2 Getting Ready
At this point, the research and decisions you have made complete the Review System Requirements step in the following workflow and you can start to prepare your site and systems.
Figure 2-1 Process for Installing Enterprise Manager Ops Center
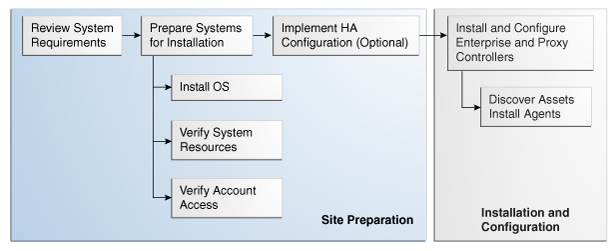
Description of "Figure 2-1 Process for Installing Enterprise Manager Ops Center"
The general procedure for preparation is summarized in this section and described in detail in the chapter:
-
Determine System Requirements
-
Determine how many Proxy Controllers your site requires.
-
Identify the servers to use for the Enterprise Controller and for the Proxy Controllers.
-
Determine which operating systems to install.
-
Determine which assets you will monitor and manage and, based on the total, determine your switch requirements.
-
-
Map Your Network
-
Determine the IP addressing scheme for the management, provisioning, and data networks.
-
Determine whether you will use a single-switch configuration or a two-switch configuration, in which the management network is isolated on one switch and the data and provisioning networks are on the second switch.
-
Determine the VLAN assignments.
-
Assign an IP address to the management port of each agent. For ILOM, ALOM, and SP-based agents, see the vendor documentation for information about assigning IP addresses to the server's management port.
-
-
Prepare the Systems
-
Install an operating system.
-
Verify system resources.
-
Verify resources needed for agent installation.
-
Verify accounts and access.
-
Preparing an Oracle Solaris System for Installation
The system that supports an Enterprise Controller or Proxy Controller requires an operating system that provides all of the resources that the Enterprise Manager Ops Center software requires.
The procedures in this topic describehow to verify that the required system resources exist. The requirements for agent installation and the procedures to verify required account access are also described.
Requirements for Installation on Oracle Solaris OS
The Enterprise Manager Ops Center software requires a full standard installation of the operating system, Oracle Solaris 10 11/06 for SPARC or x86 Systems. Install the OS using either of the following software groups:
-
SUNWCXall - Entire Distribution with OEM Support
-
SUNWCall - Entire Distribution
For information about installation procedures, see the Additional Resources.
Caution:
Do not minimize or harden the operating system until after you install the product software. For example, if you remove previously applied SUNWjass changes, the product software installation might fail.Disk and Swap Space
The Enterprise Manager Ops Center software requires the following minimum values for disk and swap space:
-
2 GB free in
/opt -
70 GB free in
/var/opt/sun/xvm -
6 GB of swap space
Oracle Solaris Patch Level
To support the product's update capability, a system running Oracle Solaris 10 11/06 or earlier must have these minimum patch levels for specific patches:
-
SPARC systems:
-
125100-04: Kernel Update Patch
-
120473-05: libc nss ldap PAM zfs Patch
-
125800-01: Fault Manager Patch
-
-
x86 systems:
-
125101-04: Kernel Update Patch
-
120037-15: libc nss ldap PAM zfs Patch
-
125801-01: Fault Manager Patch
-
Use the Oracle Solaris lscommand to verify that the /usr/lib/extendedFILE.so.1 exists on the system.
Preparing a Non-Global Zone
On servers that run Oracle Solaris 10, you can install the Enterprise Controller in a non-global zone, with the following constraints:
-
The non-global zone must be a whole root zone.
-
You cannot use a co-located Proxy Controller.
-
You cannot install a Proxy Controller or Agent software on the global zone that supports the Enterprise Controller's non-global zone.
-
Images stored on an NFS-mounted file system cannot be mounted on the Enterprise Controller. You must configure lofi devices as described in the following procedure. After configuring the devices, you can mount images that reside in the non-global zone.
Configuring the Non-Global Zone for the Enterprise Controller
-
Shut down the non-global zone.
root@globalzone# zlogin localzone shutdown -i5 -g0 -y
-
Use the
zonecfgcommand to enter zone configuration mode.root@globalzone# zonecfg -z localzone
-
Use the
add devicecommand to add the lofi devices.zonecfg:localzone> add device zonecfg:localzone:device> set match=/dev/lofictl zonecfg:localzone:device> end zonecfg:localzone> add device zonecfg:localzone:device> set match=/dev/lofi/* zonecfg:localzone:device> end zonecfg:localzone> add device zonecfg:localzone:device> set match=/dev/rlofi/* zonecfg:localzone:device> end zonecfg:localzone> exit
-
Boot the non-global zone.
root@globalzone# zoneadm -z localzone boot
-
Log in to the non-global zone.
root@globalzone# zlogin localzone [Connected to zone 'localzone' pts/2] Last login: Mon Sep 14 12:21:34 on pts/2 root@localzone#
-
Use the
lofiadma ndmountcommands to verify that you can create and mount lofi devices.root@localzone# lofiadm -a /root/sampleISO.iso /dev/lofi/1 root@localzone# mount -F hsfs /dev/lofi/1 /mnt root@localzone# ls /mnt textfile.txt example.bin sampledir/ root@localzone#
Verifying System Resources on Oracle Solaris
The Enterprise Manapter Ops Center provides the OC Doctor utility. This utility's pre-installation option checks requirements and identifies issues. If you prefer to check your systems manually, log in as the root user on the system on which you intend to install the Enterprise Controller or Proxy Controller software and use the information in this section. To keep track of your progress, use the checklist in Appendix A.
