Elements of the Administration GUI
The administration GUI for SunScreen EFS 3.0 is organized as a set of pages. Each page consists of one or more controls. For example, most pages include buttons and text fields, which you update using your keyboard and workstation mouse.
Note -
All information regarding the command-line interface is in Appendix B of this manual.
Welcome Page
The SunScreen EFS 3.0 Welcome page opens when you type http://localhost:3852 , http://ScreenName:3852 in a supported browser.
The Welcome page logs you into the administration GUI. The default user name and password is admin and admin, respectively.
Delete or change the password for the default login account as soon as possible to prevent unauthorized access to the Screen's policies.
For a description on how to change passwords, see the SunScreen EFS 3.0 Administration Guide.
Once you are logged in, the first page shows buttons on the top banner: Logout, Policies, Information, and Documentation; two instructions follow the top banner that say: "To edit a policy select one from the table and click the "Edit" button," and "For other tasks select from the top area buttons"; a banner follows titled "Policies List"; and below the Policies List banner is a table.
The table shows the Name of your policy, Version number, if present, and Active Policy Information, if present.
Beneath the table you have a choice of buttons: Add New..., Edit, Copy..., Rename..., Delete..., Activate, Backup All..., Restore All..., Initialize HA..., and Help...
-
Click the buttons on the Information area of the negotiation banner to display logs and operating statistics for the Screen.
-
Click the Logout button when you are finished configuring or monitoring the Screen.
Note -The Add New... choice list has text that is cut off when using a browser under Microsoft Windows for remote administration. This does not affect any operations and the system can continue to be used.
The Add New choice list should display the following items:
-
Generate Screen Certificate...
-
Load Issued Key Certificate...
-
Load Issued Public Certificate...
-
Associate MKID...
-
New Group...
The following figure shows the Welcome page.
Figure 3-1 SunScreen EFS 3.0 Welcome Page
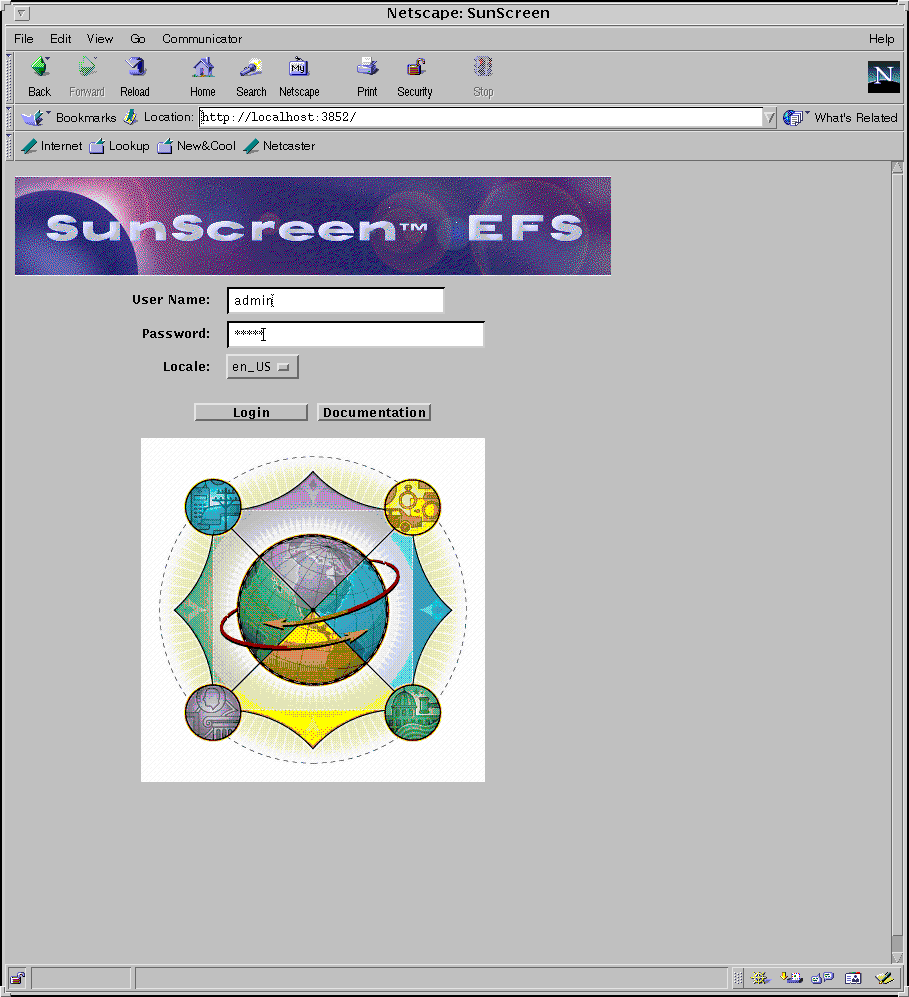
The following table describes the fields in the Welcome page.
Table 3-1 Welcome Page Fields|
Fields |
Description |
|---|---|
|
User Name |
Type your user name. The default user name is admin. |
|
Password |
Type the password associated with your user name. The default user password is admin. |
|
Locale |
Select the locale for the Screen. The default is en_US. |
|
Login |
Opens the SunScreen EFS 3.0 administration graphical users interface Policy List page. |
Administration GUI Negotiating Buttons
The top-most area of the Policies List page contain buttons for Logout,Policies, Information, and Documentation. These buttons are explained the in the following table.
