8 Setting Up OTP Anywhere
OTP Anywhere creates universal delivery options for auto-generated one-time-passwords used for secondary, risk-based user challenges to add sophisticated security to basic authentcation flows.
OTP is a form of out-of-band authentication that is used as secondary credentials. It is generated at pre-configured checkpoints based on policies configured.
This chapter focuses on the setting up Oracle Adaptive Access Manager to use a configured delivery method to authenticate users.
8.1 Introduction and Concepts
This section introduces you to the concept of One Time Password (OTP) and how it is used in Oracle Adaptive Access Manager.
8.1.1 Out-of-Band OTP Delivery
Oracle Adaptive Access Manager 11g contains one time password authentication capabilities that support the delivery of a random server-generated OTP through any of the following out-of-band channels:
-
email
-
SMS
-
voice messaging
-
instant messaging
The user is OTP-challenged to enter the single-use PIN or password code he receives into a Web interface. This form of authentication is used as a secondary credential in addition to the static username and password.
8.1.2 One Time Password (OTP)
One Time Password (OTP) is a random single use authentication credential. The OTP may be either numeric or alphanumeric and any length and the randomization algorithm is pluggable.
The following are major benefits of using out-of-band OTP:
-
The one time password is delivered to the valid user through one of the configured channels. These can include SMS, IM, email or voice.
-
The user does not require any proprietary hardware or client software of any kind.
8.1.3 Registration
Registration is the enrollment process, the opening of a new account, or other event where information is obtained from the user.
During registration, the user is asked to select supported OTP delivery channels.
When OTP-challenged, the single-use PIN or password is delivered to the user through the delivery channel he selected.
8.1.4 OTP Challenge
An OTP challenge is when the user is asked to provide the OTP as a form of authentication for high risk situations based upon configured policies.
Oracle Adaptive Access Manager, depending on its configuration for OTP, sends a time-constrained single-use PIN or password to the user when further authentication is required.
The user is OTP-challenged to enter the single-use PIN or password code he receives in to a Web interface.
The user must enter the correct OTP in to the Web interface to proceed with the operation.
8.1.5 KBA vs. OTP
Oracle Adaptive Access Manager deployments may choose to use both KBA and OTP Anywhere or each separately or no challenge mechanisms at all. If both KBA and OTP Anywhere are being used in a deployment, the security team may choose to use KBA for challenges in lower risk situations and OTP Anywhere for higher risk situations.
For example, a user logging in from a new IP in a city he often logs in from is relatively low risk on its own so a KBA challenge would be a good option to gain additional verification that this is the valid user. If, however, a user is attempting a funds transfer of more than $1000 using a device and location he has never accessed from previously and the user has never performed a transfer, a stronger measure such as OTP Anywhere would be warranted.
If a customer has both KBA and OTP Anywhere enabled, the priority is configurable through properties.
For information on KBA and OTP Anywhere priority, see Section 8.5, "Enabling OTP Challenge."
8.1.6 OTP Failure Counters
An OTP failure occurs when the user supplies an incorrect answer during an OTP-challenge and the failure counter is incremented. When a correct PIN or password is provided by the user, the failure counter is reset to 0 and the user is allowed to proceed with the operation.
When the failure counter reaches the threshold value, the user is "OTP Locked."
The maximum number for OTP challenges is configurable.
OTP failures are counted across sessions.
If the user is OTP-locked, he can call the Customer Service Representative to become unlocked.
8.1.7 OTP Resets
A customer service representative (CSR) can reset a customer's OTP profile or unlock a customer when necessary.
8.1.7.1 Reset OTP Profile
The CSR resets a user's OTP profile. The system deletes the contact information that is used to send the OTP. The customer must register OTP information at the log in.
8.2 User Flow
Example use cases that follow illustrates the user experience when the OTP framework is configured.
Use Case 1: New Registration Example
This example illustrates the user registration experience.
-
The user logs in to a protected application for the first time after Oracle Adaptive Access Manager is deployed.
-
The user selects his virtual device, and personalization image and phase.
-
The user sets up KBA challenge questions.
-
The user selects one or more of the following OTP Anywhere delivery channels:
-
cell phone
-
email address
-
home phone number
-
Instant Message ID
The delivery channel used is configured by an administrator for all users in a deployment.
-
This section illustrates an example of the user login experience when a high risk rule is triggered, and OTP Anywhere is used in the deployment.
-
A registered user logs in to a protected application.
-
If the situation is high enough risk, the user is asked to enter an OTP sent to them in another channel/band.
-
The user will enter the OTP in the web interface to authenticate himself.
8.3 Setting Up OTP Anywhere
To set up OTP Anywhere, you must perform the following tasks:
For information on customizing Oracle Adaptive Access Manager, see the Oracle Fusion Middleware Developer's Guide for Oracle Adaptive Access Manager.
8.3.1 Enabling OTP Profile Registration and Preference Setting
To enable OTP profile registration and preference setting:
-
In the Navigation tree, double-click Properties under the Environment node. The Properties Search page is displayed.
-
Search for the following properties and set them to true.
If the properties do not exist, create them.
-
bharosa.uio.default.register.userinfo.enabled
Setting the property to true enables the profile registration pages if the OTP channel is enabled and requires registration.
-
bharosa.uio.default.userpreferences.userinfo.enabled
Setting the property to true enables the user to set preferences if the OTP channel is enabled and allows preference setting.
-
OTP Challenge types must be enabled before any pages are displayed.
8.3.2 Setting Up the Contact Input Elements for OTP Registration Page
If user information registration or user preferences is set to true, configure the input information for the OTP registration or preferences page. The bharosa.uio.default.userinfo.inputs.enum property values are shown in Table 8-1.
Table 8-1 OTP Properties for Contact Input
| Property | Description |
|---|---|
|
inputname |
Name used for the input field in the HTML form |
|
inputtype |
Set for text or password input |
|
maxlength |
Maximum length of user input |
|
required |
Set if the field is required on the registration page |
|
order |
The order displayed in the user interface |
The following is an example of an enum defining mobile device registration on the OTP registration page of an authenticator:
bharosa.uio.default.userinfo.inputs.enum.mobile=0 bharosa.uio.default.userinfo.inputs.enum.mobile.name=Mobile Phone bharosa.uio.default.userinfo.inputs.enum.mobile.description=Mobile Phone bharosa.uio.default.userinfo.inputs.enum.mobile.inputname=cellnumber bharosa.uio.default.userinfo.inputs.enum.mobile.inputtype=text bharosa.uio.default.userinfo.inputs.enum.mobile.maxlength=15 bharosa.uio.default.userinfo.inputs.enum.mobile.required=true bharosa.uio.default.userinfo.inputs.enum.mobile.order=1 bharosa.uio.default.userinfo.inputs.enum.mobile.enabled=true
The following is an example of an enum for adding a second mobile device to register:
bharosa.uio.default.userinfo.inputs.enum.mobile2=2
bharosa.uio.default.userinfo.inputs.enum.mobile2.name=Mobile Phone 2
bharosa.uio.default.userinfo.inputs.enum.mobile2.description=Mobile Phone 2
bharosa.uio.default.userinfo.inputs.enum.mobile2.inputname=mobile2
bharosa.uio.default.userinfo.inputs.enum.mobile2.inputtype=text
bharosa.uio.default.userinfo.inputs.enum.mobile2.maxlength=10
bharosa.uio.default.userinfo.inputs.enum.mobile2.required=true
bharosa.uio.default.userinfo.inputs.enum.mobile2.order=2
bharosa.uio.default.userinfo.inputs.enum.mobile2.enabled=true
bharosa.uio.default.userinfo.inputs.enum.mobile2.regex=\\D?(\\d{3})\\D?\\D?(\\d{3})\\D?(\\d{4})
bharosa.uio.default.userinfo.inputs.enum.mobile2.errorCode=otp.invalid.mobile
bharosa.uio.default.userinfo.inputs.enum.mobile2.managerClass=com.bharosa.uio.manager.user.DefaultContactInfoManager
The following is an example of an enum defining email registration on the OTP registration page of an authenticator:
bharosa.uio.default.userinfo.inputs.enum.email=1
bharosa.uio.default.userinfo.inputs.enum.email.name=Email Address
bharosa.uio.default.userinfo.inputs.enum.email.description=Email Address
bharosa.uio.default.userinfo.inputs.enum.email.inputname=email
bharosa.uio.default.userinfo.inputs.enum.email.inputtype=text
bharosa.uio.default.userinfo.inputs.enum.email.maxlength=40
