| Skip Navigation Links | |
| Exit Print View | |
|
Oracle Solaris Trusted Extensions Configuration Guide |
1. Security Planning for Trusted Extensions
2. Configuration Roadmap for Trusted Extensions
3. Adding Trusted Extensions Software to the Solaris OS (Tasks)
4. Configuring Trusted Extensions (Tasks)
Setting Up the Global Zone in Trusted Extensions
Check and Install Your Label Encodings File
Enable IPv6 Networking in Trusted Extensions
Configure the Domain of Interpretation
Create ZFS Pool for Cloning Zones
Reboot and Log In to Trusted Extensions
Initialize the Solaris Management Console Server in Trusted Extensions
Make the Global Zone an LDAP Client in Trusted Extensions
Adding Network Interfaces and Routing to Labeled Zones
Add a Network Interface to Route an Existing Labeled Zone
Add a Network Interface That Does Not Use the Global Zone to Route an Existing Labeled Zone
Configure a Name Service Cache in Each Labeled Zone
Creating Roles and Users in Trusted Extensions
Create Rights Profiles That Enforce Separation of Duty
Create the Security Administrator Role in Trusted Extensions
Create a Restricted System Administrator Role
Create Users Who Can Assume Roles in Trusted Extensions
Verify That the Trusted Extensions Roles Work
Enable Users to Log In to a Labeled Zone
Creating Home Directories in Trusted Extensions
Create the Home Directory Server in Trusted Extensions
Enable Users to Access Their Home Directories in Trusted Extensions
Adding Users and Hosts to an Existing Trusted Network
Add an NIS User to the LDAP Server
Troubleshooting Your Trusted Extensions Configuration
netservices limited Was Run After Trusted Extensions Was Enabled
Cannot Open the Console Window in a Labeled Zone
Labeled Zone Is Unable to Access the X Server
Additional Trusted Extensions Configuration Tasks
How to Copy Files to Portable Media in Trusted Extensions
How to Copy Files From Portable Media in Trusted Extensions
How to Remove Trusted Extensions From the System
5. Configuring LDAP for Trusted Extensions (Tasks)
6. Configuring a Headless System With Trusted Extensions (Tasks)
B. Using CDE Actions to Install Zones in Trusted Extensions
The txzonemgr script steps you through all the following tasks that configure labeled zones.
 | Caution - You must be running the Solaris 10 8/07 release of Trusted Extensions or a later release to use the txzonemgr procedures. Or, you must install all patches for the Solaris 10 11/06 release. |
If you are running the Solaris 10 11/06 release without current patches, use the procedures in Appendix B, Using CDE Actions to Install Zones in Trusted Extensions to configure the labeled zones.
The instructions in this section configure labeled zones on a system that has been assigned at most two IP addresses. For other configurations, see the configuration options in Task Map: Preparing For and Enabling Trusted Extensions.
This task map describes and links to the tasks that configure labeled zones.
|
This script steps you through the tasks to properly configure, install, initialize, and boot labeled zones. In the script, you name each zone, associate the name with a label, install the packages to create a virtual OS, and then boot the zone to start services in that zone. The script includes copy zone and clone zone tasks. You can also halt a zone, change the state of a zone, and add zone-specific network interfaces.
This script presents a dynamically-determined menu that displays only valid choices for the current circumstances. For instance, if the status of a zone is configured, the Install zone menu item is not displayed. Tasks that are completed do not display in the list.
You are superuser.
If you plan to clone zones, you have completed the preparation for cloning zones. If you plan to use your own security templates, you have created the templates.
# /usr/sbin/txzonemgr
The script opens the Labeled Zone Manager dialog box. This zenity dialog box prompts you for the appropriate tasks, depending on the current state of your installation.
To perform a task, you select the menu item, then press the Return key or click OK. When you are prompted for text, type the text then press the Return key or click OK.
Tip - To view the current state of zone completion, click Return to Main Menu in the Labeled Zone Manager.
