1 Overview
Oracle Enterprise Manager Ops Center is a data center management solution for managing both hardware and software from one console. This document presents good practices for managing the security of Oracle Enterprise Manager Ops Center deployments.
Product Architecture
The Oracle Enterprise Manager Ops Center software has a distributed architecture with a single master controller (Enterprise Controller) and multiple slave controllers (Proxy Controllers). The Proxy Controllers are used for fan-out operations, to gain the benefits of scaling, and to support complex network topologies. Each Proxy Controller connects either to multiple Agent Controllers hosted on an Operating System instance or to managed systems or to both. Using the Internet, the Enterprise Controller can also connect to an Oracle Knowledge Base to download software for installation and to get access to dependent knowledge for installation software.
Knowledge Base (KB)
The Knowledge Base is the repository for metadata about Oracle Solaris and Linux OS components, which resides on Oracle's website. Enterprise Manager Ops Center can connect to the Knowledge Base through the Internet to obtain software updates.
Enterprise Controller
The Enterprise Controller is the central server for Enterprise Manager Ops Center and there is only one Enterprise Controller in each installation. The Enterprise Controller stores firmware and OS images, plans, profiles, and policies. It also stores the asset data and site customizations in a PostgreSQL database and hosts the web container for the user interface components. The Enterprise Controller handles all user authentication and authorization. All operations are initiated from the Enterprise Controller.
Proxy Controller
A Proxy Controller links the managed assets to the Enterprise Controller and acts for the Enterprise Controller in operations that must be located close to managed assets, such as OS provisioning. The Proxy Controller provides fan-out capabilities to minimize network load. It also contains the logic for agent-less monitoring and management of hardware.
Agent
An Agent is lightweight Java software that identifies each OS asset or OS instance and responds to requests from a Proxy Controller. Hardware management does not require an agent. The Agent receives the command, performs the required action, and reports results to the Proxy Controller. An agent never communicates directly with the Enterprise Controller.
General Principles of Security
This section describes the principles fundamental to using the software securely.
Keep Software Up To Date
Good security is maintained when all software versions and patches are up to date. This document discusses Enterprise Manager Ops Center version 11.1.1.0.0. As new versions or updates of Enterprise Manager Ops Center become available, install the new software as soon as possible.
Restrict Network Access
Firewalls restrict access to systems to a specific network route, which can be monitored and controlled. When firewalls are used in combination, they create a DMZ, a term for a subnetwork that controls access from an untrusted network to the trusted network. Using firewalls to create a DMZ provide two essential functions:
-
Blocks traffic types that are known to be illegal.
-
Contains any intrusion that attempts to take over processes or processors.
In your deployment, design an environment that locates the Enterprise Controller's system in a DMZ, that is, with a firewall between the system and the Internet and a firewall between the system and the corporate intranet.
Figure 1-1 Firewalls Restrict Access to Enterprise Controller
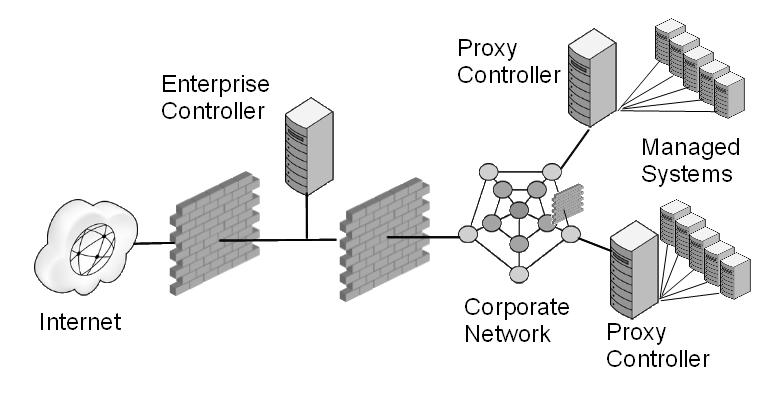
Description of "Figure 1-1 Firewalls Restrict Access to Enterprise Controller"
If your data center includes remote Proxy Controllers, use firewalls between the Enterprise Controller's system and the Proxy Controllers' systems.
