Chapter 19 Using Solaris Secure Shell (Tasks)
Solaris Secure Shell enables a user to securely access a remote host over an unsecured network. The shell provides commands for remote login and remote file transfer. The following is a list of topics in this chapter.
For reference information, see Chapter 20, Solaris Secure Shell (Reference). For information on the relationship of Solaris Secure Shell to the OpenSSH project, see Solaris Secure Shell and the OpenSSH Project.
Solaris Secure Shell (Overview)
In Solaris Secure Shell, authentication is provided by the use of passwords, public keys, or both. All network traffic is encrypted. Thus, Solaris Secure Shell prevents a would-be intruder from being able to read an intercepted communication. Solaris Secure Shell also prevents an adversary from spoofing the system.
Solaris Secure Shell can also be used as an on-demand virtual private network (VPN). A VPN can forward X Window system traffic or can connect individual port numbers between the local machines and remote machines over an encrypted network link.
With Solaris Secure Shell, you can perform these actions:
-
Log in to another host securely over an unsecured network.
-
Copy files securely between the two hosts.
-
Run commands securely on the remote host.
Solaris Secure Shell supports two versions of the Secure Shell protocol. Version 1 is the original version of the protocol. Version 2 is more secure, and it amends some of the basic security design flaws of version 1. Version 1 is provided only to assist users who are migrating to version 2. Users are strongly discouraged from using version 1.
Note –
Hereafter in this text, v1 is used to represent version 1, and v2 is used to represent version 2.
Solaris Secure Shell Authentication
Solaris Secure Shell provides public key and password methods for authenticating the connection to the remote host. Public key authentication is a stronger authentication mechanism than password authentication, because the private key never travels over the network.
The authentication methods are tried in the following order. When the configuration does not satisfy an authentication method, the next method is tried.
-
GSS-API – Uses credentials for GSS-API mechanisms such as mech_krb5 (Kerberos V) and mech_dh (AUTH_DH) to authenticate clients and servers. For more information on GSS-API, see Introduction to GSS-API in Solaris Security for Developers Guide.
-
Host-based authentication – Uses host keys and rhosts files. Uses the client's RSA and DSA public/private host keys to authenticate the client. Uses the rhosts files to authorize clients to users.
-
Public key authentication – Authenticates users with their RSA and DSA public/private keys.
-
Password authentication – Uses PAM to authenticate users. Keyboard authentication method in v2 allows for arbitrary prompting by PAM. For more information, see the SECURITY section in the sshd(1M) man page.
The following table shows the requirements for authenticating a user who is trying to log into a remote host. The user is on the local host, the client. The remote host, the server, is running the sshd daemon. The table shows the Solaris Secure Shell authentication methods, the compatible protocol versions, and the host requirements.
Table 19–1 Authentication Methods for Solaris Secure Shell|
Authentication Method (Protocol Version) |
Local Host (Client) Requirements |
Remote Host (Server) Requirements |
|---|---|---|
|
Initiator credentials for the GSS mechanism. |
Acceptor credentials for the GSS mechanism. For more information, see Acquiring GSS Credentials in Solaris Secure Shell. |
|
|
User account Local host private key in /etc/ssh/ssh_host_rsa_key or /etc/ssh/ssh_host_dsa_key HostbasedAuthentication yes in /etc/ssh/ssh_config |
User account Local host public key in /etc/ssh/known_hosts or ~/.ssh/known_hosts HostbasedAuthentication yes in /etc/ssh/sshd_config IgnoreRhosts no in /etc/ssh/sshd_config Local host entry in /etc/ssh/shosts.equiv, /etc/hosts.equiv, ~/.rhosts, or ~/.shosts |
|
|
User account Private key in ~/.ssh/id_rsa or ~/.ssh/id_dsa User's public key in ~/.ssh/id_rsa.pub or ~/.ssh/id_dsa.pub |
User account User's public key in ~/.ssh/authorized_keys |
|
|
RSA public key (v1) |
User account Private key in ~/.ssh/identity User's public key in ~/.ssh/identity.pub |
User account User's public key in ~/.ssh/authorized_keys |
|
User account |
User account Supports PAM, including arbitrary prompting and password changing when password aging is triggered. |
|
|
User account |
User account Supports PAM. |
|
|
.rhosts only (v1) |
User account |
User account IgnoreRhosts no in /etc/ssh/sshd_config Local host entry in /etc/ssh/shosts.equiv, /etc/hosts.equiv, ~/.shosts, or ~/.rhosts |
|
.rhosts with RSA (v1) on server only |
User account Local host public key in /etc/ssh/ssh_host_rsa1_key |
User account Local host public key in /etc/ssh/ssh_known_hosts or ~/.ssh/known_hosts IgnoreRhosts no in /etc/ssh/sshd_config Local host entry in /etc/ssh/shosts.equiv, /etc/hosts.equiv, ~/.shosts, or ~/.rhosts |
Solaris Secure Shell in the Enterprise
For a comprehensive discussion of Secure Shell on a Solaris system, see Secure Shell in the Enterprise, by Jason Reid, ISBN 0-13-142900-0, June 2003. The book is part of the Sun BluePrints Series, which is published by Sun Microsystems Press.