Table 3-2 Negotiating Buttons|
Buttons |
Description |
|---|---|
|
Logout |
Log out of the SunScreen EFS 3.0 session, which clears any lock you may be holding. |
|
Policies |
Open the Edit Rules page, where you create and edit the policy rules for SunScreen EFS 3.0. |
|
Information |
Open the Information page, which displays product information and HA status. |
|
Documentation |
Open the Documentation page, which contains links to the online SunScreen EFS 3.0 documentation. |
Back and Forward Buttons
Use the Back and Forward buttons in the browser negotiation banner to move from the current page to either a previous or a next page, as available.
Documentation
Online documentation for SunScreen EFS 3.0 can be accessed by clicking the Documentation button on the administration GUI negotiating buttons.
Help System
The Help button displays context-sensitive help for the page you are on. It brings up a new browser window, which you can quit to get back to your page or move it aside and keep it open for quick reference.
Policies List Page
The Policy List page identifies the policies that have been stored for a Screen. The Policies List page allows you to add, copy, rename, verify, delete, backup, and restore your policy (see the Administration Guide for procedures). The following figure shows the Policies List page.
Figure 3-2 Policies List Page
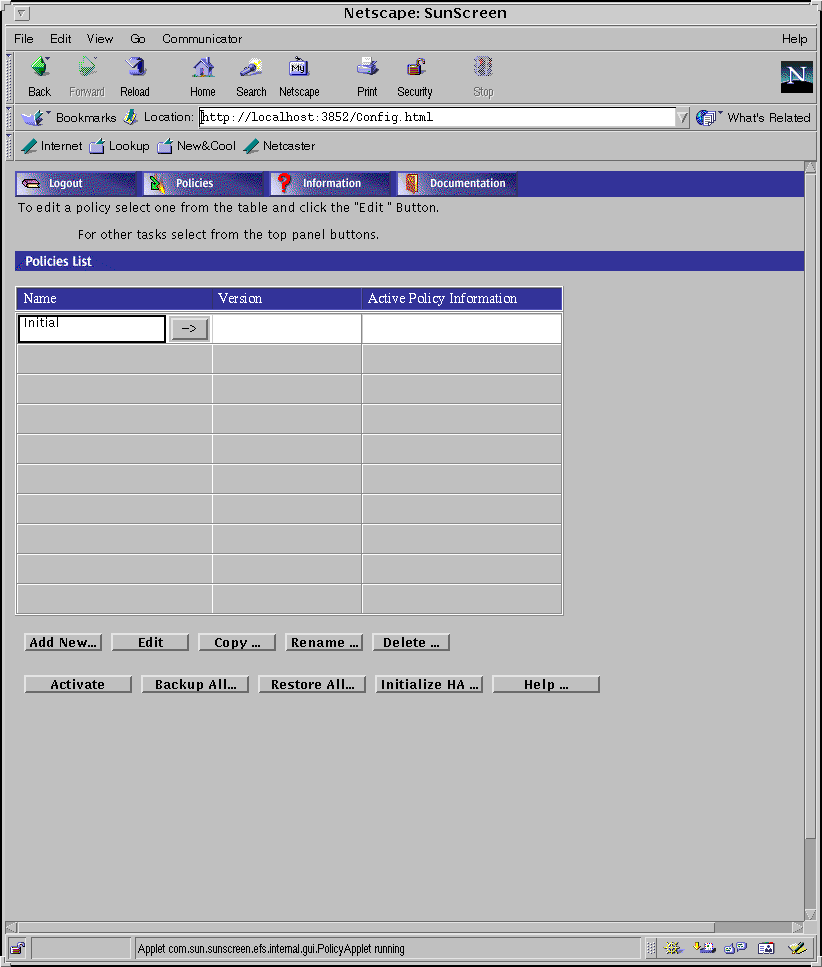
Note -
Changes made to the Policy List page take effect immediately. You cannot use the Revert Changes button to undo changes you make in this page.
The following table describes the controls available on the Policy List page.
Table 3-3 Controls on the Policy List Page|
Control |
Description |
|---|---|
|
Policy list |
Lists the policies that have been set up for your SunScreen EFS 3.0. You can manipulate Screen policies by selecting an entry in the Policy List and then clicking one of the buttons in the Policy List page. |
|
Add New button |
Opens a dialog window that prompts you for the name of the policy you want to add. |
|
Edit button |
Opens the Policy Edit page and allows you to manipulate the policy. |
|
Copy button |
Opens a dialog window that prompts you for the name of the policy to which you want to copy the information in the selected policy. |
|
Rename button |
Opens a dialog window asking for the new name you want to assign to the selected policy. |
|
Delete button |
Opens a dialog window asking you to confirm you want to delete the selected policy. |
|
Activate button |
Activates the selected policy for the Screen. After you click the Activate rule, the Config Name field in the Active Policy page turns green. |
|
Initialize HA button |
Opens the Initialize HA page. |
|
Help button |
Opens the topical help for Policy List page. |
|
Backup All button |
Opens the Backup All window, which lets you copy the SunScreen EFS 3.0 policy to a file or diskette. You cannot use the Backup All button you are using a browser whose security restrictions do not allow access to the file system from applets. |
|
Restore All button |
Opens the Restore All window, which lets you restore a SunScreen EFS 3.0 policy from a file or diskette. You cannot use the Restore All button if you are using a browser whose security restrictions do not allow access to the file system from applets. |
|
Version -> button |
Lists the different policy versions set up for your system. When you click on the Version -> button, it shows the different versions available for the selected policy, and changes to a left (<-). To remove the version information, click again and it reverts back to a right (->). |
Policy Edit Page
The top area, below the Logout, Policies, Information, and Documentation negotiating buttons, is the Common Objects area where you control the policies global and Screen-specific objects. The bottom area is the Policy Rules area where you establish rules for Packet Filtering, Administrative Access, NAT, or VPN.