To Check the Operating System Release
The Enterprise Manager Ops Center software requires at least Oracle Solaris 10 11/06 for SPARC or x86 systems. To check the release, use the following command to display the /etc/release file:
# cat /etc/release Solaris 10 5/09 s10x_u7wos_08 X86 Copyright 2009 Sun Microsystems, Inc. All Rights Reserved. Use is subject to license terms. Assembled 30 March 2009
To Check the Installed Software Group
The Enterprise Manager Ops Center software requires that the Oracle Solaris OS was installed with one of these software groups:
-
SUNWCXall - Entire distribution with OEM support
-
SUNWCall - Entire distribution
To check the installed software group, use the following command to display the /var/sadm/system/admin/CLUSTER file:
# cat /var/sadm/system/admin/CLUSTER CLUSTER=SUNWCall
To Check the Zone Identity
The Enterprise Controller can be installed in a non-global zone or the global zone. Use the following command to check the current zone:
# zonename global
To Check the Available Disk Space
The Enterprise Manager Ops Center software requires 2 GB of space in/opt and 70 GB of space in /var/opt/sun/xvm. Use the following command to display the space utilization, and verify that you have at least 70 GB available within the file system that will hold the /var/opt/sun/xvm directory structure. In this example, the /opt and /var/opt/sun/xvm directories are located within the root (/) file system, which has 78 GB of space available.
# df -h Filesystem size used avail capacity Mounted on /dev/dsk/c1t0d0s0 82G 4.0G 78G 5% / /devices 0K 0K 0K 0% /devices ctfs 0K 0K 0K 0% /system/contract proc 0K 0K 0K 0% /proc mnttab 0K 0K 0K 0% /etc/mnttab swap 5.1G 624K 5.1G 1% /etc/svc/volatile (output omitted)
To Check Swap Space
An Enterprise Controller requires 6 GB of configured swap space and Proxy Controllers require at lease 4 GB of configured swap space. Use the following command to display the amount of configured swap space:
# swap -l swapfile dev swaplo blocks free /dev/dsk/c1t0d0s1 118,1 16 8395184 8395184
The values in the blocks and free columns are expressed in 512-byte blocks.
To Verify the Amount of System Memory
An Enterprise Controller requires at least 6 GB of installed memory and each Proxy Controller requires at least 4 GB. Use the following command to display the amount of installed memory on your system:
# prtconf | grep -i meg Memory size: 4096 Megabytes
To Verify the Amount of Shared Memory
An Enterprise Controller requires at least 500 MB of shared memory. Use the following command to display the amount of shared memory on your system:
# prctl -n project.max-shm-memory -i project 1 project: 1: user.root NAME PRIVILEGE VALUE FLAG ACTION RECIPIENT project.max-shm-memory privileged 1.97GB - deny - system 16.0EB max deny -
If the privileged value is less than 500 MB, use the following command to set it to 500 MB.
# projmod -a -K "project.max-shm-memory=(priv,500mb,deny)" default
To Verify the webservd User and Group
The Oracle Solaris 10 OS creates the webservd user and group. Use the following commands to search the /etc/passwd, /etc/shadow, and /etc/group files to confirm that the webservd user and group exist:
# grep webservd /etc/passwd webservd:x:80:80:WebServer Reserved UID:/: # grep webservd /etc/shadow webservd:*LK*::::::: # grep webservd /etc/group webservd::80:
If the webservd user or group does not exist, use the User ID (UID) and Group ID (GID) values in the example to create it.
To Verify an Alternate Administrative User
To designate a user other than root as the administrative user, you must create the user account before you install the product software. This example verifies that the user droot exists as an administrative user:
# logins -l droot droot 0 root 0 Super-User
Reviewing Users and Groups
Product installation creates users and groups on the Enterprise Controller and Proxy Controllers. Review the following list of users and groups, and verify that they do not conflict with existing policies. If required by account management policies, add these users and groups before you install the software.
