NAT Examples
The following NAT examples show how to set up NAT when using only one registered IP address, and with two scenarios that illustrate how a demilitarized zone could use registered addresses or unregistered addresses with NAT.
Example One
If you only have one registered IP address (A) and you want to have all inbound traffic go to A, go to your Screen and have all other hosts use that address (A) for unidirectional, outbound traffic. Then set up NAT as shown in the table below.
Table 7-4 Example of a One-Address NAT Table Entry|
Index |
Screen |
TYPE |
Source |
Destination |
Translated Source |
Translated Destination |
Comment |
|---|---|---|---|---|---|---|---|
|
1 |
|
STATIC |
* |
A |
* |
A |
|
|
2 |
|
DYNAMIC |
Inside |
Internet |
A |
Internet |
|
Internet is all addresses on inbound interface A; and Inside is all internal hosts on all other interfaces. With only these NAT rules, all hosts in the Inside communicate with their private, unregistered addresses when communicating with the Screen or among themselves.
Write your filtering rules in the context of the internal addresses.
Example Two
Registered addresses are necessary for advertised kinds of resources, such as publicly accessible servers on your network; consequently, these machines must be at well-known, fixed addresses. Because a host must have a registered address before it can communicate over public networks, machines that host public resources either must have stable registered addresses, or their unregistered (internal) addresses must translate to stable registered addresses. The following scenarios illustrate how a demilitarized zone (DMZ), an internal network with limited public access, could use registered addresses or unregistered addresses with network address translation.
Scenario 1: DMZ Uses Registered Addresses
In the figure below, the Screen, in routing-mode, uses Q1 as its own IP address on the external network interface. It has a DMZ network with registered addresses R1 through R8 on a second interface. The Screen (Q1) and the servers in the DMZ (the FTP server, R2, and the WWW server, R3), have routable registered addresses on the public network that allow them to communicate with any other machine with a registered address. The Screen uses the remaining registered addresses (R4 through R8) for NAT.
Figure 7-1 Scenario 1: Static and Dynamic NAT

The Screen uses dynamic NAT to translate the addresses in its unregistered address range (U2-Un) to the remaining addresses in its registered address range (R4-R8). When an internal host with an unregistered address tries to connect to an external host with a registered address, the Screen assigns the internal host a registered address to use for the duration of the network communication session.
Scenario 2: DMZ Uses NAT Addresses
The figure below illustrates an organization that has a network consisting of a large number of unregistered addresses (Un) and a set of eight registered addresses (R1-R8). Hosts on the inside network must be able to communicate through the Screen with external hosts.
Figure 7-2 Scenario 2: Static and Dynamic NAT
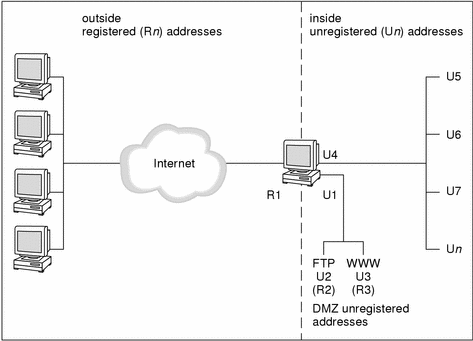
In the figure above, the Screen is connected to the public network R1-R8. R1 is its IP address on the public network interface. It uses static NAT to translate the unregistered DMZ addresses of the FTP server (U2) and the WWW server (U3) to the registered (public) addresses R2 and R3. The private addresses U4 through Un will be translated dynamically to the registered addresses R4 through R8. Because the IP addresses of the servers and the internal network are translated to routable registered addresses, they can communicate with any other registered address.
The Screen uses dynamic NAT to translate the addresses in its unregistered address range (U4-Un) to the remaining addresses in its registered address range (R4-R8). When an internal host with an unregistered address tries to connect to an external host with a registered address, the Screen assigns the internal host a registered address to use for the duration of the network communication session.
This scenario has the advantage that if you change ISPs, you do not have to re-address all the hosts on your internal registered network.
Routing Interface Examples
For routing interfaces, you can select the registered address as the address of one of the Screen's interfaces. In this case, the Screen simulates the registered address. The limitation here is that you only have a single address. Also selecting the interface address as the registered address for a static NAT rule can limit your ability to connect to the Screen itself. Because you are not adding additional networks, no routing changes are required.
For routing interfaces, you can select the unused addresses on one of the networks to which the Screen is directly connected as virtual addresses. In this case, this approach is necessary so that the addresses can respond to ARP requests for these virtual addresses.
For routing interfaces, if you select the virtual addresses from a network not directly connected to the Screen, you must make sure that the correct routing information is propagated so that packets destined for these addresses pass through the Screen. If you define new networks (especially ones in which all the addresses on the network are virtual), you may need to add static routing entries on some routers to simulate these networks.
Stealth Interface Examples
For stealth interfaces, you can select the registered addresses from the list of unused addresses on the network that the Screen segments. In this case, Screen simulates the virtual addresses and responds to ARP requests for those addresses. Since you are not adding additional networks, no routing changes are required.
For example, consider a SunScreen with stealth interfaces that segments the network 199.190.177.0 (netmask 255.255.255.0). In this example, the addresses 199.190.177.100 through 199.190.177.254 are unused and can be used as virtual addresses in network address translations.
For stealth interfaces, you can select the registered addresses from a new virtual network you create. For this to work successfully, you must be able to assign multiple addresses on multiple networks on the routers you use.
- © 2010, Oracle Corporation and/or its affiliates