The following figure shows the Policy Edit page.
Figure 3-3 Policy Edit Page
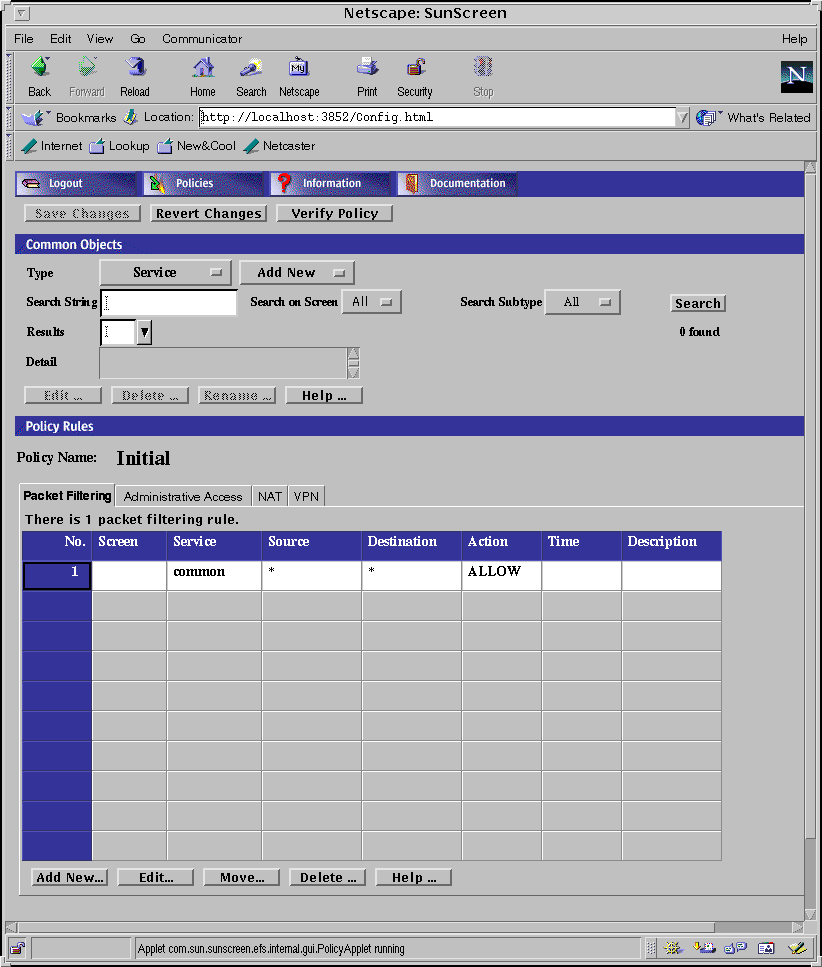
Note -
The choice list for the Action button disappears on Screens with low graphics resolution. A similar problem is seen when resizing the window, for example, the Edit Rule window. The problem goes away when you click the Cancel button and then reopen the window. You can type the first letter of the keyword in the ACTION combo box, such as the uppercase first letter (A, D, S, or E). The system automatically completes the keyword as the first letters are all unique. There are only four known keywords, which are all case sensitive: ALLOW, DENY, SECURE, and ENCRYPT.
Common Objects Area
Common objects are the components you use to make up policy rules. Before you write these rules, you add the common objects that you plan to use in the rules.
Note -
After the common objects have been added, they are stored in a database and can be used over again to create rule sets for additional policies.
Save Is Not Required With Some Common Objects
Some of the common objects that appear in the administration GUI are automatically saved when they are edited or new objects are added. You do not need to save these objects. Once these objects are added or edited, the change applies immediately and is not revertible. The reason the Save button in the administration GUI does not become active when you alter these is because there is no in-memory buffer of unsaved changes.
Note -
Although the changes made to these objects are saved immediately, they do not (except for logmacro) take effect until the next activation. The administration GUI edits Authorized Users, which are authuser objects, Proxy Users, which are proxyuser objects, and Jar Signatures and Jar Hashes, which are both vars objects.
Common Objects with this behavior are:
-
Authorized User
-
Admin User
-
Jar Signature
-
Jar Hash
-
Proxy User
Common Objects
-
Service -- Policy object that lets you identify network services for which you want SunScreen EFS 3.0 to filter packets. You can define:
-
Single Service -- Lets you add new network services and control the filtering activities applied when a service is used in a rule. Control the filtering activities by specifying what packet filtering engine you want to use and the various discriminators and parameters applicable to that filtering engine.
