12 Installing and Configuring Oracle Traffic Director for an Enterprise Deployment
This chapter describes how to install and configure Oracle Traffic Director for an Exalogic enterprise deployment.
This chapter contains the following sections:
-
Section 12.2, "Installing Oracle Traffic Director on WEBHOST1 and WEBHOST2"
-
Section 12.3, "Creating and Starting the Traffic Director Administration Server"
-
Section 12.4, "Register WEBHOST2 with the Administration Node"
-
Section 12.6, "Starting, Stopping, and Restarting Oracle Traffic Director"
-
Section 12.9, "Enabling SSL Passthrough for sso.mycompany.com"
-
Section 12.10, "Workaround for Issues caused by TMPWATCH cleanup"
-
Section 12.11, "Deploying the Configuration and Testing the Virtual Server Addresses"
-
Section 12.12, "Creating a Failover Group for Virtual Hosts"
-
Section 12.13, "Backing Up the Oracle Traffic Director Configuration"
12.1 Overview of Installing and Configuring Oracle Traffic Director for an Enterprise Deployment
Oracle Traffic Director is a software load balancer for load balancing HTTP/S and TCP traffic to servers in the back-end. These back-end servers, which are referred to as origin servers within Oracle Traffic Director, can be application servers, web servers, or LDAP servers.
Installing and configuring Oracle Traffic Director for an enterprise deployment involves performing the steps shown in Table 12-1.
Table 12-1 Overview of Installing and Configuring Oracle Traffic Director for an Enterprise Deployment
| Task | Description | More Information |
|---|---|---|
|
Review Oracle Traffic Director prerequisites. |
For example, be sure that you have set up the required virtual IP addresses, that the user account has root permission on the storage appliance, and that you have already created the initial Oracle WebLogic Server domain for the Oracle Identity Management topology. |
"Prerequisites" in the Oracle Traffic Director Installation Guide |
|
Install the Oracle Traffic Director software. |
You install the software using the directories and mount points you created in Section 7.4.4, "Recommended Directory Locations." |
Section 12.2, "Installing Oracle Traffic Director on WEBHOST1 and WEBHOST2" |
|
Create and start an Oracle Traffic Director Administration Server. |
The Oracle Traffic Director administration server hosts the administration console and command-line interface, through which you can create Oracle Traffic Director configurations, deploy them as instances on administration nodes, and manage the instances. |
Section 12.3, "Creating and Starting the Traffic Director Administration Server" |
|
Verify the installation. |
Be sure that the installation was successful before you continue configuring the environment. |
"Verifying the Installation" in the Oracle Traffic Director Installation Guide |
|
Register WEBHOST2 as administration node. |
This ensures that Oracle Traffic Director is up and running on both WEBHOST1 and WEBHOST2. |
Section 12.4, "Register WEBHOST2 with the Administration Node" |
|
Create a configuration |
The configuration should route requests from the Oracle Traffic Director instances to the managed servers in the Oracle WebLogic Server domain. The configuration should also define the required origin-server pools to which requests should be routed. |
|
|
Start the Oracle Traffic Director instances |
Start the instances on WEBHOST1 and WEBHOST2, based on the configuration you created earlier in this procedure. |
Section 12.6, "Starting, Stopping, and Restarting Oracle Traffic Director" |
|
Define the virtual servers. |
Define the virtual servers required for accessing the various management tools and login screens for the topology. |
|
|
Create Routes |
Adding routes allows a virtual server to direct requests to different server pools depending on what is contained within the URI. |
|
|
Enable SSL Passthrough for sso.mycompany.com |
Perform extra configuration steps to ensure that any application redirects occur correctly. |
Section 12.9, "Enabling SSL Passthrough for sso.mycompany.com" |
|
Deploy and test the configuration. |
Deploy the configuration and test the virtual server URLs to be sure you have configured the Oracle Traffic Director instances successfully. |
Section 12.11, "Deploying the Configuration and Testing the Virtual Server Addresses" |
|
Create an active-passive failover group. |
Create a failover group to ensure that requests will continue to be served if WEBHOST1 or WEBHOST2 become unavailable. |
Section 12.12, "Creating a Failover Group for Virtual Hosts" |
12.2 Installing Oracle Traffic Director on WEBHOST1 and WEBHOST2
This section describes how to install Oracle Traffic Director software.
Note:
Be sure that you are not logged in as root user before installing or performing any action on Oracle Traffic Director.Note:
Be sure to verify you have obtained all required patches. For more info, see Section 3.7.4, "Applying Patches and Work-arounds."To install Oracle Traffic Director:
-
Extract the contents of the installer zip file to a directory on WEBHOST1.
-
Change directory to the
Disk1subdirectory in the directory in which you unzipped the installer. -
Run the following command:
./runInstaller
-
Follow the instructions on the screen to install the software.
When the Specify Installation Location screen appears, enter the value of the OTD_ORACLE_HOME variable in the Oracle Home Directory field.
