6 Configuring SSL in Oracle Fusion Middleware
You can configure Oracle Fusion Middleware to secure communications between Oracle Fusion Middleware components using SSL, which is an industry standard for securing communications. Oracle Fusion Middleware supports SSL version 3, as well as TLS version 1.
Note:
SSL version 2 has been desupported in 11g Release 1 (11.1.1) due to security concerns; components or applications that used SSL version 2 in pre-11g Release 1 (11.1.1) will automatically be upgraded to use other SSL versions, that is, SSL version 3 and TLS version 1.See Also :
Chapter 7, "Using the SSL Automation Tool." The SSL Automation Tool enables you to configure SSL for multiple components using a domain-specific CA.This chapter provides an overview of SSL and how you can use it with Oracle Fusion Middleware components and applications. It contains these topics:
Note:
Where SSL connections are configured within Oracle WebLogic Server, this chapter provides references to the relevant Oracle WebLogic Server documentation rather than duplicating the instructions here.6.1 How SSL Works
This section introduces basic SSL concepts. It contains these topics:
6.1.1 What SSL Provides
SSL secures communication by providing message encryption, integrity, and authentication. The SSL standard allows the involved components (such as browsers and HTTP servers) to negotiate which encryption, authentication, and integrity mechanisms to use.
-
Encryption provides confidentiality by allowing only the intended recipient to read the message. SSL can use different encryption algorithms to encrypt messages. During the SSL handshake that occurs at the start of each SSL session, the client and the server negotiate which algorithm to use. Examples of encryption algorithms supported by SSL include AES, RC4, and 3DES.
-
Integrity ensures that a message sent by a client is received intact by the server, untampered. To ensure message integrity, the client hashes the message into a digest using a hash function and sends this message digest to the server. The server also hashes the message into a digest and compares the digests. Because SSL uses hash functions that make it computationally infeasible to produce the same digest from two different messages, the server can tell that if the digests do not match, then someone had tampered with the message. An example of a hash function supported by SSL is SHA1.
-
Authentication enables the server and client to check that the other party is who it claims to be. When a client initiates an SSL session, the server typically sends its certificate to the client. Certificates are digital identities that are issued by trusted certificate authorities, such as Verisign. Chapter 8, "Managing Keystores, Wallets, and Certificates" describes certificates in more detail.
The client verifies that the server is authentic and not an imposter by validating the certificate chain in the server certificate. The server certificate is guaranteed by the certificate authority (CA) who signed the server certificate.
The server can also require the client to have a certificate, if the server needs to authenticate the identity of the client.
6.1.2 About Private and Public Key Cryptography
To provide message integrity, authentication, and encryption, SSL uses both private and public key cryptography.
Private, or symmetric, key cryptography requires a single, secret key shared by two or more parties to secure communication. This key is used to encrypt and decrypt secure messages sent between the parties. This requires prior and secure distribution of the key to each party. The problem with this method is that it is difficult to securely transmit and store the key.
In SSL, each party calculates the secret key individually using random values known to each side. The parties then send messages encrypted using the secret key.
Public key cryptography solves this problem by employing public and private key pairs and a secure method for key distribution. The freely available public key is used to encrypt messages that can only be decrypted by the holder of the associated private key. The private key is securely stored, together with other security credentials, in an encrypted container such as an Oracle wallet.
Public key algorithms can guarantee the secrecy of a message, but they do not necessarily guarantee secure communication because they do not verify the identities of the communicating parties. To establish secure communication, it is important to verify that the public key used to encrypt a message does in fact belong to the target recipient. Otherwise, a third party can potentially eavesdrop on the communication and intercept public key requests, substituting its own public key for a legitimate key (the man-in-the-middle attack).
To avoid such an attack, it is necessary to verify the owner of the public key, a process called authentication. Authentication can be accomplished through a certificate authority (CA), which is a third party trusted by both of the communicating parties.
The CA issues public key certificates that contain an entity's name, public key, and certain other security credentials. Such credentials typically include the CA name, the CA signature, and the certificate effective dates (From Date, To Date).
The CA uses its private key to encrypt a message, while the public key is used to decrypt it, thus verifying that the message was encrypted by the CA. The CA public key is well known, and does not have to be authenticated each time it is accessed. Such CA public keys are stored in wallets.
6.1.3 Keystores and Wallets
In Oracle Fusion Middleware, Oracle Virtual Directory uses a JKS keystore to store keys and certificates. Configuring SSL for Oracle Virtual Directory thus requires setting up and using JKS keystores.
Other components use the Oracle wallet as their storage mechanism. An Oracle wallet is a container that stores your credentials, such as certificates, trusted certificates, certificate requests, and private keys. You can store Oracle wallets on the file system or in LDAP directories such as Oracle Internet Directory. Oracle wallets can be auto-login or password-protected wallets.
Components that use Oracle wallet include:
-
Oracle HTTP Server
-
Oracle Web Cache
-
Oracle Internet Directory
Configuring SSL for these components thus requires setting up and using Oracle wallets.
For more information about configuring keystores and wallets, see:
-
Section 6.2, "About SSL in Oracle Fusion Middleware" for a fuller description of keystore and wallet usage in Oracle Fusion Middleware
-
Chapter 8, "Managing Keystores, Wallets, and Certificates" for a discussion of these terms, and administration details
6.1.4 How SSL Sessions Are Conducted
The SSL protocol has two phases: the handshake phase and the data transfer phase. The handshake phase authenticates the server and optionally the client, and establishes the cryptographic keys that will be used to protect the data to be transmitted in the data transfer phase.
When a client requests an SSL connection to a server, the client and server first exchange messages in the handshake phase. (A common scenario is a browser requesting a page using the https:// instead of http:// protocol from a server. The HTTPS protocol indicates the usage of SSL with HTTP.)
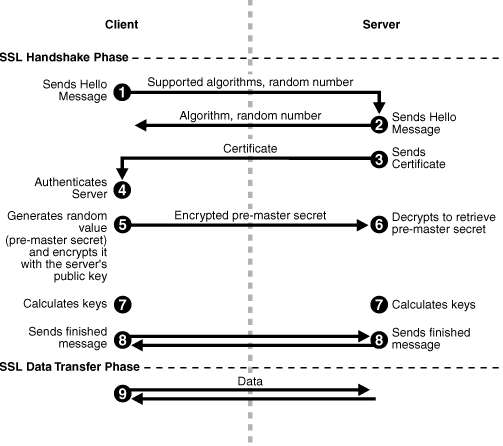
Figure 6-1 shows the handshake messages for a typical SSL connection between a Web server and a browser. The following steps are shown in the figure:
-
The client sends a Hello message to the server.
The message includes a list of algorithms supported by the client and a random number that will be used to generate the keys.
-
The server responds by sending a Hello message to the client. This message includes:
-
The algorithm to use. The server selected this from the list sent by the client.
-
A random number, which will be used to generate the keys.
-
-
The server sends its certificate to the client.
-
The client authenticates the server using the server's certificate.
-
The client generates a random value ("pre-master secret"), encrypts it using the server's public key, and sends it to the server.
-
The server uses its private key to decrypt the message to retrieve the pre-master secret.
-
The client and server separately calculate the keys that will be used in the SSL session.
These keys are not sent to each other because the keys are calculated based on the pre-master secret and the random numbers, which are known to each side. The keys include:
-
Encryption key that the client uses to encrypt data before sending it to the server
-
Encryption key that the server uses to encrypt data before sending it to the client
-
Key that the client uses to create a message digest of the data
-
Key that the server uses to create a message digest of the data
The encryption keys are symmetric, that is, the same key is used to encrypt and decrypt the data.
-
-
The client and server send a
Finishedmessage to each other. These are the first messages that are sent using the keys generated in the previous step (the first "secure" messages).The
Finishedmessage includes all the previous handshake messages that each side sent. Each side verifies that the previous messages that it received match the messages included in theFinishedmessage. This checks that the handshake messages were not tampered with. -
The client and server now transfer data using the encryption and hashing keys and algorithms.
6.2 About SSL in Oracle Fusion Middleware
This section introduces SSL in Oracle Fusion Middleware. It contains these topics:
6.2.1 SSL in the Oracle Fusion Middleware Architecture
Figure 6-2 SSL in Oracle Fusion Middleware
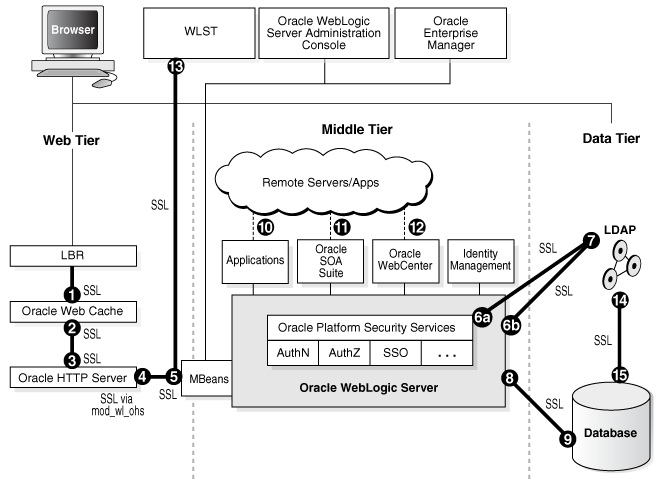
Description of "Figure 6-2 SSL in Oracle Fusion Middleware"
Notes:
-
In Figure 6-2, the label "Oracle Enterprise Manager" refers to the Fusion Middleware Control user interface.
-
Other administrative tools, such as
opmn, are available for specific tasks.
In the Oracle Fusion Middleware architecture shown in Figure 6-2, the numbered circles represent the endpoints that can be SSL-enabled. For configuration details about each endpoint, see:
-
Section 6.4.2.1, "Enable Inbound SSL for Oracle Web Cache Using Fusion Middleware Control" and Section 6.4.2.2, "Enable Inbound SSL for Oracle Web Cache Using WLST"
-
Section 6.4.2.3, "Enable Outbound SSL for Oracle Web Cache Using Fusion Middleware Control" and Section 6.4.2.4, "Specify the Wallet for Outbound SSL from Oracle Web Cache Using WLST"
-
Section 6.4.3.1, "Enable SSL for Inbound Requests to Oracle HTTP Server Virtual Hosts Using Fusion Middleware Control" and Section 6.4.3.2, "Enable SSL for Inbound Requests to Oracle HTTP Server Virtual Hosts Using WLST"
-
Section 6.4.3.3, "Enable SSL for Outbound Requests from Oracle HTTP Server"
-
Outbound connections to the LDAP server can originate from Oracle Platform Security Services or from Oracle WebLogic Server:
-
Section 6.6.1.1, "Enable Inbound SSL on an Oracle Internet Directory Listener Using Fusion Middleware Control" and Section 6.6.1.2, "Enabling Inbound SSL on an Oracle Internet Directory Listener Using WLST"
-
Section 6.6.1.3, "Enabling Outbound SSL from Oracle Internet Directory to Oracle Database"
In addition, you can configure SSL for identity management components. For details, see:
-
Section 6.5.4.1, "Configuring SSL for Oracle Directory Integration Platform"
-
Section 6.5.4.2, "Configuring SSL for Oracle Identity Federation"
-
Section 6.5.4.3, "Configuring SSL for Oracle Directory Services Manager"
Keystores and wallets are central to SSL configuration and are used to store certificates and keys.
For details, see Section 6.2.2, "Keystores and Oracle Wallets."
6.2.2 Keystores and Oracle Wallets
Oracle Fusion Middleware supports two types of keystores for keys and certificates:
-
JKS-based keystore and truststore
-
Oracle wallet
In 11g Release 1 (11.1.1), all Java components and applications use the JKS keystore. Thus all Java components and applications running on Oracle WebLogic Server use the JKS-based KeyStore and TrustStore.
The following system components continue to use the Oracle wallet:
-
Oracle HTTP Server
-
Oracle Web Cache
-
Oracle Internet Directory
You can use Fusion Middleware Control or the command-line WLST and orapki interfaces, to manage wallets and their certificates for these system components. You can use either the Fusion Middleware Control or WLST to SSL-enable the listeners for these components.
Oracle Virtual Directory uses a JKS-based keystore. You can use Fusion Middleware Control or WLST to manage JKS keystores and their certificates for Oracle Virtual Directory. You can use either the Fusion Middleware Control or WLST to SSL-enable the listeners for Oracle Virtual Directory.
JDK's keytool utility manages the keystore used by Oracle WebLogic Server listeners for Java EE applications. This is the only keystore tool to manage these keystores; no graphical user interface is available for this purpose.
For more information about these types of stores, and when to use which type of store, see Section 6.1.3, "Keystores and Wallets".
See Also:
Section 8.1, "Key and Certificate Storage in Oracle Fusion Middleware" for keystore management6.2.3 Authentication Modes
The following authentication modes are supported:
-
In no-authentication mode, neither server nor client are required to authenticate.
Other names for this mode include Anonymous SSL/No Authentication/Diffie-Hellman.
-
In server authentication mode, a server authenticates itself to a client.
This mode is also referred to as One-way SSL/Server Authentication.
-
In mutual authentication mode, a client authenticates itself to a server and that server authenticates itself to the client.
This mode is also known as Two-way SSL/Client Authentication.
-
In optional client authentication mode, the server authenticates itself to the client, but the client may or may not authenticate itself to the server. Even if the client does not authenticate itself, the SSL session still goes through.
6.2.4 Tools for SSL Configuration
Oracle Fusion Middleware uses two kinds of configuration tools, common and advanced.
-
Fusion Middleware Control
-
WLST command-line interface
-
Oracle WebLogic Server Administration Console
-
keytoolcommand-line tool
These tools allow you to configure SSL and manage Oracle Wallet/JKS keystore for any listener or component in Oracle Fusion Middleware.