-
Enterprise Controller Users:
svctag, allstart, scndb, scn, scncon, uce-sds, xvm -
Enterprise Controller Groups:
jet, scndb, uce-sds -
Proxy Controller Users:
svctag, allstart, uce-sds -
Proxy Controller Groups:
jet, uce-sds
The product software creates these users and groups with the following UID and GID values:
# cat /etc/group (output omitted) uce-sds::98194050: scndb::98194051: jet::98194052: # # cat /etc/passwd (output omitted) svctag:x:95:12:Service Tag UID:/: scn:x:231796:3::/:/bin/sh xvm:x:60:60::/:/bin/sh scncon:x:231798:1::/:/bin/true uce-sds:x:231799:98194050:UCE Engine:/opt/SUNWuce/server:/bin/sh scndb:x:231800:98194051:SCS PostgreSQL User:/opt/SUNWscs:/bin/sh allstart:x:231801:1:AllStart User:/var/opt/sun/xvm/osp/data:/bin/sh
All user accounts have locked (*LK*) passwords, except the scncon user. A password is required for the scncon user, but it has no login shell. To create the scncon user before installing the software, edit the /var/opt/sun/xvm/persistence/scn-satellite/satellite.properties file and add the password, in clear text, with the scncon.password parameter. For example:
scncon.password=2EzafaJE
To Verify the umask Value
Verify that the umask for the root user or equivalent role is set to 0022. Different shells report this value differently. The following examples list output from the umask command for the Bourne shell, the Korn shell, and the C-shell. In all three examples, the umask value is correct.
# sh # umask 0022 # ksh # umask 022 # csh # umask 22
To Verify the Locations of ssh Binaries
The binary files for ssh operations must be stored in their standard locations, even if OpenSSH is used. Verify that the following files have the following path names:
-
/usr/bin/scp -
/usr/bin/ssh -
/usr/bin/ssh-keygen -
/usr/bin/ssh-keyscan
To Verify IP Address Resolution
Verify that the configured naming services resolve the correct IP address for the host name that is assigned to Enterprise Controller's system. For example:
# host system.domain system.domain has address 192.21.26.1337
Verify that the /etc/hosts file contains the correct host name and IP address for the system. For example:
# grep system /etc/hosts 172.21.26.1337 system loghost
To Verify That /usr/local Is Writeable
Some software components of the product software are installed in the /usr/local directory. Verify that the directory is writeable, and is not a mounted remotely, or a read-only directory. For example:
# df -h /usr/local Filesystem size used avail capacity Mounted on /dev/dsk/c1t0d0s0 82G 4.0G 78G 5% / # ls -ld /usr/local drwxr-xr-x 7 root root 512 Feb 23 08:33 /usr/local
In this example, the directory is stored in the root (/) file system, and is writeable by the root user and group.
To Verify the Date and Time
Verify that the correct date and time are set on your system. For example:
# date Thu Aug 21 08:31:59 MST 2010
To Verify Online cryptosvc and gss Services
The product software requires the the cryptosvc and gss SMF services are online. For example:
# svcs cryptosvc gss STATE STIME FMRI online Feb_25 svc:/system/cryptosvc:default online Feb_25 svc:/network/rpc/gss:default
You can use the svcadm command to enable these services if they are not online.
To Remove the SMClintl Package
The SMClintl freeware package conflicts with the product software and must be removed. Use the following command to remove the SMClintl package before you install the software:
# pkgrm SMClintl
To Verify Network Access to Required Web Sites
Use a web browser to verify that your system can access the following URLs:
https://getupdates.oracle.comhttps://a248.e.akamai.nethttps://linux.oracle.comFor access to SUSE Linux updates, see http://support.novell.com/linux/registration/ to register your system and then verify you can get access to http://support.novell.com/patches.html.
Use the wget command to verify that you can download a sample file from the getupdates.oracle.com site.
-
If you use a proxy server to access the Internet, set the
https_proxyenvironment variable to point to the proxy server:# export https_proxy="http://myproxy.company.com:8080"
where myproxy.company.com is the fully-qualified domain name of your proxy server.
-
Download the sample file named
channels.xmland save it locally as/tmp/channels.xml. The following example of thewgetcommand show that the command is stored in/usr/sfw/binon Oracle Solaris systems and uses these options:-
-O - Specifies the name of the file to create on the local system
-
--http-user - Specifies the My Oracle Support account to use for authentication to
getupdates.oracle.com -
--http-password - Specifies the password for the My Oracle Support account
-
--proxy-user - (Optional) Specifies the user name used for authentication with an HTTPS proxy
-
--proxy-password - (Optional) Specifies the password for the user name that you provide for the --proxy-user option In this example, account@xyz.com and password represent the My Oracle Support credentials:
-
# /usr/sfw/bin/wget https://getupdates.oracle.com/channels3/channels.xml -O /tmp/channels.xml --http-user="account@xyz.com" --http-password="password" --11:43:41-- https://getupdates.oracle.com/channels3/channels.xml => `/tmp/channels.xml' Resolving getupdates.oracle.com... 198.232.168.136 Connecting to getupdates.oracle.com|198.232.168.136|:443... connected. HTTP request sent, awaiting response... 302 Moved Temporarily Location: https://a248.e.akamai.net/f/248/21808/15m/sun.download.akamai.com/21808/sc/channels3/channels.xml?AuthParam=1236019547_e9120d30e1ac62650c8f9284dfe47663&TUrl=L0QdUQV8Z4i0fdED3QTP3SJDWA8FMyaJsHfIWf4X29kTWQpKEzIbwqFuyRPZ&TicketId=3qfzk1SIPR9R&GroupName=SWUP&BHost=sdlc3h.sun.com&FilePath=/sc/channels3/channels.xml&File=channels.xml [following] --11:43:42-- https://a248.e.akamai.net/f/248/21808/15m/sun.download.akamai.com/21808/sc/channels3/channels.xml?AuthParam=1236019547_e9120d30e1ac62650c8f9284dfe47663&TUrl=L0QdUQV8Z4i0fdED3QTP3SJDWA8FMyaJsHfIWf4X29kTWQpKEzIbwqFuyRPZ&TicketId=3qfzk1SIPR9R&GroupName=SWUP&BHost=sdlc3h.sun.com&FilePath=/sc/channels3/channels.xml&File=channels.xml => `/tmp/channels.xml' Resolving a248.e.akamai.net... 208.51.221.73, 208.51.221.48 Connecting to a248.e.akamai.net|208.51.221.73|:443... connected. HTTP request sent, awaiting response... 200 OK Length: 66,505 (65K) [application/xml] 100%[============================================================================>] 66,505 397.16K/s 11:43:42 (396.55 KB/s) - `/tmp/channels.xml' saved [66505/66505]
To Verify Network Port Access
See Ports and Protocols to verify that your systems allow using the required network services and ports.