The recommended directory location for the OTD_ORACLE_HOME is listed in Table 7-3, "Private Storage Directories"
If you need help with any of the other options on the installer screens, click Help, or refer to "Installing Oracle Traffic Director in Graphical Mode" in the Oracle Traffic Director Installation Guide.
-
Repeat steps 1 through 5 on WEBHOST2.
12.3 Creating and Starting the Traffic Director Administration Server
After you install Oracle Traffic Director on WEBHOST1 and WEBHOST2, you can then create an Oracle Traffic Director administration server.
For more information, see "Managing the Administration Server" in the Oracle Traffic Director Administrator's Guide
To create the Oracle Traffic Director administration server on WEBHOST1 run the tadm command from the OTD_ORACLE_HOME/bin directory, as follows:
-
On WEBHOST1 enter the following command:
OTD_ORACLE_HOME/bin/tadm configure-server --port=OTD_ADMIN_PORT \ --user=otdadmin --instance-home=OTD_ORACLE_INSTANCE --host=OTDADMINVHN --server-user=root
Where:
-
OTD_ORACLE_HOME the Oracle Home location you entered in the Oracle Traffic Director installer.
-
OTD_ORACLE_INSTANCE is the recommended value listed in Table 7-3, "Private Storage Directories".
-
OTDADMINVHNis the virtual host name to be used for the Oracle Traffic Director administration server and console.
For example:
OTD_ORACLE_HOME/web/bin/tadm configure-server --port=8800 --user=otdadmin \ --instance-home=/u02/private/oracle/config/otd1 --host=OTDADMINVHN.mycompany.comNote:
If you want to run Oracle Traffic Director as the root user, which is necessary if you want Oracle Traffic Director to work using ports <1024, you must add the following additional parameter to the command:--server-user=root
-
-
Enter the administrator password.
You will later use this password to log in to the Oracle Traffic Director administration console.
A prompt to re-enter the administrator password is displayed, as follows:
Please enter admin-user-password again>
-
Confirm the administrator password by entering it again.
An Administration Server instance of Oracle Traffic Director is created and deployed on the local host in a directory named
admin-serverwithin the OTD_ORACLE_INSTANCE directory that you specified in step 1. -
Start the Administration Server by running the following command on WEBHOST1:
WEB_INSTANCE_HOME/admin-server/bin/startservIf you want the server to run as
root, start it asroot. -
Log in to the Administration Server using the following URL:
https://OTDADMINVHN:8800
where 8800 is
OTD_ADMIN_PORT.Use the password provided above and verify that you can see the Oracle Traffic Director main page.
12.4 Register WEBHOST2 with the Administration Node
This section assumes you have installed Oracle Traffic Director, started the Administration Server, and verified the installation.
WEBHOST1 and WEBHOST2 have IP over InfiniBand (IPoIB) addresses. For example, 192.168.10.5 and 192.168.10.6.
You can now register WEBHOST2 with the Oracle Traffic Director Administration Server using the tadm command from the OTD_ORACLE_HOME/bin directory, as follows:
-
On the WEBHOST2, run the
configure-servercommand to register the host with the remote Administration Server as an administration node../tadm configure-server --user=otdadmin --port=OTD_ADMIN_PORT --host=OTDADMINVHN \ --admin-node --node-port=OTD_NODE_PORT --instance-home=OTD_ORACLE_INSTANCE --node-host=WEBHOST2 --server-user=root
Where:
-
OTD_ORACLE_HOME is the path to the Oracle Traffic Director Oracle home on WEBHOST2.
-
WEB_INSTANCE_HOME is the recommended directory path listed in Table 7-3, "Private Storage Directories"
-
node-hostis the name of the machine that this instance is running on (IAMHOST1, IAMHOST2, or WEBHOST2).
For example:
./tadm configure-server --user=otdadmin --port=8800 --host=OTDADMINVHN --admin-node \ --node-port=8900 --instance-home=/u02/private/oracle/config/instances/otd2 --node-host=WEBHOST2
Note:
If you want to run Oracle Traffic Director as the root user, which is necessary if you want Oracle Traffic Director to work using ports <1024, you must add the following additional parameter to the command:--server-user=root
For more information, see "configure-server" in the Oracle Traffic Director Command-Line Reference or use the
configure-server --helpcommand to see an explanation of the command line options.The following prompt appears after you run
configure-servercommand:This command creates an Administration Node and register it with the following remote Administration Server: https://WEBHOST1.mycompany.com Enter admin-user password>
-
-
Enter the admin-user password for the Oracle Traffic Director Administration Server.
The
configure-servercommand attempts to connect to the remote administration server by using the specified administration server host, port, user, and password. The Administration Server on WEBHOST1 must be up and running.If this is the first time that the host on which you are creating the administration node is attempting to connect to the administration server, the server certificate of the administration server is displayed.