-
Oracle Wallet Manager graphical user interface
-
orapkicommand-line interface
These tools allow you to configure advanced features like managing file-based CRLs, PKCS11-based wallets, and so on.
See Also:
Section 8.1, "Key and Certificate Storage in Oracle Fusion Middleware" for keystore management6.3 Configuring SSL for Configuration Tools
Several tools are available for Oracle Fusion Middleware configuration. This section describes how to configure SSL for these tools to enable them to connect to an SSL-enabled Oracle WebLogic Server.
For a list of all the configuration tools, see Section 6.2.4, "Tools for SSL Configuration.".
This section contains these topics:
6.3.1 Oracle Enterprise Manager Fusion Middleware Control
Take these steps:
-
Ensure that the SSL port is enabled on the Oracle WebLogic Server instance on which Fusion Middleware Control is deployed, and that the browser (from which you will launch Fusion Middleware Control) trusts the server certificate.
-
Now launch Fusion Middleware Control using an SSL-based URL, in the format https://
host:port.
6.3.2 Oracle WebLogic Server Administration Console
Ensure that the SSL port is enabled on the Oracle WebLogic Server instance. Now launch the administration console by providing the SSL port in the URL. You may get a warning that the certificate is not trusted; accept this certificate and continue.
6.3.3 WLST Command-Line Tool
For details about configuring SSL for WLST, take these steps:
-
Launch the WLST shell.
-
Execute the WLST command:
help('connect')
Follow the instructions described in the help text to set up the WLST shell in SSL mode.
6.4 Configuring SSL for the Web Tier
This section contains these topics:
6.4.1 Configuring Load Balancers
Use the instructions specific to your load-balancing device to configure load balancers in your Oracle Fusion Middleware environment.
6.4.2 Enabling SSL for Oracle Web Cache Endpoints
This section explains how to enable SSL for Oracle Web Cache listening endpoints using Fusion Middleware Control and WLST.
6.4.2.1 Enable Inbound SSL for Oracle Web Cache Using Fusion Middleware Control
You can SSL-enable inbound traffic to Oracle Web Cache listening endpoints using these steps:
Note:
This information applies only to inbound communication; for information about SSL-enabling outbound traffic from Oracle Web Cache to Oracle HTTP Server, see Section 6.4.2.3, "Enable Outbound SSL for Oracle Web Cache Using Fusion Middleware Control".-
Select the Oracle Web Cache instance in the navigation pane on the left.
-
Create a wallet, if necessary, by navigating to Oracle Web Cache, then Security, then Wallets.
For details about wallet creation and maintenance, see Chapter 8, "Managing Keystores, Wallets, and Certificates".
-
Navigate to Oracle Web Cache, then Security, then SSL Configuration.
The SSL Configuration page contains two sets of information:
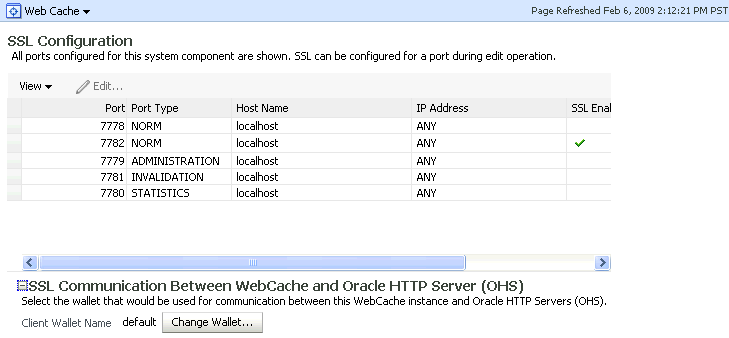
Description of the illustration wcssl1.gif
The top table shows the inbound settings for a list of listening endpoints. A check in the SSL Enabled column indicates that the endpoint is configured for SSL.
The bottom portion of the page shows outbound SSL configuration. For more information about outbound SSL, see Section 6.4.2.3, "Enable Outbound SSL for Oracle Web Cache Using Fusion Middleware Control.".
-
Select an endpoint, and click Edit.
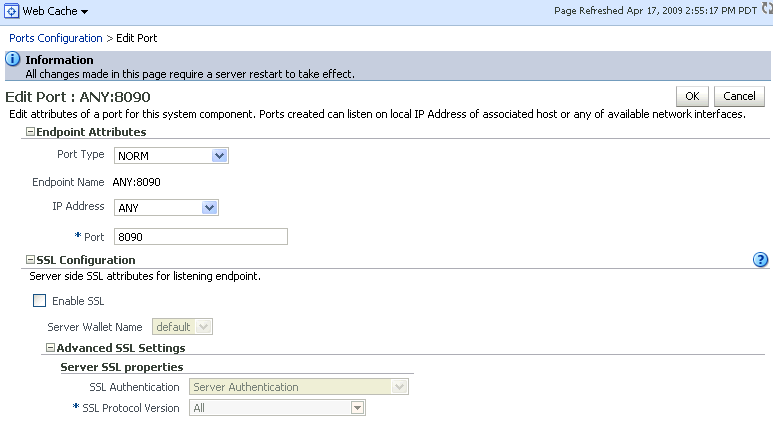
Description of the illustration wcssl2.gif
The Edit Port page appears. This page contains two sections—a top portion with general details like port and IP address, and a bottom section that configures SSL parameters.
-
To disable SSL, uncheck Enable SSL; restart the component instance by navigating to Oracle Web Cache, then Control, then Restart.
-
To enable SSL for this endpoint, check Enable SSL. Next, enter SSL configuration parameters:
-
Select an Oracle wallet from the drop-down list.
Note:
Ensure that the wallet contains the server certificate and its corresponding CA certificate. -
Select the type of SSL authentication.
-
Select the protocol version (the available options are determined by your choice of authentication).
-
-
Click OK.
-
Restart the Oracle Web Cache instance by navigating to Oracle Web Cache, then Control, then Restart.
6.4.2.2 Enable Inbound SSL for Oracle Web Cache Using WLST
You can enable SSL for inbound traffic to Oracle Web Cache using the WLST command-line tool.
SSL-Enable Oracle Web Cache Inbound in server-auth Mode Using WLST
Take these steps:
-
Determine the listening endpoints for this Oracle Web Cache instance by running the following command:
listListeners('inst1','wc1')This command will list all the listening endpoints for this instance; select the one that needs to be configured for SSL. For example, select
CACHE.index1.LISTEN.index1. -
Configure the listening endpoint with SSL properties:
configureSSL('inst1', 'wc1', 'webcache', 'CACHE.index1.LISTEN.index1')
6.4.2.3 Enable Outbound SSL for Oracle Web Cache Using Fusion Middleware Control
Outbound Oracle Web Cache refers to traffic from Oracle Web Cache to Oracle HTTP Server.
There are two aspects to set up SSL for outbound traffic from Oracle Web Cache: selecting a wallet for outbound SSL and configuring SSL.
Take these steps:
-
Navigate to Oracle Web Cache, then Security, then SSL Configuration.

Description of the illustration wcssl1.gif
-
At the bottom of the page, click Change Wallet to display the available wallets for this listener.
Description of the illustration wcssl3.gif
-
Select the desired wallet for outbound SSL and click OK.
Take these steps:
-
Navigate to the Oracle Web Cache instance, then Administration, then Origin Servers.
This page displays the Oracle HTTP Servers with which this Oracle Web Cache instance can communicate. For example, if Oracle Web Cache can talk to two different Oracle HTTP Servers you would see two rows in the table.
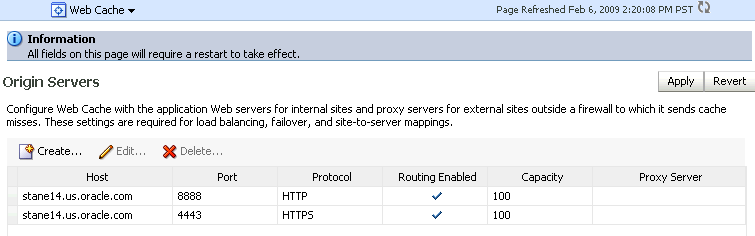
Description of the illustration wcssl4.gif
In this example, the Oracle Web Cache instance is currently configured for non-SSL communication to the origin server over this host and port.
-
To enable SSL for outbound traffic to this origin server, select the row and click Edit.
-
The Edit Origin Server page appears:
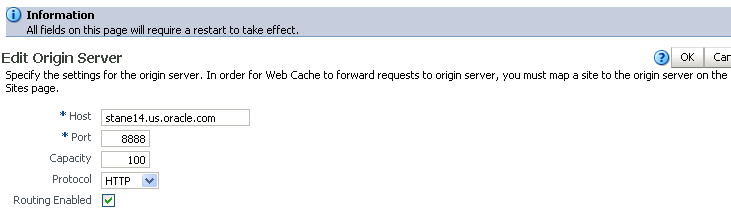
Description of the illustration wcssl5.gif
-
Use the Protocol drop-down box to change the protocol to
https. -
Click OK. Oracle Web Cache is now configured to communicate to the origin server over SSL.
Note:
When editing the origin server settings on this page, ensure that Oracle HTTP Server is listening at this port in SSL mode.6.4.2.4 Specify the Wallet for Outbound SSL from Oracle Web Cache Using WLST
To change the wallet in use for outbound SSL connections from Oracle Web Cache, use a command like the following:
configureSSL('inst1',
'wc1',
'webcache',
'CACHE.index0.CLIENTSSL',
'property-file.prop')
where:
-
inst1is the name of the application server instance -
wc1is the name of the Oracle Web Cache instance -
webcacheis the component type -
CACHE.index0.CLIENTSSLis the listener name for client SSL -
property-file.propcontains:KeyStore=wallet-path
6.4.3 Enabling SSL for Oracle HTTP Server Virtual Hosts
This section shows how to manage SSL configuration for Oracle HTTP Server virtual hosts.
For inbound traffic:
For outbound traffic:
6.4.3.1 Enable SSL for Inbound Requests to Oracle HTTP Server Virtual Hosts Using Fusion Middleware Control
You can SSL-enable inbound traffic to Oracle HTTP Server virtual hosts using these steps:
-
Select the Oracle HTTP Server instance in the navigation pane on the left.
-
Create a wallet, if necessary, by navigating to Oracle HTTP Server, then Security, then Wallets.
For details about wallet creation and maintenance, see Chapter 8, "Managing Keystores, Wallets, and Certificates".
-
Navigate to Oracle HTTP Server, then Administration, then Virtual Hosts.
This page shows what hosts are currently configured, and whether they are configured for http or https.
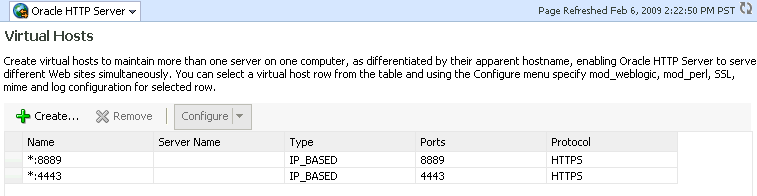
Description of the illustration ohsssl1.gif
-
Select the virtual host you wish to update, and click Configure, then SSL Configuration.
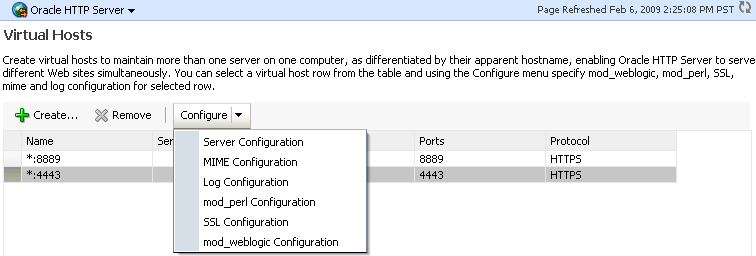
Description of the illustration ohsssl2.gif
The SSL Configuration page appears.
-
You can convert an https port to http by simply unchecking Enable SSL.
To configure SSL for a virtual host that is currently using http:
-
Check the Enable SSL box.
-
Select a wallet from the drop-down list.
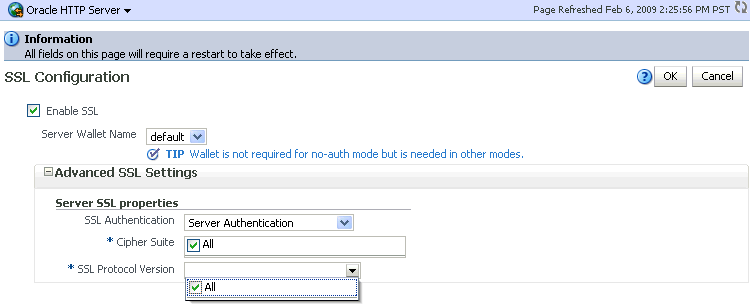
Description of the illustration ohsssl3.gif
-
From the Server SSL properties, select the SSL authentication type, cipher suites to use, and the SSL protocol version.
Note:
The default values are appropriate in most situations.Note:
The choice of authentication type determines the available cipher suites, and the selected cipher suites determine the available protocol versions. For more information about ciphers and protocol versions, see Section 6.9.28, "Properties Files for SSL".
-
-
Click OK to apply the changes.
-
Restart the Oracle HTTP Server instance by navigating to Oracle HTTP Server, then Control, then Restart.
-
Open a browser session and connect to the port number that was SSL-enabled.
6.4.3.2 Enable SSL for Inbound Requests to Oracle HTTP Server Virtual Hosts Using WLST
Take these steps:
-
Determine the virtual hosts for this Oracle HTTP Server instance by running the following command:
listListeners('inst1','ohs1' )This command lists all the virtual hosts for this instance; select the one that needs to be configured for SSL. For example, you can select vhost1.