For online information, navigate to Sun's BigAdmin System Administration Portal web site, http://www.sun.com/bigadmin/home/index.jsp. Click Docs, then Sun BluePrints under Misc./Comprehensive. Click Sun BluePrints OnLine, then Archives by Subject, then Security. The archives include the following articles:
-
Role Based Access Control and Secure Shell – A Closer Look At Two Solaris Operating Environment Security Features
-
Integrating the Secure Shell Software
-
Configuring the Secure Shell Software
Solaris Secure Shell and the OpenSSH Project
The Solaris Secure Shell is a fork of the OpenSSH project. Security fixes for vulnerabilities that are discovered in later versions of OpenSSH are integrated into Solaris Secure Shell, as are individual bug fixes and features. Internal development continues on the Solaris Secure Shell fork.
While Sun engineers provide bug fixes to the project, they have also integrated the following Solaris features into the Solaris fork of Secure Shell:
-
PAM - Solaris Secure Shell uses PAM. The OpenSSH UsePAM configuration option is not supported.
-
Privilege separation - Solaris Secure Shell does not use the privilege separation code from the OpenSSH project. Solaris Secure Shell separates the processing of auditing, record keeping and re-keying from the processing of the session protocols.
Solaris Secure Shell privilege separation code is always on and cannot be switched off. The OpenSSH UsePrivilegeSeparation option is not supported.
-
Locale - Solaris Secure Shell fully supports language negotiation as defined in RFC 4253, Secure Shell Transfer Protocol. After the user logs in, the user's login shell profile can override the Solaris Secure Shell negotiated locale settings.
-
Auditing - Solaris Secure Shell is fully integrated into the Solaris auditing subsystem. For information on auditing, see Part VII, Solaris Auditing.
-
GSS-API support - GSS-API can be used for user authentication and for initial key exchange. The GSS-API is defined in RFC4462, Generic Security Service Application Program Interface.
-
Proxy commands - Solaris Secure Shell provides proxy commands for SOCKS5 and HTTP protocols. For an example, see How to Set Up Default Connections to Hosts Outside a Firewall.
In the Solaris Express Community Edition and the OpenSolaris releases, Solaris Secure Shell resyncs the SSH_OLD_FORWARD_ADDR compatibility flag from the OpenSSH project. As of March 2009, the Solaris Secure Shell version is 1.3.
Solaris Secure Shell (Task Map)
The following task map points to task maps for configuring Solaris Secure Shell and for using Solaris Secure Shell.
|
Task |
Description |
For Instructions |
|---|---|---|
|
Configure Solaris Secure Shell |
Guides administrators in configuring Solaris Secure Shell for users. | |
|
Use Solaris Secure Shell |
Guides users in using Solaris Secure Shell. |
Configuring Solaris Secure Shell (Task Map)
The following task map points to procedures for configuring Solaris Secure Shell.