To use Enterprise Manager Ops Center in Connected mode to get access to Oracle and third-party sites, use the information in Table 1-1 to configure the firewall between the Enterprise Controller and the Internet.
Table 1-1 IP Address and Ports for Third-Party Sites
| Site | IP Address | Port |
|---|---|---|
|
updates.oracle.com |
Port 443 |
|
|
aru-akam.oracle.com |
Port 80 |
|
|
aru-llnw.oracle.com |
Port 80 |
|
|
aru-llnw-dl.oracle.com |
Port 80 |
|
|
a248.e.akamai.net |
Port 443 |
|
|
inv-cs.sun.com |
192.18.110.18 |
Port 443 |
|
inventory.sun.com |
192.18.110.16 |
Port 443 |
|
getupdates.oracle.com |
Port 443 |
|
|
inv-cs.oracle.com |
192.18.110.10 |
Port 443 |
|
support.oracle.com |
141.146.54.16 |
Port 443 |
|
hs-ws1.oracle.com |
192.18.110.11 |
Port 443 |
|
www.oracle.com |
96.17.111.33 and 96.17.111.49 |
Port 80 |
Footnote 1 This site provides local IP addresses to optimize download speed. You must resolve the IP addresses locally, use that local address in your firewall rules, and ensure that the host always uses the local address to match your firewall rules. To accomplish these tasks, use nslookup to resolve the IP address, add the address to the /etc/hosts file, and open the firewall for the address.
To configure the firewall between the Enterprise Controller and a Proxy Controller or a corporate network, allow the ports and protocols in Table 1-2.
Table 1-2 Required Ports and Protocols
| Communication | Protocol and Port | Purpose |
|---|---|---|
|
Browser to Enterprise Controller |
HTTPS, TCP 9443 |
Web interface |
|
Browser to Enterprise Controller |
HTTP, TCP 80 |
Redirects to port 9443 |
|
Proxy Controller to Enterprise Controller |
HTTPS, TCP 443 |
Proxy Controller pushes asset data to Enterprise Controller. Proxy Controller pulls data for jobs, updates, agents, and OS images. |
|
Enterprise Controller to Proxy Controller |
SSH: Port 22 |
During Proxy Controller installation or updates performed through the UI. |
|
Java client to public APIs |
Transport Layer Security (TLS): Port 11172 |
JMX access from clients |
|
Proxy Controller to NFS server |
Port 2049 (default) See operating system documentation for configuring NFS |
Proxy Controller pulls provisioning images. |
|
Enterprise Controller |
Port 8005 |
Enterprise Controller in Disconnected mode |
Follow the Principle of Least Privilege
The principle of least privilege states that users are given the least amount of privilege to perform their jobs. Granting roles or privileges in access of a user's responsibilities leaves a system open for non-compliance. Review privileges periodically to determine whether they remain appropriate for each user's current job responsibilities.
You can assign different Enterprise Manager Ops Center roles to users to restrict access to specific features or managed assets. The following roles have been defined in Enterprise Manager Ops Center:
-
The Enterprise Controller Admin role grants root access. A user with the Enterprise Controller Admin role can perform asset discovery, perform administration actions on Oracle Enterprise Manager Ops Center, add new users, edit roles, and create new profiles, policies, and plans. When Oracle Enterprise Manager Ops Center is configured, the privileged user is given this role automatically. At least one user must have this role.
-
The All Assets Admin role can perform any action, including provisioning, updating, and managing, on any asset or group. When Oracle Enterprise Manager Ops Center is configured, the privileged user is given this role automatically.
Managed assets can be assigned to one or more groups. Groups can also be used with roles to restrict access to specific assets. An Enterprise Controller Admin can grant one or more of these roles to any user for any group:
-
Group Admin: A user with the Admin role for a group has unlimited access to assets within that group. They can take any action on the assets in the group, including installing agents, updating or provisioning operating systems, provisioning firmware, and managing and monitoring assets. However, they cannot edit or add assets to the group.
-
Group Provision: A user with the Provision role for a group can provision operating systems and firmware onto assets in the group. The user can use existing profiles, policies, and plans to perform provisioning, but cannot edit them or create new ones. Deployment plans that include update components can be used by a user with this role.
-
Group Update: A user with the Update role for a group can update operating systems in the group and run update reports. The user can use existing profiles, policies, and plans to perform the update, but cannot edit them or create new ones.
-
Group Update Sim: A user with the Update Sim role for a group can perform simulated Update jobs on operating systems and run update reports.
-
Group Manage: A user with the Manage role for a group can monitor assets, gain console access, and launch reports.
In addition, a user can be granted the Admin role for a specific deployment plan, operational plan, or profile. A user with the Admin role can edit, copy, and delete the plan or profile. A user can run the plan or profile on an asset without having the Admin role.
Caution:
A user with Provision and Admin permissions is able to apply an operational profile to a managed system using root access. Take care when assigning Provision or Admin roles because the role also allows the user to use an operational profile to run scripts.Monitor System Activity
Each Enterprise Manager Ops Center component has some auditing capability. Follow audit advice in this document and regularly monitor audit records.
Enterprise Manager Ops Center performs each action as a job. The details of a job show the order of operations in the job and the managed assets that were targets of the job. You can view the details of a job from either the browser or the command-line interface. Each job is stored until it is deleted explicitly.
In addition to the jobs record, log files can be a source of activity records. Logs are written during operations and can provide additional detail about system activity. Log files are protected by file permissions and therefore requires a privileged user to access them.
General Events
-
Messages:
/var/adm/messages* -
BUI:
/var/opt/sun/xvm/logs/emoc.log -
Actions of the BUI and remote clients on the Enterprise Controller:
-
On Oracle Solaris:
/var/cacao/instances/oem-ec/audits/ -
On Linux:
/var/opt/sun/cacao/instances/oem-ec/audits/
-
-
Events between controllers and agents:
-
On an Oracle Solaris Enterprise Controller:
/var/cacao/instances/oem-ec/logs -
On a Linux Enterprise Controller:
/var/opt/sun/cacao/instances/oem-ec/logs -
On each Oracle Solaris Proxy Controller:
/var/cacao/instances/scn-proxy/logs/cacao.n -
On each Linux Proxy Controller:
/var/opt/sun/cacao/instances/scn-proxy/logs/cacao.n
-
Software Updates
The Software Update component has its own server with its own logs. The following logs provide information on the activity for this server:
-
Audit Log
-
On Oracle Solaris:
/var/opt/SUNWuce/server/logs/audit.log -
On Linux:
/usr/local/uce/server/logs/audit.log
-
-
Errors
-
On Oracle Solaris:
/var/opt/SUNWuce/server/logs/error.log -
On Linux:
/usr/local/uce/server/logs/error.log -
Log of errors in download jobs:
/opt/SUNWuce/server/logs/SERVICE_CHANNEL/error.log
-
-
Job Log
-
On Oracle Solaris:
/var/opt/SUNWuce/server/logs/job.log -
On Linux:
/usr/local/uce/server/logs/job.log
-
Component -Specific
-
Agents:
/var/scn/update-agents/logsdirectory. -
Libraries:
/var/opt/sun/xvm/logs/virtimagelib.log -
Asset Database
-
On the Enterprise Controller:
-
Log of interactions with the database of assets:
/var/opt/sun/xvm/logs/db/mgmt/logs/db.log -
Log of events in collecting data for reports:
/var/opt/sun/xvm/logs/db/reports/logs/db.log
-
-
On the Proxy Controller:
/var/opt/sun/xvm/proxydb/* -
On each agent:
/var/opt/sun/xvm/agentdb/*
-