-
Use the fields in the dialog window to type the configuration information for the Service.
Name -- Specifies the name of the service object.
Note -
If you are adding a new Service Object, either through command-line or the administration GUI and specify that you want to set the PARAMETERS but do not provide the information for these paramaters, the configuration editor dumps core. (You cannot specify a negative value for one of the parameters.) If you are using the administration GUI when this happens, it can hang as it cannot recover from the failed editing session. Make sure you always specify a PARAMETER value when specifing the use of parameters for a new service.
Description -- (Optional) Provides a brief description about the service object.
Screen -- Specifies which Screen recognizes the service object.
Use the Filter table to define the filtering activities:
Filter -- Identifies the packed filtering engine.
Port -- Identifies the port, program number, or type used by the forward filter.
Broadcast -- Determines whether the rules where the service is used allows communication to broadcast and multicast addresses.
Note -
If you want the service to work for non-broadcast addresses, type separate table entries for broadcast and non-broadcast filtering.
Parameters -- Identifies the port, program number, or type used by the Reverse filter.
Reverse -- Determines whether the filter applies to packets originating from the host in the To address of a rule and going to the From address of a rule.
Use the fields in the dialog window to type the configuration information for the service group.
Name -- Specifies the name of the service object.
Description -- (Optional) Provides a brief description about the service object.
Screen -- Specifies which Screen recognizes the service object.
Adding services to a service group:
1.Highlight the services you want in the Services list.
2.Choose Add to add the service to the Members list.
-
Address -- The address object for a range of addresses lets you associate a contiguous range of IP addresses with an address object name. For example, you can associate a name with a specified network address range and then use that name to filter traffic to all hosts on that network.
Use the fields in the Address dialog window to type the configuration information address object.
Name -- Specifies the name for the address object.
Description -- (Optional) Provides a brief description about the address object.
Screen -- Specifies which Screen recognizes the address object. The default is All.
Starting IP Address -- Specifies the starting IP address in the range.
Ending IP Address -- Specifies the ending IP address in the range.
-
Single Host
The address object for a single host lets you associate an individual host's address with the address object name in the Name field. Use the fields in the dialog window to type the configuration information for the rule.
Name -- Specifies the name for the address object.
Description -- (Optional) Adds a note about the address object.
Screen -- Specifies which Screen recognizes the address object. Default is All.
IP Address/Host Name -- Specifies the IP address of the host machine. To type an IP address in the address field you can do one of the following: Type the address directly into the field, or type the host name and use Lookup IP Address to get the host's IP address.
The address object for a range of addresses lets you associate a contiguous range of IP addresses with an address object name. For example, you can associate a name with a specified network address range and then use that name to filter traffic to all hosts on that network.
Use the fields in the Address dialog window to type the configuration information address object.
Name -- Specifies the name for the address object.
Description -- (Optional) Provides a brief description about the address object.
Screen -- Specifies which Screen recognizes the address object. Default is All.
Starting IP Address -- Specifies the starting IP address in the range.
Ending IP Address -- Specifies the ending IP address in the range.
The address object for a group of addresses lets you group host addresses, address ranges and other address groups. By grouping addresses that use similar services and have similar actions, you can use groups to save time when creating rules.
Note -
Before you create an address group, you first define the address objects-- single addresses, address ranges, or address groups-- that you want to use in the address group.
Use the fields in the dialog window to type the configuration information for the address object.
Name -- Specifies the name for the address object.
Description -- (Optional) Provides a brief description about the address object.
Screen -- Specifies which Screen recognizes the address object. The default is All.
Addresses -- Displays the addresses objects that can to be used to create the address group.
Include List -- Specifies the address objects that are currently included in the address group. Use the Add or Remove buttons to modify the list.
Exclude List -- Specifies the address objects that are excluded from the address group. For example, you can create an address group that includes all addresses except as specified in the Exclude List. Use the Add or Remove buttons to modify the list.
-
Certificate -- Certificate is a Common Object that allows you to manage certificates. You can:
-
Generate Certificate
-
To generate a certificate, use the fields in the dialog window to type the configuration information.
Name -- Specifies a name for the certificate.
Description -- (Optional) Provides a brief description about the certificate object.
Screen -- Specifies which Screen recognizes the Certificate Object. The default is All.
Installed On -- (Optional) Specifies the Screen on which the certificate is installed.
Radio buttons -- Specify the level of encryption that the Screen uses.
Generate New Certificate -- Generates the certificate. The Certificate ID field displays the certificate's certificate ID.
Also called the certificate ID, lets you assign a name to a certificate that exists on another machine. You associate a certificate ID when you want to encrypt communication between two screens or between a screen and an Administration Station.
Use the fields in the dialog window to type the information for associating the MKID.
Name -- Specifies the name for the certificate ID object.
Description -- (Optional) Provides a brief description about the certificate ID object.
Screen -- (Optional) Specifies which Screen recognizes the certificate ID object. The default is all. Specifying a Screen allows you to define packet filtering rules that encrypt traffic between any two machines, not just between an Administration Station and a Screen.
Certificate ID -- Specifies the certificate ID (hash value) for the certificate that you generated on the other system.