|
Task |
Description |
For Instructions |
|---|---|---|
|
Configure host-based authentication |
Configures host-based authentication on the client and server. |
How to Set Up Host-Based Authentication for Solaris Secure Shell |
|
Configure a host to use v1 and v2 |
Creates public key files for hosts that use v1 and v2 protocols. | |
|
Configure port forwarding |
Enables users to use port forwarding. | |
|
Configure exceptions to SSH system defaults |
For users, hosts, groups, and addresses, specifies SSH settings that are different from the system defaults. |
How to Create User and Host Exceptions to SSH System Defaults |
Configuring Solaris Secure Shell
By default, host-based authentication and the use of both protocols are not enabled in Solaris Secure Shell. Changing these defaults requires administrative intervention. Also, for port forwarding to work requires administrative intervention.
 How to Set Up Host-Based Authentication
for Solaris Secure Shell
How to Set Up Host-Based Authentication
for Solaris Secure Shell
The following procedure sets up a public key system where the client's public key is used for authentication on the server. The user must also create a public/private key pair.
In the procedure, the terms client and local host refer to the machine where a user types the ssh command. The terms server and remote host refer to the machine that the client is trying to reach.
-
Assume the Primary Administrator role, or become superuser.
The Primary Administrator role includes the Primary Administrator profile. To create the role and assign the role to a user, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
On the client, enable host-based authentication.
In the client configuration file, /etc/ssh/ssh_config, type the following entry:
HostbasedAuthentication yes
For the syntax of the file, see the ssh_config(4) man page
-
On the server, enable host-based authentication.
In the server configuration file, /etc/ssh/sshd_config, type the same entry:
HostbasedAuthentication yes
For the syntax of the file, see the sshd_config(4) man page
-
On the server, configure a file that enables the client to be recognized as a trusted host.
For more information, see the FILES section of the sshd(1M) man page.
-
On the server, ensure that the sshd daemon can access the list of trusted hosts.
Set IgnoreRhosts to no in the /etc/ssh/sshd_config file.
## sshd_config IgnoreRhosts no
-
Ensure that users of Solaris Secure Shell at your site have accounts on both hosts.
-
Do one of the following to put the client's public key on the server.
-
Modify the sshd_config file on the server, then instruct your users to add the client's public host keys to their ~/.ssh/known_hosts file.
## sshd_config IgnoreUserKnownHosts no
For user instructions, see How to Generate a Public/Private Key Pair for Use With Solaris Secure Shell.
-
Copy the client's public key to the server.
The host keys are stored in the /etc/ssh directory. The keys are typically generated by the sshd daemon on first boot.
-
Add the key to the /etc/ssh/ssh_known_hosts file on the server.
On the client, type the command on one line with no backslash.
# cat /etc/ssh/ssh_host_dsa_key.pub | ssh RemoteHost \ 'cat >> /etc/ssh/ssh_known_hosts && echo "Host key copied"'
-
When you are prompted, supply your login password.
When the file is copied, the message “Host key copied” is displayed.
Each line in the /etc/ssh/ssh_known_hosts file consists of fields that are separated by spaces:
hostnames algorithm-name publickey comment
-
Edit the /etc/ssh/ssh_known_hosts file and add RemoteHost as the first field in the copied entry.
## /etc/ssh/ssh_known_hosts File RemoteHost <copied entry>
-
-
Example 19–1 Setting Up Host-based Authentication
In the following example, each host is configured as a server and as a client. A user on either host can initiate an ssh connection to the other host. The following configuration makes each host a server and a client:
-
On each host, the Solaris Secure Shell configuration files contain the following entries:
## /etc/ssh/ssh_config HostBasedAuthentication yes # ## /etc/ssh/sshd_config HostBasedAuthentication yes IgnoreRhosts no
-
On each host, the shosts.equiv file contains an entry for the other host:
## /etc/ssh/shosts.equiv on machine2 machine1
## /etc/ssh/shosts.equiv on machine1 machine2
-
The public key for each host is in the /etc/ssh/ssh_known_hosts file on the other host:
## /etc/ssh/ssh_known_hosts on machine2 … machine1
## /etc/ssh/ssh_known_hosts on machine1 … machine2
-
Users have an account on both hosts:
## /etc/passwd on machine1 jdoe:x:3111:10:J Doe:/home/jdoe:/bin/sh
## /etc/passwd on machine2 jdoe:x:3111:10:J Doe:/home/jdoe:/bin/sh
 How to Enable Solaris Secure Shell v1
How to Enable Solaris Secure Shell v1
This procedure is useful when a host interoperates with hosts that run v1 and v2.
