Used to Retrieve User Profile |
Specify the attribute used for the user entry naming convention. By default, OpenSSO STS assumes that user entries are identified by the uid attribute. If your Directory Server uses a different attribute such as givenname, specify the attribute name in this field. |
|
Attributes Used to Search for a User to be Authenticated |
The Current Values list displays the attributes to be used to form the search filter for a user that is to be authenticated, and that allows the user to authenticate with more than one attribute in the user's entry. For example, if this field is set to uid, employeenumber, and mail, then the user could authenticate with any of these names.
|
|
User Search Filter |
Displays the attributes to be used to find the user based on the value in the DN to Start User Search field. The filter works with the User Naming Attribute. There is no default value. Any valid user entry attribute will be recognized. |
|
Search Scope |
Choose the number of levels in the Directory Server that will be searched for a matching user profile. The search begins from the node specified in DN to Start User Search field. The default value is
|
|
SSL Access to Active Directory Server |
When enabled, OpenSSO STS uses the SSL protocol to access the Directory Server specified in the Primary and Secondary Server and Port fields. By default, the box is not checked and the SSL protocol is not used to access the Directory Server. If the Active Directory server is running with SSL enabled (LDAPS), you must make sure that OpenSSO STS is configured with proper SSL trusted certificates. Otherwise OpenSSO STS cannot connect to Directory Server using the LDAPS protocol. |
|
Return User DN to Authenticate |
When enabled, the Active Directory authentication module instance returns the DN instead of the User ID, and no search is necessary. Normally, an authentication module instance returns only the User ID, and the authentication service searches for the user in the local OpenSSO STS instance. If the OpenSSO STS directory is the same as the directory configured for Active Directory, this option may be enabled. If an external Active Directory is used, this option is typically not enabled. |
|
Active Directory Server Check Interval |
Specify the number of minutes per interval in which a thread will "sleep" before verifying that the primary Active Directory server is running. This attribute is used for Active Directory Server failback. |
|
User Creation Attributes |
The Current Values list displays attributes used by the Active Directory authentication module instance when the Active Directory server is configured as an external Active Directory server. It contains a mapping of attributes between a local and an external Directory Server. The attribute uses the following form: attr1|externalattr1 attr2|externalattr2
|
|
Minimum Password Length |
The minimum password length is a value which comes into play when the directory server instance which is being used by the authentication module instance has a password policy to allow the user to reset their password. If the directory server instance returns an LDAP code that the user should reset their password, the new password entered by the user should be equal to or greater than the value of Minimum Password Length. |
|
Authentication Level |
Specify a value that indicates how much to trust an authentication mechanism. The default value is 0. The authentication level is set separately for each method of authentication. Once a user has authenticated, this value is stored in the If the authentication level stored in an SSOToken does not meet the minimum value required, the application can prompt the user to authenticate again through a service with a higher authentication level. 0 is a low value. For example, if the user accesses the URL protocol://openssoServer:openssoPort If no authentication level is specified, the SSO token stores the value specified in the Core Authentication attribute Default Authentication Level. |
In the Access Control tab, click the Authentication subtab.
In the Module Instances section, click New.
In the Name field, type a name for this Certificate authentication module instance.
For Type, choose Certificate.
Click OK.
Configure the Certificate Authentication Module Instance. See Section 6.3.4, "To Configure a Certificate Authentication Module Instance."
In the Access Control tab, click the Authentication subtab.
In the Module Instances section, click name of the Certificate authentication module instance you want to configure.
Provide values for the Certificate Authentication Module Instance Realm attributes. The following table provides a listing and descriptions of the properties you can configure.