Associate MKID (also called the certificate ID) lets you assign a name to a certificate that exists on another machine. You associate a certificate ID when you want to encrypt communication between two screens or between a Screen and an Administration Station.
Use the fields in the dialog window to type the information for associating the certificate ID.
Name -- Specifies the name for the certificate ID object.
Description -- (Optional) Provides a brief description about the certificate ID object.
Screen -- (Optional) Specifies which Screen recognizes the certificate ID object. The default is all.
Note -
Specifying a Screen allows you to define packet filtering rules that encrypt traffic between any two machines, not just between an Administration Station and a Screen.
Certificate ID -- Specifies the certificate ID (hash value) for the certificate that you generated on the other system.
-
Screen -- Allows you to edit or add Screen objects. You can edit miscellaneous Screen parameters, SNMP parameters, and Mail Proxy parameters for Screen objects that already exist.
In general, you edit rather than create Screen objects because they are automatically created during installation. However, you create new Screen objects to configure HA and centralized management.
Note -
You must enter the name of the Admin Interface of the Screen as listed in the Naming Service or in the hosts file.
Create a Screen object if you are setting up an HA cluster or centralized management group.
The HA/Master Config tab allows you to associate a certificate object with a Screen or Administration Station that is part of an HA cluster or a centralized management group. The HA menu and the Primary Name menu determine the role a Screen has within an HA cluster and centralized management group. The settings you choose for these menus determines which other controls on the HA/Master Config tab are active. The meanings and uses of the fields in the HA/Master Config tab are as follows:
High Availability -- Specifies whether the Screen is used for HA. If you are using it for HA, you can specify whether the Screen is a primary HA Screen or a secondary HA Screen.
Primary Name -- Specifies the name of the primary Screen.
Administrative IP -- Address IP address of the Screen that is used for administration.
Administration Certificate -- Specifies the Administration Station's certificate name.
High Availability IP Address -- Specifies the IP address of the HA interface.
Ethernet Address -- Generated by the system.
Key Algorithm -- Specifies the issued certificate (key) encryption algorithms supported for SunScreen SKIP, version 1.
Data Algorithm -- Specifies the data encryption algorithms supported for SunScreen SKIP, version 2.
MAC Algorithm -- Specifies the MAC (authentication) algorithms supported for manual keying.
Note -
The entry in the Name field must be the same as the entry that exists in the nameservice lookup or in the /etc/hosts file. The IP address associated with this name must match the IP address of the administrative interface.
Note -
The type of interfaces must be the same on all the machines in the HA cluster. This interface must be dedicated on each machine in the HA cluster with a dedicated network connection. For reasons of security, the HA network should not be connected to any other network. The HA primary Screen is always the Screen you administer whether it is the active or passive Screen.
Use the Miscellaneous, SNMP, and Mail Proxy tabs in the Screen dialog window to edit a Screen object.
Note -
After configuring the Screen as an HA primary remotely administered by an Administration Station (it is not part of the Centralized Management Group), the administration GUI does not show the admin certificate in the "HA/Master Config" panel from the Screen object. If you click OK from that panel, the admin certificate information is deleted from the Screen object. The result is that the activation fails because of the missing admin certificate. Use the command line to make any needed changes to the primary HA Screen object.
The Miscellaneous tab in the Screen dialog window allows you to specify miscellaneous Screen parameters.
Log Size
Stealth Network Address -- Specifies the network address for interfaces that are used as SPF interfaces. Type this parameter if you have used the Interface object to designate any Screen interfaces as Stealth interfaces.
Stealth Netmask -- Specifies the netmask for interfaces that are used as SPF interfaces. Type this parameter if you have used the Interface object to designate any Screen interfaces as Stealth interfaces.
Routing -- Specifies whether the Screen is used for routing.
Name Service -- Specifies the name service that the Screen uses.
Certificate Discovery -- Specifies whether the Screen uses Certificate Discovery.
The SNMP tab in the Screen dialog window allows you to add, edit, or delete an SNMP trap receiver.
Note -
Use the Action field of the packet filtering Rule Definition dialog window to specify actions that generate SNMP alerts. The machine that you want to receive SNMP trap alerts must not be a remote Administration Station.
The Mail Proxy tab in the Screen dialog window allows you to add, edit, or delete domains known to distribute unsolicited electronic mail (spam). You can define spam domains if you use an SMTP proxy.
Centralized management allows you to remotely administer configurations on a group of Screens. A centralized management group comprises a primary Screen and a number of secondary Screens. The primary Screen's function is to "push" policy configurations to the secondary Screens in the group.
Note -
You can configure packet filtering rules to make a specific rule apply to only one Screen. The rules apply globally by default.
Note -
The entry in the Name field must be the same as the entry that exists in the nameservice lookup or in the /etc/hosts file. The IP address associated with this name must match the IP address of the administrative interface.
-
Interface -- A Common Object that lets you define interfaces and specify the actions a Screen should take when a packet, which is received on that interface, is rejected.
Use the fields in the dialog window to type the configuration information for the interface object.
Name -- Specifies the name for the address object.
Type -- Specifies the type of interface.
Screen -- Specifies which Screen recognizes the Interface.
Address Group -- Specifies the valued source IP addresses for this interface.