-
Enter
yto trust the certificate.The following message is displayed:
OTD-70215 The administration node has been configured successfully.The node can be started by executing: OTD_ORACLE_INSTANCE/admin-server/bin/startserv -
Start the Oracle Traffic Director Server by running the following command on WEBHOST2:
WEB_INSTANCE_HOME/admin-server/bin/startservIf you want the server to run as
root, start it asroot.
After you start the administration node, you can create instances of Oracle Traffic Director configurations on the administration node. Note that on each administration node, you can create only one instance of a configuration.
12.5 Creating a Configuration
The next step in installing and configuring Oracle Traffic Director for an enterprise deployment is to create a configuration that will route requests to a server pool that consists of the managed servers in your Oracle WebLogic Server domain.
When creating a new configuration, you are required to provide the host and port information for the origin server, which in turn automatically creates (and names) an origin-server pool called origin-server-pool-1. This is the default origin-server pool and this pool can be found when you click the Server Pools option in the administration console. You cannot rename the default origin-server pool.
To create a configuration named IAM by using the administration console:
-
Log in to the OTD administration console using the URL specified in Section 20.2, "About Identity and Access Management Console URLs."
-
In the Common Tasks pane, click New Configuration.
The New Configuration wizard starts.
-
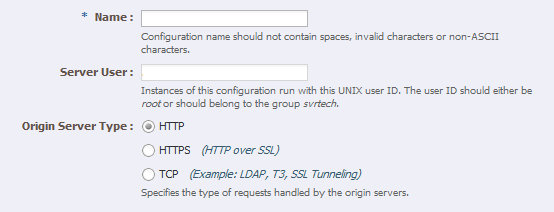
In the Step 1 Configuration Information screen, enter the following information:
-
Name:
sso.mycompany.com -
Server User:
oracle(orroot, if you want the server instances to run asroot). -
Origin Server Type: Make sure HTTP is selected.
Click Next.
-
-
On the Listener Information Screen set the port to a dummy port, for example: 6666. This port should not be the port that you want to eventually use, for example: 7777 (
WEB_HTTP_PORT). Setting this port to a dummy value is required so that the Oracle Traffic Director configuration does not interfere with the provisioning process. After provisioning the port will be updated to the correct value.Accept the other default values and click Next.
-
In the Step 3 Server Pool Information screen:
-
In the Origin Servers: Host: field, enter OAMHOST1
.mycompany.com, the port14100(OAM_PORT), and click Add Server. -
Enter OAMHOST2
.mycompany.comand port14100, click Add Server and click Next.
-
-
In the Step 4 Deployment Information screen, select the Administration Server and WEBHOST2 and click Next.
The Review screen appears.
-
Review the information and click Create Configuration.
The Results screen appears.
After the configuration is created, the Results screen of the New Configuration wizard displays a message confirming successful creation of the configuration. If you chose to create instances of the configuration, then a message confirming successful creation of the instances is also displayed.
-
Click Close on the Results screen.
In the New Configuration wizard, if you chose not to create an instance of the configuration, the message Undeployed Configuration is displayed, indicating that the configuration that you just created is yet to be deployed.
12.6 Starting, Stopping, and Restarting Oracle Traffic Director
To start and stop Oracle Traffic Director instances see Section 20.1.5, "Starting the Oracle Traffic Director Instances"
12.7 Defining the Required Oracle Traffic Director Virtual Servers for an Enterprise Deployment
Create and configure the virtual servers for the Oracle Traffic Director configuration. In this section you create the following Oracle Traffic Director virtual servers for your Oracle Identity and Access Management deployment. If External Oracle HTTP Servers are being used then several of these virtual servers should not be enabled on the Oracle Traffic Director.
Table 12-2 Defining Virtual Servers
| Virtual Server | Purpose | Creating the Virtual Server | Required with OHS |
|---|---|---|---|
|
sso.mycompany.com |
Acts as the access point for all HTTP traffic that gets directed to the single sign on services. |
This virtual server is created through administration console in Section 12.7.2, "Creating Virtual Servers.". |
No |
|
iadadmin.mycompany.com |
Acts as the access point for all internal HTTP traffic that gets directed to the administration services. |
This virtual server is created through administration console in Section 12.7.2, "Creating Virtual Servers.". |
No |
|
idstore.mycompany.com |
Acts as the access point for all Identity Store LDAP traffic. |
This virtual server is created through administration console in Section 12.7.2, "Creating Virtual Servers.". |
Yes |
|
idminternal.mycompany.com |
Acts as a load balancer, routing requests to SOA servers on IAMHOST1 and IAMHOST2. |
This virtual server is created when you configure the TCP Proxy for OUD in Section 12.7.3, "Creating a TCP Proxy and Listener for idstore.mycompany.com.". |
Yes |
|
igdadmin.mycompany.com |
Acts as the access point for all internal HTTP traffic that gets directed to the Administration services in the IAMGovernanceDomain |
The virtual server is created through the administration console in Section 12.7.2, "Creating Virtual Servers.". |
No |
To create and configure virtual servers using the administration console complete the steps in the following sections:
12.7.1 Creating an Origin-Server Pool
A server pool is a group of one or more virtualization hosts with the same processor architecture that have access to the same virtual and physical networks, and storage resources. Server pools provide load balancing, high availability capabilities, and sharing of some resources for all members of the pool.