Table 6-14 Certificate Authentication Module Instance Realm Attributes
| Attribute | Description |
|---|---|
|
Match Certificate in LDAP |
When enabled, the Certificate Authentication Module determines whether a user certificate presented at login is stored in the LDAP Server specified in the "LDAP Server Where Certificates are Stored" field below. If no match is found, then the user is denied access. If a match is found and no other validation is required, the user is granted access. By default, this option is disabled and the Certificate Authentication Module does not check for the user certificate. Note – A certificate stored in the Directory Server is not necessarily valid. It may be on the certificate revocation list. See Match Certificate to CRL. However, the web container may check the validity of the user certificate presented at login. |
|
Subject DN Attribute Used to Search LDAP for Certificates |
Specify the attribute of the certificate's SubjectDN value that will be used to search LDAP for certificates. This attribute must uniquely identify a user entry. The actual value will be used for the search. The default is |
|
Match Certificate to CRL |
When enabled, the Certificate Authentication Module compares the user certificate against the Certificate Revocation List (CRL) in the LDAP Server. The CRL is located based on one of the attribute names in the issuer's Certificates should be revoked when the owner of the certificate has changed status and no longer has the right to use the certificate or when the private key of a certificate owner has been compromised. |
|
Issuer DN Attribute Used to Search LDAP for CRLs |
Specify the attribute of the |
|
HTTP Parameters for CRL Update |
Specify the HTTP parameters for obtaining a CRL from a servlet for a CRL update. Contact the administrator of your CA for these parameters. |
|
Match CA Certificate to CRL |
When enabled, the Certificate Authentication Module compares the Certificate Authority-issued certificate against the Certificate Revocation List (CRL) in the LDAP Server. The CRL is located based on one of the attribute names in the issuer's SubjectDN. If the certificate is on the CRL, then the user is denied access. If the certificate is not on the CRL, then the user is allowed to proceed. By default this option is disabled. Certificates should be revoked when the owner of the certificate has changed status and no longer has the right to use the certificate or when the private key of a certificate owner has been compromised. |
|
OCSP Validation |
When enabled, Online Certificate Status Protocol (OCSP) validation is performed by contacting the appropriate OCSP responder. The OCSP responder is determined during runtime based on the following settings:
These settings can be configured on the Servers and Sites tab. Before enabling OCSP Validation, make sure that the time of day settings for the OpenSSO STS host and the OCSP responder host are synchronized as closely as possible. Also, the time of day setting for the OpenSSO STS host must be ahead of the time of day setting for the OCSP responder. For example, if the OCSP responder host is set at 12:00:00 PM, then the OpenSSO STS host could be set at 12:00:30 PM. |
|
LDAP Server Where Certificates are Stored |
The Current Values list displays the name and port number of the LDAP server where the certificates are stored. The default value is the host name and port specified when OpenSSO STS was installed.
|
|
LDAP Search Start DN |
The Current Values list displays the DN of the node where the search for the user's certificate should start.
Use the format servername|searchDN. There is no default value. You can enter any valid DN. Multiple entries must be prefixed by the local server name. Example: servername1|searchDN servername2|searchDN servername3|searchDN |
|
LDAP Server Principal User |
Specify the DN of the principal user for the LDAP server where the certificates are stored. There is no default value. You can use any valid DN. The principal user must be authorized to read, and search certificate information stored in the Directory Server. |
|
LDAP Server Principal Password |
Specify the LDAP password associated with the user specified in the LDAP Server Principal User field above. There is no default value. You can use any valid LDAP password for the specified principal user. This value is stored as readable text in the directory. |
|
LDAP Server Principal Password (confirm |
Type the password again to confirm it. |
|
Use SSL for LDAP Access |
Specifies whether to use SSL to access the LDAP server. The default is that the Certificate Authentication service does not use SSL for LDAP access. |
|
Certificate Field Used to Access User Profile |
From the following, choose the field in the certificate's Subject DN to be used to search for a matching user profile: email addressnoneothersubject CNsubject DNsubject UID
For example, if you choose email address, the Certificate Authentication service searches for the user profile that matches the attribute |
|
Other Certificate Field Used to Access User Profile |
This attribute is recognized only if 'other' is selected in the 'Certificate Field Used to Access User Profile' attribute above. Specify the attribute that will be selected from the received certificate's subjectDN value. The Certificate Authentication service will then search the user profile that matches the value of that attribute. |
|
SubjectAltNameExt Value Type to Access User Profile |
RFC822Name - Electronic email address UPN - User Principal Name none When 'none' is selected, the 'Certificate Field Used to Access User Profile' or 'Other Certificate Field Used to Access User Profile' attribute is used to access the User Profile. |
|
Trusted Remote Hosts |
The Current Values list displays hosts that can be trusted to send certificates to OpenSSO STS. OpenSSO STS must verify whether the certificate came from one of these hosts. This attribute is used for the Portal Server gateway, for a load balancer with SSL termination and for Distributed Authentication. By default, this attribute is set to 'none,' which disables certificate issuer host verification.