Logging -- Identifies the level of detail for log messages generated when a packet received on the interface is rejected.
Note -
You can override the level of log messages that are issued for individual rules.
SNMP Alerts -- Indicates whether SNMP alert messages are issued when a packet received on the interface is rejected.
SNMP traps -- Addressed to the defined hosts.
ICMP Action -- Identifies the ICMP rejection message that is issued if a packet received on the interface is rejected. The default is none.
Comment -- (Optional) Provides a descriptive note about the Interface object.
-
Proxy User -- A Common Object that contains the mapping information for users of SunScreen EFS 3.0 proxies. The FTP and telnet rules reference the proxy user entries.
Before you add a proxy user, define an authorized user. You must create entries for both authorized users and proxy users to use the authentication feature of the FTP and telnet proxies.
Name -- Specifies the name of the proxy user.
Description -- Adds a brief description of the proxy user.
User -- Enabled Controls whether the user can log into the Screen.
Authorized User Name -- Selects the name of the authorized user to be used to authenticate this proxy user. Names in this list are generated when you add an Authorized User Object. If this field is empty, authorization is not required for this user.
-
Authorized User -- A Common Object that lets you specify which users are allowed to use the telnet and FTP proxy.
Use the fields in the dialog window to type the configuration information for the Authorized User Object.
User Name -- Specifies the login name of the authorized user.
Description -- (Optional)Provides a brief description about the authorized user.
User Enabled -- Indicates whether the user can log into the Screen.
Password -- Specifies the login password for the authorized user.
Retype Password -- Specifies the login password for the authorized user. The password typed in this field must exactly match the password you typed in the Password field.
SecurID Name -- Specifies the user's login name for SecurID authorization.
Real Name -- Identifies the real name of the authorized user.
Contact Information -- Displays information on how to contact the specified user.
-
Administrative User -- A Common Object that lets you identify the administrators authorized to access the Screen.
Use Administrative User Objects when you define Administrative Access rules.
Use the fields in the dialog window to type the configuration information for the Administrative User.
User Name -- Specifies the login name of the administrative user.
Description -- (Optional) Provides a brief description about the administrative user.
User Enabled -- Indicates whether the user can log into the Screen.
Password -- Specifies the login password for the administrative user.
Retype Password -- Specifies the login password for the administrative user. The password typed in this field must exactly match the password you typed in the Password field.
SecurID Name -- Specifies the user's login name for SecurID authorization.
Real Name -- Identifies the real name of the administrative user.
Contact Information -- Displays information on how to contact the specified user.
After you create the Administrative User Object, you grant administrative access by creating a rule in the Administrative Access panel.
Note -
The name that you create for the Administrative User object is the same name that you use when you create an Administrative Access rule.
-
Jar Signature -- Lets you identify the Java archives (JARs) you want the Screen to pass. JAR signatures apply only to the HTTP proxy.
Use the dialog window to type the information for the JAR signature.
Certificate Name -- Identifies the name of the certificate.
Master Key ID -- Identifies the certificate ID.
Load Jar Certificate -- Loads the certificate used to authenticate the Java archive.
-
Jar Hash -- The HTTP proxy can be set up to filter the Java applets based on the Jar hash value of the Jar file.
Use the fields in the dialog window to type the information for the Jar hash.
Certificate Name -- Identifies the name of the certificate.
Master Key ID -- Identifies the certificate ID.
-
Time -- A Policy Object that lets you specify when a rule applies. You can specify the time of day and day of the week.
Use the fields and controls in the dialog window to type the configuration information for the Time Object.
Name -- Specifies a name for the Time Object.
Description -- (Optional) Adds a descriptive note about the Time Object.
Screen -- Specifies which Screen recognizes the Time Object.
Note -
The Time Object is based on a 24-hour clock. The time 00:00 is midnight on the day specified; the time 24:00 is midnight 24 hours later.
Policy Rules Page
SunScreen EFS 3.0 uses ordered sets of rules to implement the security policies for your site. Ordered set of rules means that, when a Screen receives a packet, it matches the packet against each rule in its active policy until it finds one that applies, and then takes the actions associated with that rule. Once a Screen finds an applicable rule for a packet, it ignores subsequent rules in its active policies.
Rules do not take effect until you save and activate the policy to which they belong by clicking the Save Changes button located above the Common Objects area, and the Activate button in the bottom area of the Policy List page. SunScreen EFS 3.0 sets up the basic security policy for name service lookups, Routing Information Protocol (RIP) packets, and SunScreen SKIP certificate discovery during installation. You can use the Rules area on the Policy Rules page to specify how your Screen should filter other types of packets.
Note -
If the specified filtering rule fails to detect any issued certificate (key) encryption algorithms, it may display the following error message: An error occurred in detecting the Encryption algorithms. Please check if skipd process is running.If this occurs, use the skipd_restart command to restart the skipd process.
The Policy Rules page lets you add or modify a rule in the SunScreen EFS 3.0 policy. It opens when you click the Add New button (or when you select a rule and click the Edit button) in the Common Objects page.
Some pages use tabs to organize sets of related controls. To display the controls on a tab, click the tab header. The rules area contains four tabs: Packet Filtering, Administrative Access, NAT, and VPN as described in the following sections. The following table describes the four tabs.
The following table describes the tabs that are available from the Policy Rules page.
