Network Example
For the network example, FIGURE 5-1 shows the Boston and Hong-Kong segments of the network. Looking at the diagram, a VPN is configured between the Boston and Hong-Kong offices. It shows tunnel addresses between the stealth Screen (bos-screen1) and the routing Screen (hk-screen1). SunScreen SKIP encrypts the entire original packet, including the IP header, and inserts a new IP header. The new IP header can use either the same addresses as the original packet or different (or tunnel) addresses.
Figure 6-1 Boston and Hong-Kong Segments
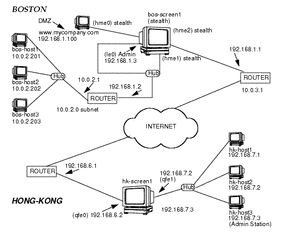
The hosts in Boston have non-routable addresses (10.0.2.0 in this example), so a tunnel address is used to hide these addresses. The stealth Screen in Boston (bos-screen1) has no IP address on its filtering interface (hme2). Thus, when the Screen in Hong-Kong inserts a new IP header on packets destined for bos-screen1, it adds a tunnel address on the 192.168.1.0 subnet and routes the packet over the Internet to the Boston router. Although bos-screen1 does not have an IP address, it responds to ARPs from the Boston router for the tunnel address so the packets from hk-screen1 are passed to bos-screen1 and decrypted.
Encryption and decryption are done by the hk-screen1 and bos-screen1 Screens. Thus, if someone ran snoop on the packets on the Internet, they would only see encrypted IP packets (Protocol 57). While, if someone ran snoop on the packets on the inside of either Screen they would find them unencrypted and using their original IP addresses.
Before you begin this example, set up an open policy on both Screens and confirm that they can communicate.
- © 2010, Oracle Corporation and/or its affiliates
