Audit Record Structure
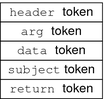
An audit record is a sequence of audit tokens. Each audit token contains event information such as user ID, time, and date. A header token begins an audit record, and an optional trailer token concludes the record. Other audit tokens contain information relevant to the audit event. The following figure shows a typical audit record.
Figure 31–3 Typical Audit Record Structure
Audit Record Analysis
Audit record analysis involves postselecting records from the audit trail. You can use one of two approaches to parsing the binary data that was collected.
-
You can parse the binary data stream. To parse the data stream, you need to know the order of the fields in each token, and the order of tokens in each record. You also need to know the variants of an audit record. For example, the ioctl() system call creates an audit record for “Bad file name” that contains different tokens from the audit record for “Invalid file descriptor”.
-
For a description of the order of binary data in each audit token, see the audit.log(4) man page.
-
For a description of the order of tokens in an audit record, use the auditrecord command. Output from the auditrecord command includes the different formats that occur under different conditions. Square brackets ([]) indicate that an audit token is optional. For more information, see the auditrecord(1M) man page. For examples, see also How to Display Audit Record Formats.
-
-
You can use the praudit command. Options to the command provide different text outputs. For example, the praudit -x command provides XML for input into scripts and browsers. praudit outputs do not include fields whose sole purpose is to help to parse the binary data. The outputs do not necessarily follow the order of the binary fields. Also, the order and format of praudit output is not guaranteed between Solaris releases.
For examples of praudit output, see How to View the Contents of Binary Audit Files, and the praudit(1M) man page.
For a description of the praudit output for each audit token, see the individual tokens in the Audit Token Formats section.
- © 2010, Oracle Corporation and/or its affiliates
