Shared Key and Public Key Encryption
SKIP uses a combination of shared key cryptography and public key cryptography to protect messages sent between hosts. SKIP hosts use shared traffic keys that change frequently to encrypt data sent from one host to another. To protect these shared traffic keys, SKIP hosts use the public key to calculate an implicit shared secret, which they use to encrypt the shared traffic keys, keeping network communication secure.
Shared Key Encryption
Shared key encryption uses one key to encrypt and decrypt messages. For shared key cryptography to work, the sender and the recipient of a message must both have the same key, which they must keep secret from everybody else. The sender uses the shared key to encrypt a message, shown in the following figure, and then sends the ciphertext message to the recipient.
Figure B-1 Sender Uses Key to Encrypt Plaintext to Ciphertext
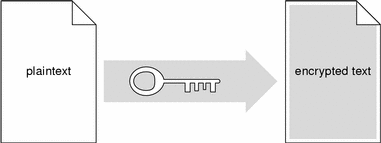
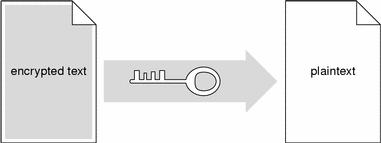
When the ciphertext message arrives, the recipient uses the identical shared key to decrypt the message, shown in the following figure.
Figure B-2 Recipient Uses Key to Decrypt Ciphertext to Plaintext
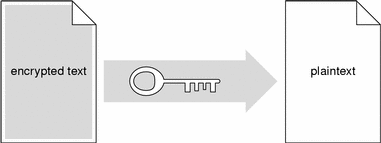
Shared key encryption/decryption is relatively fast. However, since anyone with the shared key can decrypt the information, shared key encryption requires that only the sender and recipient have access to the shared key. SunScreen SKIP uses shared key algorithms to encrypt packets sent between hosts. SunScreen SKIP protects the security of encrypted information by generating new traffic keys frequently during a communication session, making acquisition of any one traffic key useless.
Public Key Encryption
Public key encryption uses a pair of complementary keys (a public key and a private key) to encrypt and decrypt messages, as shown in the following figure. The two keys are mathematically related such that a message encoded with one key can only be decoded with the other key. Although a user's public and private keys are mathematically related, knowledge of a public key does not make it possible to calculate the corresponding private key.
Figure B-3 Complementary Public and Private Keys
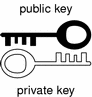
In public key encryption systems, users make their public key available to anyone and keep their private key secret. When one user wants to send a private message to another user, the sender looks up the recipient's public key and uses it to encrypt a message, as shown in the following figure, before sending it to the recipient.
Figure B-4 Sender Uses Recipient's Public Key to Encrypt Message
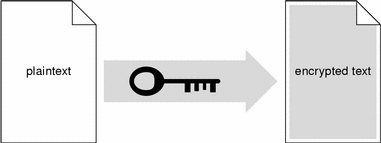
When the encrypted message arrives, the recipient uses his or her private key to decrypt the message, shown in the following figure. Because the recipient's private key is known only to the recipient, both the sender and recipient can safely assume that no one other than the recipient can read the message.
Figure B-5 Recipient Uses Private Key to Decrypt Message
Public key encryption algorithms are mathematically more complex than shared key encryption algorithms. As a result, public key encryption is significantly slower than shared key encryption. Consequently, SunScreen SKIP uses Diffie-Hellman key pairs (described in the next section) to create a shared secret between two users, and then uses shared key encryption to encrypt traffic traveling between the two hosts.
- © 2010, Oracle Corporation and/or its affiliates