To Verify ssh Access for the root User
If you intend to use root credentials to discover systems and install the agent, verify that the ssh daemon on your target systems is configured to allow root user logins. If you use a non-root user for ssh access, this configuration is not necessary.
To verify ssh access for the root user, use ssh to log in as root to the system. If the attempt succeeds, no further action is necessary. If the attempt fails, check the value of the PermitRootLogin parameter in the /etc/ssh/sshd_config file. If PermitRootLogin is set to no, edit the file to change the etting to yes. Then use the svcadm command to restart the svc:/network/ssh:default service. For example:
# svcadm restart svc:/network/ssh:default
Preparing a System for Installation on Linux
The system that supports an Enterprise Controller or Proxy Controller requires an operating system that provides all of the resources that the Enterprise Manager Ops Center software requires.
The procedures in this topic describe how to verify that the required system resources exist. The requirements for agent installation and the procedures to verify required account access are also described.
Requirements for Linux OS Installation
Product installation requires a full installation of Oracle Linux. When you install the operating system, install all optional software components in every software category except the Language category. Set the SELinux security setting to Disabled
Disk and Swap Space
-
At least 70 GB of available disk space after the operating system has been installed
-
At least 6 GB of swap space
Values for kernel.shmall and kernel.shmmax
If the /etc/sysctl.conf file has been modified, the values of kernel.shmall and kernel.shmmax might be too small, which will cause the product installation to fail. The following values are recommended:
-
kernel.shmall: 268435456
-
kernel.shmmax: 4294967295
Edit Kernel Settings
When you install Linux, the Xen kernel is set as the default kernel. Setting the standard kernel as the default kernel improves performance. Perform the following procedure on each system that will the Enterprise Controller and Proxy Controllers.
-
Edit the
/boot/grub/menu.lstfile.# vi /boot/grub/menu.lst
-
Set the value of default to 1.
default=1
-
Save the file.
-
Shut down the system.
# shutdown -r now
The system now uses the standard kernel by default.
Verifying System Resources on Linux
The Enterprise Manapter Ops Center provides the OC Doctor utility. This utility's pre-installation option checks requirements and identifies issues. If you prefer to check your systems manually, log in as the root user on the system on which you intend to install the Enterprise Controller or Proxy Controller software and use the information in this section. To keep track of your progress, use the checklist in Appendix A.
To Check the Operating System Release
Verify that a release of the Linux OS that is compatible with product software is installed. To check the release, use the following command to display the /etc/redhat-release file:
# cat /etc/redhat-release
To Verify That Required Packages Are Installed
The product software requires specific packages for installation on Linux systems:
-
python-2.4.3
-
expect-5.43.0
-
perl-DBD-Pg
-
xinetd
-
tftp-server
-
dhcp
-
gettext
-
perl-XML-Parser
-
ncompress
-
libxml2 (both the 64 bit and 32 bit RPMs are required)
Use the following command to verify that package is installed:
# rpm -q dhcp-3.0.5-3.el5 dhcp-3.0.5-3.el5
To Check the Available Disk Space
The Enterprise Manager Ops Center software requires 2 GB of space in/opt and 70 GB of space in /var/opt/sun/xvm. Use the following command to display the space utilization, and verify that you have at least 70 GB available within the file system that will hold the /var/opt/sun/xvm directory structure. In this example, the /opt and /var/opt/sun/xvm directories are located within the root (/) file system, which has 119 GB of space available.