In this section, create the Oracle Traffic Director origin-server pools listed in Table 12-5.
Table 12-3 Origin-Server Pools and Origin Servers for Physical Exalogic
| Origin-Server Pool | Origin Server Type | Origin Servers | Port |
|---|---|---|---|
|
iadadmin-pool |
HTTP |
IADADMINVHN.mycompany.com |
7001 ( |
|
igdadmin-pool |
HTTP |
IGDADMINVHN.mycompany.com |
7101 ( |
|
oud-pool |
TCP |
IAMHOST1.mycompany.com, IAMHOST2.mycompany.com |
1389 ( |
|
oim-pool |
HTTP |
OIMHOST1VHN.mycompany.com, OIMHOST2VHN.mycompany.com |
14000 ( |
|
origin-server-pool-1 |
HTTP |
IAMHOST1.mycompany.com, IAMHOST2.mycompany.com |
14100 ( |
|
soa-pool |
HTTP |
SOAHOST1VHN.mycompany.com, SOAHOST2VHN.mycompany.com |
8001 ( |
|
oaam-poolFoot 1 |
HTTP |
IAMHOST1.mycompany.com, IAMHOST2.mycompany.com |
14300 ( |
|
oaam-admin-pool |
HTTP |
IAMHOST1.mycompany.com, IAMHOST2.mycompany.com |
14200 ( |
Footnote 1 oaam-pool and oaam-admin-pool are only required if the topology includes OAAM.
Table 12-4 Origin-Server Pools and Origin Servers for External OHS Servers
| Origin-Server Pool | Origin Server Type | Origin Servers | Port |
|---|---|---|---|
|
iadadmin-pool |
HTTP |
IADADMINVHN.mycompany.com |
7001 ( |
|
igdadmin-pool |
HTTP |
IGDADMINVHN.mycompany.com |
7101 ( |
|
oud-pool |
TCP |
IAMHOST1EXT.mycompany.com, IAMHOST2EXT.mycompany.com |
1389 ( |
|
oim-pool |
HTTP |
OIMHOST1VHNEXT.mycompany.com, OIMHOST2VHNEXT.mycompany.com |
14000 ( |
|
origin-server-pool-1 |
HTTP |
IAMHOST1EXT.mycompany.com, IAMHOST2EXT.mycompany.com |
14100 ( |
|
soa-pool |
HTTP |
SOAHOST1VHN.mycompany.com, SOAHOST2VHN.mycompany.com |
8001 ( |
|
oaam-poolFoot 1 |
HTTP |
IAMHOST1EXT.mycompany.com, IAMHOST2EXT.mycompany.com |
14300 ( |
|
oaam-admin-pool |
HTTP |
IAMHOST1EXT.mycompany.com, IAMHOST2EXT.mycompany.com |
14200 ( |
Footnote 1 oaam-pool and oaam-admin-pool are only required if the topology includes OAAM.
Table 12-5 Origin-Server Pools and Origin Servers for Virtual Exalogic
| Origin-Server Pool | Origin Server Type | Origin Servers | Port |
|---|---|---|---|
|
iadadmin-pool |
HTTP |
IADADMINVHN.mycompany.com |
7001 ( |
|
igdadmin -pool |
HTTP |
IGDADMINVHN.mycompany.com |
7101 ( |
|
oud-pool |
TCP |
OAMHOST1.mycompany.com, OAMHOST2.mycompany.com |
1389 ( |
|
oim-pool |
HTTP |
OIMHOST1VHN.mycompany.com, OIMHOST2VHN.mycompany.com |
14000 ( |
|
origin-server-pool-1 |
HTTP |
OAMHOST1.mycompany.com, OAMHOST2.mycompany.com |
14100 ( |
|
soa-pool |
HTTP |
SOAHOST1VHN.mycompany.com, SOAHOST2VHN.mycompany.com |
8001 ( |
|
oaam-poolFoot 1 |
HTTP |
OAMHOST1.mycompany.com, OAMHOST2.mycompany.com |
14300 ( |
|
oaam-admin-pool |
HTTP |
OAMHOST1.mycompany.com, OAMHOST2.mycompany.com |
14200 ( |
Footnote 1 oaam-pool and oaam-admin-pool are only required if the topology includes OAAM.
Note:
Theoim-server-pool-1 is created automatically for you when you created the configuration.To create an origin-server pool:
-
Log in to the Administration Console using the following URL:
https://OTDADMINVHN:OTD_ADMIN_PORTwhere
OTD_ADMIN_PORTis defined in Section 11.1, "Assembling Information for Identity and Access Management Deployment." -
Click the Configurations button that is situated at the upper left corner of the page.
A list of the available configurations is displayed.
-
Select the configuration for which you want to create a server pool. For example: for example,
sso.mycompany.com. -
In the Common Tasks pane, click New Server Pool.