Table 3-4 Policy Rules Page Tab Items|
Tab |
Description |
|---|---|
|
Packet Filtering |
Shows the packet filtering rules(s). |
|
Administration Access |
Defines access rules for local administration and remote Administration Stations through the administration GUI or the command line (see Appendix B). |
|
NAT |
Maps private network addresses to public network addresses. |
|
VPN |
Maps name, address, certificate, issued certificate (key) algorithm, data algorithm, MAC algorithm, tunnel address, and description. |
Packet Filtering Rules
The Packet Filtering tab brings up a panel that allows you to configure packet filtering rules. Use packet filtering to control traffic using a particular service, traffic intended for a particular service, or traffic coming from a particular address.
SunScreen EFS 3.0 uses ordered packet filtering. The Screen assumes that the first rule that matches a packet is the rule that governs the disposition of the packet.
If the packet does not match any rule, the Screen uses its default action to determine the disposition of the packet. Typically, the default action logs the packet and drops it, though other options are available.
The following table describes the available fields in the Packet Filtering tab.:
-
Rule Index (No) -- (Optional) Assigns a number to a rule. By default, this field displays a number one greater than the last rule (indicating this rule will be placed at the bottom of the list). If you type a lower number, the new rule is inserted into the specified position in the list, and the rules currently in the configuration are renumbered.
-
Screen -- (Optional) Specifies the Screen for which you want the rule to apply. Type a specific Screen name in this field if you use centralized management and want a rule to apply to a specific Screen.
-
Service -- Identifies the network service or service group to which this rule applies. Network services and service groups are described in Appendix B, "Services and State Engines."
-
Source -- The value to which the source address of a packet is compared. If an asterisk (*) appears, any source address meets the criteria of the rule.
-
Destination -- The value to which the destination address of a packet is compared to determine whether the rule should apply. If an asterisk (*) appears, any destination address meets the criteria of the rule.
-
Action -- Displays the action for the rule: ALLOW, DENY, ENCRYPT, and SECURE.
-
Time -- Specifies the time of day for the rule.
-
Description -- (Optional) Provides a brief description of the Administrative Access rule.
Administrative Access Rules
Administrative Access rules allow you to specify access and encryption settings for local and remote Fm Variable:Filename (Short) administrators.
Local Administrative Access
The Local Access Rules dialog window lets you add or modify administrative access rules for local Administration Stations. Use the fields in the dialog window to type the configuration information for the rule.
-
Rule Index (No) -- (Optional) Assigns a number to a rule. By default, this field displays a number one greater than the last rule (indicating this rule will be placed bottom of the list). If you type a lower number, the new rule is inserted into the specified position in the list, and the rules currently in the configuration are renumbered.
-
Screen -- (Optional) Specifies the Screen for which you want the rule to apply. Type a specific Screen name in this field if you use centralized management and want a rule to apply to a specific Screen.
-
User -- Lists the user names of SunScreen EFS administrators. Use the names that you defined for the Administrative User object.
-
Access Level -- Specifies what actions the designated user can perform:
-
ALL -- Allows administrator to display and modify all setting for the Screen.
-
WRITE -- Administrator can perform all operations except modifying the Administration Access rules for any Policy.
-
READ -- Administrator can view both the Information and Policy. This level also allows the user to save and clear logs on the information page. With this access level users cannot modify any Policy data.
-
STATUS -- Administrator can display status information (logs, statistics, status information) but cannot display or modify management settings.
-
NONE
-
-
Description -- (Optional) Provides a brief description of the Administrative Access rule.
Remote Administrative Access
The Remote Access Rules dialog window lets you add or modify administrative access rules for remote administration stations. Use the fields in the dialog window to type the configuration information for the rule.
-
Rule Index (No) -- (Optional) Assigns a number to a rule. By default, this field displays a number one greater than the last rule (indicating this rule will be placed bottom of the list). If you type a lower number, the new rule is inserted into the specified position in the list, and the rules currently in the configuration are renumbered.
-
Screen -- (Optional) Specifies the Screen for which you want the rule to apply. Type a specific Screen name in this field if you use centralized management and want a rule to apply to a specific Screen.
-
Address Object
-
User -- Lists the user names of SunScreen EFS administrators. Use the names that you defined for the Administrative User object.
-
Encryption -- Specifies the version of SunScreen SKIP being used to encrypt traffic between the Screen and the Administration Station.
-
Certificate Group -- Specifies the name of the certificate group allowed in over this interface, which can correspond to a single certificate or a certificate group.
-
Key Algorithm -- Identifies the algorithm used to encrypt traffic-encrypting issued certificates (keys). The algorithms available depend on the version of SunScreen EFS (U.S.&Canada, Export Controlled, or Global) you are using.
-
Data Algorithm -- Identifies the algorithm used to encrypt message traffic between the Screen and the Administration Station. The algorithms available depend on the version of SunScreen EFS (U.S/Canada,Export Controlled, or Global) you are using.
-
MAC Algorithm -- Identifies the algorithm used to authenticate traffic.
-
Tunnel -- Identifies the Tunnel address used for the communication between the remote Administration Station and the Screen.
-
Access Level -- Specifies what actions the designated user can perform:
-
ALL -- Administrator can display and modify all setting for the Screen.