# df -h Filesystem Size Used Avail Use% Mounted on /dev/mapper/VolGroup00-LogVol00 131G 5.7G 119G 5% / /dev/sda1 99M 12M 83M 12% /boot tmpfs 2.0G 0 2.0G 0% /dev/shm
To Verify the Amount of System Memory and Swap Space
You must have at least 6 GB of installed memory and swap space for Enterprise Controller installations and at least 4 GB of installed memory and swap space for Proxy Controller installations. Use the following command to display the amount of installed memory and swap space:
# free -m total used free shared buffers cached Mem: 3931 1389 2542 0 220 1053 -/+ buffers/cache: 115 3816 Swap: 4096 0 4096
The value in the total column indicates the amount of installed memory or configured swap space.
You can also use the dmesg command to display the amount of memory installed. For example:
# dmesg | grep Memory Memory: 4022900k/4063168k available (2043k kernel code, 39036k reserved, 846k data, 232k init, 3145664k highmem)
To Verify the SELinux Setting
If you have installed a Security Enhanced Linux OS (SELinux), disable this capability. To check the state of SELinux, either run the sestatus command or display the contents of the /etc/selinux/config file to verify that the SELINUX variable is set to disabled. For example:
# sestatus SELinux status: disabled # # cat /etc/selinux/config # This file controls the state of SELinux on the system. # SELINUX= can take one of these three values: # enforcing - SELinux security policy is enforced. # permissive - SELinux prints warnings instead of enforcing. # disabled - SELinux is fully disabled. SELINUX=disabled # SELINUXTYPE= type of policy in use. Possible values are: # targeted - Only targeted network daemons are protected. # strict - Full SELinux protection. SELINUXTYPE=targeted
If the SELINUX state is either enforcing or permissive, edit the /etc/selinux/config file and change the SELINUX value to disabled. After making this change, reboot your system for the change to take effect.
Users and Groups
Product installation creates users and groups on the Enterprise Controller and Proxy Controllers. Review the following list of users and groups, and verify that they do not conflict with existing policies. If required by account management policies, add these users and groups before you install the software.
-
Enterprise Controller Users:
svctag, allstart, scndb, scn, scncon, uce-sds, xvm -
Enterprise Controller Groups:
jet, scndb, uce-sds -
Proxy Controller Users:
svctag, allstart, uce-sds -
Proxy Controller Groups:
jet, uce-sds
The product software creates these users and groups with the following UID and GID values:
# cat /etc/group (output omitted) uce-sds::98194050: scndb::98194051: jet::98194052: # # cat /etc/passwd (output omitted) svctag:x:95:12:Service Tag UID:/: scn:x:231796:3::/:/bin/sh xvm:x:60:60::/:/bin/sh scncon:x:231798:1::/:/bin/true uce-sds:x:231799:98194050:UCE Engine:/opt/SUNWuce/server:/bin/sh scndb:x:231800:98194051:SCS PostgreSQL User:/opt/SUNWscs:/bin/sh allstart:x:231801:1:AllStart User:/var/opt/sun/xvm/osp/data:/bin/sh
All user accounts have locked (*LK*) passwords, except the scncon user. A password is required for the scncon user, but it has no login shell. To create the scncon user before installing the software, edit the /var/opt/sun/xvm/persistence/scn-satellite/satellite.properties file and add the password, in clear text, with the scncon.password parameter. For example:
scncon.password=2EzafaJE
To Verify the umask Value
Verify that the umask in use for the root user or equivalent role is set to 022. Different shells report this value differently. The following examples list output from the umask command for the Bourne shell, the Korn shell, and the C Shell, and bash, in descending order. In all three examples, the umask value is correct.
# sh # umask 0022 # ksh # umask 0022 # csh # umask 22 # bash # umask 0022
Check the umask value set in /etc/bashrc. The umask value must be set to 022, even for non-root users. For example:
# grep umask /etc/bashrc umask 002 umask 022
To Verify the Locations of ssh Binaries
The binary files for ssh operations must be stored in their standard locations, even if OpenSSH is used. Verify that the following files have the following path names:
-
/usr/bin/scp -
/usr/bin/ssh -
/
usr/bin/ssh-keygen -
/usr/bin/ssh-keyscan
To Verify IP Address Resolution
Verify that the configured naming services resolve the correct IP address for the host name that is assigned to your system. For example:
# host x4200-brm-13 x4200-brm-13.Central.Sun.COM has address 192.20.25.169
To Verify That /usr/local Is Writeable
Some product components are installed in the /usr/local directory. Verify that the directory is writeable, and is not mounted remotely, or a read-only directory. For example:
# df -h /usr/local Filesystem Size Used Avail Use% Mounted on /dev/mapper/VolGroup00-LogVol00 131G 5.7G 119G 5% / # ls -ld /usr/local drwxr-xr-x 11 root root 4096 Nov 30 2005 /usr/local
In this example, the /usr/local directory is stored in the root (/) file system and is writeable by the root user and group.
To Verify the Date and Time
Verify that the correct date and time are set on your system. For example:
# date Thu Aug 21 08:31:59 MST 2010
If the date and time are not correct, reset them.