-
Configure the virtual host with SSL properties:
configureSSL('inst1', 'ohs1', 'ohs', 'vhost1')
6.4.3.3 Enable SSL for Outbound Requests from Oracle HTTP Server
You enable SSL for outbound requests from Oracle HTTP Server by configuring mod_wl_ohs.
The steps are as follows:
-
Generate a custom keystore for Oracle WebLogic Server (see Section 6.5.1, "Configuring SSL for Oracle WebLogic Server") containing a certificate.
-
Import the certificate used by Oracle WebLogic Server from Step 1 into the Oracle HTTP Server wallet as a trusted certificate. You can use any available utility such as WLST or Fusion Middleware Control for this task.
-
Edit the Oracle HTTP Server configuration file
INSTANCE_HOME/config/OHS/ohs1/ssl.confand add the following line to the SSL configuration undermod_weblogic:WlSSLWallet "$(ORACLE_INSTANCE}/config/COMPONENT_TYPE/COMPONENT_NAME/keystores/default"where
defaultis the name of the Oracle HTTP Server wallet in Step 2.Here is an example of how the configuration should look:
<IfModule mod_weblogic.c> WebLogicHost myweblogic.server.com WebLogicPort 7002 MatchExpression *.jsp SecureProxy On WlSSLWallet "$(ORACLE_INSTANCE)/config/OHS/ohs1/keystores/default" </IfModule>
Save the file and exit. Restart Oracle HTTP Server to activate the changes.
-
Ensure that your Oracle WebLogic Server instance is configured to use the custom keystore generated in Step 1, and that the alias points to the alias value used in generating the certificate. Restart the Oracle WebLogic Server instance.
mod_wl_ohs also supports two-way SSL communication. To configure two-way SSL:
-
Perform Steps 1 through 4 of the preceding procedure for one-way SSL.
-
Generate a trust store,
trust.jks, for Oracle WebLogic Server.The keystore created for one-way SSL (Step 1 of the preceding procedure) could also be used to store trusted certificates, but it is recommended that you create a separate truststore for this procedure.
-
Export the user certificate from the Oracle HTTP Server wallet, and import it into the truststore created in Step 2.
You can use any available utility such as WLST or Fusion Middleware Control for export, and the
keytoolutility for import. -
From the Oracle WebLogic Server Administration Console, select the Keystores tab for the server being configured.
-
Set the custom trust store with the
trust.jksfile location of the trust store that was created in Step 2 (use the full name). -
Set the keystore type as JKS, and set the passphrase used to create the keystore.
-
Under the SSL tab, ensure that Trusted Certificate Authorities is set as from Custom Trust Keystore.
6.5 Configuring SSL for the Middle Tier
Using SSL in the middle tier includes:
-
SSL-enabling the application server
-
SSL-enabling components and applications running on the application server
This section addresses mid-tier SSL configuration and contains these topics:
6.5.1 Configuring SSL for Oracle WebLogic Server
This section describes configuration for the application server.
6.5.1.1 Inbound SSL to Oracle WebLogic Server
For information and details about implementing SSL to secure Oracle WebLogic Server, see Oracle Fusion Middleware Securing Oracle WebLogic Server.
6.5.1.2 Outbound SSL from Oracle WebLogic Server
This section describes how to SSL-enable outbound connections from Oracle WebLogic Server.
6.5.1.2.1 Outbound SSL from Oracle Platform Security Services to LDAP
This section explains how to configure SSL for policy stores and credential stores connections to an LDAP directory. Anonymous and one-way SSL is supported.
Anonymous SSL (Server-side)
Start the LDAP server in anonymous authentication mode.
For Oracle Internet Directory, see Section 6.6.1.1, "Enable Inbound SSL on an Oracle Internet Directory Listener Using Fusion Middleware Control".
If using another directory, consult your LDAP server documentation for information on this task.
Anonymous SSL (Client-side)
In your jps-config.xml file, you must set the protocol to ldaps and specify the appropriate port for the property ldap.url. This information needs to be updated for policy store, credential store, key store and any other service instances that use ldap.url.
One-Way SSL (Server-side)
Prerequisite: LDAP server in SSL Server Authentication Mode.
For details on this procedure, see the Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory.
One-Way SSL (Client-side)
The following must be in place for the client-side configuration:
-
The JVM needs to know where to find the trust store that it uses to trust certificates from LDAP. You do this by setting:
-Djavax.net.ssl.trustStore=path_to_jks_fileThis property is added either to the JavaSE program, or to the server start-up properties in a Java EE environment.
-
In your
jps-config.xmlfile, you must set the protocol toldapsand specify the appropriate port for the propertyldap.url. This information needs to be updated for policy store, credential store, key store and any other service instances that useldap.url. -
Using keytool, import the LDAP server's certificate into the trust store specified in step 1.
6.5.1.2.2 Outbound SSL from Oracle Platform Security Services to Oracle Database
You can set up a one-way or two-way SSL connection to a database-based OPSS security store.
For details about configuring the database server and clients, see Oracle Fusion Middleware Application Security Guide.
6.5.1.2.3 Outbound SSL from LDAP Authenticator to LDAP
When you configure an LDAP authenticator in Oracle WebLogic Server, you can specify that connections to the LDAP store should use SSL.
Take these steps to configure the authenticator:
-
Log in to the Oracle WebLogic Server Administration Console.
-
In the left pane, select Security Realms and click the name of the realm you are configuring.
-
Select Providers, then Authentication and click New.
-
In the Name field, enter a name for the authentication provider.
-
From the Type drop-down list, select the type of the Authentication provider and click OK.
For example, if using Oracle Internet Directory, choose
OracleInternetDirectoryAuthenticator. -
Select Providers, then Authentication and click the name of the new authentication provider to complete its configuration.
-
On the Configuration page for the authentication provider, set the desired values on the Common and Provider-Specific tabs.
-
Common Tab
Set the Control Flag to
SUFFICIENTfor all authenticators, including theDefaultAuthenticator -
Provider-Specific Tab
host: host-name
port: port-number
principal: cn=
orcladmincredential/confirm: password
user base dn:
cn=Users,dc=us,dc=oracle,dc=comgroup base dn:
cn=Groups,dc=us,dc=oracle,dc=com
-
-
Save your changes and restart the server.
6.5.1.2.4 Outbound SSL to Database
Configuring SSL between Oracle WebLogic Server and the database requires two sets of steps:
-
Configuring SSL Listener for the Database
-
Configuring SSL for the Data Source on Oracle WebLogic Server
Configure an SSL Listener on Oracle Database
To configure the database with an SSL listener, you must specify the server's distinguished name (DN) and TCPS as the protocol in the client network configuration files to enable server DN matching and TCP/IP with SSL connections. Server DN matching prevents the database server from faking its identity to the client during connections by matching the server's global database name against the DN from the server certificate.
You must manually edit the client network configuration files, tnsnames.ora and listener.ora, to specify the server's DN and the TCP/IP with SSL protocol.
For details, see Section 6.6.3.1, "SSL-Enable Oracle Database."
See Also:
Configuring Secure Sockets Layer Authentication in the Oracle Database Advanced Security Administrator's Guide for more information about configuring SSL for the database listenerSSL-Enable the Data Source On Oracle WebLogic Server
6.5.2 Configuring SSL for Oracle SOA Suite
SSL configuration for Oracle SOA Suite varies with the type of connection being secured.
SSL features in Oracle WebLogic Server include:
-
How to set up SSL at the core server
-
How to enable SSL for a Web service
For these and related topics, see Oracle Fusion Middleware Securing Oracle WebLogic Server.
The following tasks are also needed to secure Oracle SOA Suite applications:
-
SSL-protecting SOA composites
-
Accessing SSL-protected Web services from within SOA composites
For these and related topics, see the Oracle Fusion Middleware Administrator's Guide for Oracle SOA Suite and Oracle Business Process Management Suite.
6.5.3 Configuring SSL for Oracle WebCenter
For information and details about how to implement SSL connections for Oracle WebCenter, see the following topics in the Oracle Fusion Middleware Administrator's Guide for Oracle WebCenter:
-
Securing the WebCenter Spaces Connection to Oracle Content Server with SSL
-
Securing the Browser Connection to WebCenter Spaces with SSL
6.5.4 Configuring SSL for Oracle Identity and Access Management
You can configure SSL for Oracle Identity and Access Management components residing on the middle tier:
6.5.4.1 Configuring SSL for Oracle Directory Integration Platform
You can configure Oracle Directory Integration Platform to use SSL for communications with connected directories. The Oracle Fusion Middleware Administrator's Guide for Oracle Directory Integration Platform provides details about the following SSL tasks for Oracle Directory Integration Platform:
-
Configuring Oracle Directory Integration Platform for SSL Mode 2 Server-Only Authentication
-
Managing the SSL Certificates of Oracle Internet Directory and Connected Directories
-
Bootstrapping in SSL Mode
-
Configuring the Third-Party Directory Connector for Synchronization in SSL Mode
-
Configuring and Testing Oracle Internet Directory with SSL Server-Side Authentication
-
Testing SSL Communication Between Oracle Internet Directory and Microsoft Active Directory
6.5.4.2 Configuring SSL for Oracle Identity Federation
See "Configuring SSL for Oracle Identity Federation" in the Oracle Fusion Middleware Administrator's Guide for Oracle Identity Federation for details.
6.5.4.3 Configuring SSL for Oracle Directory Services Manager
You can configure Oracle Directory Services Manager to use SSL for communications with connected directories. The Oracle Fusion Middleware Administrator's Guide for Oracle Virtual Directory provides details about the following SSL tasks for Oracle Directory Services Manager:
-
Logging into the Directory Server from Oracle Directory Services Manager Using SSL
-
Managing Oracle Directory Services Manager's Key Store
-
Storing Oracle Directory Services Manager's Certificate in Oracle Virtual Directory
6.5.5 SSL-Enable Oracle Reports, Forms, Discoverer, and Portal
This section contains these topics:
6.5.5.1 SSL for Oracle Reports
To SSL-enable Oracle Reports, you need to enable SSL on the components front-ending Oracle WebLogic Server.
For example, if you have an Oracle HTTP Server and an Oracle Web Cache front-ending the Oracle WebLogic Server that hosts Oracle Reports, you need to configure the following:
-
Inbound SSL for Oracle Web Cache
See Section 6.4.2.1, "Enable Inbound SSL for Oracle Web Cache Using Fusion Middleware Control."
-
Inbound SSL for Oracle HTTP Server
-
Inbound SSL for Oracle WebLogic Server
See Section 6.5.1.1, "Inbound SSL to Oracle WebLogic Server."
-
SSL between Oracle Web Cache and Oracle HTTP Server
See Section 6.4.2.3, "Enable Outbound SSL for Oracle Web Cache Using Fusion Middleware Control."
-
SSL between Oracle HTTP Server and Oracle WebLogic Server
See Section 6.4.3.3, "Enable SSL for Outbound Requests from Oracle HTTP Server."
Note:
These steps are necessary only if you wish to set up end-to-end SSL. In most cases, it is sufficient to enable SSL only on the first component getting the request, since the other components are usually within the intranet.For example, if the request is sent to Oracle Web Cache, you may only need to follow the first step. If the request is sent to Oracle HTTP Server, you may only need to follow the second step. Select the steps as dictated by your topology.
Additionally, Oracle Reports in Fusion Middleware Control accesses the reports servlet for data. If that communication needs to take place over SSL, you must complete the manual procedure described in Oracle Fusion Middleware Publishing Reports to the Web with Oracle Reports Services.
6.5.5.2 SSL for Oracle Forms
To SSL-enable Oracle Forms, you need to enable SSL on the components front-ending Oracle WebLogic Server.
For example, if you have an Oracle HTTP Server and an Oracle Web Cache front-ending the Oracle WebLogic Server that hosts Oracle Forms, you need to configure the following:
-
Inbound SSL for Oracle Web Cache
See Section 6.4.2.1, "Enable Inbound SSL for Oracle Web Cache Using Fusion Middleware Control."
-
Inbound SSL for Oracle HTTP Server
-
Inbound SSL for Oracle WebLogic Server
See Section 6.5.1.1, "Inbound SSL to Oracle WebLogic Server."
-
SSL between Oracle Web Cache and Oracle HTTP Server
See Section 6.4.2.3, "Enable Outbound SSL for Oracle Web Cache Using Fusion Middleware Control."
-
SSL between Oracle HTTP Server and Oracle WebLogic Server
See Section 6.4.3.3, "Enable SSL for Outbound Requests from Oracle HTTP Server."
Note:
These steps are necessary only if you wish to set up end-to-end SSL. In most cases, it is sufficient to enable SSL only on the first component getting the request, since the other components are usually within the intranet.For example, if the request is sent to Oracle Web Cache, you may only need to follow the first step. If the request is sent to Oracle HTTP Server, you may only need to follow the second step. Select the steps as dictated by your topology.
6.5.5.3 SSL for Oracle Discoverer
Running Oracle Discoverer over https requires installing a security certificate on the Discoverer Plus client machine, importing certificate details into the Java Plug-in certificate store, and related tasks.
The Oracle Fusion Middleware Configuration Guide for Oracle Business Intelligence Discoverer provides details about configuring SSL for Oracle Discoverer in these sections:
6.5.5.4 SSL for Oracle Portal
Oracle Portal uses a number of different components (such as the Parallel Page Engine, Oracle HTTP Server, and Oracle Web Cache) each of which may act as a client or server in HTTP communication. As a result, each component involving Oracle Portal in the middle tier is individually configured for https.
For details, see the Oracle Fusion Middleware Administrator's Guide for Oracle Portal.