Note - If you are configuring your system to use DHCP, refer to the laptop instructions in the Trusted Extensions section of OpenSolaris Community: Security web page.
Starting in the Solaris 10 10/08 release, if you are configuring a system where each labeled zone is on its own subnet, you can skip this step and continue with Name and Label the Zone. You add the network interfaces for each labeled zone in Add a Network Interface to Route an Existing Labeled Zone, after you have finished installing and customizing the zones.
In this task, you configure the networking in the global zone. You must create exactly one all-zones interface. An all-zones interface is shared by the labeled zones and the global zone. The shared interface is used to route traffic between the labeled zones and the global zone. To configure this interface, do one of the following:
Create a logical interface from a physical interface, then share the physical interface.
This configuration is the simplest to administer. Choose this configuration when your system has been assigned two IP addresses. In this procedure, the logical interface becomes the global zone's specific address, and the physical interface is shared between the global zone and the labeled zones.
Share a physical interface
Choose this configuration when your system has been assigned one IP address. In this configuration, the physical interface is shared between the global zone and the labeled zones.
Share a virtual network interface, vni0
Choose this configuration when you are configuring DHCP, or when each subnetwork is at a different label. For a sample procedure, refer to the laptop instructions in the Trusted Extensions section of OpenSolaris Community: Security web page.
Starting in the Solaris 10 10/08 release, the loopback interface in Trusted Extensions is created as an all-zones interface. Therefore, you do not need to create a vni0 shared interface.
To add zone-specific network interfaces, finish and verify zone creation before adding the interfaces. For the procedure, see Add a Network Interface to Route an Existing Labeled Zone.
You are superuser in the global zone.
The Labeled Zone Manager is displayed. To open this GUI, see Run the txzonemgr Script.
A list of interfaces is displayed.
Note - In this example, the physical interface was assigned a host name and an IP address during installation.
A system with one interface displays a menu similar to the following. The annotation is added for assistance:
vni0 DownVirtual Network Interface eri0 global 10.10.9.9 cipso Up Physical Interface
You are offered three options:
View Template Assign a label to the interface Share Enable the global zone and labeled zones to use this interface Create Logical Interface Create an interface to use for sharing
In this configuration, the host's IP address applies to all zones. Therefore, the host's address is the all-zones address. This host cannot be used as a multilevel server. For example, users cannot share files from this system. The system cannot be an LDAP proxy server, an NFS home directory server, or a print server.
eri0 all-zones 10.10.9.8 cipso Up
You are successful when the physical interface is an all-zones interface. Continue with Name and Label the Zone.
Then, share the physical interface.
This is the simplest Trusted Extensions network configuration. In this configuration, the main IP address can be used by other systems to reach any zone on this system, and the logical interface is zone-specific to the global zone. The global zone can be used as a multilevel server.
Dismiss the dialog box that confirms the creation of a new logical interface.
For example, specify machine1-services as the host name for the logical interface. The name indicates that this host offers multilevel services.
For example, specify 10.10.9.2 as the IP address for the logical interface.
The interface is displayed as Up.
eri0 global 10.10.9.1 cipso Up eri0:1 global 10.10.9.2 cipso Up
eri0 all-zones 10.10.9.1 cipso Up eri0:1 global 10.10.9.2 cipso Up
You are successful when at least one interface is an all-zones interface.
Example 4-3 Viewing the /etc/hosts File on a System With a Shared Logical Interface
On a system where the global zone has a unique interface and labeled zones share a second interface with the global zone, the /etc/hosts file appears similar to the following:
# cat /etc/hosts ... 127.0.0.1 localhost 192.168.0.11 machine1 loghost 192.168.0.12 machine1-services
In the default configuration, the tnrhdb file appears similar to the following:
# cat /etc/security/tsol/tnrhdb ... 127.0.0.1:cipso 192.168.0.11:cipso 192.168.0.12:cipso 0.0.0.0:admin_low
If the all-zones interface is not in the tnrhdb file, the interface defaults to cipso.