|
|
SSL Port Number |
Specify the port number for the secure socket layer (SSL). Currently, this attribute is only used by the Gateway servlet. Before you add or change an SSL Port Number, see the "Policy-Based Resource Management" section in the OpenSSO STS Administration Guide. |
|
HTTP Header Name for Client Certificate |
This attribute is used only when the Trusted Remote Hosts attribute is set to all' or has a specific host name defined. Specify the HTTP header name for the client certificate that is inserted by the load balancer or Secure Remote Access component. |
|
Authentication Level |
Specify a value that indicates how much to trust an authentication mechanism. The default value is 0. The authentication level is set separately for each method of authentication. Once a user has authenticated, this value is stored in the If the authentication level stored in an SSOToken does not meet the minimum value required, the application can prompt the user to authenticate again through a service with a higher authentication level. 0 is a low value. For example, if the user accesses the URL protocol://openssoServer:openssoPort If no authentication level is specified, the SSO token stores the value specified in the Core Authentication attribute Default Authentication Level. |
In the Access Control tab, click the Authentication subtab.
In the Module Instances section, click New.
In the Name field, type a name for this Data Store authentication module instance.
For Type, choose Data Store.
Click OK.
Configure the Data Store authentication module instance. Section 6.3.6, "To Configure a Data Store Authentication Module Instance."
In the Access Control tab, click the Authentication subtab.
In the Module Instances section, click name of the Data Store authentication module instance you want to configure.
Provide values for the Data Store Authentication Module Instance Realm attributes. The following table provides a listing and descriptions of the properties you can configure.
Table 6-15 Data Store Authentication Module Instance Realm Attributes
| Attribute | Description |
|---|---|
|
Authentication Level |
Specify a value that indicates how much to trust an authentication mechanism. The default value is 0. The authentication level is set separately for each method of authentication. Once a user has authenticated, this value is stored in the If the authentication level stored in an SSOToken does not meet the minimum value required, the application can prompt the user to authenticate again through a service with a higher authentication level. 0 is a low value. For example, if the user accesses the URL protocol://openssoServer:openssoPort If no authentication level is specified, the SSO token stores the value specified in the Core Authentication attribute Default Authentication Level. |
In the Access Control tab, click the Authentication subtab.
In the Module Instances section, click New.
In the Name field, type a name for this Federation Authentication module instance.
For Type, choose Federation
Click OK.
Configure the Federation authentication module instance.
On the Access > Authentication subtab, in the Module Instances section, select the Federation instance you want to configure.
On the Federation Realm Attributes page, type a value in the Authentication Level field.
Specify a value that indicates how much to trust the Federation Authentication module instance.
Once a user has authenticated, this value is stored in the SSO token for the session. When the SSO token is presented to an application the user wants to access, the application uses the stored value to determine whether the level is sufficient to grant the user access. If the authentication level stored in an SSO token does not meet the minimum value required, the application can prompt the user to authenticate again through a service with a higher authentication level. The default value is 0.
0 is a low value. For example, if the user accesses the URL protocol://openssoServer:openssoPort/opensso/UI/Loin?authlevel=0, a selection menu is displayed containing all authentication module instances with an authentication level of 0 or greater, or all authentication module instances. Similarly if the user accesses the URL protocol://openssoServer:port/opensso/UI/Loin?authlevel=50, a selection menu is displayed containing authentication module instances with an authentication level of 50 or greater. Or if only one authentication module instance meets that constraint, a login screen for that authentication module instance is displayed.
If no authentication level is specified, the SSO token stores the value specified in the Core Authentication attribute Default Authentication Level.
Click Save.
Click Back to Authentication.
In the Access Control tab, click the Authentication subtab.
In the Module Instances section, click New.
In the Name field, type a name for this JDBC authentication module instance.
For Type, choose JDBC.
Click OK.
Configure the JDBC authentication module instance. Section 6.3.9, "To Configure a JDBC Authentication Module Instance."
In the Access Control tab, click the Authentication subtab.
In the Module Instances section, click name of the JDBC authentication module instance you want to configure.
Provide values for the JDBC Authentication Module Instance Realm attributes. The following table provides a listing and descriptions of the attributes you can configure.