The New Origin-Server Pool wizard starts.
Figure 12-2 New Origin-Server Pool Wizard

Description of "Figure 12-2 New Origin-Server Pool Wizard"
-
Enter the following information in the Server Pool Information screen:
-
Name: Name of the server pool. For example,
oim-pool -
Origin Server Type: The type of requests the pool handles. For example,
HTTP.
Click Next.
-
-
Enter the following information in the Origin Server Information screen:
-
Origin Server Host:
OIMHOST1VHN.mycompany.com -
Port:
14000(OIM_PORT)
Click Add Server.
-
-
Enter the information for any other servers. For example:
-
Origin Server Host:
OIMHOST2.mycompany.com -
Port:
14000(OIM_PORT)
Click Next.
Review the information on the Review screen. If the information is correct, click Create Server Pool.
-
-
For each HTTP pool that was created and has more than one origin server, perform the additional configuration steps:
-
Click on the newly create server pool name, for example
oim-pool.The pool properties appear.
-
Expand the Advanced Settings.
-
Enable the check box Dynamic Discovery
This ensures that any new cluster members added at a later date are automatically added to the OTD server pool without you having to add them manually, although it is still good practice.
Note:
You cannot use Dynamic Discovery for the OUD origin server pool (oud-pool) -
Click Save.
-
-
Click Close on the Results screen.
-
The details of the origin-server pool that you just created are displayed on the Origin-Server Pools page.
-
In addition, the Deployment Pending message is displayed at the top of the main pane. You can either deploy the updated configuration immediately by clicking Deploy Changes, or you can do so later after making further changes as described in Section 12.11, "Deploying the Configuration and Testing the Virtual Server Addresses."
-
-
Repeat these steps for the origin-server pool listed in Table 12-3.
12.7.2 Creating Virtual Servers
Create virtual servers using the information in Table 12-7, "Routes and Conditions".
Table 12-6 Virtual Server Information
| Name | Host | Pool |
|---|---|---|
|
sso.mycompany.com |
sso.mycompany.com |
origin-server-pool-1 |
|
iadadmin.mycompany.com |
iadadmin.mycompany.com |
iadadmin-pool |
|
igdadmin.mycompany.com |
igdadmin.mycompany.com |
igdadmin-pool |
|
idminternal.mycompany.com |
idminternal.mycompany.com |
oim-pool |
Note:
Thesso.mycompany.com virtual server is created automatically when you created the configuration.To create a virtual server using the administration console:
-
Log in to the OTD administration console using the URL specified in Section 20.2, "About Identity and Access Management Console URLs.":
-
Click the Configurations button that is situated at the upper left corner of the page.
A list of the available configurations is displayed.
-
Select the configuration for which you want to create a virtual server, for example
sso.mycompany.com. -
In the Common Tasks pane, click New Virtual Server.
The New Virtual Server wizard starts.
-
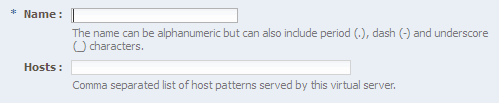
On the Virtual Server Information Page enter the following information:
-
Name: The name describing the virtual server. For example,
sso.mycompany.com -
Host: The name in the DNS/Hosts which is used to access this virtual server. For example,
sso.mycompany.com
Click Next.
-
-
On the HTTP Listener Information screen, select the existing Listener.
Click Next.
-
On the server Pool Information Screen, enter the following information:
-
Select: Select a pool of origin servers.
-
Name: Select the name of one of the server pools you created in 0, "Creating an Origin-Server Pool".
Click Next.
-
-
Review the supplied information in the Review screen and click Create Virtual Server.
-
Repeat steps 4-6 for each virtual server in Table 12-6.
12.7.3 Creating a TCP Proxy and Listener for idstore.mycompany.com
Create a TCP Proxy using the administration console.
To create a TCP Proxy:
-
Log in to the OTD administration console using the URL specified in Section 20.2, "About Identity and Access Management Console URLs.":
-
Click the Configurations button that is situated at the upper left corner of the page.
A list of the available configurations is displayed.
-
Select the configuration for which you want to create a TCP Proxy, for example
sso.mycompany.com. -
In the Common Tasks pane, click New TCP Proxy.
The New TCP Proxy wizard starts.
-
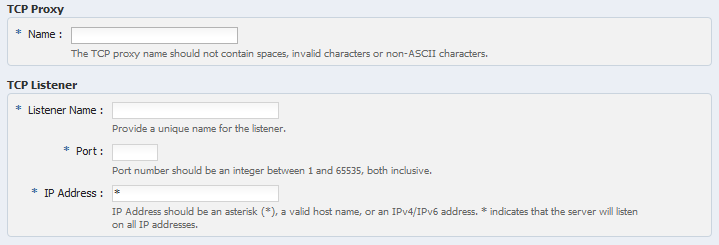
In the Step 1: TCP Proxy Information screen, enter the following information and click Next:
-
Name:
idstore.mycompany.com -
Listener Name:
listener-oud -
Port:
1489(LDAP_LBR_PORT)Note:
If OUD and OTD are running on the same host, the port used by OTD to route requests to OUD must be a different port from the OUD port -
In the IP Address field, enter
*.