-
WRITE -- Administrator can perform all operations except modifying the Administration Access rules for any Policy.
-
READ -- Administrator can view both the Information and Policy. This level also allows the user to save and clear logs on the information page. With this access level users cannot modify any Policy data.
-
STATUS -- Administrator can display status information (logs, statistics, status) but cannot display or modify management settings.
-
NONE
-
-
Description -- (Optional) Provides a brief description of the remote administrative access rule.
NAT Rules
The Network Address Translation (NAT) tab allows you to set up mapping rules to translate IP addresses according to specific rules. These rules interpret the source and destination of incoming IP packets, then translate either the apparent source or the intended destination, and send the packets on. You can map hosts, lists of addresses, ranges of addresses, or specific groups, depending on what you have configured in your EFS 3.0 installation. See Address Common Object to define addresses, ranges, or groups of addresses.
In general, you would map addresses to:
-
Ensure that internal addresses appear as registered addresses on the Internet, or
-
Send traffic for a specific destination to a different, pre-determined destination.
It is not possible to translate both source and destination addresses-- that is, to make packets appear to come from a different IP address and to simultaneously direct the packets to a different destination.
When defining NAT rules, the first rule (lowest number) that matches a packet wins, and no other rules can apply. Therefore, you might define specific rules first, then broader cases later.
The meanings and uses of the specific fields in the NAT screens are as follows:
-
Rule Index (No) -- Assigns a number to a rule. By default, this field displays a number one greater than the last rule (indicating this rule will be placed at the end of the list). If you type a specific number, the new rule is inserted into that position in the list, and the rules currently in the configuration are renumbered.
-
Screen -- Specifies the Screen for which you want the rule to apply. Type a specific Screen name in this field if you use centralized management and want a rule to apply to a specific Screen.
-
-
Static -- Specify static mapping to set up a one-to-one relationship between two addresses. You could use this to set new apparent IP addresses for hosts on your network without having to reconfigure each host, for example.
-
Dynamic -- Specify dynamic mapping to map source addresses to other addresses in a one-to-many relationship. You could use dynamic mapping to ensure that all traffic leaving the firewall appears to come from a specific address or group of addresses, or to send traffic intended for several different hosts to the same actual IP access.
-
-
Source -- Specify the source address to map from an untranslated packet. Source addresses are the actual addresses contained in the packet entering the firewall.
-
Destination -- Specify the untranslated destination address for the source packet. Destination addresses are the actual addresses contained in the packet entering the firewall.
-
Translated Source -- Specify the translated source address for a packet. The translated source is the address the packet appears to originate from.
-
Translated Destination -- Specify the translated destination packet address. The translated destination is the actual address the packet goes to after it leaves the firewall.
-
Description -- Used to provide a description of the mapping defined in this rule.
As you define rules, remember that you cannot translate both source and destination addresses. You must either translate packets so they appear to come from a different source, or translate packets so they go to a specific destination, but not both.
All NAT rules are unidirectional -- that is, they work precisely as defined, and are not interpreted as also applying in the reverse direction. If you want rules to apply in both directions, you must specify two different rules. For example, if you map a source address from internalname.com to the destination of publicip.com, you will also have to map a source of publicip.com to the destination of internalname.com to translate traffic in both directions.
Virtual Private Network (VPN) Gateway Rules
The VPN tab allows you to define Virtual Private Network (VPN) gateways. Defining VPN gateways using this mechanism simplifies the creation of VPNs that include more than two gateways.
Note -
Each gateway in this type of configuration must be able to connect to the other ones directly--without going through another gateway.
Defining VPN Gateways
Use the fields in the VPN dialog window to define VPN gateways:
-
Rule Index (No) -- (Optional) Assigns a number to a rule. By default, this field displays a number one greater than the last rule (indicating this rule will be placed bottom of the list. If you type a lower number, the new rule is inserted into the specified position in the list, and the rules currently in the configuration are renumbered.
-
Name -- Specifies the Name of the VPN to which this gateway belongs.
Note -Type the same name in the Name field for each gateway that you include in the VPN.
-
Address -- Specifies the machine to be included in the VPN.
-
Certificate -- Specifies the name of the certificate for this VPN gateway.
-
Key Algorithm -- Specifies the issued certificate (key) algorithm the VPN uses.
All gateways in the same VPN must use the same issued certificate (key) algorithm.
-
Data Algorithm -- Specifies the data algorithm the VPN uses.
All gateways in the same VPN must use the same data algorithm.
-
MAC Algorithm -- Specifies the MAC algorithm the VPN uses.
All gateways in the same VPN must use the same MAC algorithm.
-
Tunnel Address -- Specifies the destination address on the outer (unencrypted) IP packet to which tunnel packets are sent.
-
Description -- (Optional) Provides a short description of the VPN gateway.
Adding a VPN Rule
After you define the gateways in your VPN, add a Packet Filtering rule for this VPN. The simplest rule uses * for the source and destination address. This rule allows encrypted use of the specified service for all addresses in the VPN.
When you add a packet filtering rule for VPN, leave the Screen field empty.
-
Specify SECURE for the packet filtering action.
-
Type the name of the VPN in the VPN field.
- © 2010, Oracle Corporation and/or its affiliates