-
Assume the Primary Administrator role, or become superuser.
The Primary Administrator role includes the Primary Administrator profile. To create the role and assign the role to a user, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
Configure the host to use both Solaris Secure Shell protocols.
Edit the /etc/ssh/sshd_config file.
# Protocol 2 Protocol 2,1
-
Provide a separate file for the host key for v1.
Add a HostKey entry to the /etc/ssh/sshd_config file.
HostKey /etc/ssh/ssh_host_rsa_key HostKey /etc/ssh/ssh_host_dsa_key HostKey /etc/ssh/ssh_host_rsa1_key
-
Generate a host key for v1.
# ssh-keygen -t rsa1 -f /etc/ssh/ssh_host_rsa1_key -N ''
- -t rsa1
-
Indicates the RSA algorithm for v1.
- -f
-
Indicates the file that holds the host key.
- -N ''
-
Indicates that no passphrase is required.
-
Restart the sshd daemon.
# svcadm restart network/ssh:default
You can also reboot the system.
 How to Configure Port Forwarding in Solaris Secure Shell
How to Configure Port Forwarding in Solaris Secure Shell
Port forwarding enables a local port be forwarded to a remote host. Effectively, a socket is allocated to listen to the port on the local side. Similarly, a port can be specified on the remote side.
Note –
Solaris Secure Shell port forwarding must use TCP connections. Solaris Secure Shell does not support UDP connections for port forwarding.
-
Assume the Primary Administrator role, or become superuser.
The Primary Administrator role includes the Primary Administrator profile. To create the role and assign the role to a user, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
Configure a Solaris Secure Shell setting on the remote server to allow port forwarding.
Change the value of AllowTcpForwarding to yes in the /etc/ssh/sshd_config file.
# Port forwarding AllowTcpForwarding yes
-
Restart the Solaris Secure Shell service.
remoteHost# svcadm restart network/ssh:default
For information on managing persistent services, see Chapter 16, Managing Services (Overview), in System Administration Guide: Basic Administration and the svcadm(1M) man page.
-
Verify that port forwarding can be used.
remoteHost# /usr/bin/pgrep -lf sshd 1296 ssh -L 2001:remoteHost:23 remoteHost
 How to Create User and Host
Exceptions to SSH System Defaults
How to Create User and Host
Exceptions to SSH System Defaults
This procedure adds a conditional Match block after the global section of the /etc/ssh/sshd_config file. Keyword-value pairs that follow the Match block specify exceptions for the user, group, host, or address that is specified as the match.
-
Assume the Primary Administrator role, or become superuser.
The Primary Administrator role includes the Primary Administrator profile. To create the role and assign the role to a user, see Chapter 2, Working With the Solaris Management Console (Tasks), in System Administration Guide: Basic Administration.
-
Edit the sshd_config file.
-
Configure a user, group, host, or address to use different SSH keyword settings from the default settings.
Place the Match blocks after the global settings.
Note –The global section of the file might or might not list the default settings. For the defaults, see the sshd_config(4) man page.
You might have users who should not be allowed to use TCP forwarding. In the following example, any user in the group public, and any user name that begins with test cannot use TCP forwarding:
## sshd_config file ## Global settings # Example (reflects default settings): # # Host * # ForwardAgent no # ForwardX11 no # PubkeyAuthentication yes # PasswordAuthentication yes # FallBackToRsh no # UseRsh no # BatchMode no # CheckHostIP yes # StrictHostKeyChecking ask # EscapeChar ~ Match Group public AllowTcpForwarding no Match User test* AllowTcpForwarding no
For information about the syntax of the Match block, see the sshd_config(4) man page.