-
-
In the Step 2: Server Pool Information screen, click Select a pool of origin servers.
-
In the drop-down list, select oud-pool and click Next.
The Review screen appears.
-
Review the details and click Create TCP Proxy.
-
Click Close on the Results screen.
-
The details of the TCP Proxies that you just created are displayed on the TCP proxies page.
-
In addition, the Deployment Pending message is displayed at the top of the main pane. You can either deploy the updated configuration immediately by clicking Deploy Changes, or you can do so later after making further changes, as described in Section 12.11, "Deploying the Configuration and Testing the Virtual Server Addresses."
-
12.8 Creating Routes
Note:
This section is only relevant when Oracle Traffic Director is used as a web server.Routes are similar to an Oracle HTTP location directives. Any requests received for a specific URI inside a virtual server are directed to the appropriate server pool. Adding routes allows a virtual server to direct requests to different server pools depending on what is contained within the URI.
Create the routes listed in Table 12-7using the administration console. If External Oracle HTTP Servers are being used, then routes only required for IDMINTERNAL.mycompany.com. All other routing will take place on the Oracle HTTP Server.
Table 12-7 Routes and Conditions
| Virtual Host | Route | Origin-Server Pool | Conditions | Cookie Name |
|---|---|---|---|---|
|
iadadmin.mycompany.com |
default |
iadadmin-pool |
N/A |
|
|
oaam-admin-route |
oaam-admin-pool |
$uri =~ '/oaam_admin' |
||
|
igdadmin.mycompany.com |
default |
igdadmin-pool |
NA |
|
|
oim-admin-route |
oim-pool |
$uri =~ '/oim' or |
oimjsessionid |
|
|
$uri =~ '/identity' or |
||||
|
$uri =~ '/sysadmin' or |
||||
|
$uri =~ '/xlWebApp' or |
||||
|
$uri =~ '/Nexaweb' |
||||
|
sso.mycompany.com |
default |
origin-server-pool-1 |
N/A |
OAM_JSESSIONID |
|
oaam-route |
oaam-pool |
$uri =~ '/oaam_server' |
OAM_JSESSIONID |
|
|
oim-sso-route |
oim-pool |
$uri =~ '/identity' or |
oimjsessionid |
|
|
$uri =~ '/xlWebApp' or |
||||
|
$uri =~ '/HTTPClnt' or |
||||
|
$uri =~ '/reqsvc' |
||||
|
idminternal.mycompany.com |
default |
oim-pool |
N/A |
oimjsessionid |
|
soa-idminternal-route |
soa-pool |
$uri =~ '/soa-infra' or |
oimjsessionid |
|
|
$uri =~ '/sodcheck' or |
||||
|
$uri =~ '/integration' or |
||||
|
$uri =~ '/ucs' |
To create virtual server routes:
-
Log in to the OTD administration console using the URL specified in Section 20.2, "About Identity and Access Management Console URLs.":
-
Click the Configurations button that is situated at the upper left corner of the page.
A list of the available configurations is displayed.
-
Select the configuration for which you want to configure routes, for example
sso.mycompany.com. -
In the navigation pane, expand Virtual Servers, expand the sso.mycompany.com virtual server, and select Routes.
The Routes page is displayed. It lists the routes that are currently defined for the virtual server.
Creating a Route
-
Click New Route.
The New Route dialog box is displayed.
-
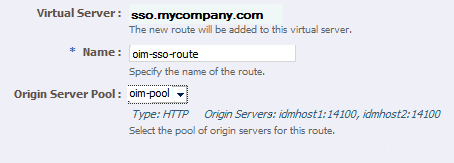
In the Step 1: Route Properties screen, in the Name field, enter
oim-sso-route -
In the Origin Server Pool drop-down select
oim-pool, and click Next. -
In the Step 2: Condition Information screen, select the $uri variable from the Variable/Function drop-down list. Select the Operator ('= ~ ' in your example). And enter the value in the Value field.
Note:
Joiner, such asandoror, cannot be used for the first expression in the sequence.Figure 12-6 New Route Condition Expressions
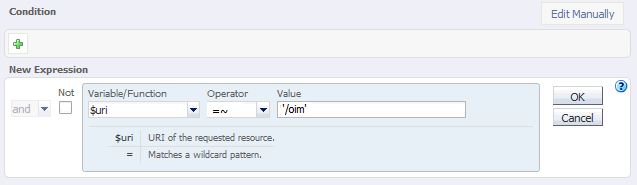
Description of "Figure 12-6 New Route Condition Expressions"
-
Click OK and click the Plus button to add the next expression.