Example 4-4 Displaying the Shared Interface on a Trusted Extensions System With One IP Address
In this example, the administrator is not planning to use the system as a multilevel server. To conserve IP addresses, the global zone is configured to share its IP address with every labeled zone.
The administrator selects Share for the hme0 interface on the system. The software configures all zones to have logical NICs. These logical NICs share a single physical NIC in the global zone.
The administrator runs the ifconfig -a command to verify that the physical interface hme0 on network interface 192.168.0.11 is shared. The value all-zones is displayed:
lo0: flags=2001000849<UP,LOOPBACK,RUNNING,MULTICAST,IPv4,VIRTUAL> mtu 8232 index 1
inet 127.0.0.1 netmask ff000000
hme0: flags=1000843<BROADCAST,RUNNING,MULTICAST,IPv4> mtu 1500 index 2
all-zones
inet 192.168.0.11 netmask fffffe00 broadcast 192.168.0.255
Starting in the Solaris 10 10/08 release, the loopback interface in Trusted Extensions is created as an all-zones interface.
lo0: flags=2001000849<UP,LOOPBACK,RUNNING,MULTICAST,IPv4,VIRTUAL> mtu 8232 index 1
all-zones
inet 127.0.0.1 netmask ff000000
hme0: flags=1000843<BROADCAST,RUNNING,MULTICAST,IPv4> mtu 1500 index 2
all-zones
inet 192.168.0.11 netmask fffffe00 broadcast 192.168.0.255
The administrator also examines the contents of the /etc/hostname.hme0 file:
192.168.0.11 all-zones
You do not have to create a zone for every label in your label_encodings file, but you can. The administrative GUIs enumerate the labels that can have zones created for them on this system.
You are superuser in the global zone. The Labeled Zone Manager dialog box is displayed. To open this GUI, see Run the txzonemgr Script. You have configured the network interfaces in the global zone.
You have created any security templates that you need. A security template defines, among other attributes, the label range that can be assigned to a network interface. The default security templates might satisfy your needs.
For an overview of security templates, see Network Security Attributes in Trusted Extensions in Oracle Solaris Trusted Extensions Administrator’s Procedures.
To use the Solaris Management Console to create security templates, see Configuring Trusted Network Databases (Task Map) in Oracle Solaris Trusted Extensions Administrator’s Procedures.
You are prompted for a name.
Tip - Give the zone a name that is similar to the zone's label. For example, the name of a zone whose label is CONFIDENTIAL: RESTRICTED would be restricted.
For example, the default label_encodings file contains the following labels:
PUBLIC CONFIDENTIAL: INTERNAL USE ONLY CONFIDENTIAL: NEED TO KNOW CONFIDENTIAL: RESTRICTED SANDBOX: PLAYGROUND MAX LABEL
Although you could create one zone per label, consider creating the following zones:
On a system for all users, create one zone for the PUBLIC label and three zones for the CONFIDENTIAL labels.
On a system for developers, create a zone for the SANDBOX: PLAYGROUND label. Because SANDBOX: PLAYGROUND is defined as a disjoint label for developers, only systems that developers use need a zone for this label.
Do not create a zone for the MAX LABEL label, which is defined to be a clearance.
The dialog box displays zone-name:configured above a list of tasks.
# /usr/sbin/smc &
Provide a password when prompted.
The dialog box displays the name of a zone that does not have an assigned label.
If you click the wrong label, click the label again to deselect it, then click the correct label.
Click OK in the Label Builder, then click OK in the Trusted Network Zones Properties dialog box.
You are finished when every zone that you want is listed in the panel, or the Add Zone Configuration menu item opens a dialog box that does not have a value for Zone Name.
Click Select Label menu item and OK to display the list of available labels.
For a zone that is named public, you would select the label PUBLIC from the list.
A list of tasks is displayed.
You are superuser in the global zone. The zone is configured, and has an assigned network interface.