6.5.6 Client-Side SSL for Applications
For information on how to write SSL-enabled applications, see "Using SSL Authentication in Java Clients" in Oracle Fusion Middleware Programming Security for Oracle WebLogic Server.
For best practices, refer to Section 6.8.2, "Best Practices for Application Developers."
6.6 Configuring SSL for the Data Tier
This section contains these topics:
6.6.1 Enabling SSL on Oracle Internet Directory Listeners
Out of the box, Oracle Internet Directory nodes are SSL-enabled in no-auth mode.
This section explains how to SSL-enable Oracle Internet Directory listeners using Fusion Middleware Control and the WLST command-line tool.
6.6.1.1 Enable Inbound SSL on an Oracle Internet Directory Listener Using Fusion Middleware Control
In this example, the following steps enable SSL in no-auth mode for an instance of Oracle Internet Directory using Fusion Middleware Control:
-
Select the Oracle Internet Directory instance in the navigation pane on the left.
-
Navigate to Oracle Internet Directory, then Administration, then Server Properties.
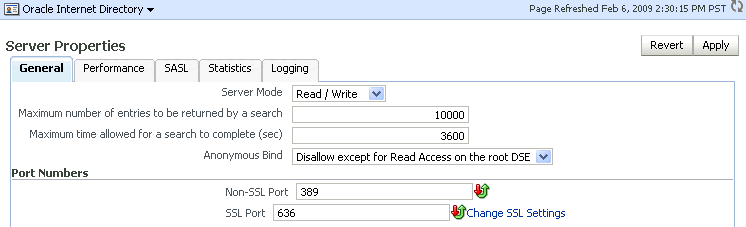
Description of the illustration oid2a.gif
-
Click Change SSL Settings.
-
On the SSL Settings dialog:
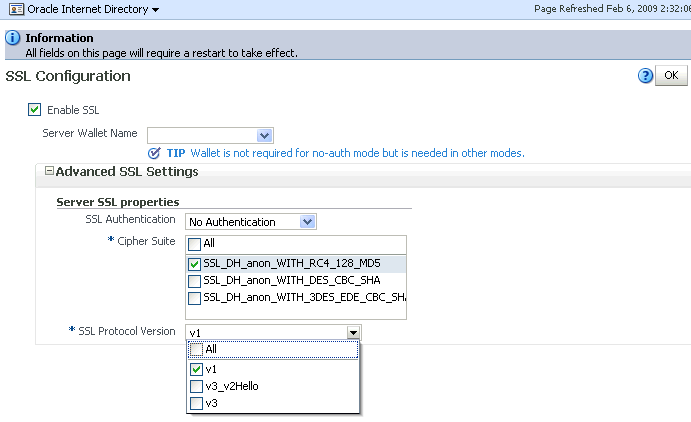
Description of the illustration oid3a.gif
-
Select Enable SSL.
-
Set SSL Authentication to No Authentication.
-
Set Cipher Suite to All.
-
Set SSL protocol version to v3.
-
Click OK.
-
-
Restart the Oracle Internet Directory instance by navigating to Oracle Internet Directory, then Control, then Restart.
-
To verify that the instance is correctly SSL-enabled, execute an
ldapbindcommand of the form:ldapbind -D cn=orcladmin -U 1 -h host -p SSL_port
Notes:
-U 1represents the no-auth mode.
SSL Enabling in Other Authentication Modes
The steps for SSL-enabling in other authentication modes are the same, except that in the SSL Settings dialog, you would set the appropriate authentication type.
Note:
Other authentication types need an Oracle wallet.6.6.1.2 Enabling Inbound SSL on an Oracle Internet Directory Listener Using WLST
Configure the listener with SSL properties in no-auth mode as follows:
Note:
The Oracle Internet Directory port name is alwayssslport1.
configureSSL('inst1',
'oid1',
'oid',
'sslport1')
Note:
SSL Enabling in Other Authentication Modes
You can do this by running the configureSSL command with a properties file as parameter and specifying an appropriate authentication type parameter value. For details, see the Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory.
6.6.1.3 Enabling Outbound SSL from Oracle Internet Directory to Oracle Database
Two sets of procedures are needed to configure SSL connections from Oracle Internet Directory to Oracle Database:
Configure SSL for the Database
The steps to configure Oracle Database for SSL are described in Section 6.6.3.1, "SSL-Enable Oracle Database."
Configure Outbound Oracle Internet Directory
Take these steps to configure SSL for outbound traffic from Oracle Internet Directory to Oracle Database:
-
Stop the Oracle Internet Directory server instances whose outbound traffic to the database is to be configured with SSL using this
opmnctlsyntax:$ORACLE_INSTANCE/bin/opmnctl stopproc ias-component=componentNameFor example:
$ORACLE_INSTANCE/bin/opmnctl stopproc ias-component=oid1
-
Configure Security Socket Layer authentication on the database to which the Oracle Internet Directory server instance is connecting.
For details, see Oracle Database Advanced Security Administrator's Guide.
-
Restart the database/listener as required.
-
Start Oracle Internet Directory server instances using this
opmnctlsyntax:$ORACLE_INSTANCE/bin/opmnctl startproc ias-component=componentNameFor example:
$ORACLE_INSTANCE/bin/opmnctl startproc ias-component=oid1
Note:
Only the no-authentication mode is supported.6.6.2 Enabling SSL on Oracle Virtual Directory Listeners
This section explains how to enable SSL for an instance of Oracle Virtual Directory.
The Oracle Fusion Middleware Administrator's Guide for Oracle Virtual Directory provides additional information on these topics:
6.6.2.1 Enable SSL for Oracle Virtual Directory Using Fusion Middleware Control
The steps to enable SSL are as follows (the example illustrates the server-auth mode):
-
Select the Oracle Virtual Directory instance in the navigation pane on the left.
-
Select a keystore to use for the operation by navigating to Oracle Virtual Directory, then Security, then Keystores
Choose from the list of keystores that appears. If you need to generate a new keystore, see Section 8.3.3.1, "Creating a Keystore Using Fusion Middleware Control" for details.
-
To SSL-enable the listener, navigate to Oracle Virtual Directory, then Administration, then Listeners.
-
Select the LDAP SSL Endpoint listener, and click Edit.
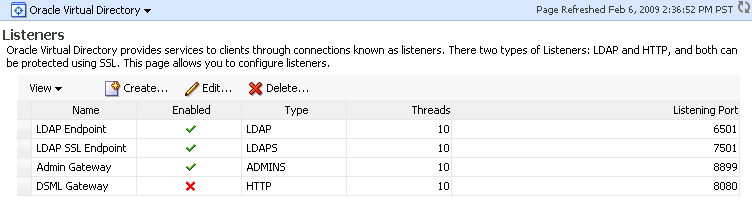
Description of the illustration ovd2a.gif
The Edit Listener page appears:
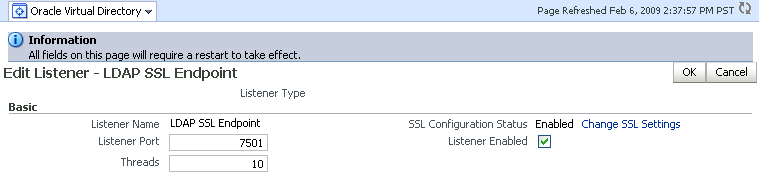
Description of the illustration ovd3a.gif
-
Click Change SSL Settings.
-
On the SSL Settings dialog:
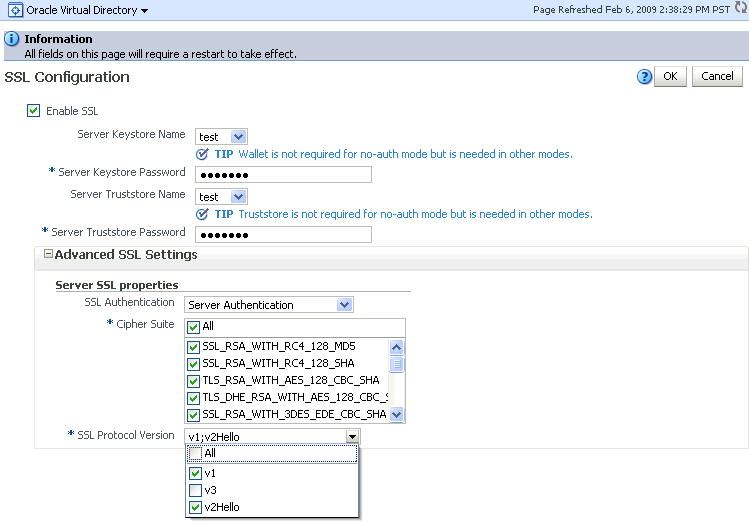
Description of the illustration ovd4a.gif
-
Select Enable SSL.
-
For Server Keystore Name, select the keystore you created in step 3, for example,
OVDtestJks. -
For Server Keystore Password, type the keystore password you specified in step 3.
-
For Server Truststore Name, select the keystore you created in step 3, for example,
OVDtestJks. -
For Server Truststore Password, type the keystore password you specified in step 3.
-
Expand Advanced SSL Settings.
-
For SSL authentication, select Server Authentication. This is the default setting.
-
For Cipher Suite, select the applicable cipher suite, in this example
All. -
Click OK.
-
-
Stop and start the Oracle Virtual Directory instance by navigating to Oracle Virtual Directory, then Control, then Stop and Start.
-
To verify that the instance is correctly SSL-enabled, execute an
ldapbindcommand of the form:ldapbind -D cn=orcladmin -U 2 -h host -p SSL_port -W "file:// DIRECTORY_SSL_WALLET"
Note:
-
-U 2represents the server-auth mode. -
DIRECTORY_SSL_WALLETis the path to a wallet file, not including the wallet file name. -
This wallet must contain the trusted certificate of the CA that issued the server certificate.
-
SSL Enabling in Other Authentication Modes
The steps for SSL-enabling in other authentication modes are similar, except that in the SSL Settings dialog, you would set the appropriate authentication type.
Note:
If configuring SSL for an LDAP listener, SSL communication is verified usingldapbind. If it is an http listener, it is verified using a browser.6.6.2.2 Enabling SSL on an Oracle Virtual Directory Listener Using WLST
Take these steps to configure the listener in server-auth mode:
-
Determine the listeners for this Oracle Virtual Directory instance by running the following command:
listListeners('inst1','ovd1' )This command lists all the listeners for this instance; select the one that needs to be configured for SSL. For this example, select LDAP SSL Endpoint.
-
Obtain the name of the SSL MBean for the Oracle Virtual Directory listener:
getSSLMBeanName('inst1', 'ovd1', 'ovd', 'LDAP SSL Endpoint')This command will return the SSL MBean name.
-
Set the passwords for the keystore and truststore in the MBean with the following commands:
cd ('SSL_MBean_Name') set('KeyStorePassword',java.lang.String('password').toCharArray()) set('TrustStorePassword',java.lang.String('password').toCharArray()) -
Configure the listener with SSL properties:
configureSSL('inst1', 'ovd1', 'ovd', 'LDAP SSL Endpoint')
Note:
Steps 2 and 3 are required only for server-auth and mutual-auth modes.Enabling SSL in Other Authentication Modes
You can do this by running the configureSSL command with a properties file as parameter and specifying appropriate authentication type parameter value. For details, see "Creating and Managing Oracle Virtual Directory Listeners" in the Oracle Fusion Middleware Administrator's Guide for Oracle Virtual Directory.
6.6.3 Configuring SSL for the Database
This section contains these topics:
6.6.3.1 SSL-Enable Oracle Database
Take these steps to SSL-enable Oracle database:
-
Create a root CA and a certificate for the DB. Here is an example:
Note:
Self-signed certificates are not recommended for production use. For information about obtain production wallets, see Section 8.4.8.3, "Changing a Self-Signed Wallet to a Third-Party Wallet.".mkdir root mkdir server # Create root wallet, add self-signed certificate and export orapki wallet create -wallet ./root -pwd password orapki wallet add -wallet ./root -dn CN=root_test,C=US -keysize 2048 -self_signed -validity 3650 -pwd password orapki wallet display -wallet ./root -pwd password orapki wallet export -wallet ./root -dn CN=root_test,C=US -cert ./root/b64certificate.txt -pwd password #Create server wallet, add self-signed certificate and export orapki wallet create -wallet ./server -pwd password orapki wallet add -wallet ./server -dn CN=server_test,C=US -keysize 2048 -pwd password orapki wallet display -wallet ./server -pwd password orapki wallet export -wallet ./server -dn CN=server_test,C=US -request ./server/creq.txt -pwd password # Import trusted certificates orapki cert create -wallet ./root -request ./server/creq.txt -cert ./server/cert.txt -validity 3650 -pwd password orapki cert display -cert ./server/cert.txt -complete orapki wallet add -wallet ./server -trusted_cert -cert ./root/b64certificate.txt -pwd password orapki wallet add -wallet ./server -user_cert -cert ./server/cert.txt -pwd password orapki wallet create -wallet ./server -auto_login -pwd password}}
-
Update
listener.ora,sqlnet.ora, andtnsnames.orafor the database.-
This example shows the default
listener.ora:SID_LIST_LISTENER = (SID_LIST =(SID_DESC =(SID_NAME = PLSExtProc)(ORACLE_HOME = /path_to_O_H)(PROGRAM = extproc))) LISTENER =(DESCRIPTION_LIST =(DESCRIPTION = (ADDRESS = (PROTOCOL = IPC)(KEY = EXTPROC1)) (ADDRESS = (PROTOCOL = TCP)(HOST = mynode.mycorp.com)(PORT = 1521)) (ADDRESS = (PROTOCOL = TCPS)(HOST = mynode.mycorp.com)(PORT = 2490)) )) WALLET_LOCATION=(SOURCE=(METHOD=FILE)(METHOD_DATA=(DIRECTORY=/wallet_location))) SSL_CLIENT_AUTHENTICATION=FALSE}}
And here is an updated
listener.orafile, illustrating a scenario with no client authentication:SID_LIST_LISTENER = (SID_LIST = (SID_DESC = (GLOBAL_DBNAME = dbname) (ORACLE_HOME = /path_to_O_H) (SID_NAME = sid) ) ) SSL_CLIENT_AUTHENTICATION = FALSE WALLET_LOCATION = (SOURCE = (METHOD = FILE) (METHOD_DATA = (DIRECTORY = /wallet_path) ) ) LISTENER = (DESCRIPTION_LIST = (DESCRIPTION = (ADDRESS = (PROTOCOL = IPC)(KEY = EXTPROC1521)) ) (DESCRIPTION = (ADDRESS = (PROTOCOL = TCP)(HOST = mynode.mycorp.com)(PORT = 1521)) ) (DESCRIPTION = (ADDRESS = (PROTOCOL = TCPS)(HOST = mycorp.com)(PORT = 2490)) ) )Note that the SSL port has been added.