Table 6-16 JDBC Authentication Module Instance Realm Attributes
| Attribute | Description |
|---|---|
|
Connection Type |
Choose the type of connection to be made to the SQL database.
|
|
Connection Pool JNDI Name |
If JNDI is selected in Connection Type, this field specifies the connection pool name. Because JDBC authentication uses the JNDI connection pool provided by the web container, the setup of JNDI connection pool may not be consistent among other web containers. See the OpenSSO STS Administration Guide for examples |
|
JDBC Driver |
If JDBC is selected in Connection Type, this field specifies the Oracle driver provided by the Oracle Database. Example: oracle.jdbc.driver.OracleDriver. The class specified by Oracle Driver must be accessible to the web container instance on which OpenSSO has been deployed and configured. Include the JAR file that contains the Oracle driver class in the OpenSSO-deploy-base/WEB-INF/lib directory. |
|
JDBC URL |
Specify the database URL if JDBC is the selected Connection Type. Example: the URL for Oracle Database is jdbc:oracle:thin:@hostname:1521/databaseName. |
|
Connect This User to Database |
Specify the username from whom the database connection is made for the JDBC connection. |
|
Password for Connecting to Database |
Type the password for the User to Connect to Database. |
|
Password for Connecting to Database (confirm) |
Type the password again to confirm it. |
|
Password Column String |
Specify the password column name in the SQL database. |
|
Prepared Statement |
Specify the SQL statement that retrieves the password of the user that is logging in. For example: select Password from Employees where |
|
Class to Transform Password Syntax |
Specify the class that transforms the password entered by the user for comparison to the password retrieved from the database. This class must implement the By default, the value of the attribute is com.sun.identity.authentication.modules.jdbc.ClearTextTranform which expects the password to be in clear text. |
|
Authentication Level |
Specify a value that indicates how much to trust an authentication mechanism. The default value is 0. The authentication level is set separately for each method of authentication. Once a user has authenticated, this value is stored in the If the authentication level stored in an SSOToken does not meet the minimum value required, the application can prompt the user to authenticate again through a service with a higher authentication level. 0 is a low value. For example, if the user accesses the URL protocol://openssoServer:openssoPort If no authentication level is specified, the SSO token stores the value specified in the Core Authentication attribute Default Authentication Level. |
In the Access Control tab, click the Authentication subtab.
In the Module Instances section, click New.
In the Name field, type a name for this LDAP authentication module instance.
For Type, choose LDAP.
Click OK.
Configure the LDAP authentication module instance. Section 6.3.11, "To Configure an LDAP Authentication Module Instance."
In the Access Control tab, click the Authentication subtab.
In the Module Instances section, click name of the LDAP authentication module instance you want to configure.
Provide values for the LDAP Authentication Module Instance Realm attributes. The following table provides a listing and descriptions of the properties you can configure.
Table 6-17 LDAP Authentication Module Instance Realm Attributes
| Attributes | Description |
|---|---|
|
Primary LDAP Server |
The Current Values list displays the host name and port number of the primary LDAP server specified during OpenSSO STS installation. This is the first server contacted for authentication. If there is no port number, the default value is 389.
|
|
Secondary LDAP Server |
The Current Values list displays the host name and port number of a secondary LDAP server available to the OpenSSO STS platform. If the primary LDAP server does not respond to a request for authentication, this secondary server is contacted. When the primary server is up, OpenSSO STS will switch back to the primary server.
|
|
DN to Start User Search |
The Current Values lists displays the DN of the node where the search for a user would start. The default value is the root of the directory tree.
|
|
DN for Root User Bind |
Specify the DN of the user that will bind as administrator to the Directory Server specified in the Primary LDAP Server and Port field. The authentication service must bind as this DN in order to search for a matching user DN based on the user login ID. The default is amldapuser. You can enter any valid DN. |
|
Password for Root User Bind |
Type the password for the administrator profile specified in the DN for Root User Bind field. There is no default value. Only the administrator's valid LDAP password will be recognized. |
|
Password for Root User Bind (confirm |
Type the password again to confirm it. |
|
Attribute Used to Retrieve User Profile |
Specify the attribute used for the naming convention of user entries. By default, OpenSSO STS identifies user entries by the uid attribute. If your Directory Server uses a different attribute, such as givenname for example, type the attribute name in this field. |
|
Attributes Used to Search for a User to be Authenticated |
The Current Values list displays the attributes to be used to form the search filter for finding a user to be authenticated, and allows the user to authenticate with more than one attribute in the user's entry. Example: if this field is set to uid, employeenumber, and mail, the user could authenticate with any of these attributes. These attributes must be set separately.