To Verify Network Access to Required Web Sites
Use a web browser to verify that your system can access the following URLs:
https://getupdates.oracle.comhttps://a248.e.akamai.nethttps://linux.oracle.comFor access to SUSE Linux updates, see http://support.novell.com/linux/registration/ to register your system and then verify you can get access to http://support.novell.com/patches.html.
Use the wget command to verify that you can download a sample file from the getupdates.oracle.com site.
-
If you use a proxy server to access the Internet, set the
https_proxyenvironment variable to point to the proxy server:# export https_proxy="http://myproxy.company.com:8080"
where myproxy.company.com is the fully-qualified domain name of your proxy server.
-
Download the sample file named
channels.xmland save it locally as/tmp/channels.xml. The following example of thewgetcommand show that the command is stored in/usr/sfw/binon Oracle Solaris systems and uses these options:-
-O - Specifies the name of the file to create on the local system
-
--http-user - Specifies the My Oracle Support account to use for authentication to getupdates.oracle.com
-
--http-password - Specifies the password for the My Oracle Support account
-
--proxy-user - (Optional) Specifies the user name used for authentication with an HTTPS proxy
-
--proxy-password - (Optional) Specifies the password for the user name that you provide for the --proxy-user option In this example, account@xyz.com and password represent the My Oracle Support credentials:
-
# /usr/sfw/bin/wget https://getupdates.oracle.com/channels3/channels.xml -O /tmp/channels.xml --http-user="account@xyz.com" --http-password="password" --11:43:41-- https://getupdates.oracle.com/channels3/channels.xml => `/tmp/channels.xml' Resolving getupdates.oracle.com... 198.232.168.136 Connecting to getupdates.oracle.com|198.232.168.136|:443... connected. HTTP request sent, awaiting response... 302 Moved Temporarily Location: https://a248.e.akamai.net/f/248/21808/15m/sun.download.akamai.com/21808/sc/channels3/channels.xml?AuthParam=1236019547_e9120d30e1ac62650c8f9284dfe47663&TUrl=L0QdUQV8Z4i0fdED3QTP3SJDWA8FMyaJsHfIWf4X29kTWQpKEzIbwqFuyRPZ&TicketId=3qfzk1SIPR9R&GroupName=SWUP&BHost=sdlc3h.sun.com&FilePath=/sc/channels3/channels.xml&File=channels.xml [following] --11:43:42-- https://a248.e.akamai.net/f/248/21808/15m/sun.download.akamai.com/21808/sc/channels3/channels.xml?AuthParam=1236019547_e9120d30e1ac62650c8f9284dfe47663&TUrl=L0QdUQV8Z4i0fdED3QTP3SJDWA8FMyaJsHfIWf4X29kTWQpKEzIbwqFuyRPZ&TicketId=3qfzk1SIPR9R&GroupName=SWUP&BHost=sdlc3h.sun.com&FilePath=/sc/channels3/channels.xml&File=channels.xml => `/tmp/channels.xml' Resolving a248.e.akamai.net... 208.51.221.73, 208.51.221.48 Connecting to a248.e.akamai.net|208.51.221.73|:443... connected. HTTP request sent, awaiting response... 200 OK Length: 66,505 (65K) [application/xml] 100%[============================================================================>] 66,505 397.16K/s 11:43:42 (396.55 KB/s) - `/tmp/channels.xml' saved [66505/66505]
To Verify Network Port Access
See Ports and Protocols to verify that your systems allow using the required network services and ports.
Verifying kernel.shmall and kernel.shmmax Values
If the /etc/sysctl.conf file has been modified, the values of kernel.shmall and kernel.shmmax might be too small. The following values are recommended:
-
kernel.shmall: 268435456
-
kernel.shmmax: 4294967295
-
Verify the values of kernel.shmall and kernel.shmmax.
# sysctl -a | grep shm vm.hugetlb_shm_group = 0 kernel.shmmni = 4096 kernel.shmall = 2097152 kernel.shmmax = 33554432 #
-
If the values for kernel.shmall and kernel.shmmax are lower than the recommended values , edit the file to set the variables equal to the recommended values.
# vi /etc/sysctl.conf kernel.shmmax = 4294967295 kernel.shmall = 268435456
-
Reboot the system.
Prepare the Agents
When Enterprise Manager Ops Center software manages an asset, it installs a small program so that the asset can respond to inquiries and commands from the Enterprise Controller or Proxy Controller. Regardless of the operating system supporting the Enterprise Controller, it can manage assets that use either Linux and Oracle Solaris systems.
Run the OC Doctor utility to check requirements and to identify potential issues on each system you intend to manage. The OC Doctor utility performs the following operations. If you prefer, you can perform the same tasks manually and keep track of your progress, using the checklist in Appendix A.
Oracle Solaris OS: To Verify Required Packages and Devices
Use the pkginfo command to verify that the following packages are installed on Oracle Solaris assets.