-
Likewise, a modified
sqlnet.orafile may look like this:NAMES.DIRECTORY_PATH= (TNSNAMES, EZCONNECT) SQLNET.AUTHENTICATION_SERVICES=(BEQ,TCPS,NTS) WALLET_LOCATION=(SOURCE=(METHOD=FILE)(METHOD_DATA=(DIRECTORY=/directory))) SSL_CLIENT_AUTHENTICATION=FALSE
-
A modified
tnsnames.orafile may look like this:OID = (DESCRIPTION = (ADDRESS = (PROTOCOL = TCP)(HOST = mynode.mycorp.com)(PORT = 1521)) (CONNECT_DATA = (SERVER = DEDICATED) (SERVICE_NAME = mynode.mycorp.com) ) ) SSL = (DESCRIPTION = (ADDRESS_LIST = (ADDRESS = (PROTOCOL = TCPS)(HOST = mynode.mycorp.com)(PORT = 2490)) ) (CONNECT_DATA = (SERVICE_NAME = mynode.mycorp.com) ) (SECURITY=(SSL_SERVER_CERT_DN=\"CN=server_test,C=US\")) )
-
-
Test the connection to the database using the new connect string. For example:
$ tnsping ssl $ sqlplus username/password@ssl
See Also:
The chapter "Configuring Secure Sockets Layer Authentication" in the Oracle Database Advanced Security Administrator's Guide.6.6.3.2 SSL-Enable a Data Source
Take these steps to configure your data sources on Oracle WebLogic Server to use SSL.
-
Create a truststore and add the root certificate (which is created when SSL-enabling the database) as a trusted certificate to the truststore.
-
In the Oracle WebLogic Server Administration Console, navigate to the Connection pool tab of the data source that you are using.
Note:
The data source can be an existing source such as an Oracle WebCenter data source, or a new data source. See Creating a JDBC Data Source in Oracle Fusion Middleware Configuring and Managing JDBC for Oracle WebLogic Server for details.The properties you need to specify in the JDBC Properties text box depend on the type of authentication you wish to configure.
-
If you will require client authentication (two way authentication):
javax.net.ssl.keyStore=..(password of the keystore) javax.net.ssl.keyStoreType=JKS javax.net.ssl.keyStorePassword=...(password of the keystore) javax.net.ssl.trustStore=...(the truststore location on the disk) javax.net.ssl.trustStoreType=JKS javax.net.ssl.trustStorePassword=...(password of the truststore) -
If you will require no client authentication:
javax.net.ssl.trustStore=...(the truststore location on the disk) javax.net.ssl.trustStoreType=JKS javax.net.ssl.trustStorePassword=...(password of the truststore)
-
-
In the URL text box, enter the JDBC connect string. Ensure that the protocol is TCPS and that SSL_SERVER_CERT_DN contains the full DN of the database certificate. Use the following syntax:
jdbc:oracle:thin:@(DESCRIPTION=(ADDRESS_LIST=(ADDRESS=(PROTOCOL=TCPS)(HOST=host-name)(PORT=port-number)))(CONNECT_DATA=(SERVICE_NAME=service))(SECURITY=(SSL_SERVER_CERT_DN="CN=server_test,C=US")))
-
Test and verify the connection. Your data source is now configured to use SSL.
6.7 Advanced SSL Scenarios
This section explains how to handle additional SSL configuration scenarios beyond the basic topologies described earlier:
6.7.1 Hardware Security Modules and Accelerators
A Hardware Security Module (HSM) is a physical plug-in card or an external security device that can be attached to a computer to provide secure storage and use of sensitive content.
Note:
This discussion applies only to Oracle HTTP Server, Oracle Web Cache, and Oracle Internet Directory, which are the system components supporting HSM.Oracle Fusion Middleware supports PKCS#11-compliant HSM devices that provide a secure storage for private keys.
Take these steps to implement SSL for a component using a PKCS#11 wallet:
-
Install the HSM libraries on the machine where the component is running. This is a one-time task and is device-dependent.
-
Next, create a wallet using Oracle Wallet Manager (OWM) or the
orapkicommand-line tool. Note the following:-
Choose
PKCS11as the wallet type. -
Specify the device-specific PKCS#11 library used to communicate with the device. This library is part of the HSM software.
On Linux, the library is located at:
For LunaSA (Safenet): /usr/lunasa/lib/libCryptoki2.so For nCipher: /opt/nfast/toolkits/pkcs11/libcknfast.so
On Windows, the library is located at:
For LunaSA (Safenet): C:\Program Files\LunaSA\cryptoki.dll
-
-
Now follow the standard procedure for obtaining third-party certificates, that is, creating a certificate request, getting the request approved by a Certificate Authority (CA), and installing the certificate signed by that CA.
The wallet you set up is used like any other wallet.
-
Verify the wallet with the
orapkiutility. Use the following command syntax:orapki wallet p11_verify [-wallet [wallet]] [-pwd password] -
Configure SSL on your component listener using the
configureSSLWLST command, providing a properties file as input. Your properties file should specify the full path of the PKCS#11 wallet directory on the machine where the component is running. (Note: Do not save the PKCS#11 wallet in the instance home directory. Only wallets created and managed through Fusion Middleware Control or WLST should reside in the instance home.)A sample properties file could look like this:
SSLEnabled=true AuthenticationType=Server PKCS11Wallet=/tmp/lunasa/wallet
Note:
You must use the WLST commandconfigureSSL to configure the PKCS11 wallet. You cannot do this task using Fusion Middleware Control or any other tool.6.7.2 CRL Integration with SSL
Note:
-
This discussion applies only to Oracle HTTP Server and Oracle Web Cache.
-
CRL validation is managed through WLST; you cannot perform this task through Fusion Middleware Control.
Components that use SSL can optionally turn on certificate validation using a certificate revocation list (CRL). This allows them to validate the peer certificate in the SSL handshake and ensure that it is not on the list of revoked certificates issued by the Certificate Authority (CA).
This section describes how to configure a component to use CRL-based validation, and how to create and set up CRLs on the file system.
6.7.2.1 Configuring CRL Validation for a Component
Configure SSL on your component listener using the configureSSL WLST command, providing a properties file as input.
The properties file must be set up as follows:
-
The CertValidation attribute must be set to
url. -
The CertValidationPath attribute must be of the form
file://file_pathordir://directory_path.-
Use the first format if you are using a single CRL file for certificate validation. This CRL file should contain a concatenation of all CRLs.
-
Use the second format if you are specifying a directory path that contains multiple CRL files in hashed form.
See Section 6.7.2.2, "Manage CRLs on the File System" on how to create CRLs in hashed form.
-
In this example, the properties file specifies a single CRL file:
SSLEnabled=true AuthenticationType=Server CertValidation=crl KeyStore=ohs1 CertValidationPath=file:///tmp/file.crl
In this example, the properties file specifies a directory path to multiple CRL files:
SSLEnabled=true AuthenticationType=Server KeyStore=ohs1 CertValidation=crl CertValidationPath=dir:///tmp
6.7.2.2 Manage CRLs on the File System
Note:
LDAP-based CRLs or CRL distribution points are not supported.You use the orapki command-line tool to manage CRLs on the file system. For details on this topic, see Section H.2.5, "Managing Certificate Revocation Lists (CRLs) with orapki Utility."
If specifying a fleshiest directory, the CRL must be renamed. This enables CRLs to be loaded in an efficient manner at runtime. This operation creates a symbolic link to the actual CRL file. On Windows, the CRL is copied to a file with a new name.
To rename a CRL:
orapki crl hash [-crl [url|filename]] [-wallet wallet] [-symlink directory] [-copy directory] [-summary] [-pwd password]
For example:
orapki crl hash -crl nzcrl.txt -symlink wltdir -pwd password
If the CRL file name is specified at runtime, multiple CRLs can be concatenated in that file. The CRL created in this example is in Base64 format, and you can use a text editor to concatenate the CRLs.
Note:
CRL creation and Certificate Revocation are for test purposes and only used in conjunction with self-signed certificates. For production use, obtain production certificates from well-known CAs and obtain the CRLs from those authorities.To create a CRL:
orapki crl create
[-crl [url|filename]] [-wallet [cawallet]] [-nextupdate [days]] [-pwd password]
For example:
orapki crl create
-crl nzcrl.txt -wallet rootwlt -nextupdate 3650 -pwd password
Revoking a certificate adds the certificate's serial number to the CRL.
To revoke a certificate:
orapki crl revoke
[-crl [url|filename]] [-wallet [cawallet]] [-cert [revokecert]] [-pwd password]
For example:
orapki crl revoke
-crl nzcrl.txt -wallet rootwlt -cert cert.txt -pwd password
6.7.2.3 Test a Component Configured for CRL Validation
To test that a component is correctly configured for CRL validation, take these steps:
-
Set up a wallet with a certificate to be used in your component.
-
Generate a CRL with this certificate in the revoked certificates list. Follow the steps outlined in Section 6.7.2.2, "Manage CRLs on the File System."
-
Configure your component to use this CRL. Follow the steps outlined in Section 6.7.2.1, "Configuring CRL Validation for a Component."
-
The SSL handshake should fail when this revoked certificate is used.
6.7.3 Oracle Fusion Middleware FIPS 140-2 Settings
This section describes how to configure Oracle Fusion Middleware components to comply with the FIPS 140-2 advanced security standard. Topics include:
See Also:
For more information about this standard, refer to the Cryptographic Modules Validation Program Web site at:6.7.3.1 FIPS-Configurable Products
Any product using the Oracle SSL SDK can be configured to run in the FIPS mode. Specifically, you can configure the following Oracle Fusion Middleware components:
-
Oracle HTTP Server
-
Oracle Web Cache
-
Oracle Internet Directory
6.7.3.2 Setting the SSLFIPS_140 Parameter
You can configure these components to run in the FIPS mode by setting the SSLFIPS_140 parameter to TRUE in the fips.ora file:
SSLFIPS_140=TRUE
This file does not exist out-of-the-box and has to be created. Locate fips.ora either in the $ORACLE_HOME/ldap/admin directory, or in the directory pointed to by the FIPS_HOME environment variable.
The SSLFIPS_140 parameter is set to FALSE by default. You must set it to TRUE for FIPS mode operation.
6.7.3.3 Selecting Cipher Suites
A cipher suite is a set of authentication, encryption, and data integrity algorithms used for exchanging messages between network nodes. During an SSL handshake, for example, the two nodes negotiate to see which cipher suite they will use when transmitting messages back and forth.
Only the following cipher suites are approved for use in FIPS mode:
SSL_RSA_WITH_3DES_EDE_CBC_SHA SSL_DH_anon_WITH_3DES_EDE_CBC_SHA TLS_RSA_WITH_AES_128_CBC_SHA TLS_RSA_WITH_AES_256_CBC_SHA
Any other ciphers should not be used while running in FIPS mode.
You can configure one or more of these ciphers using comma-separated values. These should be specified in the SSL properties file for the key 'Ciphers' in the WLST configureSSL command.
See Section 6.9.28, "Properties Files for SSL" for details about specifying the SSL properties file with the configureSSL command.
6.7.3.4 Other Configuration Parameters
The minimum key size for enabling FIPS mode is 1024 bits. Ensure that the keys used in FIPS mode are at least 1024 bits.
You can only use wallets created using Oracle tools like SSLConfig, Oracle Wallet Manager, or orapki. Third-party PKCS#12 wallet files cannot be used in FIPS mode.
6.8 Best Practices for SSL
This section outlines some best practices for Oracle Fusion Middleware component administrators and application developers. It contains these topics:
6.8.1 Best Practices for Administrators
Best practices for system administrators include the following:
-
Use self-signed wallets only in test environment. You should obtain a CA signed certificate in the wallet before moving to production environment. For details, see Chapter 8, "Managing Keystores, Wallets, and Certificates."
-
It is recommended that components (at least in the Web tier) use certificates that have the system hostname or virtual host or site name as the DN. This allows browsers to connect in SSL mode without giving unsettling warning messages.
-
A minimum key size of 1024 bits is recommended for certificates used for SSL. Higher key size provides more security but at the cost of reduced performance. Pick an appropriate key size value depending on your security and performance requirements.
-
Lack of trust is one of the most common reasons for SSL handshake failures. Ensure that the client trusts the server (by importing the server CA certificate into the client keystore) before starting SSL handshake. If client authentication is also required, then the reverse should also be true.
6.8.2 Best Practices for Application Developers
The following practices are recommended:
-
Use Java Key Store (JKS) to store certificates for your Java EE applications.
-
Externalize SSL configuration parameters like keystore path, truststore path, and authentication type in a configuration file, rather than embedding these values in the application code. This allows you the flexibility to change SSL configuration without having to change the application itself.