Using Solaris Secure Shell (Task Map)
The following task map points to user procedures for using Solaris Secure Shell.
|
Task |
Description |
For Instructions |
|---|---|---|
|
Create a public/private key pair |
Enables access to Solaris Secure Shell for sites that require public-key authentication. |
How to Generate a Public/Private Key Pair for Use With Solaris Secure Shell |
|
Change your passphrase |
Changes the phrase that authenticates your private key. |
How to Change the Passphrase for a Solaris Secure Shell Private Key |
|
Log in with Solaris Secure Shell |
Provides encrypted Solaris Secure Shell communication when logging in remotely. The process is similar to using the rsh command. | |
|
Log in to Solaris Secure Shell without being prompted for a password |
Enables login by using an agent which provides your password to Solaris Secure Shell. | |
|
Use port forwarding in Solaris Secure Shell |
Specifies a local port or a remote port to be used in a Solaris Secure Shell connection over TCP. | |
|
Copy files with Solaris Secure Shell |
Securely copies files between hosts. | |
|
Securely connect from a host inside a firewall to a host outside the firewall |
Uses Solaris Secure Shell commands that are compatible with HTTP or SOCKS5 to connect hosts that are separated by a firewall. |
How to Set Up Default Connections to Hosts Outside a Firewall |
Using Solaris Secure Shell
Solaris Secure Shell provides secure access between a local shell and a remote shell. For more information, see the ssh_config(4) and ssh(1) man pages.
 How to Generate a Public/Private Key
Pair for Use With Solaris Secure Shell
How to Generate a Public/Private Key
Pair for Use With Solaris Secure Shell
Users must generate a public/private key pair when their site implements host-based authentication or user public-key authentication. For additional options, see the ssh-keygen(1) man page.
Before You Begin
Determine from your system administrator if host-based authentication is configured.
-
Start the key generation program.
myLocalHost% ssh-keygen -t rsa Generating public/private rsa key pair. …
where -t is the type of algorithm, one of rsa, dsa, or rsa1.
-
Specify the path to the file that will hold the key.
By default, the file name id_rsa, which represents an RSA v2 key, appears in parentheses. You can select this file by pressing the Return key. Or, you can type an alternative file name.
Enter file in which to save the key (/home/jdoe/.ssh/id_rsa):<Press Return>
The file name of the public key is created automatically by appending the string .pub to the name of the private key file.
-
Type a passphrase for using your key.
This passphrase is used for encrypting your private key. A null entry is strongly discouraged. Note that the passphrase is not displayed when you type it in.
Enter passphrase (empty for no passphrase): <Type passphrase>
-
Retype the passphrase to confirm it.
Enter same passphrase again: <Type passphrase> Your identification has been saved in /home/jdoe/.ssh/id_rsa. Your public key has been saved in /home/jdoe/.ssh/id_rsa.pub. The key fingerprint is: 0e:fb:3d:57:71:73:bf:58:b8:eb:f3:a3:aa:df:e0:d1 jdoe@myLocalHost
-
Check the results.
Check that the path to the key file is correct.
% ls ~/.ssh id_rsa id_rsa.pub
At this point, you have created a public/private key pair.
-
Choose the appropriate option:
-
If your administrator has configured host-based authentication, you might need to copy the local host's public key to the remote host.
You can now log in to the remote host. For details, see How to Log In to a Remote Host With Solaris Secure Shell.
-
If your site uses user authentication with public keys, populate your authorized_keys file on the remote host.
-
Copy your public key to the remote host.
Type the command on one line with no backslash.
myLocalHost% cat $HOME/.ssh/id_rsa.pub | ssh myRemoteHost \ 'cat >> .ssh/authorized_keys && echo "Key copied"'
-
When you are prompted, supply your login password.
When the file is copied, the message “Key copied” is displayed.
Enter password: Type login password Key copied myLocalHost%
-
-
-
(Optional) Reduce the prompting for passphrases.
For a procedure, see How to Reduce Password Prompts in Solaris Secure Shell. For more information, see the ssh-agent(1) and ssh-add(1) man pages.
