Security Considerations
A company's assets are at risk when it connects to the Internet. It might want to provide Internet services for customers and other users of the Internet, while allowing its employees to connect to the Internet for services or access to corporate information.
SunScreen EFS 3.0 divides the world into discrete areas, each served by an interface. You set up filtering rules to control the access to one area from another area, which can be another network within your company or an area outside your company.
The following figure shows a sample map of a simple network in which a Screen in routing mode functions as a firewall and router to connect the Engineering network over an unsecured public network (the Internet) through a Screen in stealth mode to other secure networks.
Figure 2-1 Sample Network Map
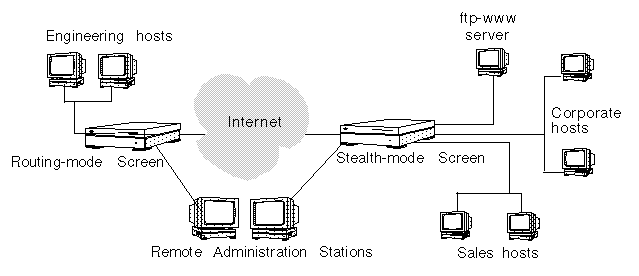
The ftp-www server might be the "public" area of the company, also called the demilitarized zone (DMZ), and the engineering, sales, and corporate network segments might be part of the "private" area. SunScreen EFS 3.0 can then control access between these areas and the rest of the Internet.
A security policy is the collection of decisions an organization makes about network security and its stance regarding what network activities are permitted or denied. The most important aspect in installing and administering a firewall is a well-defined security policy.
When defining your security policy, consider the following factors:
-
To what services do employees need access?
-
To what services or information do customers or other Internet users need access?
-
Against what or whom are you trying to protect your company?
A security policy is a protective device; therefore, it is necessary to determine what you are trying to protect and from whom. Once you have identified your security requirements for protecting the integrity and accessibility of your corporate data and computer resources, determine what services you want to support at your site for employees and customers.
To help determine your requirements, use the following questions:
-
Do users need to transfer files outside the organization?
-
Will users be downloading files from sites outside your own network?
-
What access to corporate data (that is, customer support or product information) do you provide customers?
-
Who needs to log in remotely from other locations?
-
Will you need to use "private" addresses so that you can:
-
Support more Screens or subnetworks than are available from your Internet Service Provider (ISP)?
-
More easily renumber your network and Screens, should you change ISPs?
-
Use unregistered Internet addresses?
-
Once you have determined the answers to these and any other site-specific security issues, you are ready to plan your SunScreen EFS 3.0 configuration.
Policy rules are used to control access to your computer network and to control encryption for access to your data. By default, SunScreen EFS 3.0 drops any packets that do not specifically match a rule. This makes it easier to create rules, since you only have to write a rule for the services you want to pass.
To prepare to implement policy rules, you must:
-
Identify the overall services available on your network
-
Identify the services available to a particular user or Screen or to a group of users and their IP addresses
Note -Take care when defining Screen names. See "Define Screen's Name Properly."
-
Determine the correct action for the services and addresses for each user or Screen
See the SunScreen EFS 3.0 Administration Guide for worksheets to assist you in gathering the information you need for setting up your security policy.
Define Screen's Name Properly
SunScreen EFS 3.0 automatically chooses a name for each Screen based on the hostname setting output by uname -n. There are various situations in which this name is used as an IP host name (IP address) for remote administration and centralized management groups.
Therefore, it is necessary for each Screen's name to be defined as a valid IP address for that Screen. The definition must be accessible through /etc/hosts, NIS or DNS on every remote administration station as well as every Screen in a centralized management group.
- © 2010, Oracle Corporation and/or its affiliates