The Labeled Zone Manager dialog box is displayed with the subtitle zone-name:configured. To open this GUI, see Run the txzonemgr Script.
 | Caution - This process takes some time to finish. Do not perform other tasks while this task is completing. |
The system copies packages from the global zone to the non-global zone. This task installs a labeled virtual operating system in the zone. To continue the example, this task installs the public zone. The GUI displays output similar to the following.
# Labeled Zone Manager: Installing zone-name zone Preparing to install zone <zonename> Creating list of files to copy from the global zone Copying <total> files to the zone Initializing zone product registry Determining zone package initialization order. Preparing to initialize <subtotal> packages on the zone. Initializing package <number> of <subtotal>: percent complete: percent Initialized <subtotal> packages on zone. Zone <zonename> is initialized. The file /zone/internal/root/var/sadm/system/logs/install_log contains a log of the zone installation.
Note - Messages such as cannot create ZFS dataset zone/zonename: dataset already exists are informational. The zone uses the existing dataset.
When the installation is complete, you are prompted for the name of the host. A name is supplied.
The dialog box displays zone-name:installed above a list of tasks.
If warnings that are similar to the following are displayed: Installation of these packages generated errors: SUNWpkgname, read the install log and finish installing the packages.
You are superuser in the global zone. The zone is installed, and has an assigned a network interface.
The Labeled Zone Manager dialog box is displayed with the subtitle zone-name:installed. To open this GUI, see Run the txzonemgr Script.
A separate console window appears for the current labeled zone.
The Zone Terminal Console tracks the progress of booting the zone. If the zone is created from scratch, messages that are similar to the following appear in the console:
[Connected to zone 'public' console] [NOTICE: Zone booting up] ... Hostname: zone-name Loading smf(5) service descriptions: number/total Creating new rsa public/private host key pair Creating new dsa public/private host key pair rebooting system due to change(s) in /etc/default/init [NOTICE: Zone rebooting]
 | Caution - Do not perform other tasks while this task is completing. |
When the four default zones are configured and booted, the Labeled Zone Manager displays the zones as follows:
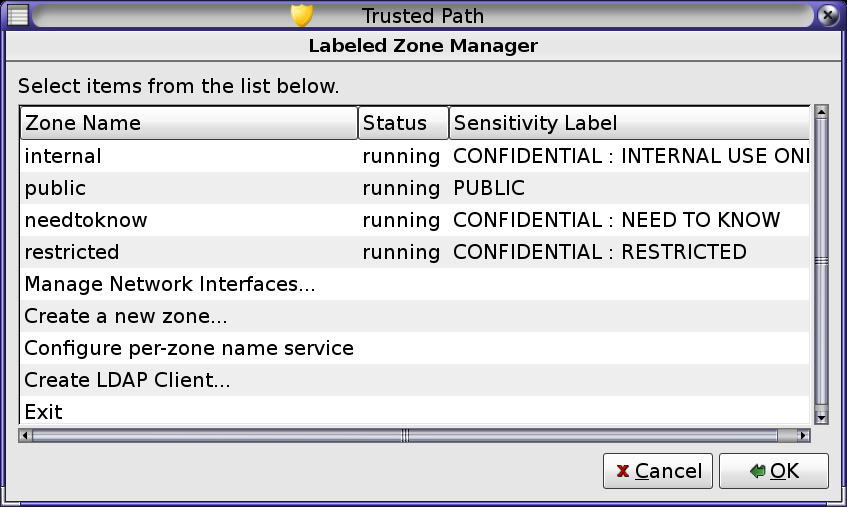
Sometimes, error messages are displayed and the zone does not reboot. In the Zone Terminal Console, press the Return key. If you are prompted to type y to reboot, type y and press the Return key. The zone reboots.
If this zone was copied or cloned from another zone, continue with Verify the Status of the Zone.
If this zone is the first zone, continue with Customize the Labeled Zone.