Example 19–2 Establishing a v1 RSA Key for a User
In the following example, the user can contact hosts that run v1 of the Solaris Secure Shell protocol. To be authenticated by v1 hosts, the user creates a v1 key, then copies the public key portion to the remote host.
myLocalHost% ssh-keygen -t rsa1 -f /home/jdoe/.ssh/identity Generating public/private rsa key pair. … Enter passphrase (empty for no passphrase): <Type passphrase> Enter same passphrase again: <Type passphrase> Your identification has been saved in /home/jdoe/.ssh/identity. Your public key has been saved in /home/jdoe/.ssh/identity.pub. The key fingerprint is: … myLocalHost% ls ~/.ssh id_rsa id_rsa.pub identity identity.pub myLocalHost% cat $HOME/.ssh/identity.pub | ssh myRemoteHost \ 'cat >> .ssh/authorized_keys && echo "Key copied"' |
 How to Change the Passphrase for a Solaris Secure Shell Private
Key
How to Change the Passphrase for a Solaris Secure Shell Private
Key
The following procedure does not change the private key. The procedure changes the authentication mechanism for the private key, the passphrase. For more information, see the ssh-keygen(1) man page.
-
Change your passphrase.
Type the ssh-keygen command with the -p option, and answer the prompts.
myLocalHost% ssh-keygen -p Enter file which contains the private key (/home/jdoe/.ssh/id_rsa):<Press Return> Enter passphrase (empty for no passphrase): <Type passphrase> Enter same passphrase again: <Type passphrase>
where -p requests changing the passphrase of a private key file.
 How to Log In to a Remote Host With Solaris Secure Shell
How to Log In to a Remote Host With Solaris Secure Shell
-
Start a Solaris Secure Shell session.
Type the ssh command, and specify the name of the remote host.
myLocalHost% ssh myRemoteHost
A prompt questions the authenticity of the remote host:
The authenticity of host 'myRemoteHost' can't be established. RSA key fingerprint in md5 is: 04:9f:bd:fc:3d:3e:d2:e7:49:fd:6e:18:4f:9c:26 Are you sure you want to continue connecting(yes/no)?
This prompt is normal for initial connections to remote hosts.
-
If prompted, verify the authenticity of the remote host key.
-
If you cannot confirm the authenticity of the remote host, type no and contact your system administrator.
Are you sure you want to continue connecting(yes/no)? no
The administrator is responsible for updating the global /etc/ssh/ssh_known_hosts file. An updated ssh_known_hosts file prevents this prompt from appearing.
-
If you confirm the authenticity of the remote host, answer the prompt and continue to the next step.
Are you sure you want to continue connecting(yes/no)? yes
-
-
Conduct transactions on the remote host.
The commands that you send are encrypted. Any responses that you receive are encrypted.
-
Close the Solaris Secure Shell connection.
When you are finished, type exit or use your usual method for exiting your shell.
myRemoteHost% exit myRemoteHost% logout Connection to myRemoteHost closed myLocalHost%
 How to Reduce Password Prompts in Solaris Secure Shell
How to Reduce Password Prompts in Solaris Secure Shell
If you do not want to type your passphrase and your password to use Solaris Secure Shell, you can use the agent daemon. Start the daemon at the beginning of the session. Then, store your private keys with the agent daemon by using the ssh-add command. If you have different accounts on different hosts, add the keys that you need for the session.
You can start the agent daemon manually when needed, as described in the following procedure.
-
Start the agent daemon.
myLocalHost% eval `ssh-agent` Agent pid 9892
-
Verify that the agent daemon has been started.
myLocalHost% pgrep ssh-agent 9892
-
Add your private key to the agent daemon.
Type the ssh-add command.
myLocalHost% ssh-add Enter passphrase for /home/jdoe/.ssh/id_rsa: <Type passphrase> Identity added: /home/jdoe/.ssh/id_rsa(/home/jdoe/.ssh/id_rsa) myLocalHost%
-
Start a Solaris Secure Shell session.
myLocalHost% ssh myRemoteHost
You are not prompted for a passphrase.