Figure 12-7 New Route Condition Information
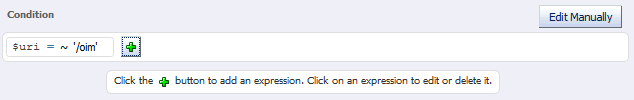
Description of "Figure 12-7 New Route Condition Information"
-
Select the Variable/Function, Operator, and Value and click OK.
Figure 12-8 New Route Condition Information
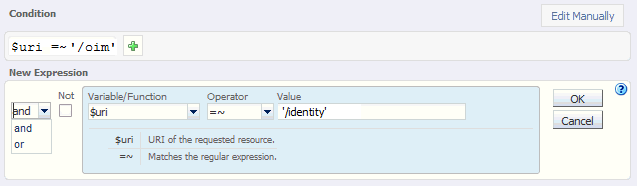
Description of "Figure 12-8 New Route Condition Information"
Note the joiner 'or' can now be selected.
-
Perform steps d to g until you have added all the required values
You can also click the Edit Manually button to edit the expressions in a text field. Note that going into the manual mode, it is not possible to go back to the default edit mode. You must continue in the manual edit mode and save the condition.
-
-
Click Next, and then Create Route.
The route that you just created is displayed on the Routes page.
In addition, the Deployment Pending message is displayed at the top of the main pane. You can either deploy the updated configuration immediately by clicking Deploy Changes, or you can do so later after making further changes as described in Section 12.11, "Deploying the Configuration and Testing the Virtual Server Addresses."
-
Update the cookie name of the newly created route and the default route:
-
Click on the newly created route.
-
Expand the Advanced Settings
-
Set Sticky Cookie to the cookie name from table Table 12-7.
-
Set the Sticky URI Parameter to the cookie name from Table 12-7.
-
Repeat these steps for the values listed in Table 12-7.
Click Save.
-
12.9 Enabling SSL Passthrough for sso.mycompany.com
In the enterprise deployment, Topology SSL is terminated at the hardware load balancer and passed through to Oracle Traffic Director using the HTTP protocol. If an external HTTP server is being used, this section is not applicable.
Oracle Traffic Director requires extra configuration steps to ensure that any application redirects occur correctly.
To ensure application redirects occur correctly:
-
Log in to the OTD administration console using the URL specified in Section 20.2, "About Identity and Access Management Console URLs.":
-
Click the Configurations button at the upper left corner of the page.
A list of the available configurations is displayed.
-
Select the configuration for which you want to configure routes, for example
sso.mycompany.com. -
In the Navigation Pane, expand Virtual Servers and select the virtual server sso.mycompany.com.
-
Click Routes.
The defined routes appear.
-
Click a route, for example, default-route.
The Route Properties screen appears.
-
Expand Advanced Settings.
-
In the Route Properties section, remove any content in the box labeled Rewrite Headers.
-
In the Parameters Forwarded to Origin Servers section, deselect the following:
-
SSL
-
Cipher
-
Key Size
-
Secret Key Size
-
SSL/TLS Session ID
-
Certificate
-
User DN
-
Issuer DN
Click Save.
-
-
Repeat for each route associated with the virtual server sso.mycompany.com.
12.10 Workaround for Issues caused by TMPWATCH cleanup
When OTD runs, it creates files in /tmp. The UNIX process TMPWATCH, which cleans up the temporary directory, can delete these files. This effects OTD's operation.
To avoid this issue, Oracle Traffic Director must be told to place its files in a location other than /tmp.
To do direct OTD to do this:
-
Create a directory called
tmpin OTD_ORACLE_INSTANCE.For example:
mkdir LOCAL_CONFIG/tmp -
Log in to the OTD Administration Console using the URL specified in Section 20.2, "About Identity and Access Management Console URLs."
-
Click Advanced Settings from the Configuration menu.
-
In the General Configuration settings, update the value of Temporary Directory to LOCAL_CONFIG
/tmp. -
Click Save.
12.11 Deploying the Configuration and Testing the Virtual Server Addresses
Deploy the configuration to create an instance of it on an administration node. When you deploy a configuration, the running instances are reconfigured to reflect the configuration changes.
Note:
The topology documented in this guide requires the following virtual IP addresses:-
idstore.mycompany.com
-
idminternal.mycompany.com
-
iadadmin.mycompany.com
You can add idstore.mycompany.com and idminternal.mycompany.com host entries to resolve them with and internal IP address.
You can register iadadmin.mycompany.com and igdadmin.mycompany.com on the DNS.
Deploying a Configuration Using the Administration Console
To deploy a configuration by using the administration console, do the following:
-
Log in to the OTD administration console using the URL specified in Section 20.2, "About Identity and Access Management Console URLs.":
-
Click the Configurations button at the upper left corner of the page.
A list of the available configurations is displayed.
-
Select the IAM configuration.
-
Click Deploy.
A message is displayed confirming that the updated configuration was successfully deployed.
-
Click Close.