Note - The X server runs in the global zone. Each labeled zone must be able to connect with the global zone to use the X server. Therefore, zone networking must work before a zone can be used. For background information, see Planning for Multilevel Access.
hostname console login: root Password: Type root password
# svcs -xv svc:/application/print/server:default (LP print server) State: disabled since Tue Oct 10 10:10:10 2006 Reason: Disabled by an administrator. See: http://sun.com/msg/SMF-8000-05 See: lpsched(1M) ...
The sendmail and print services are not critical services.
# ifconfig -a
For example, the following output shows an IP address for the hme0 interface.
# ...
hme0: flags=1000843<BROADCAST,RUNNING,MULTICAST,IPv4> mtu 1500 index 2
all-zones
inet 192.168.0.11 netmask fffffe00 broadcast 192.168.0.255# DISPLAY=global-zone-hostname:n.n # export DISPLAY
For example, display a clock.
# /usr/openwin/bin/xclock
If the clock at the label of the zone does not appear, the zone networking has not been configured correctly. For debugging suggestions, see Labeled Zone Is Unable to Access the X Server.
# zoneadm list -v ID NAME STATUS PATH BRAND IP 0 global running / native shared 3 internal running /zone/internal native shared 4 needtoknow running /zone/needtoknow native shared 5 restricted running /zone/restricted native shared
You have completed configuring the labeled zone. To add zone-specific network interfaces to the zones or to establish default routing per labeled zone, continue with Adding Network Interfaces and Routing to Labeled Zones. Otherwise, continue with Creating Roles and Users in Trusted Extensions.
If you are going to clone zones or copy zones, this procedure configures a zone to be a template for other zones. In addition, this procedure configures a zone that has not been created from a template for use.
You are superuser in the global zone. You have completed Verify the Status of the Zone.
If you are copying or cloning this zone, the services that you disable are disabled in the new zones. The services that are online on your system depend on the service manifest for the zone. Use the netservices limited command to turn off services that labeled zones do not need.
# netservices limited
# svcs ... STATE STIME FMRI online 13:05:00 svc:/application/graphical-login/cde-login:default ...
# svcadm disable svc:/application/graphical-login/cde-login # svcs cde-login STATE STIME FMRI disabled 13:06:22 svc:/application/graphical-login/cde-login:default
For information about the service management framework, see the smf(5) man page.
In the zone-name: Zone Terminal Console, the following message indicates that the zone is shut down.
[ NOTICE: Zone halted]
If you are not copying or cloning this zone, create the remaining zones in the way that you created this first zone. Otherwise, continue with the next step.
In a terminal window in the global zone, remove this file from the zone-name zone.
# cd /zone/zone-name/root/etc # ls auto_home* auto_home auto_home_zone-name # rm auto_home_zone-name
For example, if the public zone is the template for cloning other zones, remove the auto_home_public file:
# cd /zone/public/root/etc # rm auto_home_public
 | Caution - The zone for the snapshot must be in a ZFS file system. You created a ZFS file system for the zone in Create ZFS Pool for Cloning Zones. |
The Zone Terminal Console tracks the progress of booting the zone. Messages that are similar to the following appear in the console:
[Connected to zone 'public' console] [NOTICE: Zone booting up] ... Hostname: zonename
Press the Return key for a login prompt. You can log in as root.
You have completed Customize the Labeled Zone.
The Labeled Zone Manager dialog box is displayed. To open this GUI, see Run the txzonemgr Script.
For details, see Name and Label the Zone.
You will repeat these steps for every new zone.
A window displays the copying process. When the process completes, the zone is installed.
If the Labeled Zone Manager displays zone-name:configured, continue with the next step. Otherwise, continue with Step e.
For example, if you created a snapshot from public, select the zone/public@snapshot.
When the cloning process completes, the zone is installed. Continue with Step c.
For instructions, see Boot the Labeled Zone.
When you have completed Verify the Status of the Zone for every zone, and you want each zone to be on a separate physical network, continue with Add a Network Interface to Route an Existing Labeled Zone.
If you have not yet created roles, continue with Creating Roles and Users in Trusted Extensions.
If you have already created roles, continue with Creating Home Directories in Trusted Extensions.