6.9 WLST Reference for SSL
Starting with 11g Release 1 (11.1.1), WLST commands have been added to manage Oracle wallets and JKS keystores and to configure SSL for Oracle Fusion Middleware components.
Use the commands listed in Table 6-1,Table 6-2, and Table 6-3 for this task.
See Also:
Section 8.2, "Command-Line Interface for Keystores and Wallets" for important instructions on how to launch the WLST shell to run SSL-related commands. Do not launch the WLST interface from any other location.Note:
All WLST commands for SSL configuration must be run in online mode.You can obtain help for each command by issuing:
help('command_name')
Certain commands require parameters like instance name, ias-component and process type. You can obtain this information with the command:
$ORACLE_INSTANCE/bin/opmnctl status
Table 6-1 WLST Commands for SSL Configuration
| Use this command... | To... | Use with WLST... |
|---|---|---|
|
Set the SSL attributes for a component listener. |
Online |
|
|
Display the SSL attributes for a component listener. |
Online |
Table 6-2 WLST Commands for Oracle Wallet Management
| Use this command... | To... | Use with WLST... |
|---|---|---|
|
Generate a certificate signing request in an Oracle wallet. |
Online |
|
|
Add a self-signed certificate to an Oracle wallet. |
Online |
|
|
Change the password to an Oracle wallet. |
Online |
|
|
Create an Oracle wallet. |
Online |
|
|
Delete an Oracle wallet. |
Online |
|
|
Export an Oracle wallet to a file. |
Online |
|
|
Export an object (for example, a certificate) from an Oracle wallet to a file. |
Online |
|
|
Display a certificate or other object present in an Oracle wallet. |
Online |
|
|
Import an Oracle wallet from a file. |
Online |
|
|
Import a certificate or other object from a file to an Oracle wallet. |
Online |
|
|
List all objects (such as certificates) present in an Oracle wallet. |
Online |
|
|
List all Oracle wallets configured for a component instance. |
Online |
|
|
Remove a certificate or other object from a component instance's Oracle wallet. |
Online |
Table 6-3 WLST Commands for Java Keystore (JKS) Management
| Use this command... | To... | Use with WLST... |
|---|---|---|
|
Change the password to a JKS keystore. |
Online |
|
|
Create a JKS keystore. |
Online |
|
|
Delete a JKS keystore. |
Online |
|
|
Export a JKS keystore to a file. |
Online |
|
|
Export an object (for example, a certificate) from a JKS keystore to a file. |
Online |
|
|
Generate a keypair in a JKS keystore. |
Online |
|
|
Display a certificate or other object present in a JKS keystore. |
Online |
|
|
Import a JKS keystore from a file. |
Online |
|
|
Import a certificate or other object from a file to a JKS keystore. |
Online |
|
|
List all objects (for example, certificates) present in a JKS keystore. |
Online |
|
|
List all JKS keystores configured for a component instance. |
Online |
|
|
Remove a certificate or other object from a component instance's JKS keystore. |
Online |
Note:
WLST allows you to import certificates only in PEM format.6.9.1 addCertificateRequest
Online command that generates a certificate signing request in an Oracle wallet.
6.9.1.1 Description
This command generates a certificate signing request in Base64 encoded PKCS#10 format in an Oracle wallet for a component instance (Oracle HTTP Server, Oracle WebCache or Oracle Internet Directory). To get a certificate signed by a certificate authority (CA), send the certificate signing request to your CA.
6.9.1.2 Syntax
addCertificateRequest('instName', 'compName', 'compType', 'walletName', 'password', 'DN', 'keySize')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance. |
| compType | Specifies the type of component. Valid values are 'ohs', 'oid', and 'webcache'. |
| walletName | Specifies the name of the wallet file. |
| password | Specifies the password of the wallet. |
| DN | Specifies the Distinguished Name of the key pair entry. |
| keySize | Specifies the key size in bits. |
6.9.1.3 Example
The following command generates a certificate signing request with DN cn=www.acme.com and key size 1024 in wallet1, for Oracle Internet Directory instance oid1, in application server instance inst1:
wls:/mydomain/serverConfig> addCertificateRequest('inst1', 'oid1', 'oid','wallet1', 'password', 'cn=www.acme.com', '1024',)
6.9.2 addSelfSignedCertificate
Online command that adds a self-signed certificate.
6.9.2.1 Description
This command creates a key pair and wraps it in a self-signed certificate in an Oracle wallet for the specified component instance (Oracle HTTP Server, Oracle WebCache or Oracle Internet Directory). Only keys based on the RSA algorithm are generated.
6.9.2.2 Syntax
addSelfSignedCertificate('instName', 'compName', 'compType', 'walletName', 'password', 'DN', 'keySize')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance. |
| compType | Specifies the type of component. Valid values are 'ohs', 'oid', and 'webcache'. |
| walletName | Specifies the name of the wallet file. |
| password | Specifies the password of the wallet. |
| DN | Specifies the Distinguished Name of the key pair entry. |
| keySize | Specifies the key size in bits. |
6.9.2.3 Example
The following command adds a self-signed certificate with DN cn=www.acme.com, key size 1024 to wallet1, for Oracle Internet Directory instance oid1, in application server instance inst1:
wls:/mydomain/serverConfig> addSelfSignedCertificate('inst1', 'oid1', 'oid','wallet1', 'password', 'cn=www.acme.com', '1024')
6.9.3 changeKeyStorePassword
Online command that changes the keystore password.
6.9.3.1 Description
This command changes the password of a Java Keystore (JKS) file for an Oracle Virtual Directory instance.
6.9.3.2 Syntax
changeKeyStorePassword('instName', 'compName', 'compType', 'keystoreName', 'currPassword', 'newPassword')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance. |
| compType | Specifies the type of component. Valid value is 'ovd'. |
| keystoreName | Specifies the filename of the keystore. |
| currPassword | Specifies the current keystore password. |
| newPassword | Specifies the new keystore password. |
6.9.4 changeWalletPassword
Online command that changes the password of an Oracle wallet.
6.9.4.1 Description
This command changes the password of an Oracle wallet for the specified component instance (Oracle HTTP Server, Oracle WebCache or Oracle Internet Directory). This command is only applicable to password-protected wallets.
6.9.4.2 Syntax
changeWalletPassword('instName', 'compName', 'compType', 'walletName','currPassword', 'newPassword')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance. |
| compType | Specifies the type of component. Valid values are 'oid', 'ohs', and 'webcache'. |
| walletName | Specifies the filename of the wallet. |
| currPassword | Specifies the current wallet password. |
| newPassword | Specifies the new wallet password. |
6.9.5 configureSSL
Online command that sets SSL attributes.
6.9.5.1 Description
This command sets the SSL attributes for a component listener. The attributes are specified in a properties file format (name=value). If a properties file is not provided, or it does not contain any SSL attributes, default attribute values are used.
For details about the format of properties files, see Section 6.9.28, "Properties Files for SSL."
6.9.5.2 Syntax
configureSSL('instName', 'compName', 'compType', 'listener', 'filePath')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance. |
| compType | Specifies the type of component. Valid values are 'oid', 'ovd', ohs', and 'webcache'. |
| listener | Specifies the name of the component listener to be configured for SSL. |
| filePath | Specifies the absolute path of the properties file containing the SSL attributes to set. |
6.9.5.3 Examples
The following command configures SSL attributes specified in the properties file /tmp/ssl.properties for Oracle Virtual Directory instance ovd1 in application server instance inst1, for listener listener1:
wls:/mydomain/serverConfig> configureSSL('inst1', 'ovd1', 'ovd', 'listener1','/tmp/ssl.properties')
The following command configures SSL attributes without specifying a properties file. Since no file is provided, the default SSL attribute values are used:
wls:/mydomain/serverConfig> configureSSL('inst1', 'ovd1', 'ovd', 'listener2')
6.9.6 createKeyStore
Online command that creates a JKS keystore.
6.9.6.1 Description
This command creates a Java keystore (JKS) for the specified Oracle Virtual Directory instance. For keystore file location and other information, see Section 8.3.6.1, "Location of Keystores."
6.9.6.2 Syntax
createKeyStore('instName', 'compName', 'compType', 'keystoreName', 'password')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance. |
| compType | Specifies the type of component. Valid value is 'ovd'. |
| keystoreName | Specifies the filename of the keystore file to be created. |
| password | Specifies the keystore password. |
6.9.7 createWallet
Online command that creates an Oracle wallet.
6.9.7.1 Description
This command creates an Oracle wallet for the specified component instance (Oracle HTTP Server, Oracle WebCache or Oracle Internet Directory). Wallets can be of password-protected or auto-login type. For wallet details, see Chapter 8, "Managing Keystores, Wallets, and Certificates."
6.9.7.2 Syntax
createWallet('instName', 'compName', 'compType', 'walletName', 'password')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance. |
| compType | Specifies the type of component. Valid values are 'oid', 'ohs', and 'webcache'. |
| walletName | Specifies the name of the wallet file to be created. |
| password | Specifies the wallet password. |
6.9.7.3 Examples
The following command creates a wallet named wallet1 with password password, for Oracle HTTP Server instance ohs1 in application server instance inst1:
wls:/mydomain/serverConfig> createWallet('inst1', 'ohs1', 'ohs','wallet1', 'password')
The following command creates an auto-login wallet named wallet2 for Oracle WebCache instance wc1, in application server instance inst1:
wls:/mydomain/serverConfig> createWallet('inst1', 'wc1', 'webcache','wallet2', '')
6.9.8 deleteKeyStore
Online command that deletes a keystore.
6.9.8.1 Description
This command deletes a keystore for a specified Oracle Virtual Directory instance.
6.9.8.2 Syntax
deleteKeyStore('instName', 'compName', 'compType', 'keystoreName')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance. |
| compType | Specifies the type of component. Valid value is 'ovd'. |
| keystoreName | Specifies the name of the keystore file to delete. |
6.9.9 deleteWallet
Online command that deletes an Oracle wallet.
6.9.9.1 Description
This command deletes an Oracle wallet for the specified component instance (Oracle HTTP Server, Oracle WebCache or Oracle Internet Directory).
6.9.9.2 Syntax
deleteWallet('instName', 'compName', 'compType', 'walletName')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance. |
| compType | Specifies the type of component. Valid values are 'oid', 'ohs', and 'webcache'. |
| walletName | Specifies the name of the wallet file to be deleted. |
6.9.10 exportKeyStore
Online command that exports the keystore to a file.
6.9.10.1 Description
This command exports a keystore, configured for the specified Oracle Virtual Directory instance, to a file under the given directory. The exported filename is the same as the keystore name.
6.9.10.2 Syntax
exportKeyStore('instName', 'compName', 'compType', 'keystoreName', 'password', 'path')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance. |
| compType | Specifies the type of component. Valid value is 'ovd'. |
| keystoreName | Specifies the name of the keystore file. |
| password | Specifies the password of the keystore. |
| path | Specifies the absolute path of the directory under which the keystore is exported. |
6.9.11 exportKeyStoreObject
Online command that exports an object from a keystore to a file.
6.9.11.1 Description
This command exports a certificate signing request, certificate/certificate chain, or trusted certificate present in a Java keystore (JKS) to a file for the specified Oracle Virtual Directory instance. The certificate signing request is generated before exporting the object. The alias specifies the object to be exported.
6.9.11.2 Syntax
exportKeyStoreObject('instName', 'compName', 'compType', 'keystoreName', 'password', 'type', 'path', 'alias')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance. |
| compType | Specifies the type of component. Valid value is 'ovd'. |
| keystoreName | Specifies the name of the keystore file. |
| password | Specifies the password of the keystore. |
| type | Specifies the type of the keystore object to be exported. Valid values are 'CertificateRequest', 'Certificate', 'TrustedCertificate' and 'TrustedChain'. |
| path | Specifies the absolute path of the directory under which the object is exported as a file named base64.txt. |
| alias | Specifies the alias of the keystore object to be exported. |
6.9.11.3 Examples
The following command generates and exports a certificate signing request from the key-pair indicated by alias mykey in keys.jks, for Oracle Virtual Directory instance ovd1 in application server instance inst1. The certificate signing request is exported under the directory /tmp:
wls:/mydomain/serverConfig> exportKeyStoreObject('inst1', 'ovd1', 'ovd','keys.jks', 'password', 'CertificateRequest', '/tmp','mykey')
The following command exports a certificate or certificate chain indicated by alias mykey in keys.jks, for Oracle Virtual Directory instance ovd1, in application server instance inst1. The certificate or certificate chain is exported under the directory /tmp:
wls:/mydomain/serverConfig> exportKeyStoreObject('inst1', 'ovd1', 'ovd','keys.jks', 'password', 'Certificate', '/tmp','mykey')
The following command exports a trusted certificate indicated by alias mykey in keys.jks, for Oracle Virtual Directory instance ovd1, in application server instance inst1. The trusted certificate is exported under the directory /tmp:
wls:/mydomain/serverConfig> exportKeyStoreObject('inst1', 'ovd1', 'ovd','keys.jks', 'password', 'TrustedCertificate', '/tmp','mykey')
6.9.12 exportWallet
Online command that exports an Oracle wallet.
6.9.12.1 Description
This command exports an Oracle wallet, configured for a specified component instance (Oracle HTTP Server, Oracle WebCache or Oracle Internet Directory), to files under the given directory. If the exported file is an auto-login only wallet, the file name is cwallet.sso. If it is password-protected wallet, two files are created—ewallet.p12 and cwallet.sso.