|
|
User Search Filter |
Specify an attribute to use for finding the user under the 'DN to Start User Search' field. This attribute works with the User Naming Attribute. There is no default value. You can enter any valid user entry attribute. |
|
Search Scope |
Specify the number of levels in the Directory Server to search for finding a matching user profile. The search begins from the node specified in the 'DN to Start User Search' attribute. The default value is
|
|
SSL Access to LDAP Server |
When the OpenSSO STS directory is the same as the directory configured for LDAP, this option may be enabled. If enabled, this option allows the LDAP authentication module to return the DN instead of the User ID, and no search is necessary. Normally, an authentication module returns only the User ID, and the authentication service searches for the user in the local OpenSSO STS LDAP. If an external LDAP directory is used, this option is typically not enabled. |
|
Return User DN to Authenticate |
When the OpenSSO STS directory is the same as the directory configured for LDAP, this option may be enabled. If enabled, this option allows the LDAP authentication module to return the DN instead of the User ID, and no search is necessary. Normally, an authentication module returns only the User ID, and the authentication service searches for the user in the local OpenSSO STS LDAP. If an external LDAP directory is used, this option is typically not enabled |
|
LDAP Server Check Interval |
This attribute is used for LDAP Server failback. It defines the number of minutes in which a thread will "sleep" before verifying that the LDAP primary server is running. |
|
User Creation Attributes |
The Current Values list displays the attribute-pair used by the LDAP authentication module when the LDAP server is configured as an external LDAP server.
|
|
Minimum Password Length |
The minimum password length is a value which comes into play when the directory server instance which is being used by the authentication module instance has a password policy to allow the user to reset their password. If the directory server instance returns an LDAP code that the user should reset their password, the new password entered by the user should be equal to or greater than the value of Minimum Password Length. |
|
Authentication Level |
Specify a value that indicates how much to trust an authentication mechanism. The default value is 0. The authentication level is set separately for each method of authentication. Once a user has authenticated, this value is stored in the If the authentication level stored in an SSOToken does not meet the minimum value required, the application can prompt the user to authenticate again through a service with a higher authentication level. 0 is a low value. For example, if the user accesses the URL protocol://openssoServer:openssoPort If no authentication level is specified, the SSO token stores the value specified in the Core Authentication attribute Default Authentication Level. |
In the Access Control tab, click the Authentication subtab.
In the Module Instances section, click New.
In the Name field, type a name for this Oracle authentication module instance.
For Type, choose OAMAuth.
Click OK.
Configure the OAMAuth authentication module instance. Section 6.3.13, "To Configure an Oracle Authentication Module Instance."
In the Access Control tab, click the Authentication subtab.
In the Module Instances section, click name of the OAMAuth authentication module instance you want to configure.
Provide values for the Oracle Authentication Module Instance Realm attributes. The following table provides a listing and descriptions of the attributes you can configure.
Table 6-18 Oracle Authentication Module Instance Realm Attributes
| Attribute | Description |
|---|---|
|
Remote User Header Name |
Specify the name of the HTTP header used for an authenticated user. Example |
|
Allowed Users Values |
The Current Values list displays administrative users who are allowed to access the OpenSSO STS console.
|
|
Authentication level |
Specify a value that indicates how much to trust an authentication mechanism. The default value is 0. The authentication level is set separately for each method of authentication. Once a user has authenticated, this value is stored in the If the authentication level stored in an SSOToken does not meet the minimum value required, the application can prompt the user to authenticate again through a service with a higher authentication level. 0 is a low value. For example, if the user accesses the URL protocol://openssoServer:openssoPort If no authentication level is specified, the SSO token stores the value specified in the Core Authentication attribute Default Authentication Level. |
In the Access Control tab, click the Authentication subtab.
In the Module Instances section, click New.
In the Name field, type a name for this WSSAuth authentication module instance.
For Type, choose WSSAuth.
Click OK.
Configure the WSSAuth authentication module instance.