Example 19–3 Using ssh-add Options
In this example, jdoe adds two keys to the agent daemon. The -l option is used to list all keys that are stored in the daemon. At the end of the session, the -D option is used to remove all the keys from the agent daemon.
myLocalHost% ssh-agent myLocalHost% ssh-add Enter passphrase for /home/jdoe/.ssh/id_rsa: <Type passphrase> Identity added: /home/jdoe/.ssh/id_rsa(/home/jdoe/.ssh/id_rsa) myLocalHost% ssh-add /home/jdoe/.ssh/id_dsa Enter passphrase for /home/jdoe/.ssh/id_dsa: <Type passphrase> Identity added: /home/jdoe/.ssh/id_dsa(/home/jdoe/.ssh/id_dsa) myLocalHost% ssh-add -l md5 1024 0e:fb:3d:53:71:77:bf:57:b8:eb:f7:a7:aa:df:e0:d1 /home/jdoe/.ssh/id_rsa(RSA) md5 1024 c1:d3:21:5e:40:60:c5:73:d8:87:09:3a:fa:5f:32:53 /home/jdoe/.ssh/id_dsa(DSA) User conducts Solaris Secure Shell transactions |
myLocalHost% ssh-add -D Identity removed: /home/jdoe/.ssh/id_rsa(/home/jdoe/.ssh/id_rsa.pub) /home/jdoe/.ssh/id_dsa(DSA) |
 How to Use Port Forwarding in Solaris Secure Shell
How to Use Port Forwarding in Solaris Secure Shell
You can specify that a local port be forwarded to a remote host. Effectively, a socket is allocated to listen to the port on the local side. The connection from this port is made over a secure channel to the remote host. For example, you might specify port 143 to obtain email remotely with IMAP4. Similarly, a port can be specified on the remote side.
Before You Begin
To use port forwarding, the administrator must have enabled port forwarding on the remote Solaris Secure Shell server. For details, see How to Configure Port Forwarding in Solaris Secure Shell.
-
To use secure port forwarding, choose one of the following options:
-
To set a local port to receive secure communication from a remote port, specify both ports.
Specify the local port that listens for remote communication. Also, specify the remote host and the remote port that forward the communication.
myLocalHost% ssh -L localPort:remoteHost:remotePort
-
To set a remote port to receive a secure connection from a local port, specify both ports.
Specify the remote port that listens for remote communication. Also, specify the local host and the local port that forward the communication.
myLocalHost% ssh -R remotePort:localhost:localPort
-
Example 19–4 Using Local Port Forwarding to Receive Mail
The following example demonstrates how you can use local port forwarding to receive mail securely from a remote server.
myLocalHost% ssh -L 9143:myRemoteHost:143 myRemoteHost |
This command forwards connections from port 9143 on myLocalHost to port 143. Port 143 is the IMAP v2 server port on myRemoteHost. When the user launches a mail application, the user needs to specify the local port number, as shown in the following dialog box.
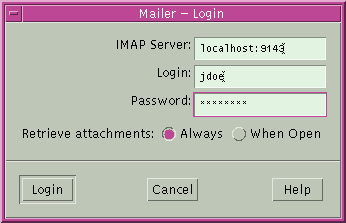
Do not confuse localhost in the dialog box with myLocalHost. myLocalHost is a hypothetical host name. localhost is a keyword that identifies your local system.
Example 19–5 Using Remote Port Forwarding to Communicate Outside of a Firewall
This example demonstrates how a user in an enterprise environment can forward connections from a host on an external network to a host inside a corporate firewall.
myLocalHost% ssh -R 9022:myLocalHost:22 myOutsideHost |
This command forwards connections from port 9022 on myOutsideHost to port 22, the sshd server, on the local host.
myOutsideHost% ssh -p 9022 localhost myLocalHost% |
 How to Copy Files With Solaris Secure Shell
How to Copy Files With Solaris Secure Shell
The following procedure shows how to use the scp command to copy encrypted files between hosts. You can copy encrypted files either between a local host and a remote host, or between two remote hosts. The command operates similarly to the rcp command, except that the scp command prompts for authentication. For more information, see the scp(1) man page.
You can also use the sftp, a more secure form of the ftp command. For more information, see the sftp(1) man page. For an example, see Example 19–6.
-
Start the secure copy program.