12.12 Creating a Failover Group for Virtual Hosts
When a request is sent to one of the virtual hosts idstore.mycompany.com and idminternal.mycompany.com it is directed to the IP address associated with the virtual host name. This IP address is enabled on one of the OTD instances. In the case of failure, IP address is moved to an OTD instance that is still available.
Each OTD instance maintains a heart beat with each other OTD instance. If that heartbeat fails then OTD moves active IP addresses on the downed instance to one of the named failover instances. You do this by creating an active-passive failover group for the IP address. This failover group lists a primary and a number of secondary instances.
The enterprise deployment on Exalogic uses the following four failover groups:
-
A failover group for distributing internal LDAP requests among the OUD servers.
-
A failover group for internal inter-app requests.
-
Two failover groups to allow the external load balancer requests among Oracle Traffic Director servers. This failover group is optional, as the load balancer could point to the OTD instances directly. The benefit of using an Oracle Traffic Director failover group is that failures are detected and resolved faster using the failover group resulting in a reduced recovery time from failed servers.
The steps below show you how to create failover groups with the information in Table 12-8.
Table 12-8 Failover Group Details
| Virtual Host | Router ID | Network Prefix | Primary Node | Primary Network Interface | Secondary Node | Secondary Network Interface |
|---|---|---|---|---|---|---|
|
idstore.mycompany.com |
50 |
19 |
Admin Node |
bond0 |
WEBHOST2 |
bond0 |
|
idminternal.mycompany.com |
51 |
19 |
WEBHOST2 |
bond0 |
Admin Node |
bond0 |
|
webhost1vhn1.mycompany.com |
53 |
19 |
Admin Node |
bond1 |
WEBHOST2 |
bond1 |
|
webhost2vhn1.mycompany.com |
52 |
19 |
WEBHOST2 |
bond1 |
Admin Node |
bond1 |
Note:
The failover groups for the external virtual IP addresses are optional since the load balancer fails over requests between the two Oracle Traffic Director instances. However, they will provide faster failure detection and failover than the typical load balancer monitors.Note:
The router ID is a unique number you assign to the routing. The number must be between 1 and 244.The Network Prefix is the subnet mask in the CIDR format.
The primary node is the node where the Failover group is initially active.
The Primary Network Interface is the interface on the host where the failover group is bound.
The Secondary Node is the Node on which the failover group can be started if the Primary node is unavailable.
The Secondary Network interface is the Network Interface used on the Secondary node.
To create a failover group by using the administration console, do the following:
-
Log in to the OTD administration console using the URL specified in Section 20.2, "About Identity and Access Management Console URLs.":
-
Click the Configurations button at the upper left corner of the page.
A list of the available configurations appears.
-
Select the configuration for which you want to create a failover group, for example
sso.mycompany.com. -
In the navigation pane, click Failover Groups.
The Failover Groups page is displayed.
-
Click New Failover Group.
The New Failover Group wizard is displayed.
-
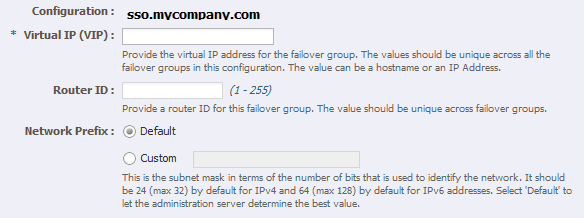
In the Virtual IP (VIP) field, enter the virtual IP address associated with
idstore.mycompany.com(192.168.50.2) and click Next.To create the failover group for the
idminternal.mycompany.comuse the VIP associated with theidminternal.mycompany.com(192.168.50.1) as shown in Table 4-1. -
In the Step 2: Failover Nodes Information screen, select the Primary and Backup nodes, (OTDADMIN, WEBHOST2), and click Next.
The details of the failover group that you just created are displayed on the Failover Groups page.
Note:
Generally it is sufficient to leave Network Interface (NIC) at the default value ofAuto Detect. If you leave the default, Oracle Traffic Director (OTD) determines which network interface card to use based on the IP address of the failover group. If, however, this is not easily derivable, for example, if you have not used a standard CIDR associated with the IP address, you may have to manually tell OTD the network interface to which the failover group should be attached.For example, if your internal IP address is 192.168.1.1, and it is associated with
bond0, and uses a valid net mask (CIDR), and your IP address of the failover group is 192.168.50.1, OTD knows to use network interfacebond0. If, however, OTD cannot determine the appropriate interface, you are required to specify it in this field.Oracle Traffic Director validates the information before creating the failover group.
-
Click Close on the Results screen.
The details of the failover group that you just created are displayed on the Failover Groups page.
Note:
A message may be displayed indicating that the failover group could not be started in the involved nodes due to insufficient privileges. To resolve this, log in to each node as root and run the following command:OTD_ORACLE_HOME/bin/tadm start-failover --instance-home=WEB_INSTANCE_HOME/ --config=sso.mycompany.com
12.13 Backing Up the Oracle Traffic Director Configuration
Back up the Oracle Traffic director configuration. For more information, see Section Section 20.5, "Performing Backups and Recoveries."