6.9.12.2 Syntax
exportWallet('instName', 'compName', 'compType', 'walletName','password', 'path')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance. |
| compType | Specifies the type of component. Valid values are 'oid', 'ohs', and 'webcache'. |
| walletName | Specifies the name of the wallet file. |
| password | Specifies the password of the wallet. |
| path | Specifies the absolute path of the directory under which the object is exported. |
6.9.12.3 Examples
The following command exports auto-login wallet wallet1 for Oracle Internet Directory instance oid1 to file cwallet.sso under /tmp:
wls:/mydomain/serverConfig> exportWallet('inst1', 'oid1', 'oid', 'wallet1','','/tmp')
The following command exports password-protected wallet wallet2 for Oracle Internet Directory instance oid1 to two files, ewallet.p12 and cwallet.sso, under /tmp:
wls:/mydomain/serverConfig> exportWallet('inst1', 'oid1', 'oid', 'wallet2', 'password', '/tmp')
6.9.13 exportWalletObject
Online command that exports a certificate or other wallet object to a file.
6.9.13.1 Description
This command exports a certificate signing request, certificate, certificate chain or trusted certificate present in an Oracle wallet to a file for the specified component instance (Oracle HTTP Server, Oracle WebCache or Oracle Internet Directory). DN indicates the object to be exported.
6.9.13.2 Syntax
exportWalletObject('instName', 'compName', 'compType', 'walletName', 'password', 'type', 'path', 'DN')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance. |
| compType | Specifies the type of component. Valid values are 'ohs', 'oid', and 'webcache'. |
| walletName | Specifies the name of the wallet file. |
| password | Specifies the password of the wallet. |
| type | Specifies the type of wallet object to be exported. Valid values are 'CertificateRequest', 'Certificate', 'TrustedCertificate' or 'TrustedChain'. |
| path | Specifies the absolute path of the directory under which the object is exported as a file base64.txt. |
| DN | Specifies the Distinguished Name of the wallet object being exported. |
6.9.13.3 Examples
The following command exports a certificate signing request with DN cn=www.acme.com in wallet1, for Oracle Internet Directory instance oid1, in application server instance inst1. The certificate signing request is exported under the directory /tmp:
wls:/mydomain/serverConfig> exportWalletObject('inst1', 'oid1', 'oid','wallet1', 'password', 'CertificateRequest', '/tmp','cn=www.acme.com')
The following command exports a certificate with DN cn=www.acme.com in wallet1, for Oracle Internet Directory instance oid1, in application server instance inst1. The certificate or certificate chain is exported under the directory /tmp:
wls:/mydomain/serverConfig> exportWalletObject('inst1', 'oid1', 'oid','wallet1', 'password', 'Certificate', '/tmp','cn=www.acme.com')
The following command exports a trusted certificate with DN cn=www.acme.com in wallet1, for Oracle Internet Directory instance oid1, in application server instance inst1. The trusted certificate is exported under the directory /tmp:
wls:/mydomain/serverConfig> exportWalletObject('inst1', 'oid1', 'oid','wallet1', 'password', 'TrustedCertificate', '/tmp','cn=www.acme.com')
The following command exports a certificate chain with DN cn=www.acme.com in wallet1, for Oracle Internet Directory instance oid1, in application server instance inst1. The certificate or certificate chain is exported under the directory /tmp:
wls:/mydomain/serverConfig> exportWalletObject('inst1', 'oid1', 'oid','wallet1', 'password', 'TrustedChain', '/tmp','cn=www.acme.com')
6.9.14 generateKey
Online command that generates a key pair in a Java keystore.
6.9.14.1 Description
This command generates a key pair in a Java keystore (JKS) for Oracle Virtual Directory. It also wraps the key pair in a self-signed certificate. Only keys based on the RSA algorithm are generated.
6.9.14.2 Syntax
generateKey('instName', 'compName', 'compType', 'keystoreName', 'password', 'DN', 'keySize', 'alias', 'algorithm')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance. |
| compType | Specifies the type of component. Valid value is 'ovd'. |
| keystoreName | Specifies the name of the keystore. |
| password | Specifies the password of the keystore. |
| DN | Specifies the Distinguished Name of the key pair entry. |
| keySize | Specifies the key size in bits. |
| alias | Specifies the alias of the key pair entry in the keystore. |
| algorithm | Specifies the key algorithm. Valid value is 'RSA'. |
6.9.14.3 Examples
The following command generates a key pair with DN cn=www.acme.com, key size 1024, algorithm RSA and alias mykey in keys.jks, for Oracle Virtual Directory instance ovd1 in application server instance inst1:
wls:/mydomain/serverConfig> generateKey('inst1', 'ovd1', 'ovd','keys.jks', 'password', 'cn=www.acme.com', '1024', 'mykey', 'RSA')
The following command is the same as above, except it does not explicitly specify the key algorithm:
wls:/mydomain/serverConfig> generateKey('inst1', 'ovd1', 'ovd','keys.jks', 'password', 'cn=www.acme.com', '1024', 'mykey')
6.9.15 getKeyStoreObject
Online command that shows details about a keystore object.
6.9.15.1 Description
This command displays a specific certificate or trusted certificate present in a Java keystore (JKS) for Oracle Virtual Directory. The keystore object is indicated by its index number, as given by the listKeyStoreObjects command. It shows the certificate details including DN, key size, algorithm, and other information.
6.9.15.2 Syntax
getKeyStoreObject('instName', 'compName', 'compType', 'keystoreName', 'password', 'type', 'index')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance. |
| compType | Specifies the type of component. Valid value is 'ovd'. |
| keystoreName | Specifies the name of the keystore file. |
| password | Specifies the password of the keystore. |
| type | Specifies the type of the keystore object to be listed. Valid values are 'Certificate' and 'TrustedCertificate'. |
| index | Specifies the index number of the keystore object as returned by the listKeyStoreObjects command. |
6.9.15.3 Examples
The following command shows a trusted certificate with index 1 present in keys.jks, for Oracle Virtual Directory instance ovd1, in application server instance inst1:
wls:/mydomain/serverConfig> getKeyStoreObject('inst1', 'ovd1', 'ovd','keys.jks', 'password', 'TrustedCertificate', '1')
The following command shows a certificate with index 1 present in keys.jks, for Oracle Virtual Directory instance ovd1, in application server instance inst1:
wls:/mydomain/serverConfig> getKeyStoreObject('inst1', 'ovd1', 'ovd','keys.jks', 'password', 'Certificate', '1')
6.9.16 getSSL
Online command that lists the configured SSL attributes.
6.9.16.1 Description
This command lists the configured SSL attributes for the specified component listener. For Oracle Internet Directory, the listener name is always sslport1.
6.9.16.2 Syntax
getSSL('instName', 'compName', 'compType', 'listener')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance. |
| compType | Specifies the type of component. Valid values are 'ovd', 'oid', 'ohs', and 'webcache'. |
| listener | Specifies the name of the component listener. |
6.9.17 getWalletObject
Online command that displays information about a certificate or other object in an Oracle wallet.
6.9.17.1 Description
This command displays a specific certificate signing request, certificate or trusted certificate present in an Oracle wallet for the specified component instance (Oracle HTTP Server, Oracle WebCache or Oracle Internet Directory). The wallet object is indicated by its index number, as given by the listWalletObjects command. For certificates or trusted certificates, it shows the certificate details including DN, key size, algorithm and other data. For certificate signing requests, it shows the subject DN, key size and algorithm.
6.9.17.2 Syntax
getWalletObject('instName', 'compName', 'compType', 'walletName', 'password', 'type', 'index')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance. |
| compType | Specifies the type of component. Valid values are 'ohs', 'oid', and 'webcache'. |
| walletName | Specifies the name of the wallet file. |
| password | Specifies the password of the wallet. |
| type | Specifies the type of wallet object to be exported. Valid values are 'CertificateRequest', 'Certificate', and 'TrustedCertificate'. |
| index | Specifies the index number of the wallet object as returned by the listWalletObjects command. |
6.9.17.3 Examples
The following command shows certificate signing request details for the object with index 0 present in wallet1, for Oracle Internet Directory instance oid1, in application server instance inst1:
wls:/mydomain/serverConfig> getKeyStoreObject('inst1', 'oid1', 'oid','wallet1','password', 'CertificateRequest', '0')
The following command shows certificate details for the object with index 0 present in wallet1, for Oracle Internet Directory instance oid1, in application server instance inst1:
wls:/mydomain/serverConfig> getKeyStoreObject('inst1', 'oid1', 'oid','wallet1','password', 'Certificate', '0')
The following command shows trusted certificate details for the object with index 0, present in wallet1, for Oracle Internet Directory instance oid1, in application serverinstance inst1:
wls:/mydomain/serverConfig> getKeyStoreObject('inst1', 'oid1', 'oid','wallet1','password', 'TrustedCertificate', '0')
6.9.18 importKeyStore
Online command that imports a keystore from a file.
6.9.18.1 Description
This command imports a Java keystore (JKS) from a file to the specified Oracle Virtual Directory instance for manageability. The component instance name must be unique.
6.9.18.2 Syntax
importKeyStore('instName', 'compName', 'compType', 'keystoreName','password', 'filePath')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance. |
| compType | Specifies the type of component. Valid value is 'ovd'. |
| keystoreName | Specifies the name of the keystore being imported. This name must be unique for this component instance. |
| password | Specifies the password of the keystore. |
| filePath | Specifies the absolute path of the keystore file to be imported. |
6.9.18.3 Example
The following command imports the keystore /tmp/keys.jks as file.jks into Oracle Virtual Directory instance ovd1. Subsequently, the keystore is managed through the name file.jks:
wls:/mydomain/serverConfig> importKeyStore('inst1', 'ovd1', 'ovd', 'file.jks','password', '/tmp/keys.jks')
6.9.19 importKeyStoreObject
Online command that imports an object from a file to a keystore.
6.9.19.1 Description
This command imports a certificate, certificate chain, or trusted certificate into a Java keystore (JKS) for Oracle Virtual Directory, assigning it the specified alias which must be unique in the keystore. If a certificate or certificate chain is being imported, the alias must match that of the corresponding key-pair.
6.9.19.2 Syntax
importKeyStoreObject('instName', 'compName', 'compType', 'keystoreName', 'password', 'type', 'filePath', 'alias')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance. |
| compType | Specifies the type of component. Valid value is 'ovd'. |
| keystoreName | Specifies the name of the keystore. |
| password | Specifies the password of the keystore. |
| type | Specifies the type of the keystore object to be imported. Valid values are 'Certificate' and 'TrustedCertificate'. |
| filePath | Specifies the absolute path of the file containing the keystore object. |
| alias | Specifies the alias to assign to the keystore object to be imported. |
6.9.19.3 Examples
The following command imports a certificate or certificate chain from file cert.txt into keys.jks, using alias mykey for Oracle Virtual Directory instance ovd1, in application server instance inst1. The file keys.jks must already have an alias mykey for a key-pair whose public key matches that in the certificate being imported:
wls:/mydomain/serverConfig> > importKeyStoreObject('inst1', 'ovd1', 'ovd','keys.jks', 'password', 'Certificate','/tmp/cert.txt', 'mykey')
The following command imports a trusted certificate from file trust.txt into keys.jks using alias mykey1, for Oracle Virtual Directory instance ovd1 in application server instance inst1:
wls:/mydomain/serverConfig> importKeyStoreObject('inst1', 'ovd1', 'ovd','keys.jks', 'password', 'TrustedCertificate','/tmp/trust.txt', 'mykey1')
6.9.20 importWallet
Online command that imports an Oracle wallet from a file.
6.9.20.1 Description
This command imports an Oracle wallet from a file to the specified component instance (Oracle HTTP Server, Oracle WebCache, or Oracle Internet Directory) for manageability. If the wallet being imported is an auto-login wallet, the file path must point to cwallet.sso; if the wallet is password-protected, it must point to ewallet.p12. The wallet name must be unique for the component instance.
6.9.20.2 Syntax
importWallet('instName', 'compName', 'compType', 'walletName', 'password', 'filePath')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance. |
| compType | Specifies the type of component. Valid values are 'ohs', 'oid', and 'webcache'. |
| walletName | Specifies the name of the wallet being imported. The name must be unique for the component instance. |
| password | Specifies the password of the wallet. |
| filePath | Specifies the absolute path of the wallet file being imported. |
6.9.20.3 Examples
The following command imports the auto-login wallet file /tmp/cwallet.sso as wallet1 into Oracle Internet Directory instance oid1. Subsequently, the wallet is managed with the name wallet1. No password is passed since it is an auto-login wallet:
wls:/mydomain/serverConfig> importWallet('inst1', 'oid1', 'oid', 'wallet1', '', '/tmp/cwallet.sso')
The following command imports password-protected wallet /tmp/ewallet.p12 as wallet2 into Oracle Internet Directory instance oid1. Subsequently, the wallet is managed with the name wallet2. The wallet password is passed as a parameter:
wls:/mydomain/serverConfig> importWallet('inst1', 'oid1', 'oid', 'wallet2', 'password', '/tmp/ewallet.p12')
6.9.21 importWalletObject
Online command that imports a certificate or other object into an Oracle wallet.
6.9.21.1 Description
This command imports a certificate, trusted certificate or certificate chain into an Oracle wallet for the specified component instance (Oracle HTTP Server, Oracle WebCache component or Oracle Internet Directory). When importing a certificate, use the same wallet file from which the certificate signing request was generated.