Table 2-1 Required Packages and Devices for Oracle Solaris Systems
| All Systems | Oracle Solaris 10 | Solaris 9 | Solaris 8 |
|---|---|---|---|
|
SUNWadmap SUNWbash SUNWctpls SUNWdtcor SUNWesu SUNWgzip SUNWlibC SUNWlibms SUNWloc SUNWmfrun SUNWswmt SUNWtoo SUNWxcu4 SUNWxwdv SUNWxwfnt SUNWxwice SUNWxwplt SUNWxwrtl SUNWzip SUNWzlib /dev/random /dev/urandom |
SUNWbzip SUNWcpp SUNWgcmn SUNWlibmsr SUNWlibpopt SUNWlxml SUNWperl584core SUNWperl584usr SUNWxwplr SUNWxwplr |
SUNWcpp SUNWgcmn SUNWlibpopt SUNWlmsx SUNWlxml SUNWpl5u SUNWpl5v SUNWzlibx |
SUNWlmsx SUNWnisr SUNWnisu SUNWtltk SUNWxildh SUNWxilow SUNWxilrl SUNWzlibx |
Linux OS: To Verify Required Packages
Use the rpm -q package command to verify that a specific package has been installed. Use the rpm -q file command to find the name of the package that installed a file.
Linux systems require the following utilities for agent installation:
coreutils
file
gettext
grep
tar
unzip
xinetd
Agent installation on Linux systems requires the 32-bit versions of the following packages:
To Verify ssh Installation
Although root ssh access is not required for agent installation, ssh must be available on systems on which you want to provision OS or firmware images.
-
Oracle Solaris OS: Use the
pkginfocommand to verify that the SUNWsshu package is installed:# pkginfo SUNWsshu system SUNWsshu SSH Client and utilities, (Usr)
-
Linux OS: Use the
rpmcommand to check for ssh installation. For example:# which ssh /usr/bin/ssh # rpm -qf /usr/bin/ssh openssh-clients-4.3p2-16.el5
To Verify Patches on Oracle Solaris 10 Systems With Non-Global Zones Installed
Oracle Solaris 10 systems that have non-global zones must have the following patches:
-
For SPARC systems:
-
124630-03 - System Administration Applications, Network, and Core
-
122660-07 - Zones patch, obsoleted by Solaris 10 8/07 kernel patch 120011-14
-
-
For x86 systems:
-
124631-03 - System Administration Applications, Network, and Core
-
122661-07 - Zones patch, obsoleted by Solaris 10 8/07 kernel patch 120012-14
-
Patches 122660-07 and 122661-07 are included on systems that are running at least Solaris 10 8/07. If the system is running an earlier version than Solaris 10 8/07, plan for the following tasks:
-
Take each system offline.
-
Install the patches in single-user mode.
-
Reboot the systems.
To Identify and Remove Duplicate Service Tags
The Enterprise Manager Ops Center software requires unique service tag uniform resource names (URNs) in each operating system instance that it manages. Service tag URNs are stored in the /var/sadm/servicetag/registry/servicetag.xml file. However, systems that have been installed using a flash archive (FLar) that contains this file have identical URNs.
-
On each system installed from a FLar file, use the following command to display the service tags that are stored in the /var/sadm/servicetag/registry/servicetag.xml file:
# stclient -x <?xml version="1.0" encoding="UTF-8"?> <registry urn="urn:st:4aa51776-9cea-e85b-ab14-aedd6ca93e49" version="1.0"> <service_tag> <instance_urn>urn:st:c76d9a11-f64b-418b-e9dc-a2fb18e7b76e</instance_urn> <product_name>Solaris 10 Operating System</product_name> <product_version>10</product_version> <product_urn>urn:uuid:5005588c-36f3-11d6-9cec-fc96f718e113</product_urn> <product_parent_urn>urn:uuid:596ffcfa-63d5-11d7-9886-ac816a682f92</product_parent_urn> <product_parent>Solaris Operating System</product_parent> <product_defined_inst_id/> <product_vendor>Sun Microsystems</product_vendor> <platform_arch>sparc</platform_arch> <timestamp>2009-01-09 22:23:42 GMT</timestamp> <container>global</container> <source>SUNWstosreg</source> <installer_uid>95</installer_uid> </service_tag> </registry> -
Compare the
instance_urnvalues on the systems and determine if duplicate URNs exist. If theinstance_urnvalue for the Oracle Solaris operating system matches theinstance_urnvalue from another system, you can remove the service tag registry and regenerate it to correct the problem. -
To remove the service tag registry:
# rm /var/sadm/servicetag/registry/servicetag.xml # ls /var/sadm/servicetag/registry/servicetag.xml /var/sadm/servicetag/registry/servicetag.xml: No such file or directory
-
Use the
svcadmcommand to restart the stosreg service, then verify that the/var/sadm/servicetag/registry/servicetag.xmlfile exists. For example:# svcadm restart stosreg # ls /var/sadm/servicetag/registry/servicetag.xml /var/sadm/servicetag/registry/servicetag.xml
-
Use the
stclient -xcommand to verify that the newinstance_urnvalues are unique. For example:# stclient -x <?xml version="1.0" encoding="UTF-8"?> <registry urn="urn:st:fdd576f6-b95c-63e6-ab54-f142ecca360f" version="1.1.4"> <service_tag> <instance_urn>urn:st:cbf9acfb-0c48-c248-fb07-9816382ceb29</instance_urn> <product_name>Solaris 10 Operating System</product_name> <product_version>10</product_version> <product_urn>urn:uuid:5005588c-36f3-11d6-9cec-fc96f718e113</product_urn> <product_parent_urn>urn:uuid:596ffcfa-63d5-11d7-9886-ac816a682f92</product_parent_urn> <product_parent>Solaris Operating System</product_parent> <product_defined_inst_id/> <product_vendor>Sun Microsystems</product_vendor> <platform_arch>sparc</platform_arch> <timestamp>2009-03-13 23:23:24 GMT</timestamp> <container>global</container> <source>SUNWstosreg</source> <installer_uid>95</installer_uid> </service_tag> </registry>
To prevent duplicate service tag entries in future provisioning , create flash archives without the /var/sadm/servicetag/registry/servicetag.xml file.