bharosa.uio.default.userinfo.inputs.enum.email.required=true
bharosa.uio.default.userinfo.inputs.enum.email.order=2
bharosa.uio.default.userinfo.inputs.enum.email.enabled=true
bharosa.uio.default.userinfo.inputs.enum.email.regex=.+@[a-zA-Z_]+?\\.[a-zA-Z]{2,3}
bharosa.uio.default.userinfo.inputs.enum.email.errorCode=otp.invalid.email
bharosa.uio.default.userinfo.inputs.enum.email.managerClass=com.bharosa.uio.manager.user.DefaultContactInfoManager
The following is an example of an enum for adding a second email to register:
bharosa.uio.default.userinfo.inputs.enum.email2=2
bharosa.uio.default.userinfo.inputs.enum.email2.name=Email Address 2
bharosa.uio.default.userinfo.inputs.enum.email2.description=Email Address 2
bharosa.uio.default.userinfo.inputs.enum.email2.inputname=email2
bharosa.uio.default.userinfo.inputs.enum.email2.inputtype=text
bharosa.uio.default.userinfo.inputs.enum.email2.maxlength=40
bharosa.uio.default.userinfo.inputs.enum.email2.required=true
bharosa.uio.default.userinfo.inputs.enum.email2.order=2
bharosa.uio.default.userinfo.inputs.enum.email2.enabled=true
bharosa.uio.default.userinfo.inputs.enum.email2.regex=.+@[a-zA-Z_]+?\\.[a-zA-Z]{2,3}
bharosa.uio.default.userinfo.inputs.enum.email2.errorCode=otp.invalid.email
bharosa.uio.default.userinfo.inputs.enum.email2.managerClass=com.bharosa.uio.manager.user.DefaultContactInfoManager
8.3.3 Configuring the OTP Challenge Types
Configure the bharosa.uio.default.challenge.type.enum property to edit out-of-the-box OTP challenge types or add a new challenge type.
Table 8-2 Challenge type Properties
| Property | Description |
|---|---|
|
available |
if the challenge type is available for use (service ready and configured). To enable/disable an OTP challenge type, the available flag should be set. |
|
processor |
java class for handling challenges of this type. The challenge mechanism is customizable through Java classes. See the Oracle Fusion Middleware Developer's Guide for Oracle Adaptive Access Manager for information. |
|
requiredInfo |
comma separated list of inputs from registration input enum |
The following is an example of an enum defining email challenge for OTP:
bharosa.uio.default.challenge.type.enum.ChallengeEmail = 1 bharosa.uio.default.challenge.type.enum.ChallengeEmail.name = Email Challenge bharosa.uio.default.challenge.type.enum.ChallengeEmail.description = Email Challenge bharosa.uio.default.challenge.type.enum.ChallengeEmail.processor = com.bharosa.uio.processor.challenge.EmailChallengeProcessor bharosa.uio.default.challenge.type.enum.ChallengeEmail.requiredInfo = mobile bharosa.uio.default.challenge.type.enum.ChallengeEmail.available = true bharosa.uio.default.challenge.type.enum.ChallengeEmail.enabled = true
The following is an example of an enum defining SMS challenge for OTP:
bharosa.uio.default.challenge.type.enum.ChallengeSMS = 2 bharosa.uio.default.challenge.type.enum.ChallengeSMS.name = SMS Challenge bharosa.uio.default.challenge.type.enum.ChallengeSMS.description = SMS Challenge bharosa.uio.default.challenge.type.enum.ChallengeSMS.processor = com.bharosa.uio.processor.challenge.SmsChallengeProcessor bharosa.uio.default.challenge.type.enum.ChallengeSMS.requiredInfo = mobile bharosa.uio.default.challenge.type.enum.ChallengeSMS.available = true bharosa.uio.default.challenge.type.enum.ChallengeSMS.enabled = true
8.4 Configuring OTP Presentation
8.4.1 Adding an OTP Device
By default, challenge devices are configured through rules. The rules are under the Authentication Pad checkpoint and determine the type of device to use based on the purpose of the device (ChallengeEmail, ChallengeSMS, ChallengeQuestion, and so on).
Alternatively, if you want to configure challenge devices using properties, you can bypass the Authentication Pad checkpoint by setting bharosa.uio.default.use.authentipad.checkpoint to false. Then, perform the following instructions:
Edit the challenge type properties (ChallengeEmail, ChallengeSMS) so that the desired device is displayed for challenging the user.