6.9.21.2 Syntax
importWalletObject('instName', 'compName', 'compType', 'walletName', 'password', 'type', 'filePath')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance. |
| compType | Specifies the type of component. Valid values are 'ohs', 'oid', and 'webcache'. |
| walletName | Specifies the name of the wallet file. |
| password | Specifies the password of the wallet. |
| type | Specifies the type of wallet object to be imported. Valid values are 'Certificate', 'TrustedCertificate' and 'TrustedChain'. |
| filePath | Specifies the absolute path of the file containing the wallet object. |
6.9.21.3 Examples
The following command imports a certificate chain in PKCS#7 format from file chain.txt into wallet1, for Oracle Internet Directory instance oid1, in application server instance inst1:
wls:/mydomain/serverConfig> importWalletObject('inst1', 'oid1', 'oid','wallet1', 'password', 'TrustedChain','/tmp/chain.txt')
The following command imports a certificate from file cert.txt into wallet1, for Oracle Internet Directory instance oid1, in application server instance inst1:
wls:/mydomain/serverConfig> > importWalletObject('inst1', 'oid1', 'oid','wallet1', 'password', 'Certificate','/tmp/cert.txt')
The following command imports a trusted certificate from file trust.txt into wallet1, for Oracle Internet Directory instance oid1, in application server instance inst1:
wls:/mydomain/serverConfig> importWalletObject('inst1', 'oid1', 'oid','wallet1', 'password', 'TrustedCertificate','/tmp/trust.txt')
6.9.22 listKeyStoreObjects
Online command that lists the contents of a keystore.
6.9.22.1 Description
This command lists all the certificates or trusted certificates present in a Java keystore (JKS) for Oracle Virtual Directory.
6.9.22.2 Syntax
listKeyStoreObjects('instName', 'compName', 'compType', 'keystoreName','password', 'type')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance. |
| compType | Specifies the type of component. Valid value is 'ovd'. |
| keystoreName | Specifies the name of the keystore file. |
| password | Specifies the password of the keystore. |
| type | Specifies the type of keystore object to be listed. Valid values are 'Certificate' and 'TrustedCertificate'. |
6.9.22.3 Examples
The following command lists all trusted certificates present in keys.jks, for Oracle Virtual Directory instance ovd1, in application server instance inst1:
wls:/mydomain/serverConfig> listKeyStoreObjects('inst1', 'ovd1', 'ovd','keys.jks', 'password', 'TrustedCertificate')
The following command lists all certificates present in keys.jks, for Oracle Virtual Directory instance ovd1, in application server instance inst1:
wls:/mydomain/serverConfig> listKeyStoreObjects('inst1', 'ovd1', 'ovd','keys.jks', 'password', 'Certificate')
6.9.23 listKeyStores
Online command that lists all the keystores for a component.
6.9.23.1 Description
This command lists all the Java keystores (JKS) configured for the specified Oracle Virtual Directory instance.
6.9.23.2 Syntax
listKeyStores('instName', 'compName', 'compType')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance |
| compType | Specifies the type of component. Valid value is 'ovd'. |
6.9.24 listWalletObjects
Online command that lists all objects in an Oracle wallet.
6.9.24.1 Description
This command lists all certificate signing requests, certificates, or trusted certificates present in an Oracle wallet for the specified component instance (Oracle HTTP Server, Oracle WebCache or Oracle Internet Directory).
6.9.24.2 Syntax
listWalletObjects('instName', 'compName', 'compType', 'walletName', password', 'type')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance. |
| compType | Specifies the type of component. Valid values are 'ohs','oid', and 'webcache'. |
| walletName | Specifies the name of the wallet file. |
| password | Specifies the password of the wallet. |
| type | Specifies the type of wallet object to be listed. Valid values are 'CertificateRequest', 'Certificate', and 'TrustedCertificate'. |
6.9.24.3 Examples
The following command lists all certificate signing requests in wallet1, for Oracle Internet Directory instance oid1, in application server instance inst1:
wls:/mydomain/serverConfig> > listWalletObjects('inst1', 'oid1', 'oid','wallet1','password', 'CertificateRequest')
The following command lists all certificates in wallet1, for Oracle Internet Directory instance oid1, in application server instance inst1:
wls:/mydomain/serverConfig> listWalletObjects('inst1', 'oid1', 'oid','wallet1','password', 'Certificate')
The following command lists all trusted certificates in wallet1, for Oracle Internet Directory instance oid1, in application server instance inst1:
wls:/mydomain/serverConfig> listWalletObjects('inst1', 'oid1', 'oid','wallet1','password', 'TrustedCertificate')
6.9.25 listWallets
Online command that lists all wallets configured for a component instance.
6.9.25.1 Description
This command displays all the wallets configured for the specified component instance (Oracle HTTP Server, Oracle WebCache or Oracle Internet Directory), and identifies the auto-login wallets.
6.9.25.2 Syntax
listWallets('instName', 'compName', 'compType')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance |
| compType | Specifies the type of component. Valid values are 'ohs','oid', and 'webcache'. |
6.9.26 removeKeyStoreObject
Online command that removes an object from a keystore.
6.9.26.1 Description
This command removes a certificate request, certificate, trusted certificate, or all trusted certificates from a Java keystore (JKS) for Oracle Virtual Directory. Use an alias to remove a specific object; no alias is needed if all trusted certificates are being removed.
6.9.26.2 Syntax
removeKeyStoreObject('instName', 'compName', 'compType', 'keystoreName','password', 'type', 'alias')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance. |
| compType | Specifies the type of component. Valid value is 'ovd'. |
| keystoreName | Specifies the name of the keystore file. |
| password | Specifies the password of the keystore. |
| type | Specifies the type of the keystore object to be removed. Valid values are 'Certificate', 'TrustedCertificate' or 'TrustedAll'. |
| alias | Specifies the alias of the keystore object to be removed. |
6.9.26.3 Examples
The following command removes a certificate or certificate chain denoted by alias mykey in keys.jks, for Oracle Virtual Directory instance ovd1, in application server instance inst1:
wls:/mydomain/serverConfig> removeKeyStoreObject('inst1', 'ovd1', 'ovd','keys.jks', 'password', 'Certificate','mykey')
The following command removes a trusted certificate denoted by alias mykey in keys.jks, for Oracle Virtual Directory instance ovd1, in application server instance inst1:
wls:/mydomain/serverConfig> removeKeyStoreObject('inst1', 'ovd1', 'ovd','keys.jks', 'password', 'TrustedCertificate','mykey')
The following command removes all trusted certificates in keys.jks, for Oracle Virtual Directory instance ovd1, in application server instance inst1. Since no alias is required, the value None is passed for that parameter:
wls:/mydomain/serverConfig> removeKeyStoreObject('inst1', 'ovd1', 'ovd','keys.jks', 'password', 'TrustedAll',None)
6.9.27 removeWalletObject
Online command that removes a certificate or other object from an Oracle wallet.
6.9.27.1 Description
This command removes a certificate signing request, certificate, trusted certificate or all trusted certificates from an Oracle wallet for the specified component instance (Oracle HTTP Server, Oracle WebCache or Oracle Internet Directory). DN is used to indicate the object to be removed.
6.9.27.2 Syntax
removeWalletObject('instName', 'compName', 'compType', 'walletName', 'password', 'type', 'DN')
| Argument | Definition |
|---|---|
| instName | Specifies the name of the application server instance. |
| compName | Specifies the name of the component instance. |
| compType | Specifies the type of component. Valid values are 'ohs','oid', and 'webcache'. |
| walletName | Specifies the name of the wallet file. |
| password | Specifies the password of the wallet. |
| type | Specifies the type of the keystore object to be removed. Valid values are 'CertificateRequest', 'Certificate', 'TrustedCertificate' or 'TrustedAll'. |
| DN | Specifies the Distinguished Name of the wallet object to be removed. |
6.9.27.3 Examples
The following command removes all trusted certificates from wallet1, for Oracle Internet Directory instance oid1, in application server instance inst1. It is not necessary to provide a DN, so you pass null (denoted by None) for the DN parameter:
wls:/mydomain/serverConfig> removeWalletObject('inst1', 'oid1', 'oid','wallet1', 'password', 'TrustedAll',None)
The following command removes a certificate signing request indicated by DN cn=www.acme.com from wallet1, for Oracle Internet Directory instance oid1, in application server instance inst1:
wls:/mydomain/serverConfig> removeWalletObject('inst1', 'oid1', 'oid','wallet1', 'password', 'CertificateRequest','cn=www.acme.com')
The following command removes a certificate indicated by DN cn=www.acme.com from wallet1, for Oracle Internet Directory instance oid1, in application server instance inst1:
wls:/mydomain/serverConfig> removeWalletObject('inst1', 'oid1', 'oid','wallet1', 'password', 'Certificate','cn=www.acme.com')
The following command removes a trusted certificate indicated by DN cn=www.acme.com from wallet1, for Oracle Internet Directory instance oid1, in application server instance inst1:
wls:/mydomain/serverConfig> removeWalletObject('inst1', 'oid1', 'oid','wallet1', 'password', 'TrustedCertificate','cn=www.acme.com')
6.9.28 Properties Files for SSL
SSL configuration employs certain properties files for use with the WLST configureSSL command. The files contain parameters to specify the desired SSL configuration, such as authentication type, cipher values, and SSL version.
You can use descriptive names if you need to manage multiple properties files for different components. For example, you could have properties files named ohs-ssl-properties.prop or ovd-ssl-properties.prop.
6.9.28.1 Structure of Properties Files
All the SSL properties files have a consistent structure.
Table 6-4 provides details about the key-value structure and usage of these files.
Table 6-4 Parameters in Properties File
| Key | Mandatory? | Allowed Values for Oracle HTTP Server, Oracle Internet Directory, and Oracle Web Cache | Allowed Values for Oracle Virtual Directory | Usage |
|---|---|---|---|---|
|
SSLEnabled |
No |
true false |
true false |
Either value |
|
Ciphers |
No |
SSL_RSA_WITH_RC4_128_MD5 SSL_RSA_WITH_RC4_128_SHA SSL_RSA_WITH_3DES_EDE_CBC_SHA SSL_RSA_WITH_DES_CBC_SHA SSL_DH_anon_WITH_RC4_128_MD5 SSL_DH_anon_WITH_DES_CBC_SHA SSL_DH_anon_WITH_3DES_EDE_CBC_SHA TLS_RSA_WITH_AES_128_CBC_SHA TLS_RSA_WITH_AES_256_CBC_SHA |
One of more of the ciphers allowed by the JSSE provider. For the complete list of ciphers allowed by JDK 1.5, see Appendix A of the following guide: |
One or more comma separated values |
|
SSLVersions |
No |
nzos_Version_3_0 nzos_Version_3_0_With_2_0_Hello nzos_Version_1_0 |
TLSv1 SSLv2Hello (cannot be specified alone, must specify at least one other version) SSLv3 |
One or more comma separated values |
|
CertValidation |
No |
none crl |
N/A |
Either value |
|
CertValidation Path |
No |
file:// dir:// |
N/A |
Path of the CRL file, or directory containing CRL files |
|
KeyStore |
No |
Valid wallet name |
Valid keystore name |
|
|
TrustStore |
No |
N/A |
Valid truststore name |
|
|
AuthenticationType |
No |
None Server Optional Mutual |
None Server Optional Mutual |
Any one value |
Table 6-5 shows the default values:
Table 6-5 Default Values of Parameters
| Key | Default Value for Oracle HTTP Server | Default Value for Oracle Web Cache | Default Value for Oracle Internet Directory | Default Value for Oracle Virtual Directory |
|---|---|---|---|---|
|
SSLEnabled |
true |
true |
true |
true |
|
Ciphers |
null |
null |
null |
null |
|
SSLVersions |
null |
null |
null |
null |
|
CertValidation |
none |
none |
- |
- |
|
CertValidation Path |
null |
null |
- |
- |
|
KeyStore |
default |
default |
null |
keys.jks |
|
TrustStore |
- |
- |
- |
keys.jks |
|
Authentication Type |
Server |
Server |
none |
Server |
Note:
-
At least one
DH_anoncipher must be used in SSL no-auth mode. For all other modes, at least oneRSAcipher must be used. -
The value of the
KeyStoreparameter must be specified when configuring SSL in server-auth, mutual-auth, or optional client auth. -
If only
AESciphers have been specified, theSSLVersionsparameter must containTLSv1ornzos_Version_1_0. -
If you are doing CRL-based validation, the value of the
CertValidationparameter should becrland the value of theCertValidationPathparameter should point to the CRL file/directory.
6.9.28.2 Examples of Properties Files
Some examples demonstrating the use of the properties files follow.
Example 1: Basic Properties File
SSLEnabled=true AuthenticationType=None CertValidation=none
This properties file specifies no authentication mode, and default values will be used during SSL configuration for ciphers and SSL version. Keystore and truststore properties are not specified since the authentication type is None. For other authentication types, keystore must be specified.
Example 2: Basic Properties File
SSLEnabled= AuthenticationType=None CertValidation=none
This properties file is exactly the same as above, except that SSLEnabled is explicitly specified without any value. This is the same as not specifying the key at all. In both cases, the default value will be used.
Therefore, all the following three settings have the same meaning:
-
The setting:
SSLEnabled=true
Here the value
trueis explicitly specified. -
The setting:
SSLEnabled=
Since no value is mentioned here, the default value of
SSLEnabled(true) is used. -
The key
SSLEnabledis not present in the properties file.Since the key is not present, its default value (
true) is used.
Example 3: Properties File with Version for OHS
SSLEnabled=true AuthenticationType=Mutual SSLVersion=nzos_Version_3_0 CertValidation=crl CertValidationPath=file:///tmp/file.crl KeyStore=ohs1
This properties file has:
-
Default values for ciphers
-
Keystore
-
SSL version v3
-
CRL validation turned on
-
Mutual Authentication mode
Example 4: Properties File with Ciphers for Oracle Virtual Directory
AuthenticationType=Server Ciphers=SSL_RSA_WITH_RC4_128_MD5 SSLVersion=SSLv3,SSLv2Hello KeyStore=ovdidentity.jks TrustStore=ovdtrust.jks SSLEnabled=true
This properties file contains:
-
Specific cipher value
-
SSL Version
-
Server authentication mode