The flar and flarcreate commands both accept the -x and -X options, which enable you to specify files to exclude from flash archives. Use these options to exclude the /var/sadm/servicetag/registry/servicetag.xml file from the flash archive of the Oracle Solaris OS you will use to provision the Oracle Solaris OS. Refer to the flar(1M) and flarcreate(1M) man pages for more information about creating Oracle Solaris flash archives.
To Check for Agent Patch Dependencies
The product software installs the following patches as part of agent provisioning:
-
Solaris 8 SPARC: 110165-05, 110380-06,110934-26, 112097-08
-
Solaris 9 SPARC: 114014-17
-
Oracle Solaris 10 SPARC: 119042-09, 119254-63, 120900-04, 121133-02, 121901-02, 137321-01
-
Oracle Solaris 10 x86: 119043-09, 119255-63, 120901-03, 121334-04, 121902-02, 137322-01
For systems running Oracle Solaris 10 versions earlier than Oracle Solaris 10 6/06, agent provisioning installs the patchadd patch 119254-52 or 119255-52, which in turn requires patches 120900 and 120901 or 121133 and 121334 respectively. For each system that is running an Oracle Solaris 10 operating system earlier than Solaris 10 6/06, plan to install patches 120900 and 120901 or 121133 and 121334. These patches require a reboot to ensure proper installation.
The patches 119254-63 and 119255-63 correct issues with Oracle Solaris 10 single-user mode operations. Before you provision an agent, verify that no IDR patches have been installed previously to address single-user mode operations.
To Verify the umask Value
Verify that the umask for the root user or equivalent role is set to 0022. Different shells report this value differently. The following examples list output from the umask command for the Bourne shell, the Korn shell, and the C-shell, in descending order. In all three examples, the umask value is correct.
# sh # umask 0022 # ksh # umask 022 # csh <host_name># umask 22
Oracle Solaris OS: To Verify cryptosvc and gss Services
Use the svcs command to verify that the cryptosvc and gss services are enabled. For example:
# svcs cryptosvc gss STATE STIME FMRI online Mar_31 svc:/system/cryptosvc:default online Mar_31 svc:/network/rpc/gss:default
Verifying Account Access
Log into My Oracle Support or register for an account and log in.
To update SUSE Linux systems, you must have a Novell account. Verify that your Novell account allows access to software updates.
Configuring for High Availability
The High Availability configuration uses manual failover procedures to transfer product functions from the primary Enterprise Controller to the secondary Enterprise Controller. Depending on the nature of the failure, different or additional procedures might be required. The procedures follow these general steps:
-
Shut down the primary Enterprise Controller, if possible.
-
Prepare the secondary Enterprise Controller for failover.
-
Transfer the storage asset that holds the
/var/opt/sun/xvmdirectory structure from the primary Enterprise Controller to the secondary Enterprise Controller the -
Run the
harestoreprogram to configure the Enterprise Manager Ops Center software on the secondary Enterprise Controller. -
Reboot the secondary Enterprise Controller and start the Enterprise Manager Ops Center operations.
The harestore command configures the secondary Enterprise Controller to use the IP addresses of the primary Enterprise Controller. As you repair the primary Enterprise Controller, prevent it from accessing the networks where the secondary Enterprise Controller is operational.
Configuring Storage
The /var/opt/sun/xvm/osp/share/allstart directory is configured as an NFS share. If you use ZFS to provide the file system that mounts as /var/opt/sun/xvm, do not use the ZFS sharenfs command to share /var/opt/sun/xvm/osp/share/allstart so that the Enterprise Manager Ops Center software can use legacy NFS sharing tools to share the /var/opt/sun/xvm/osp/share/allstart directory.
Obtaining the Product Software
For more information about planning to use the Enterprise Manager Ops Center software, go to:
http://www.oracle.com/technetwork/oem/ops-center/index.html
From that page, you can follow links to the product documentation and to the software download site or you can go to the following page and scroll down to the Enterprise Manager section:
http://www.oracle.com/technetwork/indexes/downloads/index.html
The following documents guide you through installing the product software on Oracle Solaris and Linux systems: