C Enterprise Topology with Oracle HTTP Server
This chapter describes an Oracle Identity Manager enterprise deployment on Exalogic with an external Oracle HTTP Server Web tier. It is one of the alternative topologies, discussed in Section 2.1.2, "Alternative Deployment Topologies."
This appendix contains the following topics:
-
Viewing the Oracle Identity Management Deployment Topology with Oracle HTTP Server on Exalogic
-
Understanding the Oracle Identity Manager with Oracle HTTP Server Topology Components
C.1 Viewing the Oracle Identity Management Deployment Topology with Oracle HTTP Server on Exalogic
In this alterntative Oracle Identity Manager topology on Exalogic topology, user requests are being routed by an Oracle HTTP Server Web tier, rather than the Oracle Traffic Director Web listeners.
Compare this topology with the one shown in Chapter 2, "Introduction and Planning.".
The Oracle HTTP Server topology shown here is similar to the one documented in the Oracle Fusion Middleware Enterprise Deployment Guide for Oracle Identity Management available in the Oracle Identity Management 11g Release 2 (11.1.2.1) documentation library, which is available on the Oracle Technology Network (OTN).
Figure C-1 Identity Management with Oracle HTTP Server and an Oracle RAC Database
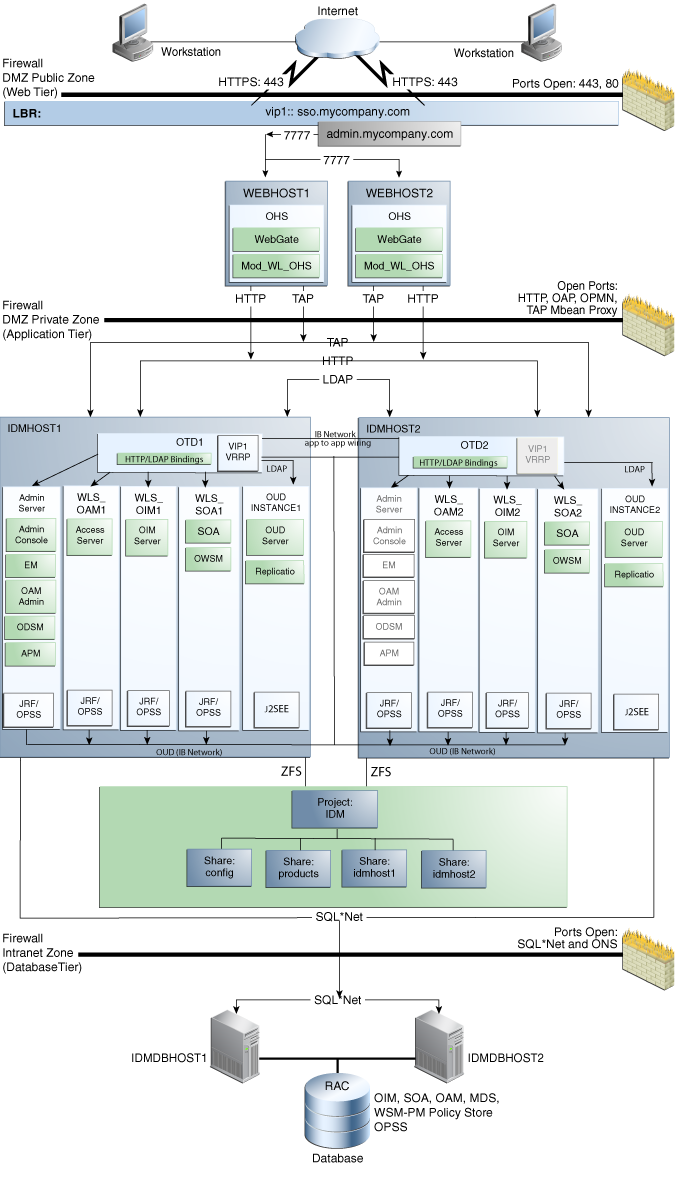
Description of "Figure C-1 Identity Management with Oracle HTTP Server and an Oracle RAC Database"
C.2 Understanding the Oracle Identity Manager with Oracle HTTP Server Topology Components
The components of the alternative Oracle Identity Manager with Oracle HTTP Server topology are identical to those described in Chapter 2, except for the following:
-
Section C.2.1, "About the Oracle HTTP Server Instances in the Web Tier"
-
Section C.2.2, "About the Oracle Traffic Director Instances on the Application Tier"
C.2.1 About the Oracle HTTP Server Instances in the Web Tier
The Web tier in the Oracle HTTP Server topology consists of two Oracle HTTP Server instances on separate WEHOST1 and WEBHOST2 host computers. These computers are outside of the Exalogic machine, and a firewall separates them from the application tier.
Most of the Identity Management components can function without the Web tier, but for most enterprise deployments, the Web tier is desirable.
In the Web tier:
-
WEBHOST1 and WEBHOST2 have Oracle HTTP Server, WebGate (an Access Manager component), and the
mod_wl_ohsplug-in module installed. Themod_wl_ohsplug-in module enables requests to be proxied from Oracle HTTP Server to a WebLogic Server running in the application tier. -
WebGate (an Oracle Access Management component) in Oracle HTTP Server uses Oracle Access Protocol (OAP) to communicate with Access Manager running on IDMHOST1 and IDMHOST2, in the Identity Management DMZ. WebGate and Access Manager are used to perform operations such as user authentication.
On the firewall protecting the Web tier, the HTTP ports are 443 (HTTP_SSL_PORT) for HTTPS and 80 (HTTP_PORT) for HTTP. Port 443 is open.
For information about configuring the Web tier for an IDM enterprise deployment, see "Installing and Configuring Oracle Web Tier for an Enterprise Deployment" in the Oracle Fusion Middleware Enterprise Deployment Guide for Oracle Identity Management
C.2.2 About the Oracle Traffic Director Instances on the Application Tier
Similar to the topology in Section 2.3, "Understanding the Topology Components," Oracle Traffic Director is used as a load balancer for internal communications within the Exalogic rack. By using Oracle Traffic Director rather than routing requests through the load balancer, you can utilise the internal IPoIB network which is both more secure and faster.
In this topology, the Oracle Traffic Director instances are in an active-passive configuration and the required virtual IP addresses used for internal communication (such as oudinternal.mycompany.com) are defined in the Oracle Traffic Director configuration.
For more information on configuring Oracle Traffic Director failover groups for active-passive mode, see "Creating Failover Groups" in the Oracle Traffic Director Administrator's Guide.