Specify the source file, the user name at the remote destination, and the destination directory.
myLocalHost% scp myfile.1 jdoe@myRemoteHost:~
-
Supply your passphrase when prompted.
Enter passphrase for key '/home/jdoe/.ssh/id_rsa': <Type passphrase> myfile.1 25% |******* | 640 KB 0:20 ETA myfile.1
After you type the passphrase, a progress meter is displayed. See the second line in the preceding output. The progress meter displays:
-
The file name
-
The percentage of the file that has been transferred
-
A series of asterisks that indicate the percentage of the file that has been transferred
-
The quantity of data transferred
-
The estimated time of arrival, or ETA, of the complete file (that is, the remaining amount of time)
-
Example 19–6 Specifying a Port When Using the sftp Command
In this example, the user wants the sftp command to use a specific port. The user uses the -o option to specify the port.
% sftp -o port=2222 guest@RemoteFileServer |
 How to Set Up Default Connections to
Hosts Outside a Firewall
How to Set Up Default Connections to
Hosts Outside a Firewall
You can use Solaris Secure Shell to make a connection from a host inside a firewall to a host outside the firewall. This task is done by specifying a proxy command for ssh either in a configuration file or as an option on the command line. For the command-line option, see Example 19–7.
In general, you can customize your ssh interactions through a configuration file.
-
You can customize either your own personal file in ~/.ssh/config.
-
Or, you can use the settings in the administrative configuration file, /etc/ssh/ssh_config.
The files can be customized with two types of proxy commands. One proxy command is for HTTP connections. The other proxy command is for SOCKS5 connections. For more information, see the ssh_config(4) man page.
-
Specify the proxy commands and hosts in a configuration file.
Use the following syntax to add as many lines as you need:
[Host outside-host] ProxyCommand proxy-command [-h proxy-server] \ [-p proxy-port] outside-host|%h outside-port|%p
- Host outside-host
-
Limits the proxy command specification to instances when a remote host name is specified on the command line. If you use a wildcard for outside-host, you apply the proxy command specification to a set of hosts.
- proxy-command
-
Specifies the proxy command.
The command can be either of the following:
-
/usr/lib/ssh/ssh-http-proxy-connect for HTTP connections
-
/usr/lib/ssh/ssh-socks5-proxy-connect for SOCKS5 connections
-
- -h proxy-server and -p proxy-port
-
These options specify a proxy server and a proxy port, respectively. If present, the proxies override any environment variables that specify proxy servers and proxy ports, such as HTTPPROXY, HTTPPROXYPORT, SOCKS5_PORT, SOCKS5_SERVER, and http_proxy. The http_proxy variable specifies a URL. If the options are not used, then the relevant environment variables must be set. For more information, see the ssh-socks5-proxy-connect(1) and ssh-http-proxy-connect(1) man pages.
- outside-host
-
Designates a specific host to connect to. Use the %h substitution argument to specify the host on the command line.
- outside-port
-
Designates a specific port to connect to. Use the %p substitution argument to specify the port on the command line. By specifying %h and %p without using the Host outside-host option, the proxy command is applied to the host argument whenever the ssh command is invoked.
-
Run Solaris Secure Shell, specifying the outside host.
For example, type the following:
myLocalHost% ssh myOutsideHost
This command looks for a proxy command specification for myOutsideHost in your personal configuration file. If the specification is not found, then the command looks in the system-wide configuration file, /etc/ssh/ssh_config. The proxy command is substituted for the ssh command.
Example 19–7 Connecting to Hosts Outside a Firewall From the Command Line
How to Set Up Default Connections to Hosts Outside a Firewall explains how to specify a proxy command in a configuration file. In this example, a proxy command is specified on the ssh command line.
% ssh -o'Proxycommand=/usr/lib/ssh/ssh-http-proxy-connect \ -h myProxyServer -p 8080 myOutsideHost 22' myOutsideHost |
The -o option to the ssh command provides a command-line method of specifying a proxy command. This example command does the following:
-
Substitutes the HTTP proxy command for ssh
-
Uses port 8080 and myProxyServer as the proxy server
-
Connects to port 22 on myOutsideHost
- © 2010, Oracle Corporation and/or its affiliates
