Authentication
Authentication is the process of verifying that individuals requesting access or sending messages are who they say they are and that information received from a remote host has not been modified in transit.
SunScreen SKIP uses the Keyed MD5 algorithm to authenticate messages. The MD5 message digest algorithm takes a message of any length and produces a 16-byte digest (the hash value). This message digest serves as a thumb print of the original file when you want to authenticate a document. The original message cannot be derived from the message digest.
The process by which SunScreen SKIP signs a message with a message digest follows.
-
The sender and destination host agree to use authentication as part of their secure communication process.
-
The sender creates a message and indicates that it can be sent to the destination host.
-
SunScreen SKIP encrypts the message using the specified encryption algorithm.
-
SunScreen SKIP uses a keyed MD5 message digest algorithm to create a digest of the message and encrypts the message digest with the time-based shared secret.
-
SunScreen SKIP adds the encrypted digest to the authentication header for the message.
-
SunScreen SKIP sends the message to the destination host.
-
The destination host receives and decrypts the encrypted message, which includes the message digest.
-
The destination host uses the time-based shared secret to decrypt the message digest.
-
The destination host creates its own message digest of the message it received, using the same keyed MD5 algorithm the sender used.
-
The destination host compares the message digest it created with the one that came with the message. If the two message digests match, the destination host knows that the text of the message has not been modified and that the person claiming to be the sender was actually the sender.
The following figure illustrates how a destination host would calculate its own MD5 digest of the message, decrypt the digest sent with the message, and compare the two digests to authenticate the integrity and source of the message.
Figure B-8 Authenticating a Message
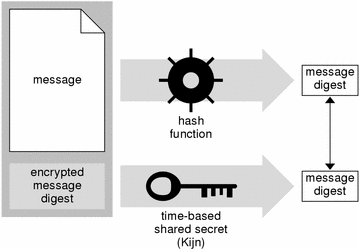
Authentication provides a digital signature that proves the identity of the sender. If the message digest can be decrypted with the time-based shared secret, the destination host knows it was encrypted with the time-based shared secret. Since the time-based shared secret is known only to the two hosts, the destination host can be confident of the message's source as well as of its integrity.
- © 2010, Oracle Corporation and/or its affiliates