For the example in Table 8-3, PinPad has been configured as the SMS and Email authenticator.
bharosa.uio.default.ChallengeSMS.authenticator.device=DevicePinPad bharosa.uio.default.ChallengeEmail.authenticator.device=DevicePinPad
Other device choices are listed in Table 8-3.
| Property | Description |
|---|---|
|
None |
No HTML page or authentication pad |
|
DeviceKeyPadFull |
Challenge user using KeyPad. |
|
DeviceKeyPadAlpha |
Challenge user with the alphanumeric KeyPad (numbers and letters only, no special characters) |
|
DeviceTextPad |
Challenge user using TextPad. |
|
DeviceQuestionPad |
Challenge user using QuestionPad. |
|
DevicePinPad |
Challenge user using PinPad. |
|
DeviceHTMLControl |
Challenge user using HTML page instead of an authentication pad. |
The OTP device is displayed at the next login to the application.
8.5 Enabling OTP Challenge
-
In the Navigation tree, double-click Properties. The Properties Search page is displayed.
-
Search for the
bharosa.uio.default.challenge.type.enum.<challengeType>.availableproperty and set it to true for the OTP challenge you want. -
If you want challenge questions enabled as well, ensure that
bharosa.uio.default.challenge.type.enum.ChallengeQuestion.availableis set to true. -
Configure a new policy with the OTP challenge type as the result action.
In default policies, if OTP is enabled, OTP challenges occurs after a user is KBA Challenge blocked.
High risk user are KBA Challenged. If the user fails the KBA challenge, the user will be presented with the appropriate virtual authentication device and receive the OTP through the proper channel.
8.6 Setting Up Failure Counter
When a user fails the OTP challenge, a counter is updated to indicate that user has had a failure. The failure counter looks across sessions.
The failure counter is set using the User: Check OTP failures condition.
Note:
A success for an OTP challenge automatically resets the OTP failure counters to 0.8.7 OTP Case Management
Steps for using case management actions for OTP are described in the following subsections.
8.7.1 Resetting OTP Profile
This Reset Profile option resets the OTP profile for the user.
-
From the Cases Search page.
For information, see Chapter 4, "Managing and Supporting Cases."
-
Click the case number of the case you want.
The Case Details page appears.
-
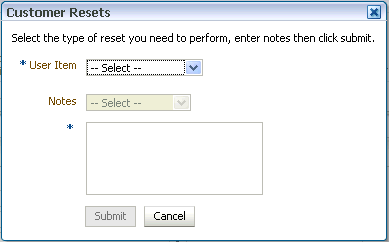
On the menu bar, click Customer Resets.
The Customer Resets screen appears.
-
In the Item to Select list, select Reset Profile.
-
In the Notes list, click the note you want to add.
-
If you selected Other from the Notes list, enter a note describing why you are taking the action.
-
Click Submit.
8.7.2 Unlocking User
This action resets the OTP failure counter for the user.
An "OTP lock" occurs when a user's failure counter across sessions is greater than the threshold value specified.
As a CSR, you can unlock a user if the lock out occurred through OTP failures. To do this:
-
Search for the case from Cases Search page.
For information, see Chapter 4, "Managing and Supporting Cases."
-
Click the case number of the case you want.
The Case Details page appears.
-
On the menu bar, click Customer Resets.
The Customer Resets screen appears.
-
In the Item to Select list, select Unlock Customer.
-
In the Notes list, click the note you want to add.
-
If you selected Other from the Notes list, enter a note describing why you are taking the action.
-
Click Submit.
An OTP unlock resets the OTP failure count to 0.
Note:
An "Unlock OTP" action does not affect KBA functionality and vice versa.8.7.3 OTP Case Details
The Case Details page provides the following OTP-specific information:
-
In the Navigation tree, double-click Cases.
The Cases Search page is displayed.
-
Create a case for a user who has a registered OTP profile.
-
From the Case Details, click Customer Resets and select Reset OTP Profile. Enter notes and click Submit.
OTP Profile is reset. Last Case Action and Last Case Action date in Case Details page display the Reset OTP Profile action and date.
8.8 Viewing OTP Performance Data
-
In the Navigation tree, double-click Dashboard.
-
Check Section I of the Dashboard for OTP Challenges per minute.
The graph displays the OTP Challenges per minute statistics
-
Check Section II of the Dashboard
The summary table of the Dashboard displays the Count of OTP Challenges for the specified time period.
-
Check Section III of the Dashboard under Locations.
The Location Dashboard displays performance statistics, such as count, percentage, and others.