In the Access Control tab, click the Authentication subtab.
In the Module Instances section, click name of the WSSAuth authentication module instance you want to configure.
Provide values for the WSSAuth Authentication Module Instance Realm attributes. The following table provides a listing and descriptions of the attributes you can configure.
Table 6-19 WSSAuth Authentication Module Instance Realm Attributes
| Attribute | Description |
|---|---|
|
User search attribute |
Specify a user attribute that to be used to search for a user. Examples: |
|
User realm |
Specify the realm the user belongs to. For OpenSSO STS it is always root realm, indicated by a forward slash ( /) . |
|
User password attribute |
Specify a password attribute (password equivalent) for the user. The default could be |
|
Authentication Level |
Specify a value that indicates how much to trust an authentication mechanism. The default value is 0. The authentication level is set separately for each method of authentication. Once a user has authenticated, this value is stored in the If the authentication level stored in an SSOToken does not meet the minimum value required, the application can prompt the user to authenticate again through a service with a higher authentication level. 0 is a low value. For example, if the user accesses the URL protocol://openssoServer:openssoPort If no authentication level is specified, the SSO token stores the value specified in the Core Authentication attribute Default Authentication Level. |
In the Access Control tab, click the Authentication subtab.
In the Module Instances section, select the name of the module instance to be deleted.
Click Delete.
You can configure multiple authentication modules instance so that a user must pass authentication credentials to all of them. This is known as authentication chaining.
When you configure an authentication chain, the user interacts with each of the authentication module instances in the chain, from the top down, in order to pass the authentication process. A criteria flag is assigned to each instance in the chain. The criteria flag defines how authentication proceeds through the ordered group of modules if, for example, authentication to one of the modules fails. Once authentication to all modules in the chain has been successfully achieved, the Authentication Service validates that all user identifiers in the chain are mapped to the same user. After validation occurs, a session token is issued for the user and the policy evaluation process begins. Authentication chains can be assigned to a realm, a user, a role, or a service.
In the Access Control tab, click the Authentication subtab.
To add a new chain, in the Authentication Chains section, click New.
In the Name field, type a name for the new authentication chain.
Click OK.
To add an authentication module to the authentication chain, in the ChainName Properties page, in the Items section, click Add.
The authentication module instance name is displayed in the Items list.
To configure chaining for an authentication module in the Items list, first mark the box that corresponds to the authentication module you want to configure, then provide values for the Required Authentication Module Instance Chaining properties.
The following table provides a listing and descriptions of the properties you can configure.
Table 6-20 Required Authentication Module Instance Chaining Properties
| Property | Description |
|---|---|
|
Instance |
In the Instance column, a drop down list displays the authentication modules instantiated in the realm. Choose the authentication module instance to be configured. |
|
Criteria |
In the Criteria column, a dropdown list displays the supported options. Choose the criteria to be used for this authentication module instance.
|
|
Options |
In the Options column, you can define additional options for the authentication module instance. Type a key=value pair. Example: if the authentication module supports debugging, type |
To reorder the authentications modules in the list, click Reorder.
The authentication module instances will be invoked in the order listed the authentication configuration. For example, if authentication module instance A which is moved below authentication module instance B, then B will be invoked before A.
a. In the Reorder Authentication Chains page, click a module instance name and then click Move Up, Move Down, Move to Top, or Move to Bottom until the instance name is in the proper place in the list.
b. Click OK.
(Optional) Provide values for the optional Authentication Chaining Post-Processing properties. The following table provides a listing and descriptions of the properties you can configure.
Table 6-21 Optional Authentication Chaining Post-Processing Properties
| Property | Description |
|---|---|
|
Successful Login URL |
The Current Values list displays URLs that the user will be redirected to upon successful authentication.
|
|
Failed Login URL |
The Current Values list displays URLs that the user will be redirected to upon failed authentication.
|
|
Post Authentication Processing Class |
The Current Values list displays the name of a Java class to be used for customizing any post-authentication processes regardless of whether authentication succeeds or fails.
|
In the ChainName Properties page, click Save.
Caution:
Do not delete ldapService. Deleting ldapService may cause problems with logging into OpenSSO STS administration console.In the Access Control tab, click the Authentication subtab.
In the Authentication Chains section, select the name of the authentication chain to be deleted.
Click Delete.